Foundations of Cyber Security: C Program, Data Handling & Encryption
VerifiedAdded on 2023/06/03
|23
|5334
|304
Homework Assignment
AI Summary
This assignment delves into the foundations of cyber security, covering topics such as creating and modifying a C program for encryption using the Vigenère cipher, explaining data deletion and recovery methods with secure data destruction techniques, evaluating encrypted e-mail solutions, and critically analyzing network traffic to identify potential vulnerabilities. The C program encrypts and decrypts messages using the Vigenère cipher. Data deletion and recovery methods are discussed, emphasizing the importance of secure data destruction policies, especially in organizational contexts. The current state of encrypted e-mail solutions is examined, including the challenges of PGP standards. Network traffic analysis is conducted to identify vulnerabilities based on captured data frames. The assignment concludes by emphasizing the importance of cyber security measures in protecting data and maintaining privacy, and students can find similar solved assignments and past papers on Desklib.

FOUNDATION OF CYBER SECURITY 1
Foundation of Cyber Security
VENKATA THOTA
Institutional Affiliation
Foundation of Cyber Security
VENKATA THOTA
Institutional Affiliation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

FOUNDATION OF CYBER SECURITY 2
Table of Contents
Question 1........................................................................................................................................4
Introduction..................................................................................................................................4
Vigenère Cipher C Program.........................................................................................................4
Program Output........................................................................................................................7
Encryption and Decryption Methods...........................................................................................8
Vigenère Cipher Robustness........................................................................................................8
Question 2........................................................................................................................................9
Data Deletion...............................................................................................................................9
Data Recovery..............................................................................................................................9
Securely Destroying Data..........................................................................................................10
Importance of Data Destruction.................................................................................................11
Question 3......................................................................................................................................12
Current State of Encrypted E-Mail Solutions............................................................................12
Extracting Information from Intercepted Emails.......................................................................13
Solution......................................................................................................................................14
Question 4......................................................................................................................................16
Start frame..................................................................................................................................16
Host Initiating Connection Mac Address...................................................................................16
Mac Address of Destination Host..............................................................................................17
Source and Destination IP Addresses........................................................................................18
Source and Destination Ports.....................................................................................................19
Conclusion.....................................................................................................................................20
Reference List................................................................................................................................22
Table of Contents
Question 1........................................................................................................................................4
Introduction..................................................................................................................................4
Vigenère Cipher C Program.........................................................................................................4
Program Output........................................................................................................................7
Encryption and Decryption Methods...........................................................................................8
Vigenère Cipher Robustness........................................................................................................8
Question 2........................................................................................................................................9
Data Deletion...............................................................................................................................9
Data Recovery..............................................................................................................................9
Securely Destroying Data..........................................................................................................10
Importance of Data Destruction.................................................................................................11
Question 3......................................................................................................................................12
Current State of Encrypted E-Mail Solutions............................................................................12
Extracting Information from Intercepted Emails.......................................................................13
Solution......................................................................................................................................14
Question 4......................................................................................................................................16
Start frame..................................................................................................................................16
Host Initiating Connection Mac Address...................................................................................16
Mac Address of Destination Host..............................................................................................17
Source and Destination IP Addresses........................................................................................18
Source and Destination Ports.....................................................................................................19
Conclusion.....................................................................................................................................20
Reference List................................................................................................................................22

FOUNDATION OF CYBER SECURITY 3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
FOUNDATION OF CYBER SECURITY 4
Question 1
Introduction
The program provides the users with the options to enter a message and either encrypt or decrypt
it. When the program executes, the user is prompted to enter the keyword to be used in the cipher
and the paraphrase. Vigenère cipher is a type of cryptography that employs the technique of
polyalphabetic substitution for encrypting a plain message (Dey, 2012). Caesar cipher approach
can better explain the Vigenère cipher because in Caesar cipher every character of the plain
message is reshuffled to a different place while in Vigenère cipher the characters are shifted
based on distinct shift values (MushtaqSherAli and Hassan-Sarhan, 2014).
