INFS 3070 - Global Security Breach Incident Analysis and Top Threats
VerifiedAdded on 2023/06/14
|13
|2018
|472
Report
AI Summary
This report provides an analysis of global security breach incidents over the past five years, identifying key trends and potential threats to an organization. It discusses management measures to overcome these threats, focusing on physical, operational, and communication security. The report emphasizes the importance of the CIA triangle (Confidentiality, Integrity, Availability) and proposes strategic planning for risk mitigation, including short-term monitoring and resource allocation. Recommendations include firewall configuration, security software implementation, and security policy development. The report concludes by highlighting the need for risk management programs, proper planning, and threat identification. Desklib offers a variety of solved assignments and past papers to aid students in their studies.

REPORT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Executive Summary
Information Security System is the practice which helps in preventing the unauthorized access,
use or the disclosure of the data or any information destruction. It has been seen that the
information primary focus is on the balanced protection of confidentiality, integrity and data
availability to maintain the effective policy implementation without hampering the productivity.
The report will discuss the incidents related to information security breach and how the threats
can impact the functioning of the organization. Apart from this, we are going to focus on the
technical and the administrative controls which will be important to take any step for overcoming
the threats and securing the organization information assets.
Information Security System is the practice which helps in preventing the unauthorized access,
use or the disclosure of the data or any information destruction. It has been seen that the
information primary focus is on the balanced protection of confidentiality, integrity and data
availability to maintain the effective policy implementation without hampering the productivity.
The report will discuss the incidents related to information security breach and how the threats
can impact the functioning of the organization. Apart from this, we are going to focus on the
technical and the administrative controls which will be important to take any step for overcoming
the threats and securing the organization information assets.

Contents
Introduction......................................................................................................................................3
Purpose of report..........................................................................................................................3
Limitations...................................................................................................................................3
Scope of Report...........................................................................................................................3
Body of Report................................................................................................................................4
Analysis of Information Security Incidents for 5 years...............................................................4
Threats which has potential threats to your organisation............................................................4
Propose and Discuss the management measures to overcome them...........................................6
Recommendations............................................................................................................................9
Conclusion.....................................................................................................................................10
References......................................................................................................................................11
Introduction......................................................................................................................................3
Purpose of report..........................................................................................................................3
Limitations...................................................................................................................................3
Scope of Report...........................................................................................................................3
Body of Report................................................................................................................................4
Analysis of Information Security Incidents for 5 years...............................................................4
Threats which has potential threats to your organisation............................................................4
Propose and Discuss the management measures to overcome them...........................................6
Recommendations............................................................................................................................9
Conclusion.....................................................................................................................................10
References......................................................................................................................................11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Introduction
Information security match with the risk management process that tends to identify the assets,
threat sources, vulnerabilities and the potential impacts of other possible controls. In order to
standardize this, there is guidance based on industry standards on password, firewall and the
encryption software with legal liabilities for the training standards. Being the Information
Security Manager of ABC organization, I have been asked by CISO to review the breach
incidents and analyze the trends. With this, I have to focus on the policy development and
assessment of the risks, contingency planning, and operational planning in an effective manner.
Purpose of report
Being the Information Security Manager, my major focus is on reviewing the global security
breach and examine the threats which can have a major impact on the organization functioning.
Limitations
The limitations for CISOs is the signature-based patterns where the sheer volume of new
malware is created daily. The lack of scalability and non-supporting distributed environment.
The major focus is on the compliance which is a static event and is intrusion centric to handle the
threats and protect the data. (Soomro et al., 2016)
Scope of Report
The report will discuss the different recommendations and the management measures which are
required to handle the threats. The risk-based development and security policy structure is
discussed with policy development process focusing on the business and the other organizational
requirements.
Information security match with the risk management process that tends to identify the assets,
threat sources, vulnerabilities and the potential impacts of other possible controls. In order to
standardize this, there is guidance based on industry standards on password, firewall and the
encryption software with legal liabilities for the training standards. Being the Information
Security Manager of ABC organization, I have been asked by CISO to review the breach
incidents and analyze the trends. With this, I have to focus on the policy development and
assessment of the risks, contingency planning, and operational planning in an effective manner.
