Risk Assessment and Security Upgrade: Griffith University Pool
VerifiedAdded on 2023/06/12
|17
|3796
|54
Report
AI Summary
This report presents a security risk assessment conducted at the Griffith University swimming pool, focusing on potential threats, vulnerabilities, and recommendations for security enhancements. The assessment methodology involved site visits, consultations with staff, and analysis of existing security measures. Key areas of concern identified include inadequate security in the parking area, unsecured lockers, and potential theft in the candy store. The report proposes several security upgrades, such as installing surveillance cameras, implementing biometric access control, providing private lockers, and increasing physical security presence. It also emphasizes the importance of employee training in security awareness and data protection. The assessment highlights the strengths and weaknesses of current security measures and offers practical recommendations to improve the overall safety and security of the swimming pool area.

Running Head: Risk assessment
Risk assessment
Risk assessment
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Risk assessment 1
Executive summary
In this report risk assessment is done regarding the location of Griffith university
swimming pool the problems that are associated with the pool and the possible solutions have
been discussed. While analyzing the area I found various things that cause risks to the
swimming role. There are various areas were security is needed like locker area, parking zone
and candy stores. Thus in this report the security challenges are identified and they are
recovered by applying various techniques.
Executive summary
In this report risk assessment is done regarding the location of Griffith university
swimming pool the problems that are associated with the pool and the possible solutions have
been discussed. While analyzing the area I found various things that cause risks to the
swimming role. There are various areas were security is needed like locker area, parking zone
and candy stores. Thus in this report the security challenges are identified and they are
recovered by applying various techniques.

Risk assessment 2
Table of Contents
Introduction................................................................................................................................3
Method.......................................................................................................................................3
Map and description of the site..................................................................................................6
Description of functions and personnel......................................................................................7
Assessment of threats and vulnerabilities..................................................................................7
Assessment of security and safety strengths and weaknesses....................................................9
Recommendations....................................................................................................................12
Conclusion................................................................................................................................13
Table of Contents
Introduction................................................................................................................................3
Method.......................................................................................................................................3
Map and description of the site..................................................................................................6
Description of functions and personnel......................................................................................7
Assessment of threats and vulnerabilities..................................................................................7
Assessment of security and safety strengths and weaknesses....................................................9
Recommendations....................................................................................................................12
Conclusion................................................................................................................................13
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Risk assessment 3
Introduction
Principals of security management are the key component that would help in
mitigating the risk associated. In this report the risk assessment is done of the university as
there are various possible areas were attackers can easily attack the place. Security
management is not just using firewalls or defining the access control. It involves managing
the information as well as monitoring that confidentiality, integrity is maintained of all the
assets. In this report discussion is done on various methods available to conduct risk
assessment. Once risks are identified proper techniques are used to make sure that personal as
well as overall security is maintained. Analysis is done on all the possible threats and
vulnerabilities associated in the campus area so that strategies could be developed to gain
advanced security.
Method
Risk is associated in very sector and it affects the overall objective. The objective of
this case is to maintain the security of the swimming pool area by considering societal,
environmental and security outcomes. There are many activities that were analyzed that cause
risk need to be managed. The risk management helps in making decisions by taking
precautions and removing the chances of uncertainty (Li, 2014). In this case I researched the
risk by directly community g to the people in the campus and also by consulting with them
regarding the whole scenario and knowing how the process is undertaken. I visited the place
for establishing and identifying the risks associated and then treating the risk by regularly
monitoring the review (Forouzanfar, Alexander, Anderson, Bachman, Biryukov, Brauer &
Delwiche, 2015). There are several methods to analyze the risk by simply identifying the
consequences and then estimating the cost and other factors that is associated with the risk.
Introduction
Principals of security management are the key component that would help in
mitigating the risk associated. In this report the risk assessment is done of the university as
there are various possible areas were attackers can easily attack the place. Security
management is not just using firewalls or defining the access control. It involves managing
the information as well as monitoring that confidentiality, integrity is maintained of all the
assets. In this report discussion is done on various methods available to conduct risk
assessment. Once risks are identified proper techniques are used to make sure that personal as
well as overall security is maintained. Analysis is done on all the possible threats and
vulnerabilities associated in the campus area so that strategies could be developed to gain
advanced security.