Vigenère Cipher C Program
#include<stdio.h>
#include<string.h>
#include<ctype.h>
#include<stdlib.h>
main()
{
int i,j,k,numberstring[100],numberkey[100],numbercipher[100]; //declaring variables
char str[100],key[100];
printf("Enter a string\n");
gets(str);
//converting entered string to Capital letters
for(i=0,j=0;i<strlen(str);i++)
{
if(str[i]!=' ')
{
str[j]=toupper(str[i]);
Question 1
Introduction
The program provides the users with the options to enter a message and either encrypt or decrypt
it. When the program executes, the user is prompted to enter the keyword to be used in the cipher
and the paraphrase. Vigenère cipher is a type of cryptography that employs the technique of
polyalphabetic substitution for encrypting a plain message (Dey, 2012). Caesar cipher approach
can better explain the Vigenère cipher because in Caesar cipher every character of the plain
message is reshuffled to a different place while in Vigenère cipher the characters are shifted
based on distinct shift values (MushtaqSherAli and Hassan-Sarhan, 2014).
Vigenère Cipher C Program
#include<stdio.h>
#include<string.h>
#include<ctype.h>
#include<stdlib.h>
main()
{
int i,j,k,numberstring[100],numberkey[100],numbercipher[100]; //declaring variables
char str[100],key[100];
printf("Enter a string\n");
gets(str);
