First National University: Network Redesign and Security Solution
VerifiedAdded on 2023/06/11
|49
|7817
|325
Report
AI Summary
This document presents a solution to a network redesign and security implementation assignment based on the First National University (FNU) case study. The solution is divided into two parts: network redesign and security technology implementation. The network redesign section covers business and technical goals, existing network analysis, network traffic analysis, and logical and physical network redesign proposals, focusing on the Headquarters and Operations facilities. The technical goals address scalability, availability, network performance, security, manageability, usability, adaptability, and affordability. The security technology implementation section details the implementation of five security controls, including their objectives and the resources used. The solution emphasizes VPN services for secure remote access and the use of third-party providers for web services, ensuring security, load balancing, and failover. This document provides a comprehensive approach to enhancing FNU's network infrastructure and security posture and is available for review and download on Desklib, a platform offering various study tools and resources.

Table of Contents
PART 2-Network redesign............................................................................................................................2
1. Overview.................................................................................................................................................2
1.1 Business goals........................................................................................................................................3
1.2 Technical goals......................................................................................................................................4
1.3 Existing network....................................................................................................................................9
1.4 Network traffic analysis.......................................................................................................................13
1.5 Logical network redesign.....................................................................................................................14
1.6 Physical network redesign...................................................................................................................18
2. Conclusion.............................................................................................................................................19
References.................................................................................................................................................20
PART 3-Security technology implementation............................................................................................22
3. Overview...............................................................................................................................................22
3.1 Control 1..............................................................................................................................................23
3.2 Control 2..............................................................................................................................................44
3.3 Control 3..............................................................................................................................................44
3.4 Control 4..............................................................................................................................................45
3.5 Control 5..............................................................................................................................................45
4. Conclusion.............................................................................................................................................46
References.................................................................................................................................................47
1
PART 2-Network redesign............................................................................................................................2
1. Overview.................................................................................................................................................2
1.1 Business goals........................................................................................................................................3
1.2 Technical goals......................................................................................................................................4
1.3 Existing network....................................................................................................................................9
1.4 Network traffic analysis.......................................................................................................................13
1.5 Logical network redesign.....................................................................................................................14
1.6 Physical network redesign...................................................................................................................18
2. Conclusion.............................................................................................................................................19
References.................................................................................................................................................20
PART 3-Security technology implementation............................................................................................22
3. Overview...............................................................................................................................................22
3.1 Control 1..............................................................................................................................................23
3.2 Control 2..............................................................................................................................................44
3.3 Control 3..............................................................................................................................................44
3.4 Control 4..............................................................................................................................................45
3.5 Control 5..............................................................................................................................................45
4. Conclusion.............................................................................................................................................46
References.................................................................................................................................................47
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

PART 2-Network redesign
1. Overview
In this project the network redesign is considered about the design of network in the
organization and it helps to make a way to the person access the needed one. According to the
scenario the network such as LAN and wan network used in the network design and multiple
devices take a place in the design of the network and make a clear vision to the user and in that
scenario it is used to the students in the organization.
And the implementation of network design described below kind of diagrams. And the
scenario is tell about the requirements such as network based and the design used to be the
students with the goal of technical and also in business. So in the organization the network is
much needed one and that network used to the students to get the access from the department and
the network is to be used in the way kind of LAN and wan network.
These both network has been used to the design of such network platform used to the
students and their related studies. In the organization they are used to different platform for the
students and it has the goals such as business and technical. LAN network is used completely in
the form of network connection inside the areas such as lab and similarly the wan network is
used to the network for the total place occupied in the organization.
And in this project the network made by using the devices and that is related to the
network. And the network platform has made upon using the firewall and the techniques are used
in this design to make perfect network for the organization. And in that network design it
includes the traffic analysis of the network by using the hosts in that it includes many servers and
the network design in the way of logical and physical design.
In that logical design it explains about the network devices design and mentioned about
ip address allocation and virtual LAN configuration and described about the sub netting and the
sub netting is used to spread the network to the below network based on the scenario such as the
work or resources to the basic network.
