University Cybersecurity Report: Hacking a Major 21st Century Problem
VerifiedAdded on 2021/04/24
|9
|1702
|125
Report
AI Summary
This report provides a comprehensive overview of hacking as a significant problem in the 21st century. It begins by defining cybercrime and hacking, then delves into the motivations behind hacking, including hobby, theft, and activism. The report categorizes hackers into white hat, black hat, and grey hat, explaining their roles and intentions. It highlights the effects of hacking through a case study involving a major bank data breach, emphasizing the financial and reputational damage. Furthermore, the report outlines preventive measures, such as choosing the right firewall, updating antivirus software, and responding to system compromises. A Gantt chart is included to illustrate the recovery process from a hacking incident. The report concludes that organizations must implement robust cybersecurity measures to mitigate the threats posed by hacking, emphasizing the importance of network security in the modern digital landscape. Access this report and more on Desklib, a platform providing past papers and solved assignments for students.

Running head: HACKING: A MAJOR PROBLEM OF THE 21ST CENTURY
Hacking: A Major Problem of the 21st Century
Name of the student:
Name of the University:
Author note:
Hacking: A Major Problem of the 21st Century
Name of the student:
Name of the University:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
HACKING: A MAJOR PROBLEM OF THE 21ST CENTURY
Executive Summary
The report aims at describing the threats of hacking alongside the types of hackers who threat
the cyber world. A possible case study shall also be discussed to highlight the graveness of
the hack attacks. The report would finally help to conclude the importance of cybersecurity to
protect the society against one such problem, in the 21st century.
HACKING: A MAJOR PROBLEM OF THE 21ST CENTURY
Executive Summary
The report aims at describing the threats of hacking alongside the types of hackers who threat
the cyber world. A possible case study shall also be discussed to highlight the graveness of
the hack attacks. The report would finally help to conclude the importance of cybersecurity to
protect the society against one such problem, in the 21st century.

3
HACKING: A MAJOR PROBLEM OF THE 21ST CENTURY
Table of Contents
Introduction................................................................................................................................4
Cybercrime and Hacking............................................................................................................4
Reasons of Hacking....................................................................................................................5
Effects of Hacking......................................................................................................................6
Preventive measures against hacking.........................................................................................7
Gantt Chart.................................................................................................................................7
Conclusion..................................................................................................................................8
HACKING: A MAJOR PROBLEM OF THE 21ST CENTURY
Table of Contents
Introduction................................................................................................................................4
Cybercrime and Hacking............................................................................................................4
Reasons of Hacking....................................................................................................................5
Effects of Hacking......................................................................................................................6
Preventive measures against hacking.........................................................................................7
Gantt Chart.................................................................................................................................7
Conclusion..................................................................................................................................8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4
HACKING: A MAJOR PROBLEM OF THE 21ST CENTURY
Introduction
With the advent of technology, human life has only become easier with time.
Computers have now become the mandatory option to conduct a business of any fashion,
successfully. However, these systems cannot be kept isolated. It is extremely necessary to
have network-facilitated connections. Henceforth, the business or the entire information
system is now exposed to the external world. This is where the threat from hacking peeps in.
Cybersecurity is the basic need of the hour (Von and Van 2013). Hacking and other such
similar cybercrimes cost millions to many organizations and personalities all over the world,
every year. This report aims at describing the well-known facts about hacking and highlight
its effects in the modern society. Finally, recommendable solutions to protect against this
fatal issue shall also be proposed with definitive diagrammatic description through a Gantt
chart.
Cybercrime and Hacking
Before conducting a detailed research on what hacking is and how harmful it can
prove to be, first it is important to emphasize on the aspects of cybercrime. Any form of
crime that takes place due to the involvement of computing devices and a network can be
termed as cybercrime. Such crimes are committed against groups or individuals in order to
harm the individuals or organization’s fame and finance. There are several forms of
cybercrime. Piracy and hacking are two of the most common forms that are dominant all over
the world presently. Hacking can be defined as a method to identify weakness in a computer
system or network and gain access to the system by exploiting its weaknesses. Elmaghraby
and Losavio (2014), states that with more and more devices being connected to the internet,
thanks to smart city concepts and IOT (Internet of Things) cyber threats are growing as well.
HACKING: A MAJOR PROBLEM OF THE 21ST CENTURY
Introduction
With the advent of technology, human life has only become easier with time.
