Detailed Plan for Forensic Acquisition of SD Card with FTK Imager
VerifiedAdded on 2022/10/02
|15
|1369
|94
Practical Assignment
AI Summary
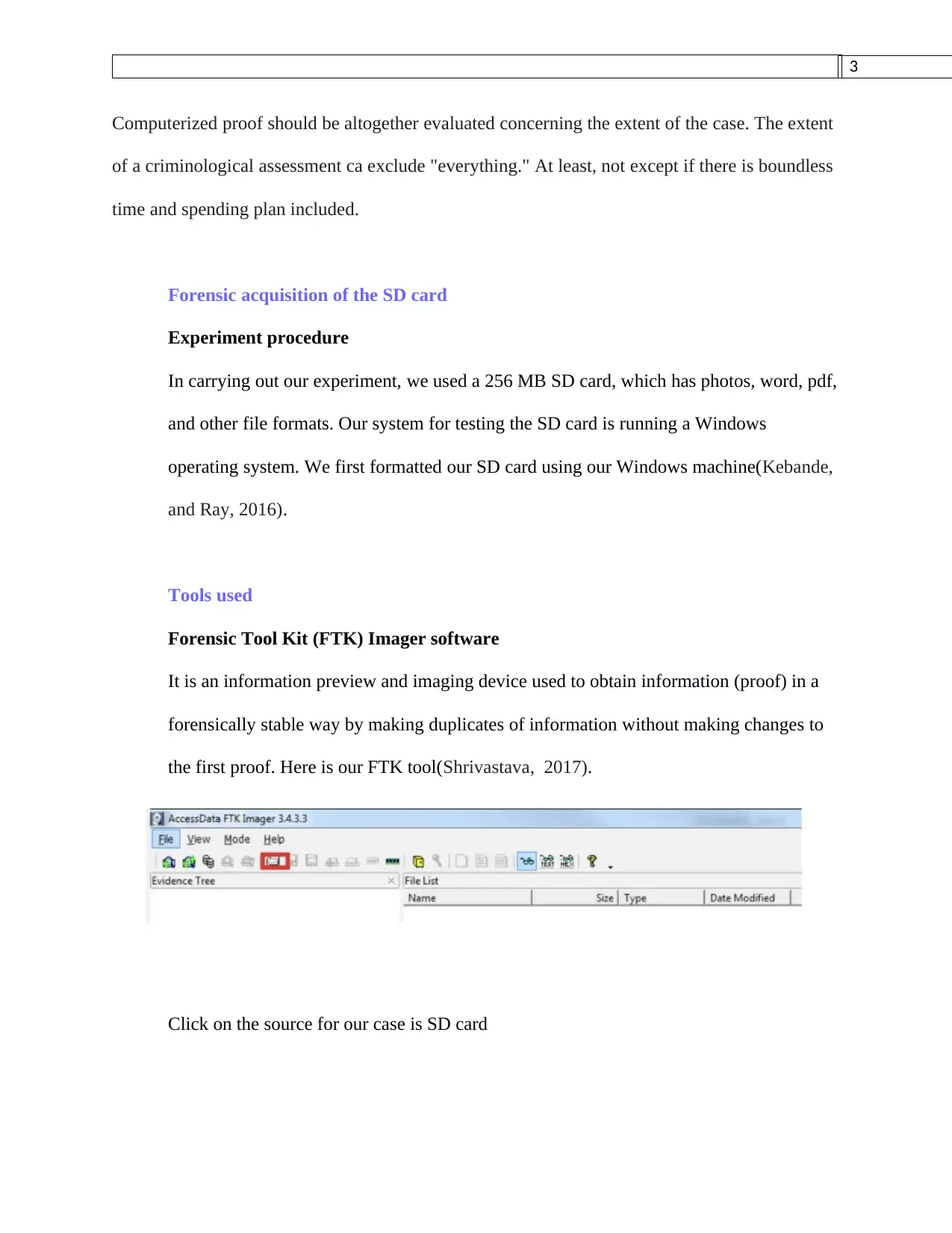
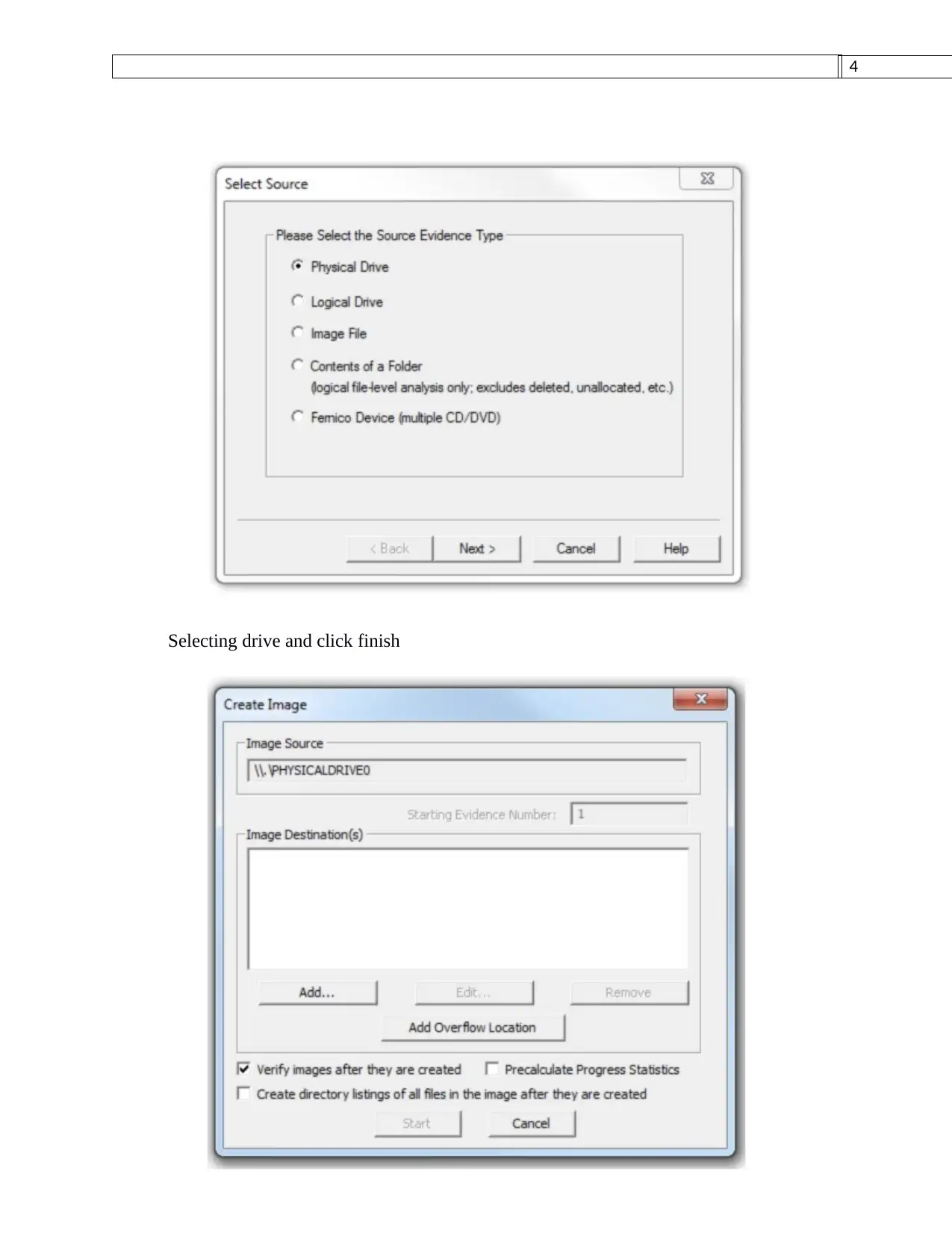
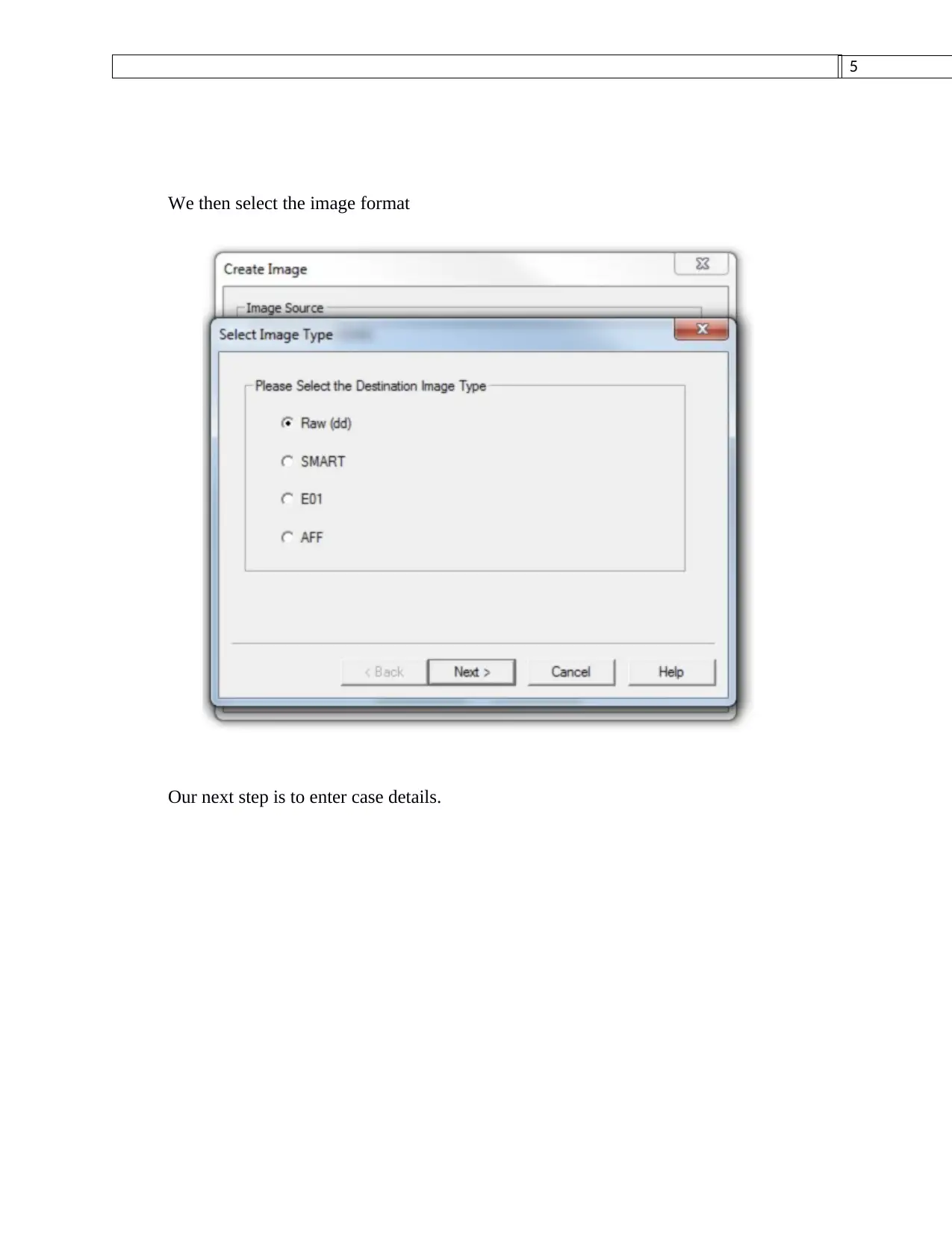
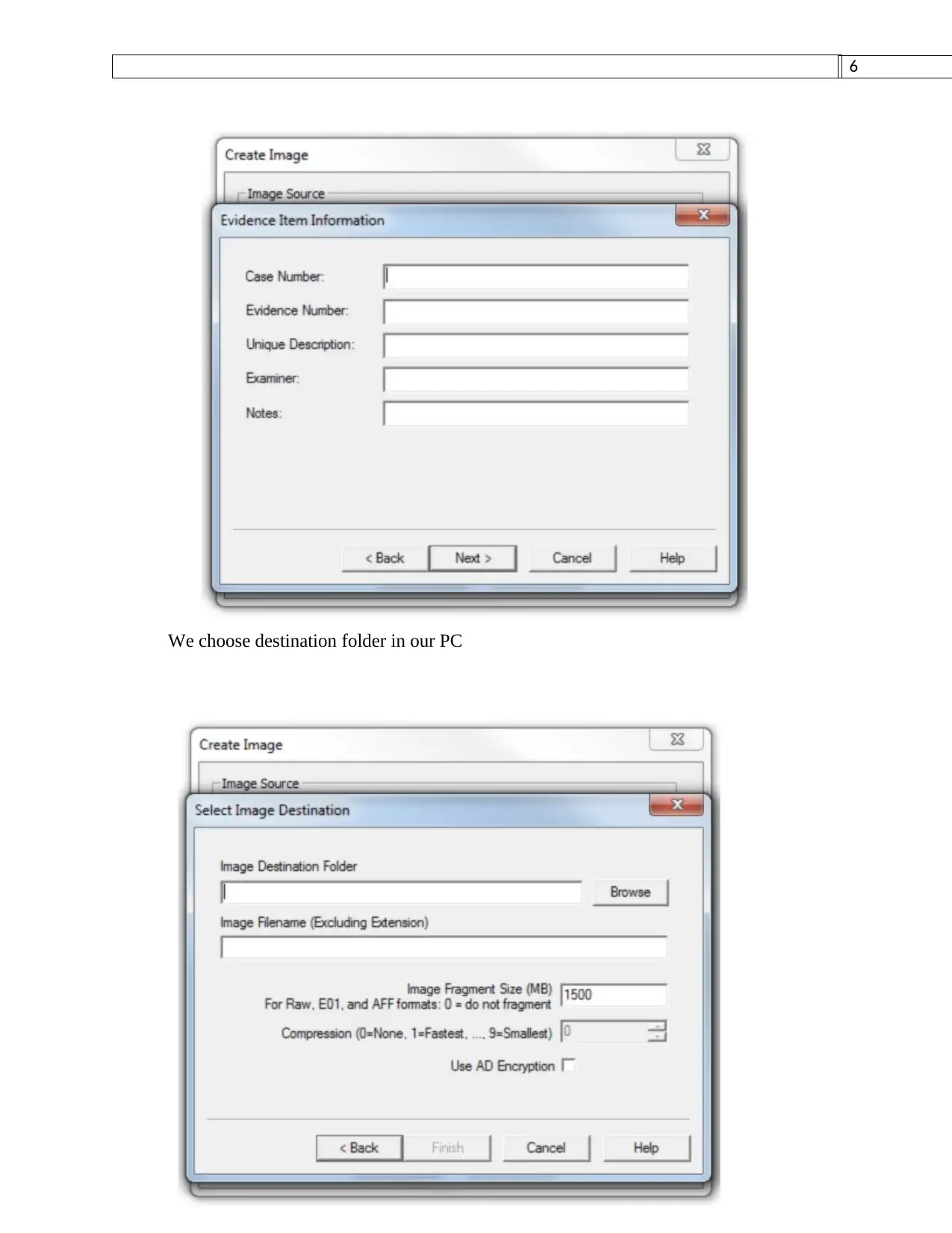