2
1. Overview
In this project the network redesign is considered about the design of network in the
organization and it helps to make a way to the person access the needed one. According to the
scenario the network such as LAN and wan network used in the network design and multiple
devices take a place in the design of the network and make a clear vision to the user and in that
scenario it is used to the students in the organization.
And the implementation of network design described below kind of diagrams. And the
scenario is tell about the requirements such as network based and the design used to be the
students with the goal of technical and also in business. So in the organization the network is
much needed one and that network used to the students to get the access from the department and
the network is to be used in the way kind of LAN and wan network.
These both network has been used to the design of such network platform used to the
students and their related studies. In the organization they are used to different platform for the
students and it has the goals such as business and technical. LAN network is used completely in
the form of network connection inside the areas such as lab and similarly the wan network is
used to the network for the total place occupied in the organization.
And in this project the network made by using the devices and that is related to the
network. And the network platform has made upon using the firewall and the techniques are used
in this design to make perfect network for the organization. And in that network design it
includes the traffic analysis of the network by using the hosts in that it includes many servers and
the network design in the way of logical and physical design.
In that logical design it explains about the network devices design and mentioned about
ip address allocation and virtual LAN configuration and described about the sub netting and the
sub netting is used to spread the network to the below network based on the scenario such as the
work or resources to the basic network.
2

1.1 Business goals
The business goal of the organization is to make a design of network which is used to the
students and their studies. And not only students and the high position people also follow the
network to their work using this network redesign by the parameters of the network.
In this business goals it is related to the scenario in that it has the big organization
through this they providing the network to the operations and the operation in the kind of
metropolitan and regional and these separated as graduate in the way undergraduate and post
graduate and in here many students are offered many programs.
And it has three options like operation, Headquarters and backup. And each of the
operation is held on different places within the certain range. And has a warehouse to provide the
data to the related person as staff and the backup is used to store the contents about the operation
and include the technical related functions.
And in that each operation uses the network devices such as routers and LAN and wan
networks. And the topology is used to the network kind of design and transfer of data. And the
network design should be support the learning and research activity.
And the network should be good in performance and need to be constant in the network
design and the departments should follow the network used to share the content related to the
department for the technical information.
And this network design is used to solve the problems happened in the network. And by
the usage of network in the scenario the staff can communicate easily with the students. And the
security issues are analyzed in these network connection.
Security is the main issue in the network and it has to be solved through this network
design by using the network components and devices and the traffic has to be analyzed through
the firewall settings in the network design and the sub netting is help to manage the network
traffic in terms of spread the network to the sub fields in the network.
3
The business goal of the organization is to make a design of network which is used to the
students and their studies. And not only students and the high position people also follow the
network to their work using this network redesign by the parameters of the network.
In this business goals it is related to the scenario in that it has the big organization
through this they providing the network to the operations and the operation in the kind of
metropolitan and regional and these separated as graduate in the way undergraduate and post
graduate and in here many students are offered many programs.
And it has three options like operation, Headquarters and backup. And each of the
operation is held on different places within the certain range. And has a warehouse to provide the
data to the related person as staff and the backup is used to store the contents about the operation
and include the technical related functions.
And in that each operation uses the network devices such as routers and LAN and wan
networks. And the topology is used to the network kind of design and transfer of data. And the
network design should be support the learning and research activity.
And the network should be good in performance and need to be constant in the network
design and the departments should follow the network used to share the content related to the
department for the technical information.
And this network design is used to solve the problems happened in the network. And by
the usage of network in the scenario the staff can communicate easily with the students. And the
security issues are analyzed in these network connection.
Security is the main issue in the network and it has to be solved through this network
design by using the network components and devices and the traffic has to be analyzed through
the firewall settings in the network design and the sub netting is help to manage the network
traffic in terms of spread the network to the sub fields in the network.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

And in networking design the security is the essential operation to send the data with
secured structure and the design has to be secured to the process in the network platform. And in
this students can make the problems with the organization rules and can make proxy through this
network so we have to provide the security for the network design.
