Comprehensive Forensic Report: JLA Enterprise Network Intrusion
VerifiedAdded on 2023/06/09
|10
|1815
|434
Report
AI Summary
This report presents a forensic examination of a network intrusion that occurred at JLA Enterprise. The intrusion, caused by the release of worms, resulted in unauthorized access to the company's computer systems and the theft of sensitive data, including employee information and strategic business plans. The report details the various sources of network intrusion, such as traffic flooding attacks, protocol-specific attacks, asymmetric routing attacks, and the use of worms and Trojans. The analysis reveals that the attack occurred during working hours, utilizing a worm that infiltrated the network, compromising nearly 90% of the computers within minutes. The attackers, who had control of the network for approximately half an hour, extracted data from the database, which was then sold to a rival company. The report concludes by emphasizing the increasing threat of cybercrimes and the need for robust security measures, including regular software updates, updated anti-spyware, and enhanced security on servers, to mitigate future attacks.

Running head: NETWORK INTRUSION
Network Intrusion
Name of the student:
Name of the university:
Author note:
Network Intrusion
Name of the student:
Name of the university:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1NETWORK INTRUSION
Abstract
The forensic report deals with network intrusion that an enterprise has faced. The report broadly
describes the sources of network intrusion and the effects that it has on corporate data. The main
sources of intrusions are Trojan horses, worms, viruses. There are different types of attack that
are performed on the network like the traffic flooding attack, protocol specific attack and so on.
However, the mentioned company faced the unauthorized action due to the release of worms into
the network.
Keywords: Network intrusion, Worms, Cybercrime, anti-viruses
Abstract
The forensic report deals with network intrusion that an enterprise has faced. The report broadly
describes the sources of network intrusion and the effects that it has on corporate data. The main
sources of intrusions are Trojan horses, worms, viruses. There are different types of attack that
are performed on the network like the traffic flooding attack, protocol specific attack and so on.
However, the mentioned company faced the unauthorized action due to the release of worms into
the network.
Keywords: Network intrusion, Worms, Cybercrime, anti-viruses

2NETWORK INTRUSION
Table of Contents
Introduction......................................................................................................................................1
Discussion........................................................................................................................................1
Sources of network intrusion.......................................................................................................1
Traffic flooding Attack.....................................................................................................1
Protocol specific attacks....................................................................................................1
Asymmetric Routing attack..............................................................................................1
Worms and Trojans...........................................................................................................1
JLA enterprise Case Scenario..........................................................................................................1
Time of attack..............................................................................................................................1
The method by which the hacker intruded the network..............................................................1
The computers compromised by the attack.................................................................................1
Computers that were accessed.....................................................................................................1
Data extracted from the network.................................................................................................1
Type of attack conducted.............................................................................................................1
Total time the attacker had control over the network..................................................................1
Possibility of future attacks.........................................................................................................1
Conclusion.......................................................................................................................................1
References........................................................................................................................................1
Table of Contents
Introduction......................................................................................................................................1
Discussion........................................................................................................................................1
Sources of network intrusion.......................................................................................................1
Traffic flooding Attack.....................................................................................................1
Protocol specific attacks....................................................................................................1
Asymmetric Routing attack..............................................................................................1
Worms and Trojans...........................................................................................................1
JLA enterprise Case Scenario..........................................................................................................1
Time of attack..............................................................................................................................1
The method by which the hacker intruded the network..............................................................1
The computers compromised by the attack.................................................................................1
Computers that were accessed.....................................................................................................1
Data extracted from the network.................................................................................................1
Type of attack conducted.............................................................................................................1
Total time the attacker had control over the network..................................................................1
Possibility of future attacks.........................................................................................................1
Conclusion.......................................................................................................................................1
References........................................................................................................................................1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3NETWORK INTRUSION
Introduction:
This assignment requires conducting a forensic examination on network intrusion that
occurred in JLA Enterprise. Network Intrusion are the unauthorized actions made by the
intruders on the computer systems of various enterprises in order to steal personal information of
the company and provide them to their rivals. There are several other reasons for such actions.
For example, hacking the personal accounts of the employees of a particular company to get
salary information. Such actions by the intruders places the company into a great risk (Chung et
al., 2013). However, proper designing of detection system might help them to deal with the risks.
