Digital Forensics Report: Impact, Evidence, and Investigation
VerifiedAdded on 2019/12/03
|18
|5256
|724
Report
AI Summary
This report delves into the evolving field of digital forensics, specifically focusing on mobile device investigations. It examines the increasing need for mobile forensics due to the widespread use of smartphones for data storage, online transactions, and criminal activities. The report evaluates current forensic practices, highlighting the challenges associated with obtaining evidence from mobile devices and the impact of forensic investigations on both social and commercial environments. It discusses the influence of motivation, data manipulation, and malware, providing figures on malware rates and the impact of these threats. The report also presents a case study involving the use of mobile forensics in a criminal investigation, emphasizing the principles of evidence gathering and the importance of adhering to legal authorities. Finally, it assesses current evidence gathering practices and the implications of new legislations and communication technologies in addressing emerging digital crimes.

Digital Forensics
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
INTRODUCTION...........................................................................................................................1
Evaluating current forensic practice............................................................................................1
Potential impact of forensic investigation on the social and commercial environments.............3
Examined the impact of motivation, data manipulation and malware........................................4
Criminal activity associated with chosen case.............................................................................5
Discussing the principles of evidence gathering.........................................................................6
Evaluating current evidence gathering practices and assess their impacts................................10
New legislations and communication technologies to deal new area of crime:........................11
CONCLUSION..............................................................................................................................12
REFERENCES..............................................................................................................................13
INTRODUCTION...........................................................................................................................1
Evaluating current forensic practice............................................................................................1
Potential impact of forensic investigation on the social and commercial environments.............3
Examined the impact of motivation, data manipulation and malware........................................4
Criminal activity associated with chosen case.............................................................................5
Discussing the principles of evidence gathering.........................................................................6
Evaluating current evidence gathering practices and assess their impacts................................10
New legislations and communication technologies to deal new area of crime:........................11
CONCLUSION..............................................................................................................................12
REFERENCES..............................................................................................................................13

LIST OF FIGURES
Figure 1: Social impact of mobile phones.......................................................................................3
Figure 2: Malware and chargeware rates in UK.............................................................................5
Figure 3: Smartphone Forensic Investigation Process Model.........................................................7
LIST OF TABLE
Table 1: Models used for Smartphone investigation.....................................................................10
Figure 1: Social impact of mobile phones.......................................................................................3
Figure 2: Malware and chargeware rates in UK.............................................................................5
Figure 3: Smartphone Forensic Investigation Process Model.........................................................7
LIST OF TABLE
Table 1: Models used for Smartphone investigation.....................................................................10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INTRODUCTION
In digital era, due to several reasons need for mobile forensics are increasing
continuously such as use of smartphones to data storage, online transactions, law enforcement,
and increases use of mobile phone devices for criminal purpose etc. Digital forensic which is the
branch is of forensic science has considered in the context of recovery and investigation of
material found in digital devices in relation to computer crime. As per the present case scenario,
Mobile device forensics topic has been taken to understand the impact of digital forensics on the
social and commercial environments. Furthermore, report also discussed the potential impact of
forensic investigation on individuals and influence of motivation, data manipulation and malware
on environments. At the end, report provides detail about current evidence and assessing their
impact on organizations and customers with help of case study.
Evaluating current forensic practice
Today’s breakneck mobile device market, mobile devices such as cell phones,
BlackBerrys, Androids, iPads are available everywhere. For different purposes such as send texts
and email, photographs, update Facebook, search the web and consult maps etc. users are using
these devices. Besides that, advance mobile device forensics provide facilities of recover deleted
data, detect malware, bypass locks and detect data stored in Third-Party Applications (Fang and
et.al., 2012). However, along with several benefits the process of obtaining mobile device
evidence, associated laws and technologies used in devices itself are the major challenges which
are creating issues for mobile users and forensics experts across the world.
Evidence: Over the past few years, mobile devices forensics has expanded significantly.
The term digital evidence can be defined in term of information of probative value that is
stored and transmitted in binary form. It is explored as the process of recovering digital
evidence from a mobile device by effective utilization of acceptable methods (Lee and
Hong, 2011). In mobile era, generally information can be retrieved from various sources
such as Internet browsing history, information regarding mobile apps, geo-location
information, map histories and records of access to wireless networks etc. Smartphones
are replacing the needs of personal computers and it becomes a main source of digital
evidence. By using this, individual movements can be traced. All of this information
could be useful in many cases. For example, through accessing the Google map, a
criminal suspect’s mobile device can be traced. It also provides facility of investigate the
1
In digital era, due to several reasons need for mobile forensics are increasing
continuously such as use of smartphones to data storage, online transactions, law enforcement,
and increases use of mobile phone devices for criminal purpose etc. Digital forensic which is the
branch is of forensic science has considered in the context of recovery and investigation of
material found in digital devices in relation to computer crime. As per the present case scenario,
Mobile device forensics topic has been taken to understand the impact of digital forensics on the
social and commercial environments. Furthermore, report also discussed the potential impact of
forensic investigation on individuals and influence of motivation, data manipulation and malware
on environments. At the end, report provides detail about current evidence and assessing their
impact on organizations and customers with help of case study.
