ICT60415: Disaster Recovery Plan for Glasgow Health Board
VerifiedAdded on 2023/06/07
|6
|1595
|79
Report
AI Summary
This report provides a comprehensive analysis of a disaster recovery plan, focusing on a case study involving the Glasgow Health Board (GHB). The introduction highlights the importance of IT services and the consequences of system disruptions. The objectives are to identify measures to prevent future incidents and improve IT policies. The scope includes IT systems, staff responsibilities, and existing IT policies. The report defines Recovery Point Objective (RPO) and Recovery Time Objective (RTO) targets, outlining service-level agreements for various IT services. It then details the GHB's IT system, including data entry processes and system monitoring. A plan review reveals shortcomings in data backup and system maintenance. A risk assessment phase identifies system flaws and potential causes of data loss, followed by a safeguard determination phase proposing improvements. A Business Impact Analysis (BIA) assesses critical business processes and their impact on operations. The report concludes by determining strategies, including newer IT security policies such as regular system upgrades and mandatory daily backups. The report references relevant sources and provides a practical framework for disaster recovery planning.

Disaster Recovery Plan
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Introduction
IT services are an essential part of modern day business organizations. Thus it is essential that
all the IT related machinery as well as software are maintained timely and any problem in the
system may be resolved promptly. Any problem in the IT system may disrupt the whole
system and may hamper the overall functionality of the organization (Borgianni et al., 2015).
In this case study a similar incident is observed in case of Glasgow Health Board (GHB)
where the disruption in the IT system resulted in the postponing of several appointments of
the patients.
Objectives
The main objective of this study is to find appropriate measures to avoid similar incidents in
the future and make changes in the company IT policies.
Scope
The study will cover the IT system, the staff responsibilities and the IT policies to determine
the loopholes in the existing system.
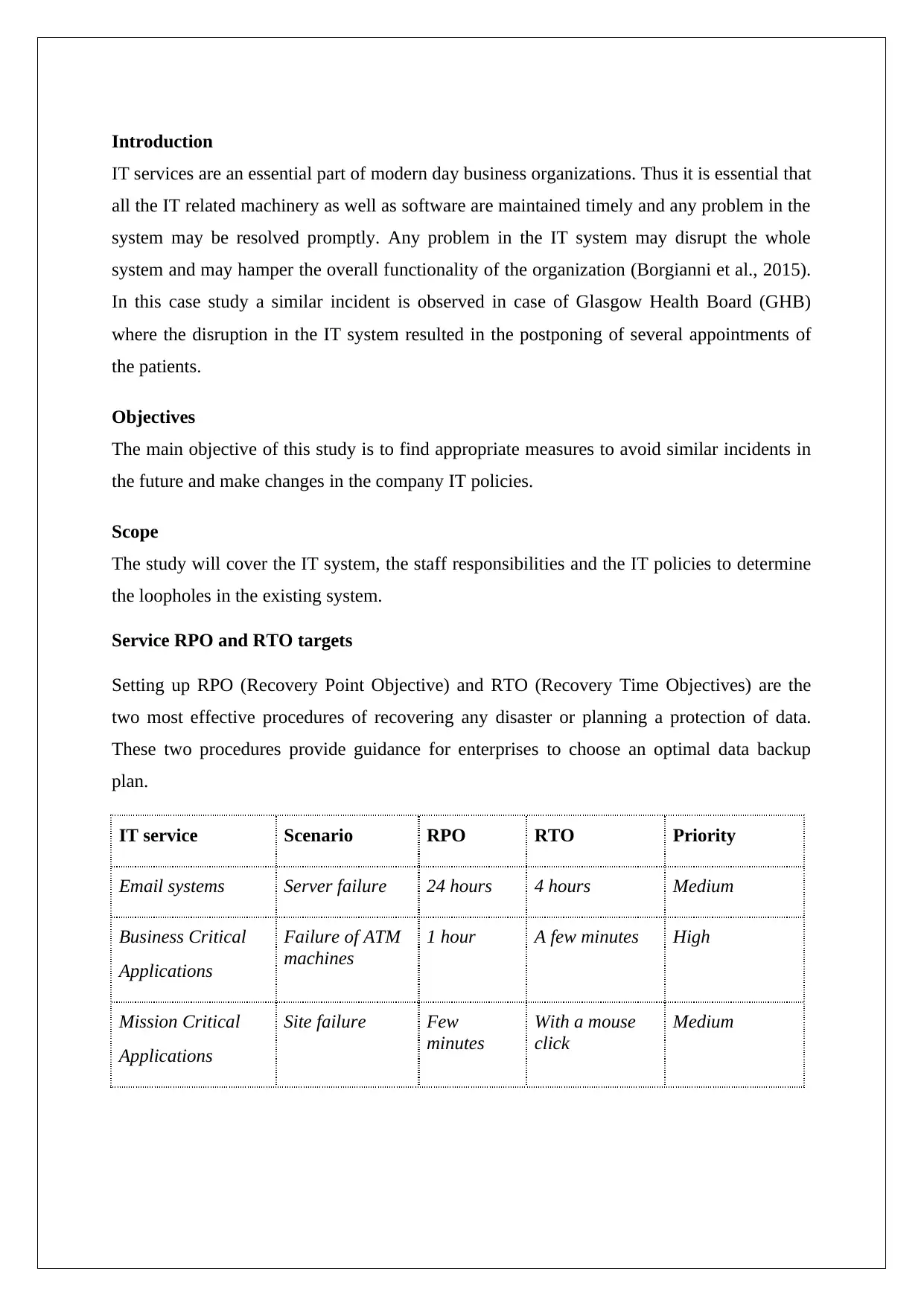
Service RPO and RTO targets
Setting up RPO (Recovery Point Objective) and RTO (Recovery Time Objectives) are the
two most effective procedures of recovering any disaster or planning a protection of data.