It becomes the responsibilities of the enterprise to find ways to overcome them. As a result, they
hire network detectives to assist them solving the issues.
Discussion:
Sources of network intrusion:
Any one of the following might do the attacks on the networks:
Traffic flooding Attack: Flooding is done by sending a lot of fake data packets in the
network. There are mainly two methods of network flooding attack. They are direct
attack and indirect attack (Choi, Kim, Kim, & Roh, 2013). In direct attack, the attackers
send fake error messages directly to the victims with the help of single or multiple
sources. Whereas, in indirect attack intermediate nodes called the reflectors are used to
launch attack.
Protocol specific attacks: Networks utilizes a number of protocol to establish
connection between the client and the server. They are mainly TCP/IP, ARP and so on.
Initially, security concerns were minimum. However, with the growth of the other
Introduction:
This assignment requires conducting a forensic examination on network intrusion that
occurred in JLA Enterprise. Network Intrusion are the unauthorized actions made by the
intruders on the computer systems of various enterprises in order to steal personal information of
the company and provide them to their rivals. There are several other reasons for such actions.
For example, hacking the personal accounts of the employees of a particular company to get
salary information. Such actions by the intruders places the company into a great risk (Chung et
al., 2013). However, proper designing of detection system might help them to deal with the risks.
It becomes the responsibilities of the enterprise to find ways to overcome them. As a result, they
hire network detectives to assist them solving the issues.
Discussion:
Sources of network intrusion:
Any one of the following might do the attacks on the networks:
Traffic flooding Attack: Flooding is done by sending a lot of fake data packets in the
network. There are mainly two methods of network flooding attack. They are direct
attack and indirect attack (Choi, Kim, Kim, & Roh, 2013). In direct attack, the attackers
send fake error messages directly to the victims with the help of single or multiple
