Detailed Report on Hardware, Software, and Network System Analysis
VerifiedAdded on 2022/11/10
|7
|1038
|479
Report
AI Summary
This report provides an overview of information systems used in business, focusing on hardware, software, and network requirements. It examines different types of information systems, including Executive Support Systems, Management Information Systems, Decision Support Systems, Knowledge Management Systems, Transaction Processing Systems, and Office Automation Systems. The report explores the relationship between business processes and information systems, illustrating this with a flowchart example. It also addresses information system usage and security concerns, as well as the ethical handling of customer's private information. The conclusion summarizes the key aspects of information systems and their components. The report includes references to relevant academic sources.

Running head: HARDWARE, SOFTWARE AND NETWORK REQUIREMENT
HARDWARE, SOFTWARE AND NETWORK REQUIREMENT
Name of the Student:
Name of the University:
Author Note:
HARDWARE, SOFTWARE AND NETWORK REQUIREMENT
Name of the Student:
Name of the University:
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1HARDWARE, SOFTWARE AND NETWORK REQUIREMENT
Table of Contents
1. Introduction:.............................................................................................................................2
2. Overview of the top information system:.................................................................................2
3. Relationship between business process and information systems:..........................................3
4. Flowchart of Microsoft® Visio®:............................................................................................3
5. Flowchart for handling an online registration:.......................................................................4
.........................................................................................................................................................4
6. Information systems usage and security concerns:..................................................................5
7. Ethical handling of customer’s private information:................................................................5
8. Conclusion:...............................................................................................................................5
9. References:...............................................................................................................................6
Table of Contents
1. Introduction:.............................................................................................................................2
2. Overview of the top information system:.................................................................................2
3. Relationship between business process and information systems:..........................................3
4. Flowchart of Microsoft® Visio®:............................................................................................3
5. Flowchart for handling an online registration:.......................................................................4
.........................................................................................................................................................4
6. Information systems usage and security concerns:..................................................................5
7. Ethical handling of customer’s private information:................................................................5
8. Conclusion:...............................................................................................................................5
9. References:...............................................................................................................................6

2HARDWARE, SOFTWARE AND NETWORK REQUIREMENT
1. Introduction:
This research proposal is aimed to provide an outline of a top information system which
is used in business today and how they relate to Karen’s business needs. This proposal
offered brief framework of the relationship between business processes and information
systems along with implementing research aim and objectives. Moreover, this study also
provided brief regarding the ethical handling of customers’ private information.
2. Overview of the top information system:
Executive Support Systems was formed to support senior management in the business
and build strategic decisions. ESS evaluates the summary of the internal and external
information used in today’s business. Management Information Systems designed for the
internal information which means collect data from the transaction processing systems and
outline it into management reports (Cassidy, 2016). Decision Support System is support users
when a decision-making condition rises. Knowledge Management Systems formed to help
businesses designed and share different information, such as knowledge and facilities
(Ifinedo, 2014). Transaction Processing Systems are formed to develop repetitive
transactions accurately. Office Automation Systems are designed to increase the work
effectiveness of employees who want to build data and information (Dwivedi et al., 2015).
Small businesses are worried about keeping their consumer by giving them high quality
goods and services. Business owners are suffered the challenges like considerable challenge
of turning large amount of data into actionable information. Owner of the business carefully
handled some aspects such as list of customers, Sales information, Finance, inventory.
1. Introduction:
This research proposal is aimed to provide an outline of a top information system which
is used in business today and how they relate to Karen’s business needs. This proposal
offered brief framework of the relationship between business processes and information
systems along with implementing research aim and objectives. Moreover, this study also
provided brief regarding the ethical handling of customers’ private information.
2. Overview of the top information system:
Executive Support Systems was formed to support senior management in the business
and build strategic decisions. ESS evaluates the summary of the internal and external
information used in today’s business. Management Information Systems designed for the
internal information which means collect data from the transaction processing systems and
outline it into management reports (Cassidy, 2016). Decision Support System is support users
when a decision-making condition rises. Knowledge Management Systems formed to help
businesses designed and share different information, such as knowledge and facilities
(Ifinedo, 2014). Transaction Processing Systems are formed to develop repetitive
transactions accurately. Office Automation Systems are designed to increase the work
effectiveness of employees who want to build data and information (Dwivedi et al., 2015).