Purpose of report
Being the Information Security Manager, my major focus is on reviewing the global security
breach and examine the threats which can have a major impact on the organization functioning.
Limitations
The limitations for CISOs is the signature-based patterns where the sheer volume of new
malware is created daily. The lack of scalability and non-supporting distributed environment.
The major focus is on the compliance which is a static event and is intrusion centric to handle the
threats and protect the data. (Soomro et al., 2016)
Scope of Report
The report will discuss the different recommendations and the management measures which are
required to handle the threats. The risk-based development and security policy structure is
discussed with policy development process focusing on the business and the other organizational
requirements.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Body of Report
Analysis of Information Security Incidents for 5 years
a. There was a Petra cyber attack on the company, where the ransomware hit the servers in
Australia where the people had to face issues related to the loss of data. The malicious or
the criminal attacks were seen to be the primary causes for the breach.
b. The information security breach with Krebs on Security by point-of-sale credit card used.
c. The Dun & Bradstreet incident happened in 2017, where most of the marketing database
with the different corporate contacts were shared over the web (Peltier, 2016).
d. The next security incident was Gmail users in the company were targeted with the
sophisticated phishing scam which was seeking the gain in the access to the accounts
through the third-party application. The emails were loosed as if they came from the
trusted contact and then notified the individual that they wanted to share a Google Doc
with the people.
e. DocuSign Attack where the customers and the users were mainly targeted by the phishing
attacks of malware. It includes the breach of one system where one could obtain the email
address and no other personal information. The hackers then used this email address to
mainly conducting the malicious email campaigns where the DocuSign branded message
was then sent for the prompted recipients to click and download the Microsoft Word
document (Nazareth et al., 2015).
Threats which has potential threats to your organisation.
Some of the major threats which seems to be an issue for the development are:
Analysis of Information Security Incidents for 5 years
a. There was a Petra cyber attack on the company, where the ransomware hit the servers in
Australia where the people had to face issues related to the loss of data. The malicious or
the criminal attacks were seen to be the primary causes for the breach.
b. The information security breach with Krebs on Security by point-of-sale credit card used.
c. The Dun & Bradstreet incident happened in 2017, where most of the marketing database
with the different corporate contacts were shared over the web (Peltier, 2016).
d. The next security incident was Gmail users in the company were targeted with the
sophisticated phishing scam which was seeking the gain in the access to the accounts
through the third-party application. The emails were loosed as if they came from the
trusted contact and then notified the individual that they wanted to share a Google Doc
with the people.
e. DocuSign Attack where the customers and the users were mainly targeted by the phishing
attacks of malware. It includes the breach of one system where one could obtain the email
address and no other personal information. The hackers then used this email address to
mainly conducting the malicious email campaigns where the DocuSign branded message
was then sent for the prompted recipients to click and download the Microsoft Word
document (Nazareth et al., 2015).
Threats which has potential threats to your organisation.
Some of the major threats which seems to be an issue for the development are:

a. There is a possibility of exploiting the known vulnerabilities, with crimes as a service
with ready to use kits for ransomware. The increased sophistication will then be used for
the high-value networks.
b. The critical infrastructure is likely to populate the target for the sophisticated attacks with
supply chain targeting that tends to continue as the third party works over the weak links
and handling the outsourcing arrangements mainly at a higher risk.
c. The management of the service providers will tend to continue with attractive targets
which have a higher number of customers, connectivity as well as the customer access for
the networks and the data (Ab Rahman & Choo, 2015).
d. IoT (Internet of Things) will tend to create risks with pressure on the consumers for the
manufacturing which includes certain security controls.
e. The explosion of threats, privacy, and the ethical concerns are the major concern for big
data with stringent global regulations where the huge demands are based on the security
professionals with the evolvement of certain grounded expertise.
with ready to use kits for ransomware. The increased sophistication will then be used for
the high-value networks.
b. The critical infrastructure is likely to populate the target for the sophisticated attacks with
supply chain targeting that tends to continue as the third party works over the weak links
and handling the outsourcing arrangements mainly at a higher risk.
c. The management of the service providers will tend to continue with attractive targets
which have a higher number of customers, connectivity as well as the customer access for
the networks and the data (Ab Rahman & Choo, 2015).
d. IoT (Internet of Things) will tend to create risks with pressure on the consumers for the
manufacturing which includes certain security controls.
e. The explosion of threats, privacy, and the ethical concerns are the major concern for big
data with stringent global regulations where the huge demands are based on the security
professionals with the evolvement of certain grounded expertise.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Figure: Cyber Security Skill Gap
Propose and Discuss the management measures to overcome them
In order to overcome the issues, the physical security (security of the physical assets and the
workplace threats), operational security, communication security needs to be managed properly.