//converting entered string to Capital letters
for(i=0,j=0;i<strlen(str);i++)
{
if(str[i]!=' ')
{
str[j]=toupper(str[i]);
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

FOUNDATION OF CYBER SECURITY 5
j++;
}
}
str[j]='\0';
printf("Entered string is : %s \n",str);
//Storing string in terms of ascii
for(i=0;i<strlen(str);i++)
{
numberstring[i]=str[i]-'A';
}
printf("Enter a key\n");
gets(key);
//converting entered key to Capital letters
for(i=0,j=0;i<strlen(key);i++)
{
if(key[i]!=' ')
{
key[j]=toupper(key[i]);
j++;
}
}
key[j]='\0';
//Assigning key to the string
for(i=0;i<strlen(str);)
{
for(j=0;(j<strlen(key))&&(i<strlen(str));j++)
{
numberkey[i]=key[j]-'A';
j++;
}
}
str[j]='\0';
printf("Entered string is : %s \n",str);
//Storing string in terms of ascii
for(i=0;i<strlen(str);i++)
{
numberstring[i]=str[i]-'A';
}
printf("Enter a key\n");
gets(key);
//converting entered key to Capital letters
for(i=0,j=0;i<strlen(key);i++)
{
if(key[i]!=' ')
{
key[j]=toupper(key[i]);
j++;
}
}
key[j]='\0';
//Assigning key to the string
for(i=0;i<strlen(str);)
{
for(j=0;(j<strlen(key))&&(i<strlen(str));j++)
{
numberkey[i]=key[j]-'A';

FOUNDATION OF CYBER SECURITY 6
i++;
}
}
for(i=0;i<strlen(str);i++)
{
numbercipher[i]=numberstring[i]+numberkey[i];
}
for(i=0;i<strlen(str);i++)
{
if(numbercipher[i]>25)
