Cybersecurity Project: Google Hacking and Security Program Outline
VerifiedAdded on 2022/08/12
|19
|1026
|29
Project
AI Summary
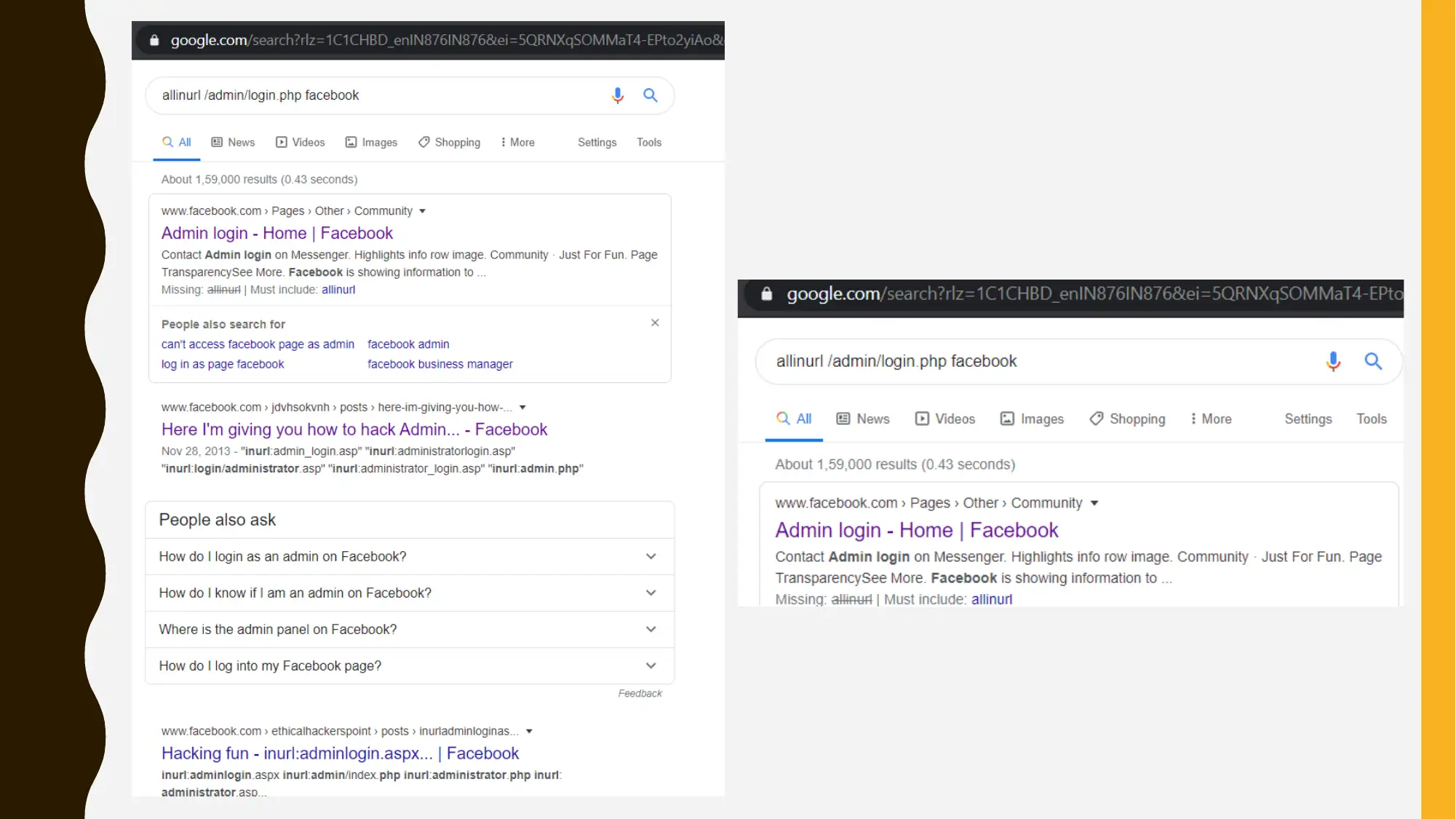
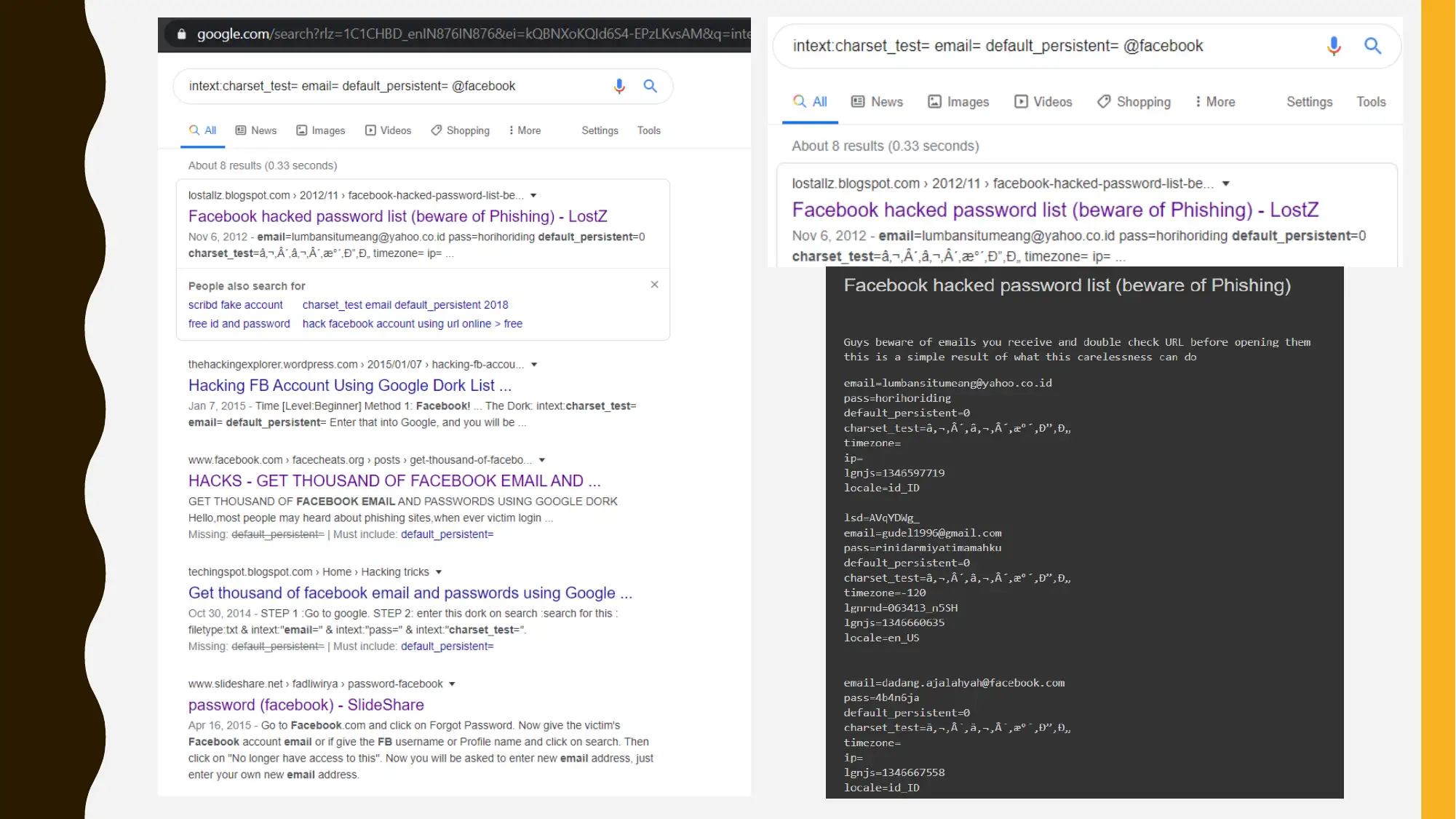
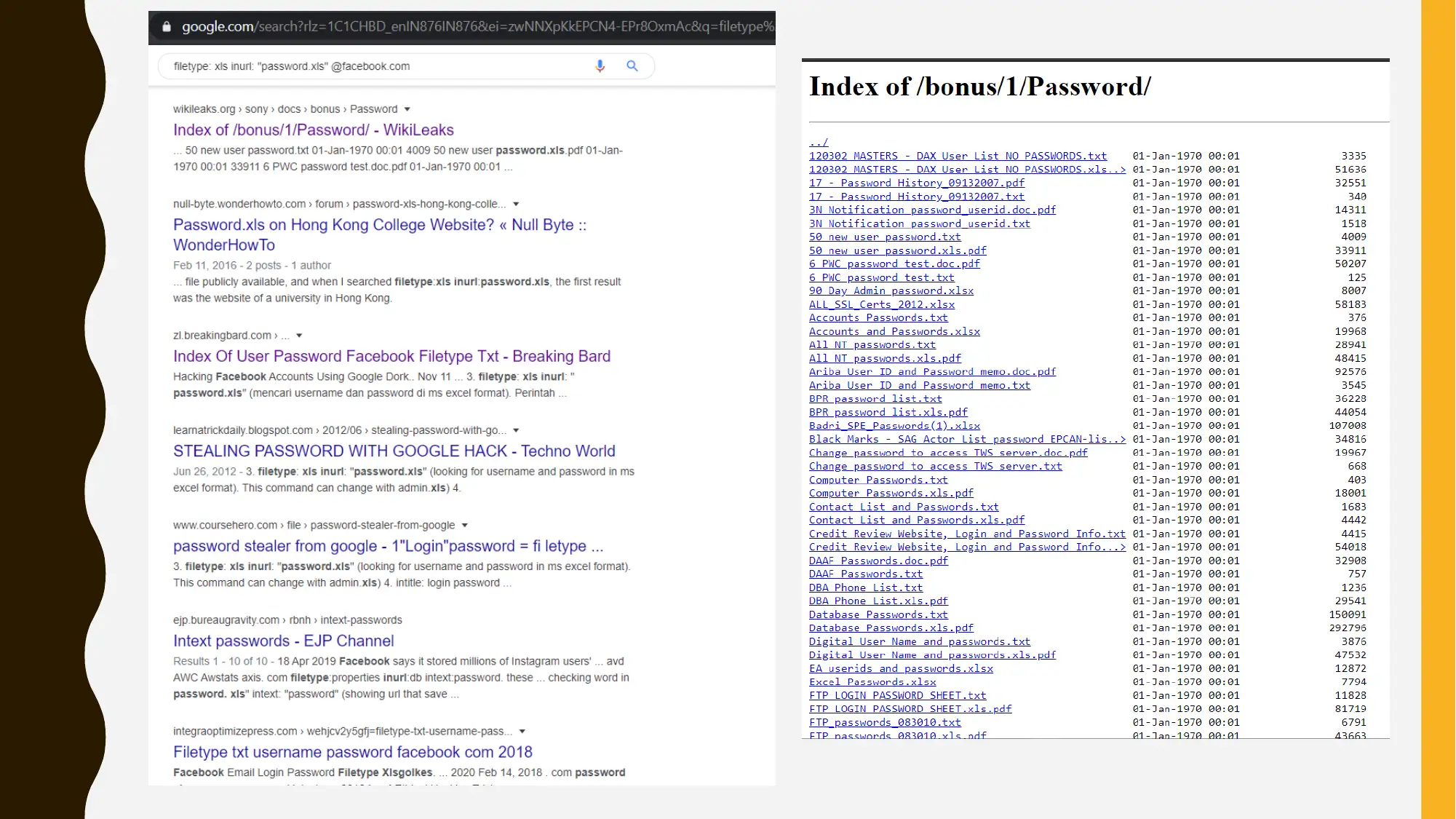
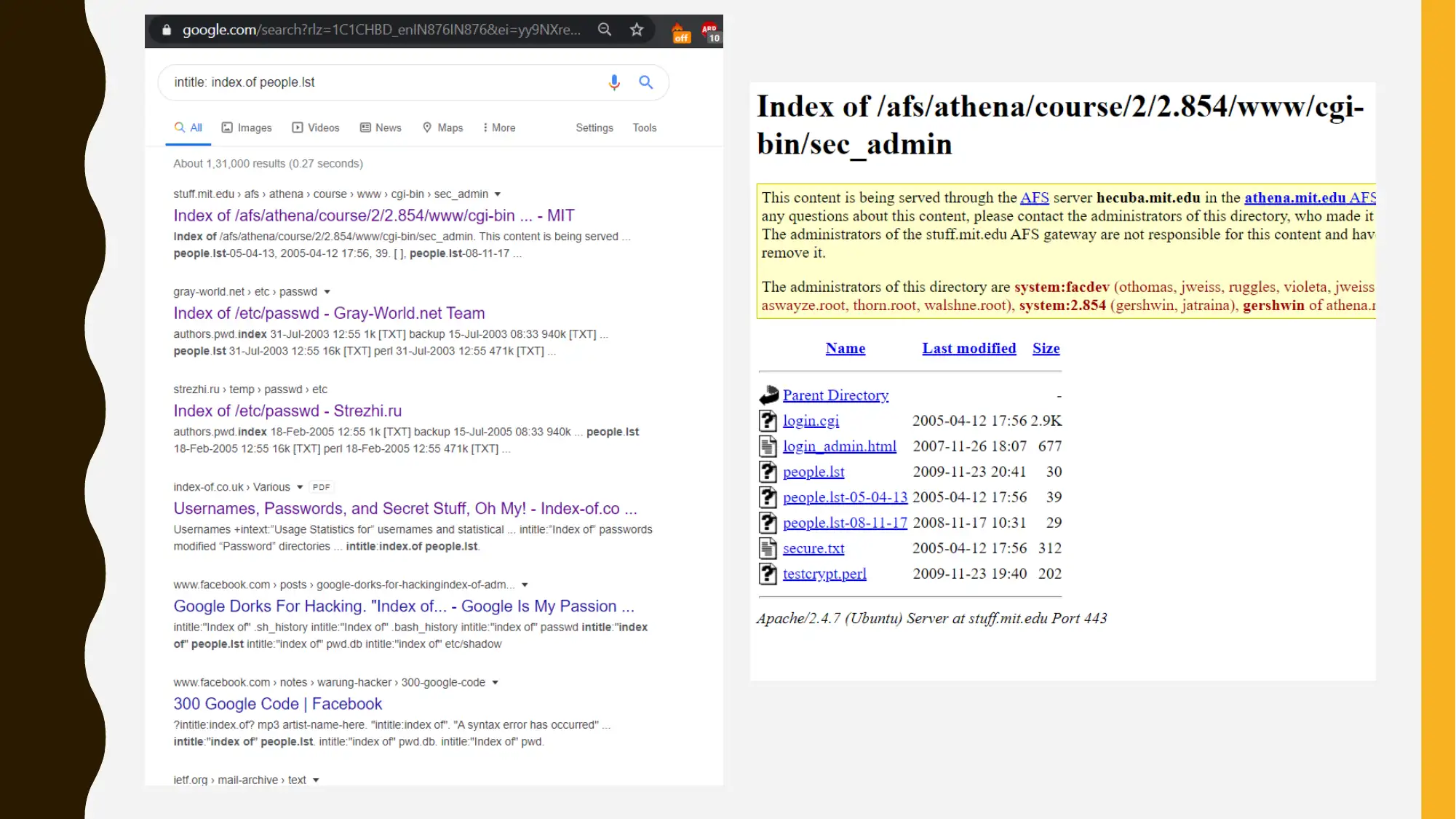