Method
Risk is associated in very sector and it affects the overall objective. The objective of
this case is to maintain the security of the swimming pool area by considering societal,
environmental and security outcomes. There are many activities that were analyzed that cause
risk need to be managed. The risk management helps in making decisions by taking
precautions and removing the chances of uncertainty (Li, 2014). In this case I researched the
risk by directly community g to the people in the campus and also by consulting with them
regarding the whole scenario and knowing how the process is undertaken. I visited the place
for establishing and identifying the risks associated and then treating the risk by regularly
monitoring the review (Forouzanfar, Alexander, Anderson, Bachman, Biryukov, Brauer &
Delwiche, 2015). There are several methods to analyze the risk by simply identifying the
consequences and then estimating the cost and other factors that is associated with the risk.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Risk assessment 4
Some of the methods I used to conduct the security risk assessment of this area.
Brainstorming- This technique includes having a free flow conversation with the
people present in that area to gain the knowledge and understand the perception of
different people. Thus this technique is used to gain imagination about the problems
and concerns in the system. It involves a high level of discussion to understand the
problem deeply.
Checklist-This covers list of hazards or failures that might occur due to violation of
security. With the discussion I also checked all the resources that have been used to
maintain the security (Li, Ma, Yuan & Huang, 2014). This technique is important to
check that the place is covered with various security measures and it secured.
Scenario analysis- I analyzed the entire campus by exploring the implications and
looking for future development. It helped me in fid the best and worst case scenario.
Thus by my methods of risk analysis I found that there are various places which is not
secured. Specially while talking to the staffs over that it was found that swimming pool
area had very small fences so any one can enter that area and try to access the resources.
Some of the methods I used to conduct the security risk assessment of this area.
Brainstorming- This technique includes having a free flow conversation with the
people present in that area to gain the knowledge and understand the perception of
different people. Thus this technique is used to gain imagination about the problems
and concerns in the system. It involves a high level of discussion to understand the
problem deeply.
Checklist-This covers list of hazards or failures that might occur due to violation of
security. With the discussion I also checked all the resources that have been used to
maintain the security (Li, Ma, Yuan & Huang, 2014). This technique is important to
check that the place is covered with various security measures and it secured.
Scenario analysis- I analyzed the entire campus by exploring the implications and
looking for future development. It helped me in fid the best and worst case scenario.
Thus by my methods of risk analysis I found that there are various places which is not
secured. Specially while talking to the staffs over that it was found that swimming pool
area had very small fences so any one can enter that area and try to access the resources.

Risk assessment 5
Also, while analyzing the campus I found that parking system is also not managed
properly as cars are parked in an open area which could be easily robbed. The parking