{
numbercipher[i]=numbercipher[i]-26;
}
}
printf("Vigenere Cipher text is\n");
for(i=0;i<strlen(str);i++)
{
printf("%c",(numbercipher[i]+'A'));
}
printf("\n");
}
i++;
}
}
for(i=0;i<strlen(str);i++)
{
numbercipher[i]=numberstring[i]+numberkey[i];
}
for(i=0;i<strlen(str);i++)
{
if(numbercipher[i]>25)
{
numbercipher[i]=numbercipher[i]-26;
}
}
printf("Vigenere Cipher text is\n");
for(i=0;i<strlen(str);i++)
{
printf("%c",(numbercipher[i]+'A'));
}
printf("\n");
}
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
FOUNDATION OF CYBER SECURITY 7
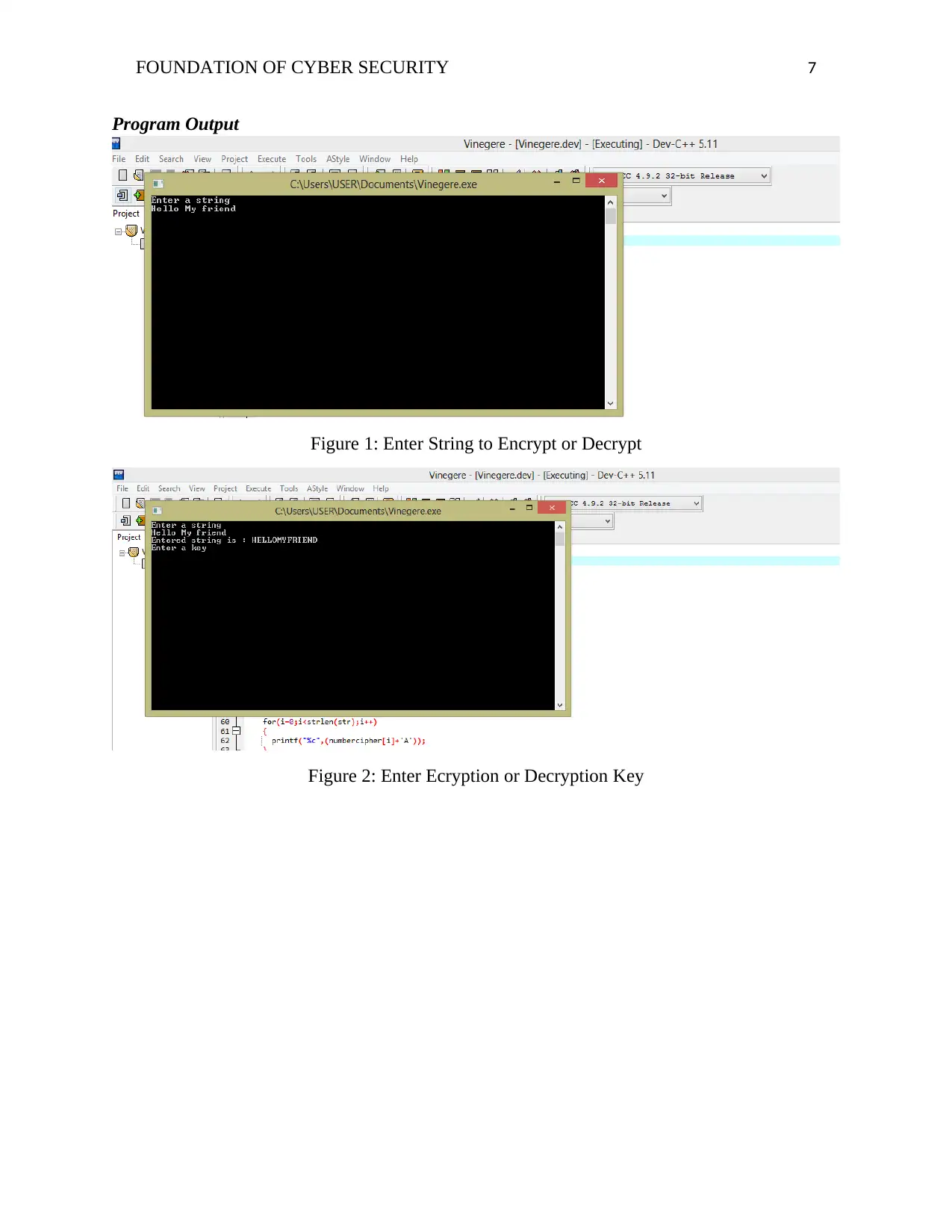
Program Output
Figure 1: Enter String to Encrypt or Decrypt
Figure 2: Enter Ecryption or Decryption Key
Program Output
Figure 1: Enter String to Encrypt or Decrypt
Figure 2: Enter Ecryption or Decryption Key
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
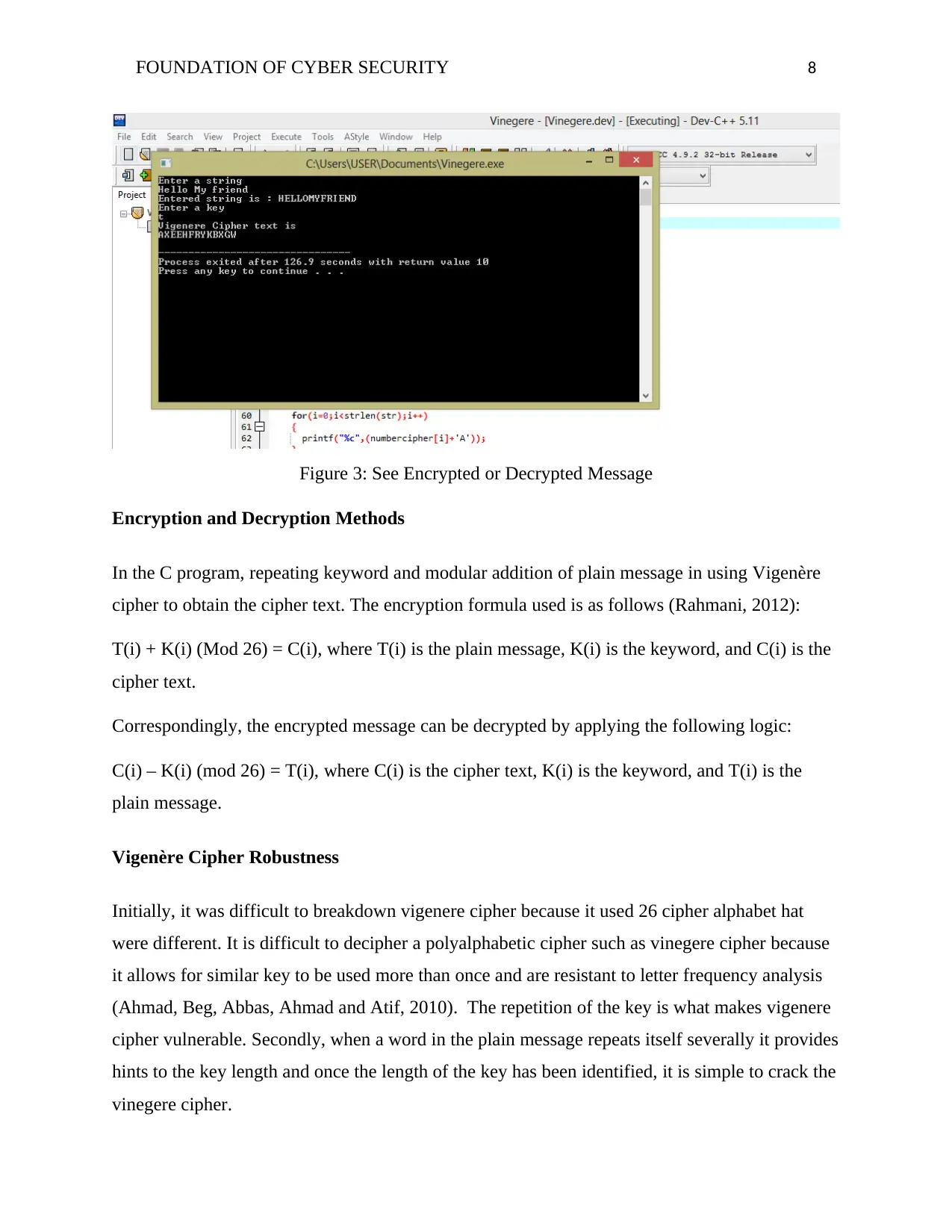
FOUNDATION OF CYBER SECURITY 8
Figure 3: See Encrypted or Decrypted Message
Encryption and Decryption Methods
In the C program, repeating keyword and modular addition of plain message in using Vigenère
cipher to obtain the cipher text. The encryption formula used is as follows (Rahmani, 2012):
T(i) + K(i) (Mod 26) = C(i), where T(i) is the plain message, K(i) is the keyword, and C(i) is the
cipher text.
