HI5019 Strategic Information Systems Case Study: Giant Eggplant Review
VerifiedAdded on 2022/08/31
|14
|2878
|20
Case Study
AI Summary
This case study examines the strategic information systems of Giant Eggplant, a company facing challenges due to its manual business processes. The report analyzes the company's revenue and expenditure cycles, highlighting weaknesses in internal controls and the inefficiencies of manual document management. It includes data flow diagrams for both cycles and identifies issues such as inefficient register management, lack of a centralized transaction system, and difficulties in information updating and retrieval. The report then proposes IT controls, including audit logs, information security measures, and incident management strategies, to address these weaknesses and improve the company's overall efficiency and security. The IT controls include audit logs for recording system events, information security measures to protect against threats, and incident management protocols for handling errors and disruptions. The conclusion emphasizes the need for the company to adopt these IT solutions to streamline its operations and improve its business structure.

Running head: STRATEGIC INFORMATION SYSTEMS FOR BUSINESS AND
ENTERPRISE
STRATEGIC INFORMATION SYSTEMS FOR BUSINESS AND ENTERPRISE
Name of student
Name of university
Author’s note:
ENTERPRISE
STRATEGIC INFORMATION SYSTEMS FOR BUSINESS AND ENTERPRISE
Name of student
Name of university
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
STRATEGIC INFORMATION SYSTEMS FOR BUSINESS AND ENTERPRISE
Table of Contents
Introduction....................................................................................................................2
Discussion......................................................................................................................3
Data flow diagrams........................................................................................................3
Data flow diagram of revenue cycle..........................................................................3
Data flow diagram of expenditure cycle....................................................................4
Analysis of physical internal control weaknesses......................................................4
Description of IT controls..........................................................................................5
Conclusion......................................................................................................................9
References....................................................................................................................10
STRATEGIC INFORMATION SYSTEMS FOR BUSINESS AND ENTERPRISE
Table of Contents
Introduction....................................................................................................................2
Discussion......................................................................................................................3
Data flow diagrams........................................................................................................3
Data flow diagram of revenue cycle..........................................................................3
Data flow diagram of expenditure cycle....................................................................4
Analysis of physical internal control weaknesses......................................................4
Description of IT controls..........................................................................................5
Conclusion......................................................................................................................9
References....................................................................................................................10

2
STRATEGIC INFORMATION SYSTEMS FOR BUSINESS AND ENTERPRISE
Introduction
The introduction of various technologies in the modern businesses has led to the
revolutionised the methods by which the businesses functions. Giant eggplant is a company
that offers various products ranging from dairy, agricultural as well as bakery from the local
bakeries as well as factories. Presently the company utilises the manual methods of managing
the business and it has been noticed by the administration, that the business is not generating
adequate revenue from the business. This report intends to analyse the present weaknesses in
the business and recommend various solutions to the company that could be implemented.
This report concludes with an appropriate conclusion.
STRATEGIC INFORMATION SYSTEMS FOR BUSINESS AND ENTERPRISE
Introduction
The introduction of various technologies in the modern businesses has led to the
revolutionised the methods by which the businesses functions. Giant eggplant is a company
that offers various products ranging from dairy, agricultural as well as bakery from the local
bakeries as well as factories. Presently the company utilises the manual methods of managing
the business and it has been noticed by the administration, that the business is not generating
adequate revenue from the business. This report intends to analyse the present weaknesses in
the business and recommend various solutions to the company that could be implemented.
