Ethics of Hacking: Consequentialism and Deontology Analysis
VerifiedAdded on 2019/10/09
|4
|1187
|124
Essay
AI Summary
This essay delves into the ethical complexities of hacking, examining the incident of a website leak exposing Australian buyers' information. It analyzes the morality of hacking through the frameworks of consequentialism and deontology, exploring whether hacking can ever be justified, and under what circumstances. The essay presents contrasting viewpoints, considering hacking as inherently unethical under deontological principles, which emphasize adherence to rules and duties, while also exploring consequentialist arguments that assess morality based on outcomes. The analysis includes real-world examples such as hacking to uncover marital infidelity or to obtain competitive business information, evaluating the actions through the lens of Immanuel Kant's philosophical perspectives and the potential consequences of such actions. The paper concludes that morality and ethics are subjective, dependent on individual interpretation and the principles applied in the context of each action.

Rent-a-hacker site leaks Australian buyers' names and addresses
The given article highlights the incident of hackers being hired by different people from Sweden
to Australia for a variety of purposes. The purpose of that hiring were legal and illegal as well, at
least on the face of it. However, the actual embarrassment began when it was discovered that the
hacking job description was linked to the personal information of the clients and because of that
their identification was disclosed. The question that arises here is whether the hacking per se is
completely moral and unethical or could it be serving any rightful purpose at the end?
This particular incident, like any other act, could be seen from different perspectives depending
on what one wants to look at it. Let us analyze it from the perspective of the theory of
consequentialism and deontology. It is one’s own discretion what decision is he going to make
irrespective of the rightness or wrongness of it. As per my own opinion, hacking in itself is
morally wrong as it is a deliberate act of destroying something that has been created by someone
or stealing an information that could be extremely crucial for a particular person. In relation to
this Immanuel Kant believed that the moral and ethical values are the guiding posts in daily
decision making. The deontological theory of ethics states that the morality of any action adheres
to the closest degrees of rules or duties (Alexander & Moore, 2007). In other words,
deontological approach is essentially the rule based ethics because the rules bind any person to
his/her duty. In the present scenario, the Australian buyers asked the hackers to find out for them
whether their spouses were cheating on them. They might have taken such a decision out of
frustration because they couldn’t have found any other means to find out about it. However, such
an action on their part, according to me, was ethically wrong because this act of taking a hacker’s
help in itself is a cheating as it is immoral to try to get illegal access to someone else’s account.
As we know, according to Kant, the wrongness or rightness depends upon the commitment
The given article highlights the incident of hackers being hired by different people from Sweden
to Australia for a variety of purposes. The purpose of that hiring were legal and illegal as well, at
least on the face of it. However, the actual embarrassment began when it was discovered that the
hacking job description was linked to the personal information of the clients and because of that
their identification was disclosed. The question that arises here is whether the hacking per se is
completely moral and unethical or could it be serving any rightful purpose at the end?
This particular incident, like any other act, could be seen from different perspectives depending
on what one wants to look at it. Let us analyze it from the perspective of the theory of
consequentialism and deontology. It is one’s own discretion what decision is he going to make
irrespective of the rightness or wrongness of it. As per my own opinion, hacking in itself is
morally wrong as it is a deliberate act of destroying something that has been created by someone
or stealing an information that could be extremely crucial for a particular person. In relation to
this Immanuel Kant believed that the moral and ethical values are the guiding posts in daily
decision making. The deontological theory of ethics states that the morality of any action adheres
to the closest degrees of rules or duties (Alexander & Moore, 2007). In other words,
deontological approach is essentially the rule based ethics because the rules bind any person to
his/her duty. In the present scenario, the Australian buyers asked the hackers to find out for them
whether their spouses were cheating on them. They might have taken such a decision out of
frustration because they couldn’t have found any other means to find out about it. However, such
an action on their part, according to me, was ethically wrong because this act of taking a hacker’s
help in itself is a cheating as it is immoral to try to get illegal access to someone else’s account.
As we know, according to Kant, the wrongness or rightness depends upon the commitment
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

towards duty not on the consequences of the actions. Kant further goes on to suggest that if a
person decides something and performs the action based on that decision, then it is also very
crucial to understand that would they like the other person to act in a likewise manner. Whether
something good results out of that action would still not justify the deviation from the path of
morality if it wasn’t done as per the rules and duties. So, in the ambit of deontological morality,
such a person would always like to abstain from taking such actions.
If a person wants to know the inside information business strategies and customer database of his
rival and employs a hacker to do this job for him, then again he is not going according to the
universal laws of morality because it is not done following the rules and duty (Spafford, 1992).
