COIT20263 Report: Information Security Management of FuturePlus
VerifiedAdded on 2022/09/14
|13
|3239
|19
Report
AI Summary
This report analyzes the information security management of FuturePlus, an Australian charitable organization that provides free education to underprivileged students. The report focuses on developing a comprehensive 'Privacy and Security of Donor Information Policy' to protect the sensitive data of its contributors. It covers key aspects such as the importance of a donor privacy policy, strategies to prevent data breaches, and guidelines for ensuring donor data safety. The discussion includes recommendations for using updated software, secure connections, encrypted databases, strong passwords, experienced employees, 24/7 monitoring, and proper working maintenance. The report emphasizes the need for a robust security infrastructure to maintain social respect, build trust, and ensure the long-term sustainability of FuturePlus by supporting its mission of providing education to backward economic students. The report is structured with an executive summary, table of contents, introduction, detailed discussion of guidelines, conclusion, and references, adhering to Harvard citation style.

Running head: INFORMATION SECURITY MANAGEMENT OF FUTUREPLUS
INFORMATION SECURITY MANAGEMENT OF FUTUREPLUS
Name of the Student:
Name of the University:
Author Note:
INFORMATION SECURITY MANAGEMENT OF FUTUREPLUS
Name of the Student:
Name of the University:
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
INFORMATION SECURITY MANAGEMENT OF FUTUREPLUS
Executive Summary
Future plus is the Australian charitable organization. They started the current educational project
for backward economic student. They provide education with a free of cost. Many Australian
people contribute some donations to this organization. The Sydney based organization try to
secure their donor privacy data. So for a reason, if they should implement modern structures of
database and also recruit some professional technician, then they create an extraordinary impact
on Australian society. Their network structure is also very much enhancing because they use the
fifth-generation network. In this organization recruit, two types of employee one are full time
another is part-time. Full-time employee operates and manages all official matters with the help
of a part-time employee .This company is enhancing day by day, and that is the reason they store
a massive number of data and necessary information of their clients. In this paper, the writer
discusses how future plus creates a good security structure for their contributor. Data storage
policy and privacy strategy are very much crucial for the future plus to maintain social respect.
INFORMATION SECURITY MANAGEMENT OF FUTUREPLUS
Executive Summary
Future plus is the Australian charitable organization. They started the current educational project
for backward economic student. They provide education with a free of cost. Many Australian
people contribute some donations to this organization. The Sydney based organization try to
secure their donor privacy data. So for a reason, if they should implement modern structures of
database and also recruit some professional technician, then they create an extraordinary impact
on Australian society. Their network structure is also very much enhancing because they use the
fifth-generation network. In this organization recruit, two types of employee one are full time
another is part-time. Full-time employee operates and manages all official matters with the help
of a part-time employee .This company is enhancing day by day, and that is the reason they store
a massive number of data and necessary information of their clients. In this paper, the writer
discusses how future plus creates a good security structure for their contributor. Data storage
policy and privacy strategy are very much crucial for the future plus to maintain social respect.

2
INFORMATION SECURITY MANAGEMENT OF FUTUREPLUS
Table of Contents
Introduction......................................................................................................................................3
Discussion:-.....................................................................................................................................3
The basic idea of Donor Privacy policy:-....................................................................................3
To prevent the Dangerous problem:-...........................................................................................4
Future Plus Donor Safety Guidelines:-........................................................................................4
Contributor data safety technique:-.............................................................................................5
Recognize the confidential value:-..........................................................................................5
Use updated Software:-............................................................................................................6
Use protected connection:-......................................................................................................6
Create an Encrypted Database for Data storage:-....................................................................6
Strong Password:-....................................................................................................................7
Experience employee:-............................................................................................................7
24*7 monitoring:-....................................................................................................................8
Proper working maintenance:-.................................................................................................8
Unique privacy facility for contributor:-.....................................................................................9
Conclusion:-...................................................................................................................................10
References:-...................................................................................................................................11
INFORMATION SECURITY MANAGEMENT OF FUTUREPLUS
Table of Contents
Introduction......................................................................................................................................3
Discussion:-.....................................................................................................................................3
The basic idea of Donor Privacy policy:-....................................................................................3
To prevent the Dangerous problem:-...........................................................................................4
Future Plus Donor Safety Guidelines:-........................................................................................4
Contributor data safety technique:-.............................................................................................5
Recognize the confidential value:-..........................................................................................5
Use updated Software:-............................................................................................................6
Use protected connection:-......................................................................................................6
Create an Encrypted Database for Data storage:-....................................................................6
Strong Password:-....................................................................................................................7
Experience employee:-............................................................................................................7
24*7 monitoring:-....................................................................................................................8
Proper working maintenance:-.................................................................................................8
Unique privacy facility for contributor:-.....................................................................................9
Conclusion:-...................................................................................................................................10
References:-...................................................................................................................................11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
INFORMATION SECURITY MANAGEMENT OF FUTUREPLUS
Introduction:-
Future plus is the recently inaugurated Australian charity association. The work purpose
of this organization is mainly helping Australian students. The backward economic student who
are meritorious this company try to develops their future and provide them with an education.
