Geocaching System Project: Desktop Application Design and Development
VerifiedAdded on 2019/09/23
|24
|4129
|409
Project
AI Summary
This project report outlines the design and development of a desktop-based geocaching system for tracking and managing geocaching activities. The project begins with a system vision document, detailing requirements and system capabilities. It progresses through project planning, including work breakdown structures and iteration plans. The report then delves into understanding requirements, including use case diagrams, class diagrams, and user experience design. The software architecture design covers database design, and the report explores the rationale behind choosing a desktop-based system. Detailed design elements, including workflow diagrams, are provided, and the project concludes with a discussion of testing and deployment considerations. The system aims to allow users to log, track, and share geocaching information and activities, including creating new logs, sharing interests, and updating information from remote locations. The report includes various figures such as use case diagrams, class diagrams, and database schema to illustrate the system's design.

[School]
[Course title]
[Document title]
[Document subtitle]
[Course title]
[Document title]
[Document subtitle]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Task 0: System Vision document 2
Description 2
Following would be the system capabilities 2
Task 1 Plan the Project 4
Assignment D1-1: Iteration 4
Iteration 2 4
Assignment D1-2: Work Breakdown Structure 4
Task 2: understand the requirements 6
Sub task 2.1: Create use case diagram 6
Sub task 2.2: Class Diagram 100 7
Task 3: Define user experience 8
Sub-Task 3.1: Single use-case and identify the steps to do the use case 8
Sub Task 3.2: Workflow of the selected use case 10
Task 4: Develop the Software Architecture Design 11
Sub Task 4.1: Preliminary database 11
Sub Task: 4.2: desktop or browser based system 12
Task 5: Develop detailed design 13
Task 6: Test and Deploy the system 14
1
Task 0: System Vision document 2
Description 2
Following would be the system capabilities 2
Task 1 Plan the Project 4
Assignment D1-1: Iteration 4
Iteration 2 4
Assignment D1-2: Work Breakdown Structure 4
Task 2: understand the requirements 6
Sub task 2.1: Create use case diagram 6
Sub task 2.2: Class Diagram 100 7
Task 3: Define user experience 8
Sub-Task 3.1: Single use-case and identify the steps to do the use case 8
Sub Task 3.2: Workflow of the selected use case 10
Task 4: Develop the Software Architecture Design 11
Sub Task 4.1: Preliminary database 11
Sub Task: 4.2: desktop or browser based system 12
Task 5: Develop detailed design 13
Task 6: Test and Deploy the system 14
1

List of Figures
Figure 1: Use Case Diagram 7
Figure 2: Class Diagram 8
Figure 3: Use Case Description 10
Figure 4: Workflow Diagram 11
Figure 5: Preliminary Database 12
Figure 6: User Interface 15
2
Figure 1: Use Case Diagram 7
Figure 2: Class Diagram 8
Figure 3: Use Case Description 10
Figure 4: Workflow Diagram 11
Figure 5: Preliminary Database 12
Figure 6: User Interface 15
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Task 0: System Vision document
Description
As per the case study the Wayne Johansen has become great fan of geocaching and want to keep
all the geocaching activities being tracked and well managed. As the Wayne is looking for
developing his own website rather than using any free or commercial websites that are available
around internet. As per the requirement the system that would be developed for various of
geocaching activities that would include several interesting geocaches and along with the various
trips the Wayne have ever made and other trips he would like to go to, along with the places the
Wayne have discovered using the new device. As Wayne is looking forward to create his own
logs and geocaches, he wants to develop a portal that would create the portal for his purpose,
track other places that have been shared with public along with the updating of various geocache
logs. (Al-alshuhai & Siewe, 2015)
The system that would be developed is an information storing system with information being
provided in form of longitudes and latitudes along with the needs to store the databased to
manage all the information and video logs as well of the places. For the current approach of
Wayne, he has decided to develop the system that would work on laptop or desktop and mobile
version can be launched later. (Alhumaidan & Zafar, 2014)
Following would be the system capabilities
The system that would be developed should be able to provide following functionalities or
features:
Keep logs of the geocaches which have not been found/located by the Wayne
Keep the logs of the geocaches that have been found or located by Wayne
Record the details of the geocaches along with the supplementary information needed for
the geocache activities.
Keep logs of the geocaches that have been created by Wayne in recent past and marked
them as new.
Keep log of the geocaches that have been posted by Wayne over other geocaching
websites.