sources. Whereas, in indirect attack intermediate nodes called the reflectors are used to
launch attack.
Protocol specific attacks: Networks utilizes a number of protocol to establish
connection between the client and the server. They are mainly TCP/IP, ARP and so on.
Initially, security concerns were minimum. However, with the growth of the other
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4NETWORK INTRUSION
protocols, physical security of the access points cannot be guaranteed (Woo, Jo, & Lee,
2015). The attackers use this advantage to hack the network systems.
Asymmetric Routing attack: In some network connections, the data packets are route
through different paths in different directions (Abdelaziz, Nafaa, & Salim, 2013, April).
This makes the connection between the client and the server insecure and gives
opportunity to the hackers to steal information.
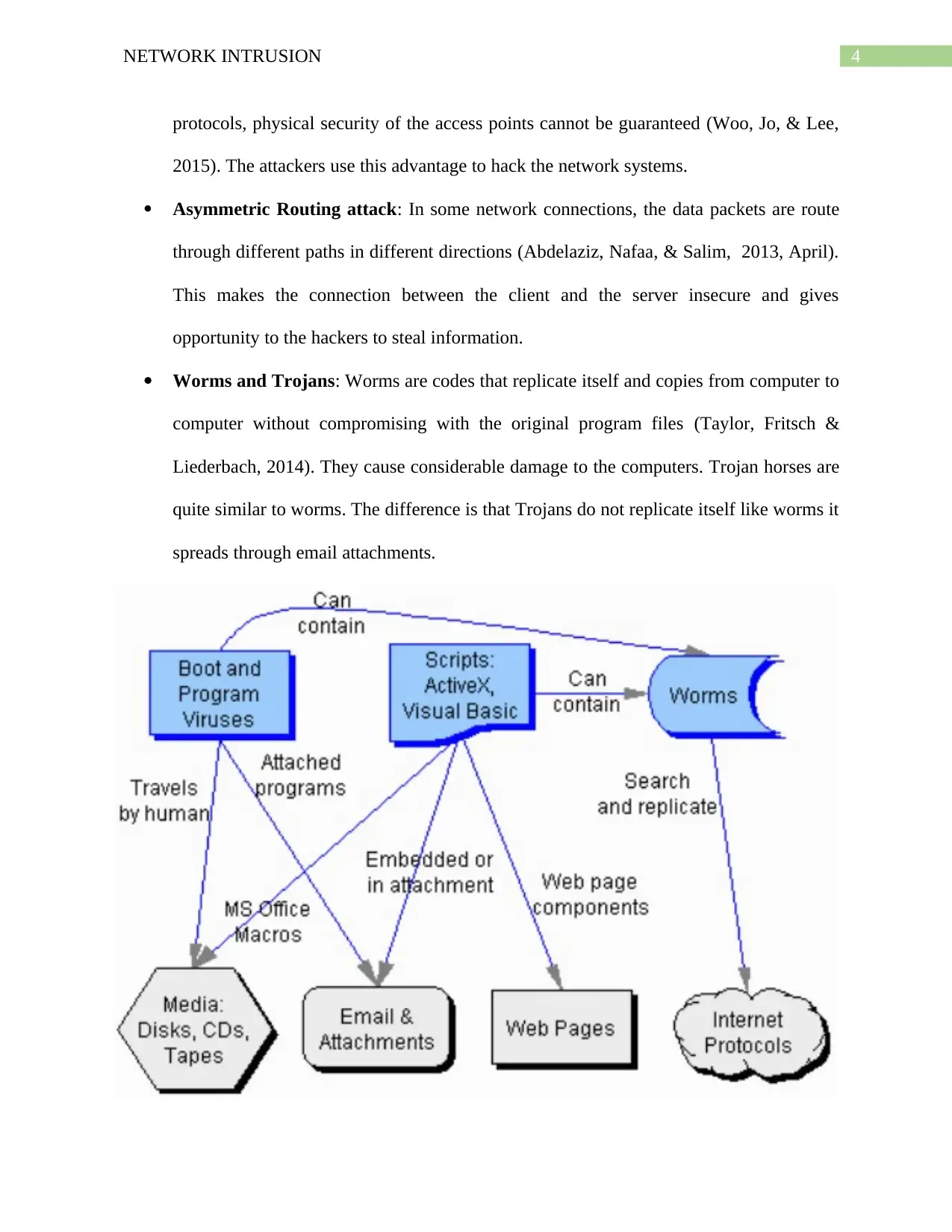
Worms and Trojans: Worms are codes that replicate itself and copies from computer to
computer without compromising with the original program files (Taylor, Fritsch &
Liederbach, 2014). They cause considerable damage to the computers. Trojan horses are
quite similar to worms. The difference is that Trojans do not replicate itself like worms it
spreads through email attachments.
protocols, physical security of the access points cannot be guaranteed (Woo, Jo, & Lee,
2015). The attackers use this advantage to hack the network systems.
Asymmetric Routing attack: In some network connections, the data packets are route
through different paths in different directions (Abdelaziz, Nafaa, & Salim, 2013, April).
This makes the connection between the client and the server insecure and gives
opportunity to the hackers to steal information.
Worms and Trojans: Worms are codes that replicate itself and copies from computer to
computer without compromising with the original program files (Taylor, Fritsch &
Liederbach, 2014). They cause considerable damage to the computers. Trojan horses are
quite similar to worms. The difference is that Trojans do not replicate itself like worms it
spreads through email attachments.
5NETWORK INTRUSION
Figure 1.