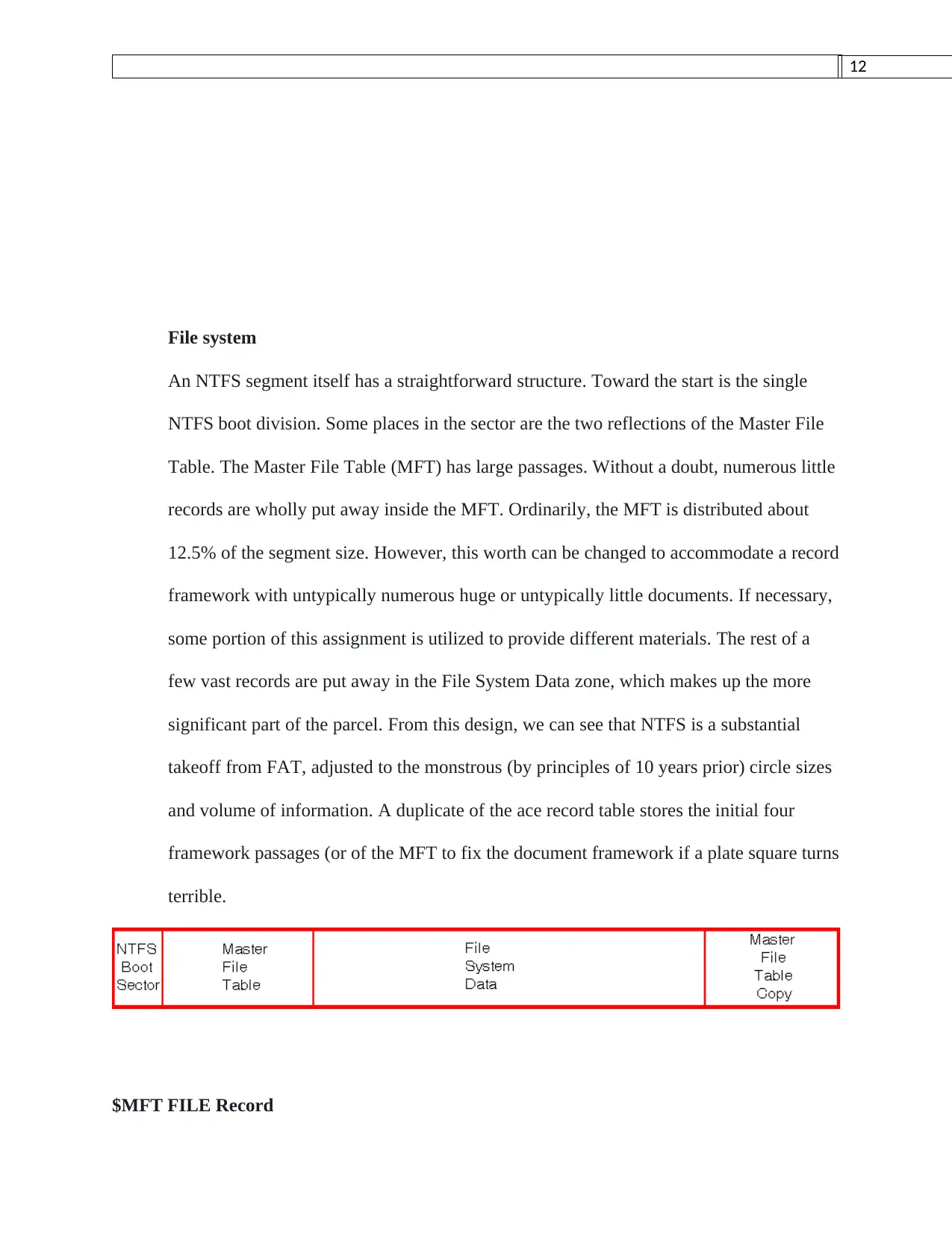
This assignment provides a comprehensive plan for the forensic acquisition of data from an SD card, formatted with a FAT32 file system, using the FTK Imager tool. The plan begins with establishing the scope and identifying key players, followed by the use of FTK Imager to create a forensically sound image of the SD card. The process includes selecting the SD card as the source, choosing the image format, and entering case details. The assignment also describes the tools used for data recovery, such as MjM Free Photo Recovery Software and Inspector Smart Recovery, and provides insights into the file system structure, including the NTFS segment and the MFT record. The student's methodology ensures the reliability and admissibility of the evidence, emphasizing the importance of a structured report understandable to both technical and non-technical readers. The assignment also references relevant academic papers to support the methodology and tools used, demonstrating a strong understanding of digital forensic principles and practices.
1 out of 15




![[object Object]](/_next/static/media/star-bottom.7253800d.svg)