Forensic Investigation of Illegal Content: A Western Australia Case
VerifiedAdded on 2023/06/03
|47
|5976
|157
Case Study
AI Summary
This document presents a computer forensics case study involving the investigation of illegal clown content on a seized computer in Western Australia. The investigation utilizes tools such as FTK Imager, OSForensics, and Autopsy to analyze a forensic image of the computer's hard drive. The report details the strategies and resources employed, including the installation and application of the forensic tools. It covers key aspects of the investigation, such as identifying the content related to the offense, determining the intent behind the digital content, quantifying the number of relevant files, and examining software installed in relation to the investigation. The case study includes the suspect's denial of accessing the content and outlines the steps taken to acquire and analyze the forensic image, aiming to uncover evidence and provide a comprehensive overview of the digital forensic process.

Computer Forensics
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Introduction...................................................................................................................................2
2. Overview of tasks...........................................................................................................................2
3. Strategies and Resources...............................................................................................................2
4. Progress........................................................................................................................................17
4.1 Representation of Content related to offence........................................................................17
4.2 Evidence Identification............................................................................................................35
4.3 Intent of the digital content.....................................................................................................36
4.4 File Quantity............................................................................................................................37
4.5 Software installed related to investigation.............................................................................38
5. Conclusion....................................................................................................................................38
6. References....................................................................................................................................39
APPENDIX A......................................................................................................................................43
APPENDIX B.......................................................................................................................................45
Page 1 of 47
1. Introduction...................................................................................................................................2
2. Overview of tasks...........................................................................................................................2
3. Strategies and Resources...............................................................................................................2
4. Progress........................................................................................................................................17
4.1 Representation of Content related to offence........................................................................17
4.2 Evidence Identification............................................................................................................35
4.3 Intent of the digital content.....................................................................................................36
4.4 File Quantity............................................................................................................................37
4.5 Software installed related to investigation.............................................................................38
5. Conclusion....................................................................................................................................38
6. References....................................................................................................................................39
APPENDIX A......................................................................................................................................43
APPENDIX B.......................................................................................................................................45
Page 1 of 47

1. Introduction
In the Western Australia, a computer is seized from a work place. Because, the according
to the information the clown content is accessed by the computer. Accessing, owing and
distributing the clown content in Western Australia is illegal. The seized computer is forensically
investigated. The forensic image of hard drive is obtained. The forensic image is known as
digital evidence. The digital evidence related to the offence is collected. Now, the forensic
investigation will be done on the obtained forensic image. This will be done by using forensic
tools. The tools used for forensic investigation are OSForensics, Autopsy and FTK Imager. The
ownership identification, intention of the offence and the number of files present in the forensic
image will be found.
2. Overview of tasks
The forensic tools are downloaded and installed to analyze the forensic image from the
computer in which the offence is take place. First task is collecting the forensic image of the
offence computer. After that analyze the forensic image using appropriate tools. By using these
tools the clown content is found which is illegal in Western Australia.
3. Strategies and Resources
The resources used for the investigation are FTK Imager, OSForensics tool and Autopsy.
The Clark who is a suspect, the investigator and a junior investigator. And a system in which the
forensic investigation will done. The tools used for investigating the given forensic image are
explained below in detail ("Dendroecology: A Key Forensic Age-Dating Tool", 2005).
FTK imager
FTK imager is a forensic tool and a software library package which is used for Access the
data from the image ("AccessData", 2018). FTK stores the images in the SMART file format and
it is used in the different technologies. It is used to find the different PC crime scene and
investigation programming made by Access Data. The toolbox likewise incorporates an
independent plate imaging program called FTK Imager. The FTK imager is a software
Page 2 of 47
In the Western Australia, a computer is seized from a work place. Because, the according
to the information the clown content is accessed by the computer. Accessing, owing and
distributing the clown content in Western Australia is illegal. The seized computer is forensically
investigated. The forensic image of hard drive is obtained. The forensic image is known as
digital evidence. The digital evidence related to the offence is collected. Now, the forensic
investigation will be done on the obtained forensic image. This will be done by using forensic
tools. The tools used for forensic investigation are OSForensics, Autopsy and FTK Imager. The
ownership identification, intention of the offence and the number of files present in the forensic
image will be found.
