Cyber Security Report: GitHub 1.35 TBPS DDoS Attack Analysis
VerifiedAdded on 2023/04/11
|13
|2099
|392
Report
AI Summary
This report provides an in-depth analysis of a Distributed Denial of Service (DDoS) attack on GitHub, specifically the 1.35 TBPS attack. It begins with an introduction to cyberattacks and DDoS, then delves into the chosen attack type, explaining its real-world operation and the stages involved. The report details the attack, including the exploitation of Memcached servers, and outlines its impact on GitHub, including service outages and potential consequences. It also examines the aim of the security breach and the resulting consequences, such as loss of reputation and financial implications. Finally, the report concludes with a discussion of various methods to mitigate such attacks, including disabling UDP ports, firewalling Memcached servers, preventing IP spoofing, and developing software to reduce UDP response. The report underscores the importance of cybersecurity measures in preventing and responding to DDoS attacks.

Running head: CYBER SECURITY
Cyber Security
Name of the Student
Name of the University
Author Note:
Cyber Security
Name of the Student
Name of the University
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CYBER SECURITY
Table of Contents
Introduction......................................................................................................................................2
Discussion........................................................................................................................................2
CHOSEN ATTACK TYPE OPERATES IN REAL WORLD....................................................2
Stages of GITHUB: 1.35 TBPS Attack.......................................................................................3
Details of Attack (Answer to Question 1)...................................................................................4
Outcome of GITHUB: 1.35 TBPS Attack (Answer to Question 2)............................................4
Impact of the attack (Answer to Question 3)...............................................................................6
Aim of security breach and result of consequence (Answer to Question 4)...............................7
Methods of mitigating the issue (Answer to Question 5)............................................................8
Conclusion.....................................................................................................................................10
References......................................................................................................................................11
Table of Contents
Introduction......................................................................................................................................2
Discussion........................................................................................................................................2
CHOSEN ATTACK TYPE OPERATES IN REAL WORLD....................................................2
Stages of GITHUB: 1.35 TBPS Attack.......................................................................................3
Details of Attack (Answer to Question 1)...................................................................................4
Outcome of GITHUB: 1.35 TBPS Attack (Answer to Question 2)............................................4
Impact of the attack (Answer to Question 3)...............................................................................6
Aim of security breach and result of consequence (Answer to Question 4)...............................7
Methods of mitigating the issue (Answer to Question 5)............................................................8
Conclusion.....................................................................................................................................10
References......................................................................................................................................11

2CYBER SECURITY
Introduction
Cybercriminals have come up with the plan to abuse widely used Memcrashed server for
launching 51,000 times powerful DDoS attack. GitHub is considered to be common target of
Chinese government that has been suspected leaving the attack in the year 2015 (Ortu,
Destefanis, Counsell, Swift, Marchesi et al. 2016). Memcached DDoS attack aims to overload
the victim by making use of interent based traffic. Attacker can easily spoof the request which is
vulnerable to UDP Memcached server. It is then targeted victim is completely flooded with
internet traffic. When the given infrastructure is overloaded then new kind of request cannot be
processed with regular traffic (Wang, Zheng, Lou & Hou, 2015). They are unable to gain access
to resources that are internet based which will ultimately result in denial of services.
The report aims to provide a discussion with respect to details of the attack. After that, an
overview has been given with respect to outcome of this GITHUB 1.35 TBPS attack. The overall
impact of this attack has been discussed in details. Overall aim of this security breach and its
consequence of the attack has been discussed in details. The last section of the report deals with
methods or ways to mitigate the issues.
Discussion
CHOSEN ATTACK TYPE OPERATES IN REAL WORLD
Distributed Denial of Service (DDoS) can be defined as a cyber-attack that results in
victim not being able to access the system and network based resources. It ultimately results in
disruption of the internet based services. DDoS attack like GITHUB: 1.35 TBPS Attack can
work like online service or website unable to have traffic from different systems (Kolias,
Kambourakis, Stavrou, & Voas, 2017). If the DDoS attack needs to be successful, then an
Introduction
Cybercriminals have come up with the plan to abuse widely used Memcrashed server for
launching 51,000 times powerful DDoS attack. GitHub is considered to be common target of
Chinese government that has been suspected leaving the attack in the year 2015 (Ortu,
Destefanis, Counsell, Swift, Marchesi et al. 2016). Memcached DDoS attack aims to overload
the victim by making use of interent based traffic. Attacker can easily spoof the request which is
vulnerable to UDP Memcached server. It is then targeted victim is completely flooded with
internet traffic. When the given infrastructure is overloaded then new kind of request cannot be
processed with regular traffic (Wang, Zheng, Lou & Hou, 2015). They are unable to gain access
to resources that are internet based which will ultimately result in denial of services.
The report aims to provide a discussion with respect to details of the attack. After that, an
overview has been given with respect to outcome of this GITHUB 1.35 TBPS attack. The overall
impact of this attack has been discussed in details. Overall aim of this security breach and its
consequence of the attack has been discussed in details. The last section of the report deals with
methods or ways to mitigate the issues.