Computers have now become the mandatory option to conduct a business of any fashion,
successfully. However, these systems cannot be kept isolated. It is extremely necessary to
have network-facilitated connections. Henceforth, the business or the entire information
system is now exposed to the external world. This is where the threat from hacking peeps in.
Cybersecurity is the basic need of the hour (Von and Van 2013). Hacking and other such
similar cybercrimes cost millions to many organizations and personalities all over the world,
every year. This report aims at describing the well-known facts about hacking and highlight
its effects in the modern society. Finally, recommendable solutions to protect against this
fatal issue shall also be proposed with definitive diagrammatic description through a Gantt
chart.
Cybercrime and Hacking
Before conducting a detailed research on what hacking is and how harmful it can
prove to be, first it is important to emphasize on the aspects of cybercrime. Any form of
crime that takes place due to the involvement of computing devices and a network can be
termed as cybercrime. Such crimes are committed against groups or individuals in order to
harm the individuals or organization’s fame and finance. There are several forms of
cybercrime. Piracy and hacking are two of the most common forms that are dominant all over
the world presently. Hacking can be defined as a method to identify weakness in a computer
system or network and gain access to the system by exploiting its weaknesses. Elmaghraby
and Losavio (2014), states that with more and more devices being connected to the internet,
thanks to smart city concepts and IOT (Internet of Things) cyber threats are growing as well.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5
HACKING: A MAJOR PROBLEM OF THE 21ST CENTURY
It is necessary to understand the concept of hacking from the perspective of the
various forms of hackers. It requires handsome expertise and intelligence in order to hack
into any secured network environment. Hackers are broadly categorized as white hat, black
hat and grey hat hackers. Ethical hackers are generally referred to as the white hat hackers.
Their job is to try to hack into their own systems and make it hack proof. These people make
an organization’s network more secured by through constant testing of its vulnerability
(Baase 2012). Black hat and grey hat hackers are the ones to do the dirty work. They hack
into network systems with the aim to take control of them and gain personally. Black hat
hackers however leave a note for the network admin to let them know of the weakness that
their system possesses, also through doing this, they can advertise their presence before the
world (Sethi and Gera 2014). Grey hat hackers are considered to be the most dangerous ones
among the lost. They commit crimes by stealing confidential organizational information for
personal or financial gains. They generally belong to large groups who work under the cover.
All types of hacking barring the white hat professionals are considered to be acts of
cybercrime.
Reasons of Hacking
Apart from the causes of hacking where an ill-maintained and unsecured network
lures the hackers, most of the general mass is still unaware of how hackers work towards the
fulfilment of their needs. There are various reasons that compel a personnel or group to
hacking. They are as follows:
A hobby: Most of the hackers hack for the foremost reason of self-pleasure. They
tend to get immense satisfaction from hacking into the victim’s system and leave a
note in order to spread awareness about their existence.
To steal and leak information: Some hackers are only interested to steal what is not
theirs. This may be through stealing classified information or digitally stored
HACKING: A MAJOR PROBLEM OF THE 21ST CENTURY
It is necessary to understand the concept of hacking from the perspective of the
various forms of hackers. It requires handsome expertise and intelligence in order to hack
into any secured network environment. Hackers are broadly categorized as white hat, black
hat and grey hat hackers. Ethical hackers are generally referred to as the white hat hackers.
Their job is to try to hack into their own systems and make it hack proof. These people make
an organization’s network more secured by through constant testing of its vulnerability
(Baase 2012). Black hat and grey hat hackers are the ones to do the dirty work. They hack
into network systems with the aim to take control of them and gain personally. Black hat
hackers however leave a note for the network admin to let them know of the weakness that
their system possesses, also through doing this, they can advertise their presence before the
world (Sethi and Gera 2014). Grey hat hackers are considered to be the most dangerous ones
among the lost. They commit crimes by stealing confidential organizational information for
personal or financial gains. They generally belong to large groups who work under the cover.
All types of hacking barring the white hat professionals are considered to be acts of
cybercrime.
Reasons of Hacking
Apart from the causes of hacking where an ill-maintained and unsecured network
lures the hackers, most of the general mass is still unaware of how hackers work towards the
fulfilment of their needs. There are various reasons that compel a personnel or group to
hacking. They are as follows:
A hobby: Most of the hackers hack for the foremost reason of self-pleasure. They
tend to get immense satisfaction from hacking into the victim’s system and leave a
note in order to spread awareness about their existence.
