Forensic Study of IMO Call and Chat App on Android and iOS Devices
VerifiedAdded on 2022/08/25
|19
|13087
|193
Report
AI Summary
This report presents a forensic study of the IMO call and chat application, focusing on both Android and iOS platforms. The research investigates device forensics by examining the app's file structure and identifying artifacts stored in the device's memory. The study also delves into network forensics, analyzing the encrypted traffic generated by IMO, including calls and chats. A novel approach using a firewall to analyze IMO's client-server communication in a controlled environment is introduced. The report outlines the methodology, experimental setup, and results, including differences between Android and iOS platforms. The findings are applied to reconstruct a crime scene involving IMO. The research highlights the importance of digital forensics in investigating social media apps and provides valuable insights for investigators.

Forensics study of IMO call and chat app
M.A.K. Sudozaib
, Shahzad Saleemb
, William J. Buchanana, * , Nisar Habibb
,
Haleemah Ziab
a The Cyber Academy,Edinburgh Napier University,Edinburgh,UK
b School of Electrical Engineering and Computer Science (SEECS),National University of Sciences and Technology (NUST),Islamabad,44000,Pakistan
a r t i c l e i n f o
Article history:
Received 4 January 2018
Received in revised form
17 April 2018
Accepted 18 April 2018
Available online 25 April 2018
Keywords:
IMO
Encryption
Android
iOS
Network forensic
Device forensic
a b s t r a c t
Smart phones often leave behind a wealth of information that can be used as an evidence during an
investigation.There are thus many smart phone applications that employ encryption to store and/or
transmit data,and this can add a layer of complexity for an investigator.IMO is a popular application
which employs encryption for both call and chat activities.This paper explores important artifacts from
both the device and from the network traffic. This was generated for both Android and iOS platforms. The
novel aspect of the work is the extensive analysis of encrypted network traf fic generated by IMO.Along
with this the paper defines a new method of using a firewall to explore the obscured options of con-
nectivity,and in a way which is independent of the protocolused by the IMO client and server.Our
results outline that we can correctly detect IMO traffic flows and classify different events of its chat and
call related activities. We have also compared IMO network traffic of Android and iOS platforms to report
the subtle differences.The results are valid for IMO 9.8.00 on Android and 7.0.55 on iOS.
© 2018 Elsevier Ltd.All rights reserved.
Introduction
IMO (http://imo.im) is a free messaging,voice and video call
application (app) and which was launched in 2007 by Ralph Harik,
Georges Harik and Praveen Krishnamurthy (Crunchbase,May 23,
2013 [accessed 16-March-2017]; Eldon,2007 [accessed 16-March-
2017]). According to a survey conducted in 2016 by App Annie, IMO
is one of the top communication apps being used worldwide
(AppAnnie,2016 [accessed 16-March-2017]).Apart from its user-
friendly design and reliable connectivity,one major factor that
contributes to this popularity is its provision of service in countries
where competitor apps (WhatsApp or Viber) are blocked by gov-
ernment agencies (Quora,May, 2016 [accessed 17-March-2017];
ProVpnAccounts, May,2016 [accessed 17-March-2017]).
Our major contribution in this paper is the exploration and
analysis of IMO artifacts for:
The artifacts generated through the usage on of mobile device.
The artifacts generated through usage over the network.
An investigation of both Android and iOS devices.
The results of mobile device forensics indicate that IMO stores
data in plain text,so that anyone with the controlof the smart
phone can have access to the underlying data. We have conducted a
detailed study of IMO file structure on both Android and iOS plat-
forms and define the grey areas which can be exploited during the
forensics study of IMO.
From the network perspective,it is important to highlight that
the communication protocol of IMO,as well as its security archi-
tecture, are not known in public literature. We have performed an
extensive review of the traffic analysis of IMO and have introduced
the idea of incorporating a firewall approach to the investigation.
The firewall helps understand the patterns of connectivity and then
can regulate the traffic based on a progressive study. We thus forced
the IMO client to connect to its servers in a controlled environment
and this arrangement revealed the obscured design of IMO client
connectivity to its servers.After this, we experimented with the
network activities of IMO on both the platforms in order to study
different traffic characteristics.
In Section Related work,we have summarized the previous
work done in forensics analysis of social media apps. Section Device
forensics of IMO covers the device forensics part of IMO, along with
our analysis methodology,detailed experimental setup for access-
ing the Android and iOS storage/memory and results of our study
have been separately mentioned for both these platforms.Section
Network forensics of IMO defines the network forensics elements
of IMO, and discuss the traffic analysis setup and the results for both
Android and iOS platforms.Section Crime scene reconstruction* Corresponding author.
E-mail address: w.buchanan@napier.ac.uk (W.J.Buchanan).
Contents lists available at ScienceDirect
Digital Investigation
j o u r n a lhomepage: w w w . e l s e v i e r . c o m / l o c a t e / d i i n
https://doi.org/10.1016/j.diin.2018.04.006
1742-2876/© 2018 Elsevier Ltd.All rights reserved.
Digital Investigation 25 (2018) 5e23
M.A.K. Sudozaib
, Shahzad Saleemb
, William J. Buchanana, * , Nisar Habibb
,
Haleemah Ziab
a The Cyber Academy,Edinburgh Napier University,Edinburgh,UK
b School of Electrical Engineering and Computer Science (SEECS),National University of Sciences and Technology (NUST),Islamabad,44000,Pakistan
a r t i c l e i n f o
Article history:
Received 4 January 2018
Received in revised form
17 April 2018
Accepted 18 April 2018
Available online 25 April 2018
Keywords:
IMO
Encryption
Android
iOS
Network forensic
Device forensic
a b s t r a c t
Smart phones often leave behind a wealth of information that can be used as an evidence during an
investigation.There are thus many smart phone applications that employ encryption to store and/or
transmit data,and this can add a layer of complexity for an investigator.IMO is a popular application
which employs encryption for both call and chat activities.This paper explores important artifacts from
both the device and from the network traffic. This was generated for both Android and iOS platforms. The
novel aspect of the work is the extensive analysis of encrypted network traf fic generated by IMO.Along
with this the paper defines a new method of using a firewall to explore the obscured options of con-
nectivity,and in a way which is independent of the protocolused by the IMO client and server.Our
results outline that we can correctly detect IMO traffic flows and classify different events of its chat and
call related activities. We have also compared IMO network traffic of Android and iOS platforms to report
the subtle differences.The results are valid for IMO 9.8.00 on Android and 7.0.55 on iOS.
© 2018 Elsevier Ltd.All rights reserved.
Introduction
IMO (http://imo.im) is a free messaging,voice and video call
application (app) and which was launched in 2007 by Ralph Harik,
Georges Harik and Praveen Krishnamurthy (Crunchbase,May 23,
2013 [accessed 16-March-2017]; Eldon,2007 [accessed 16-March-
2017]). According to a survey conducted in 2016 by App Annie, IMO
is one of the top communication apps being used worldwide
(AppAnnie,2016 [accessed 16-March-2017]).Apart from its user-
friendly design and reliable connectivity,one major factor that
contributes to this popularity is its provision of service in countries
where competitor apps (WhatsApp or Viber) are blocked by gov-
ernment agencies (Quora,May, 2016 [accessed 17-March-2017];
ProVpnAccounts, May,2016 [accessed 17-March-2017]).
Our major contribution in this paper is the exploration and
analysis of IMO artifacts for:
The artifacts generated through the usage on of mobile device.
The artifacts generated through usage over the network.
An investigation of both Android and iOS devices.
The results of mobile device forensics indicate that IMO stores
data in plain text,so that anyone with the controlof the smart
phone can have access to the underlying data. We have conducted a
detailed study of IMO file structure on both Android and iOS plat-
forms and define the grey areas which can be exploited during the
forensics study of IMO.
From the network perspective,it is important to highlight that
the communication protocol of IMO,as well as its security archi-
tecture, are not known in public literature. We have performed an
extensive review of the traffic analysis of IMO and have introduced
the idea of incorporating a firewall approach to the investigation.
The firewall helps understand the patterns of connectivity and then
can regulate the traffic based on a progressive study. We thus forced
the IMO client to connect to its servers in a controlled environment
and this arrangement revealed the obscured design of IMO client
connectivity to its servers.After this, we experimented with the
network activities of IMO on both the platforms in order to study
different traffic characteristics.
In Section Related work,we have summarized the previous
work done in forensics analysis of social media apps. Section Device
forensics of IMO covers the device forensics part of IMO, along with
our analysis methodology,detailed experimental setup for access-
ing the Android and iOS storage/memory and results of our study
have been separately mentioned for both these platforms.Section
Network forensics of IMO defines the network forensics elements
of IMO, and discuss the traffic analysis setup and the results for both
Android and iOS platforms.Section Crime scene reconstruction* Corresponding author.
E-mail address: w.buchanan@napier.ac.uk (W.J.Buchanan).
Contents lists available at ScienceDirect
Digital Investigation
j o u r n a lhomepage: w w w . e l s e v i e r . c o m / l o c a t e / d i i n
https://doi.org/10.1016/j.diin.2018.04.006
1742-2876/© 2018 Elsevier Ltd.All rights reserved.
Digital Investigation 25 (2018) 5e23
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
demonstrates the application of our results to reconstruct a crime
scene involving IMO. The paper is finally concluded in Section
Conclusion.
Related work
Over the past few years,users concerns over their privacy has
been increasing, alongside the number of social media apps
providing privacy to their users (Taylor et al.,2014).Besides their
positive use,the secure services offered by these apps are also
extensively exploited in variety of criminal cases.Digital forensics
thus has become an most important componentof any crime
investigation (Seigfried-Spellar and Leshney,2015; Huber et al.,
2011; Brunty et al.,2014).For any mobile social media app,foren-
sics analysis has two dimensions:
Device forensics. This includes analyzing memory and storage
elements (Norouzizadeh Dezfouli et al.,2016).
Network forensics. This involves the study of network traffic for
different activities of users and services (Lillard,2010).
The most comprehensive study of network and device forensics
of Android social-messaging applications has been carried out by
(Walnycky et al., 2015). This includes the forensics analysis of 20 of
the most popular social media apps for Android. The authors
highlight the features of target apps and which leave artifacts of
evidentiary value for an investigation.More specifically,the pos-
sibility of full or partial reconstruction of a crime scene through
network and/or device forensics ofthese was explored.Besides
Android, other platforms hosting social media apps, such as
BlackBerrys and iPhones,have also been studied with respect to
their utilization in a digital forensics investigation (Al Mutawa et al.,
2012; Tso et al.,2012).
Device and network forensics of popular apps have been carried
out regularly. As a leading platform for secure voice, video and chat
services, studies on Skype have become fundamental in this
domain (Dupasquier et al.,2010; Molnar and Perenyi,2011).Simi-
larly artifacts of Viber (Appelman et al.,2011; Marik et al.,2015),
Telegram (Anglano et al., 2017) on Android smart phones, Telegram
on Windows phone (Gregorio et al., 2017),WeChat (Wu et al.,
2017),ChatSecure (Anglano etal., 2016),Wickr (Mehrotra and
Mehtre,2013),KiK on iOS (Ovens and Morison,2016) and What-
sApp (Anglano, 2014; Karpisek et al., 2015; Majeed et al., 2015) have
also been studied in detail (Azfar et al.,2016).contains a detailed
research of Android forensics,and where 30 Android apps were
studied with a focus on extracting useful information from memory
using XRY - a well known mobile forensics tool. A generic taxonomy
of the Android forensics is also proposed and which is correlated as
a study of forensics artifacts of these apps.
Following the same motivation, we chose IMO apps for forensics
study and which covered both device- and network-based analysis.