Discussion
CHOSEN ATTACK TYPE OPERATES IN REAL WORLD
Distributed Denial of Service (DDoS) can be defined as a cyber-attack that results in
victim not being able to access the system and network based resources. It ultimately results in
disruption of the internet based services. DDoS attack like GITHUB: 1.35 TBPS Attack can
work like online service or website unable to have traffic from different systems (Kolias,
Kambourakis, Stavrou, & Voas, 2017). If the DDoS attack needs to be successful, then an
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CYBER SECURITY
attacker needs to spread the malicious software to system through infected email and
attachments. It will create network of infected machines that is known botnet. By the help of
DDoS attack any particular site can be taken to offline mode.
Fig 1: Mechanism of GITHUB: 1.35 TBPS Attack
(Source: Created by Author)
Stages of GITHUB: 1.35 TBPS Attack
GITHUB: 1.35 TBPS Attack was carried out using following steps like
Reconnaissance
Weaponization.
Delivery
Exploitation
Installation
Command and Control (C2)
Actions on Objectives.
attacker needs to spread the malicious software to system through infected email and
attachments. It will create network of infected machines that is known botnet. By the help of
DDoS attack any particular site can be taken to offline mode.
Fig 1: Mechanism of GITHUB: 1.35 TBPS Attack
(Source: Created by Author)
Stages of GITHUB: 1.35 TBPS Attack
GITHUB: 1.35 TBPS Attack was carried out using following steps like
Reconnaissance
Weaponization.
Delivery
Exploitation
Installation
Command and Control (C2)
Actions on Objectives.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
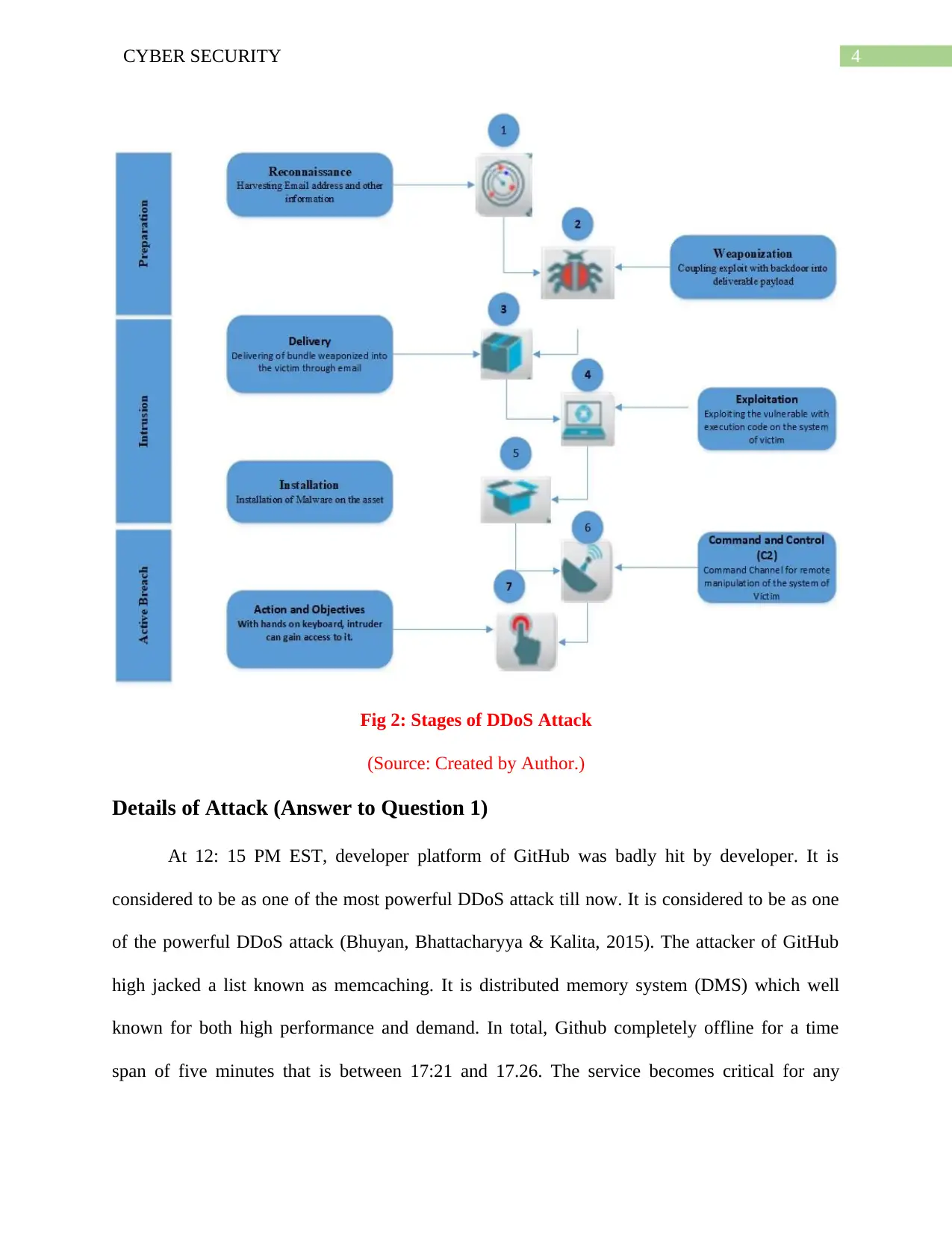
4CYBER SECURITY
Fig 2: Stages of DDoS Attack
(Source: Created by Author.)