This organization started some modern technique for giving the knowledge of these students like
the tutorial, early intervention (Hess 2015). Many famous public figures and familiar Australian
people donate some money for this charity. This organization organized some charitable events
which are directly telecasted by Australian national media. This organization also run special
fund-collecting events, and it telecast on social media, television and websites. The head office
of this organization in Sydney. Their network structure is also very much enhancing because
they use the fifth-generation network. In this organization recruit, two types of employee one are
full time another is part-time. Full-time employee operates and manages all official matters with
the help of a part-time employee (Bredenoord 2015). This company is enhancing day by day, and
that is the reason they store a massive number of data and necessary information of their clients.
If the internet is not secure, then this organization faced a big problem. So the main target of this
project is to implement a new service design, which is ethical and reliable.
Discussion:-
The basic idea of Donor Privacy policy:-
AFP mentions the acceptance of a confidentiality strategy for any association that collects
individual data, including names, statements, addresses and credit card information from
contributors at superior proceedings. It is an official, inscribed declaration explanation of how
INFORMATION SECURITY MANAGEMENT OF FUTUREPLUS
Introduction:-
Future plus is the recently inaugurated Australian charity association. The work purpose
of this organization is mainly helping Australian students. The backward economic student who
are meritorious this company try to develops their future and provide them with an education.
This organization started some modern technique for giving the knowledge of these students like
the tutorial, early intervention (Hess 2015). Many famous public figures and familiar Australian
people donate some money for this charity. This organization organized some charitable events
which are directly telecasted by Australian national media. This organization also run special
fund-collecting events, and it telecast on social media, television and websites. The head office
of this organization in Sydney. Their network structure is also very much enhancing because
they use the fifth-generation network. In this organization recruit, two types of employee one are
full time another is part-time. Full-time employee operates and manages all official matters with
the help of a part-time employee (Bredenoord 2015). This company is enhancing day by day, and
that is the reason they store a massive number of data and necessary information of their clients.
If the internet is not secure, then this organization faced a big problem. So the main target of this
project is to implement a new service design, which is ethical and reliable.
Discussion:-
The basic idea of Donor Privacy policy:-
AFP mentions the acceptance of a confidentiality strategy for any association that collects
individual data, including names, statements, addresses and credit card information from
contributors at superior proceedings. It is an official, inscribed declaration explanation of how
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
INFORMATION SECURITY MANAGEMENT OF FUTUREPLUS
organization use and shield contributor’s private information. This strategy determines to
provoke faith and highlight that the association will not share or sell private information without
authorization (Costa-Cabral and Lynsky 2017). Having a donor confidentiality strategy can
permit the non-profit to connect to their donors the rank that they place on defensive their
contributor’s information. Some Watchdog agencies and evaluations collections check whether
administrations have a contributor privacy plan. For example, Charity Guide takes this influence
into account for its answerability and transparency tally.