3
Description
As per the case study the Wayne Johansen has become great fan of geocaching and want to keep
all the geocaching activities being tracked and well managed. As the Wayne is looking for
developing his own website rather than using any free or commercial websites that are available
around internet. As per the requirement the system that would be developed for various of
geocaching activities that would include several interesting geocaches and along with the various
trips the Wayne have ever made and other trips he would like to go to, along with the places the
Wayne have discovered using the new device. As Wayne is looking forward to create his own
logs and geocaches, he wants to develop a portal that would create the portal for his purpose,
track other places that have been shared with public along with the updating of various geocache
logs. (Al-alshuhai & Siewe, 2015)
The system that would be developed is an information storing system with information being
provided in form of longitudes and latitudes along with the needs to store the databased to
manage all the information and video logs as well of the places. For the current approach of
Wayne, he has decided to develop the system that would work on laptop or desktop and mobile
version can be launched later. (Alhumaidan & Zafar, 2014)
Following would be the system capabilities
The system that would be developed should be able to provide following functionalities or
features:
Keep logs of the geocaches which have not been found/located by the Wayne
Keep the logs of the geocaches that have been found or located by Wayne
Record the details of the geocaches along with the supplementary information needed for
the geocache activities.
Keep logs of the geocaches that have been created by Wayne in recent past and marked
them as new.
Keep log of the geocaches that have been posted by Wayne over other geocaching
websites.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Provide detailed reports of the information from various sources by the Wayne geocaches
activities.
Benefits of the Application developed
Following are benefits that system should be able to provide Wayne:
Wayne should be able to track his all the geocaching based activities and able to custom
search the activities logs
Able to create new activity logs and new geocaches.
Able to share his interest regarding the geocaches with his friends.
Able to update his log from remote based location, like travelling on a geocache based
activity and able to update on the run.
4
activities.
Benefits of the Application developed
Following are benefits that system should be able to provide Wayne:
Wayne should be able to track his all the geocaching based activities and able to custom
search the activities logs
Able to create new activity logs and new geocaches.
Able to share his interest regarding the geocaches with his friends.
Able to update his log from remote based location, like travelling on a geocache based
activity and able to update on the run.
4

Task 1 Plan the Project
Assignment D1-1: Iteration 1
As per the feasibility analysis of the vision document, the laptop based solution to be developed
seems to be ideal for the current case. The system would be developing from first to be Laptop or
Desktop based application and then can be further enhanced to mobile based system support.
Currently the major focus being the Desktop based application that can run on laptops as well.
(Ibrahim, Ibrahim, Saringat, Mansor & Herawan, 2011)
Iteration 2
The second iteration would be to develop the mobile based system that can support the features
of the laptop based applications. The user would be then able to perform all the actions as it
would have done on a laptop. (Ibrahim, Ibrahim, Saringat, Mansor & Herawan, 2011)
Assignment D1-2: Work Breakdown Structure
I. We need to check all the details Wayne wants to log for the geocaches that have been
completed:
1. Identify the requirements based on the discussions that have been made in order to
learn more about the expected system by the Wayne,
2. Identify the requirements regarding the data that Wayne would like to keep on the
system.
3. Identify the system use cases and develop the case around the requirements of the
system.
4. Later when the use cases have been defined develop the workflows for them.
II. Develop the various components of the system
1. Develop the database schema
2. Based on the schema develop the ERD
3. Develop the prototype based screens
4. Develop the specification based on the software applications
5. Develop the overall program details.
III. Develop the System for the laptop based system
1. Based on the ERD develop the physical schema
5
Assignment D1-1: Iteration 1
As per the feasibility analysis of the vision document, the laptop based solution to be developed
seems to be ideal for the current case. The system would be developing from first to be Laptop or
Desktop based application and then can be further enhanced to mobile based system support.
Currently the major focus being the Desktop based application that can run on laptops as well.
(Ibrahim, Ibrahim, Saringat, Mansor & Herawan, 2011)
Iteration 2
The second iteration would be to develop the mobile based system that can support the features
of the laptop based applications. The user would be then able to perform all the actions as it
would have done on a laptop. (Ibrahim, Ibrahim, Saringat, Mansor & Herawan, 2011)
Assignment D1-2: Work Breakdown Structure
I. We need to check all the details Wayne wants to log for the geocaches that have been
completed:
1. Identify the requirements based on the discussions that have been made in order to
learn more about the expected system by the Wayne,
2. Identify the requirements regarding the data that Wayne would like to keep on the
system.