Normally the business goal of some organizations is like have to grow the efficiency and
to increase the performance level and services and need to be focus on the development of the
company or some organizations. In the scenario it mainly focusing on the college and network
settings for that infrastructure.
And the main business goal is to make a network design to reach them to all who the
students and other staffs and in that organization they leads that such kind of business in the way
of providing opportunities to the students in the way of reduce the complex and make the place
in terms of network connect and also the wireless connection for the students.
For the network connection here different kind of networks has been used and the
networks is useful for the communication and development of the organization works and also it
is used more kind of things related to the network.
The business goal of organization is in the way to provide the secured with feasible
opportunities to the students through the network. And the network should be appropriate and
usable. And it have a connection with technical goals and it acts as an overview for the technical
goals. And the business goals contains the requirements to accomplish the goal useful for the
students.
1.2 Technical goals
The technical aim of this network to make a perfect design with the network devices and
in that network it concerns about the security issues and the data, scalability, Availability and use
to analyze the network performance and also usability.
Scalability
In information technology the scalability used to two different usage. First one it has the
ability of the computer hardware or software. And also it changes the size and volume of the
4
secured structure and the design has to be secured to the process in the network platform. And in
this students can make the problems with the organization rules and can make proxy through this
network so we have to provide the security for the network design.
Normally the business goal of some organizations is like have to grow the efficiency and
to increase the performance level and services and need to be focus on the development of the
company or some organizations. In the scenario it mainly focusing on the college and network
settings for that infrastructure.
And the main business goal is to make a network design to reach them to all who the
students and other staffs and in that organization they leads that such kind of business in the way
of providing opportunities to the students in the way of reduce the complex and make the place
in terms of network connect and also the wireless connection for the students.
For the network connection here different kind of networks has been used and the
networks is useful for the communication and development of the organization works and also it
is used more kind of things related to the network.
The business goal of organization is in the way to provide the secured with feasible
opportunities to the students through the network. And the network should be appropriate and
usable. And it have a connection with technical goals and it acts as an overview for the technical
goals. And the business goals contains the requirements to accomplish the goal useful for the
students.
1.2 Technical goals
The technical aim of this network to make a perfect design with the network devices and
in that network it concerns about the security issues and the data, scalability, Availability and use
to analyze the network performance and also usability.
Scalability
In information technology the scalability used to two different usage. First one it has the
ability of the computer hardware or software. And also it changes the size and volume of the
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

computer application based on the user. The re scaling process has a big size of volume. It
includes lot of resources like a line of computer system, different size if terms, and RAM.
The second usage is the function of the rescaled situation. For instance an application
program should be scalable, and then it moves from small operating system to large operating
system. Then we need large number of users for control the operating system. Scalability is the
best method for downloaders.
Scalability describes the ability of a process, network, software or organizational growth.
And also is used for manage the system, business, and also the software. Scalability has an
ability to adapt the changes based on the user needs. The organization, network system, or
software’s are use the scalability process for handle the demands, increase the productions, and
also perform the user needs.
Availability
Availability means percentage of time, in a particular time interval which server is
complete designed and built it using cloud service or other machines. Normally the formula is
used to calculate the network availability. Availability is the ratio between the uptime and total
time.
Availability= uptime/total time
And also,
Total time= down time+ uptime. The total time is calculated by adding the down time
and up time. The VPN tunnel is used for calculate the network availability. In VPN tunnel it
includes only the internal applications not the external applications.
In this calculation, the availability is calculated by the multiplication of external
application weight and internet network availability. Then add the result into multiplication of
internal application weight and VPN network availability.
5
includes lot of resources like a line of computer system, different size if terms, and RAM.
The second usage is the function of the rescaled situation. For instance an application
program should be scalable, and then it moves from small operating system to large operating
system. Then we need large number of users for control the operating system. Scalability is the
best method for downloaders.