To prevent the Dangerous problem:-
It is crucial to avoid the related issues of this charitable organization. When employees can
prevent and resolve these issues, then they create some strategy for organizational enhancement
(Sargeant and Jay 2014).The standard data storage places of the future plus are shaving cabinets,
servers, and cloud storage. However, if that document is accepted positions, it shouldn't, an
organization can get into problem. Future plus showing industry offline and online, here are
certain hazard zones:
Gathering credit card information and online dispensation payments.
Future plus are Storing individual evidence on smartphones or laptops.
Allowing admission to individual material to third parties without proper protections
Storing private content on cloud servers or structures, or unsafe sites
Future Plus Donor Safety Guidelines:-
Future Plus delivers a privacy strategy on its website or by a demand that designates how
contributor evidence is composed and used. It permits contributors to choose to make their
private evidence accessible or shared (Watts and Casanovas 2018). Future Plus has a board-
INFORMATION SECURITY MANAGEMENT OF FUTUREPLUS
organization use and shield contributor’s private information. This strategy determines to
provoke faith and highlight that the association will not share or sell private information without
authorization (Costa-Cabral and Lynsky 2017). Having a donor confidentiality strategy can
permit the non-profit to connect to their donors the rank that they place on defensive their
contributor’s information. Some Watchdog agencies and evaluations collections check whether
administrations have a contributor privacy plan. For example, Charity Guide takes this influence
into account for its answerability and transparency tally.
To prevent the Dangerous problem:-
It is crucial to avoid the related issues of this charitable organization. When employees can
prevent and resolve these issues, then they create some strategy for organizational enhancement
(Sargeant and Jay 2014).The standard data storage places of the future plus are shaving cabinets,
servers, and cloud storage. However, if that document is accepted positions, it shouldn't, an
organization can get into problem. Future plus showing industry offline and online, here are
certain hazard zones:
Gathering credit card information and online dispensation payments.
Future plus are Storing individual evidence on smartphones or laptops.
Allowing admission to individual material to third parties without proper protections
Storing private content on cloud servers or structures, or unsafe sites
Future Plus Donor Safety Guidelines:-
Future Plus delivers a privacy strategy on its website or by a demand that designates how
contributor evidence is composed and used. It permits contributors to choose to make their
private evidence accessible or shared (Watts and Casanovas 2018). Future Plus has a board-

5
INFORMATION SECURITY MANAGEMENT OF FUTUREPLUS
approved discontinue contact strategy assuring that contributors can be uninvolved from
solicitation and other dispatching lists. The only individual data that future plus accumulate from
contributors is the evidence that happily delivers the future plus organisation. If contributors
choose to contribute by clicking the donate button on a future plus website, or if a donor
contributes to Future plus via social media or other online sites.
Future plus will collect correct individually recognizable data, which may contain
donor’s name, postal address, email address, contact information and payment information.
Concerning treating contributor donations whether or not administered through the other
payment processor (Novikov 2015). The payment evidence contributor delivers to future plus
will only be used to procedure the client's payment. If a donor chooses to make a periodic
contribution, then compulsory payment evidence will be kept to simplify upcoming payments.
Otherwise, a donor's payment evidence will not be saved or used for any other drive. Future plus
do not trade, share, charge, or else make accessible the names. The individual data of future plus
donors with any other association or person. Importantly future plus do not send mails to the
company's contributors on behalf of different administrations. Future plus only sending emails to
the clients for payment confirmations and other official purposes.
Contributor data safety technique:-
Recognize the confidential value:-
When it originates to information safety and privacy, keep in attention that different
conditions and contributor bases call for different methods. Some contributors proclaim their
charities openly while others select anonymity (DSS 2016). Knowing the privacy level that every
donor imagines is just one step toward constriction up documents safety.
INFORMATION SECURITY MANAGEMENT OF FUTUREPLUS
approved discontinue contact strategy assuring that contributors can be uninvolved from
solicitation and other dispatching lists. The only individual data that future plus accumulate from
contributors is the evidence that happily delivers the future plus organisation. If contributors
choose to contribute by clicking the donate button on a future plus website, or if a donor
contributes to Future plus via social media or other online sites.
Future plus will collect correct individually recognizable data, which may contain
donor’s name, postal address, email address, contact information and payment information.
