Cybercrime Case Study: A Detailed Report on the DDOS Attack on Github
VerifiedAdded on 2023/06/04
|5
|1194
|491
Report
AI Summary
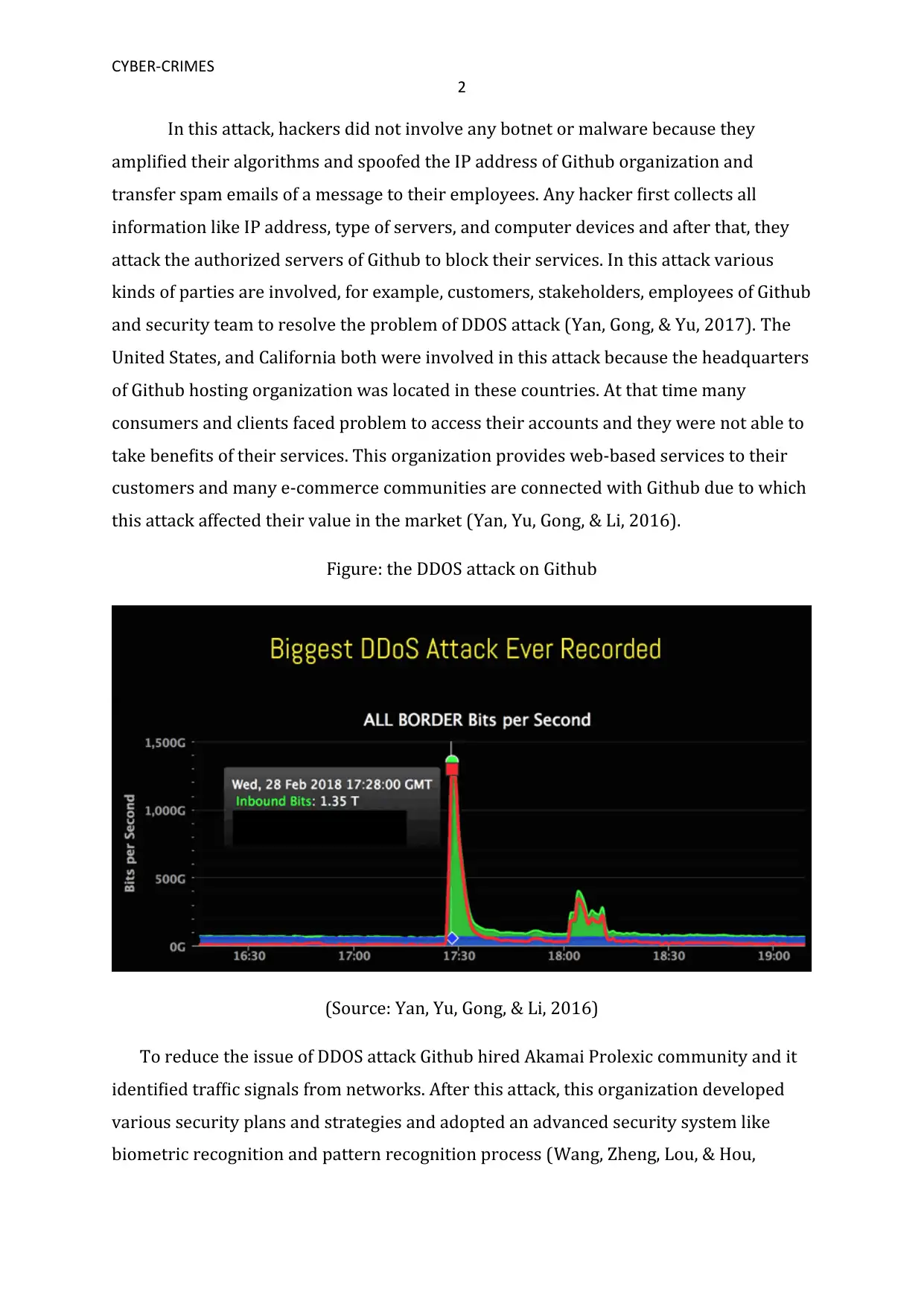
This report delves into a Distributed Denial of Service (DDOS) attack, a prevalent form of cybercrime, focusing on a specific incident targeting Github in 2018. The attack, which reached 1.35 terabits per second, disrupted Github's services and highlighted vulnerabilities in its network security. The report identifies the methods used by hackers, including flooding and malware servers, and discusses the involvement of various parties, such as Github's customers, stakeholders, employees, and security team. To mitigate the attack, Github collaborated with Akamai Prolexic, an information security community, to filter malicious traffic. The report also outlines preventive measures, including proper configuration, encryption technologies, data backup plans, and robust password systems, to enhance network security and prevent future DDOS attacks. Furthermore, it emphasizes the importance of securing computer networks and adopting encryption techniques to combat spam and fraudulent emails, ultimately protecting consumers and organizations from such cyber threats. The document is contributed by a student and available on Desklib for educational purposes.
1 out of 5











![[object Object]](/_next/static/media/star-bottom.7253800d.svg)