area is near swimming pool which is easily visible to outsiders and there is no automatic
security system.
Apart from that the desks in which swimmers keep their belongings is just protected
through glass that can easily be broken and there is no one responsible for the belongings
and the front store of candy shop has various candies which could easily be stolen by the
guests.
Also, while analyzing the campus I found that parking system is also not managed
properly as cars are parked in an open area which could be easily robbed. The parking
area is near swimming pool which is easily visible to outsiders and there is no automatic
security system.
Apart from that the desks in which swimmers keep their belongings is just protected
through glass that can easily be broken and there is no one responsible for the belongings
and the front store of candy shop has various candies which could easily be stolen by the
guests.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
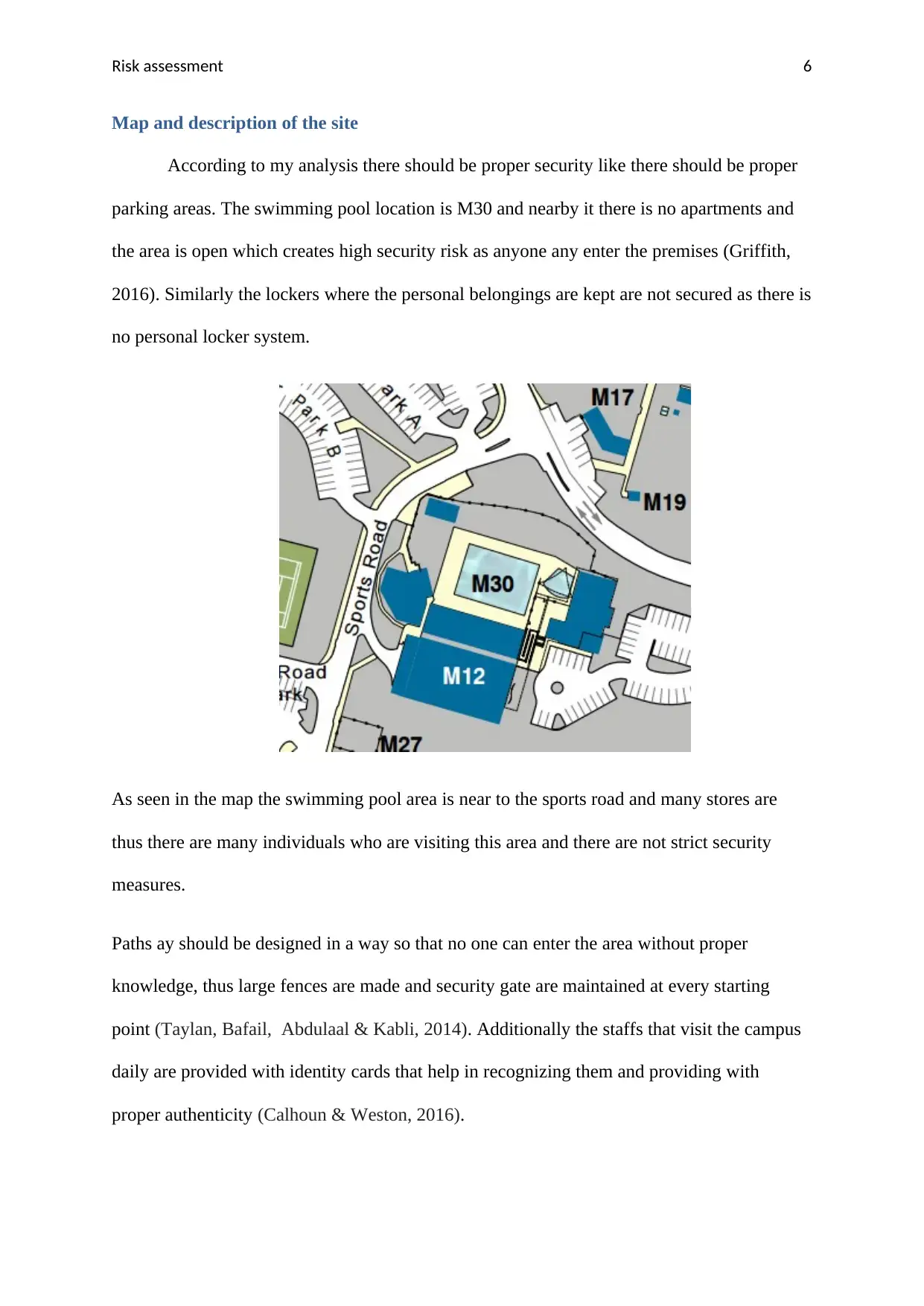
Risk assessment 6
Map and description of the site
According to my analysis there should be proper security like there should be proper
parking areas. The swimming pool location is M30 and nearby it there is no apartments and
the area is open which creates high security risk as anyone any enter the premises (Griffith,
2016). Similarly the lockers where the personal belongings are kept are not secured as there is
no personal locker system.
As seen in the map the swimming pool area is near to the sports road and many stores are
thus there are many individuals who are visiting this area and there are not strict security
measures.
Paths ay should be designed in a way so that no one can enter the area without proper
knowledge, thus large fences are made and security gate are maintained at every starting
point (Taylan, Bafail, Abdulaal & Kabli, 2014). Additionally the staffs that visit the campus
daily are provided with identity cards that help in recognizing them and providing with
proper authenticity (Calhoun & Weston, 2016).
Map and description of the site
According to my analysis there should be proper security like there should be proper
parking areas. The swimming pool location is M30 and nearby it there is no apartments and
the area is open which creates high security risk as anyone any enter the premises (Griffith,
2016). Similarly the lockers where the personal belongings are kept are not secured as there is
no personal locker system.
As seen in the map the swimming pool area is near to the sports road and many stores are
thus there are many individuals who are visiting this area and there are not strict security
measures.
Paths ay should be designed in a way so that no one can enter the area without proper
knowledge, thus large fences are made and security gate are maintained at every starting
point (Taylan, Bafail, Abdulaal & Kabli, 2014). Additionally the staffs that visit the campus
daily are provided with identity cards that help in recognizing them and providing with
proper authenticity (Calhoun & Weston, 2016).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Risk assessment 7
Description of functions and personnel
Utilising principles of security management there are various functions that need to be
undertaken. To maintain the security in swimming pool are there are various alarms that need
to installed these alarms work as an invisible faces who are there to check upon an individual
on all activities (Bennett & Bates, 2015). There are four kinds of alarms that are installed in
the area. Perimeter alarm is use to key an eye on the field and shows indication whenever
some animals or child penetrates into the area.