For the device forensics part,we carried out a study of IMO files
structure on Android and iOS platforms. This provided a way to find
the critical artifacts and their significance.Similarly,a study of
network forensics ofIMO is presented on both the platforms in
which network traffic is analyzed to classify the IMO flows and
detection of user activities by analyzing the sniffed traffic. Novelty
of our work lies in the study of IMO at such a scale. Moreover,our
methodology of network forensics is interesting because most of
the related research is limited to plaintext, whereas we have
included encrypted network traffic in our study.
Contrary to other studies of chat and calling apps where
network traffic is sniffed and then analyzed to draw important
conclusions,a firewall is used to carry out analysis of IMO client-
server communication in a controlled environment.Observing a
known behavior of a IMO client,a firewall is then used to restrict
the IMO client traffic and to force it to expose allthe alternate
connectivity methods.Our methodology of studying network
traffic of IMO in a controlled environment with a firewall is generic
and can be used for network forensics of other apps as well.
Referring to the goal of forensics analysis which should exhibit
the specific properties listed in (Anglano et al.,2017),and where
our methodology of both the domains of device and network fo-
rensics was aimed to achieve completeness,repeatability and
generality.The limitations,we observed during the course of our
study are clearly highlighted for the future work. It is important to
mention that the results of this paper are presented with reference
to specific versions ofAndroid and iOS,but the conclusions are
applicable to contemporary versions of Android and iOS with their
supporting handsets.
Device forensics of IMO
Analysis methodology
We carried out device forensics of the IMO app on Android and
on the iOS platform,separately.Our methodology of device foren-
sics is focused to identify maximum possible artifacts from the
device's internal and external memory. The analysis of IMO app on
both the platforms of Android and iOS makes our work more
comprehensive as each platform has unique identifiers and method
of access to one are not applicable to the other.
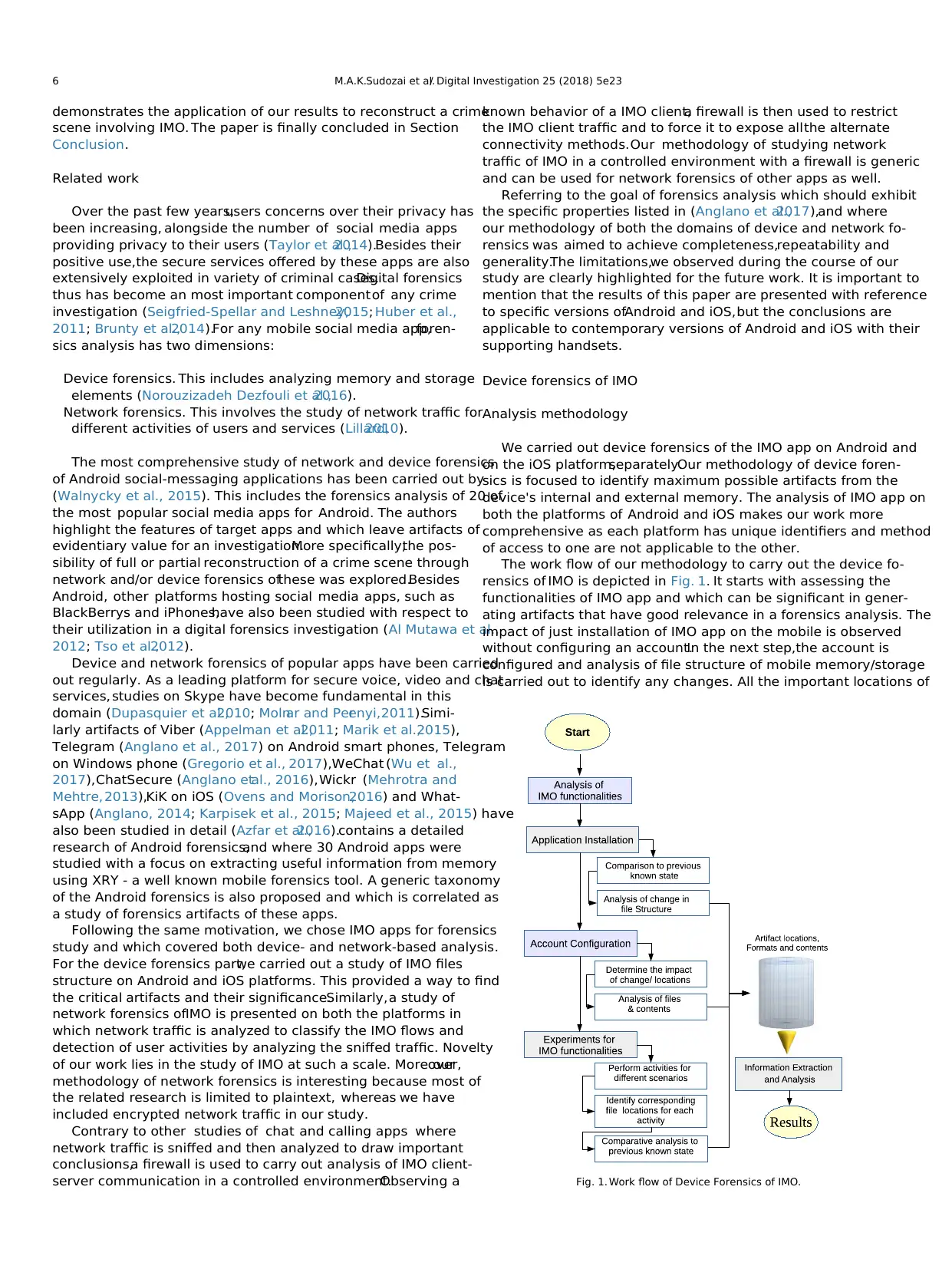
The work flow of our methodology to carry out the device fo-
rensics of IMO is depicted in Fig. 1. It starts with assessing the
functionalities of IMO app and which can be significant in gener-
ating artifacts that have good relevance in a forensics analysis. The
impact of just installation of IMO app on the mobile is observed
without configuring an account.In the next step,the account is
configured and analysis of file structure of mobile memory/storage
is carried out to identify any changes. All the important locations of
Fig. 1. Work flow of Device Forensics of IMO.
M.A.K.Sudozai et al./ Digital Investigation 25 (2018) 5e236
scene involving IMO. The paper is finally concluded in Section
Conclusion.
Related work
Over the past few years,users concerns over their privacy has
been increasing, alongside the number of social media apps
providing privacy to their users (Taylor et al.,2014).Besides their
positive use,the secure services offered by these apps are also
extensively exploited in variety of criminal cases.Digital forensics
thus has become an most important componentof any crime
investigation (Seigfried-Spellar and Leshney,2015; Huber et al.,
2011; Brunty et al.,2014).For any mobile social media app,foren-
sics analysis has two dimensions:
Device forensics. This includes analyzing memory and storage
elements (Norouzizadeh Dezfouli et al.,2016).
Network forensics. This involves the study of network traffic for
different activities of users and services (Lillard,2010).
The most comprehensive study of network and device forensics
of Android social-messaging applications has been carried out by
(Walnycky et al., 2015). This includes the forensics analysis of 20 of
the most popular social media apps for Android. The authors
highlight the features of target apps and which leave artifacts of
evidentiary value for an investigation.More specifically,the pos-
sibility of full or partial reconstruction of a crime scene through
network and/or device forensics ofthese was explored.Besides
Android, other platforms hosting social media apps, such as
BlackBerrys and iPhones,have also been studied with respect to
their utilization in a digital forensics investigation (Al Mutawa et al.,
2012; Tso et al.,2012).
Device and network forensics of popular apps have been carried
out regularly. As a leading platform for secure voice, video and chat
services, studies on Skype have become fundamental in this
domain (Dupasquier et al.,2010; Molnar and Perenyi,2011).Simi-
larly artifacts of Viber (Appelman et al.,2011; Marik et al.,2015),
Telegram (Anglano et al., 2017) on Android smart phones, Telegram
on Windows phone (Gregorio et al., 2017),WeChat (Wu et al.,
2017),ChatSecure (Anglano etal., 2016),Wickr (Mehrotra and
Mehtre,2013),KiK on iOS (Ovens and Morison,2016) and What-
sApp (Anglano, 2014; Karpisek et al., 2015; Majeed et al., 2015) have
also been studied in detail (Azfar et al.,2016).contains a detailed
research of Android forensics,and where 30 Android apps were
studied with a focus on extracting useful information from memory
using XRY - a well known mobile forensics tool. A generic taxonomy
of the Android forensics is also proposed and which is correlated as
a study of forensics artifacts of these apps.
Following the same motivation, we chose IMO apps for forensics
study and which covered both device- and network-based analysis.
For the device forensics part,we carried out a study of IMO files
structure on Android and iOS platforms. This provided a way to find
the critical artifacts and their significance.Similarly,a study of
network forensics ofIMO is presented on both the platforms in
which network traffic is analyzed to classify the IMO flows and
detection of user activities by analyzing the sniffed traffic. Novelty
of our work lies in the study of IMO at such a scale. Moreover,our
methodology of network forensics is interesting because most of
the related research is limited to plaintext, whereas we have
included encrypted network traffic in our study.
Contrary to other studies of chat and calling apps where
network traffic is sniffed and then analyzed to draw important
conclusions,a firewall is used to carry out analysis of IMO client-
server communication in a controlled environment.Observing a
known behavior of a IMO client,a firewall is then used to restrict
the IMO client traffic and to force it to expose allthe alternate
connectivity methods.Our methodology of studying network
traffic of IMO in a controlled environment with a firewall is generic
and can be used for network forensics of other apps as well.
Referring to the goal of forensics analysis which should exhibit
the specific properties listed in (Anglano et al.,2017),and where
our methodology of both the domains of device and network fo-
rensics was aimed to achieve completeness,repeatability and
generality.The limitations,we observed during the course of our
study are clearly highlighted for the future work. It is important to
mention that the results of this paper are presented with reference
to specific versions ofAndroid and iOS,but the conclusions are
applicable to contemporary versions of Android and iOS with their
supporting handsets.
Device forensics of IMO
Analysis methodology
We carried out device forensics of the IMO app on Android and
on the iOS platform,separately.Our methodology of device foren-
sics is focused to identify maximum possible artifacts from the
device's internal and external memory. The analysis of IMO app on
both the platforms of Android and iOS makes our work more
comprehensive as each platform has unique identifiers and method
of access to one are not applicable to the other.
The work flow of our methodology to carry out the device fo-
rensics of IMO is depicted in Fig. 1. It starts with assessing the
functionalities of IMO app and which can be significant in gener-
ating artifacts that have good relevance in a forensics analysis. The
impact of just installation of IMO app on the mobile is observed
without configuring an account.In the next step,the account is
configured and analysis of file structure of mobile memory/storage
is carried out to identify any changes. All the important locations of
Fig. 1. Work flow of Device Forensics of IMO.
M.A.K.Sudozai et al./ Digital Investigation 25 (2018) 5e236

IMO files are then determined along with their formats.The last
stage are experiments for functionality analysis at the start ofa
functional aspect and then analyze the changes in files of IMO. The
files of IMO can be extracted out of mobile memory whenever
required during any ofthe above for their content analysis and
correlation.Artifacts are then studied in order to identify their
mappings to different activities of an IMO user.