These two procedures provide guidance for enterprises to choose an optimal data backup
plan.
IT service Scenario RPO RTO Priority
Email systems Server failure 24 hours 4 hours Medium
Business Critical
Applications
Failure of ATM
machines
1 hour A few minutes High
Mission Critical
Applications
Site failure Few
minutes
With a mouse
click
Medium
IT services are an essential part of modern day business organizations. Thus it is essential that
all the IT related machinery as well as software are maintained timely and any problem in the
system may be resolved promptly. Any problem in the IT system may disrupt the whole
system and may hamper the overall functionality of the organization (Borgianni et al., 2015).
In this case study a similar incident is observed in case of Glasgow Health Board (GHB)
where the disruption in the IT system resulted in the postponing of several appointments of
the patients.
Objectives
The main objective of this study is to find appropriate measures to avoid similar incidents in
the future and make changes in the company IT policies.
Scope
The study will cover the IT system, the staff responsibilities and the IT policies to determine
the loopholes in the existing system.
Service RPO and RTO targets
Setting up RPO (Recovery Point Objective) and RTO (Recovery Time Objectives) are the
two most effective procedures of recovering any disaster or planning a protection of data.
These two procedures provide guidance for enterprises to choose an optimal data backup
plan.
IT service Scenario RPO RTO Priority
Email systems Server failure 24 hours 4 hours Medium
Business Critical
Applications
Failure of ATM
machines
1 hour A few minutes High
Mission Critical
Applications
Site failure Few
minutes
With a mouse
click
Medium
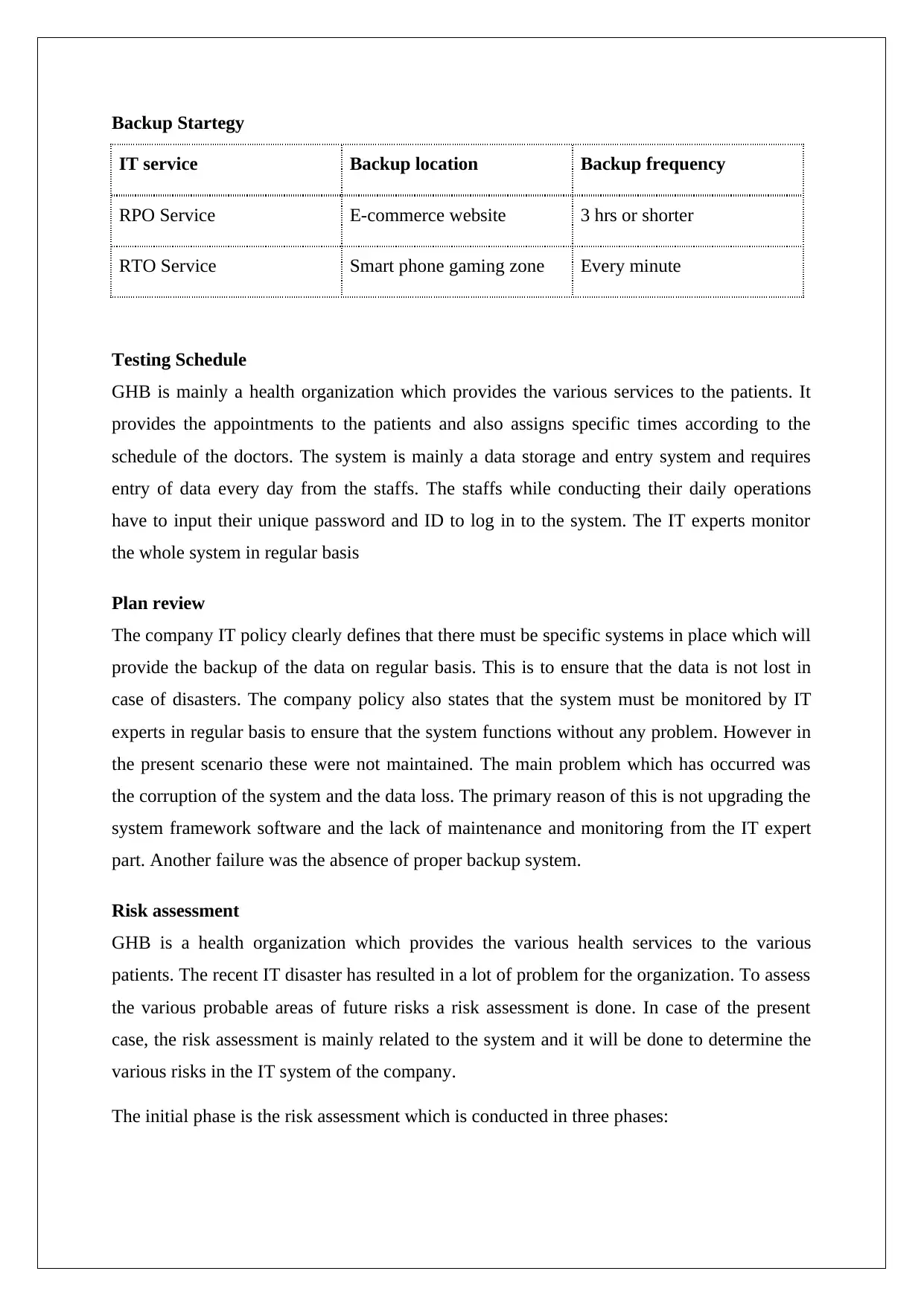
Backup Startegy
IT service Backup location Backup frequency
RPO Service E-commerce website 3 hrs or shorter
RTO Service Smart phone gaming zone Every minute
Testing Schedule
GHB is mainly a health organization which provides the various services to the patients. It
provides the appointments to the patients and also assigns specific times according to the
schedule of the doctors. The system is mainly a data storage and entry system and requires
entry of data every day from the staffs. The staffs while conducting their daily operations
have to input their unique password and ID to log in to the system. The IT experts monitor
the whole system in regular basis
Plan review
The company IT policy clearly defines that there must be specific systems in place which will