Details of Attack (Answer to Question 1)
At 12: 15 PM EST, developer platform of GitHub was badly hit by developer. It is
considered to be as one of the most powerful DDoS attack till now. It is considered to be as one
of the powerful DDoS attack (Bhuyan, Bhattacharyya & Kalita, 2015). The attacker of GitHub
high jacked a list known as memcaching. It is distributed memory system (DMS) which well
known for both high performance and demand. In total, Github completely offline for a time
span of five minutes that is between 17:21 and 17.26. The service becomes critical for any
Fig 2: Stages of DDoS Attack
(Source: Created by Author.)
Details of Attack (Answer to Question 1)
At 12: 15 PM EST, developer platform of GitHub was badly hit by developer. It is
considered to be as one of the most powerful DDoS attack till now. It is considered to be as one
of the powerful DDoS attack (Bhuyan, Bhattacharyya & Kalita, 2015). The attacker of GitHub
high jacked a list known as memcaching. It is distributed memory system (DMS) which well
known for both high performance and demand. In total, Github completely offline for a time
span of five minutes that is between 17:21 and 17.26. The service becomes critical for any
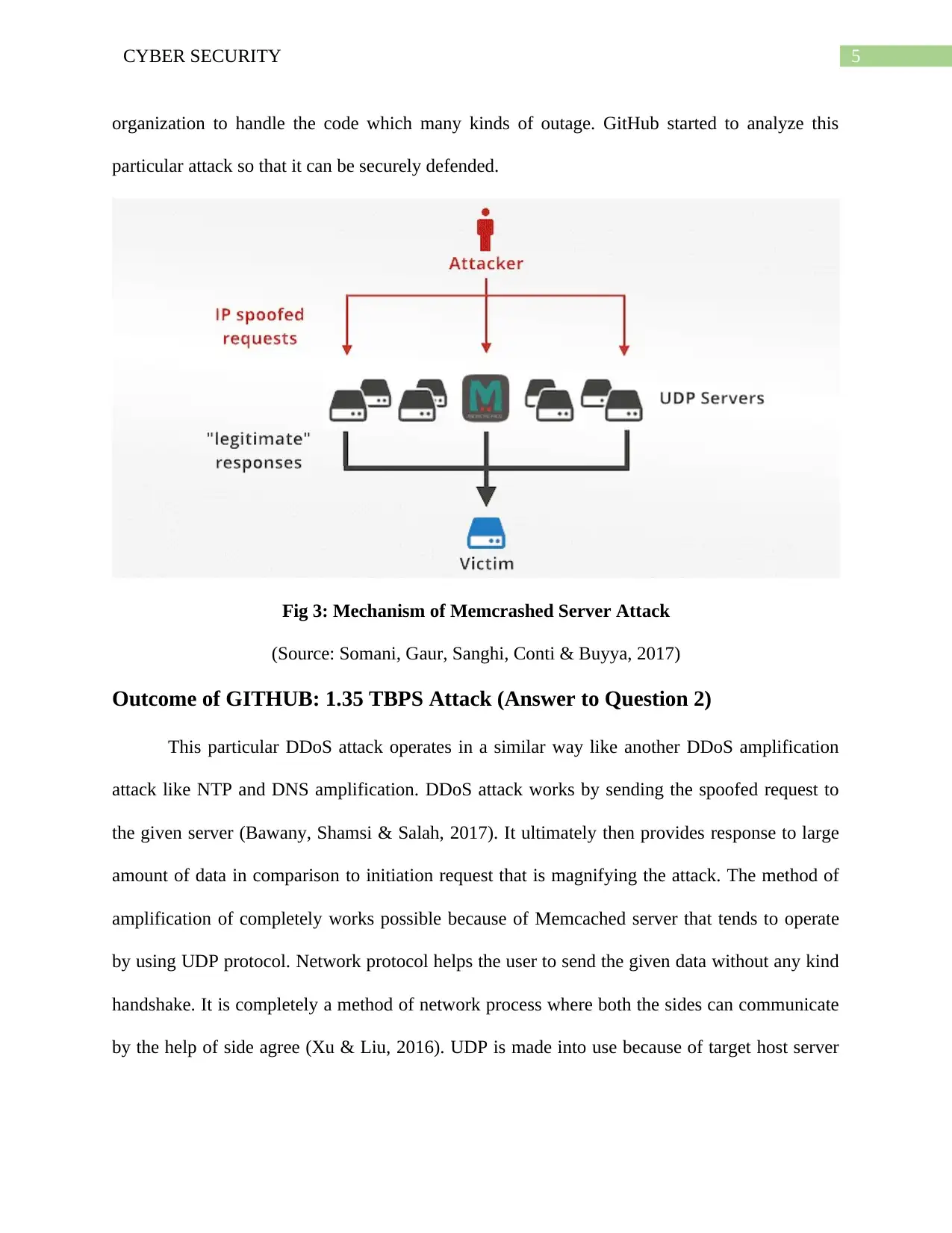
5CYBER SECURITY
organization to handle the code which many kinds of outage. GitHub started to analyze this
particular attack so that it can be securely defended.