Concerning treating contributor donations whether or not administered through the other
payment processor (Novikov 2015). The payment evidence contributor delivers to future plus
will only be used to procedure the client's payment. If a donor chooses to make a periodic
contribution, then compulsory payment evidence will be kept to simplify upcoming payments.
Otherwise, a donor's payment evidence will not be saved or used for any other drive. Future plus
do not trade, share, charge, or else make accessible the names. The individual data of future plus
donors with any other association or person. Importantly future plus do not send mails to the
company's contributors on behalf of different administrations. Future plus only sending emails to
the clients for payment confirmations and other official purposes.
Contributor data safety technique:-
Recognize the confidential value:-
When it originates to information safety and privacy, keep in attention that different
conditions and contributor bases call for different methods. Some contributors proclaim their
charities openly while others select anonymity (DSS 2016). Knowing the privacy level that every
donor imagines is just one step toward constriction up documents safety.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
INFORMATION SECURITY MANAGEMENT OF FUTUREPLUS
Use updated Software:-
Software updates are essential portions of the right safety approach. Updates are
particularly significant if a future plus website is assembled on some popular platforms. Future
plus is the public donor depended on organization, so this organisation is a viral target for
hackers (Bandara 2014). If the software does not upgrade, then the hacker easily hacked future
plus’s database and website. After that, they also collect the donor bank details and personal
details. So the website specialists upgrade their web structure, software and data source then the
hacker does not create any vulnerabilities. For this reason, the donor feels secure and also try to
donate more amount for children education.
Use protected connection:-
Future plus is the company they used modern fifth-generation technology. But assure
future plus office network is encrypted and protected. It is crucial that future plus cannot use
public networks to access economic resources. If future plus technician are not assuring where to
start, an encoded VPN is one of the most significant safe ways to access future plus network
(Van Zoonen 2016). A VPN is a cloud-based network that permits future plus employees to
access a protected connection no matter where they are. It supports confirm that data sent to and
from the future plus servers are harmless from hacker's eyes . It is also a significant efficiency
improvement. Future plus employees can steadily contact business possessions from any
location, allowing remote work with the same confidentiality and safety structures at the Future
plus’s Sydney office.
Create an Encrypted Database for Data storage:-
Make sure several economic or otherwise delicate data, including contributor names, is
stored in an encoded databank. Monetary numbers, Pins and all other data should never be
INFORMATION SECURITY MANAGEMENT OF FUTUREPLUS
Use updated Software:-
Software updates are essential portions of the right safety approach. Updates are
particularly significant if a future plus website is assembled on some popular platforms. Future
plus is the public donor depended on organization, so this organisation is a viral target for
hackers (Bandara 2014). If the software does not upgrade, then the hacker easily hacked future
plus’s database and website. After that, they also collect the donor bank details and personal
details. So the website specialists upgrade their web structure, software and data source then the
hacker does not create any vulnerabilities. For this reason, the donor feels secure and also try to
donate more amount for children education.
Use protected connection:-
Future plus is the company they used modern fifth-generation technology. But assure
future plus office network is encrypted and protected. It is crucial that future plus cannot use
public networks to access economic resources. If future plus technician are not assuring where to
start, an encoded VPN is one of the most significant safe ways to access future plus network
(Van Zoonen 2016). A VPN is a cloud-based network that permits future plus employees to
access a protected connection no matter where they are. It supports confirm that data sent to and
from the future plus servers are harmless from hacker's eyes . It is also a significant efficiency
improvement. Future plus employees can steadily contact business possessions from any
location, allowing remote work with the same confidentiality and safety structures at the Future
plus’s Sydney office.
Create an Encrypted Database for Data storage:-
Make sure several economic or otherwise delicate data, including contributor names, is
stored in an encoded databank. Monetary numbers, Pins and all other data should never be
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
INFORMATION SECURITY MANAGEMENT OF FUTUREPLUS
deposited in simple text (Sun 2014). With encryption, if Future plus’s other safety procedures
fail and an assailant does get contact with company records, they unable to do anything with
them. It is both the organization’s last line of protection and the single most significant object the
company can do to defend the confidentiality of future plus contributors. If future plus cannot
have enough money to supply and preserve contributor’s data onsite. It is not a big problem
because sufficiently of cloud-based storing sites try to deal with high-level safety at realistic
amounts (QC 2016). Furthermore, be clear about the records the future plus does stock, and what
future plus does with it. Fate plus website should have a predictable confidentiality strategy page
outlining precisely what contributor material will be recorded.