Analysis of IMO functionalities
As shown in Fig. 1,the first step of our work flow is to identify
those functionalities of IMO app which are important for the fo-
rensics analysis of the mobile device. Like any calling and chat app,
IMO provides a long list of features including live chat,voice call,
video call,media share (Photos and video),story sharing,group
chat, and so on. Starting from the IMO app installation in a mobile
device,different app features and activities ofuser which leave
possible traces of information in mobile storage are:
a) Installation of IMO app.Different chat and calling apps follow
different file structures upon installation. Many files and folders
are created in both user and system space during the installa-
tion process.Identifying the location of these files and folders
along with their usage can be important for an investigator.
b) Accountconfiguration.After the installation, the account
configuration of IMO user is an important event and which
has a unique impact on file storage. According to the specific
user credentials and app permissions thatare granted,a
number of databases of IMO are updated.
c) Fetching contacts list of users from a mobile.Depending upon
the settings and permissions, IMO fetches contacts which are
already stored on the device.Details of these contacts and
their format can help in forensics analysis of IMO.
d) Exchange of chat messages. IMO provides the functionality of
message exchange including voice clips,stickers,images,
videos, and so on. All chats are encrypted before trans-
mission, however the IMO app stores these messages in
plaintext form. The location and format of each type of these
artifacts is important from forensics point of view.
e) Status of chat messages.Like other contemporary apps,IMO
maintains the status of chat messages including delivered,
read,and so on.Specific identifiers indicating the status of
different messages are fixed by IMO.
f) Voice and video calls. IMO provides the functionality of audio
and video calls which are encrypted. Records of these calls is
maintained in the memory and their location could be
important to any crime scene investigation involving IMO.
Results for Android and iOS forensics provided a good deal of
similarity.However,to give clarity on access to mobile storage in
each case,there are differences in file structures,and peculiar
format of artifacts from the extraction from mobile memory/stor-
age and thus Android and iOS will be outlined separately.
Device forensics on android
Experimental setup
We installed IMO on a rooted Samsung Galaxy 6.0 having an
Android version of 6.0.1. On a Ubuntu 16.04 terminal, the following
steps were taken to access the smart phone's file structure:
Run the command ”adb shell”.This was to run the Android
Debug Bridge (adb) tool in order to access the mobile memory.
Pressed ”Allow” on mobile against the prompt ”Allow access to
mobile data”.
User then entered to ”shell@zeroflte:/$ ”.
To gain root previligaes,we pressed ”su”.Root privileges were
shown as ”root@zeroflte:/#”.
Entering the command ”ls” will display all the files and folders
on the mobile in both user and system space.
To identifying the file structure of IMO app, we used a number of
controlled activities related to text,voice, and video chats,and
observed their corresponding traces within different storage re-
cords maintained by IMO.These were validated using the Helium
Backup (Chris,2014 [accessed 3-june-2017]) to retrieve.db files of
the IMO app. Finally,an Android backup extractor and db browser
for SQLite was used to analyze the contents of storage elements
against each activity.
Results and their analysis e android device
Following the steps of our work flow as shown in Fig. 1, the file
structure of IMO on Android is identified and shown in Fig.2.
The following section will throw some light on the files and
folders that were identified during device forensics ofIMO on
Android platform.
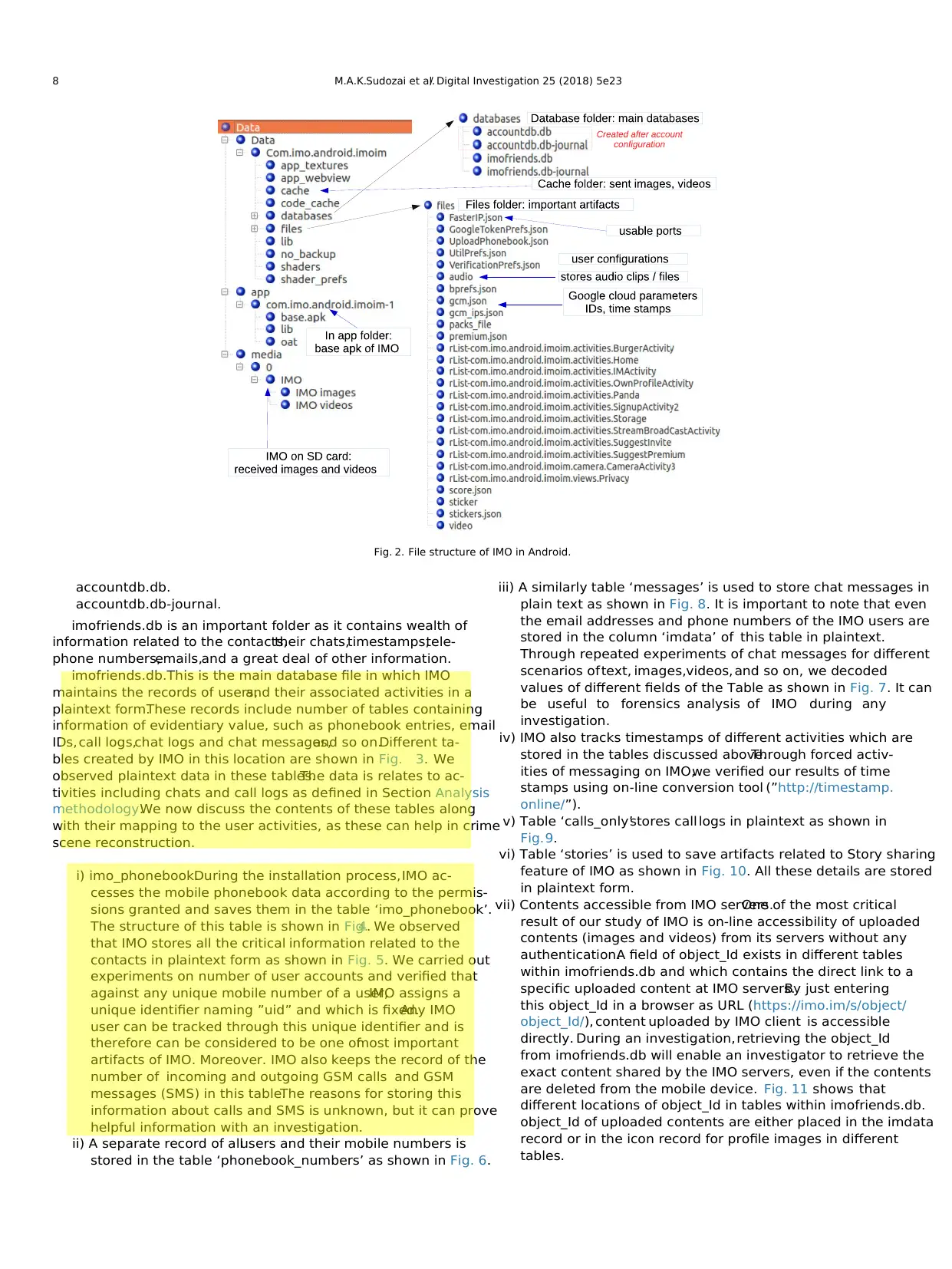
Main folders of IMO file structure.Upon installation of IMO on
Android,three main folders are created at fixed locations as:
com.imo.android.imoim-1 at location ”/data/app/”.
com.imo.android.imoim at location ”/data/data/”.
IMO at location ”/data/media/0/”. This is a location of SD card or
user accessible memory and which is normally visible through
USB connectivity on a PC,even without the root privileges.
The sub folders and files which are created within each of the
main folders are depicted in Fig.2. We now discuss the important
files,their locations and related artifacts stored by IMO with their
mapping to functionalities discussed in Section Analysis
methodology.
File structure ofcom.imo.android.imoim-1.Like other popular chat
and calling apps namely WhatsApp,Signal and Telegram,IMO
creates this folder in device memory at ”/data/app/”. Each of these
apps store their basic apk files along with other associated files in
app folder. IMO also creates a folder with its name IMO in app folder
and base.apk file is stored there.
File structure of com.imo.android.imoim.IMO stores most of its user
related artifacts in this folder. This location is critical because arti-
facts related to user credentials/activities are stored there.We
experimented number of user activities outlined in Section Analysis
methodology and observed their corresponding storage patterns by
IMO. Referring to Fig.2 again,the following explains the files and
folders at this location.
a) “cache” folder.IMO stores sent images and videos in a ”cache”
folder,whereas received images and videos are stored in user
space within IMO folder.This will be discussed in detailin a
following section. All these images and videos are stored in non-
encrypted form in the device memory.
b) “Databases” folder.From forensics point of view, Databases
folder is considered as one of the most important component of
file structure of IMO. Upon installation of IMO app, the following
two files are created in this folder before the account
configuration:
imofriends.db.
imofriends.db-journal.
c) After the user account is configured with IMO servers,the app
creates two additional files in Databases folder:
M.A.K.Sudozai et al./ Digital Investigation 25 (2018) 5e23 7
stage are experiments for functionality analysis at the start ofa
functional aspect and then analyze the changes in files of IMO. The
files of IMO can be extracted out of mobile memory whenever
required during any ofthe above for their content analysis and
correlation.Artifacts are then studied in order to identify their
mappings to different activities of an IMO user.
Analysis of IMO functionalities
As shown in Fig. 1,the first step of our work flow is to identify
those functionalities of IMO app which are important for the fo-
rensics analysis of the mobile device. Like any calling and chat app,
IMO provides a long list of features including live chat,voice call,
video call,media share (Photos and video),story sharing,group
chat, and so on. Starting from the IMO app installation in a mobile
device,different app features and activities ofuser which leave
possible traces of information in mobile storage are:
a) Installation of IMO app.Different chat and calling apps follow
different file structures upon installation. Many files and folders
are created in both user and system space during the installa-
tion process.Identifying the location of these files and folders
along with their usage can be important for an investigator.
b) Accountconfiguration.After the installation, the account
configuration of IMO user is an important event and which
has a unique impact on file storage. According to the specific
user credentials and app permissions thatare granted,a
number of databases of IMO are updated.
c) Fetching contacts list of users from a mobile.Depending upon
the settings and permissions, IMO fetches contacts which are
already stored on the device.Details of these contacts and
their format can help in forensics analysis of IMO.
d) Exchange of chat messages. IMO provides the functionality of
message exchange including voice clips,stickers,images,
videos, and so on. All chats are encrypted before trans-
mission, however the IMO app stores these messages in
plaintext form. The location and format of each type of these
artifacts is important from forensics point of view.
e) Status of chat messages.Like other contemporary apps,IMO
maintains the status of chat messages including delivered,
read,and so on.Specific identifiers indicating the status of
different messages are fixed by IMO.
f) Voice and video calls. IMO provides the functionality of audio
and video calls which are encrypted. Records of these calls is
maintained in the memory and their location could be
important to any crime scene investigation involving IMO.
Results for Android and iOS forensics provided a good deal of
similarity.However,to give clarity on access to mobile storage in
each case,there are differences in file structures,and peculiar
format of artifacts from the extraction from mobile memory/stor-
age and thus Android and iOS will be outlined separately.
Device forensics on android
Experimental setup
We installed IMO on a rooted Samsung Galaxy 6.0 having an
Android version of 6.0.1. On a Ubuntu 16.04 terminal, the following
steps were taken to access the smart phone's file structure:
Run the command ”adb shell”.This was to run the Android
Debug Bridge (adb) tool in order to access the mobile memory.
Pressed ”Allow” on mobile against the prompt ”Allow access to
mobile data”.
User then entered to ”shell@zeroflte:/$ ”.
To gain root previligaes,we pressed ”su”.Root privileges were
shown as ”root@zeroflte:/#”.
Entering the command ”ls” will display all the files and folders
on the mobile in both user and system space.
To identifying the file structure of IMO app, we used a number of
controlled activities related to text,voice, and video chats,and
observed their corresponding traces within different storage re-
cords maintained by IMO.These were validated using the Helium
Backup (Chris,2014 [accessed 3-june-2017]) to retrieve.db files of
the IMO app. Finally,an Android backup extractor and db browser
for SQLite was used to analyze the contents of storage elements
against each activity.
Results and their analysis e android device
Following the steps of our work flow as shown in Fig. 1, the file
structure of IMO on Android is identified and shown in Fig.2.
The following section will throw some light on the files and
folders that were identified during device forensics ofIMO on
Android platform.