This report concludes with an appropriate conclusion.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
STRATEGIC INFORMATION SYSTEMS FOR BUSINESS AND ENTERPRISE
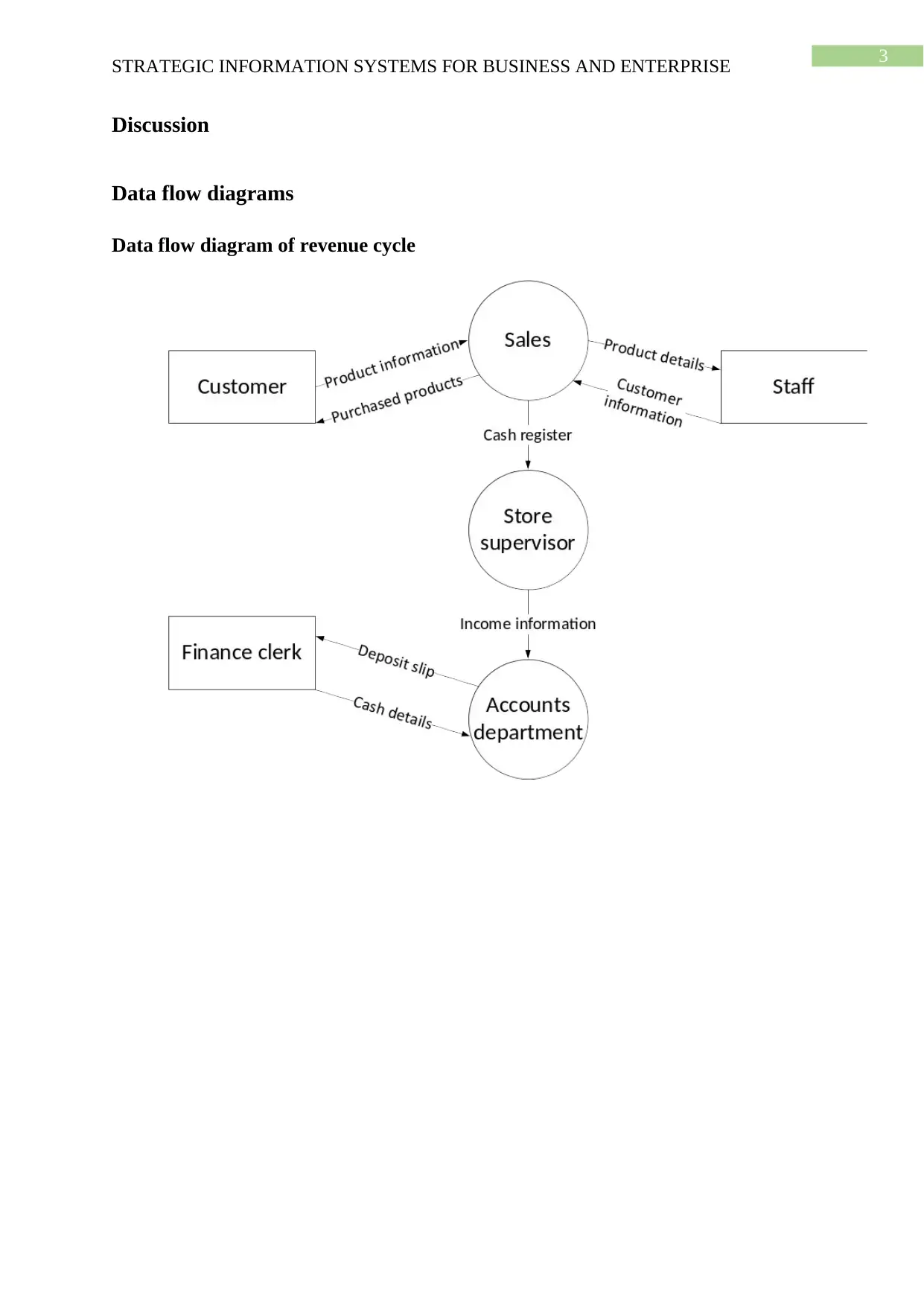
Discussion
Data flow diagrams
Data flow diagram of revenue cycle
STRATEGIC INFORMATION SYSTEMS FOR BUSINESS AND ENTERPRISE
Discussion
Data flow diagrams
Data flow diagram of revenue cycle
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
STRATEGIC INFORMATION SYSTEMS FOR BUSINESS AND ENTERPRISE
Data flow diagram of expenditure cycle
Analysis of physical internal control weaknesses
The company consists of revenue cycle and the expenditure cycle. The manual
process in the company of managing the registers is causing significant efficiency issues in
the company. The staff of the company are not able to manage the registers efficiently. The
company does not have any centralised system in place for managing all the transactions that
are made by the customers. It could be considered that the company faced minimal
difficulties in the initial stages but with the increase of the customer base of this company, the
management of finance as well as accounts of the company became significantly difficult.