2. Overview of tasks
The forensic tools are downloaded and installed to analyze the forensic image from the
computer in which the offence is take place. First task is collecting the forensic image of the
offence computer. After that analyze the forensic image using appropriate tools. By using these
tools the clown content is found which is illegal in Western Australia.
3. Strategies and Resources
The resources used for the investigation are FTK Imager, OSForensics tool and Autopsy.
The Clark who is a suspect, the investigator and a junior investigator. And a system in which the
forensic investigation will done. The tools used for investigating the given forensic image are
explained below in detail ("Dendroecology: A Key Forensic Age-Dating Tool", 2005).
FTK imager
FTK imager is a forensic tool and a software library package which is used for Access the
data from the image ("AccessData", 2018). FTK stores the images in the SMART file format and
it is used in the different technologies. It is used to find the different PC crime scene and
investigation programming made by Access Data. The toolbox likewise incorporates an
independent plate imaging program called FTK Imager. The FTK imager is a software
Page 2 of 47
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

acquisition tool. It is used to preview the evidence quickly ("Chapter 8 - FTK Imager
Walkthrough - Incident Response and Computer Forensics, 3rd Edition", 2018). The computer
forensics will be examined through the forensic toolkit manager. This forensic tool mainly used
to get the evidence and keep it as secure. Also make the analysis about the evidence. IT makes
the computer evidence as original. For that it had two ways, one is creating the image off suspect
drive by the usage of hardware devices or software resources. It had many specifications
regarding with the forensic investigation. They are described below ("Evidence Acquisition
Using Accessdata FTK Imager", 2018). First one is email analysis. According to the email
analysis the forensic tool provides interface for the email analysis. Also this tool is used to make
the email parsing, header analysis regarding to the IP address. Next one is the file encryption. It
is considered as the essential feature of forensic toolkit imager ("Forensic Toolkit FTK Imager
Free Download - ALL PC World", 2018). It is used to crack the password. By the use of FTK
imager we can retrieve the passwords over hundred applications ("FTK Imager - ForensicsWiki",
2018). Third one is data carving. By use the of forensic toolkit imager the robust data would be
obtained. Also the investigators have the option to find the files based on the size and data types
of the file. Fourth one is data visualization. This is considered as emerging one regarding to the
forensic investigation. For the analysis of text data the investigators using the data visualization.
It also helpful for the users in the way of making timeline construction, cluster graphs and also
the geo location ("Ftk Imager - Free downloads and reviews - CNET Download.com", 2018).
The web viewer also considered as the important one and it is used to accelerate the case
assessments in real time. The multicast routing would be done by using the web viewer. Another
feature is represented as Cerberus. It is used as the powerful automated malware detection. Here
the machine intelligence concepts are used to sniffing the malware regarding the computers.
OCR is next feature and it known as optical character recognition. It is used to make the images
into readable text. Also it enables the multi-language support.
Installation of Forensic toolkit imager
The steps are listed below regarding to the installation of forensic toolkit imager. The
screenshots are added for the installation steps. It staring with the initial step of installation and
ending with the completion.
Step 1- Welcome page
Page 3 of 47
Walkthrough - Incident Response and Computer Forensics, 3rd Edition", 2018). The computer
forensics will be examined through the forensic toolkit manager. This forensic tool mainly used
to get the evidence and keep it as secure. Also make the analysis about the evidence. IT makes
the computer evidence as original. For that it had two ways, one is creating the image off suspect
drive by the usage of hardware devices or software resources. It had many specifications
regarding with the forensic investigation. They are described below ("Evidence Acquisition
Using Accessdata FTK Imager", 2018). First one is email analysis. According to the email
analysis the forensic tool provides interface for the email analysis. Also this tool is used to make
the email parsing, header analysis regarding to the IP address. Next one is the file encryption. It
is considered as the essential feature of forensic toolkit imager ("Forensic Toolkit FTK Imager
Free Download - ALL PC World", 2018). It is used to crack the password. By the use of FTK
imager we can retrieve the passwords over hundred applications ("FTK Imager - ForensicsWiki",
2018). Third one is data carving. By use the of forensic toolkit imager the robust data would be
obtained. Also the investigators have the option to find the files based on the size and data types
of the file. Fourth one is data visualization. This is considered as emerging one regarding to the
forensic investigation. For the analysis of text data the investigators using the data visualization.