(Source: "The 12 Types Of Cyber Crime | Chapter No. 2 | Fasttrack To Cyber Crime | Digit",
2018)
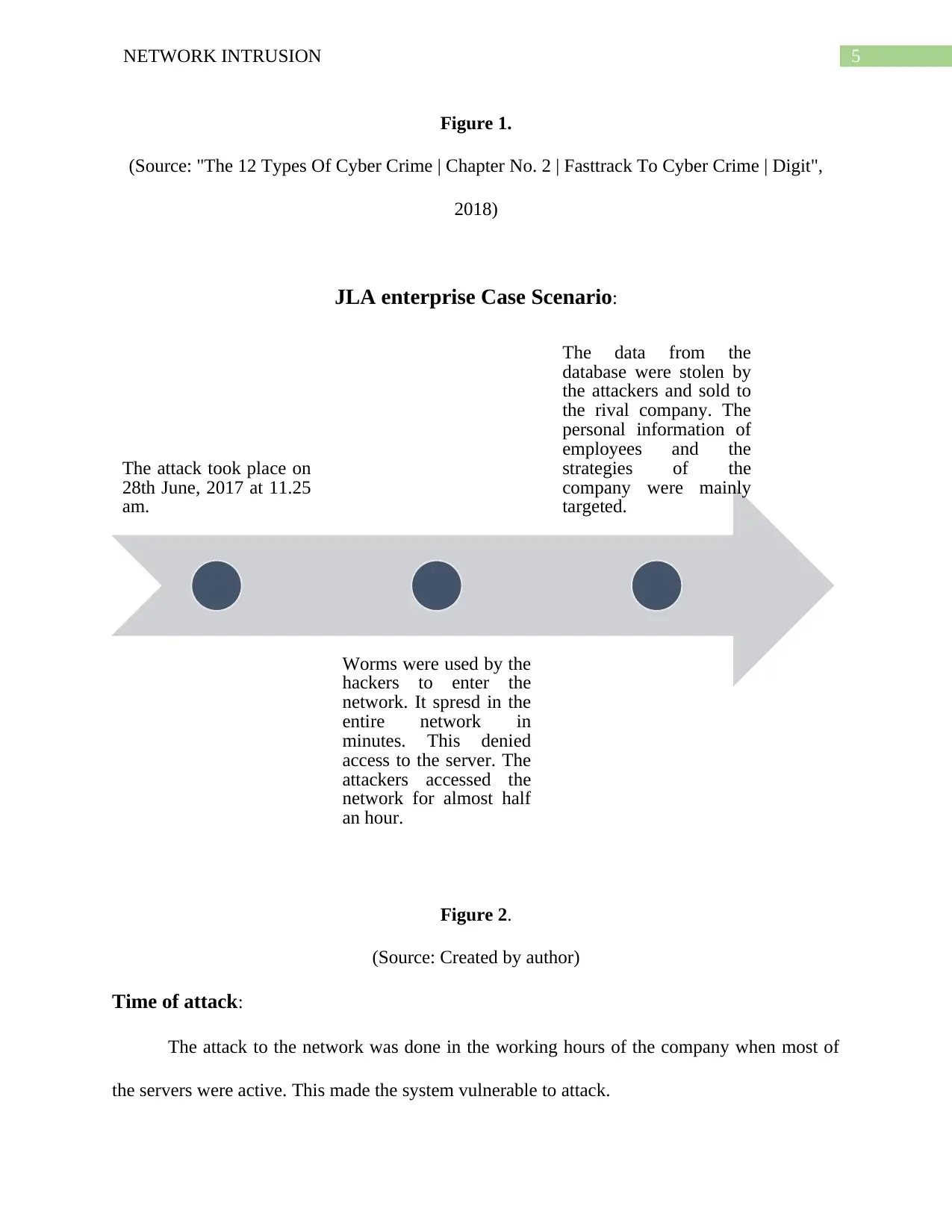
JLA enterprise Case Scenario:
Figure 2.
(Source: Created by author)
Time of attack:
The attack to the network was done in the working hours of the company when most of
the servers were active. This made the system vulnerable to attack.
The attack took place on
28th June, 2017 at 11.25
am.
Worms were used by the
hackers to enter the
network. It spresd in the
entire network in
minutes. This denied
access to the server. The
attackers accessed the
network for almost half
an hour.
The data from the
database were stolen by
the attackers and sold to
the rival company. The
personal information of
employees and the
strategies of the
company were mainly
targeted.
Figure 1.
(Source: "The 12 Types Of Cyber Crime | Chapter No. 2 | Fasttrack To Cyber Crime | Digit",
2018)
JLA enterprise Case Scenario:
Figure 2.
(Source: Created by author)
Time of attack:
The attack to the network was done in the working hours of the company when most of
the servers were active. This made the system vulnerable to attack.
The attack took place on
28th June, 2017 at 11.25
am.
Worms were used by the
hackers to enter the
network. It spresd in the
entire network in
minutes. This denied
access to the server. The
attackers accessed the
network for almost half
an hour.
