Google Dorking: Operators, Examples, Threat Actors, and Defense
VerifiedAdded on 2022/11/15
|9
|786
|198
Homework Assignment
AI Summary
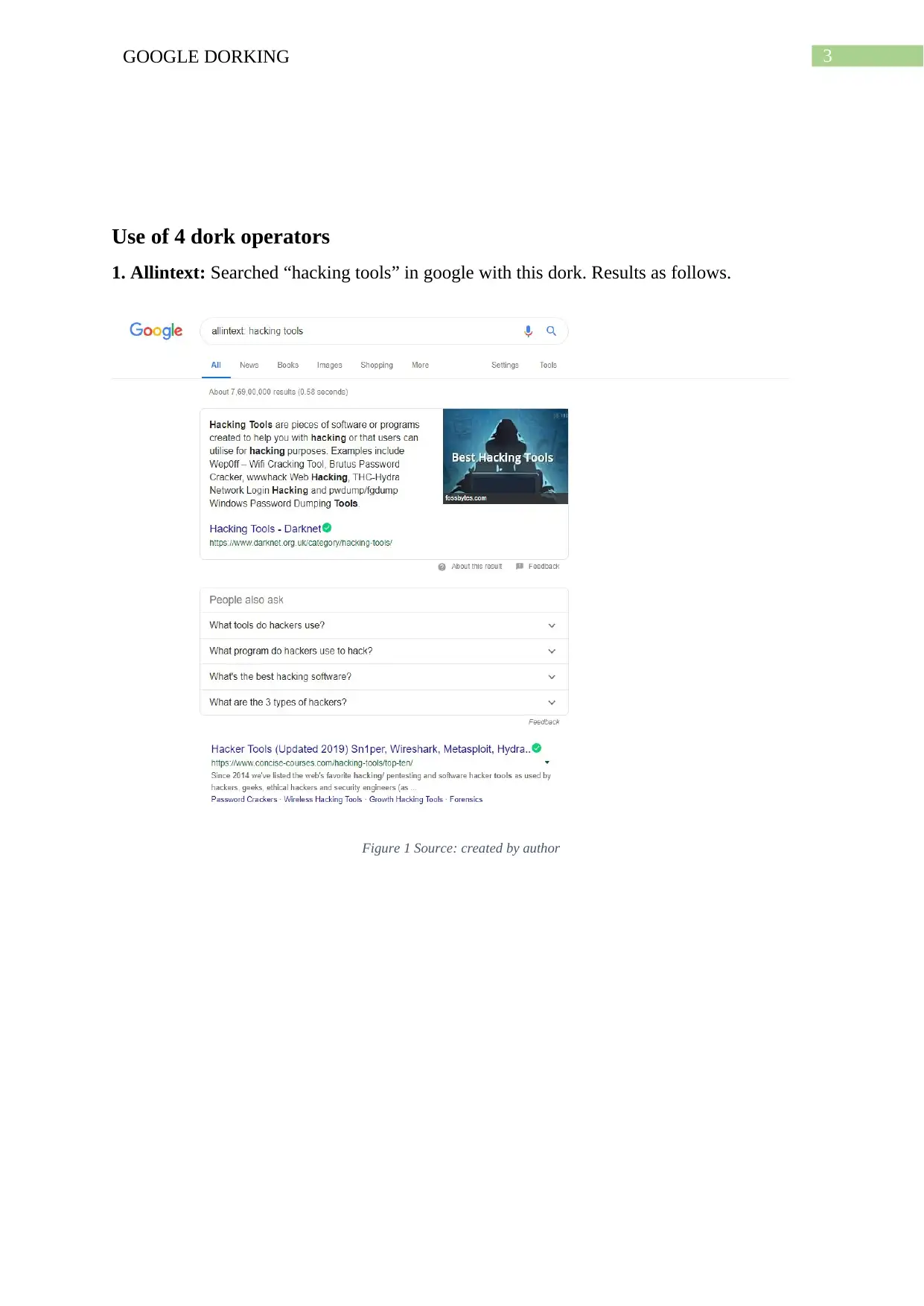
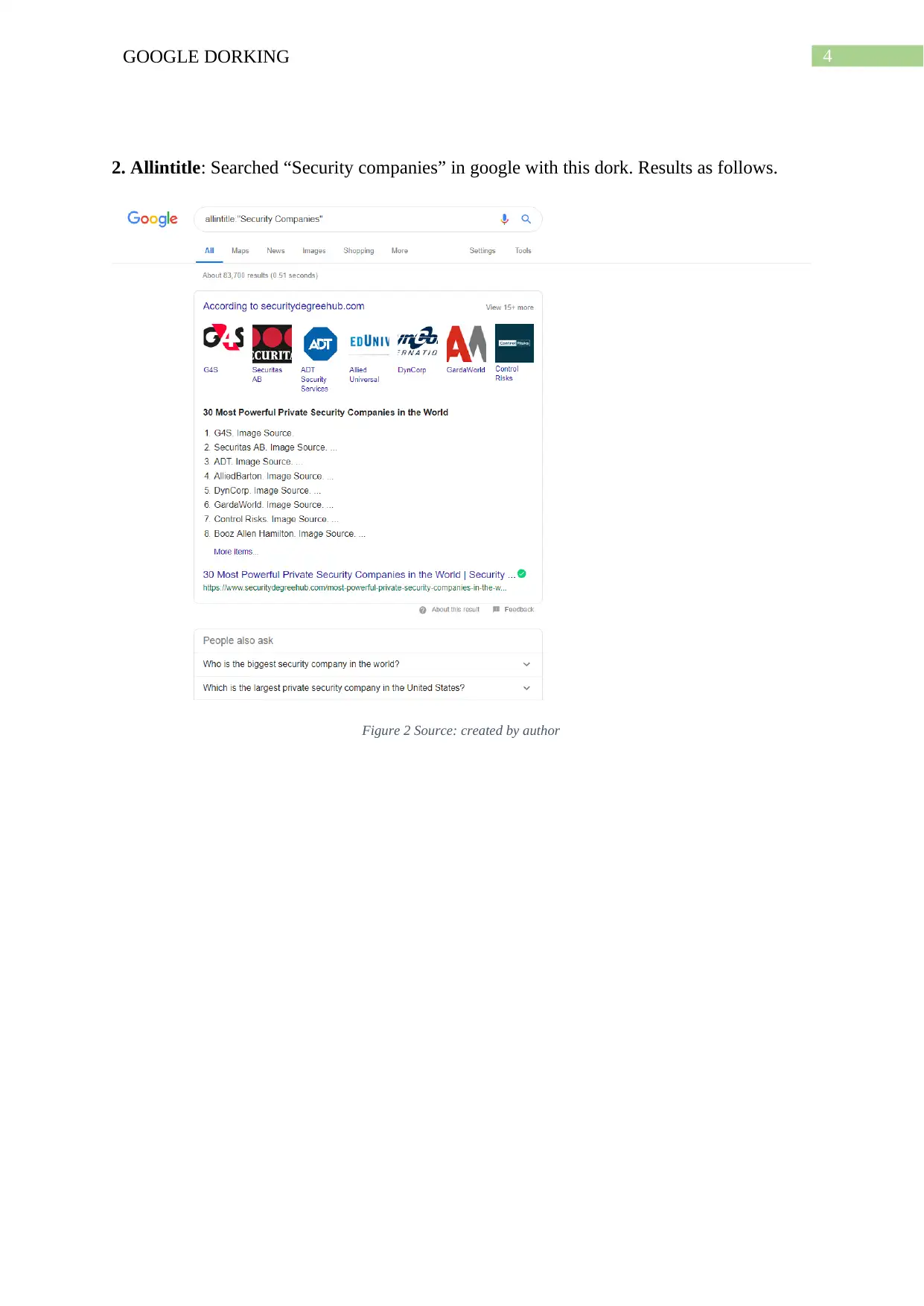
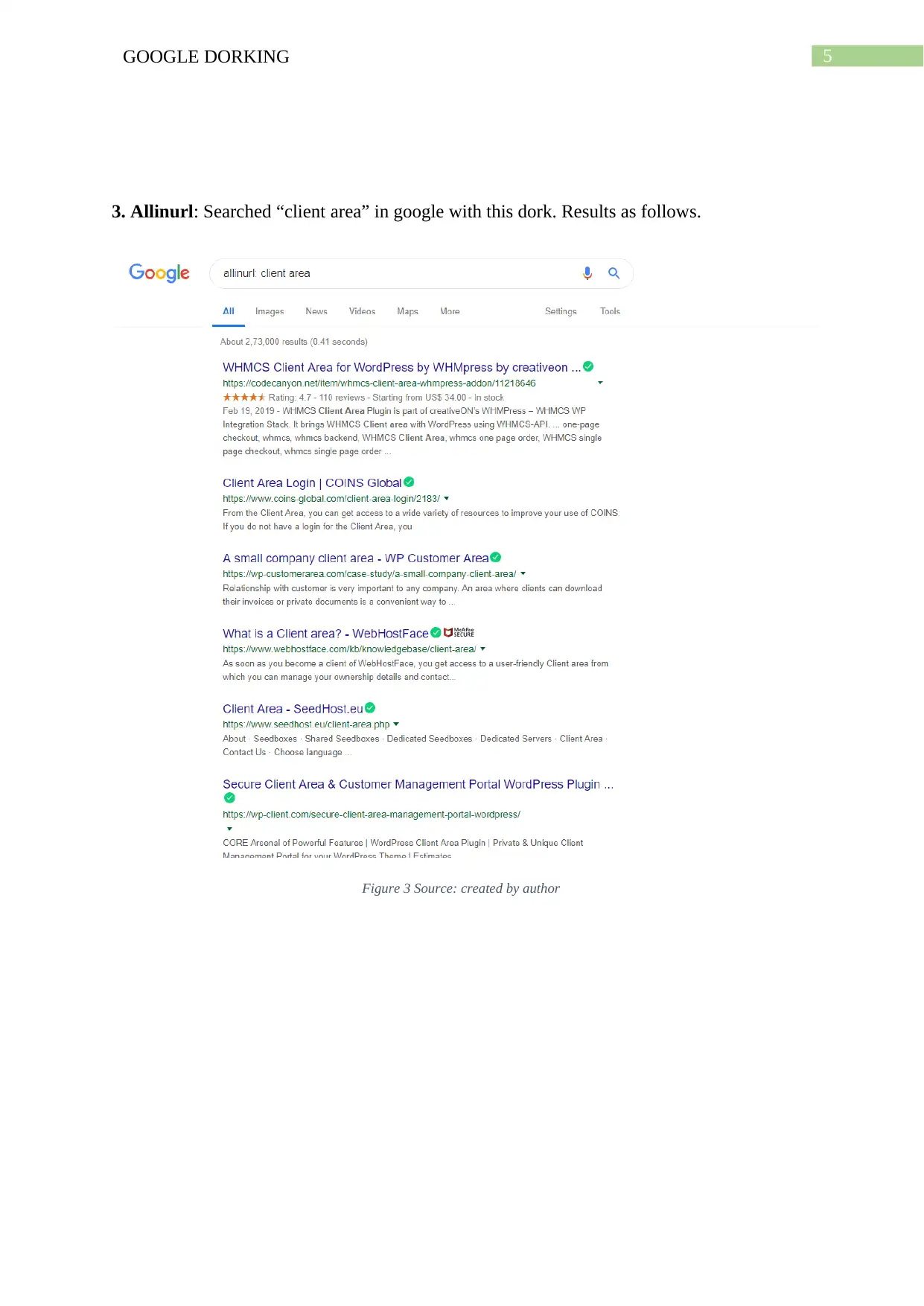
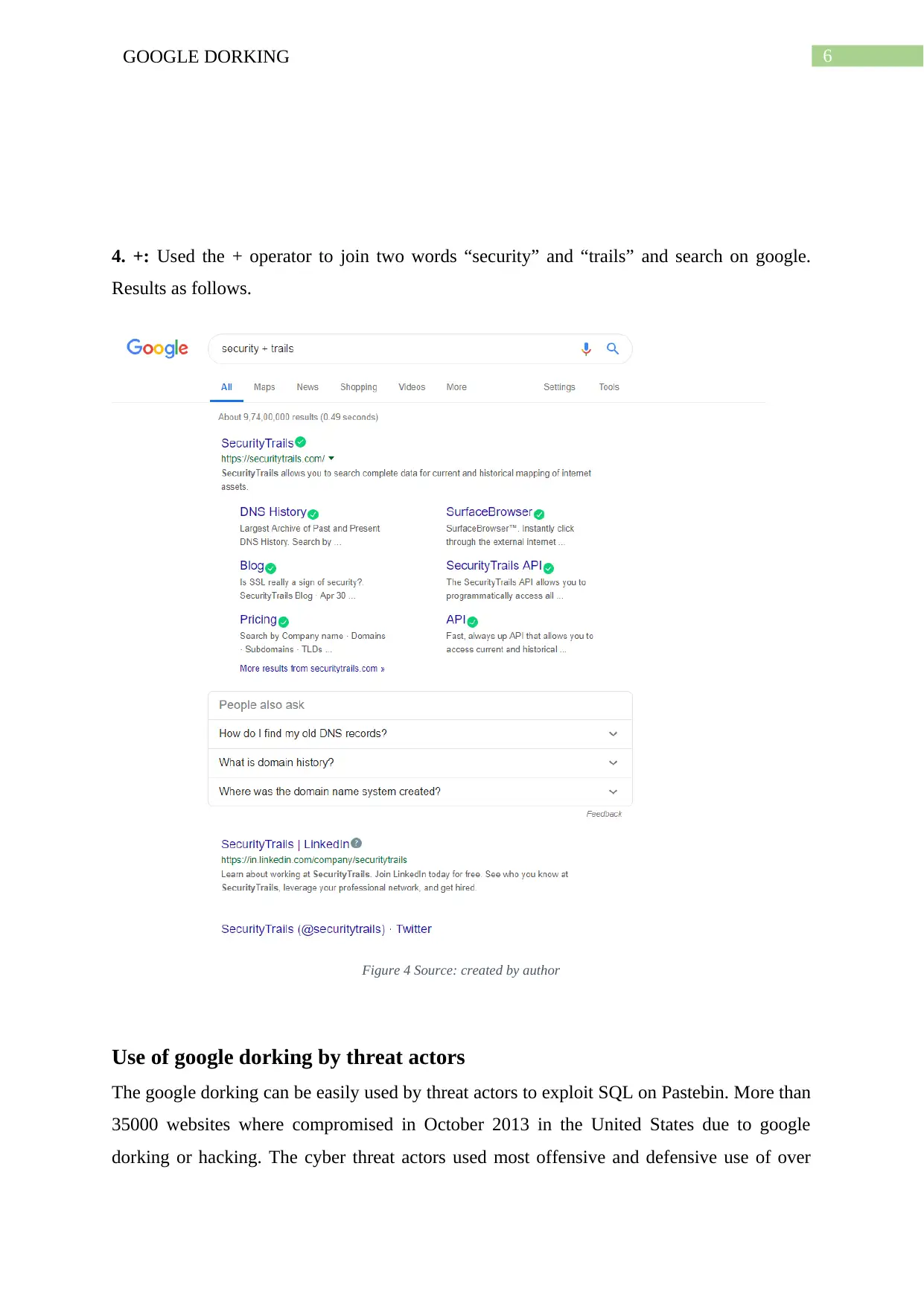
This assignment provides a comprehensive overview of Google dorking, a computer hacking technique that uses Google search to identify security vulnerabilities. It begins by defining Google dorking and its core concept of using advanced search operators to find specific text strings. The assignment details various operators like allintext, allintitle, allinurl, and others, explaining their functionalities with examples. It then discusses how threat actors utilize Google dorking to exploit vulnerabilities, referencing real-world examples like SQL injection attacks. The assignment concludes with recommendations for mitigating Google dorking risks, such as proactive use of dorking techniques to identify vulnerabilities and reducing web presence. The content is supported by figures illustrating the use of different dork operators, and references are provided for further reading. This assignment is a valuable resource for students studying cybersecurity, providing a practical understanding of a common hacking method and defensive strategies.
1 out of 9









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)