Scalability describes the ability of a process, network, software or organizational growth.
And also is used for manage the system, business, and also the software. Scalability has an
ability to adapt the changes based on the user needs. The organization, network system, or
software’s are use the scalability process for handle the demands, increase the productions, and
also perform the user needs.
Availability
Availability means percentage of time, in a particular time interval which server is
complete designed and built it using cloud service or other machines. Normally the formula is
used to calculate the network availability. Availability is the ratio between the uptime and total
time.
Availability= uptime/total time
And also,
Total time= down time+ uptime. The total time is calculated by adding the down time
and up time. The VPN tunnel is used for calculate the network availability. In VPN tunnel it
includes only the internal applications not the external applications.
In this calculation, the availability is calculated by the multiplication of external
application weight and internet network availability. Then add the result into multiplication of
internal application weight and VPN network availability.
5

Network performance
The network performance defines the analysis and review of collection of network
statistics. The underlying computer networks are used for define the quality of service. It is also
known as qualitative and quantitative process. That measures the performance of available
network. And also it tells the details about the network administrator review, measures, and also
takes some improvements.
The user deliver the quality of network service, using network performance and this
service are easily deployed. Normally the network performance is used for measure the end user
perspective. The following network components are used for measure the statistics and metrics
of the network performance.
Network bandwidth or capacity
Network throughput
Network delay or latency
Data loses
Network errors
The network bandwidth is used for check the availability of data transfer. Capacity
means shows the entire storage of the system. Second one is network throughput; it means the
entire amount of data is successfully transferred over the network in a given time limit. Third one
is network delay or latency, the packet transfer is little slow compared to the normal packets.
Final one is data loss and network errors, the packets are dropped or lose their quality, and also
the transmission and delivery is lost.
Security
Network security means is any activity, used for protect the usability and integrity of the
networks and also the data. The computer hardware and software use the network security. The
most effective network security is used to manage the accessible network. We are using several
threats to stop the network spreading.
Different types of network securities are used, like access control, antivirus, and
antimalware software, application security, behavioral analytics, data loss prevention, and email
6
The network performance defines the analysis and review of collection of network
statistics. The underlying computer networks are used for define the quality of service. It is also
known as qualitative and quantitative process. That measures the performance of available
network. And also it tells the details about the network administrator review, measures, and also
takes some improvements.
The user deliver the quality of network service, using network performance and this
service are easily deployed. Normally the network performance is used for measure the end user
perspective. The following network components are used for measure the statistics and metrics
of the network performance.
Network bandwidth or capacity
Network throughput
Network delay or latency
Data loses
Network errors
The network bandwidth is used for check the availability of data transfer. Capacity
means shows the entire storage of the system. Second one is network throughput; it means the
entire amount of data is successfully transferred over the network in a given time limit. Third one
is network delay or latency, the packet transfer is little slow compared to the normal packets.
Final one is data loss and network errors, the packets are dropped or lose their quality, and also
the transmission and delivery is lost.
Security
Network security means is any activity, used for protect the usability and integrity of the
networks and also the data. The computer hardware and software use the network security. The
most effective network security is used to manage the accessible network. We are using several
threats to stop the network spreading.
Different types of network securities are used, like access control, antivirus, and
antimalware software, application security, behavioral analytics, data loss prevention, and email
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

security, firewalls, intrusion prevention system, mobile device security, network segmentation,
security information and event management, VPA, web security, and wireless security.
Manageability
Sample diagram
The manageability functions are classified into four categories:
Logging, health monitoring, and alerting
Control and configuration
Updates and deployment
Asset discovery and inventory
Usability
The web applications and software consider the usability for achieving their goals
effectively and also efficiently. The usability includes the different level of user interface. And
also the non-functional requirement is used in this technique. The usability design process
consider three different principals, they are
Iterative focus on the user and the task
7
security information and event management, VPA, web security, and wireless security.