provide the backup of the data on regular basis. This is to ensure that the data is not lost in
case of disasters. The company policy also states that the system must be monitored by IT
experts in regular basis to ensure that the system functions without any problem. However in
the present scenario these were not maintained. The main problem which has occurred was
the corruption of the system and the data loss. The primary reason of this is not upgrading the
system framework software and the lack of maintenance and monitoring from the IT expert
part. Another failure was the absence of proper backup system.
Risk assessment
GHB is a health organization which provides the various health services to the various
patients. The recent IT disaster has resulted in a lot of problem for the organization. To assess
the various probable areas of future risks a risk assessment is done. In case of the present
case, the risk assessment is mainly related to the system and it will be done to determine the
various risks in the IT system of the company.
The initial phase is the risk assessment which is conducted in three phases:
IT service Backup location Backup frequency
RPO Service E-commerce website 3 hrs or shorter
RTO Service Smart phone gaming zone Every minute
Testing Schedule
GHB is mainly a health organization which provides the various services to the patients. It
provides the appointments to the patients and also assigns specific times according to the
schedule of the doctors. The system is mainly a data storage and entry system and requires
entry of data every day from the staffs. The staffs while conducting their daily operations
have to input their unique password and ID to log in to the system. The IT experts monitor
the whole system in regular basis
Plan review
The company IT policy clearly defines that there must be specific systems in place which will
provide the backup of the data on regular basis. This is to ensure that the data is not lost in
case of disasters. The company policy also states that the system must be monitored by IT
experts in regular basis to ensure that the system functions without any problem. However in
the present scenario these were not maintained. The main problem which has occurred was
the corruption of the system and the data loss. The primary reason of this is not upgrading the
system framework software and the lack of maintenance and monitoring from the IT expert
part. Another failure was the absence of proper backup system.