According to CNSS (Committee on National Security Model), they help in maintaining the gap
in coverage of Information Security Program. The use of CIA triangle focusses on maintaining
the confidentiality, integrity and the availability of privacy, identification and the authentication
system stability (Tsohou et al., 2015). For the confidentiality,
a. The secured documentation and the storage of data, cryptography, education of
information custodians is important.
b. Integrity includes the stability of access or error control.
c. The availability of the authorized users could be maintained through backups, up-
gradation of the system and recovery of disaster.
Propose and Discuss the management measures to overcome them
In order to overcome the issues, the physical security (security of the physical assets and the
workplace threats), operational security, communication security needs to be managed properly.
According to CNSS (Committee on National Security Model), they help in maintaining the gap
in coverage of Information Security Program. The use of CIA triangle focusses on maintaining
the confidentiality, integrity and the availability of privacy, identification and the authentication
system stability (Tsohou et al., 2015). For the confidentiality,
a. The secured documentation and the storage of data, cryptography, education of
information custodians is important.
b. Integrity includes the stability of access or error control.
c. The availability of the authorized users could be maintained through backups, up-
gradation of the system and recovery of disaster.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

d. The privacy could be maintained through access control and policies.
e. The authentication and identification through the use of certain cryptographic
certifications.
f. The authorisation is to handle the access, modification, or the deletion of information.
There is a need for focusing on the information security strategic planning so that one can handle
the mitigation, transferring, acceptance or avoidance of information which is related to the
people risks, process and technologies (Safa et al., 2016). The planning will focus on the short-
term focus with increased monitoring of the other external connections. The budgeting, resource
allocation, and the personal details are critical to the tactical planning which includes the security
strategies like monitoring the external connection, associated risks with increased connectivity
and handling the security hardening process. The strategy will help in redundancy for the critical
production system with improved availability of the services as well. The customer facing issues
are set in accordance to the security standards in order to replace the network bridges with the
switches to rebuild a better customer application which will allow the business to be relocated
inside the organization with the trusted network (Fenz et al., 2014). The planning for the strategic
implementation includes the tactical and the operational security plans which are based on
handling the development where the Information Security Governance focus on determining the
standards which measure progress towards the better achievements. It also includes the
accountabilities and the methods for the proper measurement of progress with verification of
risks management practices.
e. The authentication and identification through the use of certain cryptographic
certifications.
f. The authorisation is to handle the access, modification, or the deletion of information.
There is a need for focusing on the information security strategic planning so that one can handle
the mitigation, transferring, acceptance or avoidance of information which is related to the
people risks, process and technologies (Safa et al., 2016). The planning will focus on the short-
term focus with increased monitoring of the other external connections. The budgeting, resource
allocation, and the personal details are critical to the tactical planning which includes the security
strategies like monitoring the external connection, associated risks with increased connectivity
and handling the security hardening process. The strategy will help in redundancy for the critical
production system with improved availability of the services as well. The customer facing issues
are set in accordance to the security standards in order to replace the network bridges with the
switches to rebuild a better customer application which will allow the business to be relocated
inside the organization with the trusted network (Fenz et al., 2014). The planning for the strategic
implementation includes the tactical and the operational security plans which are based on
handling the development where the Information Security Governance focus on determining the
standards which measure progress towards the better achievements. It also includes the
accountabilities and the methods for the proper measurement of progress with verification of
risks management practices.