The company manages a ledger of all the transaction made in the sales department and the
finance department. The main downfall of the manual document filling is amount of the
space that is taken by the documents. With the increase of the customers in the business, the
management of documents has become significantly troublesome and the frequency of
STRATEGIC INFORMATION SYSTEMS FOR BUSINESS AND ENTERPRISE
Data flow diagram of expenditure cycle
Analysis of physical internal control weaknesses
The company consists of revenue cycle and the expenditure cycle. The manual
process in the company of managing the registers is causing significant efficiency issues in
the company. The staff of the company are not able to manage the registers efficiently. The
company does not have any centralised system in place for managing all the transactions that
are made by the customers. It could be considered that the company faced minimal
difficulties in the initial stages but with the increase of the customer base of this company, the
management of finance as well as accounts of the company became significantly difficult.
The company manages a ledger of all the transaction made in the sales department and the
finance department. The main downfall of the manual document filling is amount of the
space that is taken by the documents. With the increase of the customers in the business, the
management of documents has become significantly troublesome and the frequency of

5
STRATEGIC INFORMATION SYSTEMS FOR BUSINESS AND ENTERPRISE
document misplacing has increased significantly. With the increase in the frequency of
document misplacing, the productivity of the company has been damaged severely.
The manual document filling in the company denotes that the company has put
significant faith on the people who are handling the files. There are several ways by which
the documents could be misplaced, lost or even damaged. Once, the files are damaged, the
information retrieval is significantly difficult and it leads to mishandling of information of the
organisation. Presently, the company faces significant issues with the information updating as
the manual system does not permit the information updating. The manual document filing of
the company has been observed to be immensely time consuming. Not solely the company
needs to organise as well as store all the files, tracking down the information in the time of
need has been observed to be significantly difficult. The sales staff of the company faces
severe issues while searching for the files or even providing the optimal services to the
customers.
Description of IT controls
IT controls could be described as the policies, procedures as well as activities that are
mainly conducted in the company for meeting the IT objectives, manage the risks, comply
with the regulations as well as conform to the standards. The automation of the controls or
the human activities could be done. All these aspects could be driven by the requirements, the
calendars, processes or the events. The high level management practices could be the controls
or it could be low level management. The controls that are required to be implemented in the
company could be categorised as:
Audit log: The audit log could be described as the document that efficiently records
any event in the IT system of the company. Additionally, along with the addition of
documentation of accessing of the resources of the company, the entries in the audit log
STRATEGIC INFORMATION SYSTEMS FOR BUSINESS AND ENTERPRISE
document misplacing has increased significantly. With the increase in the frequency of
document misplacing, the productivity of the company has been damaged severely.
The manual document filling in the company denotes that the company has put
significant faith on the people who are handling the files. There are several ways by which
the documents could be misplaced, lost or even damaged. Once, the files are damaged, the
information retrieval is significantly difficult and it leads to mishandling of information of the
organisation. Presently, the company faces significant issues with the information updating as
the manual system does not permit the information updating. The manual document filing of
the company has been observed to be immensely time consuming. Not solely the company
needs to organise as well as store all the files, tracking down the information in the time of
need has been observed to be significantly difficult. The sales staff of the company faces
severe issues while searching for the files or even providing the optimal services to the
customers.
