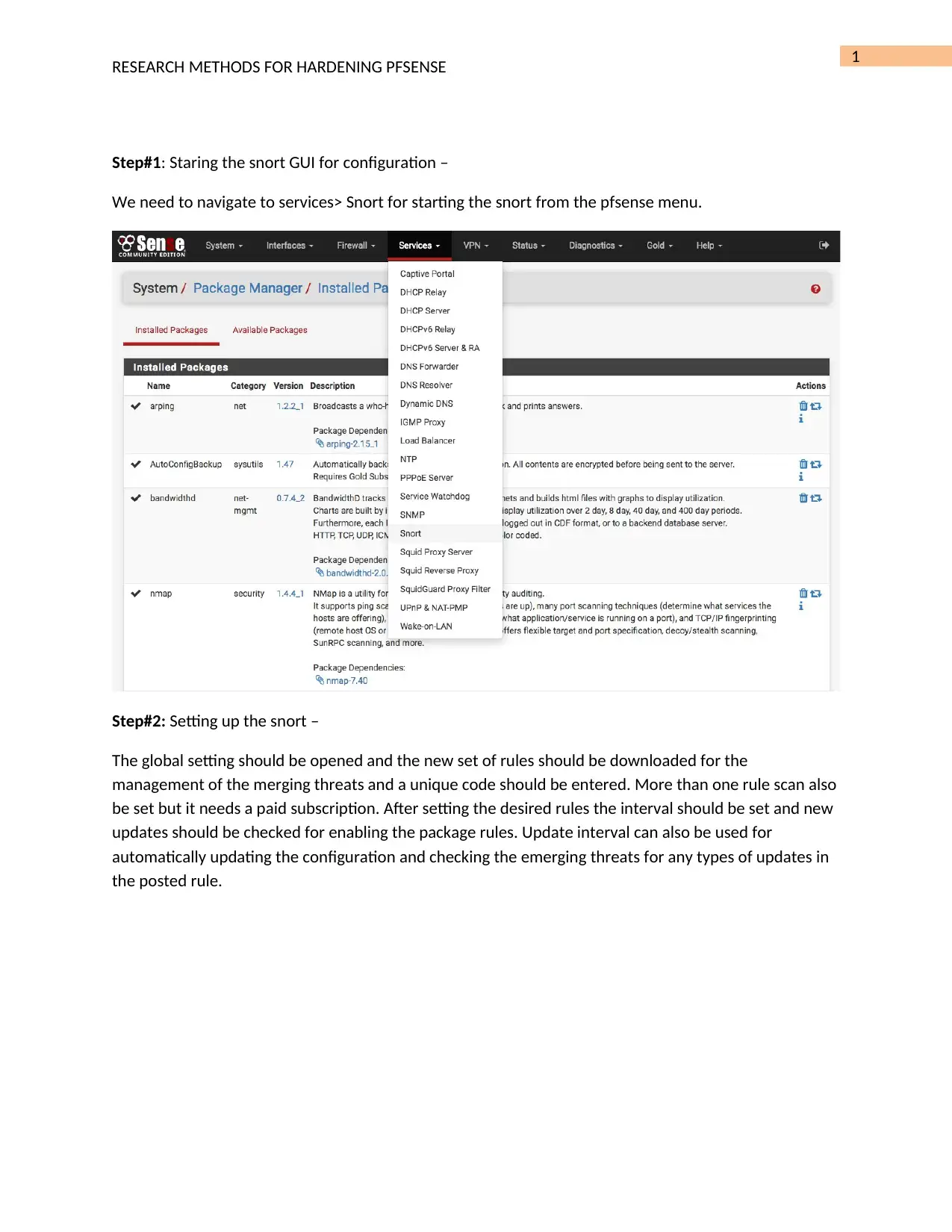
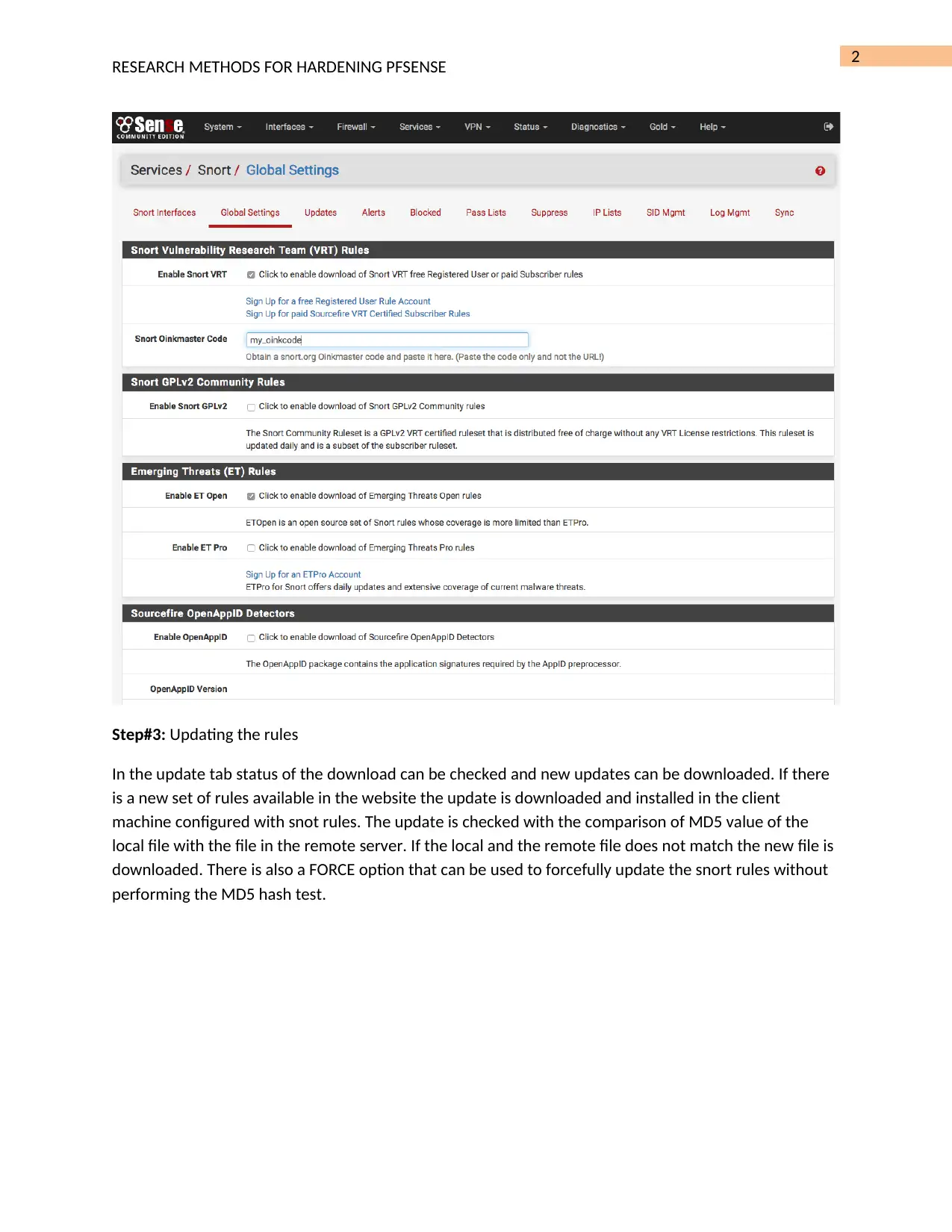
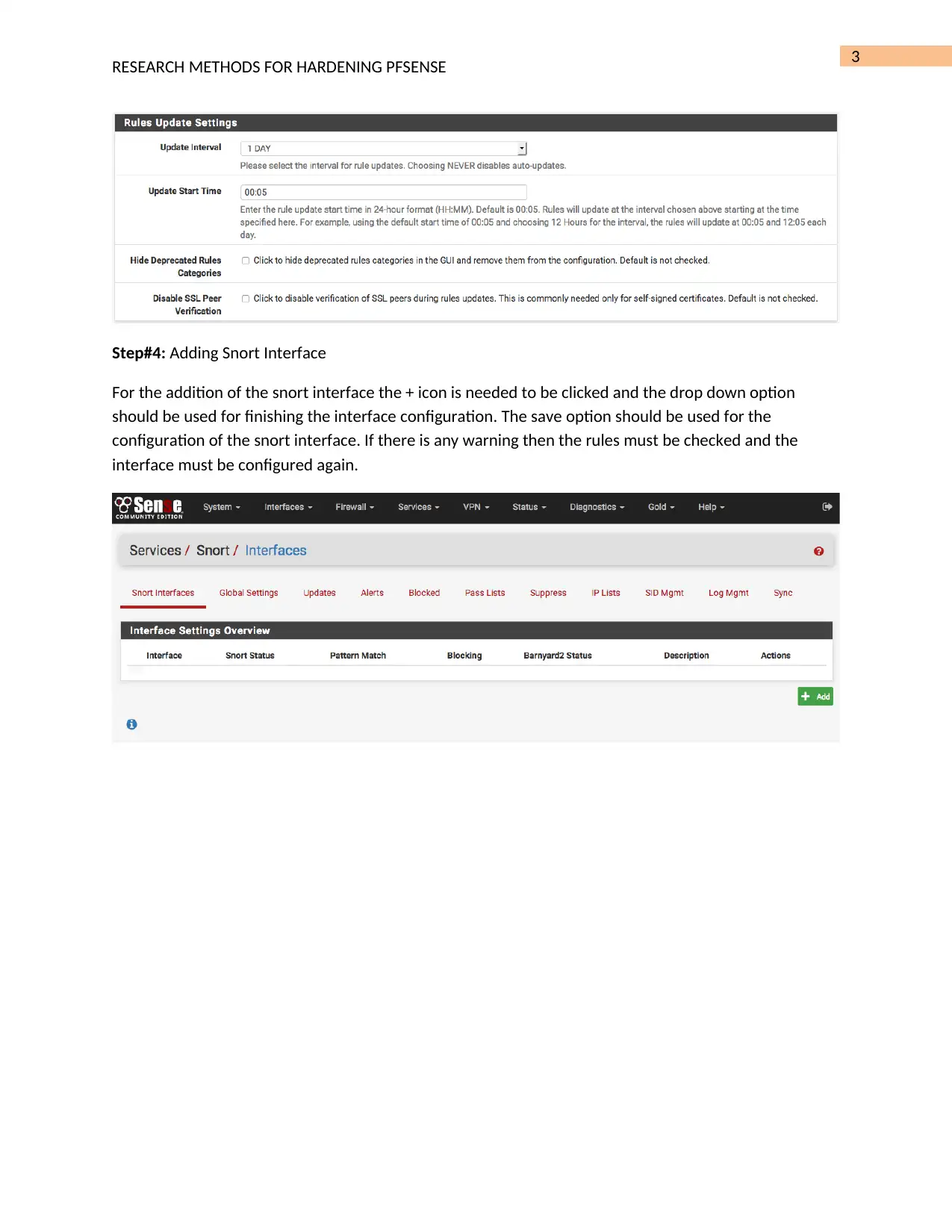
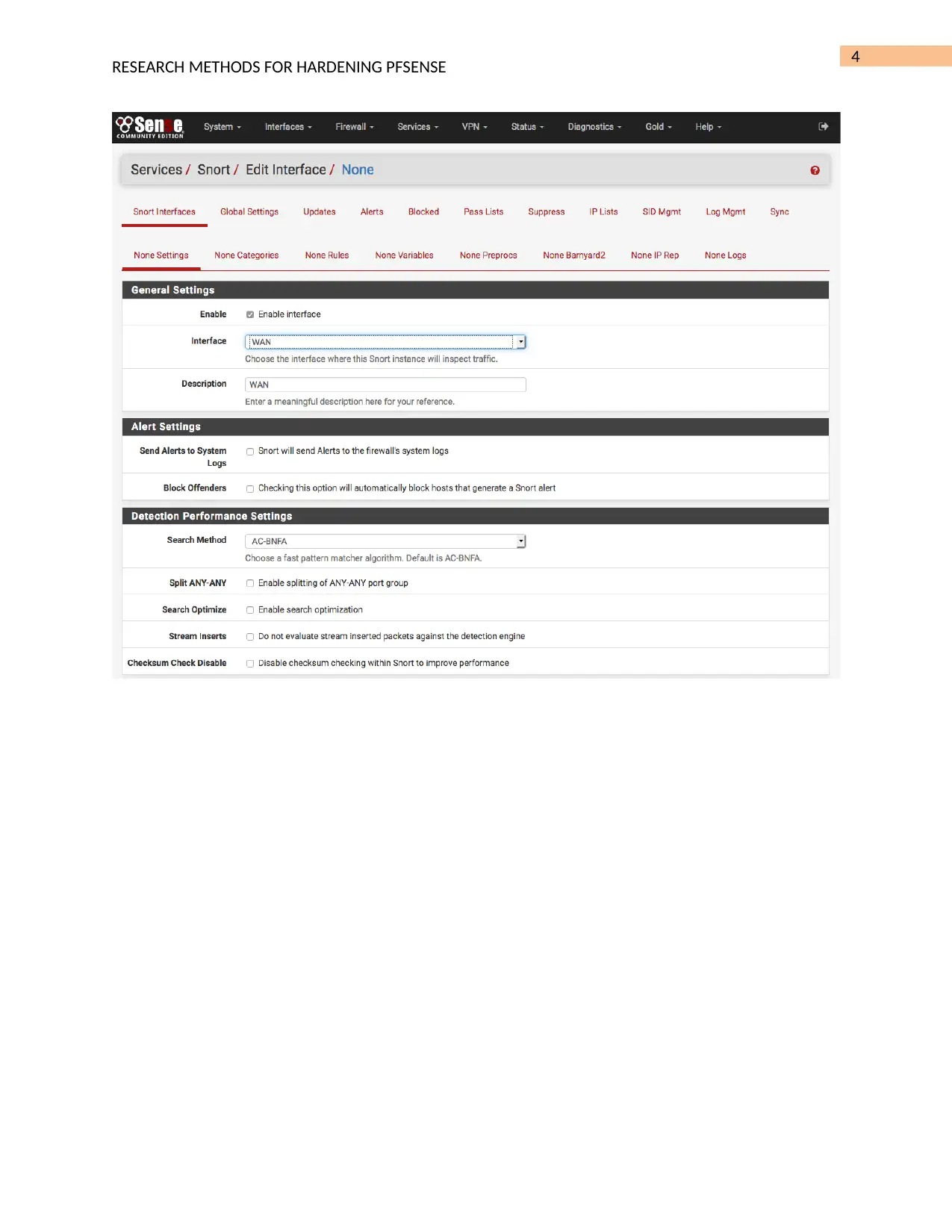
Hardening PFSense System: Detecting Port Scans with Snort