Main folders of IMO file structure.Upon installation of IMO on
Android,three main folders are created at fixed locations as:
com.imo.android.imoim-1 at location ”/data/app/”.
com.imo.android.imoim at location ”/data/data/”.
IMO at location ”/data/media/0/”. This is a location of SD card or
user accessible memory and which is normally visible through
USB connectivity on a PC,even without the root privileges.
The sub folders and files which are created within each of the
main folders are depicted in Fig.2. We now discuss the important
files,their locations and related artifacts stored by IMO with their
mapping to functionalities discussed in Section Analysis
methodology.
File structure ofcom.imo.android.imoim-1.Like other popular chat
and calling apps namely WhatsApp,Signal and Telegram,IMO
creates this folder in device memory at ”/data/app/”. Each of these
apps store their basic apk files along with other associated files in
app folder. IMO also creates a folder with its name IMO in app folder
and base.apk file is stored there.
File structure of com.imo.android.imoim.IMO stores most of its user
related artifacts in this folder. This location is critical because arti-
facts related to user credentials/activities are stored there.We
experimented number of user activities outlined in Section Analysis
methodology and observed their corresponding storage patterns by
IMO. Referring to Fig.2 again,the following explains the files and
folders at this location.
a) “cache” folder.IMO stores sent images and videos in a ”cache”
folder,whereas received images and videos are stored in user
space within IMO folder.This will be discussed in detailin a
following section. All these images and videos are stored in non-
encrypted form in the device memory.
b) “Databases” folder.From forensics point of view, Databases
folder is considered as one of the most important component of
file structure of IMO. Upon installation of IMO app, the following
two files are created in this folder before the account
configuration:
imofriends.db.
imofriends.db-journal.
c) After the user account is configured with IMO servers,the app
creates two additional files in Databases folder:
M.A.K.Sudozai et al./ Digital Investigation 25 (2018) 5e23 7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
accountdb.db.
accountdb.db-journal.
imofriends.db is an important folder as it contains wealth of
information related to the contacts,their chats,timestamps,tele-
phone numbers,emails,and a great deal of other information.
imofriends.db.This is the main database file in which IMO
maintains the records of users,and their associated activities in a
plaintext form.These records include number of tables containing
information of evidentiary value, such as phonebook entries, email
IDs, call logs,chat logs and chat messages,and so on.Different ta-
bles created by IMO in this location are shown in Fig. 3. We
observed plaintext data in these tables.The data is relates to ac-
tivities including chats and call logs as defined in Section Analysis
methodology.We now discuss the contents of these tables along
with their mapping to the user activities, as these can help in crime
scene reconstruction.
i) imo_phonebook.During the installation process,IMO ac-
cesses the mobile phonebook data according to the permis-
sions granted and saves them in the table ‘imo_phonebook’.
The structure of this table is shown in Fig.4. We observed
that IMO stores all the critical information related to the
contacts in plaintext form as shown in Fig. 5. We carried out
experiments on number of user accounts and verified that
against any unique mobile number of a user,IMO assigns a
unique identifier naming ”uid” and which is fixed.Any IMO
user can be tracked through this unique identifier and is
therefore can be considered to be one ofmost important
artifacts of IMO. Moreover. IMO also keeps the record of the
number of incoming and outgoing GSM calls and GSM
messages (SMS) in this table.The reasons for storing this
information about calls and SMS is unknown, but it can prove
helpful information with an investigation.
ii) A separate record of allusers and their mobile numbers is
stored in the table ‘phonebook_numbers’ as shown in Fig. 6.
iii) A similarly table ‘messages’ is used to store chat messages in
plain text as shown in Fig. 8. It is important to note that even
the email addresses and phone numbers of the IMO users are
stored in the column ‘imdata’ of this table in plaintext.
Through repeated experiments of chat messages for different
scenarios oftext, images,videos, and so on, we decoded
values of different fields of the Table as shown in Fig. 7. It can
be useful to forensics analysis of IMO during any
investigation.
iv) IMO also tracks timestamps of different activities which are
stored in the tables discussed above.Through forced activ-
ities of messaging on IMO,we verified our results of time
stamps using on-line conversion tool (”http://timestamp.
online/”).
v) Table ‘calls_only’stores call logs in plaintext as shown in
Fig.9.
vi) Table ‘stories’ is used to save artifacts related to Story sharing
feature of IMO as shown in Fig. 10. All these details are stored
in plaintext form.
vii) Contents accessible from IMO servers.One of the most critical
result of our study of IMO is on-line accessibility of uploaded
contents (images and videos) from its servers without any
authentication.A field of object_Id exists in different tables
within imofriends.db and which contains the direct link to a
specific uploaded content at IMO servers.By just entering
this object_Id in a browser as URL (https://imo.im/s/object/
object_Id/), content uploaded by IMO client is accessible
directly. During an investigation,retrieving the object_Id
from imofriends.db will enable an investigator to retrieve the
exact content shared by the IMO servers, even if the contents
are deleted from the mobile device. Fig. 11 shows that
different locations of object_Id in tables within imofriends.db.
object_Id of uploaded contents are either placed in the imdata
record or in the icon record for profile images in different
tables.
Fig. 2. File structure of IMO in Android.
M.A.K.Sudozai et al./ Digital Investigation 25 (2018) 5e238
accountdb.db-journal.
imofriends.db is an important folder as it contains wealth of
information related to the contacts,their chats,timestamps,tele-
phone numbers,emails,and a great deal of other information.
imofriends.db.This is the main database file in which IMO
maintains the records of users,and their associated activities in a
plaintext form.These records include number of tables containing
information of evidentiary value, such as phonebook entries, email
IDs, call logs,chat logs and chat messages,and so on.Different ta-
bles created by IMO in this location are shown in Fig. 3. We
observed plaintext data in these tables.The data is relates to ac-
tivities including chats and call logs as defined in Section Analysis
methodology.We now discuss the contents of these tables along
with their mapping to the user activities, as these can help in crime
scene reconstruction.
i) imo_phonebook.During the installation process,IMO ac-
cesses the mobile phonebook data according to the permis-
sions granted and saves them in the table ‘imo_phonebook’.
The structure of this table is shown in Fig.4. We observed
that IMO stores all the critical information related to the
contacts in plaintext form as shown in Fig. 5. We carried out
experiments on number of user accounts and verified that
against any unique mobile number of a user,IMO assigns a
unique identifier naming ”uid” and which is fixed.Any IMO
user can be tracked through this unique identifier and is
therefore can be considered to be one ofmost important
artifacts of IMO. Moreover. IMO also keeps the record of the
number of incoming and outgoing GSM calls and GSM
messages (SMS) in this table.The reasons for storing this
information about calls and SMS is unknown, but it can prove
helpful information with an investigation.
ii) A separate record of allusers and their mobile numbers is
stored in the table ‘phonebook_numbers’ as shown in Fig. 6.
iii) A similarly table ‘messages’ is used to store chat messages in
plain text as shown in Fig. 8. It is important to note that even
the email addresses and phone numbers of the IMO users are
stored in the column ‘imdata’ of this table in plaintext.
Through repeated experiments of chat messages for different
scenarios oftext, images,videos, and so on, we decoded
values of different fields of the Table as shown in Fig. 7. It can
be useful to forensics analysis of IMO during any
investigation.
iv) IMO also tracks timestamps of different activities which are
stored in the tables discussed above.Through forced activ-
ities of messaging on IMO,we verified our results of time
stamps using on-line conversion tool (”http://timestamp.
online/”).
v) Table ‘calls_only’stores call logs in plaintext as shown in
Fig.9.
vi) Table ‘stories’ is used to save artifacts related to Story sharing
feature of IMO as shown in Fig. 10. All these details are stored
in plaintext form.
vii) Contents accessible from IMO servers.One of the most critical
result of our study of IMO is on-line accessibility of uploaded
contents (images and videos) from its servers without any
authentication.A field of object_Id exists in different tables
within imofriends.db and which contains the direct link to a
specific uploaded content at IMO servers.By just entering
this object_Id in a browser as URL (https://imo.im/s/object/
object_Id/), content uploaded by IMO client is accessible
directly. During an investigation,retrieving the object_Id
from imofriends.db will enable an investigator to retrieve the
exact content shared by the IMO servers, even if the contents
are deleted from the mobile device. Fig. 11 shows that
different locations of object_Id in tables within imofriends.db.
object_Id of uploaded contents are either placed in the imdata
record or in the icon record for profile images in different
tables.
Fig. 2. File structure of IMO in Android.
M.A.K.Sudozai et al./ Digital Investigation 25 (2018) 5e238
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

d) Files folder. Files is another important folder in which number
of artifacts are sorted by IMO and which has forensics value.
The detailed view of contents within Files folder has been
marked in Fig.2. Through repeated experiments of user ac-
tivities and analysis of files within Files folder, the following
files are considered significant having important contents:
i) FasterIP.json. This is JSON file which contains the useable
TCP ports of IMO. FasterIP.json shows that IMO desig-
nates the ports of 5228, 5223 and 443 for client to server
connection establishment.Though device and network
forensics of IMO were carried out as independent studies,
results of one portion support the findings of the other.
Our network analysis part also highlights the IMO con-
nectivity patterns on useable ports of 5228 and 5223.If
these ports are blocked,IMO still communicates on 443
which is a standard port of HTTPS. This unique feature of
IMO connectivity pattern makes it a difficult choice for
app blocking solutions.We will explain this design flex-
ibility of IMO with more details in Section Network
forensics of IMO later.
ii) audio folder. IMO stores audio files, recordings and clips in
audio folder. By repeating number of forced activities on
IMO client,we verified that IMO always stored all audio
clips/files in plaintext form at this location.
Fig. 3. DB tables of IMO
Fig. 4. Fields of imo_phonebook table.
M.A.K.Sudozai et al./ Digital Investigation 25 (2018) 5e23 9
of artifacts are sorted by IMO and which has forensics value.
The detailed view of contents within Files folder has been
marked in Fig.2. Through repeated experiments of user ac-
tivities and analysis of files within Files folder, the following
files are considered significant having important contents:
i) FasterIP.json. This is JSON file which contains the useable
TCP ports of IMO. FasterIP.json shows that IMO desig-
nates the ports of 5228, 5223 and 443 for client to server
connection establishment.Though device and network
forensics of IMO were carried out as independent studies,
results of one portion support the findings of the other.
Our network analysis part also highlights the IMO con-
nectivity patterns on useable ports of 5228 and 5223.If
these ports are blocked,IMO still communicates on 443
which is a standard port of HTTPS. This unique feature of
IMO connectivity pattern makes it a difficult choice for
app blocking solutions.We will explain this design flex-
ibility of IMO with more details in Section Network
forensics of IMO later.
ii) audio folder. IMO stores audio files, recordings and clips in
audio folder. By repeating number of forced activities on
IMO client,we verified that IMO always stored all audio
clips/files in plaintext form at this location.
Fig. 3. DB tables of IMO
Fig. 4. Fields of imo_phonebook table.