Fig 3: Mechanism of Memcrashed Server Attack
(Source: Somani, Gaur, Sanghi, Conti & Buyya, 2017)
Outcome of GITHUB: 1.35 TBPS Attack (Answer to Question 2)
This particular DDoS attack operates in a similar way like another DDoS amplification
attack like NTP and DNS amplification. DDoS attack works by sending the spoofed request to
the given server (Bawany, Shamsi & Salah, 2017). It ultimately then provides response to large
amount of data in comparison to initiation request that is magnifying the attack. The method of
amplification of completely works possible because of Memcached server that tends to operate
by using UDP protocol. Network protocol helps the user to send the given data without any kind
handshake. It is completely a method of network process where both the sides can communicate
by the help of side agree (Xu & Liu, 2016). UDP is made into use because of target host server
organization to handle the code which many kinds of outage. GitHub started to analyze this
particular attack so that it can be securely defended.
Fig 3: Mechanism of Memcrashed Server Attack
(Source: Somani, Gaur, Sanghi, Conti & Buyya, 2017)
Outcome of GITHUB: 1.35 TBPS Attack (Answer to Question 2)
This particular DDoS attack operates in a similar way like another DDoS amplification
attack like NTP and DNS amplification. DDoS attack works by sending the spoofed request to
the given server (Bawany, Shamsi & Salah, 2017). It ultimately then provides response to large
amount of data in comparison to initiation request that is magnifying the attack. The method of
amplification of completely works possible because of Memcached server that tends to operate
by using UDP protocol. Network protocol helps the user to send the given data without any kind
handshake. It is completely a method of network process where both the sides can communicate
by the help of side agree (Xu & Liu, 2016). UDP is made into use because of target host server
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
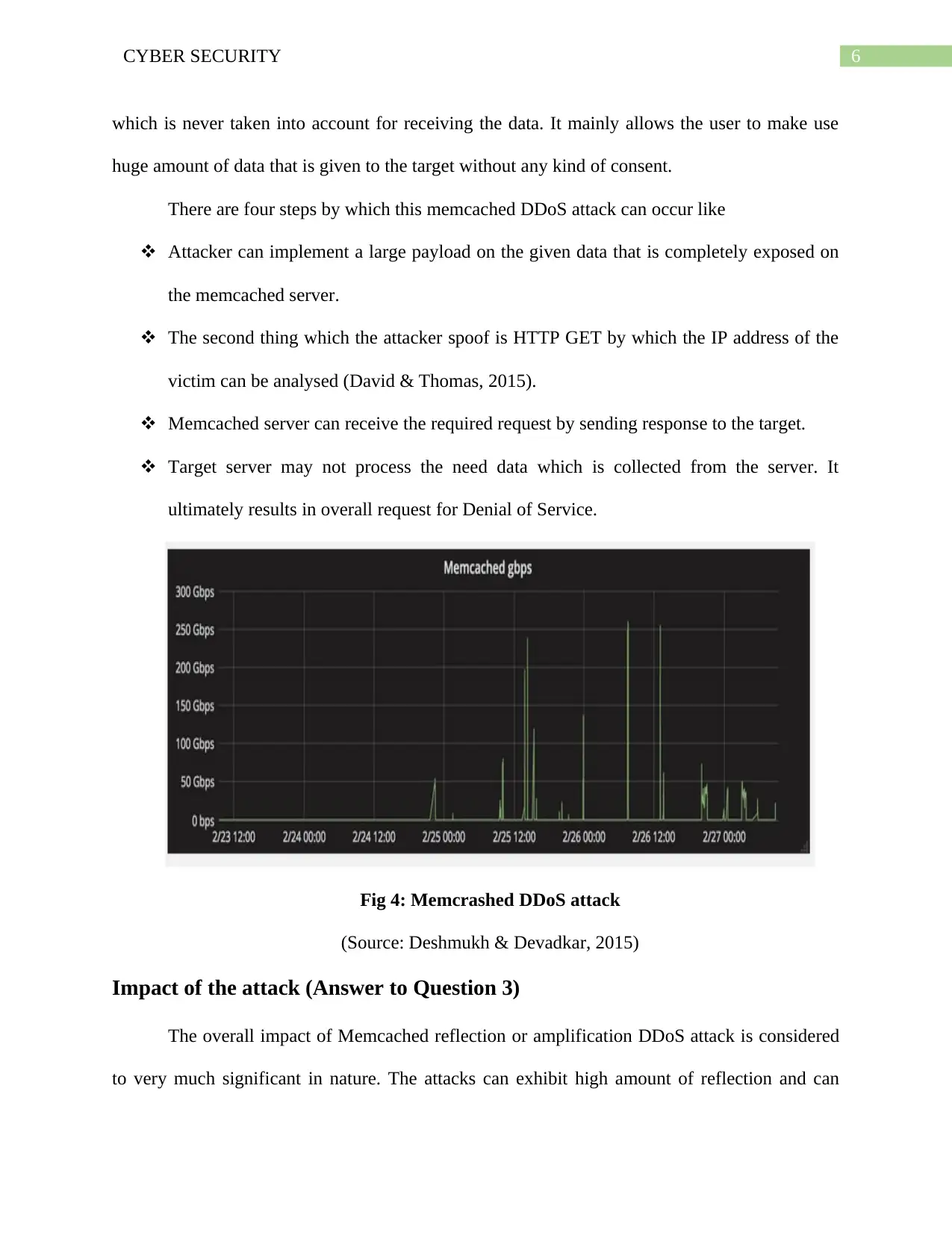
6CYBER SECURITY
which is never taken into account for receiving the data. It mainly allows the user to make use
huge amount of data that is given to the target without any kind of consent.
