Cybersecurity Project: Google Hacking and Security Program Design
VerifiedAdded on 2022/08/12
|9
|344
|34
Project
AI Summary
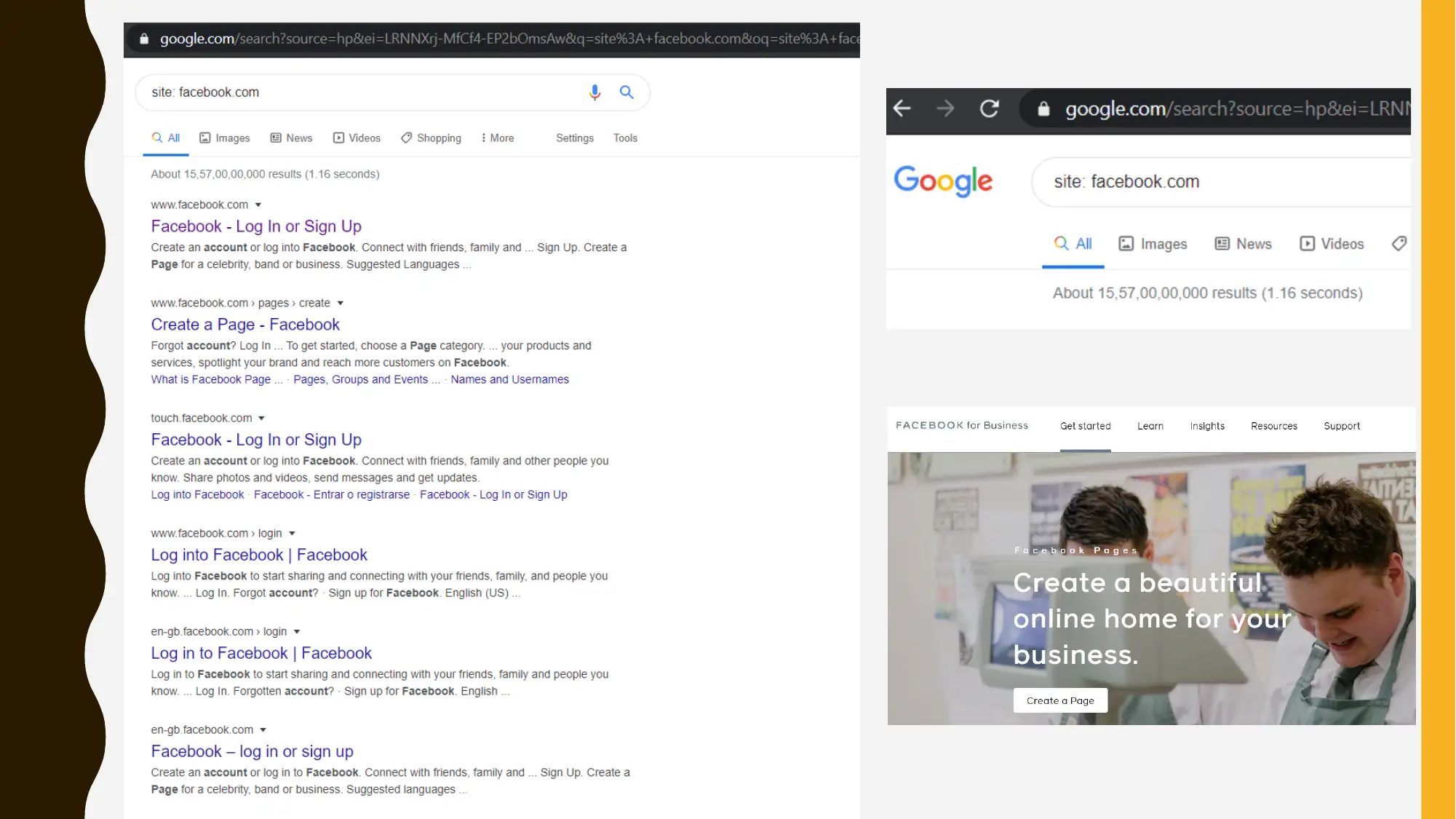
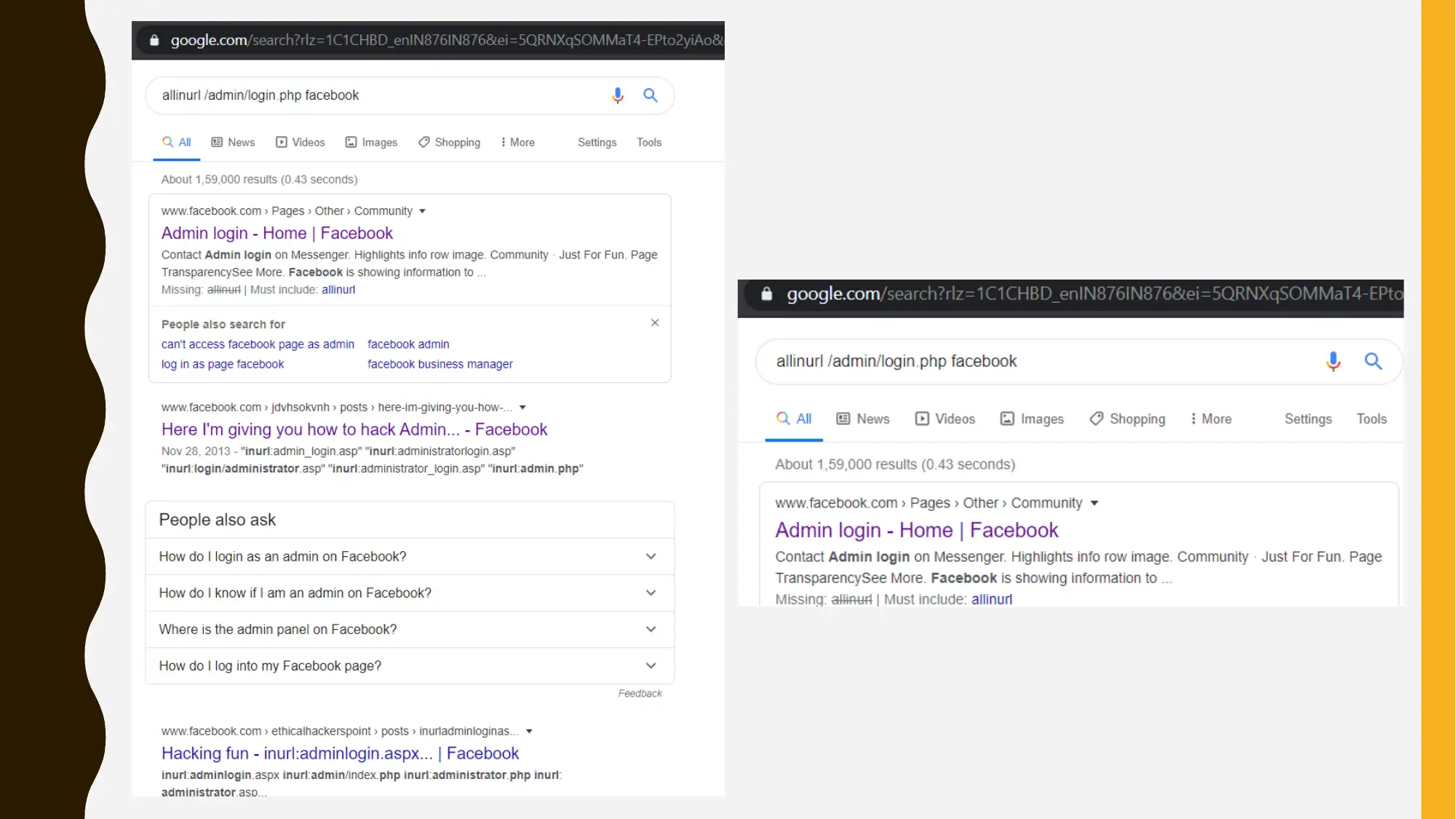
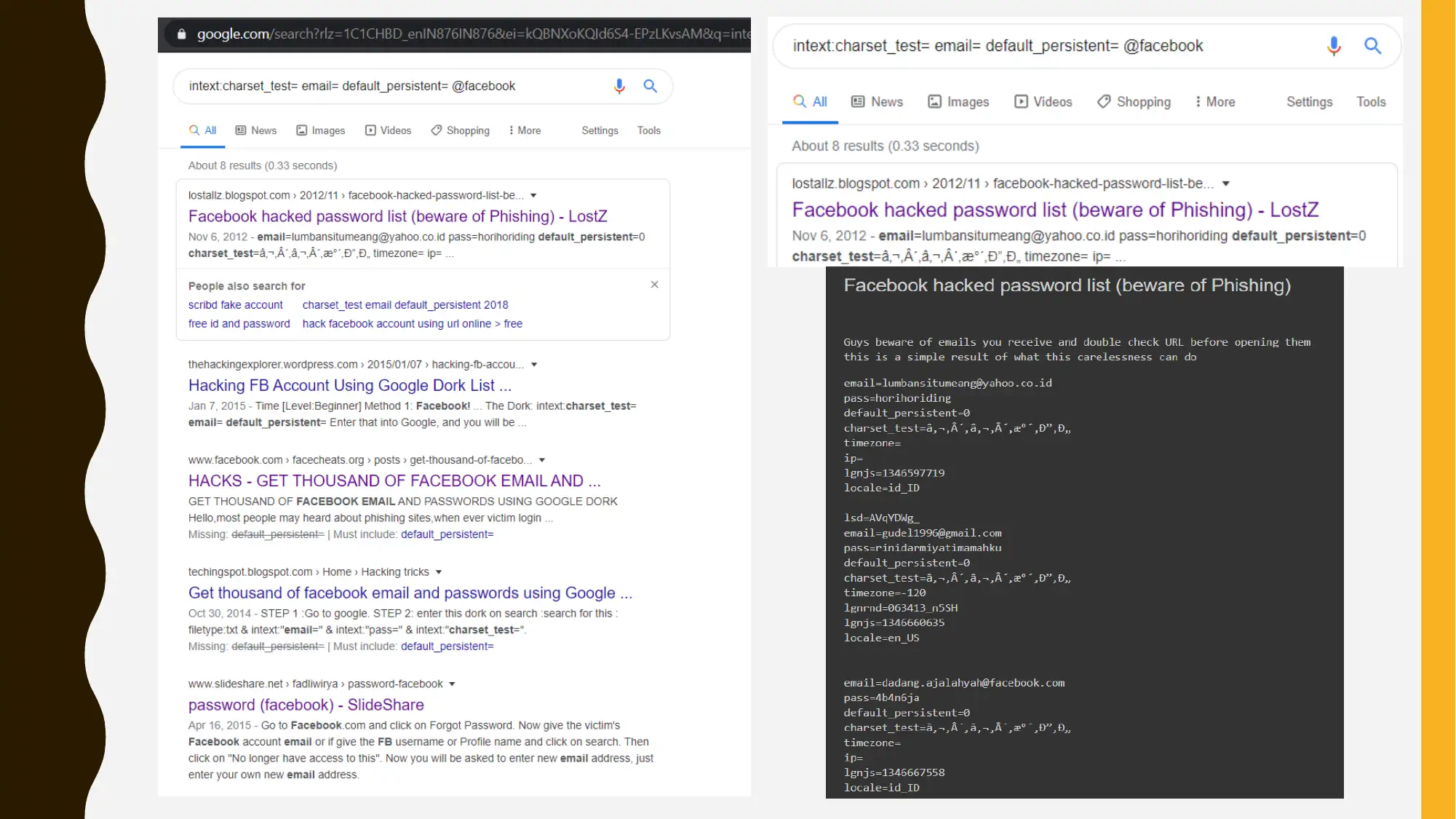
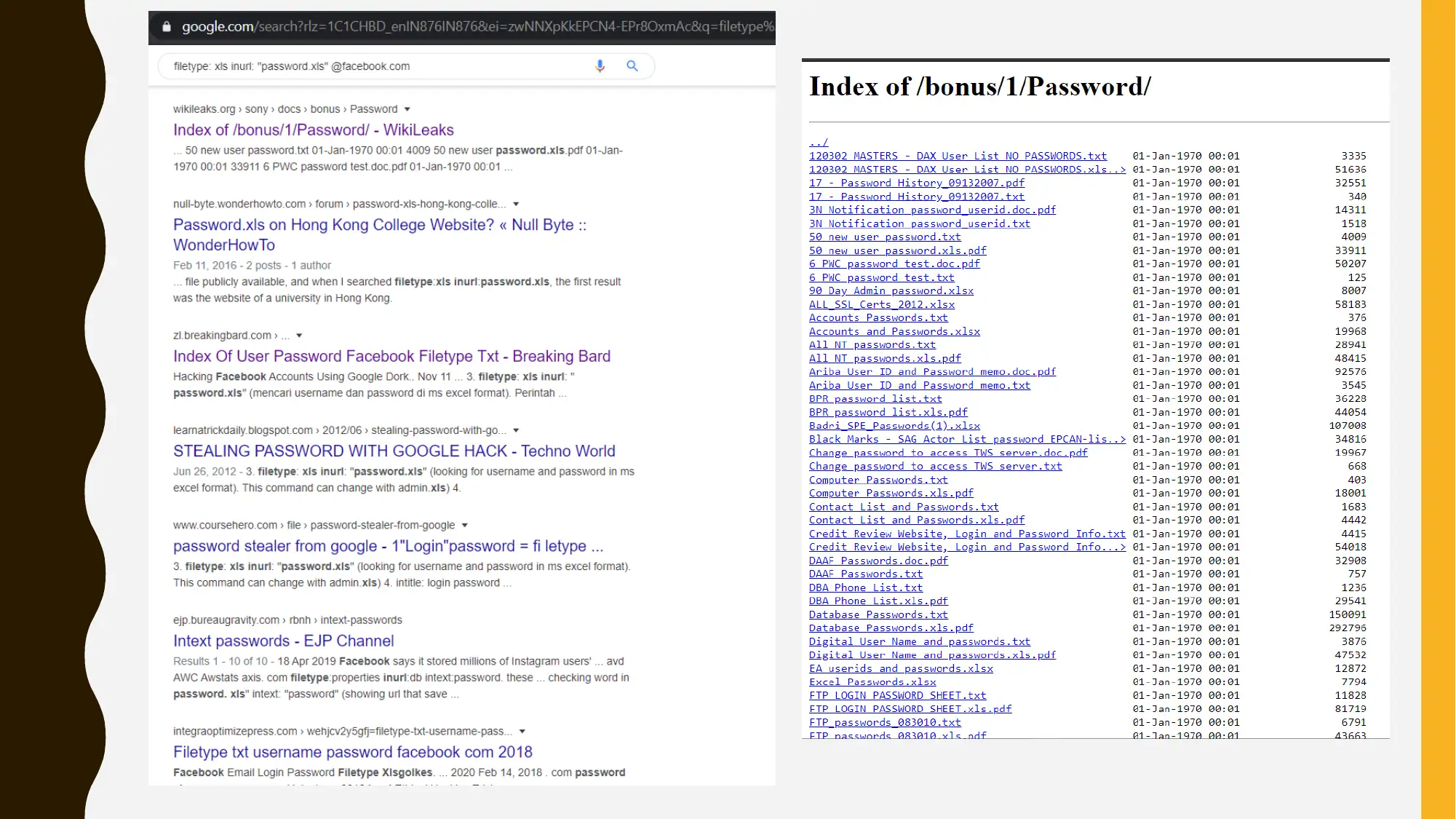