It also helpful for the users in the way of making timeline construction, cluster graphs and also
the geo location ("Ftk Imager - Free downloads and reviews - CNET Download.com", 2018).
The web viewer also considered as the important one and it is used to accelerate the case
assessments in real time. The multicast routing would be done by using the web viewer. Another
feature is represented as Cerberus. It is used as the powerful automated malware detection. Here
the machine intelligence concepts are used to sniffing the malware regarding the computers.
OCR is next feature and it known as optical character recognition. It is used to make the images
into readable text. Also it enables the multi-language support.
Installation of Forensic toolkit imager
The steps are listed below regarding to the installation of forensic toolkit imager. The
screenshots are added for the installation steps. It staring with the initial step of installation and
ending with the completion.
Step 1- Welcome page
Page 3 of 47
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
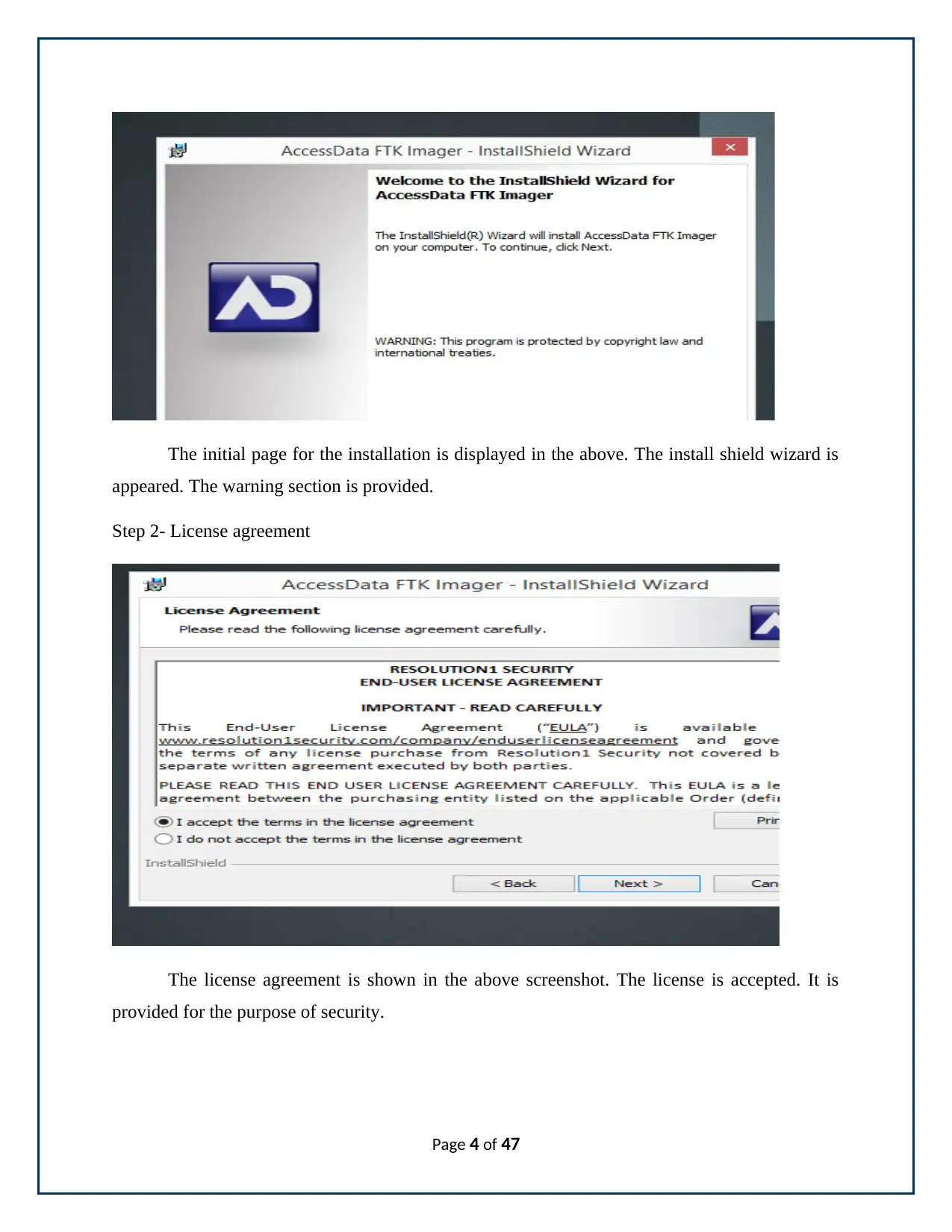
The initial page for the installation is displayed in the above. The install shield wizard is
appeared. The warning section is provided.
Step 2- License agreement
The license agreement is shown in the above screenshot. The license is accepted. It is
provided for the purpose of security.