Evaluating current forensic practice
Today’s breakneck mobile device market, mobile devices such as cell phones,
BlackBerrys, Androids, iPads are available everywhere. For different purposes such as send texts
and email, photographs, update Facebook, search the web and consult maps etc. users are using
these devices. Besides that, advance mobile device forensics provide facilities of recover deleted
data, detect malware, bypass locks and detect data stored in Third-Party Applications (Fang and
et.al., 2012). However, along with several benefits the process of obtaining mobile device
evidence, associated laws and technologies used in devices itself are the major challenges which
are creating issues for mobile users and forensics experts across the world.
Evidence: Over the past few years, mobile devices forensics has expanded significantly.
The term digital evidence can be defined in term of information of probative value that is
stored and transmitted in binary form. It is explored as the process of recovering digital
evidence from a mobile device by effective utilization of acceptable methods (Lee and
Hong, 2011). In mobile era, generally information can be retrieved from various sources
such as Internet browsing history, information regarding mobile apps, geo-location
information, map histories and records of access to wireless networks etc. Smartphones
are replacing the needs of personal computers and it becomes a main source of digital
evidence. By using this, individual movements can be traced. All of this information
could be useful in many cases. For example, through accessing the Google map, a
criminal suspect’s mobile device can be traced. It also provides facility of investigate the
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

time of the crime and distance from the scene of the crime (Chun and Park, 2012).
Operating systems: BlackBerry OS, Nokia’s Symbian OS, HP’s web OS Apple’s iOS,
Google’s Android and many others operating systems are widely‐used throughout the
world by people. Presence of diverse software is creating challenges for developers of
forensic software to deal with such kind of issues. In the context of extracting digital
evidence from smartphones, organizations are offering different types of technologies for
mobile forensics (Rodríguez-Domínguez and et.al., 2013). From a hardware and
software perspective, personal computers may differ from mobile devices so forensic
software tools for mobile devices are considered different.
Data storage methods: For personal communication, Mobile phones have become a very
important tool and it provides facility of data storage in SIM-cards and internal
memories. By default, data is stored in internal memory of mobile which is also called
RAM (Random Access Memory) and its ROM (Read Only Memory). For the purpose of
temporary data storage, RAM is the memory space used by smartphones. But when
power is off then temporarily store information in RAM is generally lost. Besides that, in
mobile devices, data can also be stored in SIM (Subscriber Identity Module) cards and
memory cards (Chen, Yang and Liu, 2011). For the general purpose of data storage
including photographs, music, videos, and the like, memory card is also used. Despite of
these two methods, mobile users can store information on the various other machines and
devices that may be service providers, personal computers and email servers.
Purpose of forensic analysis: For the purpose of mobile device examination, different
types of software which include forensic tools as well as non-forensic tools are available.
They are mainly use for device management, testing, and diagnostics purposes (Glisson
and et.al., 2011). In modern smartphones, a long range of evidence items such as images,
sound, email, web browser history, calendar items and contacts are found. Different
methods of physical imaging of mobile phone memory units can be used in order to
recover important evidence such as deleted text messages (Al-Mutawa, Baggili and
Marrington, 2012). In order to forensically analyze mobile devices different types of
techniques such as videotaping, simply manipulating the phone data and backup or
syncing application etc. are also employed. Among these techniques, backup or syncing
application is most suitable in term of preserve and effective use of user created data.
2
Operating systems: BlackBerry OS, Nokia’s Symbian OS, HP’s web OS Apple’s iOS,
Google’s Android and many others operating systems are widely‐used throughout the
world by people. Presence of diverse software is creating challenges for developers of
forensic software to deal with such kind of issues. In the context of extracting digital
evidence from smartphones, organizations are offering different types of technologies for
mobile forensics (Rodríguez-Domínguez and et.al., 2013). From a hardware and
software perspective, personal computers may differ from mobile devices so forensic
software tools for mobile devices are considered different.
Data storage methods: For personal communication, Mobile phones have become a very
important tool and it provides facility of data storage in SIM-cards and internal
memories. By default, data is stored in internal memory of mobile which is also called
RAM (Random Access Memory) and its ROM (Read Only Memory). For the purpose of
temporary data storage, RAM is the memory space used by smartphones. But when
power is off then temporarily store information in RAM is generally lost. Besides that, in
mobile devices, data can also be stored in SIM (Subscriber Identity Module) cards and
memory cards (Chen, Yang and Liu, 2011). For the general purpose of data storage
including photographs, music, videos, and the like, memory card is also used. Despite of
these two methods, mobile users can store information on the various other machines and
devices that may be service providers, personal computers and email servers.
Purpose of forensic analysis: For the purpose of mobile device examination, different
types of software which include forensic tools as well as non-forensic tools are available.