Risk assessment
GHB is a health organization which provides the various health services to the various
patients. The recent IT disaster has resulted in a lot of problem for the organization. To assess
the various probable areas of future risks a risk assessment is done. In case of the present
case, the risk assessment is mainly related to the system and it will be done to determine the
various risks in the IT system of the company.
The initial phase is the risk assessment which is conducted in three phases:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

System Documentation Phase- In this phase the whole system is analyzed. It is
particularly important as it will help to determine the possible areas where there may
be some flaws or loopholes (Castelli et al., 2017). This phase also provides the
detailed information about the list of people who are associated with the system and
their roles (Haimes, 2015). In case of GHB the system is mainly an information which
stores data of the patients as well as assigns the various appointments of doctors to the
patients. Thepeople associated with the system are the staffs entering the data, the IT
experts managing the system as well as the administrators.
Risk Determination Phase- The risks in the system are identified in this phase
(Joodi, 2015). From the analysis of the operational system as well as the disaster
various important information was gained (Sadgrove,2016). There were no risk on the
side of the employees as the data was safe. The main problem occurred after the
corruption of the system. Possible causes are using an outdated system, inadequate
reporting of the flaw by the IT expert and lack of regular inspection. The data loss
would have been avoided if the company’s data backup policy was strictly maintained
by the IT experts.
Safeguard Determination Phase- After determining the risks and the various
problems of the system, this phase is solely dedicated to provide the various areas of
improvement of the system (Peltier, 2016). From the above discussion it can be easily
said GHB must review its existing backup policies and the IT system and upgrade the
whole system to avoid all the future risks. If necessary, the organization may change
the IT experts and employ new experts. The whole plan must be implemented and
strictly monitored on regular basis to mitigate future occurrences of risk in the
organization (Alles et al., 2018).
Business Impact Analysis (BIA)
In this portion the critical process of the business which has the highest impact on the
organization is assessed (Torabi, et al., 2014). In case of GHB the BIA is as follows:
1. Business process and functions- Data entry, storage and retrieval.
2. Business recovery- Proper backup system of the data. Upgraded framework.
3. Resource interdependencies- The staffs are dependent on the software system and the
software system is mainly dependent on the proper maintenance by the IT experts.
4. Impact on operations- Improper handling and outdated system will result in the
overall disruption of the total operation of the whole organization.
particularly important as it will help to determine the possible areas where there may
be some flaws or loopholes (Castelli et al., 2017). This phase also provides the
detailed information about the list of people who are associated with the system and
their roles (Haimes, 2015). In case of GHB the system is mainly an information which
stores data of the patients as well as assigns the various appointments of doctors to the
patients. Thepeople associated with the system are the staffs entering the data, the IT
experts managing the system as well as the administrators.
Risk Determination Phase- The risks in the system are identified in this phase
(Joodi, 2015). From the analysis of the operational system as well as the disaster
various important information was gained (Sadgrove,2016). There were no risk on the
side of the employees as the data was safe. The main problem occurred after the
corruption of the system. Possible causes are using an outdated system, inadequate
reporting of the flaw by the IT expert and lack of regular inspection. The data loss
would have been avoided if the company’s data backup policy was strictly maintained
by the IT experts.
Safeguard Determination Phase- After determining the risks and the various
problems of the system, this phase is solely dedicated to provide the various areas of
improvement of the system (Peltier, 2016). From the above discussion it can be easily
said GHB must review its existing backup policies and the IT system and upgrade the
whole system to avoid all the future risks. If necessary, the organization may change
the IT experts and employ new experts. The whole plan must be implemented and
strictly monitored on regular basis to mitigate future occurrences of risk in the
organization (Alles et al., 2018).
Business Impact Analysis (BIA)
In this portion the critical process of the business which has the highest impact on the
organization is assessed (Torabi, et al., 2014). In case of GHB the BIA is as follows:
1. Business process and functions- Data entry, storage and retrieval.
2. Business recovery- Proper backup system of the data. Upgraded framework.
3. Resource interdependencies- The staffs are dependent on the software system and the
software system is mainly dependent on the proper maintenance by the IT experts.