Correspondingly, the encrypted message can be decrypted by applying the following logic:
C(i) – K(i) (mod 26) = T(i), where C(i) is the cipher text, K(i) is the keyword, and T(i) is the
plain message.
Vigenère Cipher Robustness
Initially, it was difficult to breakdown vigenere cipher because it used 26 cipher alphabet hat
were different. It is difficult to decipher a polyalphabetic cipher such as vinegere cipher because
it allows for similar key to be used more than once and are resistant to letter frequency analysis
(Ahmad, Beg, Abbas, Ahmad and Atif, 2010). The repetition of the key is what makes vigenere
cipher vulnerable. Secondly, when a word in the plain message repeats itself severally it provides
hints to the key length and once the length of the key has been identified, it is simple to crack the
vinegere cipher.
Figure 3: See Encrypted or Decrypted Message
Encryption and Decryption Methods
In the C program, repeating keyword and modular addition of plain message in using Vigenère
cipher to obtain the cipher text. The encryption formula used is as follows (Rahmani, 2012):
T(i) + K(i) (Mod 26) = C(i), where T(i) is the plain message, K(i) is the keyword, and C(i) is the
cipher text.
Correspondingly, the encrypted message can be decrypted by applying the following logic:
C(i) – K(i) (mod 26) = T(i), where C(i) is the cipher text, K(i) is the keyword, and T(i) is the
plain message.
Vigenère Cipher Robustness
Initially, it was difficult to breakdown vigenere cipher because it used 26 cipher alphabet hat
were different. It is difficult to decipher a polyalphabetic cipher such as vinegere cipher because
it allows for similar key to be used more than once and are resistant to letter frequency analysis
(Ahmad, Beg, Abbas, Ahmad and Atif, 2010). The repetition of the key is what makes vigenere
cipher vulnerable. Secondly, when a word in the plain message repeats itself severally it provides
hints to the key length and once the length of the key has been identified, it is simple to crack the
vinegere cipher.

FOUNDATION OF CYBER SECURITY 9
Recommendation
Vinegere cipher can be used in non-technical colleges and environments because it is difficult to
crack, has a complex encryption method, and the message cannot be decrypted without the key.
Question 2
Data Deletion
Deleting files or data using the delete function provided by the operating system does not
necessarily mean that the data has been completed destroyed or deleted because they can still be
recovered. As such, it is important to ensure that if the data has been deleted it should remain
deleted (Keele, 2009). Since Global Designs Limited has set the lifetime of data at one year, a lot
of data need to be destroyed to ensure that no other person can access such data after it has been
destroyed. Many of the employees at Global Design are non-technical and sometimes they
consider that by just pressing the delete button and emptying the recycle, they have completely
and permanently deleted the data. This is not the case because if another person was to get access
to the hard disk, he/she could still recover the data deleted from the recycle bin (Shu, Zhang, Li,
Li and Gu, 2017).
Data Recovery
There exist several ways that such data can be recovered:
Data that have been deleted and are currently in the recycle bin can be recovered by moving the
back using the restore option provided by the recycle bin (McCrea, Morgan, Brown and
Robinson, 2012).
If data was also deleted from recycle bin, it can be recovered using several recovery or undelete
utilities available. In reality, the “delete” option does not necessarily mean that the data has been
completely deleted because it does not overwrite the data files. As such, it is possible for data
recovery tools to reconstruct and rediscover it from the trail left by the deleted data (Salimath,
2016). An example of such recovery tool is Recuva.
Recommendation
Vinegere cipher can be used in non-technical colleges and environments because it is difficult to
crack, has a complex encryption method, and the message cannot be decrypted without the key.