They are mainly use for device management, testing, and diagnostics purposes (Glisson
and et.al., 2011). In modern smartphones, a long range of evidence items such as images,
sound, email, web browser history, calendar items and contacts are found. Different
methods of physical imaging of mobile phone memory units can be used in order to
recover important evidence such as deleted text messages (Al-Mutawa, Baggili and
Marrington, 2012). In order to forensically analyze mobile devices different types of
techniques such as videotaping, simply manipulating the phone data and backup or
syncing application etc. are also employed. Among these techniques, backup or syncing
application is most suitable in term of preserve and effective use of user created data.
2

Besides that, Holy Grail of mobile device forensic technique can also be applied for
creating full physical copy of the entire memory store data.
Potential impact of forensic investigation on the social and commercial environments
Social impact: Throughout the daily lives of people worldwide, contemporary mobile devices
are used for different purposes. In order to access sensitive data and personally identifiable
information (PII) such as electronic transaction of health records and medical history,
smartphones devices play an important role (Kubi, Saleem and Popov, 2011) Along with several
benefits of mobile devices, a genuine security and privacy threats to mobile device and mobile
apps are also increasing day by day. In such kind of situation, mobile forensic may be beneficial
because it provides facility of crime investigation during retention of data on the device. The
other major impact of mobile forensic on an individual and entire community can be understood
with help of below figure.
Figure 1: Social impact of mobile phones
(Source: Deloitee access economics, 2013)
For example, if data of an individual will use unethical manner then it directly affects their
personality and perception about use of digital evidence. However, loss of confidence and loss of
access are the major negative impact of forensic investigation on an individual in the absence of
better policies. Sometimes, financial loss to customers, security lapse in network and malicious
activities can also create negative image of forensic investigation in the mind of community.
Commercial impact: Positive impact of mobile forensic can be seen in term of financial
implication and build corporate image of enterprises in the canvas of the minds of their
customers and entire community throughout the world. It can also enhance confidence of
3
creating full physical copy of the entire memory store data.
Potential impact of forensic investigation on the social and commercial environments
Social impact: Throughout the daily lives of people worldwide, contemporary mobile devices
are used for different purposes. In order to access sensitive data and personally identifiable
information (PII) such as electronic transaction of health records and medical history,
smartphones devices play an important role (Kubi, Saleem and Popov, 2011) Along with several
benefits of mobile devices, a genuine security and privacy threats to mobile device and mobile
apps are also increasing day by day. In such kind of situation, mobile forensic may be beneficial
because it provides facility of crime investigation during retention of data on the device. The
other major impact of mobile forensic on an individual and entire community can be understood
with help of below figure.
Figure 1: Social impact of mobile phones
(Source: Deloitee access economics, 2013)
For example, if data of an individual will use unethical manner then it directly affects their
personality and perception about use of digital evidence. However, loss of confidence and loss of
access are the major negative impact of forensic investigation on an individual in the absence of
better policies. Sometimes, financial loss to customers, security lapse in network and malicious
activities can also create negative image of forensic investigation in the mind of community.
Commercial impact: Positive impact of mobile forensic can be seen in term of financial
implication and build corporate image of enterprises in the canvas of the minds of their
customers and entire community throughout the world. It can also enhance confidence of
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

customers by providing the remedial action in order to harden the present security system
(Aquilina, Casey and Malin, 2008). However, along with this, data protection and management,
privacy issues and legislation related issues are also associated with the use of mobile forensics.
If any organizations or investigators has decided to collect data then they should be consider
legal guidelines related to collect and preserve data, privacy and reliability. Besides that, they
must be emphasized on usage policies and privacy warnings associated with the use of mobile
devices. It is necessary that smartphones evidence should be analyzed in a defensible and reliable
manner (Grispos, Storer and Glisson, 2011). In European countries strict laws such a labour and
data protect act etc. have been framed for the purpose of preventing people to view other private
information in a corporate network and their day to day life. In this appropriate use of particular
forensic tools are required to enhance the validity and reliability of entire investigation process.
Examined the impact of motivation, data manipulation and malware
With the use of mobile devices increases, privacy, data manipulation and motivation
related issues also occurred. Due to large storage capacity and a wide range of applications,
spyware and worm related issues are raised which affects mobile users throughout the world.
Besides that, there is no standard method available for analyzing mobile phone internal memory.
Presently, data is extracted from smartphone by utilizing a cable, infrared or Bluetooth
connection. In this regard, standard command is set for the extraction of certain evidence and it is
vary from manufacturer to manufacturer or even from model to model (Brickell and Li, 2009).
Despite of that, AT-commands, GSM specifications, Cell-Seizure, TULP, Oxygen Phone
Manager and many more types of software packages are available for extracting information
from the phone.
In all these methods, information is extracted through using the operating system of
phones but the main issue of these types of techniques is that deleted information cannot be
extracted. These kinds of software’s are unable to provide facility of imaging and analysis of
internal memory of mobile phone so that data manipulation related task cannot be achieved in a
significant manner. Besides that, many devices that are cheaply manufactured in China and they
have no International Mobile Equipment Identity (IMEI) (Goel, Tyagi and Agarwal, 2012). Due
to absence of this identity, criminals and terrorists who often utilize the Chinese cell phones for
conducting activities because, it is impossible for forensics department to track these mobile
devices in the absence of IMEI number (Lookout, 2015). Figure shows that UK was able to
4
(Aquilina, Casey and Malin, 2008). However, along with this, data protection and management,
privacy issues and legislation related issues are also associated with the use of mobile forensics.