Page 4 of 47
appeared. The warning section is provided.
Step 2- License agreement
The license agreement is shown in the above screenshot. The license is accepted. It is
provided for the purpose of security.
Page 4 of 47
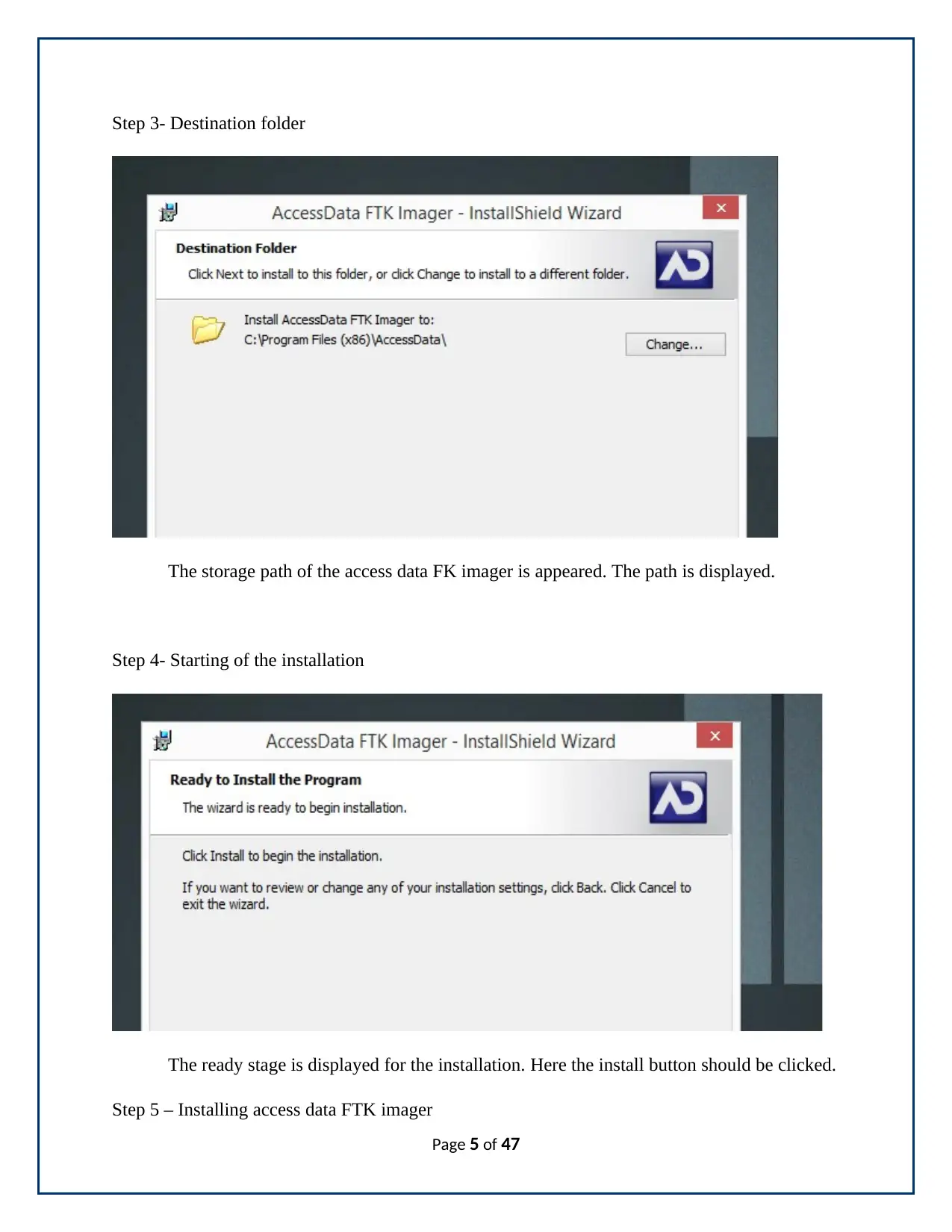
Step 3- Destination folder
The storage path of the access data FK imager is appeared. The path is displayed.
Step 4- Starting of the installation
The ready stage is displayed for the installation. Here the install button should be clicked.
Step 5 – Installing access data FTK imager
Page 5 of 47
The storage path of the access data FK imager is appeared. The path is displayed.
Step 4- Starting of the installation
The ready stage is displayed for the installation. Here the install button should be clicked.
Step 5 – Installing access data FTK imager
Page 5 of 47
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
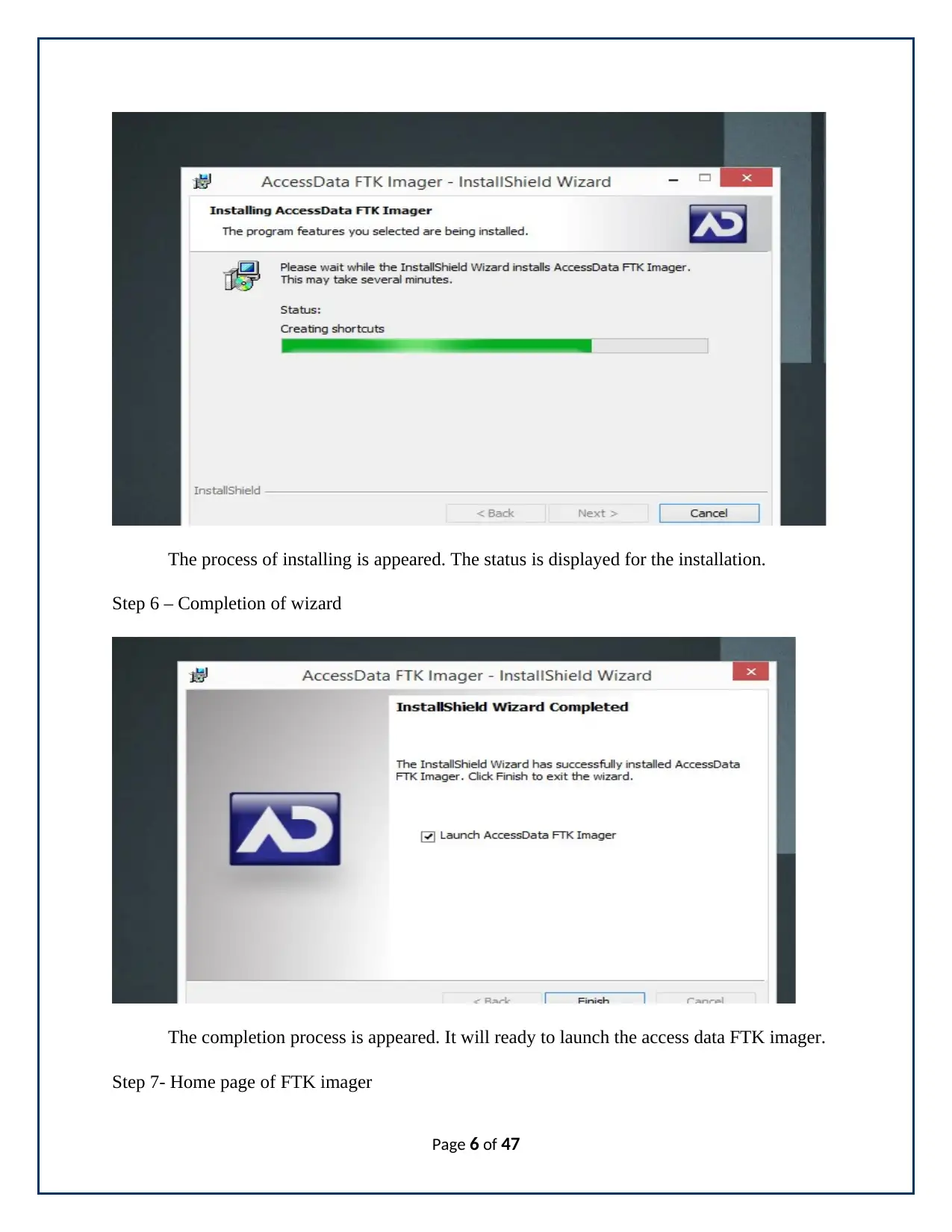
The process of installing is appeared. The status is displayed for the installation.
Step 6 – Completion of wizard
The completion process is appeared. It will ready to launch the access data FTK imager.
Step 7- Home page of FTK imager
Page 6 of 47
Step 6 – Completion of wizard
The completion process is appeared. It will ready to launch the access data FTK imager.
Step 7- Home page of FTK imager
Page 6 of 47