To steal and leak information: Some hackers are only interested to steal what is not
theirs. This may be through stealing classified information or digitally stored

6
HACKING: A MAJOR PROBLEM OF THE 21ST CENTURY
monetary amounts. With the increase in awareness for digital banking and payment
gateways, there has been a potential increase in threat from hackers. Some also aim to
break into the systems to come out with top-secret findings and expose them before
the world.
To bring down websites: DDOS attacks are conducted on certain websites with the
aim to cease their functioning.
Idealism or Hactivism: Famous hacker group, ANONYMOUS came to the limelight
as they promoted their presence with public agendas by hacking into targets like
religious groups, government portals and so on (Goode 2015).
Effects of Hacking
From the above discussion, the effects that hacking can leave on an individual or
organization is quite clear. Hackers can deplete organizational resources or steal away with
financial benefits and leave the respective victims with enormous losses. Below is a report
from 2017, where a famous global bank was hacked and the critical identities of their clients
were at a risk.
About a year ago, UniCredit, one of the largest global banks in Italy fell prey of
hacking. It had been reported that hackers had gained access to more than 400 thousand client
accounts. It is still considered to be one of the biggest security breaches in Europe till date. It
was also revealed by the bank that these accounts were previously hacked as well in the
autumn of 2016. The bank consoled its customers stating that none of their banking
information was stolen. However, PII (Personally Identifiable Information) of each individual
was compromised. It meant that the hackers had access to the personal information like
names, addresses and contact details of thousands of people all around the globe. Banks are
considered as popular targets for the cyber-criminals. They can gain the wealth of critical
information about both proprietary and personal aspects of the public (BBC News, 2018).
HACKING: A MAJOR PROBLEM OF THE 21ST CENTURY
monetary amounts. With the increase in awareness for digital banking and payment
gateways, there has been a potential increase in threat from hackers. Some also aim to
break into the systems to come out with top-secret findings and expose them before
the world.
To bring down websites: DDOS attacks are conducted on certain websites with the
aim to cease their functioning.
Idealism or Hactivism: Famous hacker group, ANONYMOUS came to the limelight
as they promoted their presence with public agendas by hacking into targets like
religious groups, government portals and so on (Goode 2015).
Effects of Hacking
From the above discussion, the effects that hacking can leave on an individual or
organization is quite clear. Hackers can deplete organizational resources or steal away with
financial benefits and leave the respective victims with enormous losses. Below is a report
from 2017, where a famous global bank was hacked and the critical identities of their clients
were at a risk.
About a year ago, UniCredit, one of the largest global banks in Italy fell prey of
hacking. It had been reported that hackers had gained access to more than 400 thousand client
accounts. It is still considered to be one of the biggest security breaches in Europe till date. It
was also revealed by the bank that these accounts were previously hacked as well in the
autumn of 2016. The bank consoled its customers stating that none of their banking
information was stolen. However, PII (Personally Identifiable Information) of each individual
was compromised. It meant that the hackers had access to the personal information like
names, addresses and contact details of thousands of people all around the globe. Banks are
considered as popular targets for the cyber-criminals. They can gain the wealth of critical
information about both proprietary and personal aspects of the public (BBC News, 2018).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7
HACKING: A MAJOR PROBLEM OF THE 21ST CENTURY
Preventive measures against hacking
It is extremely necessary for any organization to work in a secured network
environment. The steps that can be adopted to secure a network based computing system
from the threat of hacks or DDoS attacks are as follows:
Hire an experienced group of network professionals to look after the
It is important to choose the right firewall and restrict external access.
The antivirus software products should be updated on a regular basis (Perlroth 2014).
In case a system has already been compromised, the necessary steps to follow are:
Confirm that an attack has actually taken place.
Pull the system offline.
Investigate the scope of the compromise as early as possible.
Communicate with all stakeholders.
Find the loopholes and prepare for future attacks with rigorous testing for more
vulnerabilities (Shinde and Ardhapurkar 2016).
Gantt Chart
A gantt chart for the recovering from a compromised situation is presented below in
Fig.1. It is assumed that the hack was discovered on 16 July.
HACKING: A MAJOR PROBLEM OF THE 21ST CENTURY
Preventive measures against hacking
It is extremely necessary for any organization to work in a secured network
environment. The steps that can be adopted to secure a network based computing system
from the threat of hacks or DDoS attacks are as follows:
Hire an experienced group of network professionals to look after the
It is important to choose the right firewall and restrict external access.
The antivirus software products should be updated on a regular basis (Perlroth 2014).
In case a system has already been compromised, the necessary steps to follow are:
Confirm that an attack has actually taken place.