If any organizations or investigators has decided to collect data then they should be consider
legal guidelines related to collect and preserve data, privacy and reliability. Besides that, they
must be emphasized on usage policies and privacy warnings associated with the use of mobile
devices. It is necessary that smartphones evidence should be analyzed in a defensible and reliable
manner (Grispos, Storer and Glisson, 2011). In European countries strict laws such a labour and
data protect act etc. have been framed for the purpose of preventing people to view other private
information in a corporate network and their day to day life. In this appropriate use of particular
forensic tools are required to enhance the validity and reliability of entire investigation process.
Examined the impact of motivation, data manipulation and malware
With the use of mobile devices increases, privacy, data manipulation and motivation
related issues also occurred. Due to large storage capacity and a wide range of applications,
spyware and worm related issues are raised which affects mobile users throughout the world.
Besides that, there is no standard method available for analyzing mobile phone internal memory.
Presently, data is extracted from smartphone by utilizing a cable, infrared or Bluetooth
connection. In this regard, standard command is set for the extraction of certain evidence and it is
vary from manufacturer to manufacturer or even from model to model (Brickell and Li, 2009).
Despite of that, AT-commands, GSM specifications, Cell-Seizure, TULP, Oxygen Phone
Manager and many more types of software packages are available for extracting information
from the phone.
In all these methods, information is extracted through using the operating system of
phones but the main issue of these types of techniques is that deleted information cannot be
extracted. These kinds of software’s are unable to provide facility of imaging and analysis of
internal memory of mobile phone so that data manipulation related task cannot be achieved in a
significant manner. Besides that, many devices that are cheaply manufactured in China and they
have no International Mobile Equipment Identity (IMEI) (Goel, Tyagi and Agarwal, 2012). Due
to absence of this identity, criminals and terrorists who often utilize the Chinese cell phones for
conducting activities because, it is impossible for forensics department to track these mobile
devices in the absence of IMEI number (Lookout, 2015). Figure shows that UK was able to
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
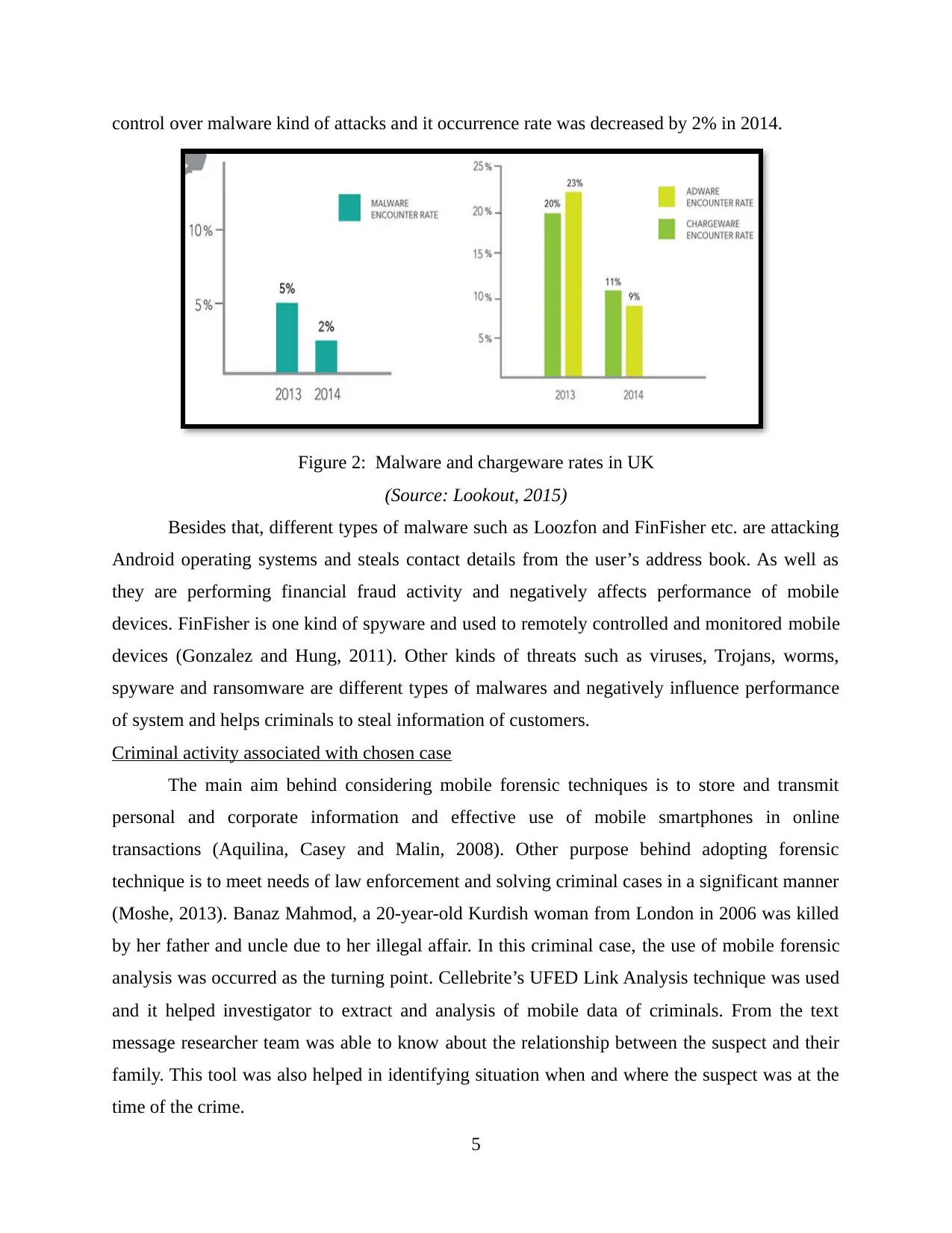
control over malware kind of attacks and it occurrence rate was decreased by 2% in 2014.