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The home page of the forensic toolkit imager is appeared in the screenshot. It shown the
generic options regarding the tool (Bowser-Rollins, 2018).
Step 8- Source selection
The source selection is displayed in the screenshot. The evidence types are shown.
Autopsy
Page 7 of 47
generic options regarding the tool (Bowser-Rollins, 2018).
Step 8- Source selection
The source selection is displayed in the screenshot. The evidence types are shown.
Autopsy
Page 7 of 47

Autopsy is a computerized device and it is mainly used for doing the forensics things and
it is tool works in forensics platform and the GUI ("Autopsy - Basis Technology", 2018). It is
mainly used in the fields like law requirement activities, defense services, and other corporate
analysts who wants to secure their contents ("Autopsy - Digital Forensics Platform - Hacking
Vision", 2018). This tool is also used for exploring the contents like checking and investigating
the computers to find what kind of activities occurred on a Personal Computers. Using this we
can also does the features like recovering images in our camera's memory card. This tool is also
used for other backup purposes ("Autopsy – Training | Autopsy", 2018). The software is to a
great extent kept up by Basis Technology Corp. with the help of developers from the network.
The organization offers bolster administrations and preparing for utilizing the product. The GUI
of this tool shows the outcomes from the fundamental volume creation and using this tool it
simpler for specialists to retrieve the relevant areas of information ("Autopsy | Open Source
Digital Forensics", 2018). It is the forensic tool or software that makes it less difficult to send a
significant number of the free generation programs and modules which are used in the Sleuth Kit
("Autopsy of a Dill Pickle-Introductory Lab for Anatomy or Forensics!", 2018). This tool also
gives various capacities that guide on the off chance that administration. Specifically,
examinations began inside this tools are composed by cases, which can contains different hosts
("Autopsy", 2018). Each and every hosts are arranged to have its opportunity zone for setting the
time with the goal that the occasions demonstrated are the equivalent as the first client would
have seen. Each host can contain at least one record framework pictures to investigate. The
designed autopsy tool has some specific principles. First one is extensible ("International
Environmental Forensics Conference Qingdao, China, May 27–30, 2008", 2007). The new
functionality should be added by developing the plugins. Also the tool should be provide the
standard mechanism regarding the features. It offer many function to the development of case
management. Investigators mostly use this case management. The functions are listed below.