There are four steps by which this memcached DDoS attack can occur like
Attacker can implement a large payload on the given data that is completely exposed on
the memcached server.
The second thing which the attacker spoof is HTTP GET by which the IP address of the
victim can be analysed (David & Thomas, 2015).
Memcached server can receive the required request by sending response to the target.
Target server may not process the need data which is collected from the server. It
ultimately results in overall request for Denial of Service.
Fig 4: Memcrashed DDoS attack
(Source: Deshmukh & Devadkar, 2015)
Impact of the attack (Answer to Question 3)
The overall impact of Memcached reflection or amplification DDoS attack is considered
to very much significant in nature. The attacks can exhibit high amount of reflection and can
which is never taken into account for receiving the data. It mainly allows the user to make use
huge amount of data that is given to the target without any kind of consent.
There are four steps by which this memcached DDoS attack can occur like
Attacker can implement a large payload on the given data that is completely exposed on
the memcached server.
The second thing which the attacker spoof is HTTP GET by which the IP address of the
victim can be analysed (David & Thomas, 2015).
Memcached server can receive the required request by sending response to the target.
Target server may not process the need data which is collected from the server. It
ultimately results in overall request for Denial of Service.
Fig 4: Memcrashed DDoS attack
(Source: Deshmukh & Devadkar, 2015)
Impact of the attack (Answer to Question 3)
The overall impact of Memcached reflection or amplification DDoS attack is considered
to very much significant in nature. The attacks can exhibit high amount of reflection and can
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CYBER SECURITY
leverage server class amplifiers (Gupta & Badve, 2017). It mainly tends to provide high
bandwidth along with access link where internet data centers can reside. It will ultimately aim to
provide high speed link for upstream transit. While outbound Memcached reflection attack
traffic can be due to high volume. Apart from this, it can have negative impact on the population
Memcached servers (Mousavi & St-Hilaire, 2015). Memcached can also have cross bound
amplification attack server that resides in the same given IDC like Memcached server.
Fig 5: Working Mechanism of Memcrashed Attack
(Source: Ain, Bhuyan, Bhattacharyya & Kalita, 2016)
The total magnification factor of this particular attack is known to be completely
staggering in nature. An amplification factor of around 51200 times. It merely highlights a
request of 15 bytes that is 750 KB can be provided only. It ultimately highlights the massive
amplification factor and overall security risk of the website (Ortu, Destefanis, Counsell, Swift,
Marchesi et al. 2016). It is mainly done because of weight or volume of attack traffic. It is all
about having a large amplification factor which is coupled with the servers. This ultimately
makes the Memcached server the main case for attackers for launching this DDoS attack.
leverage server class amplifiers (Gupta & Badve, 2017). It mainly tends to provide high
bandwidth along with access link where internet data centers can reside. It will ultimately aim to
provide high speed link for upstream transit. While outbound Memcached reflection attack
traffic can be due to high volume. Apart from this, it can have negative impact on the population
Memcached servers (Mousavi & St-Hilaire, 2015). Memcached can also have cross bound
amplification attack server that resides in the same given IDC like Memcached server.
Fig 5: Working Mechanism of Memcrashed Attack
(Source: Ain, Bhuyan, Bhattacharyya & Kalita, 2016)
The total magnification factor of this particular attack is known to be completely
staggering in nature. An amplification factor of around 51200 times. It merely highlights a
request of 15 bytes that is 750 KB can be provided only. It ultimately highlights the massive
amplification factor and overall security risk of the website (Ortu, Destefanis, Counsell, Swift,
Marchesi et al. 2016). It is mainly done because of weight or volume of attack traffic. It is all
about having a large amplification factor which is coupled with the servers. This ultimately
makes the Memcached server the main case for attackers for launching this DDoS attack.