The data from the
database were stolen by
the attackers and sold to
the rival company. The
personal information of
employees and the
strategies of the
company were mainly
targeted.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6NETWORK INTRUSION
The method by which the hacker intruded the network:
Through various examination and from several evidences it has been assumed that the
hackers have passed a worm in the computer network that took all the data that were passing
through the network. The worm can determine the sources as well as the destinations of the data
packets. Additionally the worm has some features that enabled it to filter the passwords and gain
private information about the network like the IP address, physical address and the topology. It
gives complete information of the data to the hackers that helps them to gain complete control
over the network. To achieve this control, intruders had a network card that gave access to the
traffic passing through the network. The worm named Slammer replicated itself and spread to all
the computers.
The computers compromised by the attack:
In this crime case, it is assumed that almost 90% of the computer in the enterprise has
been compromised within few minutes of the release of worm in the network. The speed of this
worm was so fast that it spread through the network within seconds. The server denied the
services of these computers.
Computers that were accessed:
The worm mainly attacked the server or the hub. Then it spread to the client computers
through the network. When the clients were trying to send or receive the data packets the worm
captured all the information and the access to the hub was denied by the network. The attackers
were able to gain control over the entire network within few minutes.
Data extracted from the network:
The attackers targeted the private information of the company. JLA enterprise deals with
the web services mainly like cloud computing, big data analysis and so on. A lot of personal data
The method by which the hacker intruded the network:
Through various examination and from several evidences it has been assumed that the
hackers have passed a worm in the computer network that took all the data that were passing
through the network. The worm can determine the sources as well as the destinations of the data
packets. Additionally the worm has some features that enabled it to filter the passwords and gain
private information about the network like the IP address, physical address and the topology. It
gives complete information of the data to the hackers that helps them to gain complete control
over the network. To achieve this control, intruders had a network card that gave access to the
traffic passing through the network. The worm named Slammer replicated itself and spread to all
the computers.
The computers compromised by the attack:
In this crime case, it is assumed that almost 90% of the computer in the enterprise has
been compromised within few minutes of the release of worm in the network. The speed of this
worm was so fast that it spread through the network within seconds. The server denied the
services of these computers.
Computers that were accessed:
The worm mainly attacked the server or the hub. Then it spread to the client computers
through the network. When the clients were trying to send or receive the data packets the worm
captured all the information and the access to the hub was denied by the network. The attackers
were able to gain control over the entire network within few minutes.
Data extracted from the network:
The attackers targeted the private information of the company. JLA enterprise deals with
the web services mainly like cloud computing, big data analysis and so on. A lot of personal data
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7NETWORK INTRUSION
of the employees and the company is stored in the database. Once the attackers got access to the
network, they stole all the secured data from the database and sold it to the rival company. This
will help the rival company to know about the strategies that JLA enterprise is planning to
increase business profit largely by big data analytics.
Type of attack conducted:
From the investigation conducted, it was found that Worms are malicious software that
cause one or the other harm to the network. The code that is used to cause this harm is referred to
as payload. The effect that this payload have on the network is deletion of important files
especially on the host system, encryption of data and spoofing.
Total time the attacker had control over the network:
Evidences say that the attackers had access to the network for almost half an hour. They
had already installed backdoor in most of the computers by remotely accessing them. Therefore,
it took less time to intrude the network.
Possibility of future attacks:
Continuous upgradation of the antiviruses might avoid the possibility of future attacks.
Security updates on regular basis should be the first priority of the company. As the enterprise
has already faced this kind of problem, they should become aware of further attacks. They
should install updated anti-spyware in all the computers. Special security should be imposed on
the servers so that no malicious software can further invade the network.
Conclusion
It can be concluded that cybercrimes are increasing day by day. Initially, network
connections needed no security. However, with the discovery of various malicious software like
Trojan horses, worms and viruses, security needs to be imposed on the network. These intruders
of the employees and the company is stored in the database. Once the attackers got access to the
network, they stole all the secured data from the database and sold it to the rival company. This
will help the rival company to know about the strategies that JLA enterprise is planning to
increase business profit largely by big data analytics.