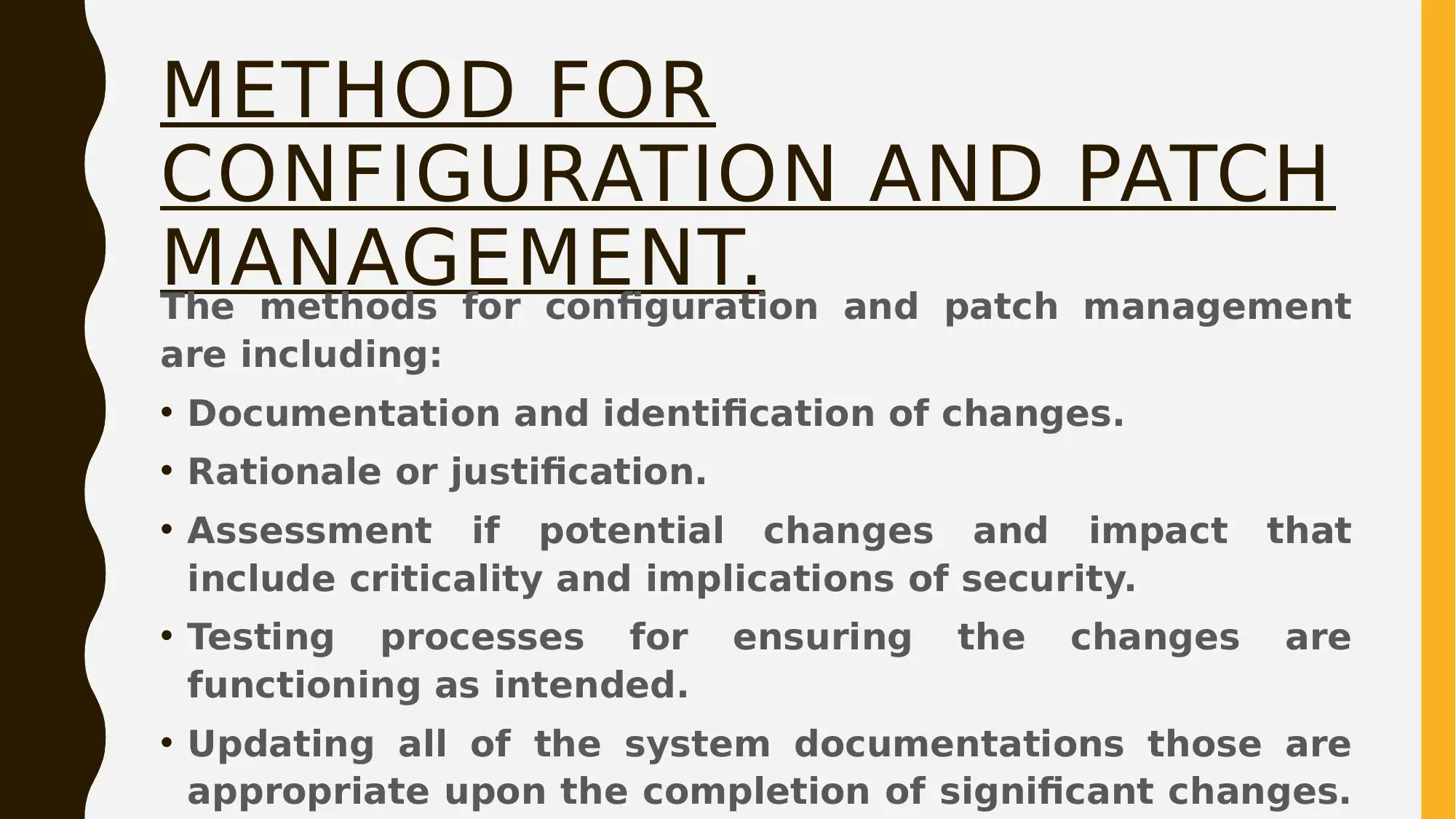
This project is divided into two main parts. Part 1 focuses on Google hacking and open-source intelligence (OSINT), using Google Dorking techniques to gather information about a target organization (Facebook). The student experiments with various search queries to uncover potential vulnerabilities and information. Part 2 outlines a security program management tabletop exercise, covering configuration and patch management, incident response, email security awareness training, and disaster recovery planning. The outline includes documentation, change justification, testing, and communication protocols. The incident response plan details steps for handling security breaches, while the email security training emphasizes awareness of email-borne threats. Finally, the disaster recovery plan outlines steps for resuming operations after an unplanned incident. The project concludes by emphasizing the importance of a comprehensive information security plan in protecting organizational data and ensuring confidentiality, integrity, and availability.
1 out of 19












![[object Object]](/_next/static/media/star-bottom.7253800d.svg)