The event sequencer is a kind of function used in the case management. The time based
events could be added ("Autopsy", 2018). The autopsy tool is used to sort the events. So through
this function the investigators can easily determine the events. Next function is the notes. These
notes could be saved based on the investigators. These functions are used to the investigators for
creating the notes about the files and structures. These notes are stored in the format such as
ASCII value. The image integrity is considered as the third function ("Autopsy: Lesson 1:
Page 8 of 47
it is tool works in forensics platform and the GUI ("Autopsy - Basis Technology", 2018). It is
mainly used in the fields like law requirement activities, defense services, and other corporate
analysts who wants to secure their contents ("Autopsy - Digital Forensics Platform - Hacking
Vision", 2018). This tool is also used for exploring the contents like checking and investigating
the computers to find what kind of activities occurred on a Personal Computers. Using this we
can also does the features like recovering images in our camera's memory card. This tool is also
used for other backup purposes ("Autopsy – Training | Autopsy", 2018). The software is to a
great extent kept up by Basis Technology Corp. with the help of developers from the network.
The organization offers bolster administrations and preparing for utilizing the product. The GUI
of this tool shows the outcomes from the fundamental volume creation and using this tool it
simpler for specialists to retrieve the relevant areas of information ("Autopsy | Open Source
Digital Forensics", 2018). It is the forensic tool or software that makes it less difficult to send a
significant number of the free generation programs and modules which are used in the Sleuth Kit
("Autopsy of a Dill Pickle-Introductory Lab for Anatomy or Forensics!", 2018). This tool also
gives various capacities that guide on the off chance that administration. Specifically,
examinations began inside this tools are composed by cases, which can contains different hosts
("Autopsy", 2018). Each and every hosts are arranged to have its opportunity zone for setting the
time with the goal that the occasions demonstrated are the equivalent as the first client would
have seen. Each host can contain at least one record framework pictures to investigate. The
designed autopsy tool has some specific principles. First one is extensible ("International
Environmental Forensics Conference Qingdao, China, May 27–30, 2008", 2007). The new
functionality should be added by developing the plugins. Also the tool should be provide the
standard mechanism regarding the features. It offer many function to the development of case
management. Investigators mostly use this case management. The functions are listed below.
The event sequencer is a kind of function used in the case management. The time based
events could be added ("Autopsy", 2018). The autopsy tool is used to sort the events. So through
this function the investigators can easily determine the events. Next function is the notes. These
notes could be saved based on the investigators. These functions are used to the investigators for
creating the notes about the files and structures. These notes are stored in the format such as
ASCII value. The image integrity is considered as the third function ("Autopsy: Lesson 1:
Page 8 of 47
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Analyzing Deleted JPEGs", 2018). Here the forensic investigation is used to ensuring the data is
modified during the analysis. The autopsy tool develop the MD5 value for all files ("Hacking &
Digital Forensics & Autopsy - Stay Anonymous", 2018). This tool is used to validate the
integrity of the file. Then the fourth function is the reports. It can create the ASCII reports for the
files and other file system structures. These reports are used for the developers to create the
datasheets (Galvao, 2006).