M.A.K.Sudozai et al./ Digital Investigation 25 (2018) 5e23 9
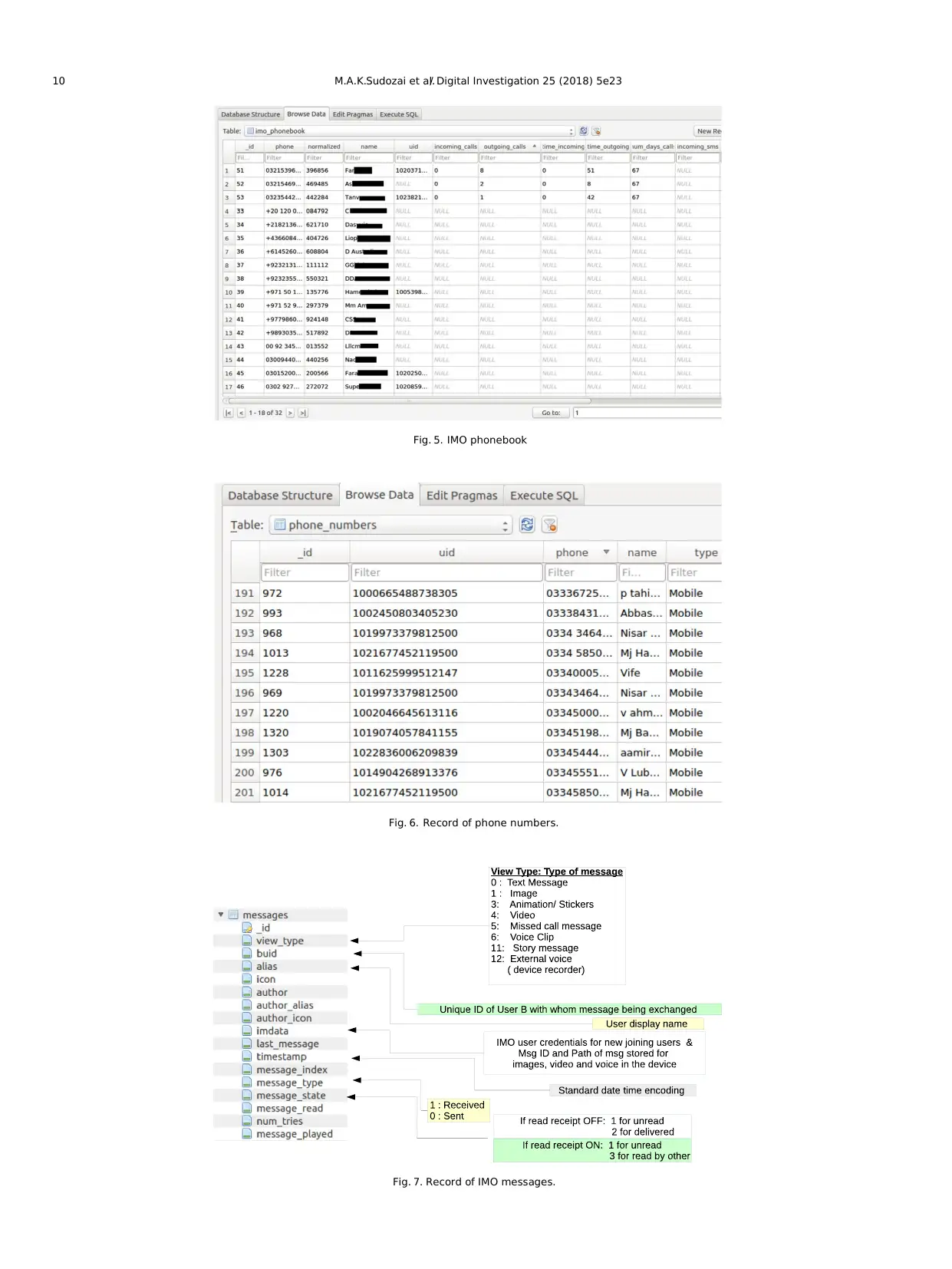
Fig. 5. IMO phonebook
Fig. 6. Record of phone numbers.
Fig. 7. Record of IMO messages.
M.A.K.Sudozai et al./ Digital Investigation 25 (2018) 5e2310
Fig. 6. Record of phone numbers.
Fig. 7. Record of IMO messages.
M.A.K.Sudozai et al./ Digital Investigation 25 (2018) 5e2310
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
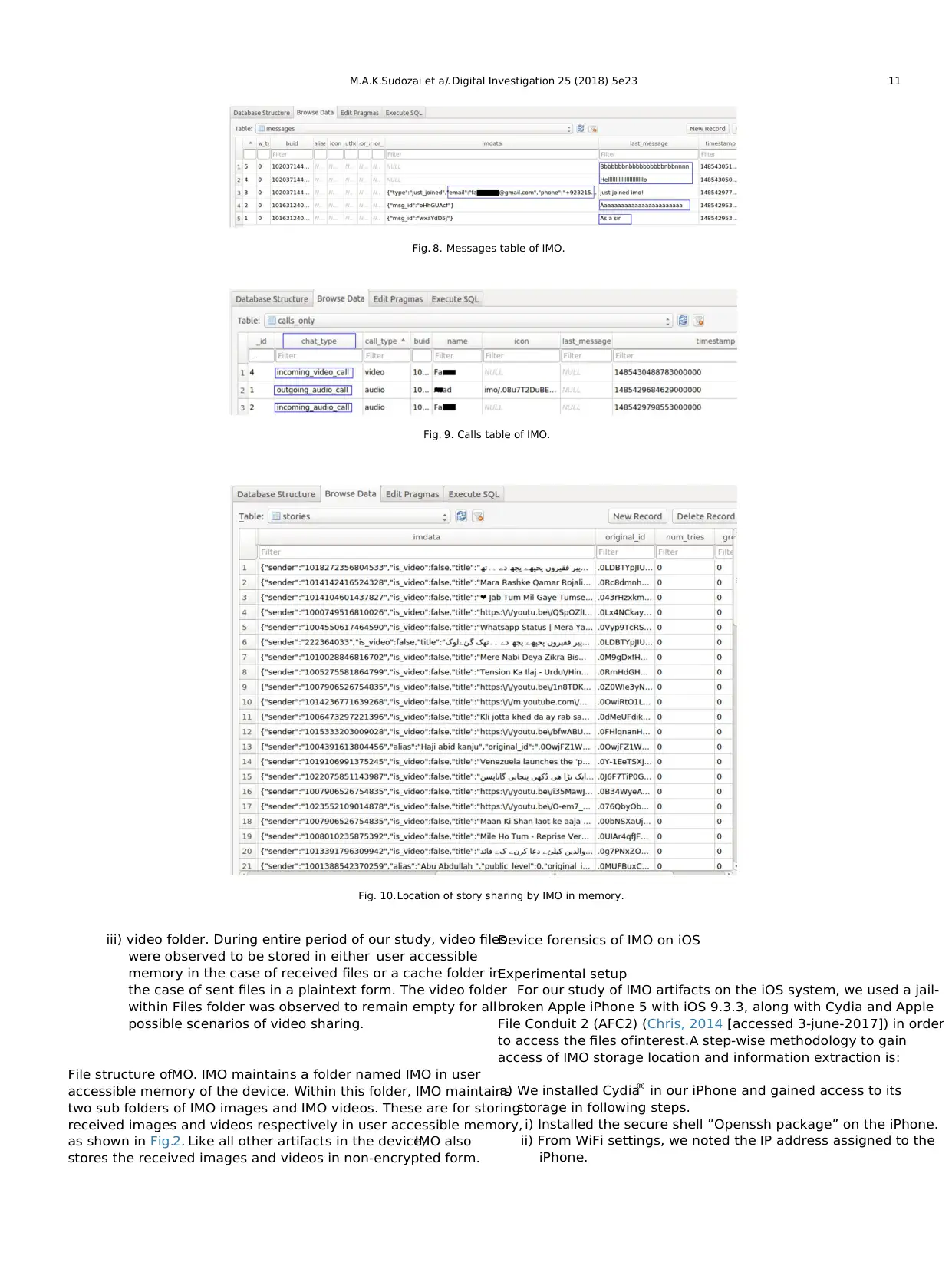
iii) video folder. During entire period of our study, video files
were observed to be stored in either user accessible
memory in the case of received files or a cache folder in
the case of sent files in a plaintext form. The video folder
within Files folder was observed to remain empty for all
possible scenarios of video sharing.
File structure ofIMO. IMO maintains a folder named IMO in user
accessible memory of the device. Within this folder, IMO maintains
two sub folders of IMO images and IMO videos. These are for storing
received images and videos respectively in user accessible memory,
as shown in Fig.2. Like all other artifacts in the device,IMO also
stores the received images and videos in non-encrypted form.
Device forensics of IMO on iOS
Experimental setup
For our study of IMO artifacts on the iOS system, we used a jail-
broken Apple iPhone 5 with iOS 9.3.3, along with Cydia and Apple
File Conduit 2 (AFC2) (Chris, 2014 [accessed 3-june-2017]) in order
to access the files ofinterest.A step-wise methodology to gain
access of IMO storage location and information extraction is:
a) We installed Cydia® in our iPhone and gained access to its
storage in following steps.
i) Installed the secure shell ”Openssh package” on the iPhone.
ii) From WiFi settings, we noted the IP address assigned to the
iPhone.
Fig. 8. Messages table of IMO.
Fig. 9. Calls table of IMO.
Fig. 10.Location of story sharing by IMO in memory.
M.A.K.Sudozai et al./ Digital Investigation 25 (2018) 5e23 11
were observed to be stored in either user accessible
memory in the case of received files or a cache folder in
the case of sent files in a plaintext form. The video folder
within Files folder was observed to remain empty for all
possible scenarios of video sharing.
File structure ofIMO. IMO maintains a folder named IMO in user
accessible memory of the device. Within this folder, IMO maintains
two sub folders of IMO images and IMO videos. These are for storing
received images and videos respectively in user accessible memory,
as shown in Fig.2. Like all other artifacts in the device,IMO also
stores the received images and videos in non-encrypted form.
Device forensics of IMO on iOS
Experimental setup
For our study of IMO artifacts on the iOS system, we used a jail-
broken Apple iPhone 5 with iOS 9.3.3, along with Cydia and Apple
File Conduit 2 (AFC2) (Chris, 2014 [accessed 3-june-2017]) in order
to access the files ofinterest.A step-wise methodology to gain
access of IMO storage location and information extraction is:
a) We installed Cydia® in our iPhone and gained access to its
storage in following steps.
i) Installed the secure shell ”Openssh package” on the iPhone.
ii) From WiFi settings, we noted the IP address assigned to the
iPhone.
Fig. 8. Messages table of IMO.
Fig. 9. Calls table of IMO.
Fig. 10.Location of story sharing by IMO in memory.
M.A.K.Sudozai et al./ Digital Investigation 25 (2018) 5e23 11
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

iii) Opened a terminal in our Ubuntu 16.04 host.The same can
be attained on a Microsoft Windows platform through the
use of PuTTY.(http://www.putty.org/).
iv) Run the command ”ssh root@[IP address of iPhone]” in ter-
minal to gain the secure access of iPhone.
v) Entered the Password ”alpine”.
vi) The connection to the iPhone was successfully established
after another prompt ofYes/No at the terminal.We were
then connected to the iPhone as iPhone: root #.
b) Similar to Section Analysis methodology, artifacts of IMO on iOS
are also identified and discussed in the following section.To
avoid any unnecessary repetition,we will explain only those
aspects in detail which are different in case of iOS. Moreover, the
similarities will also be briefly discussed.
Results and their analysis e iOS device
IMO app maintains different file structure in iOS as compared to
what we have seen in case ofAndroid. Analysis of iOS internal
memory revealed file structure of IMO app as shown in Fig. 12.