Figure 2: Malware and chargeware rates in UK
(Source: Lookout, 2015)
Besides that, different types of malware such as Loozfon and FinFisher etc. are attacking
Android operating systems and steals contact details from the user’s address book. As well as
they are performing financial fraud activity and negatively affects performance of mobile
devices. FinFisher is one kind of spyware and used to remotely controlled and monitored mobile
devices (Gonzalez and Hung, 2011). Other kinds of threats such as viruses, Trojans, worms,
spyware and ransomware are different types of malwares and negatively influence performance
of system and helps criminals to steal information of customers.
Criminal activity associated with chosen case
The main aim behind considering mobile forensic techniques is to store and transmit
personal and corporate information and effective use of mobile smartphones in online
transactions (Aquilina, Casey and Malin, 2008). Other purpose behind adopting forensic
technique is to meet needs of law enforcement and solving criminal cases in a significant manner
(Moshe, 2013). Banaz Mahmod, a 20-year-old Kurdish woman from London in 2006 was killed
by her father and uncle due to her illegal affair. In this criminal case, the use of mobile forensic
analysis was occurred as the turning point. Cellebrite’s UFED Link Analysis technique was used
and it helped investigator to extract and analysis of mobile data of criminals. From the text
message researcher team was able to know about the relationship between the suspect and their
family. This tool was also helped in identifying situation when and where the suspect was at the
time of the crime.
5
Figure 2: Malware and chargeware rates in UK
(Source: Lookout, 2015)
Besides that, different types of malware such as Loozfon and FinFisher etc. are attacking
Android operating systems and steals contact details from the user’s address book. As well as
they are performing financial fraud activity and negatively affects performance of mobile
devices. FinFisher is one kind of spyware and used to remotely controlled and monitored mobile
devices (Gonzalez and Hung, 2011). Other kinds of threats such as viruses, Trojans, worms,
spyware and ransomware are different types of malwares and negatively influence performance
of system and helps criminals to steal information of customers.
Criminal activity associated with chosen case
The main aim behind considering mobile forensic techniques is to store and transmit
personal and corporate information and effective use of mobile smartphones in online
transactions (Aquilina, Casey and Malin, 2008). Other purpose behind adopting forensic
technique is to meet needs of law enforcement and solving criminal cases in a significant manner
(Moshe, 2013). Banaz Mahmod, a 20-year-old Kurdish woman from London in 2006 was killed
by her father and uncle due to her illegal affair. In this criminal case, the use of mobile forensic
analysis was occurred as the turning point. Cellebrite’s UFED Link Analysis technique was used
and it helped investigator to extract and analysis of mobile data of criminals. From the text
message researcher team was able to know about the relationship between the suspect and their
family. This tool was also helped in identifying situation when and where the suspect was at the
time of the crime.
5

Along with this, it is essential for forensic team to follow legal authorities both
international and local records during collection of digital data from electronic devices. For
agencies in their fight against cartels, mobile and other digital evidence are becoming an
increasingly powerful tool. By accessing digital files or programs, investigators can access to a
new source of information (Bennett, 2011). For digital evidence gathering as an investigative
tool, enterprises are required staff, IT-staff / Forensic Analysts and co-operation with other public
agencies.
Discussing the principles of evidence gathering
In digital era, more and more electronic information is being generated, stored and
distributed by mobile phone devices. Forensic department is used digital information as evidence
in many cases. Mainly, information is gathered by the tapping or monitoring of network traffic,
confiscation of the storage media and making of digital copies such as forensic images and file
copies etc. Mobile forensic which is also known as the name of investigative and analytical
techniques can be employed in order to conform that evidentiary standards used in or appropriate
for a court of law (EnCase Forensic, 2013). In many circumstances and jurisdictions including
raids or inspections, searches and compelled discovery, digital information is collected.