Manageability
Sample diagram
The manageability functions are classified into four categories:
Logging, health monitoring, and alerting
Control and configuration
Updates and deployment
Asset discovery and inventory
Usability
The web applications and software consider the usability for achieving their goals
effectively and also efficiently. The usability includes the different level of user interface. And
also the non-functional requirement is used in this technique. The usability design process
consider three different principals, they are
Iterative focus on the user and the task
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Iterative design
Empirical measurement
The evaluation of usability is done by the following methods.
Cognitive modeling
Inspection
Inquiry
Prototyping
Testing
Adaptability
A good network means they have an ability to adapt any kind of new technologies and
also the changes. They have no of features for adapting the new protocols, new business,
practical, new goals, and new registration. The availability needs more effects. And the traffic
patterns are changed by using the flexible design.
Using adaptability we can achieve three working models
WG1- GESCANT
WG2- ADAPNA
WG3- OR BITS
Affordability
Affordability is also known as cost effectiveness process, the main goal of affordability is
reduce the total amount of traffic from the given financial cost. Basically all the campus
networks are low cost and also reduce the network traffic. Sometimes we are using the enterprise
networks for achieving the low cost.
8
Empirical measurement
The evaluation of usability is done by the following methods.
Cognitive modeling
Inspection
Inquiry
Prototyping
Testing
Adaptability
A good network means they have an ability to adapt any kind of new technologies and
also the changes. They have no of features for adapting the new protocols, new business,
practical, new goals, and new registration. The availability needs more effects. And the traffic
patterns are changed by using the flexible design.
Using adaptability we can achieve three working models
WG1- GESCANT
WG2- ADAPNA
WG3- OR BITS
Affordability
Affordability is also known as cost effectiveness process, the main goal of affordability is
reduce the total amount of traffic from the given financial cost. Basically all the campus
networks are low cost and also reduce the network traffic. Sometimes we are using the enterprise
networks for achieving the low cost.
8
The campus network design must use the affordability for reduce the financial cost.
Quality routing protocol is the best example of affordability.
Sample affordable policy diagram
1.3 Existing network
The network is used her such as LAN and wan. And the LAN network is used to provide
the network within the particular area. And the wan network provides the network within one
city. In this scenario is mentioned the LAN network is considered inside the class room and the
wan network considered in the total areas.
Many systems are connected together is called network. Advantage of network in
conversation and transfer many files or documents into one system to another system.
Existing network called disadvantages of network, if network wires and servers can be
hostile. Administration of big network is a very complicated and occur many problems. Mainly
drawback virus, it spreader one computer another computer. Hacking is one of the main reason,
unwanted person access your files very dangerous. Network Topology classified at two types.
9
Quality routing protocol is the best example of affordability.
Sample affordable policy diagram
1.3 Existing network
The network is used her such as LAN and wan. And the LAN network is used to provide
the network within the particular area. And the wan network provides the network within one
city. In this scenario is mentioned the LAN network is considered inside the class room and the
wan network considered in the total areas.
Many systems are connected together is called network. Advantage of network in
conversation and transfer many files or documents into one system to another system.
Existing network called disadvantages of network, if network wires and servers can be
hostile. Administration of big network is a very complicated and occur many problems. Mainly
drawback virus, it spreader one computer another computer. Hacking is one of the main reason,
unwanted person access your files very dangerous. Network Topology classified at two types.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Physical Network Topologies
It is used to build the network. Basically hardware tool is used to configure of
many network. Hardware tool used commonly lack that the architecture of web based on given
design.
Types
It has five types. And they are Point to point topology, Bus topology, Ring
Topology, Star Topology, Hub and Spoke Topology, Point to Multipoint topology.
Point to point topology
Point to point topology is used to communication purpose. This communication
link connect to two stations up a lone hardware connection. This topology used for connectivity
purpose at serial port of topology. It is called as daisy chaining.
Bus Topology
Topology worked at connect too many computer in single cable. That single cable
is type of coaxial cable used.