Salients aspects of device forensics for iOS are as under:
a) Similar to Android, IMO stores all the artifacts on iOS device
in plaintext form. It includes account information,friends
list, phonebook, chat messages, audio clips, video clips, story
sharing, and so on.
b) Main installer directory of IMO app on iOS is at the
path:=private=var=mobile=Applications=1391315FD105
40BF BCE3 5371F278E603.
c) Within Applications folder,iOS creates folder for different
installed apps with 32 character alpha-numeric names as
unique identifiers (UID) as shown in Fig. 12.
d) We observed that UID name of IMO app changed on each
installation.
e) IMO stores profile picture and shared pictures/images
at:1391315F D105 40BF BCE3 5371F278E603=
Library=Caches=default=com:hackemist:SDWebImageCache:
default.
f) Similar to Android,IMO stores images in WebP format.
g) Path for captured images was identified as:1391315F
D105 40BF BCE3 5371F278E603=Library=Caches=
libcache=com:hackemist:SDWebImageCache:libcache.
h) Videos captured from the iPhone,but not sent,were found
at:1391315F D105 40BF BCE3 5371F278E603=
tmp=imotmp.
i) Sent and received videos or audio messages were identified
at:1391315F D105 40BF BCE3 5371F278E603=
Library=Caches=videos.
j) IMO stores user account credentials,phonebook contacts,
chat messages,call records,and so on,in main database file
(IMODb2:sqlite) at path:1391315F D105 40BF BCE3
5371F278E603=Documents=.
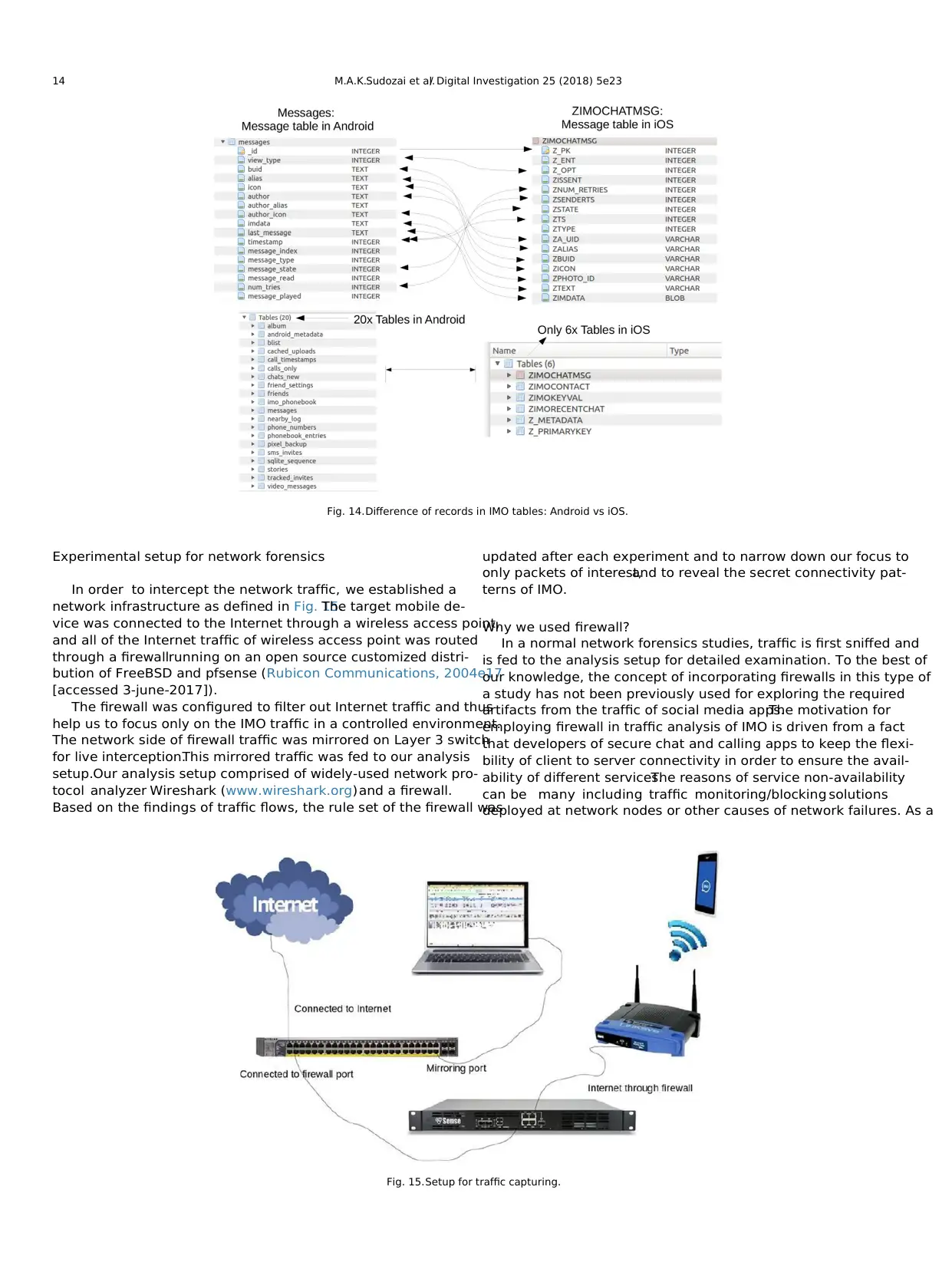
k) Similar to Android,IMO on iOS maintains records of chats
and contacts in number of tables as shown in Fig. 13.In the
case of iOS, a number of tables within IMODb2:sqlite are
reduced to six, as compared to Android version of IMO where
20 tables were used. We observed that the number of records
maintained within each table are also different for IMO on
iOS.
l) The naming convention for the records in iOS is also
different.It can be easily correlated to the set of activities
found in Android, as shown in Fig. 14. It is a representation of
a single case of message table for both Android and iOS
platforms.
m) Besides storing all the contents of IMO app in a specific folder
with UID number at path=private=var=mobile=Applications=,
IMO also creates a snap folder at path =home=snap.within
snap, another snap folder contains the same list of folders or
Fig. 11.Contents at IMO servers.
M.A.K.Sudozai et al./ Digital Investigation 25 (2018) 5e2312
be attained on a Microsoft Windows platform through the
use of PuTTY.(http://www.putty.org/).
iv) Run the command ”ssh root@[IP address of iPhone]” in ter-
minal to gain the secure access of iPhone.
v) Entered the Password ”alpine”.
vi) The connection to the iPhone was successfully established
after another prompt ofYes/No at the terminal.We were
then connected to the iPhone as iPhone: root #.
b) Similar to Section Analysis methodology, artifacts of IMO on iOS
are also identified and discussed in the following section.To
avoid any unnecessary repetition,we will explain only those
aspects in detail which are different in case of iOS. Moreover, the
similarities will also be briefly discussed.
Results and their analysis e iOS device
IMO app maintains different file structure in iOS as compared to
what we have seen in case ofAndroid. Analysis of iOS internal
memory revealed file structure of IMO app as shown in Fig. 12.
Salients aspects of device forensics for iOS are as under:
a) Similar to Android, IMO stores all the artifacts on iOS device
in plaintext form. It includes account information,friends
list, phonebook, chat messages, audio clips, video clips, story
sharing, and so on.
b) Main installer directory of IMO app on iOS is at the
path:=private=var=mobile=Applications=1391315FD105
40BF BCE3 5371F278E603.
c) Within Applications folder,iOS creates folder for different
installed apps with 32 character alpha-numeric names as
unique identifiers (UID) as shown in Fig. 12.
d) We observed that UID name of IMO app changed on each
installation.
e) IMO stores profile picture and shared pictures/images
at:1391315F D105 40BF BCE3 5371F278E603=
Library=Caches=default=com:hackemist:SDWebImageCache:
default.
f) Similar to Android,IMO stores images in WebP format.
g) Path for captured images was identified as:1391315F
D105 40BF BCE3 5371F278E603=Library=Caches=
libcache=com:hackemist:SDWebImageCache:libcache.
h) Videos captured from the iPhone,but not sent,were found
at:1391315F D105 40BF BCE3 5371F278E603=
tmp=imotmp.
i) Sent and received videos or audio messages were identified
at:1391315F D105 40BF BCE3 5371F278E603=
Library=Caches=videos.
j) IMO stores user account credentials,phonebook contacts,
chat messages,call records,and so on,in main database file
(IMODb2:sqlite) at path:1391315F D105 40BF BCE3
5371F278E603=Documents=.
k) Similar to Android,IMO on iOS maintains records of chats
and contacts in number of tables as shown in Fig. 13.In the
case of iOS, a number of tables within IMODb2:sqlite are
reduced to six, as compared to Android version of IMO where
20 tables were used. We observed that the number of records
maintained within each table are also different for IMO on
iOS.
l) The naming convention for the records in iOS is also
different.It can be easily correlated to the set of activities
found in Android, as shown in Fig. 14. It is a representation of
a single case of message table for both Android and iOS
platforms.
m) Besides storing all the contents of IMO app in a specific folder
with UID number at path=private=var=mobile=Applications=,
IMO also creates a snap folder at path =home=snap.within
snap, another snap folder contains the same list of folders or
Fig. 11.Contents at IMO servers.
M.A.K.Sudozai et al./ Digital Investigation 25 (2018) 5e2312
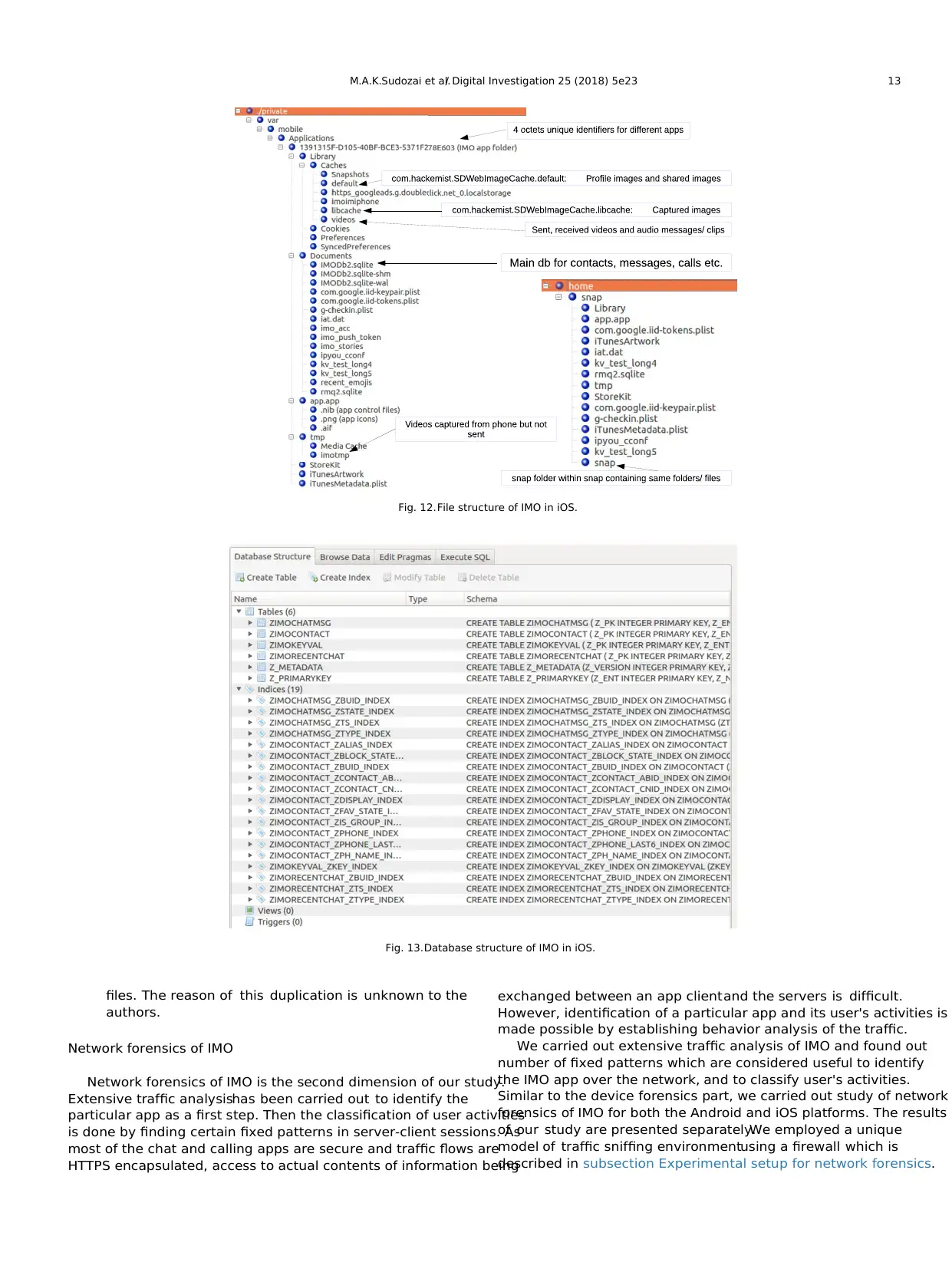
files. The reason of this duplication is unknown to the
authors.