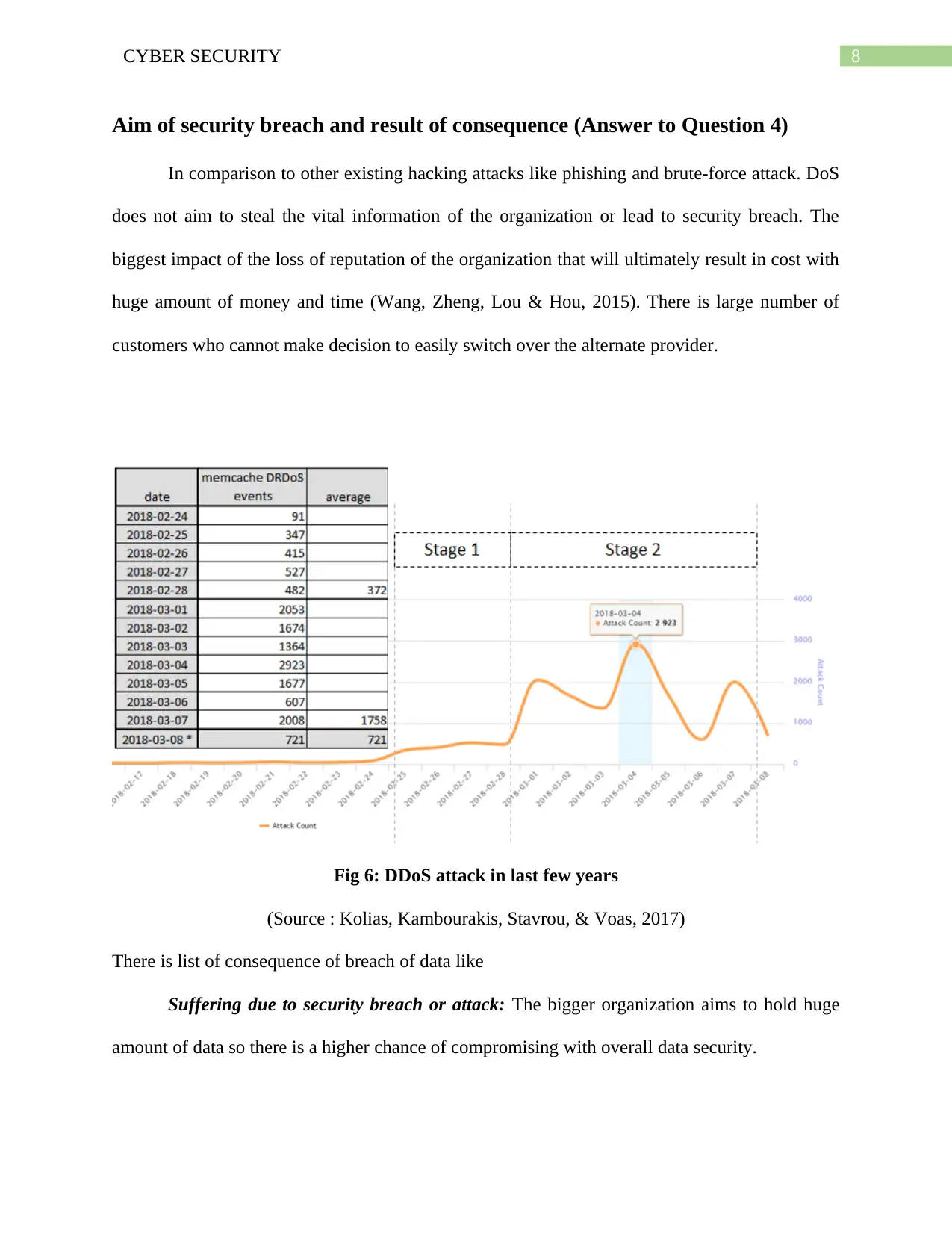
8CYBER SECURITY
Aim of security breach and result of consequence (Answer to Question 4)
In comparison to other existing hacking attacks like phishing and brute-force attack. DoS
does not aim to steal the vital information of the organization or lead to security breach. The
biggest impact of the loss of reputation of the organization that will ultimately result in cost with
huge amount of money and time (Wang, Zheng, Lou & Hou, 2015). There is large number of
customers who cannot make decision to easily switch over the alternate provider.
Fig 6: DDoS attack in last few years
(Source : Kolias, Kambourakis, Stavrou, & Voas, 2017)
There is list of consequence of breach of data like
Suffering due to security breach or attack: The bigger organization aims to hold huge
amount of data so there is a higher chance of compromising with overall data security.
Aim of security breach and result of consequence (Answer to Question 4)
In comparison to other existing hacking attacks like phishing and brute-force attack. DoS
does not aim to steal the vital information of the organization or lead to security breach. The
biggest impact of the loss of reputation of the organization that will ultimately result in cost with
huge amount of money and time (Wang, Zheng, Lou & Hou, 2015). There is large number of
customers who cannot make decision to easily switch over the alternate provider.
Fig 6: DDoS attack in last few years
(Source : Kolias, Kambourakis, Stavrou, & Voas, 2017)
There is list of consequence of breach of data like
Suffering due to security breach or attack: The bigger organization aims to hold huge
amount of data so there is a higher chance of compromising with overall data security.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9CYBER SECURITY
Loss or compromise of data of customers: This particular DDoS attack led to losing of
huge number of customers of the organization.
Loss of money: A large number of cyber-security attacks tend to focus on the wallet of
the organization (Somani, Gaur, Sanghi, Conti & Buyya, 2017). By the year 2021, it is expected
that cyber-crimes will damage around 6 million to the whole world.
Methods of mitigating the issue (Answer to Question 5)
There are large number of ways by which Memcached attack can be mitigated that is
Disabling the UDP port: For the given memcached server, the user needs to make sure of
the fact of disabling of UDP port if the user needs (Bhuyan, Bhattacharyya & Kalita, 2015). Due
to default mode, Memcached comes up with disable port leaving behind the whole server very
much vulnerable.
Firewall Memcached server: By default, the firewalling is done by Memcached server
from the internet where system administrator comes up with ability to make use of UDP port. It
is mainly done because of the fact it is very much necessary with any kind of exposure.