Laws governing forensic science
The European anti-fraud office (OLAF) was framed by Association chief police officers
(ACPO) for the purpose of identification, collection and preservation of digital evidence. The
Criminal Procedure Rules (CRPR), The Criminal Procedure and Investigations Act, 1996 and
Contracts, criminal law and the adversarial system related legislation were framed for forensic
service providers to solve criminal cases in more appropriate manner. The United Kingdom’s
Association of Chief Police Officers (ACPOL) had defined the following instruction for forensic
experts while handling of mobile phones are processes that can be enlisted as follow.
Principle of evidence gathering
Principle 1: Law enforcement agencies should not take any action on storage media
because it may subsequently be relied upon in court (Goel, Tyagi and Agarwal, 2012).
Principle 2: Person must be competent to access original data held on a storage medium
or mobile phones. At this stage, forensic team experts decides that if any other evidence
is required from the phone before handling such as DNA, fingerprints, drugs and
accelerants etc.
6
international and local records during collection of digital data from electronic devices. For
agencies in their fight against cartels, mobile and other digital evidence are becoming an
increasingly powerful tool. By accessing digital files or programs, investigators can access to a
new source of information (Bennett, 2011). For digital evidence gathering as an investigative
tool, enterprises are required staff, IT-staff / Forensic Analysts and co-operation with other public
agencies.
Discussing the principles of evidence gathering
In digital era, more and more electronic information is being generated, stored and
distributed by mobile phone devices. Forensic department is used digital information as evidence
in many cases. Mainly, information is gathered by the tapping or monitoring of network traffic,
confiscation of the storage media and making of digital copies such as forensic images and file
copies etc. Mobile forensic which is also known as the name of investigative and analytical
techniques can be employed in order to conform that evidentiary standards used in or appropriate
for a court of law (EnCase Forensic, 2013). In many circumstances and jurisdictions including
raids or inspections, searches and compelled discovery, digital information is collected.
Laws governing forensic science
The European anti-fraud office (OLAF) was framed by Association chief police officers
(ACPO) for the purpose of identification, collection and preservation of digital evidence. The
Criminal Procedure Rules (CRPR), The Criminal Procedure and Investigations Act, 1996 and
Contracts, criminal law and the adversarial system related legislation were framed for forensic
service providers to solve criminal cases in more appropriate manner. The United Kingdom’s
Association of Chief Police Officers (ACPOL) had defined the following instruction for forensic
experts while handling of mobile phones are processes that can be enlisted as follow.
Principle of evidence gathering
Principle 1: Law enforcement agencies should not take any action on storage media
because it may subsequently be relied upon in court (Goel, Tyagi and Agarwal, 2012).
Principle 2: Person must be competent to access original data held on a storage medium
or mobile phones. At this stage, forensic team experts decides that if any other evidence
is required from the phone before handling such as DNA, fingerprints, drugs and
accelerants etc.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Principle 3: For creating and preserving electronic data, an audit trail or other record of
all processes are required so that third part can easily examine those processes and