Network forensics of IMO
Network forensics of IMO is the second dimension of our study.
Extensive traffic analysishas been carried out to identify the
particular app as a first step. Then the classification of user activities
is done by finding certain fixed patterns in server-client sessions. As
most of the chat and calling apps are secure and traffic flows are
HTTPS encapsulated, access to actual contents of information being
exchanged between an app clientand the servers is difficult.
However, identification of a particular app and its user's activities is
made possible by establishing behavior analysis of the traffic.
We carried out extensive traffic analysis of IMO and found out
number of fixed patterns which are considered useful to identify
the IMO app over the network, and to classify user's activities.
Similar to the device forensics part, we carried out study of network
forensics of IMO for both the Android and iOS platforms. The results
of our study are presented separately.We employed a unique
model of traffic sniffing environmentusing a firewall which is
described in subsection Experimental setup for network forensics.
Fig. 12.File structure of IMO in iOS.
Fig. 13.Database structure of IMO in iOS.
M.A.K.Sudozai et al./ Digital Investigation 25 (2018) 5e23 13
authors.
Network forensics of IMO
Network forensics of IMO is the second dimension of our study.
Extensive traffic analysishas been carried out to identify the
particular app as a first step. Then the classification of user activities
is done by finding certain fixed patterns in server-client sessions. As
most of the chat and calling apps are secure and traffic flows are
HTTPS encapsulated, access to actual contents of information being
exchanged between an app clientand the servers is difficult.
However, identification of a particular app and its user's activities is
made possible by establishing behavior analysis of the traffic.
We carried out extensive traffic analysis of IMO and found out
number of fixed patterns which are considered useful to identify
the IMO app over the network, and to classify user's activities.
Similar to the device forensics part, we carried out study of network
forensics of IMO for both the Android and iOS platforms. The results
of our study are presented separately.We employed a unique
model of traffic sniffing environmentusing a firewall which is
described in subsection Experimental setup for network forensics.
Fig. 12.File structure of IMO in iOS.
Fig. 13.Database structure of IMO in iOS.
M.A.K.Sudozai et al./ Digital Investigation 25 (2018) 5e23 13
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Experimental setup for network forensics
In order to intercept the network traffic, we established a
network infrastructure as defined in Fig. 15.The target mobile de-
vice was connected to the Internet through a wireless access point,
and all of the Internet traffic of wireless access point was routed
through a firewallrunning on an open source customized distri-
bution of FreeBSD and pfsense (Rubicon Communications, 2004e17
[accessed 3-june-2017]).
The firewall was configured to filter out Internet traffic and thus
help us to focus only on the IMO traffic in a controlled environment.
The network side of firewall traffic was mirrored on Layer 3 switch
for live interception.This mirrored traffic was fed to our analysis
setup.Our analysis setup comprised of widely-used network pro-
tocol analyzer Wireshark (www.wireshark.org)and a firewall.
Based on the findings of traffic flows, the rule set of the firewall was
updated after each experiment and to narrow down our focus to
only packets of interest,and to reveal the secret connectivity pat-
terns of IMO.
Why we used firewall?
In a normal network forensics studies, traffic is first sniffed and
is fed to the analysis setup for detailed examination. To the best of
our knowledge, the concept of incorporating firewalls in this type of
a study has not been previously used for exploring the required
artifacts from the traffic of social media apps.The motivation for
employing firewall in traffic analysis of IMO is driven from a fact
that developers of secure chat and calling apps to keep the flexi-
bility of client to server connectivity in order to ensure the avail-
ability of different services.The reasons of service non-availability
can be many including traffic monitoring/blocking solutions
deployed at network nodes or other causes of network failures. As a
Fig. 14.Difference of records in IMO tables: Android vs iOS.
Fig. 15.Setup for traffic capturing.
M.A.K.Sudozai et al./ Digital Investigation 25 (2018) 5e2314
In order to intercept the network traffic, we established a
network infrastructure as defined in Fig. 15.The target mobile de-
vice was connected to the Internet through a wireless access point,
and all of the Internet traffic of wireless access point was routed
through a firewallrunning on an open source customized distri-
bution of FreeBSD and pfsense (Rubicon Communications, 2004e17
[accessed 3-june-2017]).
The firewall was configured to filter out Internet traffic and thus
help us to focus only on the IMO traffic in a controlled environment.
The network side of firewall traffic was mirrored on Layer 3 switch
for live interception.This mirrored traffic was fed to our analysis
setup.Our analysis setup comprised of widely-used network pro-
tocol analyzer Wireshark (www.wireshark.org)and a firewall.
Based on the findings of traffic flows, the rule set of the firewall was
updated after each experiment and to narrow down our focus to
only packets of interest,and to reveal the secret connectivity pat-
terns of IMO.
Why we used firewall?
In a normal network forensics studies, traffic is first sniffed and
is fed to the analysis setup for detailed examination. To the best of
our knowledge, the concept of incorporating firewalls in this type of
a study has not been previously used for exploring the required
artifacts from the traffic of social media apps.The motivation for
employing firewall in traffic analysis of IMO is driven from a fact
that developers of secure chat and calling apps to keep the flexi-
bility of client to server connectivity in order to ensure the avail-
ability of different services.The reasons of service non-availability
can be many including traffic monitoring/blocking solutions
deployed at network nodes or other causes of network failures. As a
Fig. 14.Difference of records in IMO tables: Android vs iOS.
Fig. 15.Setup for traffic capturing.
M.A.K.Sudozai et al./ Digital Investigation 25 (2018) 5e2314
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

result, a cluster of servers are often deployed and which are
physically distributed to provide an alternate mechanismsfor
connectivity.This supports redundancy and anonymity.Server
ranges and an alternate set of TCP/UDP ports and series of other
parameters are often kept hidden to ensure availability of service.
Thus, the problem domain ofcarrying out study ofnetwork fo-
rensics of IMO is characterized by following fundamental facts:
The communication protocol between IMO client to its servers is
not known.
All sessions between IMO client and IMO servers are encrypted.
Alternate mechanisms of connectivity are not known.
With the traffic available over the network, we propose the use
of firewall in studying the encrypted traffic of IMO and reach from
unknown to maximum possible known. The process is progressive
in nature. Sniffing the traffic as shown in Fig. 15 with no restriction
on firewall and its analysis lead us to the first stage observations,
and which helped to define basic restrictions of TCP ports through
firewall. Against the blocking on firewall,IMO changed its con-
nectivity on other TCP ports.The firewall was then reconfigured
with updated rule sets and this process continued to identify all the
methods of connectivity of IMO client to its servers which are kept
secret in the design.This helped us to develop correct modelof
detection of IMO and various events of user activities.Though our
results are specific to IMO,the methodology ofconfiguration of
firewall according to the observed events of traffic analysis can be
employed to study any app/service that exchanges data over the
Internet.The role of firewall and type of different rule sets,which
we employed to identify the IMO connectivity patterns,will be
explained in more detail in Section Results and their analysis.
It is important to note that any social media app which is
designed to provide privacy has to follow certain set ofrules to
enable itselfto communicate over the TCP/IP stack.Even if the
contents are secured,communication to the servers and their re-
sponses often leaks sensitive information.We studied these leak-
ages for thousands of samples and important deductions are made
about the parties involved in communication, including the type of
information they are exchanging like text chats,voice messages,
video chats and file sharing.
Though the structure of IMO communication protocol and se-
curity architecture was unknown to us,we analyzed its traffic
dumps againstthe possible list of user activities (described in
Section Identification of IMO traffic). The known knowledge of OSI
and TCP/IP communication layerswas mapped to the filtered
traffic, and which was fed to the analysis setup to draw certain
signatures of encrypted traffic (described in Section Identification
of IMO traffic). To bring out important artifacts of IMO.We thus
used a combination of techniques such as port-based analysis,in-
spection of bytes exchanged between the client and server,and a
behavior analysis in a controlled network environment. The use of
firewall in this study helped us to identify alternate connectivity
mechanisms of IMO and which usually remains obscured in normal
traffic sniffing scenarios.
Results and their analysis
IMO supports encrypted traffic for chats,voice and video calls.
From these encrypted sessions,we were not able to reconstruct
them to retrieve any helpful information. However, we were able to
study important artifacts from extensive traffic analysis of IMO in
relation to the series of forced activities. The list of forced activities
is described in Section Identification of IMO traffic.
Although we have only studied IMO, the methodology in Section
Experimentalsetup for network forensics is generic and can be
used to study other related applications. During this study, we have
engineered the role of firewallin a network traffic sniffing envi-
ronment to clearly determine the unknown communication pro-
tocol associated with IMO. Traffic was analyzed for a series of
triggered events of messaging,voice and video calls,in order to
define consistent patterns through filtration.Based on these pat-
terns, different rule sets were configured on firewall to filter out the
specific traffic.This phenomenon not only helped us stop or filter
the targeted traffic,but also helped us to discover the network
connectivity patterns used by IMO.Our results indicate that this
flexibility could prove to be a problem area for law enforcement
agencies in blocking IMO in some countries of the world.
TCP ports
Like many other eXtensible Messaging and Presence Protocol
(XMPP) based chat applications (GitHub,2017 [accessed 3-june-
2017]),IMO uses the standard TCP ports of 5222 and 5223 (XMPP
over SSL).The use of firewall helped us to identify hidden design
flexibilities of IMO connectivity and which provides the reason as to
why IMO is hard to block.Table 1 shows a case scenario of using
firewall to enforce strict control on IMO traffic through TCP ports
only and progressive re-configuration of firewall after each obser-
vation of IMO client connectivity to its servers (see Table 2).
We also observed a good deal of IMO chat sessions using TCP on
port 5228.Once we blocked TCP connection on Port 5228 for IMO
client to its server through firewall, IMO established connections on
5222 and then on 5223.Once we updated the firewall rule sets to
block all these ports, IMO continued to exchange messages on TCP
port 443 (HTTPS). It is important to note that port 443 is used for all
HTTPS traffic and blocking 443 can have undesired consequences,
and is this is perhaps one of the hurdles in blocking IMO. We further
observed thatthe communication on the aforementioned ports
could be chat, voice/video, adding/removing a contact, or any other
messenger activity.Thus TCP ports of 5222,5223,5228 and 443
could be observed over the network for IMO sessions.
Server ranges and traffic behavior
IMO uses SSL/TLS to encrypt voice, video and chat conversations,
and where the client is designed to initiate connections with
number of servers depending upon a few unknown conditions. We
added these IP subnets in firewall rules and forced IMO client to
switch over to alternate connection options with its servers.In a
few cases, we observed that the IMO client established the
connection with two servers initially, and then communicated
through one of these servers, while maintaining the connection in
parallel with the other server. Fig. 16 clearly shows that two parallel
connectionsare established by IMO client with its servers at
192.12.31.89 and 108.177.15.188.Network forensics helped us to
discover the IMO connectivity patterns.For this we identified the
server ranges being used by IMO in our geographical region,and
progressively blocked the identified server ranges on the firewall
and observed that IMO was still able to communicate. Server ranges
of 64:233:0:0=16, 207:154:0:0=16, 74:125:0:0=16, 108:177:15:0=2
and 192:12:31:0=24 were observed for IMO connectivity.