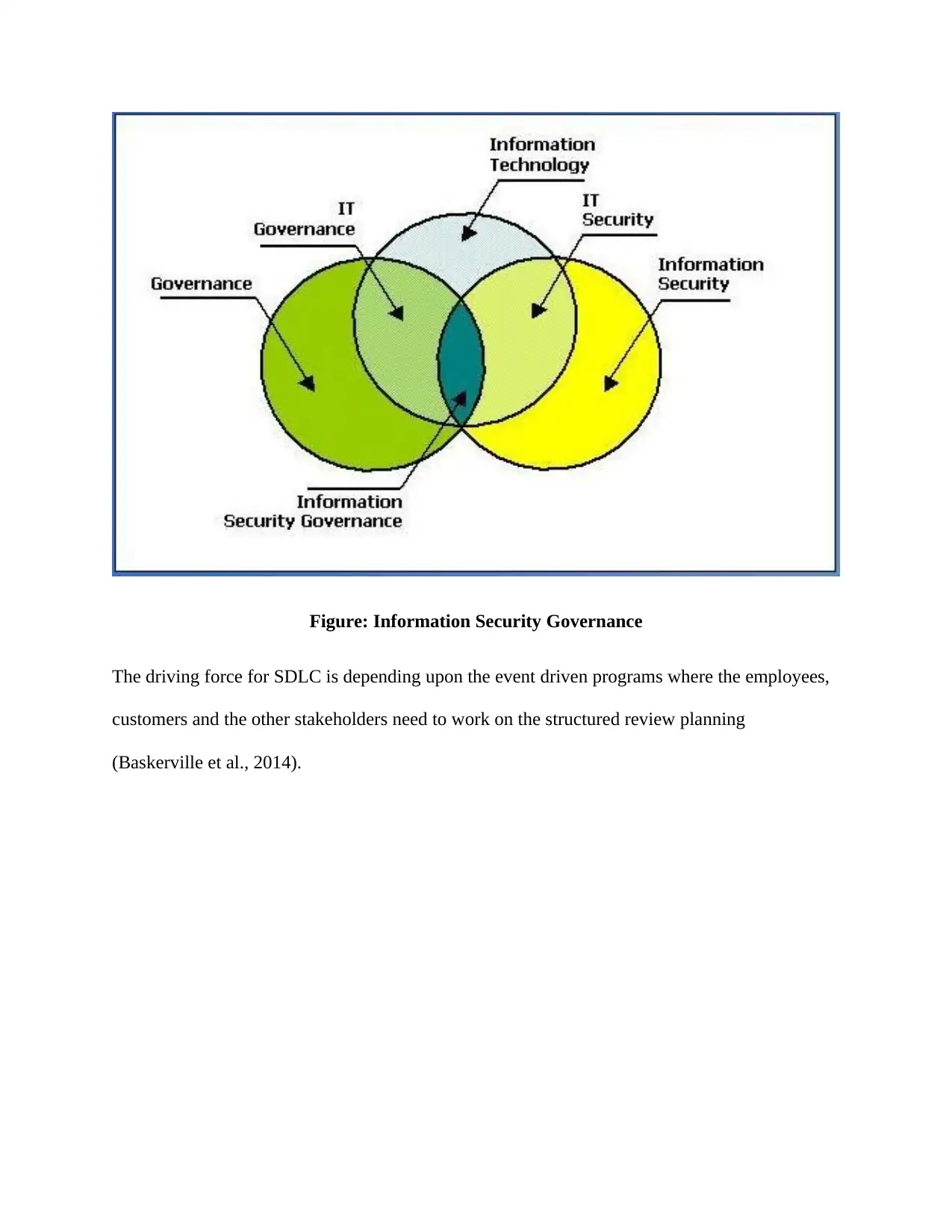
Figure: Information Security Governance
The driving force for SDLC is depending upon the event driven programs where the employees,
customers and the other stakeholders need to work on the structured review planning
(Baskerville et al., 2014).