Prevention of IP spoofing: It is mainly done with the IP address that can be spoofed
where DDoS attack is completely vulnerable in nature. It is mainly used for directing the given
traffic to the victim network (Bawany, Shamsi & Salah, 2017). The prevention of IP spoofing is
considered to be as one of the biggest challenges which can be implemented by any of the
network administrator.
Development of software which reduces UDP response: It is considered to be another
kind of method by which any kind of amplification attack can be removed the given
amplification factor for any upcoming request (Xu & Liu, 2016). It is mainly done for providing
response to the data which is sent due to UDP request.
Loss or compromise of data of customers: This particular DDoS attack led to losing of
huge number of customers of the organization.
Loss of money: A large number of cyber-security attacks tend to focus on the wallet of
the organization (Somani, Gaur, Sanghi, Conti & Buyya, 2017). By the year 2021, it is expected
that cyber-crimes will damage around 6 million to the whole world.
Methods of mitigating the issue (Answer to Question 5)
There are large number of ways by which Memcached attack can be mitigated that is
Disabling the UDP port: For the given memcached server, the user needs to make sure of
the fact of disabling of UDP port if the user needs (Bhuyan, Bhattacharyya & Kalita, 2015). Due
to default mode, Memcached comes up with disable port leaving behind the whole server very
much vulnerable.
Firewall Memcached server: By default, the firewalling is done by Memcached server
from the internet where system administrator comes up with ability to make use of UDP port. It
is mainly done because of the fact it is very much necessary with any kind of exposure.
Prevention of IP spoofing: It is mainly done with the IP address that can be spoofed
where DDoS attack is completely vulnerable in nature. It is mainly used for directing the given
traffic to the victim network (Bawany, Shamsi & Salah, 2017). The prevention of IP spoofing is
considered to be as one of the biggest challenges which can be implemented by any of the
network administrator.
Development of software which reduces UDP response: It is considered to be another
kind of method by which any kind of amplification attack can be removed the given
amplification factor for any upcoming request (Xu & Liu, 2016). It is mainly done for providing
response to the data which is sent due to UDP request.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
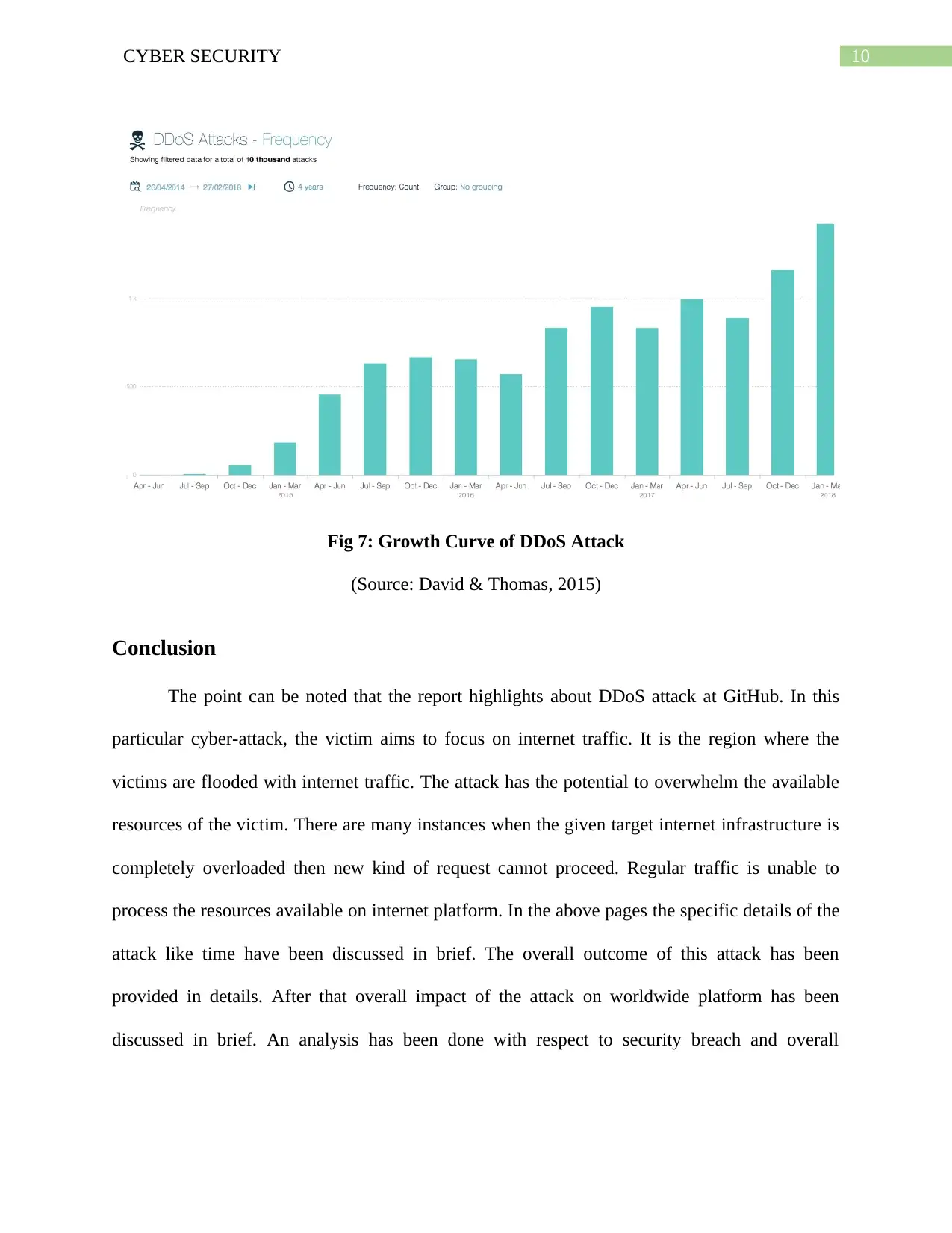
10CYBER SECURITY
Fig 7: Growth Curve of DDoS Attack
(Source: David & Thomas, 2015)
Conclusion
The point can be noted that the report highlights about DDoS attack at GitHub. In this
particular cyber-attack, the victim aims to focus on internet traffic. It is the region where the
victims are flooded with internet traffic. The attack has the potential to overwhelm the available
resources of the victim. There are many instances when the given target internet infrastructure is
completely overloaded then new kind of request cannot proceed. Regular traffic is unable to
process the resources available on internet platform. In the above pages the specific details of the
attack like time have been discussed in brief. The overall outcome of this attack has been
provided in details. After that overall impact of the attack on worldwide platform has been
discussed in brief. An analysis has been done with respect to security breach and overall
Fig 7: Growth Curve of DDoS Attack