Servers with IP range of 192:12:31:0=24 are only designated for
IMO publicly. Filtering this range through the firewallforces the
IMO client to switch over to Google's servers at 64:233:187:0=24 for
its services. This behavior of IMO was noted repeatedly for number
of call and chat events.In normal connectivity scenarios,once the
firewall was configured on an all pass rule set, the IMO client always
connected with one of the servers in the range of 192:12:31:0=24.
M.A.K.Sudozai et al./ Digital Investigation 25 (2018) 5e23 15
physically distributed to provide an alternate mechanismsfor
connectivity.This supports redundancy and anonymity.Server
ranges and an alternate set of TCP/UDP ports and series of other
parameters are often kept hidden to ensure availability of service.
Thus, the problem domain ofcarrying out study ofnetwork fo-
rensics of IMO is characterized by following fundamental facts:
The communication protocol between IMO client to its servers is
not known.
All sessions between IMO client and IMO servers are encrypted.
Alternate mechanisms of connectivity are not known.
With the traffic available over the network, we propose the use
of firewall in studying the encrypted traffic of IMO and reach from
unknown to maximum possible known. The process is progressive
in nature. Sniffing the traffic as shown in Fig. 15 with no restriction
on firewall and its analysis lead us to the first stage observations,
and which helped to define basic restrictions of TCP ports through
firewall. Against the blocking on firewall,IMO changed its con-
nectivity on other TCP ports.The firewall was then reconfigured
with updated rule sets and this process continued to identify all the
methods of connectivity of IMO client to its servers which are kept
secret in the design.This helped us to develop correct modelof
detection of IMO and various events of user activities.Though our
results are specific to IMO,the methodology ofconfiguration of
firewall according to the observed events of traffic analysis can be
employed to study any app/service that exchanges data over the
Internet.The role of firewall and type of different rule sets,which
we employed to identify the IMO connectivity patterns,will be
explained in more detail in Section Results and their analysis.
It is important to note that any social media app which is
designed to provide privacy has to follow certain set ofrules to
enable itselfto communicate over the TCP/IP stack.Even if the
contents are secured,communication to the servers and their re-
sponses often leaks sensitive information.We studied these leak-
ages for thousands of samples and important deductions are made
about the parties involved in communication, including the type of
information they are exchanging like text chats,voice messages,
video chats and file sharing.
Though the structure of IMO communication protocol and se-
curity architecture was unknown to us,we analyzed its traffic
dumps againstthe possible list of user activities (described in
Section Identification of IMO traffic). The known knowledge of OSI
and TCP/IP communication layerswas mapped to the filtered
traffic, and which was fed to the analysis setup to draw certain
signatures of encrypted traffic (described in Section Identification
of IMO traffic). To bring out important artifacts of IMO.We thus
used a combination of techniques such as port-based analysis,in-
spection of bytes exchanged between the client and server,and a
behavior analysis in a controlled network environment. The use of
firewall in this study helped us to identify alternate connectivity
mechanisms of IMO and which usually remains obscured in normal
traffic sniffing scenarios.
Results and their analysis
IMO supports encrypted traffic for chats,voice and video calls.
From these encrypted sessions,we were not able to reconstruct
them to retrieve any helpful information. However, we were able to
study important artifacts from extensive traffic analysis of IMO in
relation to the series of forced activities. The list of forced activities
is described in Section Identification of IMO traffic.
Although we have only studied IMO, the methodology in Section
Experimentalsetup for network forensics is generic and can be
used to study other related applications. During this study, we have
engineered the role of firewallin a network traffic sniffing envi-
ronment to clearly determine the unknown communication pro-
tocol associated with IMO. Traffic was analyzed for a series of
triggered events of messaging,voice and video calls,in order to
define consistent patterns through filtration.Based on these pat-
terns, different rule sets were configured on firewall to filter out the
specific traffic.This phenomenon not only helped us stop or filter
the targeted traffic,but also helped us to discover the network
connectivity patterns used by IMO.Our results indicate that this
flexibility could prove to be a problem area for law enforcement
agencies in blocking IMO in some countries of the world.
TCP ports
Like many other eXtensible Messaging and Presence Protocol
(XMPP) based chat applications (GitHub,2017 [accessed 3-june-
2017]),IMO uses the standard TCP ports of 5222 and 5223 (XMPP
over SSL).The use of firewall helped us to identify hidden design
flexibilities of IMO connectivity and which provides the reason as to
why IMO is hard to block.Table 1 shows a case scenario of using
firewall to enforce strict control on IMO traffic through TCP ports
only and progressive re-configuration of firewall after each obser-
vation of IMO client connectivity to its servers (see Table 2).
We also observed a good deal of IMO chat sessions using TCP on
port 5228.Once we blocked TCP connection on Port 5228 for IMO
client to its server through firewall, IMO established connections on
5222 and then on 5223.Once we updated the firewall rule sets to
block all these ports, IMO continued to exchange messages on TCP
port 443 (HTTPS). It is important to note that port 443 is used for all
HTTPS traffic and blocking 443 can have undesired consequences,
and is this is perhaps one of the hurdles in blocking IMO. We further
observed thatthe communication on the aforementioned ports
could be chat, voice/video, adding/removing a contact, or any other
messenger activity.Thus TCP ports of 5222,5223,5228 and 443
could be observed over the network for IMO sessions.
Server ranges and traffic behavior
IMO uses SSL/TLS to encrypt voice, video and chat conversations,
and where the client is designed to initiate connections with
number of servers depending upon a few unknown conditions. We
added these IP subnets in firewall rules and forced IMO client to
switch over to alternate connection options with its servers.In a
few cases, we observed that the IMO client established the
connection with two servers initially, and then communicated
through one of these servers, while maintaining the connection in
parallel with the other server. Fig. 16 clearly shows that two parallel
connectionsare established by IMO client with its servers at
192.12.31.89 and 108.177.15.188.Network forensics helped us to
discover the IMO connectivity patterns.For this we identified the
server ranges being used by IMO in our geographical region,and
progressively blocked the identified server ranges on the firewall
and observed that IMO was still able to communicate. Server ranges
of 64:233:0:0=16, 207:154:0:0=16, 74:125:0:0=16, 108:177:15:0=2
and 192:12:31:0=24 were observed for IMO connectivity.
Servers with IP range of 192:12:31:0=24 are only designated for
IMO publicly. Filtering this range through the firewallforces the
IMO client to switch over to Google's servers at 64:233:187:0=24 for
its services. This behavior of IMO was noted repeatedly for number
of call and chat events.In normal connectivity scenarios,once the
firewall was configured on an all pass rule set, the IMO client always
connected with one of the servers in the range of 192:12:31:0=24.
M.A.K.Sudozai et al./ Digital Investigation 25 (2018) 5e23 15
This shows that up to 255 servers are dedicated for IMO services,
but we observed that it actually doesn't always happen. Moreover,
any Google server hosting the IMO might be assigned to provide the
services to users in different conditions of connectivity.
From the observed behavior ofIMO client-server connectivity
with alternate connections, we can safely make following inferences:
a) The alternate connection is used to initially check the reliable
connectivity and then to balance the traffic load among the
servers.
b) This alternate connection acts as a backup for the commu-
nication because it provides the same services to the client as
any actual IMO server.
Table 1
Firewall rules for TCP ports used by IMO.
Step Protocol Source Port Dest Port Action Observation
I Any Any Any Any Server TCP port connections on 5228
II TCP 5228 Any Block TCP port connections on 5222
TCP Any 5228 Block
III TCP 5228,5222 Any Block TCP port connection on 5223
TCP Any 5228,5222 Block
IV TCP 5228,5222, 5223 Any Block TCP port connection on 443
UDP Any 5228,5222, 5223 Block
V TCP 5228,5222, 5223,443 Any Block TCP connection failed
TCP Any 5228,5222, 5223,443 Block
Table 2
Traffic characteristics of IMO on Android.
Event Description
Access to IMO messenger application As explained earlier
User A is typing Client
Beginning: packets with 160 bytes of payload from client to server
Incremental: 16 bytes depending on message length
Server
8 bytes of payload sent in acknowledgement of each packet sent from the target
User B is typing Server
Beginning: packets with 144 bytes of payload from Server to Target
Incremental: 16 bytes depending on message length
Client
64 bytes of payload sent in acknowledgement of each packet sent from the server
Call initiated from User A Client
Two consecutive packet having payload size of 272 bytes and 128 bytes respectively are sent to the server
Server
In response of these messages,the server acknowledges with 48 bytes of packets.
In less than a second, a series of packets are also sent by the server in which one of the packet size is greater than
1000 bytes and the others are short in length.
Call initiated from User B Server
Packet having payload size of 112 bytes is received from the server
Client
Target mobile acknowledges by sending a packet of payload size 64 bytes
Server
In less than a second, a series of packets are also sent by the server in which one of the packet size is greater than
1000 bytes and the others are short in length
Client
Two consecutive packet having payload size of 64 bytes and 176 bytes respectively are sent to the server
Voice/video call termination UDP stream flowing from the target IP stops
Fig. 16.Two TCP connections on port 5228.
M.A.K.Sudozai et al./ Digital Investigation 25 (2018) 5e2316
but we observed that it actually doesn't always happen. Moreover,
any Google server hosting the IMO might be assigned to provide the
services to users in different conditions of connectivity.
From the observed behavior ofIMO client-server connectivity
with alternate connections, we can safely make following inferences:
a) The alternate connection is used to initially check the reliable
connectivity and then to balance the traffic load among the
servers.
b) This alternate connection acts as a backup for the commu-
nication because it provides the same services to the client as
any actual IMO server.
Table 1
Firewall rules for TCP ports used by IMO.
Step Protocol Source Port Dest Port Action Observation
I Any Any Any Any Server TCP port connections on 5228
II TCP 5228 Any Block TCP port connections on 5222
TCP Any 5228 Block
III TCP 5228,5222 Any Block TCP port connection on 5223
TCP Any 5228,5222 Block
IV TCP 5228,5222, 5223 Any Block TCP port connection on 443
UDP Any 5228,5222, 5223 Block
V TCP 5228,5222, 5223,443 Any Block TCP connection failed
TCP Any 5228,5222, 5223,443 Block
Table 2
Traffic characteristics of IMO on Android.
Event Description
Access to IMO messenger application As explained earlier
User A is typing Client
Beginning: packets with 160 bytes of payload from client to server
Incremental: 16 bytes depending on message length
Server
8 bytes of payload sent in acknowledgement of each packet sent from the target
User B is typing Server
Beginning: packets with 144 bytes of payload from Server to Target
Incremental: 16 bytes depending on message length
Client
64 bytes of payload sent in acknowledgement of each packet sent from the server
Call initiated from User A Client
Two consecutive packet having payload size of 272 bytes and 128 bytes respectively are sent to the server
Server
In response of these messages,the server acknowledges with 48 bytes of packets.
In less than a second, a series of packets are also sent by the server in which one of the packet size is greater than
1000 bytes and the others are short in length.
Call initiated from User B Server
Packet having payload size of 112 bytes is received from the server
Client
Target mobile acknowledges by sending a packet of payload size 64 bytes
Server
In less than a second, a series of packets are also sent by the server in which one of the packet size is greater than
1000 bytes and the others are short in length
Client
Two consecutive packet having payload size of 64 bytes and 176 bytes respectively are sent to the server
Voice/video call termination UDP stream flowing from the target IP stops
Fig. 16.Two TCP connections on port 5228.
M.A.K.Sudozai et al./ Digital Investigation 25 (2018) 5e2316
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