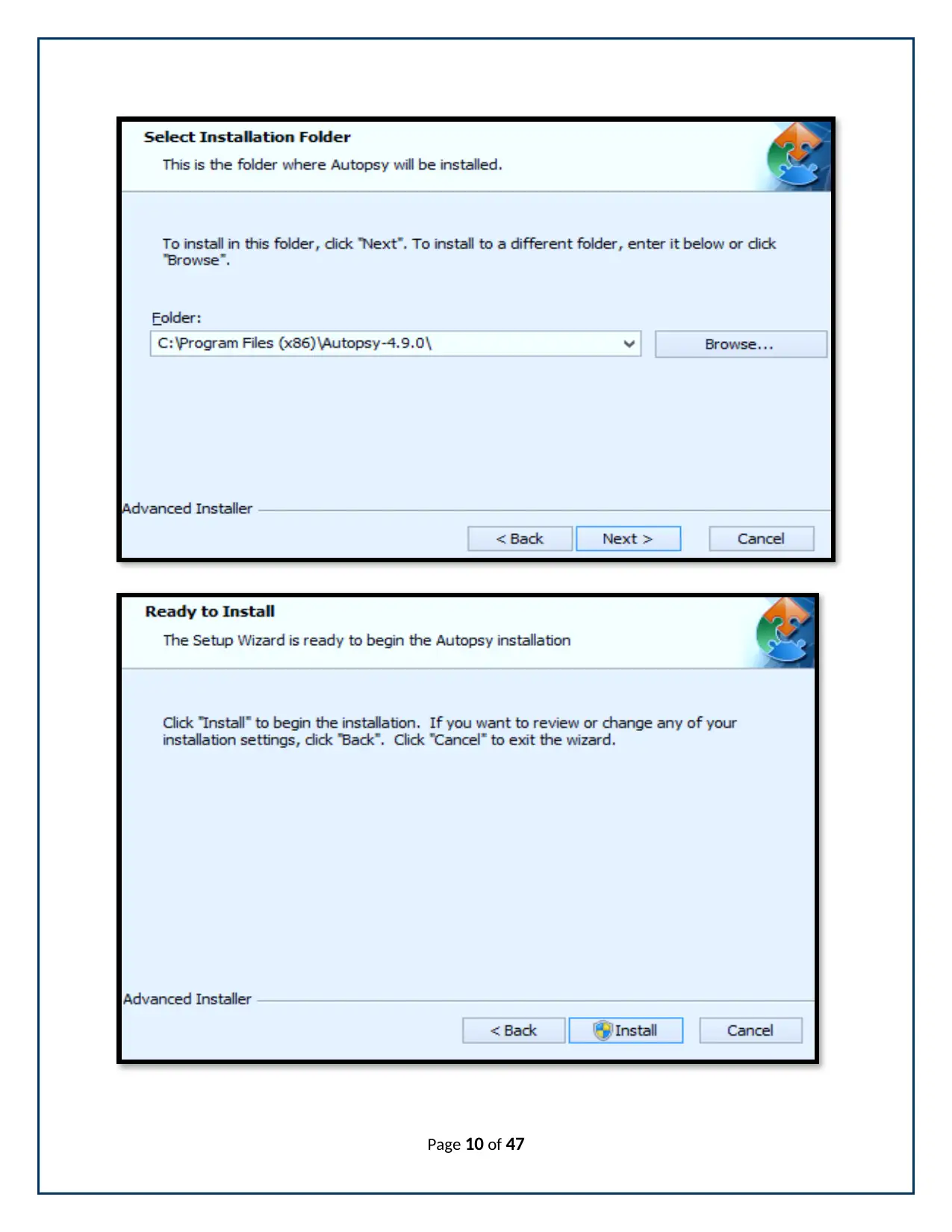
Installation of Autopsy
The steps are listed below regarding to the installation of Autopsy ("Autopsy:
Download", 2018). The screenshots are added for the installation steps. It staring with the initial
step of installation and ending with the completion.
Page 9 of 47
modified during the analysis. The autopsy tool develop the MD5 value for all files ("Hacking &
Digital Forensics & Autopsy - Stay Anonymous", 2018). This tool is used to validate the
integrity of the file. Then the fourth function is the reports. It can create the ASCII reports for the
files and other file system structures. These reports are used for the developers to create the
datasheets (Galvao, 2006).
Installation of Autopsy
The steps are listed below regarding to the installation of Autopsy ("Autopsy:
Download", 2018). The screenshots are added for the installation steps. It staring with the initial
step of installation and ending with the completion.
Page 9 of 47
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Page 10 of 47
Page 11 of 47
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 47
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