Even if the fences are small if a robber tries to enter the premises it could easily be identified.
Other than that there are pressure alarms that are used to check that water level and pressure
conditions are normal. Apart from that the entrance gate of swimming pool and locker room
should have an alarm that is use to catch the person who tries to break the locker or tries or
enter the field (Garattini, Jakobsen, Wetterslev, Bertelé, Banzi, Rath & Eikermann, 2016).
The main motive to improve the security challenge is by increasing the supervision as it tracks the area by
paying close attention.
It is important to maintain personal security; there are three components that involve personal security
that is to remain loyal, trustworthy and reliable. It identifies the resources that need to be secured and educating
the individuals to monitor the arrangements (Hawley, et. al, 2016). Personal security is done by controlling
the culture by environment and then detecting the issues that can affect a person. Thus it is very important to
maintain personal security.
Assessment of threats and vulnerabilities
There are various threats and vulnerability that are associated with an organization.
Threat is something than can violet the asset or resource of an area intentionally or accidental.
Description of functions and personnel
Utilising principles of security management there are various functions that need to be
undertaken. To maintain the security in swimming pool are there are various alarms that need
to installed these alarms work as an invisible faces who are there to check upon an individual
on all activities (Bennett & Bates, 2015). There are four kinds of alarms that are installed in
the area. Perimeter alarm is use to key an eye on the field and shows indication whenever
some animals or child penetrates into the area.
Even if the fences are small if a robber tries to enter the premises it could easily be identified.
Other than that there are pressure alarms that are used to check that water level and pressure
conditions are normal. Apart from that the entrance gate of swimming pool and locker room
should have an alarm that is use to catch the person who tries to break the locker or tries or
enter the field (Garattini, Jakobsen, Wetterslev, Bertelé, Banzi, Rath & Eikermann, 2016).
The main motive to improve the security challenge is by increasing the supervision as it tracks the area by
paying close attention.
It is important to maintain personal security; there are three components that involve personal security
that is to remain loyal, trustworthy and reliable. It identifies the resources that need to be secured and educating
the individuals to monitor the arrangements (Hawley, et. al, 2016). Personal security is done by controlling
the culture by environment and then detecting the issues that can affect a person. Thus it is very important to
maintain personal security.
Assessment of threats and vulnerabilities
There are various threats and vulnerability that are associated with an organization.
Threat is something than can violet the asset or resource of an area intentionally or accidental.

Risk assessment 8
Some of the threats associated with this is case is security of resources as well as
personal security. There is no security in the parking which increases the chances of robbers
to steel the cars or can cause damage to the cars and personal belonging. This will lead to
negative effect on the surrounding as people will not visit the place on regular basis with the
fear that their cars could get robbed (Early, et. al, 2016). To remove such proper security
management needs to be done, like keeping the area under camera surveillance and also by
installing biometric check-in so that only true user does enter the premises. If in any miss-
happening occurs camera records could be tracked this improve customers experience and
help in building trust.
The second issue is while keeping the personal belonging in the lockers they should
not be kept in glass cabins as they could be easily broken. This approach is not at all safe thus
a private lockers need to be designed to resolve this threat (Bolante & Dykeman, 2015).
Private lockers provide advanced security as person can keep their expensive belonging
without the fear of getting lost. Additionally, creating private lockers help in providing a
proper facility and gaining customers trust.
Other than that candy stores have only one or two staff that remains busy in serving
the customers. There is variety of candy’s, gifts and creative stuff which remains open and
there are chances that this stuff gets robbed intentionally (Smith, et. al, 2014). These miss-
happenings occur because there is no security. If these threats and vulnerabilities are not
handled properly it would adverse effect the profit margins. There will be less number of
customers vising the place which in turn will cause poor profit margins.
Additionally not only believing on the automatic security equipment’s,
employees working in the university should undertake various measures. Employees should
deeply understand the consequence and should identify all the ways in which security could
Some of the threats associated with this is case is security of resources as well as
personal security. There is no security in the parking which increases the chances of robbers
to steel the cars or can cause damage to the cars and personal belonging. This will lead to
negative effect on the surrounding as people will not visit the place on regular basis with the
fear that their cars could get robbed (Early, et. al, 2016). To remove such proper security
management needs to be done, like keeping the area under camera surveillance and also by
installing biometric check-in so that only true user does enter the premises. If in any miss-
happening occurs camera records could be tracked this improve customers experience and
help in building trust.