Type of attack conducted:
From the investigation conducted, it was found that Worms are malicious software that
cause one or the other harm to the network. The code that is used to cause this harm is referred to
as payload. The effect that this payload have on the network is deletion of important files
especially on the host system, encryption of data and spoofing.
Total time the attacker had control over the network:
Evidences say that the attackers had access to the network for almost half an hour. They
had already installed backdoor in most of the computers by remotely accessing them. Therefore,
it took less time to intrude the network.
Possibility of future attacks:
Continuous upgradation of the antiviruses might avoid the possibility of future attacks.
Security updates on regular basis should be the first priority of the company. As the enterprise
has already faced this kind of problem, they should become aware of further attacks. They
should install updated anti-spyware in all the computers. Special security should be imposed on
the servers so that no malicious software can further invade the network.
Conclusion
It can be concluded that cybercrimes are increasing day by day. Initially, network
connections needed no security. However, with the discovery of various malicious software like
Trojan horses, worms and viruses, security needs to be imposed on the network. These intruders

8NETWORK INTRUSION
have proven to cause huge damage to the system. Several anti-viruses and anti-spywares are used
nowadays to detect unauthorized actions on the network.
have proven to cause huge damage to the system. Several anti-viruses and anti-spywares are used
nowadays to detect unauthorized actions on the network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9NETWORK INTRUSION
References:
Abdelaziz, A. K., Nafaa, M., & Salim, G. (2013, April). Survey of routing attacks and
countermeasures in mobile ad hoc networks. In Computer Modelling and Simulation
(UKSim), 2013 UKSim 15th International Conference on (pp. 693-698). IEEE.
Choi, S., Kim, K., Kim, S., & Roh, B. H. (2013, January). Threat of DoS by interest flooding
attack in content-centric networking. In Information Networking (ICOIN), 2013
International Conference on (pp. 315-319). IEEE.
Chung, C. J., Khatkar, P., Xing, T., Lee, J., & Huang, D. (2013). NICE: Network intrusion
detection and countermeasure selection in virtual network systems. IEEE transactions on
dependable and secure computing, 10(4), 198-211.
Taylor, R., Fritsch, E., & Liederbach, J (2014). Digital crime and digital terrorism. Taylor, R.,
Fritsch, E., & Liederbach, J. Digital crime and digital terrorism.
The 12 Types Of Cyber Crime | Chapter No. 2 | Fasttrack To Cyber Crime | Digit. (2018).
Retrieved from https://www.digit.in/technology-guides/fasttrack-to-cyber-crime/the-12-
types-of-cyber-crime.html
Woo, S., Jo, H. J., & Lee, D. H. (2015). A practical wireless attack on the connected car and
security protocol for in-vehicle CAN. IEEE Transactions on Intelligent Transportation
Systems, 16(2), 993-1006.
References:
Abdelaziz, A. K., Nafaa, M., & Salim, G. (2013, April). Survey of routing attacks and
countermeasures in mobile ad hoc networks. In Computer Modelling and Simulation
(UKSim), 2013 UKSim 15th International Conference on (pp. 693-698). IEEE.
Choi, S., Kim, K., Kim, S., & Roh, B. H. (2013, January). Threat of DoS by interest flooding
attack in content-centric networking. In Information Networking (ICOIN), 2013
International Conference on (pp. 315-319). IEEE.
Chung, C. J., Khatkar, P., Xing, T., Lee, J., & Huang, D. (2013). NICE: Network intrusion
detection and countermeasure selection in virtual network systems. IEEE transactions on
dependable and secure computing, 10(4), 198-211.
Taylor, R., Fritsch, E., & Liederbach, J (2014). Digital crime and digital terrorism. Taylor, R.,
Fritsch, E., & Liederbach, J. Digital crime and digital terrorism.
The 12 Types Of Cyber Crime | Chapter No. 2 | Fasttrack To Cyber Crime | Digit. (2018).
Retrieved from https://www.digit.in/technology-guides/fasttrack-to-cyber-crime/the-12-
types-of-cyber-crime.html
Woo, S., Jo, H. J., & Lee, D. H. (2015). A practical wireless attack on the connected car and
security protocol for in-vehicle CAN. IEEE Transactions on Intelligent Transportation
Systems, 16(2), 993-1006.
1 out of 10
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