Strong Password:-
When future plus have lots of data, it looks like an excessive impression to either uses a
similar keyword for all financial records or use simple, user friendly passwords. While future
plus cannot have a roughly in what organization’s donors use as pin away on the website.
Passwords that involve figures and signs in addition to letters are decent, as are lengthier pins, so
set these as necessities when operators set up their financial records and personal information
(Zhang 2018).One object this organization does not want to do is need vital systematic
deviations. Amazingly, this can reason operators to select less protected passwords due to the
apparent annoyance of continuously altering them. There is an acceptable mark to walk between
protection and difficulties, of course, but with main cybercrimes as mutual as they are, it possibly
most significant to be excessively alert.
Experience employee:-
To accomplish the processes of the future, plus, they have employed both full time and
part-time staff. The full-time supervisor contains a Working Manager, an Auditor, a
INFORMATION SECURITY MANAGEMENT OF FUTUREPLUS
deposited in simple text (Sun 2014). With encryption, if Future plus’s other safety procedures
fail and an assailant does get contact with company records, they unable to do anything with
them. It is both the organization’s last line of protection and the single most significant object the
company can do to defend the confidentiality of future plus contributors. If future plus cannot
have enough money to supply and preserve contributor’s data onsite. It is not a big problem
because sufficiently of cloud-based storing sites try to deal with high-level safety at realistic
amounts (QC 2016). Furthermore, be clear about the records the future plus does stock, and what
future plus does with it. Fate plus website should have a predictable confidentiality strategy page
outlining precisely what contributor material will be recorded.
Strong Password:-
When future plus have lots of data, it looks like an excessive impression to either uses a
similar keyword for all financial records or use simple, user friendly passwords. While future
plus cannot have a roughly in what organization’s donors use as pin away on the website.
Passwords that involve figures and signs in addition to letters are decent, as are lengthier pins, so
set these as necessities when operators set up their financial records and personal information
(Zhang 2018).One object this organization does not want to do is need vital systematic
deviations. Amazingly, this can reason operators to select less protected passwords due to the
apparent annoyance of continuously altering them. There is an acceptable mark to walk between
protection and difficulties, of course, but with main cybercrimes as mutual as they are, it possibly
most significant to be excessively alert.
Experience employee:-
To accomplish the processes of the future, plus, they have employed both full time and
part-time staff. The full-time supervisor contains a Working Manager, an Auditor, a

8
INFORMATION SECURITY MANAGEMENT OF FUTUREPLUS
Development Officer, two Situation Officers, and three provision staff. There are three part-time
employees provided that additional maintenance to the Circumstance Officers with suitability
payments and appointments to the applicant learners, also offered that informs students who
obtain help from Future Plus.At this moment, future plus enhance their business structure then
they try to employ more employee for system control (Borgesius, Gray and van 2015). If these
employees are more experience in the technical field and they are very much known for the
database maintaining. So it is very much helpful for data protection of future plus donor. If future
plus trained there employee by the experienced trainer, then this training may be beneficial for
the organization.
24*7 monitoring:-
If future plus creates a good impact in between the Australian people, then they should
monitor their websites in every moment like 24*7 (Tremblay-Boire and Prakash 2017).
Previously Future Plus delivers their part-time staff with transportable devices to take on-site
case records throughout their website calls and direct these to the workplace via protected
infrastructures. Since they supply delicate material about their contributors, students were
receiving contributions, as well as payment particulars such as bank details and credit card
details.