(Source: David & Thomas, 2015)
Conclusion
The point can be noted that the report highlights about DDoS attack at GitHub. In this
particular cyber-attack, the victim aims to focus on internet traffic. It is the region where the
victims are flooded with internet traffic. The attack has the potential to overwhelm the available
resources of the victim. There are many instances when the given target internet infrastructure is
completely overloaded then new kind of request cannot proceed. Regular traffic is unable to
process the resources available on internet platform. In the above pages the specific details of the
attack like time have been discussed in brief. The overall outcome of this attack has been
provided in details. After that overall impact of the attack on worldwide platform has been
discussed in brief. An analysis has been done with respect to security breach and overall

11CYBER SECURITY
consequence of the attack. The report ends with list of mitigation technique for tackling the
DDoS attack.
References
Ain, A., Bhuyan, M. H., Bhattacharyya, D. K., & Kalita, J. K. (2016). Rank Correlation for Low-
Rate DDoS Attack Detection: An Empirical Evaluation. IJ Network Security, 18(3), 474-
480.
Bawany, N. Z., Shamsi, J. A., & Salah, K. (2017). DDoS attack detection and mitigation using
SDN: methods, practices, and solutions. Arabian Journal for Science and
Engineering, 42(2), 425-441.
Bhuyan, M. H., Bhattacharyya, D. K., & Kalita, J. K. (2015). An empirical evaluation of
information metrics for low-rate and high-rate DDoS attack detection. Pattern
Recognition Letters, 51, 1-7.
David, J., & Thomas, C. (2015). DDoS attack detection using fast entropy approach on flow-
based network traffic. Procedia Computer Science, 50, 30-36.
Deshmukh, R. V., & Devadkar, K. K. (2015). Understanding DDoS attack & its effect in cloud
environment. Procedia Computer Science, 49, 202-210.
Gupta, B. B., & Badve, O. P. (2017). Taxonomy of DoS and DDoS attacks and desirable defense
mechanism in a cloud computing environment. Neural Computing and
Applications, 28(12), 3655-3682.
Kolias, C., Kambourakis, G., Stavrou, A., & Voas, J. (2017). DDoS in the IoT: Mirai and other
botnets. Computer, 50(7), 80-84.
consequence of the attack. The report ends with list of mitigation technique for tackling the
DDoS attack.
References
Ain, A., Bhuyan, M. H., Bhattacharyya, D. K., & Kalita, J. K. (2016). Rank Correlation for Low-
Rate DDoS Attack Detection: An Empirical Evaluation. IJ Network Security, 18(3), 474-
480.
Bawany, N. Z., Shamsi, J. A., & Salah, K. (2017). DDoS attack detection and mitigation using
SDN: methods, practices, and solutions. Arabian Journal for Science and
Engineering, 42(2), 425-441.
Bhuyan, M. H., Bhattacharyya, D. K., & Kalita, J. K. (2015). An empirical evaluation of
information metrics for low-rate and high-rate DDoS attack detection. Pattern
Recognition Letters, 51, 1-7.
David, J., & Thomas, C. (2015). DDoS attack detection using fast entropy approach on flow-
based network traffic. Procedia Computer Science, 50, 30-36.
Deshmukh, R. V., & Devadkar, K. K. (2015). Understanding DDoS attack & its effect in cloud
environment. Procedia Computer Science, 49, 202-210.
Gupta, B. B., & Badve, O. P. (2017). Taxonomy of DoS and DDoS attacks and desirable defense
mechanism in a cloud computing environment. Neural Computing and
Applications, 28(12), 3655-3682.
Kolias, C., Kambourakis, G., Stavrou, A., & Voas, J. (2017). DDoS in the IoT: Mirai and other
botnets. Computer, 50(7), 80-84.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