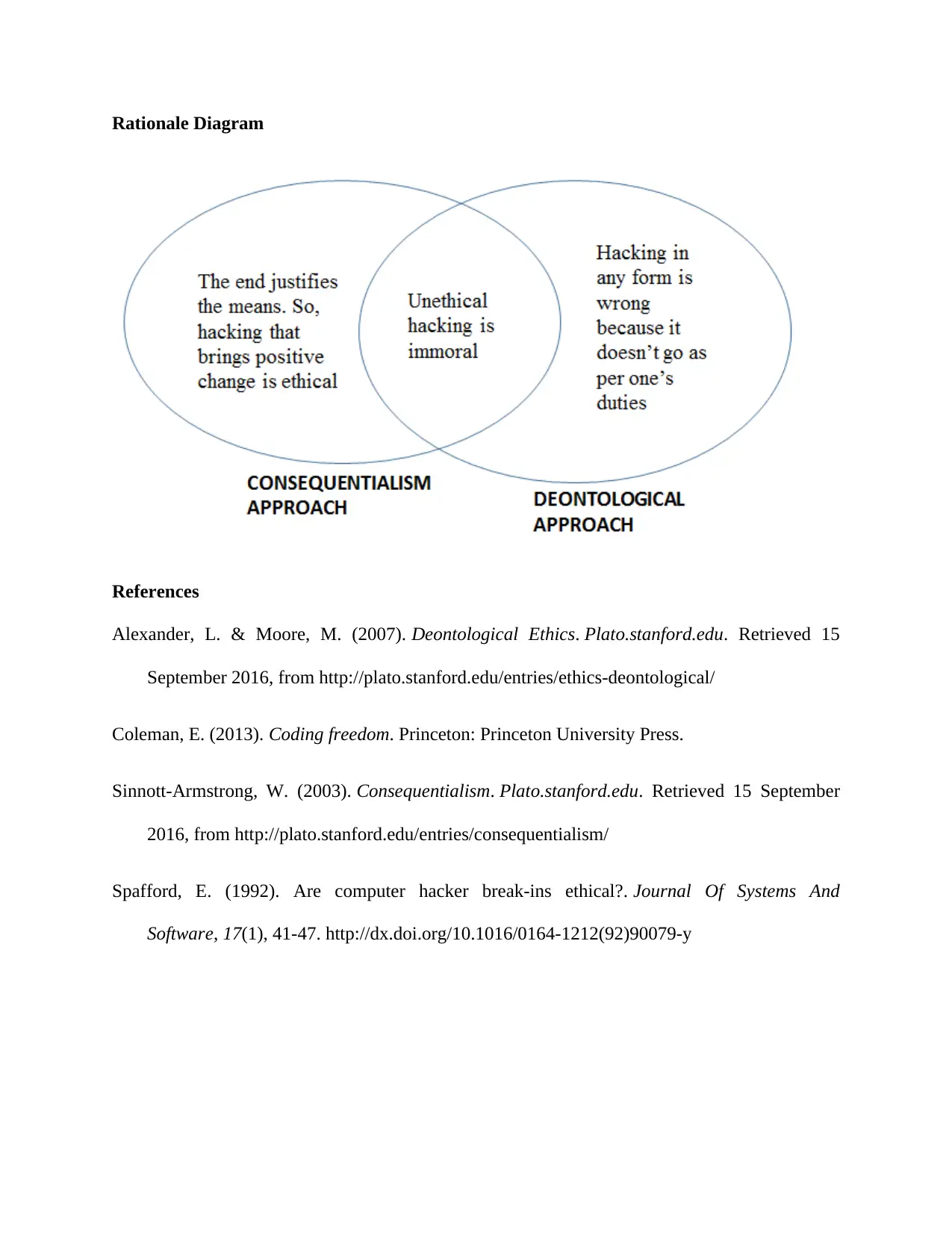
So, the moot point that is to be made over here is that any form of hacking whether it is done in
order to bring out some relevant or important information, is still be considered an immoral and
unethical act. It may bring about some positive results to a particular person or anything
substantial for the society at large, but the fact that it has not been done by following the
requisite principles of duty and rules, it will always be considered as an immoral act.
The other theory with which the above hacking incident could be understood in a different
perspective is the Consequentialist theory of morality. The theory states that any action is ethical
or moral is based on the consequences of that action as every action has consequences. It is the
consequence that makes a clear distinction about the rightness or wrongness of an action. In plain
and simple words we can say that the end justifies the means (Sinnott-Armstrong, 2003). Now, in
relation to the hacking incident, there is a clear dichotomy that emerges at this point. As per
consequentialism, hacking is something irrespective of whether it is guided by the moral
principles or not, it will be considered wrong whenever it is intended to hurt someone because by
the very act of hacking, there could be grave consequences for a person’s life or for the system as
person decides something and performs the action based on that decision, then it is also very
crucial to understand that would they like the other person to act in a likewise manner. Whether
something good results out of that action would still not justify the deviation from the path of
morality if it wasn’t done as per the rules and duties. So, in the ambit of deontological morality,
such a person would always like to abstain from taking such actions.