The driving force for SDLC is depending upon the event driven programs where the employees,
customers and the other stakeholders need to work on the structured review planning
(Baskerville et al., 2014).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
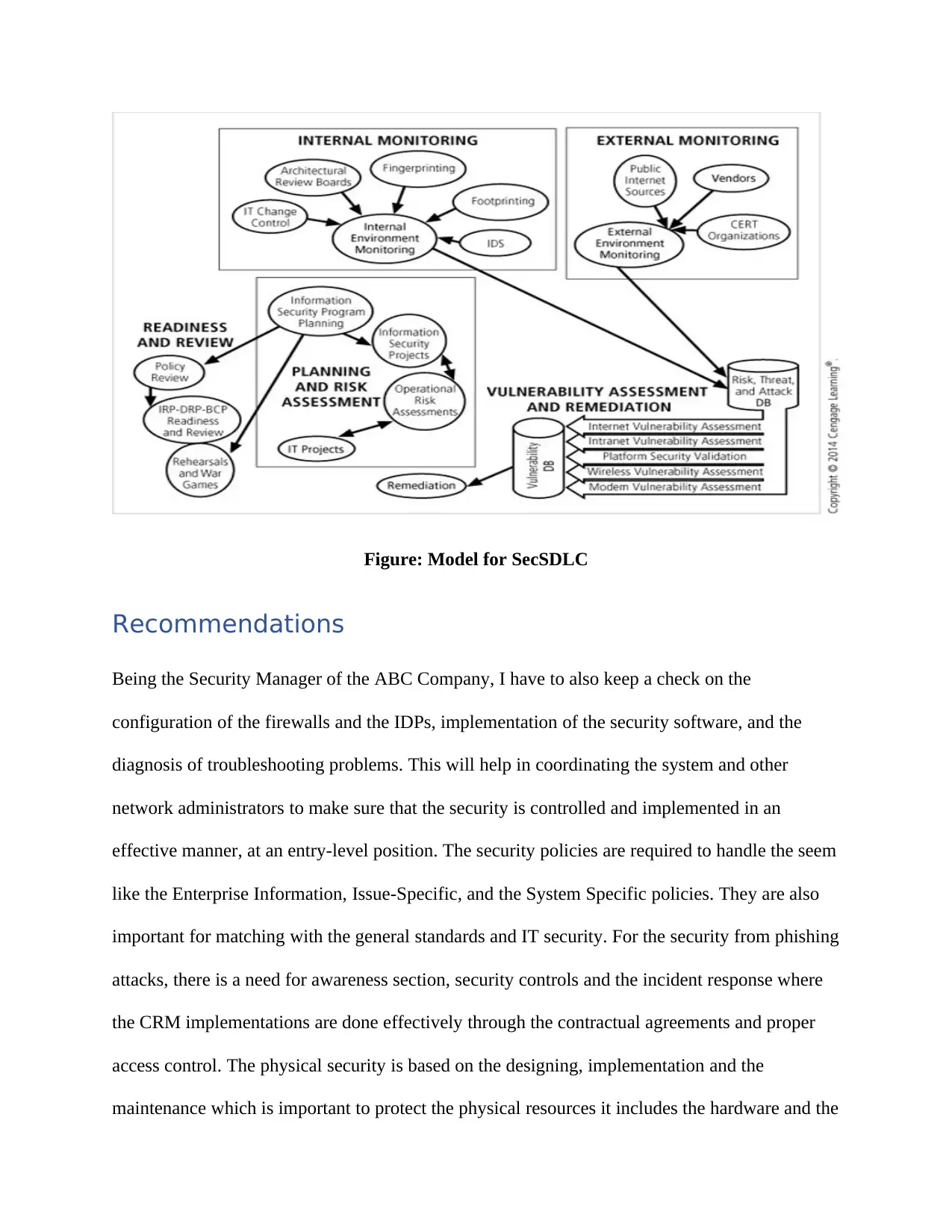
Figure: Model for SecSDLC
Recommendations
Being the Security Manager of the ABC Company, I have to also keep a check on the
configuration of the firewalls and the IDPs, implementation of the security software, and the
diagnosis of troubleshooting problems. This will help in coordinating the system and other
network administrators to make sure that the security is controlled and implemented in an
effective manner, at an entry-level position. The security policies are required to handle the seem
like the Enterprise Information, Issue-Specific, and the System Specific policies. They are also
important for matching with the general standards and IT security. For the security from phishing
attacks, there is a need for awareness section, security controls and the incident response where
the CRM implementations are done effectively through the contractual agreements and proper
access control. The physical security is based on the designing, implementation and the