3. Identify the system use cases and develop the case around the requirements of the
system.
4. Later when the use cases have been defined develop the workflows for them.
II. Develop the various components of the system
1. Develop the database schema
2. Based on the schema develop the ERD
3. Develop the prototype based screens
4. Develop the specification based on the software applications
5. Develop the overall program details.
III. Develop the System for the laptop based system
1. Based on the ERD develop the physical schema
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2. Develop the system software or web based system that satisfies all the major
requirements.
IV. Test the overall system
1. Test the system using the unit testing
2. Test the system using the integration testing
3. Test the system using the system testing
4. Provide the running prototype to Wayne for final user based testing
6
requirements.
IV. Test the overall system
1. Test the system using the unit testing
2. Test the system using the integration testing
3. Test the system using the system testing
4. Provide the running prototype to Wayne for final user based testing
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Task 2: understand the requirements
Sub task 2.1: Create use case diagram
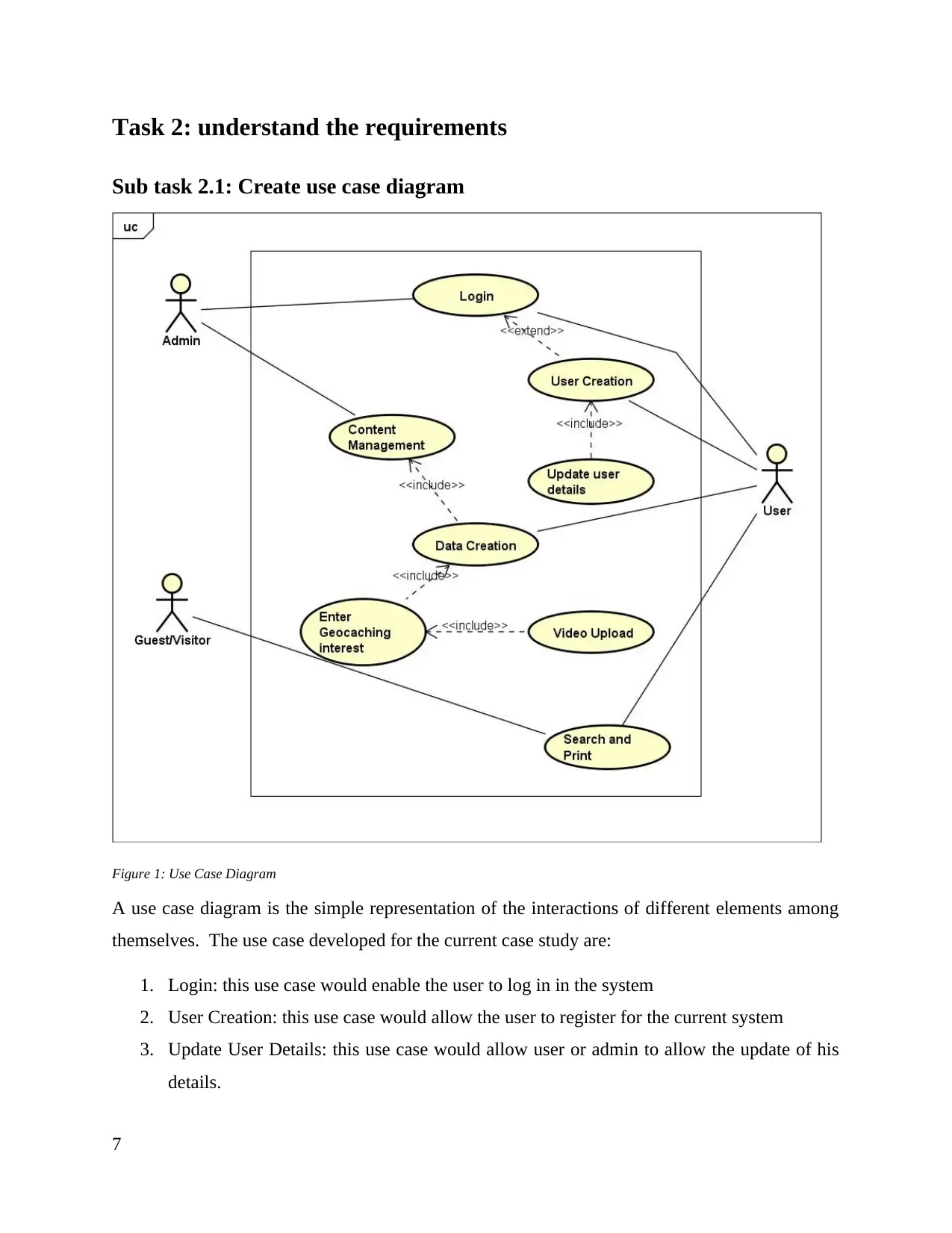
Figure 1: Use Case Diagram
A use case diagram is the simple representation of the interactions of different elements among
themselves. The use case developed for the current case study are:
1. Login: this use case would enable the user to log in in the system
2. User Creation: this use case would allow the user to register for the current system
3. Update User Details: this use case would allow user or admin to allow the update of his
details.