Question 2
Data Deletion
Deleting files or data using the delete function provided by the operating system does not
necessarily mean that the data has been completed destroyed or deleted because they can still be
recovered. As such, it is important to ensure that if the data has been deleted it should remain
deleted (Keele, 2009). Since Global Designs Limited has set the lifetime of data at one year, a lot
of data need to be destroyed to ensure that no other person can access such data after it has been
destroyed. Many of the employees at Global Design are non-technical and sometimes they
consider that by just pressing the delete button and emptying the recycle, they have completely
and permanently deleted the data. This is not the case because if another person was to get access
to the hard disk, he/she could still recover the data deleted from the recycle bin (Shu, Zhang, Li,
Li and Gu, 2017).
Data Recovery
There exist several ways that such data can be recovered:
Data that have been deleted and are currently in the recycle bin can be recovered by moving the
back using the restore option provided by the recycle bin (McCrea, Morgan, Brown and
Robinson, 2012).
If data was also deleted from recycle bin, it can be recovered using several recovery or undelete
utilities available. In reality, the “delete” option does not necessarily mean that the data has been
completely deleted because it does not overwrite the data files. As such, it is possible for data
recovery tools to reconstruct and rediscover it from the trail left by the deleted data (Salimath,
2016). An example of such recovery tool is Recuva.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

FOUNDATION OF CYBER SECURITY 10
For the securely deleted data, it is nearly impossible to recover such data but there are some
special cases such is if the data is overwritten only once by the securely deleted data, expensive
and advanced data recovery approaches can be employed that uses previous data residual
magnetic fields to try restore it (Yang, 2013).
Securely Destroying Data
Destroying data is one of the critical phase in the life cycle of data when it useful period is over.
For Global Design limited, data is normally destroyed after 1 year. This step should never be
overlooked because it may have dire consequence. Every technique of destroying data is
dependent of the medium that the data is stored such as hard drives, magnetic media, tables,
DVDs/CDs, and flash drives (Omprakash, 2017).
The technique of securely destroying the data depends on the level of data sensitivity or paranoia
being destroyed. For Global Design LTD, most of the users are novice, that is, non-technical and
they consider the combination of permanent delete and recycle bin as sufficient to securely
destroy the data which is may not be the case. There are several methods to securely destroy data
including:
Dban is one tool than can be used to fully erase the data from the hard drive before handing over
the hard drive or computer that may have had very sensitive data. Secondly, secure delete utility
is another reasonable approach that can be used to periodically wipe free space on the hard disk
(Zoubek and Sack, 2017). By doing so the data that has not been overwritten by other data
cannot be recovered.
Shredding is another approach that can be used to securely destroy data by literally shredding the
hard drive that contains the information to be destroyed. This renders impossible to recover data
from hard drive debris.
Degaussing is an approach of destroying data securely through removing the magnetic glue in
the hard drive thus creating a breakdown and scrambling the bits and bytes making it difficult to
recover and restore. Bits and bytes can be destroyed at user level to facilitate reusability of the
degaussing device (Schembri, 2018). Users have often considered degaussing as a way of erasing
a drive but it is a mechanism of destroying data.
For the securely deleted data, it is nearly impossible to recover such data but there are some
special cases such is if the data is overwritten only once by the securely deleted data, expensive
and advanced data recovery approaches can be employed that uses previous data residual
magnetic fields to try restore it (Yang, 2013).
Securely Destroying Data
Destroying data is one of the critical phase in the life cycle of data when it useful period is over.
For Global Design limited, data is normally destroyed after 1 year. This step should never be
overlooked because it may have dire consequence. Every technique of destroying data is
dependent of the medium that the data is stored such as hard drives, magnetic media, tables,
DVDs/CDs, and flash drives (Omprakash, 2017).
The technique of securely destroying the data depends on the level of data sensitivity or paranoia
being destroyed. For Global Design LTD, most of the users are novice, that is, non-technical and
they consider the combination of permanent delete and recycle bin as sufficient to securely
destroy the data which is may not be the case. There are several methods to securely destroy data
including:
Dban is one tool than can be used to fully erase the data from the hard drive before handing over
the hard drive or computer that may have had very sensitive data. Secondly, secure delete utility
is another reasonable approach that can be used to periodically wipe free space on the hard disk
(Zoubek and Sack, 2017). By doing so the data that has not been overwritten by other data
cannot be recovered.