If a person wants to know the inside information business strategies and customer database of his
rival and employs a hacker to do this job for him, then again he is not going according to the
universal laws of morality because it is not done following the rules and duty (Spafford, 1992).
So, the moot point that is to be made over here is that any form of hacking whether it is done in
order to bring out some relevant or important information, is still be considered an immoral and
unethical act. It may bring about some positive results to a particular person or anything
substantial for the society at large, but the fact that it has not been done by following the
requisite principles of duty and rules, it will always be considered as an immoral act.
The other theory with which the above hacking incident could be understood in a different
perspective is the Consequentialist theory of morality. The theory states that any action is ethical
or moral is based on the consequences of that action as every action has consequences. It is the
consequence that makes a clear distinction about the rightness or wrongness of an action. In plain
and simple words we can say that the end justifies the means (Sinnott-Armstrong, 2003). Now, in
relation to the hacking incident, there is a clear dichotomy that emerges at this point. As per
consequentialism, hacking is something irrespective of whether it is guided by the moral
principles or not, it will be considered wrong whenever it is intended to hurt someone because by
the very act of hacking, there could be grave consequences for a person’s life or for the system as

a whole. However, the picture changes completely when the hacking is done to bring out positive
results so that people get benefit from that. So, in this case, even if it is seemingly an immoral act
but the consequences are coming out to be positive. Then, it will become a moral and ethical act
in the end. Likewise in the present hacking scenario, the Australian woman must have been fed
up of her husband’s behavior and could not have figured out any other way as to what was going
on and she decided to take hackers’ help. So, as per the theory of consequentialism, she would
have known the reality and must have benefited by it, that is, the consequences for her were
positive by the very act of hacking. Therefore, in this case it is morally right thing to do. Also, if
hacking has been carried out to know about the impending threats for one’s country and how to
make preparations to defend it, then clearly its consequences will always be positive and we can
safely conclude that the particular act was morally right (Coleman, 2013).
Hence, it boils down the basic approach as to how one sees any action being performed around
him/her. Morality and ethics are bound to one’s own discretion. How an individual interprets a
particular action is always guided by the principles that he thinks are applicable at that instant.
results so that people get benefit from that. So, in this case, even if it is seemingly an immoral act
but the consequences are coming out to be positive. Then, it will become a moral and ethical act
in the end. Likewise in the present hacking scenario, the Australian woman must have been fed
up of her husband’s behavior and could not have figured out any other way as to what was going
on and she decided to take hackers’ help. So, as per the theory of consequentialism, she would
have known the reality and must have benefited by it, that is, the consequences for her were
positive by the very act of hacking. Therefore, in this case it is morally right thing to do. Also, if
hacking has been carried out to know about the impending threats for one’s country and how to
make preparations to defend it, then clearly its consequences will always be positive and we can
safely conclude that the particular act was morally right (Coleman, 2013).
Hence, it boils down the basic approach as to how one sees any action being performed around
him/her. Morality and ethics are bound to one’s own discretion. How an individual interprets a
particular action is always guided by the principles that he thinks are applicable at that instant.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Rationale Diagram
References
Alexander, L. & Moore, M. (2007). Deontological Ethics. Plato.stanford.edu. Retrieved 15
September 2016, from http://plato.stanford.edu/entries/ethics-deontological/
Coleman, E. (2013). Coding freedom. Princeton: Princeton University Press.
Sinnott-Armstrong, W. (2003). Consequentialism. Plato.stanford.edu. Retrieved 15 September
2016, from http://plato.stanford.edu/entries/consequentialism/
Spafford, E. (1992). Are computer hacker break-ins ethical?. Journal Of Systems And
Software, 17(1), 41-47. http://dx.doi.org/10.1016/0164-1212(92)90079-y
References
Alexander, L. & Moore, M. (2007). Deontological Ethics. Plato.stanford.edu. Retrieved 15
September 2016, from http://plato.stanford.edu/entries/ethics-deontological/
Coleman, E. (2013). Coding freedom. Princeton: Princeton University Press.
Sinnott-Armstrong, W. (2003). Consequentialism. Plato.stanford.edu. Retrieved 15 September
2016, from http://plato.stanford.edu/entries/consequentialism/
Spafford, E. (1992). Are computer hacker break-ins ethical?. Journal Of Systems And
Software, 17(1), 41-47. http://dx.doi.org/10.1016/0164-1212(92)90079-y
1 out of 4
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