Description of IT controls
IT controls could be described as the policies, procedures as well as activities that are
mainly conducted in the company for meeting the IT objectives, manage the risks, comply
with the regulations as well as conform to the standards. The automation of the controls or
the human activities could be done. All these aspects could be driven by the requirements, the
calendars, processes or the events. The high level management practices could be the controls
or it could be low level management. The controls that are required to be implemented in the
company could be categorised as:
Audit log: The audit log could be described as the document that efficiently records
any event in the IT system of the company. Additionally, along with the addition of
documentation of accessing of the resources of the company, the entries in the audit log
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
STRATEGIC INFORMATION SYSTEMS FOR BUSINESS AND ENTERPRISE
mainly includes the source as well as the destination addresses, the timestamp as well as the
information of the user login (Rose et al. 2017). The audit log is also referred as the
chronological record that are related to the security of the company, set of records or the
source and destination of the records that offers the evidence of documentary of main
sequence of the activities that have mainly affected the people at any point of time during any
particular, procedure, event or operation (Cheng, Xu and Gong 2016). The audit records
mainly result from the activities like the financial transactions and the sales data in the
company. The procedure that develops the audit log is commonly required to execute in the
privileged mode, for allowing the accessing as well as supervising all the actions from the
users (Le, Mitchell and Arad 2019). Moreover, for similar reason, the trail file or the database
table with the trail is not needed to be accessible to the normal users (Zhao et al. 2018). One
more method of handling the issue is with the user of role-based security model integrated in
all the software of the organisation (Amir-Mohammadian, Chong and Skalka 2016).
Information security: The aspect of information security could be described as the
collection of strategies that are used for the management of processes, policies as well as
tools required for preventing, detecting, documenting as well as countering the threats to the
non-digital as well as digital information (Peltier 2016). The responsibilities in the
information security mainly includes the establishment of appropriate set of appropriate
business processes that would help in protecting the information assets, in spite of the method
of formatting of the information or even in the transit (Safa, Von Solms and Furnell 2016).
Several large corporations hire an appropriate security group for implementing as well as
maintaining the information security programs of the companies. Commonly, this particular
group is led by the chief information security officer (Soomro, Shah and Ahmed 2016).
This particular security group is commonly accountable for the execution of risk
management, which is the procedure of assessment of the threats and the vulnerabilities of
STRATEGIC INFORMATION SYSTEMS FOR BUSINESS AND ENTERPRISE
mainly includes the source as well as the destination addresses, the timestamp as well as the
information of the user login (Rose et al. 2017). The audit log is also referred as the
chronological record that are related to the security of the company, set of records or the
source and destination of the records that offers the evidence of documentary of main
sequence of the activities that have mainly affected the people at any point of time during any
particular, procedure, event or operation (Cheng, Xu and Gong 2016). The audit records
mainly result from the activities like the financial transactions and the sales data in the
company. The procedure that develops the audit log is commonly required to execute in the
privileged mode, for allowing the accessing as well as supervising all the actions from the
users (Le, Mitchell and Arad 2019). Moreover, for similar reason, the trail file or the database
table with the trail is not needed to be accessible to the normal users (Zhao et al. 2018). One
more method of handling the issue is with the user of role-based security model integrated in
all the software of the organisation (Amir-Mohammadian, Chong and Skalka 2016).
Information security: The aspect of information security could be described as the
collection of strategies that are used for the management of processes, policies as well as
tools required for preventing, detecting, documenting as well as countering the threats to the
non-digital as well as digital information (Peltier 2016). The responsibilities in the
information security mainly includes the establishment of appropriate set of appropriate
business processes that would help in protecting the information assets, in spite of the method
of formatting of the information or even in the transit (Safa, Von Solms and Furnell 2016).
Several large corporations hire an appropriate security group for implementing as well as
maintaining the information security programs of the companies. Commonly, this particular
group is led by the chief information security officer (Soomro, Shah and Ahmed 2016).
This particular security group is commonly accountable for the execution of risk
management, which is the procedure of assessment of the threats and the vulnerabilities of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
STRATEGIC INFORMATION SYSTEMS FOR BUSINESS AND ENTERPRISE
the information assets (Safa and Von Solms 2016). The information security programs could
be developed in the company around the core objectives of CIA triad, managing the integrity,
confidentiality as well as the availability of IT systems as well as the business data. These
particular objectives mainly ensures that all the sensitive information could be only disclosed
to the authorised parties, prevent any unauthorised modification of the data of the company as
well as ensure that the data could be solely accessed by the authorised parties when it is
requested (McCormac et al. 2017).