The second issue is while keeping the personal belonging in the lockers they should
not be kept in glass cabins as they could be easily broken. This approach is not at all safe thus
a private lockers need to be designed to resolve this threat (Bolante & Dykeman, 2015).
Private lockers provide advanced security as person can keep their expensive belonging
without the fear of getting lost. Additionally, creating private lockers help in providing a
proper facility and gaining customers trust.
Other than that candy stores have only one or two staff that remains busy in serving
the customers. There is variety of candy’s, gifts and creative stuff which remains open and
there are chances that this stuff gets robbed intentionally (Smith, et. al, 2014). These miss-
happenings occur because there is no security. If these threats and vulnerabilities are not
handled properly it would adverse effect the profit margins. There will be less number of
customers vising the place which in turn will cause poor profit margins.
Additionally not only believing on the automatic security equipment’s,
employees working in the university should undertake various measures. Employees should
deeply understand the consequence and should identify all the ways in which security could
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Risk assessment 9
be violated (MacGregor, et. al, 2015). Thus employees plan and design ways to make sure
that security is maintained in all area. Physical security is most important that could be
achieved by keeping security guards at every entrance this strictness will create a fear among
robbers. Thus they will find difficult to enter the system and will reduces the chance of false
activities taking place. Physical security is not the key concern; employee working in this
university should also take care of the sensitive data stored of the students and workers
working in the college (Ferson, Pastorok, Bartell & Ginzburg, 2016). The sensitive
information is stored on internet and that is not totally secure as cybercrime is increasing day
by day. Thus it is important for the employees to know about all the possible attacks so that
they can proper precautions. There are various soft wares that need to be installed to avoid
the chances off data leakage and reduce the possibilities of cyber-attacks (Hollister &
Scalora, 2015). Additionally, employees should be aware who are authorized users and
should dis-allow cust9mers who do not have proper registration for using the resources.
Assessment of security and safety strengths and weaknesses
Security risk assessment is an important process that is used for discovering the
concerns and correcting the measures to prevent any security problems. Risk assessment is an
integral part of managing the risk; it is done by designing various security levels.
There are various techniques used to manage the security like security threat assessment,
security architecture review, automated scanning of external entities using tools, automated
analysis that penetrated manual testing (Suder & Kahraman, 2015). While assessing the
security measures it is used to identify the possible type of threats that can hit the application,
once the vulnerabilities are identified then they are estimated in terms of impact that may
cause on the business. Analysing and accessing the consequences help in determining the
be violated (MacGregor, et. al, 2015). Thus employees plan and design ways to make sure
that security is maintained in all area. Physical security is most important that could be
achieved by keeping security guards at every entrance this strictness will create a fear among
robbers. Thus they will find difficult to enter the system and will reduces the chance of false
activities taking place. Physical security is not the key concern; employee working in this
university should also take care of the sensitive data stored of the students and workers
working in the college (Ferson, Pastorok, Bartell & Ginzburg, 2016). The sensitive
information is stored on internet and that is not totally secure as cybercrime is increasing day
by day. Thus it is important for the employees to know about all the possible attacks so that
they can proper precautions. There are various soft wares that need to be installed to avoid
the chances off data leakage and reduce the possibilities of cyber-attacks (Hollister &
Scalora, 2015). Additionally, employees should be aware who are authorized users and
should dis-allow cust9mers who do not have proper registration for using the resources.
Assessment of security and safety strengths and weaknesses
Security risk assessment is an important process that is used for discovering the
concerns and correcting the measures to prevent any security problems. Risk assessment is an
integral part of managing the risk; it is done by designing various security levels.
There are various techniques used to manage the security like security threat assessment,
security architecture review, automated scanning of external entities using tools, automated
analysis that penetrated manual testing (Suder & Kahraman, 2015). While assessing the
security measures it is used to identify the possible type of threats that can hit the application,
once the vulnerabilities are identified then they are estimated in terms of impact that may
cause on the business. Analysing and accessing the consequences help in determining the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Risk assessment 10
priorities that are attached to the system so that mitigation of risk becomes easy. There are
various strength and weakness associated with assessing the security issues.
Strengths
Assessment helps in focusing on all the activities and then defining the targets to meet
the security concerns.
Performing threat assessment is useful for end users as it allows them to focus on the
requirements and work on operations to maintain security.
It helps in finding the raw vulnerabilities (Icasa, 2017).
It provides deep knowledge about how attackers can hit the system and spoil the
security.
Assessment is helpful for testing team as it helps in knowing the how factor and the
why factor of business security so that control can be done on security constraints.