7
Sub task 2.1: Create use case diagram
Figure 1: Use Case Diagram
A use case diagram is the simple representation of the interactions of different elements among
themselves. The use case developed for the current case study are:
1. Login: this use case would enable the user to log in in the system
2. User Creation: this use case would allow the user to register for the current system
3. Update User Details: this use case would allow user or admin to allow the update of his
details.
7

4. Content Management: the content management use case would allow the user to manage
the content that have been uploaded.
5. Data Creation: data regarding the video, geocache locations are being update and
uploaded on the system
6. Enter Geocaching Interest: user would be able to include their interest and interested
areas of the system.
7. Video Upload: the video upload will work along with the content management and data
creation and would allow users to upload videos on the system
8. Search and Print: reports and different locations would be given to user as per the
searched query on a particular geographical location.
8
the content that have been uploaded.
5. Data Creation: data regarding the video, geocache locations are being update and
uploaded on the system
6. Enter Geocaching Interest: user would be able to include their interest and interested
areas of the system.
7. Video Upload: the video upload will work along with the content management and data
creation and would allow users to upload videos on the system
8. Search and Print: reports and different locations would be given to user as per the
searched query on a particular geographical location.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Sub task 2.2: Class Diagram 100
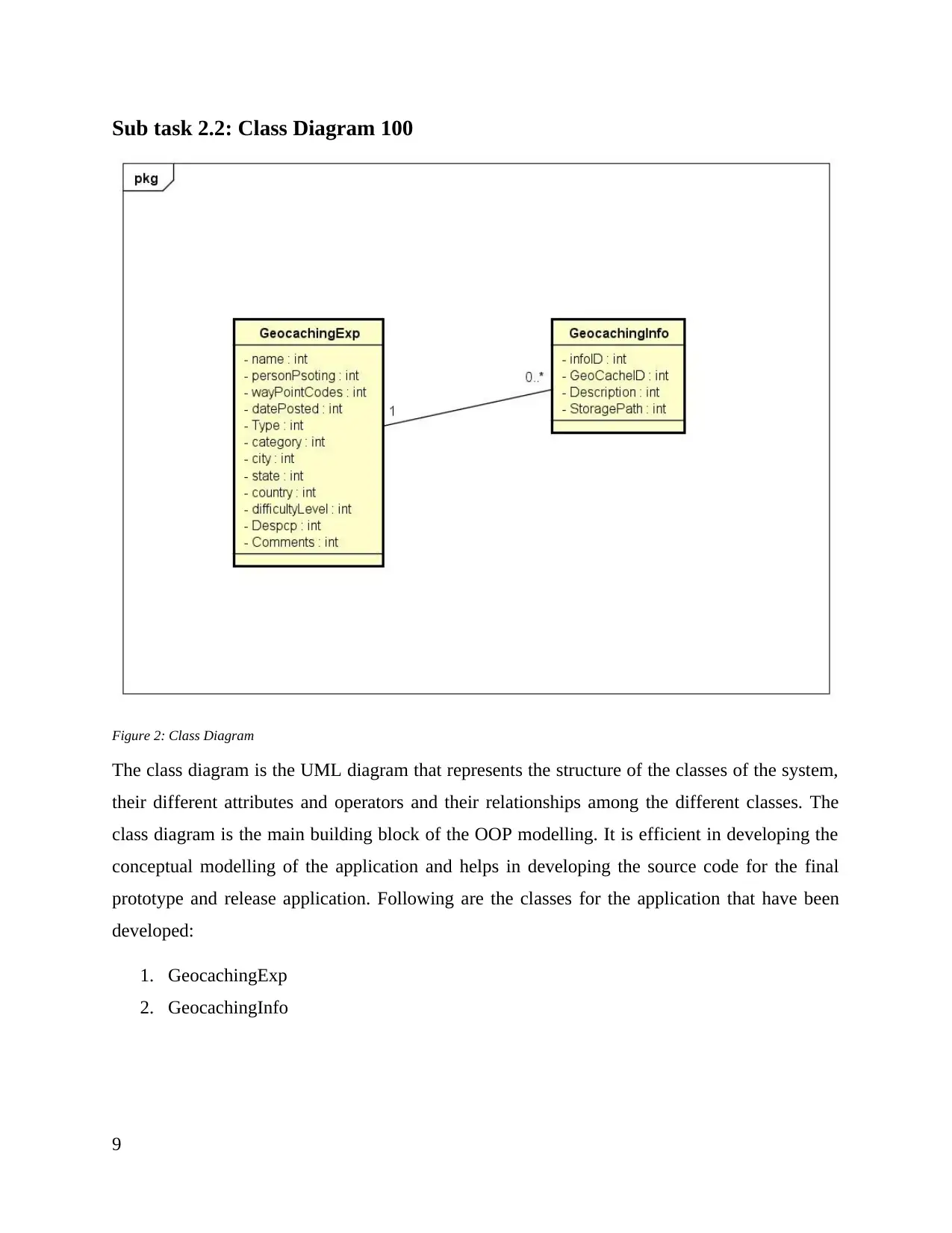
Figure 2: Class Diagram
The class diagram is the UML diagram that represents the structure of the classes of the system,
their different attributes and operators and their relationships among the different classes. The