Pull the system offline.
Investigate the scope of the compromise as early as possible.
Communicate with all stakeholders.
Find the loopholes and prepare for future attacks with rigorous testing for more
vulnerabilities (Shinde and Ardhapurkar 2016).
Gantt Chart
A gantt chart for the recovering from a compromised situation is presented below in
Fig.1. It is assumed that the hack was discovered on 16 July.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
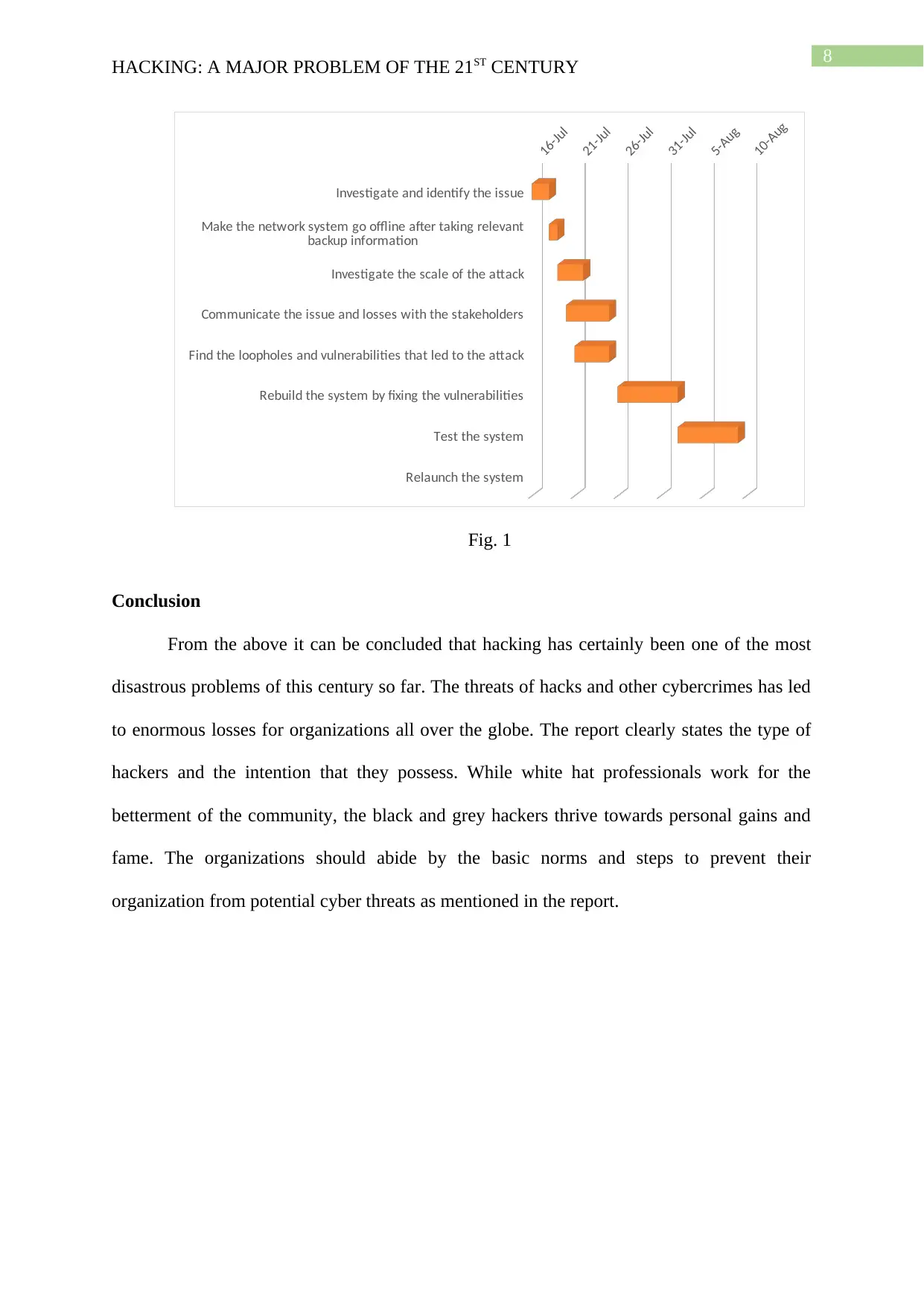
8
HACKING: A MAJOR PROBLEM OF THE 21ST CENTURY
Investigate and identify the issue
Make the network system go offline after taking relevant
backup information
Investigate the scale of the attack
Communicate the issue and losses with the stakeholders
Find the loopholes and vulnerabilities that led to the attack
Rebuild the system by fixing the vulnerabilities
Test the system
Relaunch the system
16-Jul
21-Jul
26-Jul
31-Jul
5-Aug
10-Aug
Fig. 1
Conclusion
From the above it can be concluded that hacking has certainly been one of the most
disastrous problems of this century so far. The threats of hacks and other cybercrimes has led
to enormous losses for organizations all over the globe. The report clearly states the type of
hackers and the intention that they possess. While white hat professionals work for the
betterment of the community, the black and grey hackers thrive towards personal gains and
fame. The organizations should abide by the basic norms and steps to prevent their
organization from potential cyber threats as mentioned in the report.