Ring Topology
Ring topology defines as connecting from one system to many systems. This
process in commonly used for both interfaces. Token ring is used for allow to transfer process.
Star Topology
Star typology is the important topology of physical network. Because star
topology is used for all network building purpose. To use hub for all network connected to
station.
Point to Multi point
It is defined as a single platform network to run a multi-platform network.
10
It is used to build the network. Basically hardware tool is used to configure of
many network. Hardware tool used commonly lack that the architecture of web based on given
design.
Types
It has five types. And they are Point to point topology, Bus topology, Ring
Topology, Star Topology, Hub and Spoke Topology, Point to Multipoint topology.
Point to point topology
Point to point topology is used to communication purpose. This communication
link connect to two stations up a lone hardware connection. This topology used for connectivity
purpose at serial port of topology. It is called as daisy chaining.
Bus Topology
Topology worked at connect too many computer in single cable. That single cable
is type of coaxial cable used.
Ring Topology
Ring topology defines as connecting from one system to many systems. This
process in commonly used for both interfaces. Token ring is used for allow to transfer process.
Star Topology
Star typology is the important topology of physical network. Because star
topology is used for all network building purpose. To use hub for all network connected to
station.
Point to Multi point
It is defined as a single platform network to run a multi-platform network.
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
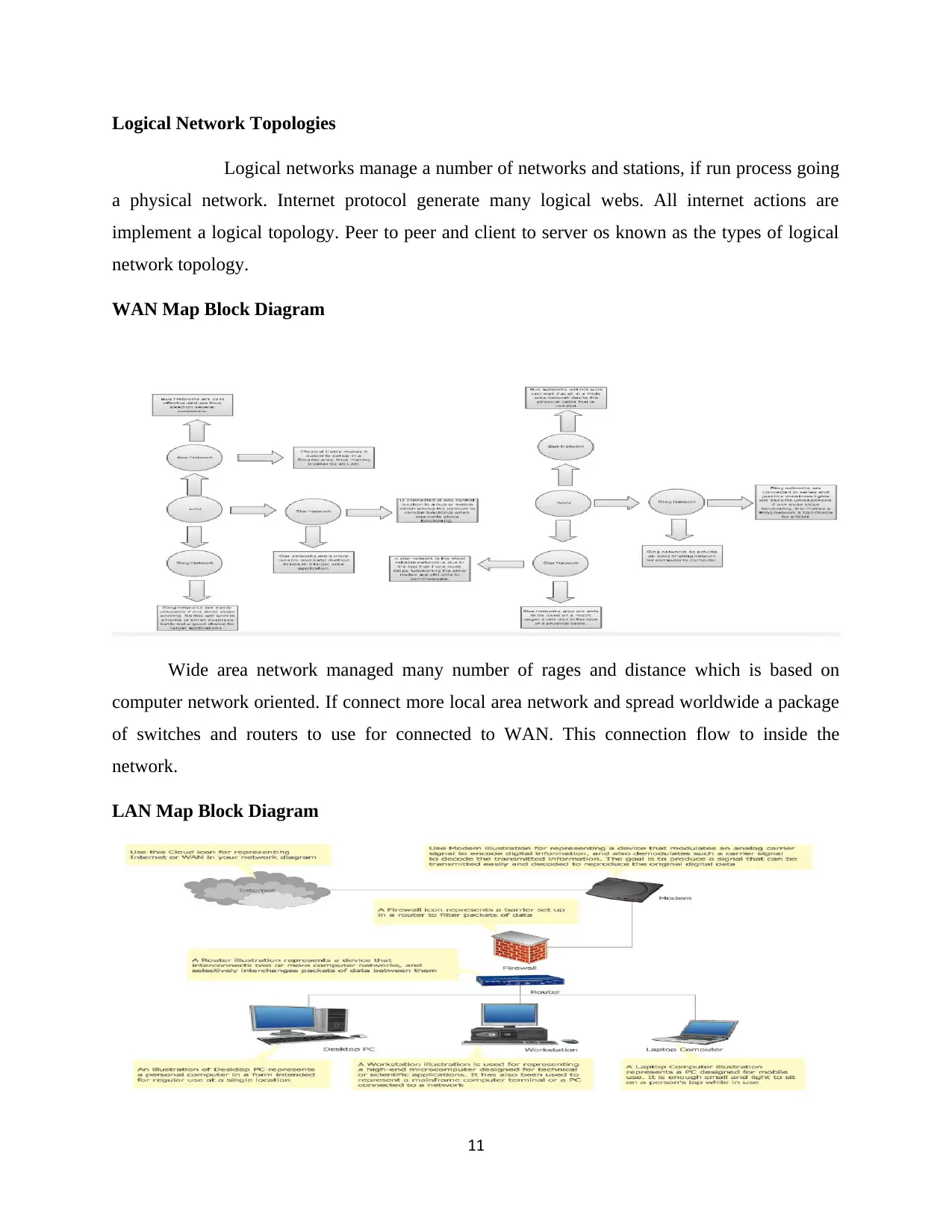
Logical Network Topologies
Logical networks manage a number of networks and stations, if run process going
a physical network. Internet protocol generate many logical webs. All internet actions are
implement a logical topology. Peer to peer and client to server os known as the types of logical
network topology.
WAN Map Block Diagram
Wide area network managed many number of rages and distance which is based on
computer network oriented. If connect more local area network and spread worldwide a package
of switches and routers to use for connected to WAN. This connection flow to inside the
network.
LAN Map Block Diagram
11
Logical networks manage a number of networks and stations, if run process going
a physical network. Internet protocol generate many logical webs. All internet actions are
implement a logical topology. Peer to peer and client to server os known as the types of logical
network topology.
WAN Map Block Diagram
Wide area network managed many number of rages and distance which is based on