Shredding is another approach that can be used to securely destroy data by literally shredding the
hard drive that contains the information to be destroyed. This renders impossible to recover data
from hard drive debris.
Degaussing is an approach of destroying data securely through removing the magnetic glue in
the hard drive thus creating a breakdown and scrambling the bits and bytes making it difficult to
recover and restore. Bits and bytes can be destroyed at user level to facilitate reusability of the
degaussing device (Schembri, 2018). Users have often considered degaussing as a way of erasing
a drive but it is a mechanism of destroying data.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

FOUNDATION OF CYBER SECURITY 11
Smelting is a data destruction technique where users have put in efforts to securely destroy the
data by wiping the magnetic field of the hard drive or physically destroying it. The hard drive
will remain in the same physical state but without the magnetic field no data can be recovered.
Smelting involve changing the state of the hard drive from solid to liquid state. This is an
extreme approach but it is an effective one when it involves extremely confidential and sensitive
data. Smelting involves subjecting high temperatures to the hard disk magnetic fields in order to
destroy the magnetic fields that were holding the data.
Encryption is an approach that is destructive in nature and involves encrypting the data from the
beginning to protect it from prying eyes during destruction or deletion. The decryption key is
stored away from the storage media, however, compared to the other destruction techniques; it is
not 100% because it still gives sophisticated and skilled data recovery scientists a chance to
recover data using advanced tools, but the attacker will need physical access to the operating
system of the computer.
Importance of Data Destruction
Global Designs LTD should implement a data destruction policy when disposing off data storage
media, old computers, or other computing devices that contains company’s data. It is not
effective to simply employ the use of data deletion functions provided by the operating system
because they still give options for the attackers preying on the company’s data a chance to
recover it. Having data destruction policies greatly minimizes the chances of breaching
confidentiality and privacy. In case of data breaches, the company may be liable making
investment on data destruction techniques worth. The company can implement data destruction
policies by overwriting or destroying all media and devices that the company no longer uses
(Sagar, 2016). It is the responsibility of the Global Designs to ensure that all the employees have
undergone training and have been educated on data destruction policies of the company. The
company should also ensure that the data destruction policy is in compliance with the state,
industry, and federal laws, standards, and regulation.
Throwing the storage media that contains confidential data poses immense security risks to the
partners doing business with the company and the company itself. It is recommended that such
media be shredded by NAID certified and licensed data destruction company. Shredding is the
Smelting is a data destruction technique where users have put in efforts to securely destroy the
data by wiping the magnetic field of the hard drive or physically destroying it. The hard drive
will remain in the same physical state but without the magnetic field no data can be recovered.
Smelting involve changing the state of the hard drive from solid to liquid state. This is an
extreme approach but it is an effective one when it involves extremely confidential and sensitive
data. Smelting involves subjecting high temperatures to the hard disk magnetic fields in order to
destroy the magnetic fields that were holding the data.
Encryption is an approach that is destructive in nature and involves encrypting the data from the
beginning to protect it from prying eyes during destruction or deletion. The decryption key is
stored away from the storage media, however, compared to the other destruction techniques; it is
not 100% because it still gives sophisticated and skilled data recovery scientists a chance to
recover data using advanced tools, but the attacker will need physical access to the operating
system of the computer.
Importance of Data Destruction
Global Designs LTD should implement a data destruction policy when disposing off data storage
media, old computers, or other computing devices that contains company’s data. It is not
effective to simply employ the use of data deletion functions provided by the operating system
because they still give options for the attackers preying on the company’s data a chance to
recover it. Having data destruction policies greatly minimizes the chances of breaching
confidentiality and privacy. In case of data breaches, the company may be liable making
investment on data destruction techniques worth. The company can implement data destruction
policies by overwriting or destroying all media and devices that the company no longer uses
(Sagar, 2016). It is the responsibility of the Global Designs to ensure that all the employees have
undergone training and have been educated on data destruction policies of the company. The
company should also ensure that the data destruction policy is in compliance with the state,
industry, and federal laws, standards, and regulation.