4. Impact on operations- Improper handling and outdated system will result in the
overall disruption of the total operation of the whole organization.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
5. Priorities- Maintenance of the system in regular basis.
6. Recovery time- The backup must be done regularly and the recovery after a disaster
must be done after the correction of the problem.
7. Impact on disruption- The disruption in the system may result in the loss of the patient
data. It will result in the overall financial loss of the company and will totally stop the
ongoing operation.
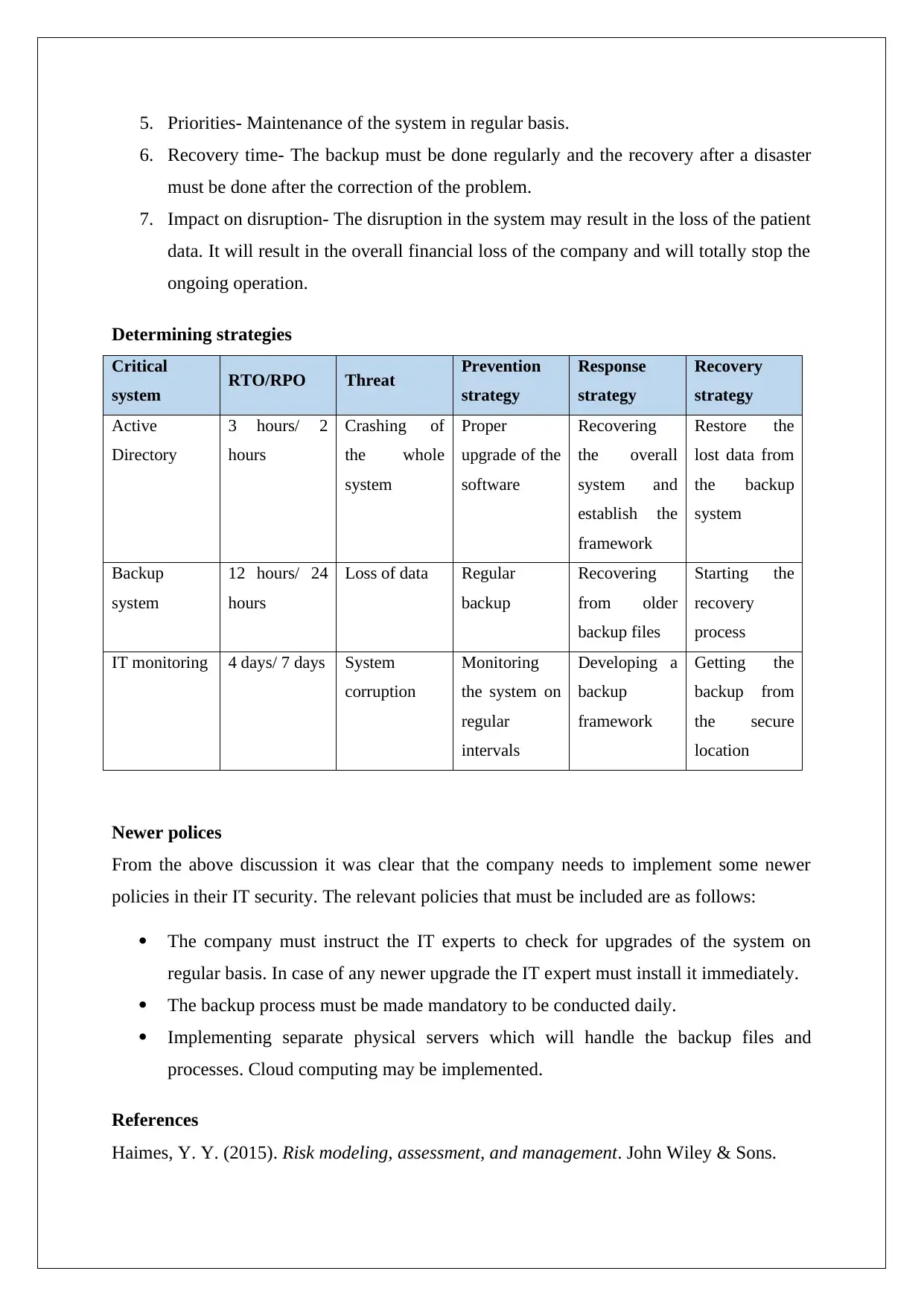
Determining strategies
Critical
system RTO/RPO Threat Prevention
strategy
Response
strategy
Recovery
strategy
Active
Directory
3 hours/ 2
hours
Crashing of
the whole
system
Proper
upgrade of the
software
Recovering
the overall
system and
establish the
framework
Restore the
lost data from
the backup
system
Backup
system
12 hours/ 24
hours
Loss of data Regular
backup
Recovering
from older
backup files
Starting the
recovery
process
IT monitoring 4 days/ 7 days System
corruption
Monitoring
the system on
regular
intervals
Developing a
backup
framework
Getting the
backup from
the secure
location
Newer polices
From the above discussion it was clear that the company needs to implement some newer
policies in their IT security. The relevant policies that must be included are as follows:
The company must instruct the IT experts to check for upgrades of the system on
regular basis. In case of any newer upgrade the IT expert must install it immediately.