Proper working maintenance:-
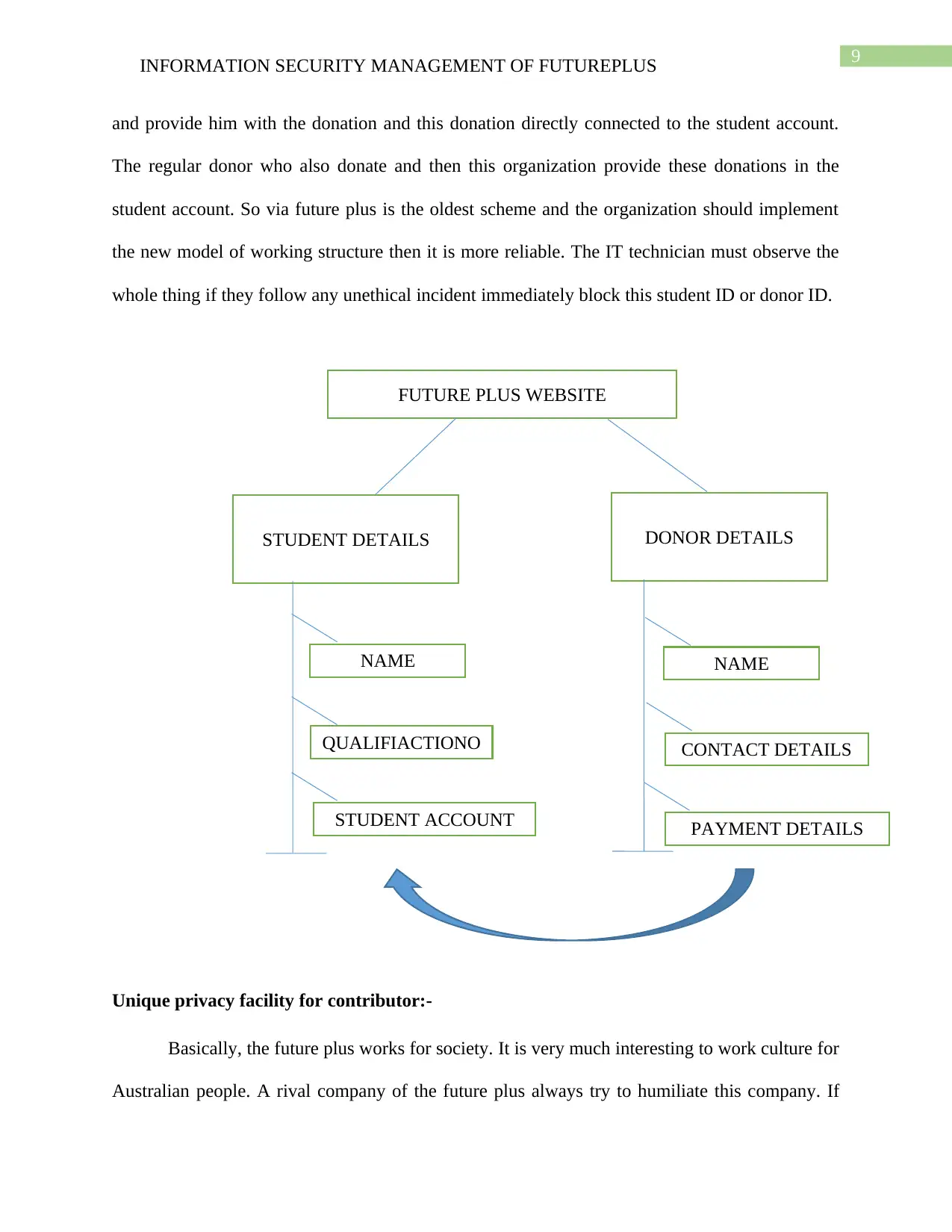
The working procedure of the future plus should be ethical. There are two processes. One
is the Student registration process, and other is the donor information process. The student
registration procedure is mainly related to the student personal details, their qualification and
student account. And another donor information process is related to the donor's name, address,
contact details and payment information (Zhang et al. 2015). Any donor can choose the student
INFORMATION SECURITY MANAGEMENT OF FUTUREPLUS
Development Officer, two Situation Officers, and three provision staff. There are three part-time
employees provided that additional maintenance to the Circumstance Officers with suitability
payments and appointments to the applicant learners, also offered that informs students who
obtain help from Future Plus.At this moment, future plus enhance their business structure then
they try to employ more employee for system control (Borgesius, Gray and van 2015). If these
employees are more experience in the technical field and they are very much known for the
database maintaining. So it is very much helpful for data protection of future plus donor. If future
plus trained there employee by the experienced trainer, then this training may be beneficial for
the organization.