It is helpful as it reduces the time and has the ability to provide better baselines to
remove the on-going vulnerabilities (Fernández & García , 2017).
It reduces the time by identifying the content and removing the chances of
misconfiguration.
Weakness
Even after identifying and performing proper assessment there are few
vulnerabilities that are left undiscovered.
The complex architecture makes it difficult in identifying the political as well as
security issues involved in the system (Sciencedirect, 2016).
priorities that are attached to the system so that mitigation of risk becomes easy. There are
various strength and weakness associated with assessing the security issues.
Strengths
Assessment helps in focusing on all the activities and then defining the targets to meet
the security concerns.
Performing threat assessment is useful for end users as it allows them to focus on the
requirements and work on operations to maintain security.
It helps in finding the raw vulnerabilities (Icasa, 2017).
It provides deep knowledge about how attackers can hit the system and spoil the
security.
Assessment is helpful for testing team as it helps in knowing the how factor and the
why factor of business security so that control can be done on security constraints.
It is helpful as it reduces the time and has the ability to provide better baselines to
remove the on-going vulnerabilities (Fernández & García , 2017).
It reduces the time by identifying the content and removing the chances of
misconfiguration.
Weakness
Even after identifying and performing proper assessment there are few
vulnerabilities that are left undiscovered.
The complex architecture makes it difficult in identifying the political as well as
security issues involved in the system (Sciencedirect, 2016).

Risk assessment 11
The security principals can be linked to the theory SCP, which stands for structure, conduct
and performance. This theory relates the structure of the university with its performance. In
this list of assets are structured to conduct the research and measure the security efficiency.
According to the structure, conduct and performance theory it has direct impact on the issues
caused to environment structure. It is also used to identify the direct influence on the
economic concerns which may affect the performance. Additionally, it also includes feedback
that affects the structure and also helps in better improvement. Knowing about the past
experience is useful as it provides additional support in designing plans. Additionally, there
are some external factors like legal or political interventions that also affect the system.
In the given scenario assessment is security is considered as important factor as it helps in
finding all the possibilities that could violet the security of capes. Once the area has been
identified from the hackers could enter the premises, proper plans are designed to make sure
campus is free from attackers. The plans are then imposed by using some tools that identify
all the false activities. Assessment helps in analysing the ways attacker and hit the system and
then implementing the concern. Like as the risk was identified in the locker room, swimming
pool area and candy stores. So, that proper precaution was applied to avoid the chances of
future security violation. Security assessment helped in focusing the impact of vulnerabilities
by reviewing the system and applications. Reviewing method helped in understanding the
critical phase of the system. After reviewing method, examination method arises that helps in
checking the technical analysis of the system by installing firewalls and intrusion detection
systems. Lastly, testing method is used to check that no bugs have penetrated in the system
(Potts, et. al, 2016). It is a process when someone imitates the security by breaking the
security. The assessment method is a tool that provides improvement and allows the
organization to achieve security goals that mitigates risk.
The security principals can be linked to the theory SCP, which stands for structure, conduct
and performance. This theory relates the structure of the university with its performance. In
this list of assets are structured to conduct the research and measure the security efficiency.
According to the structure, conduct and performance theory it has direct impact on the issues
caused to environment structure. It is also used to identify the direct influence on the
economic concerns which may affect the performance. Additionally, it also includes feedback
that affects the structure and also helps in better improvement. Knowing about the past
experience is useful as it provides additional support in designing plans. Additionally, there
are some external factors like legal or political interventions that also affect the system.
In the given scenario assessment is security is considered as important factor as it helps in
finding all the possibilities that could violet the security of capes. Once the area has been
identified from the hackers could enter the premises, proper plans are designed to make sure
campus is free from attackers. The plans are then imposed by using some tools that identify
all the false activities. Assessment helps in analysing the ways attacker and hit the system and
then implementing the concern. Like as the risk was identified in the locker room, swimming
pool area and candy stores. So, that proper precaution was applied to avoid the chances of
future security violation. Security assessment helped in focusing the impact of vulnerabilities
by reviewing the system and applications. Reviewing method helped in understanding the
critical phase of the system. After reviewing method, examination method arises that helps in
checking the technical analysis of the system by installing firewalls and intrusion detection
systems. Lastly, testing method is used to check that no bugs have penetrated in the system
(Potts, et. al, 2016). It is a process when someone imitates the security by breaking the
security. The assessment method is a tool that provides improvement and allows the
organization to achieve security goals that mitigates risk.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