maintenance which is important to protect the physical resources it includes the hardware and the
Recommendations
Being the Security Manager of the ABC Company, I have to also keep a check on the
configuration of the firewalls and the IDPs, implementation of the security software, and the
diagnosis of troubleshooting problems. This will help in coordinating the system and other
network administrators to make sure that the security is controlled and implemented in an
effective manner, at an entry-level position. The security policies are required to handle the seem
like the Enterprise Information, Issue-Specific, and the System Specific policies. They are also
important for matching with the general standards and IT security. For the security from phishing
attacks, there is a need for awareness section, security controls and the incident response where
the CRM implementations are done effectively through the contractual agreements and proper
access control. The physical security is based on the designing, implementation and the
maintenance which is important to protect the physical resources it includes the hardware and the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
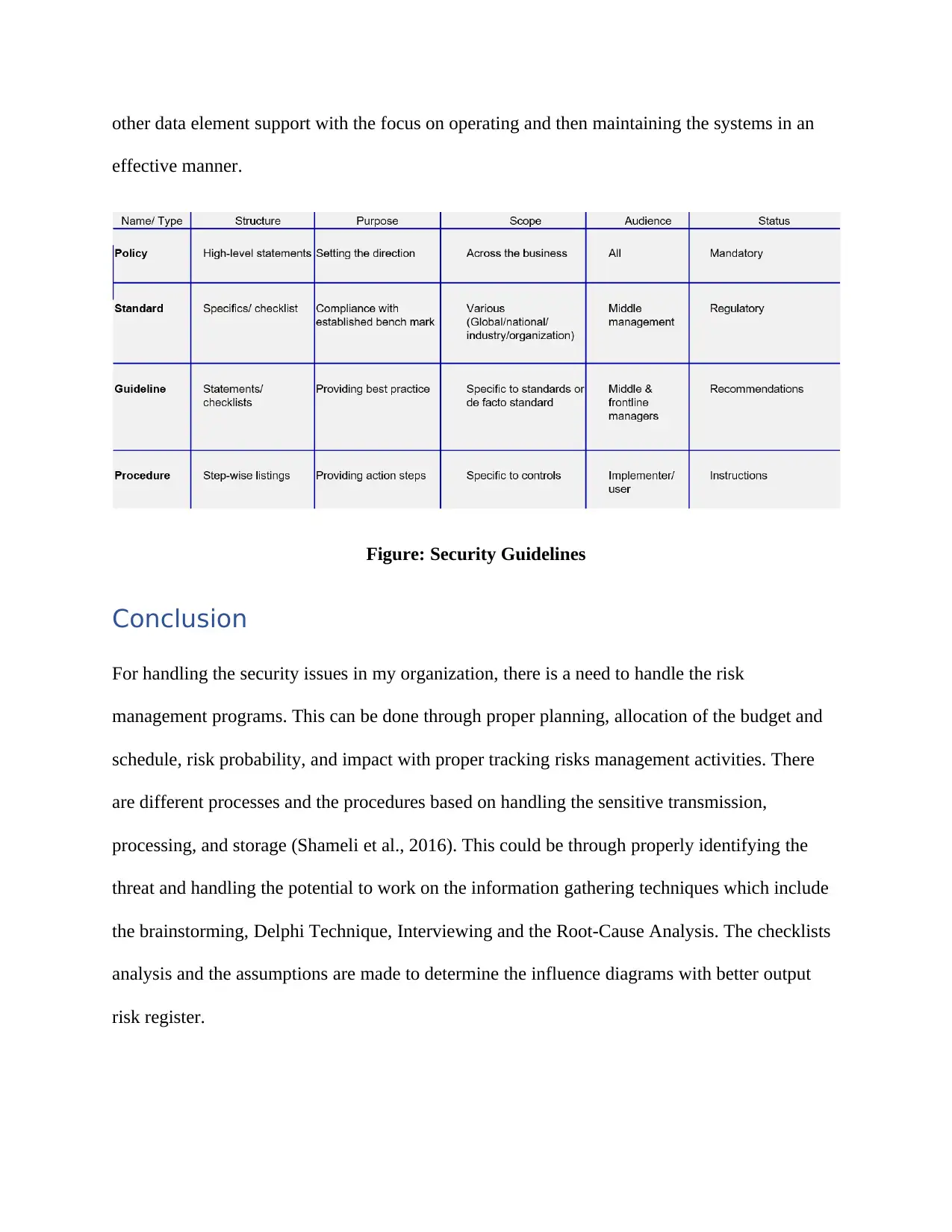
other data element support with the focus on operating and then maintaining the systems in an
effective manner.