24*7 monitoring:-
If future plus creates a good impact in between the Australian people, then they should
monitor their websites in every moment like 24*7 (Tremblay-Boire and Prakash 2017).
Previously Future Plus delivers their part-time staff with transportable devices to take on-site
case records throughout their website calls and direct these to the workplace via protected
infrastructures. Since they supply delicate material about their contributors, students were
receiving contributions, as well as payment particulars such as bank details and credit card
details.
Proper working maintenance:-
The working procedure of the future plus should be ethical. There are two processes. One
is the Student registration process, and other is the donor information process. The student
registration procedure is mainly related to the student personal details, their qualification and
student account. And another donor information process is related to the donor's name, address,
contact details and payment information (Zhang et al. 2015). Any donor can choose the student
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
INFORMATION SECURITY MANAGEMENT OF FUTUREPLUS
and provide him with the donation and this donation directly connected to the student account.
The regular donor who also donate and then this organization provide these donations in the
student account. So via future plus is the oldest scheme and the organization should implement
the new model of working structure then it is more reliable. The IT technician must observe the
whole thing if they follow any unethical incident immediately block this student ID or donor ID.
Unique privacy facility for contributor:-
Basically, the future plus works for society. It is very much interesting to work culture for
Australian people. A rival company of the future plus always try to humiliate this company. If
FUTURE PLUS WEBSITE
STUDENT DETAILS DONOR DETAILS
NAME
QUALIFIACTIONO
STUDENT ACCOUNT
NAME
CONTACT DETAILS
PAYMENT DETAILS
INFORMATION SECURITY MANAGEMENT OF FUTUREPLUS
and provide him with the donation and this donation directly connected to the student account.
The regular donor who also donate and then this organization provide these donations in the
student account. So via future plus is the oldest scheme and the organization should implement
the new model of working structure then it is more reliable. The IT technician must observe the
whole thing if they follow any unethical incident immediately block this student ID or donor ID.
Unique privacy facility for contributor:-
Basically, the future plus works for society. It is very much interesting to work culture for
Australian people. A rival company of the future plus always try to humiliate this company. If
FUTURE PLUS WEBSITE
STUDENT DETAILS DONOR DETAILS
NAME
QUALIFIACTIONO
STUDENT ACCOUNT
NAME
CONTACT DETAILS
PAYMENT DETAILS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
INFORMATION SECURITY MANAGEMENT OF FUTUREPLUS
future plus authority was very much aware of this, then it should be right for their organization.
The backward economic students are very much lucky to get this opportunity. The future plus
also try to spread this work culture through social media and national media. If this company
invent new facilities for donors, then they are more interested in this company. So the main
facilities are security (Kent 2016). If it is possible when every employee is concern about their
donor security. If they recruit professional technician, then this is very much helpful for this
organization. The IT officials categorised this the donor from level 1, level 2 in according to the
contribution. Every donor who donates high or low money is equally important to the future
plus. Future plus should complete their security task in a respectful manner.
Conclusion:-
Future plus is the Australian charitable organization. They started the current educational
project for backward economic student. They provide education with a free of cost. Many
Australian people contribute some donations to this organization. The Sydney based organization
try to secure their donor privacy data. So for a reason, if they should implement modern
structures of database and also recruit some professional technician, then they create an
extraordinary impact on Australian society. In this paper, the writer discusses how future plus
creates a good security structure for their contributor. Data storage policy and privacy strategy
are very much crucial for the future plus to maintain social respect.
INFORMATION SECURITY MANAGEMENT OF FUTUREPLUS
future plus authority was very much aware of this, then it should be right for their organization.