achieve the same result in same circumstance (Cartel working group, 2010).
Principle 4: It is responsibility of investigation officer to ensure that the law and these
principles are adhered to.
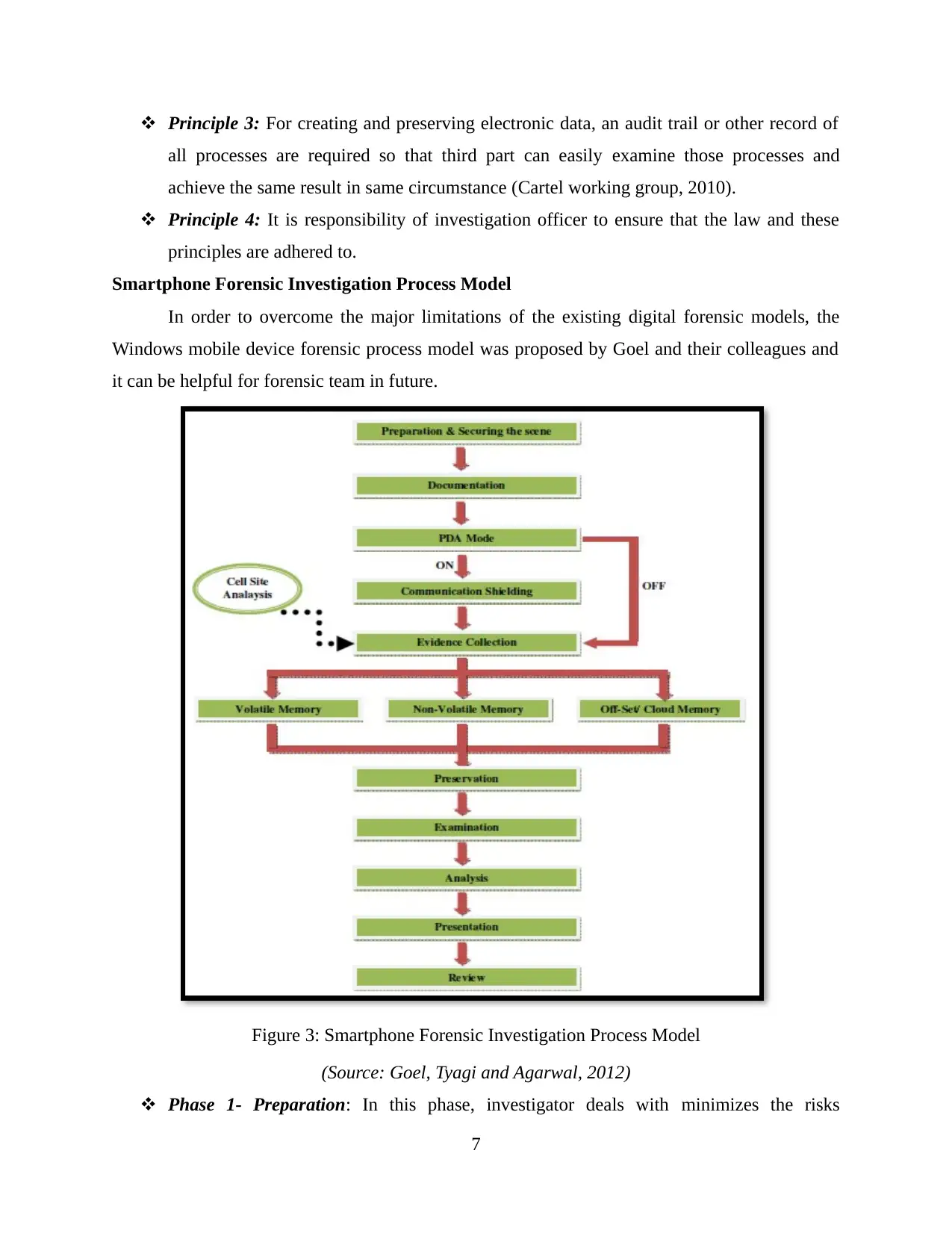
Smartphone Forensic Investigation Process Model
In order to overcome the major limitations of the existing digital forensic models, the
Windows mobile device forensic process model was proposed by Goel and their colleagues and
it can be helpful for forensic team in future.
Figure 3: Smartphone Forensic Investigation Process Model
(Source: Goel, Tyagi and Agarwal, 2012)
Phase 1- Preparation: In this phase, investigator deals with minimizes the risks
7
all processes are required so that third part can easily examine those processes and
achieve the same result in same circumstance (Cartel working group, 2010).
Principle 4: It is responsibility of investigation officer to ensure that the law and these
principles are adhered to.
Smartphone Forensic Investigation Process Model
In order to overcome the major limitations of the existing digital forensic models, the
Windows mobile device forensic process model was proposed by Goel and their colleagues and
it can be helpful for forensic team in future.
Figure 3: Smartphone Forensic Investigation Process Model
(Source: Goel, Tyagi and Agarwal, 2012)
Phase 1- Preparation: In this phase, investigator deals with minimizes the risks
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

associated with an investigation and enhance the quality of electronic evidence. Further,
nature of the crime and activities are conducted prior to the occurrence of actual
investigation.
Phase 2- Securing the Scene: Ensuring systematic and secure custody at the crime spot
and contamination and corruption of evidences are the main concerns of this stage.
Investigators are responsible for the control of scene and ensured safety of all the people
at the scene (John, 2012).
Phase 3- Documenting the Scene: Adequate documentation is required for the purpose
of maintaining a proper chain of custody. At this stage, all profs including Photographs,
sketches, crime-scene mapping, classification of people (witnesses, victims, suspects and
other assisting personnel) and recreating the crime scene are merged together into a
single documentation.
Phase 4- PDA Mode: This phase determines devices are active or inactive mode. It is
advisable never to change the state of device while it is working (Gonzalez and Hung,
2011).
Phase 5- Communication Shielding: It concentrates on to block the further
communication options on the devices and ensures that no overwriting of the existing
information on the devices is done (Goel, Tyagi and Agarwal, 2012). For example, if
mobile devices in off but some communication feature like wireless or Bluetooth may be
enabled and it can affect result.
Phase 6- Volatile Evidence Collection: Timely collection and management is required in
case of mobile devices because they are in volatile nature. For example, the device is
running out of battery power then information can be loss.
Phase 7– Non-volatile Evidence Collection: Evidences from mobile and other handheld
devices such as MMC card, memory sticks and secure digital (SD) cards etc. are
extracted at this stage. Electric and non-electric nature evidences are also looked along
with applying hash algorithm to ensure that the integrity and authenticity has been
followed. As well as considering admissibility of evidences as per the court of law
criteria is also considered at this stage (Willassen, 2012).
Phase 8- Off-set: In order to increase capability of potential search evidence, cloud
computing and other offset storage techniques can be used by companies. These kinds of
8
nature of the crime and activities are conducted prior to the occurrence of actual
investigation.