The backup process must be made mandatory to be conducted daily.
Implementing separate physical servers which will handle the backup files and
processes. Cloud computing may be implemented.
References
Haimes, Y. Y. (2015). Risk modeling, assessment, and management. John Wiley & Sons.
6. Recovery time- The backup must be done regularly and the recovery after a disaster
must be done after the correction of the problem.
7. Impact on disruption- The disruption in the system may result in the loss of the patient
data. It will result in the overall financial loss of the company and will totally stop the
ongoing operation.
Determining strategies
Critical
system RTO/RPO Threat Prevention
strategy
Response
strategy
Recovery
strategy
Active
Directory
3 hours/ 2
hours
Crashing of
the whole
system
Proper
upgrade of the
software
Recovering
the overall
system and
establish the
framework
Restore the
lost data from
the backup
system
Backup
system
12 hours/ 24
hours
Loss of data Regular
backup
Recovering
from older
backup files
Starting the
recovery
process
IT monitoring 4 days/ 7 days System
corruption
Monitoring
the system on
regular
intervals
Developing a
backup
framework
Getting the
backup from
the secure
location
Newer polices
From the above discussion it was clear that the company needs to implement some newer
policies in their IT security. The relevant policies that must be included are as follows:
The company must instruct the IT experts to check for upgrades of the system on
regular basis. In case of any newer upgrade the IT expert must install it immediately.
The backup process must be made mandatory to be conducted daily.
Implementing separate physical servers which will handle the backup files and
processes. Cloud computing may be implemented.
References
Haimes, Y. Y. (2015). Risk modeling, assessment, and management. John Wiley & Sons.

Torabi, S. A., Soufi, H. R., &Sahebjamnia, N. (2014). A new framework for business impact
analysis in business continuity management (with a case study). Safety Science, 68,
(309-323).
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines
for effective information security management. Auerbach Publications.
Sadgrove, K. (2016). The complete guide to business risk management. Routledge.
Borgianni, Y., Cascini, G., & Rotini, F. (2015). Business process reengineering driven by
customer value: a support for undertaking decisions under uncertainty
conditions. Computers in Industry, 68, (132-147).
Alles, M., Brennan, G., Kogan, A., &Vasarhelyi, M. A. (2018). Continuous monitoring of
business process controls: A pilot implementation of a continuous auditing system at
Siemens. In Continuous Auditing: Theory and Application (pp. 219-246). Emerald
Publishing Limited.
Castelli, V., Florian, R., Moon, T., &Sil, A. (2017). U.S. Patent Application No. 15/075,262.
Joodi, P. M. (2015). U.S. Patent No. 9,202,182. Washington, DC: U.S. Patent and Trademark
Office.
analysis in business continuity management (with a case study). Safety Science, 68,
(309-323).
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines
for effective information security management. Auerbach Publications.
Sadgrove, K. (2016). The complete guide to business risk management. Routledge.
Borgianni, Y., Cascini, G., & Rotini, F. (2015). Business process reengineering driven by
customer value: a support for undertaking decisions under uncertainty
conditions. Computers in Industry, 68, (132-147).
Alles, M., Brennan, G., Kogan, A., &Vasarhelyi, M. A. (2018). Continuous monitoring of
business process controls: A pilot implementation of a continuous auditing system at
Siemens. In Continuous Auditing: Theory and Application (pp. 219-246). Emerald
Publishing Limited.
Castelli, V., Florian, R., Moon, T., &Sil, A. (2017). U.S. Patent Application No. 15/075,262.
Joodi, P. M. (2015). U.S. Patent No. 9,202,182. Washington, DC: U.S. Patent and Trademark
Office.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