class diagram is the main building block of the OOP modelling. It is efficient in developing the
conceptual modelling of the application and helps in developing the source code for the final
prototype and release application. Following are the classes for the application that have been
developed:
1. GeocachingExp
2. GeocachingInfo
9
Figure 2: Class Diagram
The class diagram is the UML diagram that represents the structure of the classes of the system,
their different attributes and operators and their relationships among the different classes. The
class diagram is the main building block of the OOP modelling. It is efficient in developing the
conceptual modelling of the application and helps in developing the source code for the final
prototype and release application. Following are the classes for the application that have been
developed:
1. GeocachingExp
2. GeocachingInfo
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Task 3: Define user experience
Sub-Task 3.1: Single use-case and identify the steps to do the use case
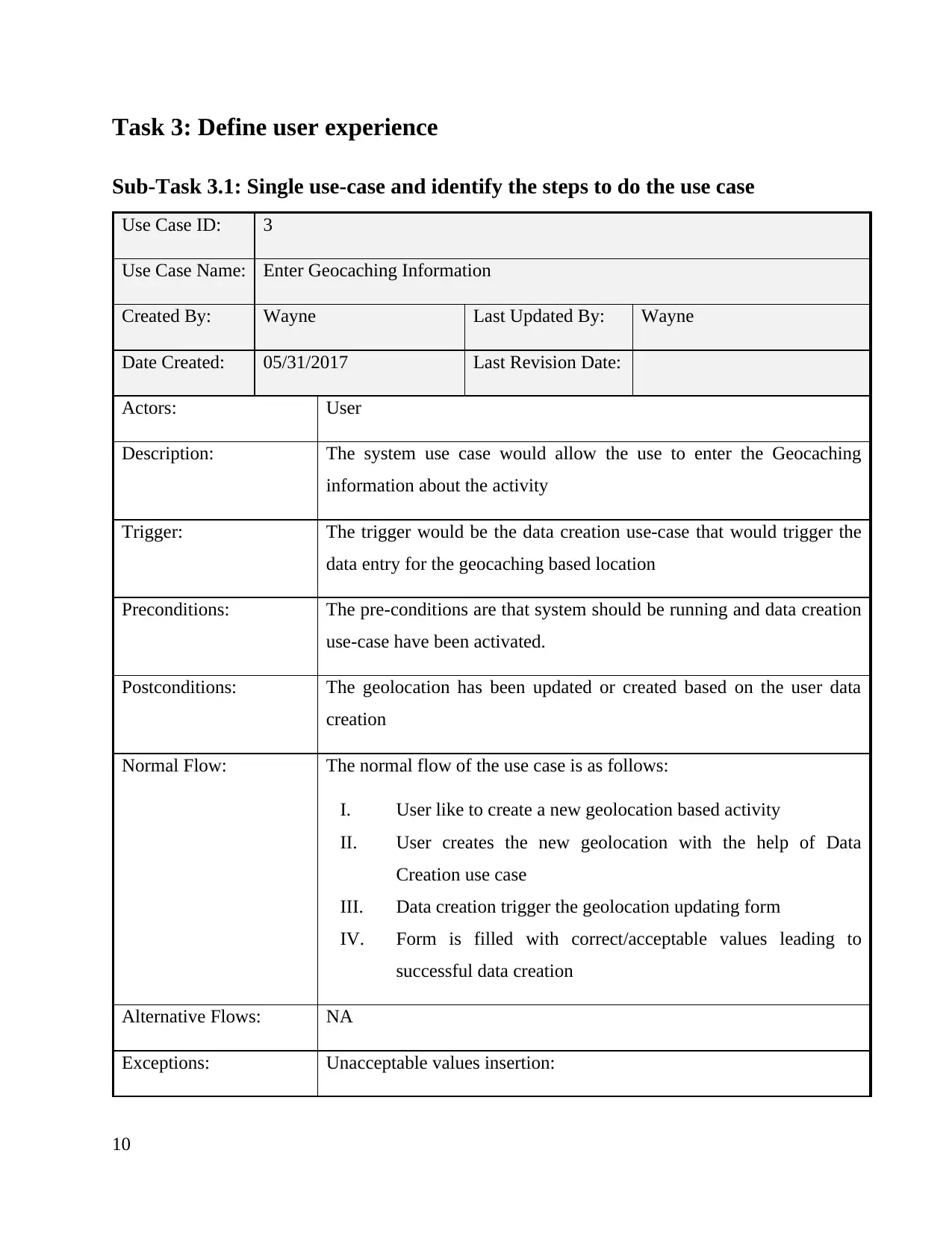
Use Case ID: 3
Use Case Name: Enter Geocaching Information
Created By: Wayne Last Updated By: Wayne
Date Created: 05/31/2017 Last Revision Date:
Actors: User
Description: The system use case would allow the use to enter the Geocaching
information about the activity
Trigger: The trigger would be the data creation use-case that would trigger the
data entry for the geocaching based location
Preconditions: The pre-conditions are that system should be running and data creation
use-case have been activated.
Postconditions: The geolocation has been updated or created based on the user data
creation
Normal Flow: The normal flow of the use case is as follows:
I. User like to create a new geolocation based activity
II. User creates the new geolocation with the help of Data
Creation use case
III. Data creation trigger the geolocation updating form
IV. Form is filled with correct/acceptable values leading to
successful data creation
