Foundation Networks Assignment 2 Solutions - Electrical Engineering
VerifiedAdded on 2022/10/02
|6
|1096
|348
Homework Assignment
AI Summary
This document provides comprehensive solutions to Foundation Networks Assignment 2. The solutions cover a range of topics including point-to-point links, ARQ strategies, throughput and link efficiency calculations, bit error rates, the p-persistence algorithm, CSMA/CD networks, frame length and transmission calculations, the 5-4-3 rule, IEEE 802.3 and other frame standards, DQDB bus operation, IP version 4 addressing (classes, hexadecimal conversion), and network management functions such as performance and fault management. The solutions are detailed, showing step-by-step calculations and explanations for each problem. The document is designed to aid students in understanding and solving networking problems, providing a valuable resource for their studies in electrical engineering and related fields. It includes calculations and explanations to help students learn and solve similar problems.
1 out of 6





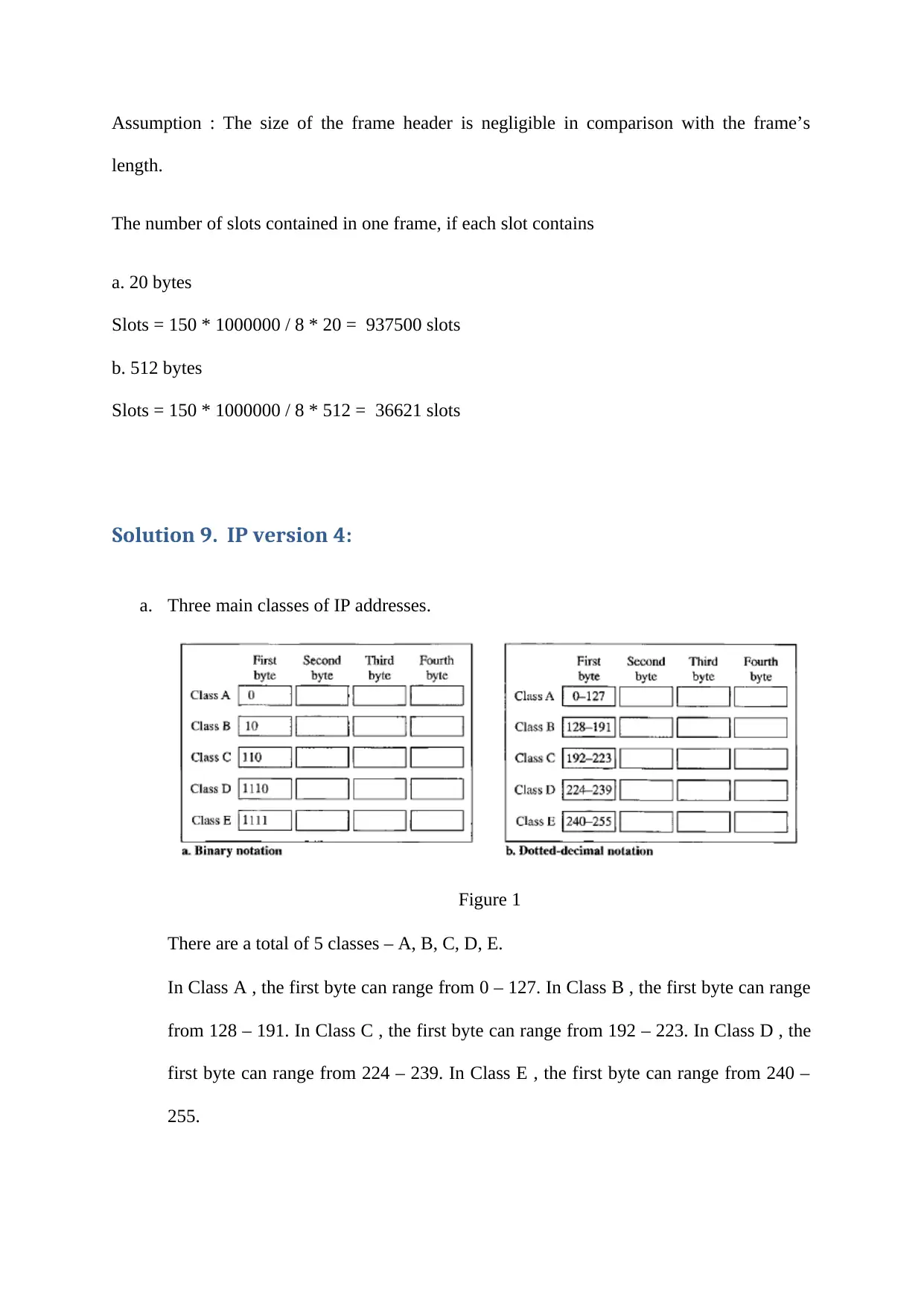
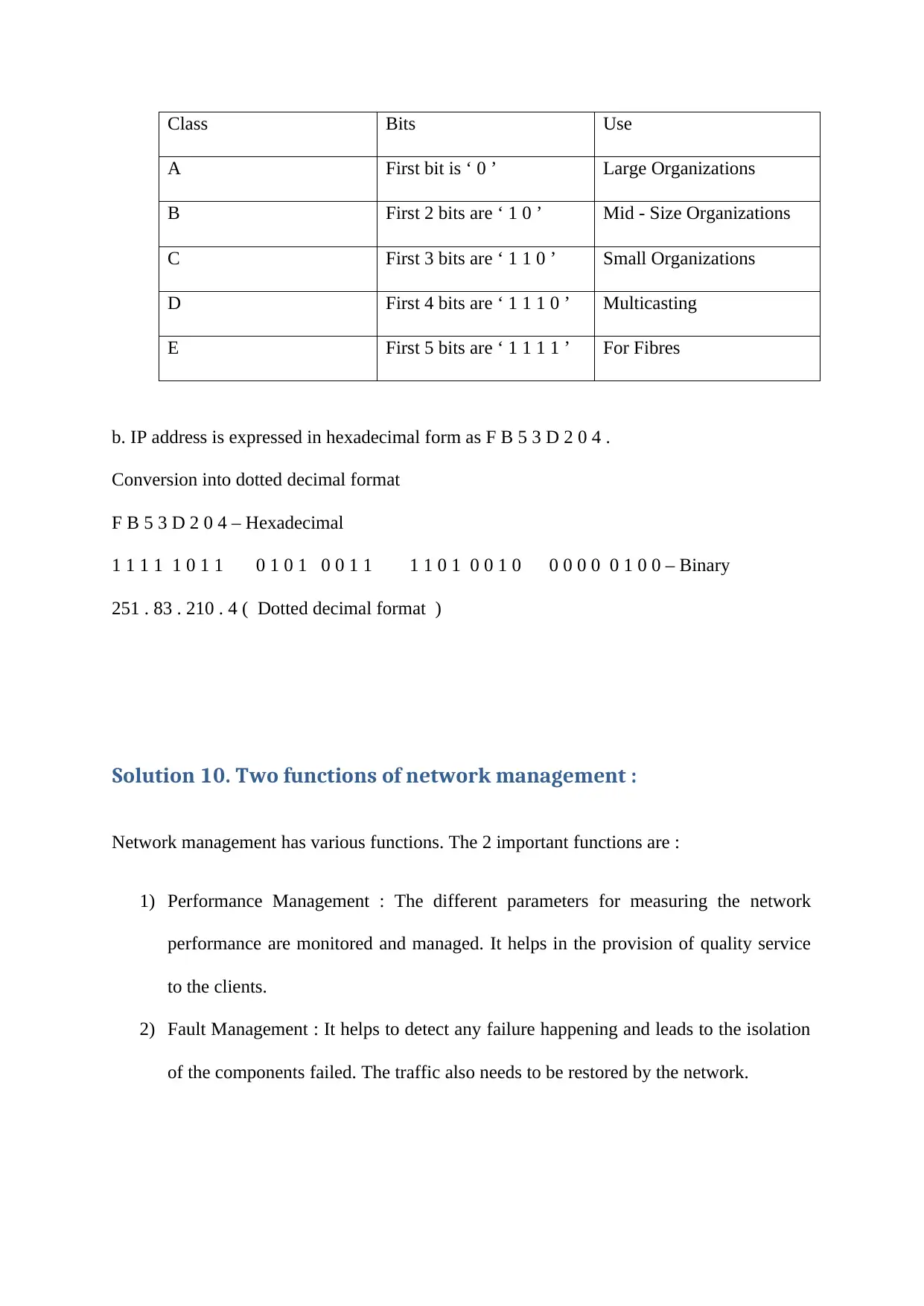




![[object Object]](/_next/static/media/star-bottom.7253800d.svg)