Figure: Security Guidelines
Conclusion
For handling the security issues in my organization, there is a need to handle the risk
management programs. This can be done through proper planning, allocation of the budget and
schedule, risk probability, and impact with proper tracking risks management activities. There
are different processes and the procedures based on handling the sensitive transmission,
processing, and storage (Shameli et al., 2016). This could be through properly identifying the
threat and handling the potential to work on the information gathering techniques which include
the brainstorming, Delphi Technique, Interviewing and the Root-Cause Analysis. The checklists
analysis and the assumptions are made to determine the influence diagrams with better output
risk register.
effective manner.
Figure: Security Guidelines
Conclusion
For handling the security issues in my organization, there is a need to handle the risk
management programs. This can be done through proper planning, allocation of the budget and
schedule, risk probability, and impact with proper tracking risks management activities. There
are different processes and the procedures based on handling the sensitive transmission,
processing, and storage (Shameli et al., 2016). This could be through properly identifying the
threat and handling the potential to work on the information gathering techniques which include
the brainstorming, Delphi Technique, Interviewing and the Root-Cause Analysis. The checklists
analysis and the assumptions are made to determine the influence diagrams with better output
risk register.

References
Ab Rahman, N.H. and Choo, K.K.R., 2015. A survey of information security incident handling
in the cloud. Computers & Security, 49, pp.45-69.
Baskerville, R., Spagnoletti, P. and Kim, J., 2014. Incident-centered information security:
Managing a strategic balance between prevention and response. Information &
Management, 51(1), pp.138-151.
Fenz, S., Heurix, J., Neubauer, T. and Pechstein, F., 2014. Current challenges in information
security risk management. Information Management & Computer Security, 22(5), pp.410-430.
Nazareth, D.L. and Choi, J., 2015. A system dynamics model for information security
management. Information & Management, 52(1), pp.123-134.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Safa, N.S., Von Solms, R. and Furnell, S., 2016. Information security policy compliance model
in organizations. Computers & Security, 56, pp.70-82.
Shameli-Sendi, A., Aghababaei-Barzegar, R. and Cheriet, M., 2016. Taxonomy of information
security risk assessment (ISRA). Computers & security, 57, pp.14-30.
Soomro, Z.A., Shah, M.H. and Ahmed, J., 2016. Information security management needs more
holistic approach: A literature review. International Journal of Information Management, 36(2),
pp.215-225.
Ab Rahman, N.H. and Choo, K.K.R., 2015. A survey of information security incident handling
in the cloud. Computers & Security, 49, pp.45-69.
Baskerville, R., Spagnoletti, P. and Kim, J., 2014. Incident-centered information security:
Managing a strategic balance between prevention and response. Information &
Management, 51(1), pp.138-151.
Fenz, S., Heurix, J., Neubauer, T. and Pechstein, F., 2014. Current challenges in information
security risk management. Information Management & Computer Security, 22(5), pp.410-430.
Nazareth, D.L. and Choi, J., 2015. A system dynamics model for information security
management. Information & Management, 52(1), pp.123-134.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Safa, N.S., Von Solms, R. and Furnell, S., 2016. Information security policy compliance model
in organizations. Computers & Security, 56, pp.70-82.
Shameli-Sendi, A., Aghababaei-Barzegar, R. and Cheriet, M., 2016. Taxonomy of information
security risk assessment (ISRA). Computers & security, 57, pp.14-30.
Soomro, Z.A., Shah, M.H. and Ahmed, J., 2016. Information security management needs more
holistic approach: A literature review. International Journal of Information Management, 36(2),
pp.215-225.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