The backward economic students are very much lucky to get this opportunity. The future plus
also try to spread this work culture through social media and national media. If this company
invent new facilities for donors, then they are more interested in this company. So the main
facilities are security (Kent 2016). If it is possible when every employee is concern about their
donor security. If they recruit professional technician, then this is very much helpful for this
organization. The IT officials categorised this the donor from level 1, level 2 in according to the
contribution. Every donor who donates high or low money is equally important to the future
plus. Future plus should complete their security task in a respectful manner.
Conclusion:-
Future plus is the Australian charitable organization. They started the current educational
project for backward economic student. They provide education with a free of cost. Many
Australian people contribute some donations to this organization. The Sydney based organization
try to secure their donor privacy data. So for a reason, if they should implement modern
structures of database and also recruit some professional technician, then they create an
extraordinary impact on Australian society. In this paper, the writer discusses how future plus
creates a good security structure for their contributor. Data storage policy and privacy strategy
are very much crucial for the future plus to maintain social respect.

11
INFORMATION SECURITY MANAGEMENT OF FUTUREPLUS
References:-
Bandara, I., Ioras, F. and Maher, K., 2014. Cyber security concerns in e-learning education.
Borgesius, F.Z., Gray, J. and van Eechoud, M., 2015. Open data, privacy, and fair information
principles: Towards a balancing framework. Berkeley Technology Law Journal, 30(3), pp.2073-
2131.
Bredenoord, A.L., Mostert, M., Isasi, R. and Knoppers, B.M., 2015. Data sharing in stem cell
translational science: policy statement by the international stem cell forum ethics working party.
Regenerative medicine, 10(7), pp.857-861.
Costa-Cabral, F. and Lynskey, O., 2017. Family ties: the intersection between data protection
and competition in EU Law. Common Market Law Review, 54(1), pp.11-50.
DSS, P., 2016. Payment Card Industry Data Security Standards. International Information
Security Standard.
Hess, A.N., LaPorte-Fiori, R. and Engwall, K., 2015. Preserving patron privacy in the 21st
century academic library. The Journal of Academic Librarianship, 41(1), pp.105-114.
Kent, A.D., 2016. Cyber security data sources for dynamic network research. In Dynamic
Networks and Cyber-Security (pp. 37-65).
Novikov, R.A. and Tomilov, Y.V., 2015. Dimerization of donor–acceptor cyclopropanes.
Mendeleev Communications, 1(25), pp.1-10.
QC, F.G., Muraszkiewicz, J. and Vavoula, N., 2016. The role of technology in the fight against
human trafficking: Reflections on privacy and data protection concerns. Computer Law &
Security Review, 32(2), pp.205-217.
INFORMATION SECURITY MANAGEMENT OF FUTUREPLUS
References:-
Bandara, I., Ioras, F. and Maher, K., 2014. Cyber security concerns in e-learning education.
Borgesius, F.Z., Gray, J. and van Eechoud, M., 2015. Open data, privacy, and fair information
principles: Towards a balancing framework. Berkeley Technology Law Journal, 30(3), pp.2073-
2131.
Bredenoord, A.L., Mostert, M., Isasi, R. and Knoppers, B.M., 2015. Data sharing in stem cell
translational science: policy statement by the international stem cell forum ethics working party.
Regenerative medicine, 10(7), pp.857-861.
Costa-Cabral, F. and Lynskey, O., 2017. Family ties: the intersection between data protection
and competition in EU Law. Common Market Law Review, 54(1), pp.11-50.
DSS, P., 2016. Payment Card Industry Data Security Standards. International Information
Security Standard.
Hess, A.N., LaPorte-Fiori, R. and Engwall, K., 2015. Preserving patron privacy in the 21st
century academic library. The Journal of Academic Librarianship, 41(1), pp.105-114.
Kent, A.D., 2016. Cyber security data sources for dynamic network research. In Dynamic
Networks and Cyber-Security (pp. 37-65).
Novikov, R.A. and Tomilov, Y.V., 2015. Dimerization of donor–acceptor cyclopropanes.
Mendeleev Communications, 1(25), pp.1-10.
QC, F.G., Muraszkiewicz, J. and Vavoula, N., 2016. The role of technology in the fight against
human trafficking: Reflections on privacy and data protection concerns. Computer Law &
Security Review, 32(2), pp.205-217.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




