Google Dorking: A Deep Dive into Data Security and Exploitation
VerifiedAdded on 2022/11/15
|5
|311
|52
Homework Assignment
AI Summary
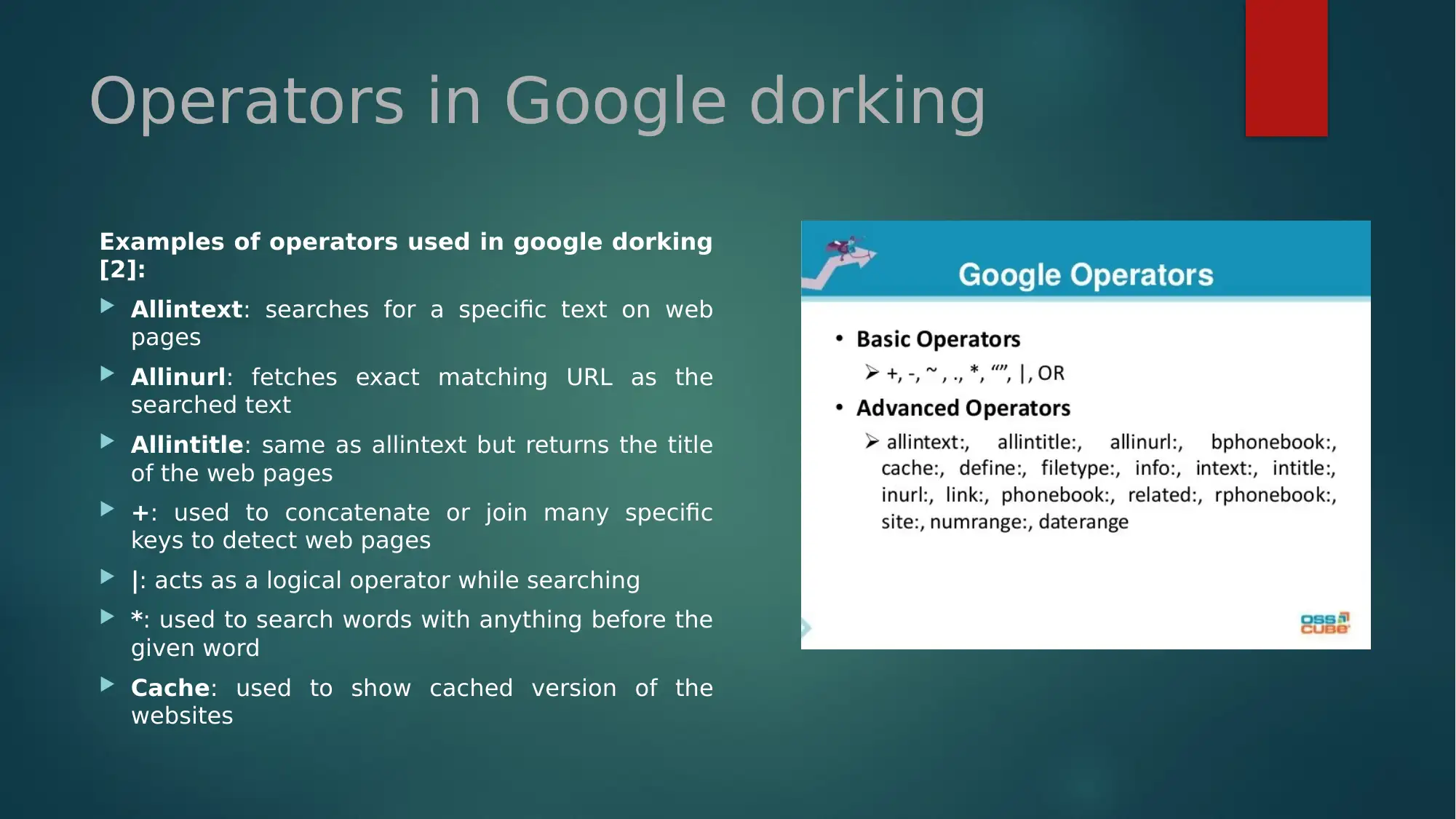
This assignment provides an overview of Google Dorking, a technique used to retrieve information from the internet using specific search operators. It discusses the basic concepts, including how Google Dorking works and its potential for both ethical and malicious purposes. The assignment highlights the use of various operators like allintext, allinurl, and allintitle, and their functions. It also mentions the use of tools like SQL injection and the impact of Google Dorking on data security, referencing a significant number of companies affected. The assignment concludes with a list of references used. Desklib provides this and other solved assignments for students.
1 out of 5









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)