Throwing the storage media that contains confidential data poses immense security risks to the
partners doing business with the company and the company itself. It is recommended that such
media be shredded by NAID certified and licensed data destruction company. Shredding is the

FOUNDATION OF CYBER SECURITY 12
most effective data destruction technique because it leaves no trails that attackers can use to
recover data. Shredding ensure that the company adheres to ethical and legal responsibilities in
regard to protecting privacy. Additionally, it is important for the company to have several data
backups just in case data that was not supposed to be destroyed can be recovered.
Classified equipment refers to any media or computer device that is regarded sensitive because
of the data stored on it. They include mobile devices, computers, hard drives, tablets, backup
tapes, and flash drives. It is necessary to dispose the equipment properly to ensure security of the
company along with clients’ data. Legal and ethical responsibilities apply when it comes to
disposal and destruction of classified equipment.
Question 3
Current State of Encrypted E-Mail Solutions
For several decades, e-mail communication has been regarded as the most secure means of
communication but is employs security measure like that of sending post card in the email. Email
companies have made lots of progress in ensuring safety of the mail through encryption while
sending an email (Calinawan, 2015). Many people would want to keep private, personal, and
sensitive information, file and conversations secret indefinitely. Emails are scanned for
advertising if you are using free email service.
It is important for Data Storage Solutions to know that many email providers are using
encryption to secure email communication using the PGP standard. But this standard has been
faced with numerous challenges rendering it undependable. It relies on the key security and in
case the key is compromised the all the previous mails can be decrypted. This standard lacks
forward secrecy. It is quite a hassle to manage the keys and thus, the company needs to take extra
care of their private key. It is essential to store the keys on devices such as YubiKey but
configuring such a device to handle PGP is quite difficult. Storing the on the local machine or in
the cloud makes it more vulnerable. The mail server spam cannot parse encrypted email to apply
server-side search or intelligent filtering.
This make it difficult for Data Storage Solution to adopt PGP standard because the non-technical
users will lose the needed properties to manage mailbox. One approach that mail providers often
most effective data destruction technique because it leaves no trails that attackers can use to
recover data. Shredding ensure that the company adheres to ethical and legal responsibilities in
regard to protecting privacy. Additionally, it is important for the company to have several data
backups just in case data that was not supposed to be destroyed can be recovered.
Classified equipment refers to any media or computer device that is regarded sensitive because
of the data stored on it. They include mobile devices, computers, hard drives, tablets, backup
tapes, and flash drives. It is necessary to dispose the equipment properly to ensure security of the
company along with clients’ data. Legal and ethical responsibilities apply when it comes to
disposal and destruction of classified equipment.
Question 3
Current State of Encrypted E-Mail Solutions
For several decades, e-mail communication has been regarded as the most secure means of
communication but is employs security measure like that of sending post card in the email. Email
companies have made lots of progress in ensuring safety of the mail through encryption while
sending an email (Calinawan, 2015). Many people would want to keep private, personal, and
sensitive information, file and conversations secret indefinitely. Emails are scanned for
advertising if you are using free email service.
It is important for Data Storage Solutions to know that many email providers are using
encryption to secure email communication using the PGP standard. But this standard has been
faced with numerous challenges rendering it undependable. It relies on the key security and in
case the key is compromised the all the previous mails can be decrypted. This standard lacks
forward secrecy. It is quite a hassle to manage the keys and thus, the company needs to take extra
care of their private key. It is essential to store the keys on devices such as YubiKey but
configuring such a device to handle PGP is quite difficult. Storing the on the local machine or in
the cloud makes it more vulnerable. The mail server spam cannot parse encrypted email to apply
server-side search or intelligent filtering.
This make it difficult for Data Storage Solution to adopt PGP standard because the non-technical
users will lose the needed properties to manage mailbox. One approach that mail providers often
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 23
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