Phase 2- Securing the Scene: Ensuring systematic and secure custody at the crime spot
and contamination and corruption of evidences are the main concerns of this stage.
Investigators are responsible for the control of scene and ensured safety of all the people
at the scene (John, 2012).
Phase 3- Documenting the Scene: Adequate documentation is required for the purpose
of maintaining a proper chain of custody. At this stage, all profs including Photographs,
sketches, crime-scene mapping, classification of people (witnesses, victims, suspects and
other assisting personnel) and recreating the crime scene are merged together into a
single documentation.
Phase 4- PDA Mode: This phase determines devices are active or inactive mode. It is
advisable never to change the state of device while it is working (Gonzalez and Hung,
2011).
Phase 5- Communication Shielding: It concentrates on to block the further
communication options on the devices and ensures that no overwriting of the existing
information on the devices is done (Goel, Tyagi and Agarwal, 2012). For example, if
mobile devices in off but some communication feature like wireless or Bluetooth may be
enabled and it can affect result.
Phase 6- Volatile Evidence Collection: Timely collection and management is required in
case of mobile devices because they are in volatile nature. For example, the device is
running out of battery power then information can be loss.
Phase 7– Non-volatile Evidence Collection: Evidences from mobile and other handheld
devices such as MMC card, memory sticks and secure digital (SD) cards etc. are
extracted at this stage. Electric and non-electric nature evidences are also looked along
with applying hash algorithm to ensure that the integrity and authenticity has been
followed. As well as considering admissibility of evidences as per the court of law
criteria is also considered at this stage (Willassen, 2012).
Phase 8- Off-set: In order to increase capability of potential search evidence, cloud
computing and other offset storage techniques can be used by companies. These kinds of
8

new technology advancement provides facility of accessing data from anywhere anytime
from any device in an appropriate manner.
Phase 9- Cell Site Analysis: In the context of identifying a specific position or position
where a mobile phone was or is, this technique can be used. Information can be assessed
on the basis of SMS is either sent or received and call is made from a mobile phone or a
call is received.
Phase 10- Preservation: At this stage, for sealing the evidences like devices and other
accessories, anti-static packaging envelopes are used. Along with this, before packaging,
identification and their labeling are done (Yates, n.d.). Besides that, proper transportation
and storage procedures are followed as per the guidelines of National Institute of
Standards and Technology.
Phase 11- Examination: Data filtering, validation, pattern matching and searching
activities are performed in order to critical examination of the evidences collected at
particular place. In this regard, investigators can select text messages, voice messages,
documents and emails evidences before proceeding to examination. For mathematical
authentication of data, hashing techniques like md5 can be employed by forensic experts.
Phase 12- Analysis: In the context of analyzing hidden data, reconstructing the event
data, analyzing hidden data to arriving at proper conclusions, some activities are to be
performed at this stage. On the basis of the results of the previous examination, analysis
processes are analyzed and properly documented to identify actual outcome (John, 2012).
Phase 13- Presentation: After completing the whole analysis, findings or outcomes are
presented to variety of audience such as law enforcement officials, technical experts,
legal experts and corporate management etc. to present actual findings.
Phase 14:- Review: In this stage of the Windows Mobile Forensic Process Model, review
of all the steps during the investigation is done. It may be used for the purpose of further
refining data and to get the total picture of an incident or crime effectively.
Besides that, different models can also be employed for the purpose of mobile phone
forensics that can be described as follow.
9
from any device in an appropriate manner.
Phase 9- Cell Site Analysis: In the context of identifying a specific position or position
where a mobile phone was or is, this technique can be used. Information can be assessed
on the basis of SMS is either sent or received and call is made from a mobile phone or a
call is received.
Phase 10- Preservation: At this stage, for sealing the evidences like devices and other
accessories, anti-static packaging envelopes are used. Along with this, before packaging,
identification and their labeling are done (Yates, n.d.). Besides that, proper transportation
and storage procedures are followed as per the guidelines of National Institute of
Standards and Technology.
Phase 11- Examination: Data filtering, validation, pattern matching and searching
activities are performed in order to critical examination of the evidences collected at
particular place. In this regard, investigators can select text messages, voice messages,
documents and emails evidences before proceeding to examination. For mathematical
authentication of data, hashing techniques like md5 can be employed by forensic experts.
Phase 12- Analysis: In the context of analyzing hidden data, reconstructing the event
data, analyzing hidden data to arriving at proper conclusions, some activities are to be
performed at this stage. On the basis of the results of the previous examination, analysis
processes are analyzed and properly documented to identify actual outcome (John, 2012).
Phase 13- Presentation: After completing the whole analysis, findings or outcomes are
presented to variety of audience such as law enforcement officials, technical experts,
legal experts and corporate management etc. to present actual findings.
Phase 14:- Review: In this stage of the Windows Mobile Forensic Process Model, review
of all the steps during the investigation is done. It may be used for the purpose of further
refining data and to get the total picture of an incident or crime effectively.
Besides that, different models can also be employed for the purpose of mobile phone
forensics that can be described as follow.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