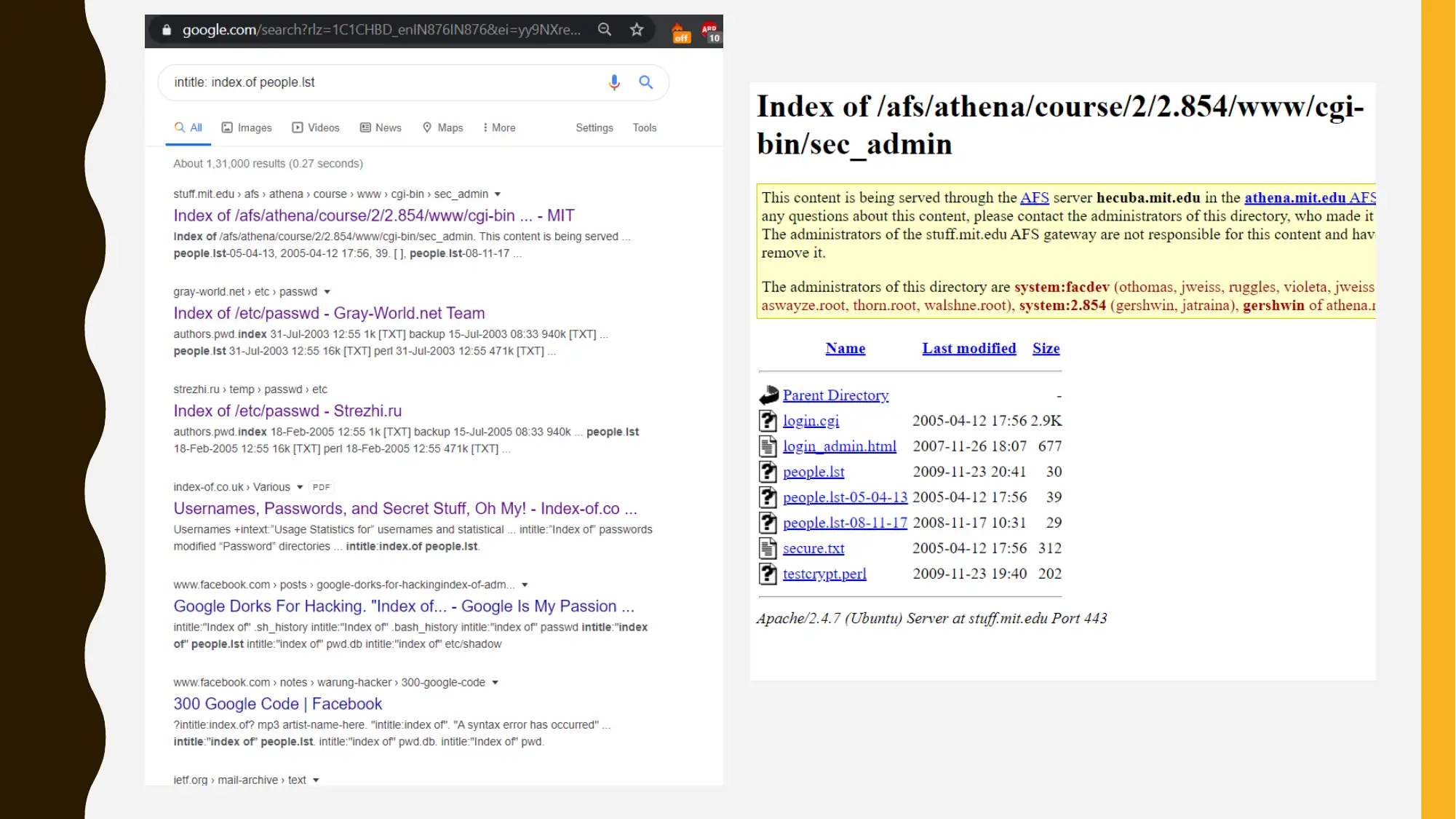
This project focuses on cybersecurity reconnaissance using Google Hacking and Open Source Intelligence (OSINT) techniques. The assignment involves using Google Dorking to gather information about a target organization, specifically Facebook. The student experimented with various Google hacking queries to discover information related to SEO backlinks, competitors, and potential web vulnerabilities. The project also includes an outline for a security program management tabletop exercise, focusing on the NIST Cybersecurity Framework's five pillars: Identify, Protect, Detect, Respond, and Recover, with a specific focus on the 'Identify' pillar, assessing risks, threats, and vulnerabilities. The solution references relevant cybersecurity publications and research papers to support the methodologies used. The assignment is presented as a PowerPoint presentation, detailing the searches and tools used to gather information. The project is a part of group assignment and the solution covers the portion that the student was assigned to do.
1 out of 9








![[object Object]](/_next/static/media/star-bottom.7253800d.svg)