VerifiedAdded on 2023/06/03
|8
|522
|177
Practical Assignment
AI Summary
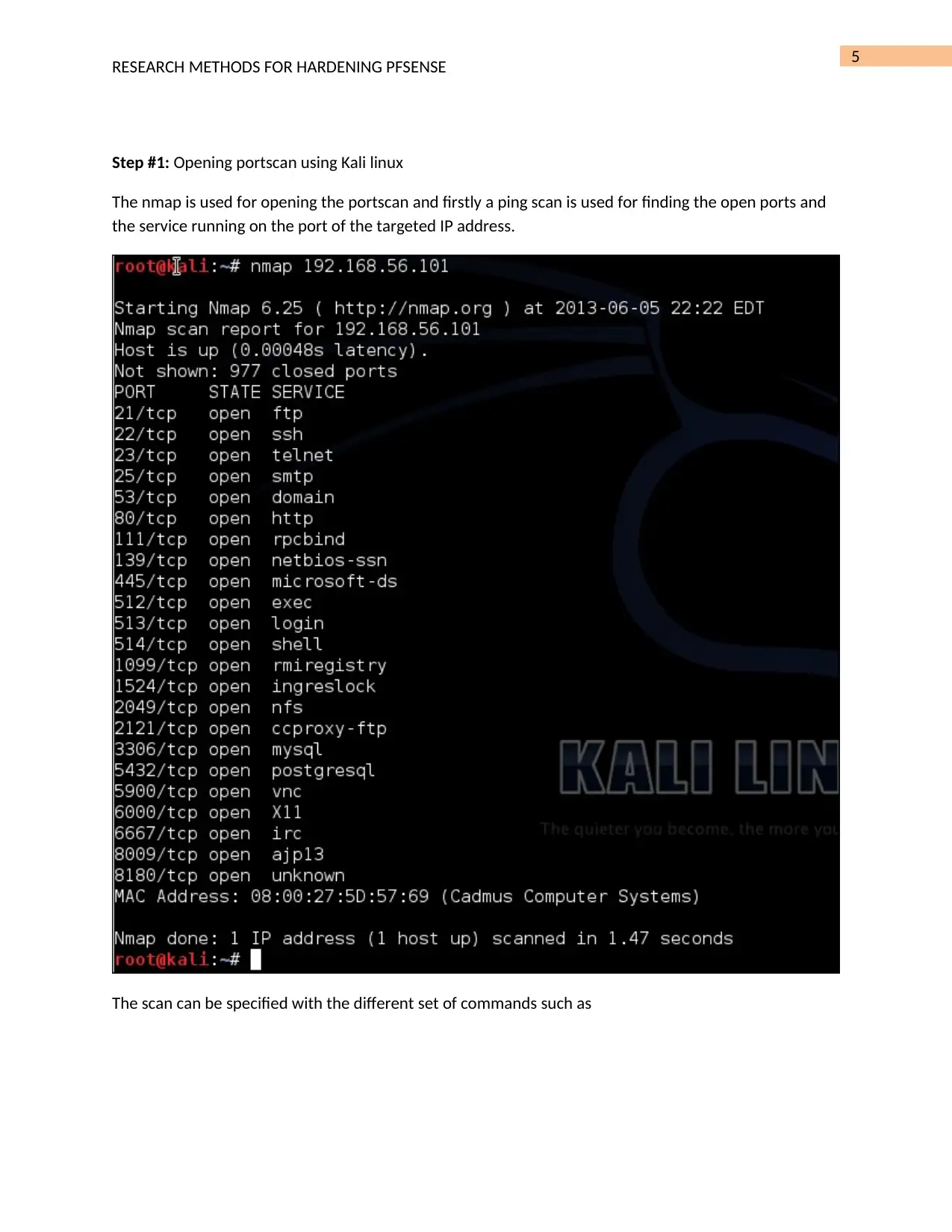
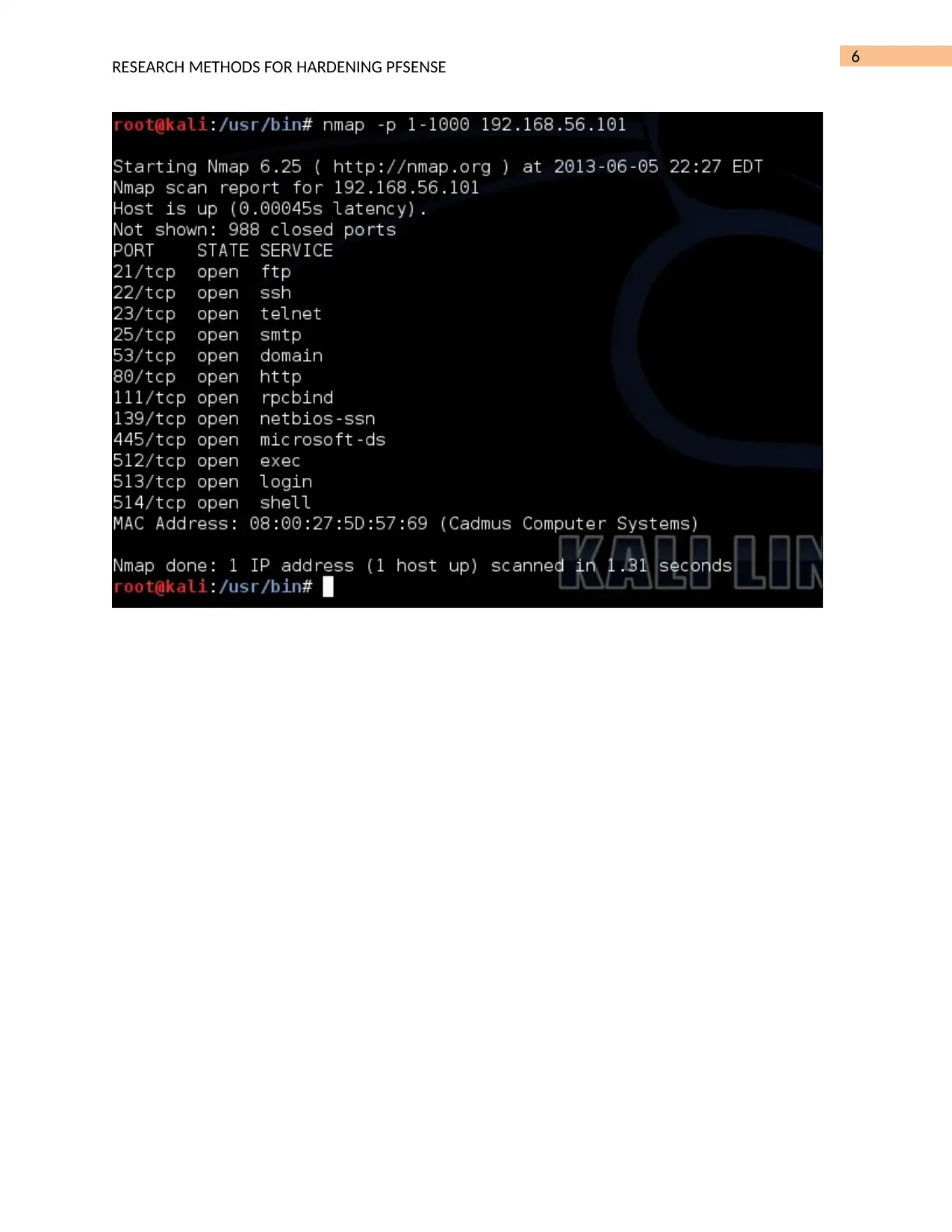
This assignment provides a comprehensive guide to hardening a PFSense system using Snort, an intrusion detection system. The student starts by configuring Snort within the PFSense interface, including starting the service, downloading and updating the latest community rules. The guide details the steps for setting up Snort, configuring global settings, updating rules, and adding a Snort interface. To test the configuration, the student uses Kali Linux to perform a port scan, demonstrating how Snort detects such activities. The assignment includes screenshots to illustrate each step, along with a detailed explanation of hardening, Snort's functionality, and the rationale behind using Snort in this scenario. The document also briefly mentions other methods for hardening PFSense. The assignment concludes with a bibliography of relevant sources.
1 out of 8





![[object Object]](/_next/static/media/star-bottom.7253800d.svg)