The initial consideration, which is the confidentiality, commonly needs the proper
utilisation of the encryption keys as well as encryption. Second consideration, which is
integrity mainly implies that during the reading back of data, it would be specifically similar
as when it had been written. Third part includes the availability. This prospect of the principle
mainly seeks to ensure that any new data could be utilised in proper manner as well as the
restoring of backup data could be done in the acceptable recovery time. The major threats to
the sensitive as well as the private information could originate in various forms in the
company like phishing and malware attacks, ransomware or identity theft. For deterring the
attackers as well as mitigate the vulnerability at several points, multiple security controls
could be implemented as well as coordinated as the part of the layered defense in the depth
strategy. It could help in minimising the main impact of any attack. For being effectively
prepared for any security breach, the security groups of the company should possess the
incident response plan. It would allow the company with containing as well as restricting the
damage, eliminate the main cause as well as implement the appropriate defence controls.
The information security of the company could possess all the processes as well as
policies that commonly includes the physical as well as the digital security measures for
protecting the data from any kind of unauthorised access, utilisation, replication or even the
destruction. The measures that could be applied in the company are the mantraps, the
STRATEGIC INFORMATION SYSTEMS FOR BUSINESS AND ENTERPRISE
the information assets (Safa and Von Solms 2016). The information security programs could
be developed in the company around the core objectives of CIA triad, managing the integrity,
confidentiality as well as the availability of IT systems as well as the business data. These
particular objectives mainly ensures that all the sensitive information could be only disclosed
to the authorised parties, prevent any unauthorised modification of the data of the company as
well as ensure that the data could be solely accessed by the authorised parties when it is
requested (McCormac et al. 2017).
The initial consideration, which is the confidentiality, commonly needs the proper
utilisation of the encryption keys as well as encryption. Second consideration, which is
integrity mainly implies that during the reading back of data, it would be specifically similar
as when it had been written. Third part includes the availability. This prospect of the principle
mainly seeks to ensure that any new data could be utilised in proper manner as well as the
restoring of backup data could be done in the acceptable recovery time. The major threats to
the sensitive as well as the private information could originate in various forms in the
company like phishing and malware attacks, ransomware or identity theft. For deterring the
attackers as well as mitigate the vulnerability at several points, multiple security controls
could be implemented as well as coordinated as the part of the layered defense in the depth
strategy. It could help in minimising the main impact of any attack. For being effectively
prepared for any security breach, the security groups of the company should possess the
incident response plan. It would allow the company with containing as well as restricting the
damage, eliminate the main cause as well as implement the appropriate defence controls.
The information security of the company could possess all the processes as well as
policies that commonly includes the physical as well as the digital security measures for
protecting the data from any kind of unauthorised access, utilisation, replication or even the
destruction. The measures that could be applied in the company are the mantraps, the

8
STRATEGIC INFORMATION SYSTEMS FOR BUSINESS AND ENTERPRISE
encryption keys management, the network intrusion detection systems, the password policies
as well as the regulatory compliance.
Incident management: The error logs of the major applications of the organisation are
extensively monitored for any kind of severe errors. The incident tickets could be easily
created when these kinds of errors happens (Brownstone et al. 2017). Any incident could be
described as the event that can lead to the loss of or even the disruption to the operations,
services or the functions of the orgnaisaitons.
The incident management could be referred as the term that is mainly used for
describing all the activities of any organisation for identifying, analysing as well as correcting
the hazards for preventing any future re-occurrence. These incidents would be considered as
the events that takes place in any organisation and it is mainly dealt by the incident response
team (Flin, Lauche and Crichton 2017). The incident management at any organisation is
executed in stages, that includes the incident logging, incident classification, incident
prioritisation, investigation and diagnosis and the incident resolution and closure. In the stage
of incident logging, the identified incident is reported in the company. It is mainly executed
by any of end users themselves or the agents could execute it on their behalf. It is required
from the IT team to efficiently capture the complete information regarding the incident by
using the form template for speeding up the recovery process (Palilingan and Batmetan
2018). It is also required to establish connected channels for the end users for reporting any
issue directly.