Alternative Flows: NA
Exceptions: Unacceptable values insertion:
10
Sub-Task 3.1: Single use-case and identify the steps to do the use case
Use Case ID: 3
Use Case Name: Enter Geocaching Information
Created By: Wayne Last Updated By: Wayne
Date Created: 05/31/2017 Last Revision Date:
Actors: User
Description: The system use case would allow the use to enter the Geocaching
information about the activity
Trigger: The trigger would be the data creation use-case that would trigger the
data entry for the geocaching based location
Preconditions: The pre-conditions are that system should be running and data creation
use-case have been activated.
Postconditions: The geolocation has been updated or created based on the user data
creation
Normal Flow: The normal flow of the use case is as follows:
I. User like to create a new geolocation based activity
II. User creates the new geolocation with the help of Data
Creation use case
III. Data creation trigger the geolocation updating form
IV. Form is filled with correct/acceptable values leading to
successful data creation
Alternative Flows: NA
Exceptions: Unacceptable values insertion:
10
1. incorrect data updated
2. incorrect location longitude and latitude updated
Includes: Video Upload Use case is included in this use case
Frequency of Use: The frequency is quite high as the use case will define the overall
content of the website.
Special Requirements: Desktop based system
Assumptions: User can add/update records on the system
Notes and Issues: NA
Figure 3: Use Case Description
11
2. incorrect location longitude and latitude updated
Includes: Video Upload Use case is included in this use case
Frequency of Use: The frequency is quite high as the use case will define the overall
content of the website.
Special Requirements: Desktop based system
Assumptions: User can add/update records on the system
Notes and Issues: NA
Figure 3: Use Case Description
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 24
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