HACKING: A MAJOR PROBLEM OF THE 21ST CENTURY
Investigate and identify the issue
Make the network system go offline after taking relevant
backup information
Investigate the scale of the attack
Communicate the issue and losses with the stakeholders
Find the loopholes and vulnerabilities that led to the attack
Rebuild the system by fixing the vulnerabilities
Test the system
Relaunch the system
16-Jul
21-Jul
26-Jul
31-Jul
5-Aug
10-Aug
Fig. 1
Conclusion
From the above it can be concluded that hacking has certainly been one of the most
disastrous problems of this century so far. The threats of hacks and other cybercrimes has led
to enormous losses for organizations all over the globe. The report clearly states the type of
hackers and the intention that they possess. While white hat professionals work for the
betterment of the community, the black and grey hackers thrive towards personal gains and
fame. The organizations should abide by the basic norms and steps to prevent their
organization from potential cyber threats as mentioned in the report.

9
HACKING: A MAJOR PROBLEM OF THE 21ST CENTURY
References
Baase, S., 2012. A gift of fire. Pearson Education Limited.
BBC News. (2018). Bank customers hit by major data breach. [online] Available at:
http://www.bbc.com/news/technology-40728447 [Accessed 27 Feb. 2018].
Elmaghraby, A.S. and Losavio, M.M., 2014. Cyber security challenges in Smart Cities:
Safety, security and privacy. Journal of advanced research, 5(4), pp.491-497.
Goode, L., 2015. Anonymous and the political ethos of hacktivism. Popular
Communication, 13(1), pp.74-86.
Perlroth, N., 2014. Hacked vs. hackers: Game on. New York Times Bits Blog. http://bits.
blogs. nytimes. com/2014/12/02/hacked-vs-hackers-game-on.
Sethi, N. and Gera, A., 2014. A revived survey of various credit card fraud detection
techniques. International Journal of Computer Science and Mobile Computing, 3(4), pp.780-
791.
Shinde, P.S. and Ardhapurkar, S.B., 2016, February. Cyber security analysis using
vulnerability assessment and penetration testing. In Futuristic Trends in Research and
Innovation for Social Welfare (Startup Conclave), World Conference on (pp. 1-5). IEEE.
Von Solms, R. and Van Niekerk, J., 2013. From information security to cyber
security. computers & security, 38, pp.97-102.
HACKING: A MAJOR PROBLEM OF THE 21ST CENTURY
References
Baase, S., 2012. A gift of fire. Pearson Education Limited.
BBC News. (2018). Bank customers hit by major data breach. [online] Available at:
http://www.bbc.com/news/technology-40728447 [Accessed 27 Feb. 2018].
Elmaghraby, A.S. and Losavio, M.M., 2014. Cyber security challenges in Smart Cities:
Safety, security and privacy. Journal of advanced research, 5(4), pp.491-497.
Goode, L., 2015. Anonymous and the political ethos of hacktivism. Popular
Communication, 13(1), pp.74-86.
Perlroth, N., 2014. Hacked vs. hackers: Game on. New York Times Bits Blog. http://bits.
blogs. nytimes. com/2014/12/02/hacked-vs-hackers-game-on.
Sethi, N. and Gera, A., 2014. A revived survey of various credit card fraud detection
techniques. International Journal of Computer Science and Mobile Computing, 3(4), pp.780-
791.
Shinde, P.S. and Ardhapurkar, S.B., 2016, February. Cyber security analysis using
vulnerability assessment and penetration testing. In Futuristic Trends in Research and
Innovation for Social Welfare (Startup Conclave), World Conference on (pp. 1-5). IEEE.
Von Solms, R. and Van Niekerk, J., 2013. From information security to cyber
security. computers & security, 38, pp.97-102.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