The next stage in the incident management is the incident classification. The incidents
are segmented with the appropriate category for easily identifying the correct agent and the
group (Cao and Zhang 2016). The incident form is customised with the correct fields and
then establish the automated rules for the ticket classification, the prioritisation as well as the
STRATEGIC INFORMATION SYSTEMS FOR BUSINESS AND ENTERPRISE
encryption keys management, the network intrusion detection systems, the password policies
as well as the regulatory compliance.
Incident management: The error logs of the major applications of the organisation are
extensively monitored for any kind of severe errors. The incident tickets could be easily
created when these kinds of errors happens (Brownstone et al. 2017). Any incident could be
described as the event that can lead to the loss of or even the disruption to the operations,
services or the functions of the orgnaisaitons.
The incident management could be referred as the term that is mainly used for
describing all the activities of any organisation for identifying, analysing as well as correcting
the hazards for preventing any future re-occurrence. These incidents would be considered as
the events that takes place in any organisation and it is mainly dealt by the incident response
team (Flin, Lauche and Crichton 2017). The incident management at any organisation is
executed in stages, that includes the incident logging, incident classification, incident
prioritisation, investigation and diagnosis and the incident resolution and closure. In the stage
of incident logging, the identified incident is reported in the company. It is mainly executed
by any of end users themselves or the agents could execute it on their behalf. It is required
from the IT team to efficiently capture the complete information regarding the incident by
using the form template for speeding up the recovery process (Palilingan and Batmetan
2018). It is also required to establish connected channels for the end users for reporting any
issue directly.
The next stage in the incident management is the incident classification. The incidents
are segmented with the appropriate category for easily identifying the correct agent and the
group (Cao and Zhang 2016). The incident form is customised with the correct fields and
then establish the automated rules for the ticket classification, the prioritisation as well as the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
STRATEGIC INFORMATION SYSTEMS FOR BUSINESS AND ENTERPRISE
assignment and then save significantly valuable time in process. With the help of proper
classification of all the incidents, the report generation could be done faster. The next stage in
the incident management is the incident prioritisation (Aguiar et al. 2018). The task of
assigning the correct priority to the appropriate ticket makes direct impact on the decision of
SLA policy as well as addressing the business critical issues in the appropriate time.
In the stage of investigation and diagnosis, when any incident has been raised, the
initial analysis is performed by the IT team and then the resolution is sent to end user. In
event of the unavailability of immediate resolution, the incident is escalated to the tier II for
conducting the brief investigation. The review of the components that are required to be
identified, analysed as well as contained of any incident is done. Incident that is associated
with connected CI is also done for executing the faster diagnosis. Among the primary goals
of the IT team, the main aspect is resolving any incident that is presented to them. It has been
observed that the effective communication regarding the resolution as well as closure of
resolved tickets is significant vital. The process of closing could also be automated by the
team.
Conclusion
Therefore, it could be concluded that that presently the company is having significant
issues in their business structure and it needs to improve the methods by which business is
done. The manual process in the company of managing the registers is causing significant
efficiency issues in the company. The staff of the company are not able to manage the
registers efficiently. The company does not have any centralised system in place for
managing all the transactions that are made by the customers. IT controls could be described
as the policies, procedures as well as activities that are mainly conducted in the company for
STRATEGIC INFORMATION SYSTEMS FOR BUSINESS AND ENTERPRISE
assignment and then save significantly valuable time in process. With the help of proper
classification of all the incidents, the report generation could be done faster. The next stage in
the incident management is the incident prioritisation (Aguiar et al. 2018). The task of
assigning the correct priority to the appropriate ticket makes direct impact on the decision of
SLA policy as well as addressing the business critical issues in the appropriate time.
In the stage of investigation and diagnosis, when any incident has been raised, the
initial analysis is performed by the IT team and then the resolution is sent to end user. In
event of the unavailability of immediate resolution, the incident is escalated to the tier II for
conducting the brief investigation. The review of the components that are required to be
identified, analysed as well as contained of any incident is done. Incident that is associated
with connected CI is also done for executing the faster diagnosis. Among the primary goals
of the IT team, the main aspect is resolving any incident that is presented to them. It has been
observed that the effective communication regarding the resolution as well as closure of
resolved tickets is significant vital. The process of closing could also be automated by the
team.