computer network oriented. If connect more local area network and spread worldwide a package
of switches and routers to use for connected to WAN. This connection flow to inside the
network.
LAN Map Block Diagram
11

This figure mentioned at below to spread internet via LAN. Internet broadcast to modem.
Modem is used to delivery purpose. Modem send to signal at firewall. Firewall used for security
purpose. Next router connect one port to many systems include workstation. Router connected to
firewall and spread to internet from workstation and sub systems.
Interconnection Device
This device grant that single system to communicate at many systems. This
communication process flowing an LAN wire or Landline. Is converted to big and difficult
switching method to used interconnecting way to build number of networks.
This figure mentioned at single core switch used. Core switch is a high quality switch, is placed
in physical part. Core switch is main part of diagram, is broad cast link to firewall and router,
number of switches.
Workgroup switch is an approximately low quality switch, it supply the work for smaller
group of labors. Floor switch is an electrical cabling and used for control the lights. The
workgroup and floor switch is continuously connected at different paths.
Network Segments
Network portion is a part of network that described as actions of network. This machine
supported as a repeater, hub, bridge, switch or router. Given segment control at single to many
computer.
12
Modem is used to delivery purpose. Modem send to signal at firewall. Firewall used for security
purpose. Next router connect one port to many systems include workstation. Router connected to
firewall and spread to internet from workstation and sub systems.
Interconnection Device
This device grant that single system to communicate at many systems. This
communication process flowing an LAN wire or Landline. Is converted to big and difficult
switching method to used interconnecting way to build number of networks.
This figure mentioned at single core switch used. Core switch is a high quality switch, is placed
in physical part. Core switch is main part of diagram, is broad cast link to firewall and router,
number of switches.
Workgroup switch is an approximately low quality switch, it supply the work for smaller
group of labors. Floor switch is an electrical cabling and used for control the lights. The
workgroup and floor switch is continuously connected at different paths.
Network Segments
Network portion is a part of network that described as actions of network. This machine
supported as a repeater, hub, bridge, switch or router. Given segment control at single to many
computer.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 49
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