Conclusion
Therefore, it could be concluded that that presently the company is having significant
issues in their business structure and it needs to improve the methods by which business is
done. The manual process in the company of managing the registers is causing significant
efficiency issues in the company. The staff of the company are not able to manage the
registers efficiently. The company does not have any centralised system in place for
managing all the transactions that are made by the customers. IT controls could be described
as the policies, procedures as well as activities that are mainly conducted in the company for
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
STRATEGIC INFORMATION SYSTEMS FOR BUSINESS AND ENTERPRISE
meeting the IT objectives, manage the risks, comply with the regulations as well as conform
to the standards.
STRATEGIC INFORMATION SYSTEMS FOR BUSINESS AND ENTERPRISE
meeting the IT objectives, manage the risks, comply with the regulations as well as conform
to the standards.

11
STRATEGIC INFORMATION SYSTEMS FOR BUSINESS AND ENTERPRISE
References
Rose, I., Felts, N., George, A., Miller, E. and Planck, M., 2017, September. Something is
better than everything: A distributed approach to audit log anomaly detection. In 2017 IEEE
Cybersecurity Development (SecDev) (pp. 77-82). IEEE.
Le, T., Mitchell, W. and Arad, B., 2019. Customized Intrusion Detection Based on a
Database Audit Log. Proceedings of 34th International Confer, 58, pp.117-126.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. Auerbach Publications.
Safa, N.S., Von Solms, R. and Furnell, S., 2016. Information security policy compliance
model in organizations. computers & security, 56, pp.70-82.
Soomro, Z.A., Shah, M.H. and Ahmed, J., 2016. Information security management needs
more holistic approach: A literature review. International Journal of Information
Management, 36(2), pp.215-225.
Safa, N.S. and Von Solms, R., 2016. An information security knowledge sharing model in
organizations. Computers in Human Behavior, 57, pp.442-451.
McCormac, A., Zwaans, T., Parsons, K., Calic, D., Butavicius, M. and Pattinson, M., 2017.
Individual differences and information security awareness. Computers in Human
Behavior, 69, pp.151-156.
Brownstone, D., McBride, M., Mahmassani, A. and Kong, S.Y., 2017. Experimental Studies
of Traffic Incident Management with Pricing, Private Information, and Diverse Subjects.
STRATEGIC INFORMATION SYSTEMS FOR BUSINESS AND ENTERPRISE
References
Rose, I., Felts, N., George, A., Miller, E. and Planck, M., 2017, September. Something is
better than everything: A distributed approach to audit log anomaly detection. In 2017 IEEE
Cybersecurity Development (SecDev) (pp. 77-82). IEEE.
Le, T., Mitchell, W. and Arad, B., 2019. Customized Intrusion Detection Based on a
Database Audit Log. Proceedings of 34th International Confer, 58, pp.117-126.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. Auerbach Publications.
Safa, N.S., Von Solms, R. and Furnell, S., 2016. Information security policy compliance
model in organizations. computers & security, 56, pp.70-82.
Soomro, Z.A., Shah, M.H. and Ahmed, J., 2016. Information security management needs
more holistic approach: A literature review. International Journal of Information
Management, 36(2), pp.215-225.
Safa, N.S. and Von Solms, R., 2016. An information security knowledge sharing model in
organizations. Computers in Human Behavior, 57, pp.442-451.
McCormac, A., Zwaans, T., Parsons, K., Calic, D., Butavicius, M. and Pattinson, M., 2017.
Individual differences and information security awareness. Computers in Human
Behavior, 69, pp.151-156.
Brownstone, D., McBride, M., Mahmassani, A. and Kong, S.Y., 2017. Experimental Studies
of Traffic Incident Management with Pricing, Private Information, and Diverse Subjects.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