Small businesses are worried about keeping their consumer by giving them high quality
goods and services. Business owners are suffered the challenges like considerable challenge
of turning large amount of data into actionable information. Owner of the business carefully
handled some aspects such as list of customers, Sales information, Finance, inventory.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3HARDWARE, SOFTWARE AND NETWORK REQUIREMENT
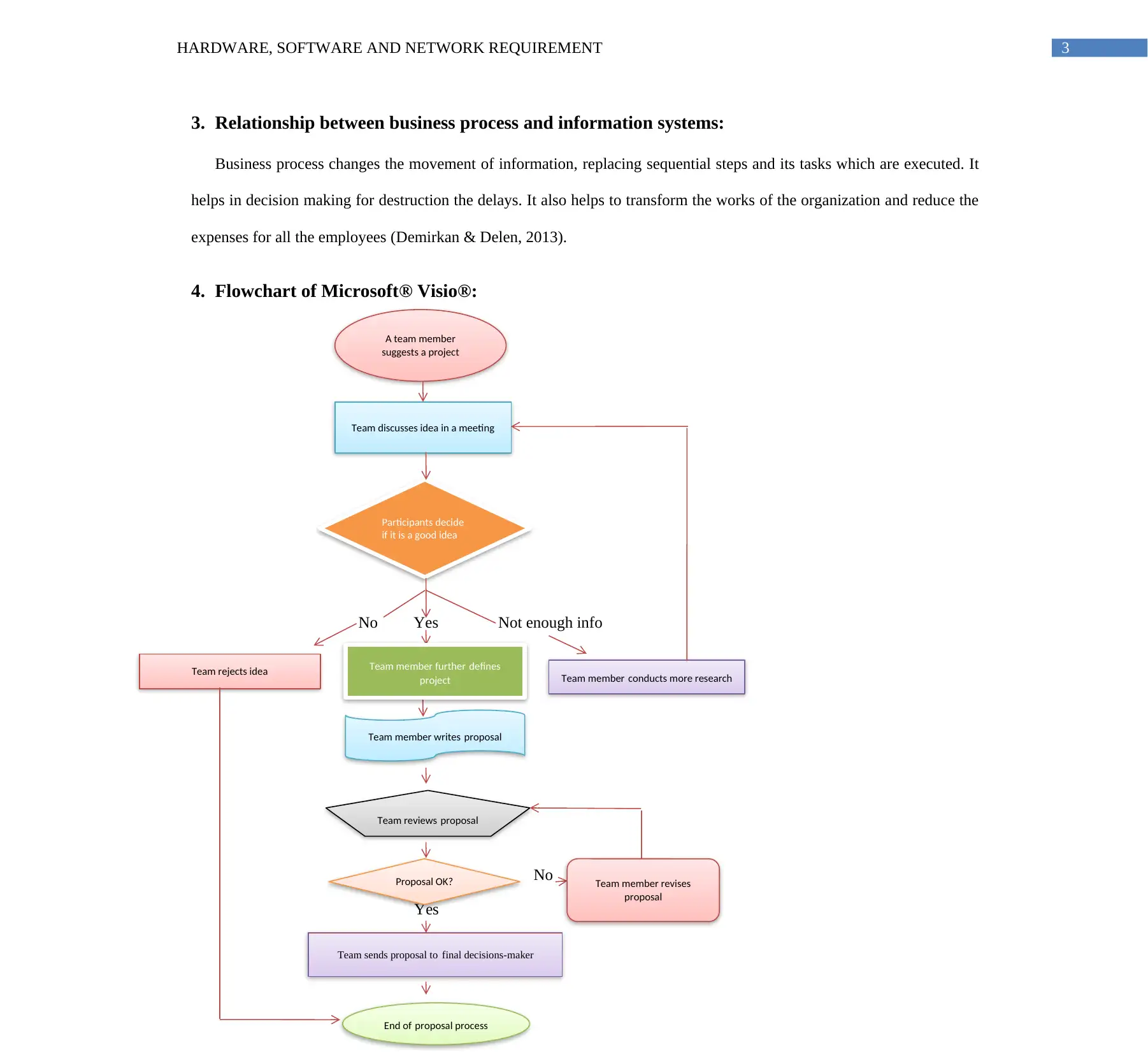
3. Relationship between business process and information systems:
Business process changes the movement of information, replacing sequential steps and its tasks which are executed. It
helps in decision making for destruction the delays. It also helps to transform the works of the organization and reduce the
expenses for all the employees (Demirkan & Delen, 2013).
4. Flowchart of Microsoft® Visio®:
No Yes Not enough info
No
Yes
Team sends proposal to final decisions-maker
A team member
suggests a project
Team discusses idea in a meeting
Participants decide
if it is a good idea
Team rejects idea Team member further defines
project Team member conducts more research
Team member writes proposal
Team reviews proposal
Proposal OK?
End of proposal process
Team member revises
proposal
3. Relationship between business process and information systems:
Business process changes the movement of information, replacing sequential steps and its tasks which are executed. It
helps in decision making for destruction the delays. It also helps to transform the works of the organization and reduce the
expenses for all the employees (Demirkan & Delen, 2013).
4. Flowchart of Microsoft® Visio®:
No Yes Not enough info
No
Yes
Team sends proposal to final decisions-maker
A team member
suggests a project
Team discusses idea in a meeting
Participants decide
if it is a good idea
Team rejects idea Team member further defines
project Team member conducts more research
Team member writes proposal
Team reviews proposal
Proposal OK?
End of proposal process
Team member revises
proposal
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4HARDWARE, SOFTWARE AND NETWORK REQUIREMENT
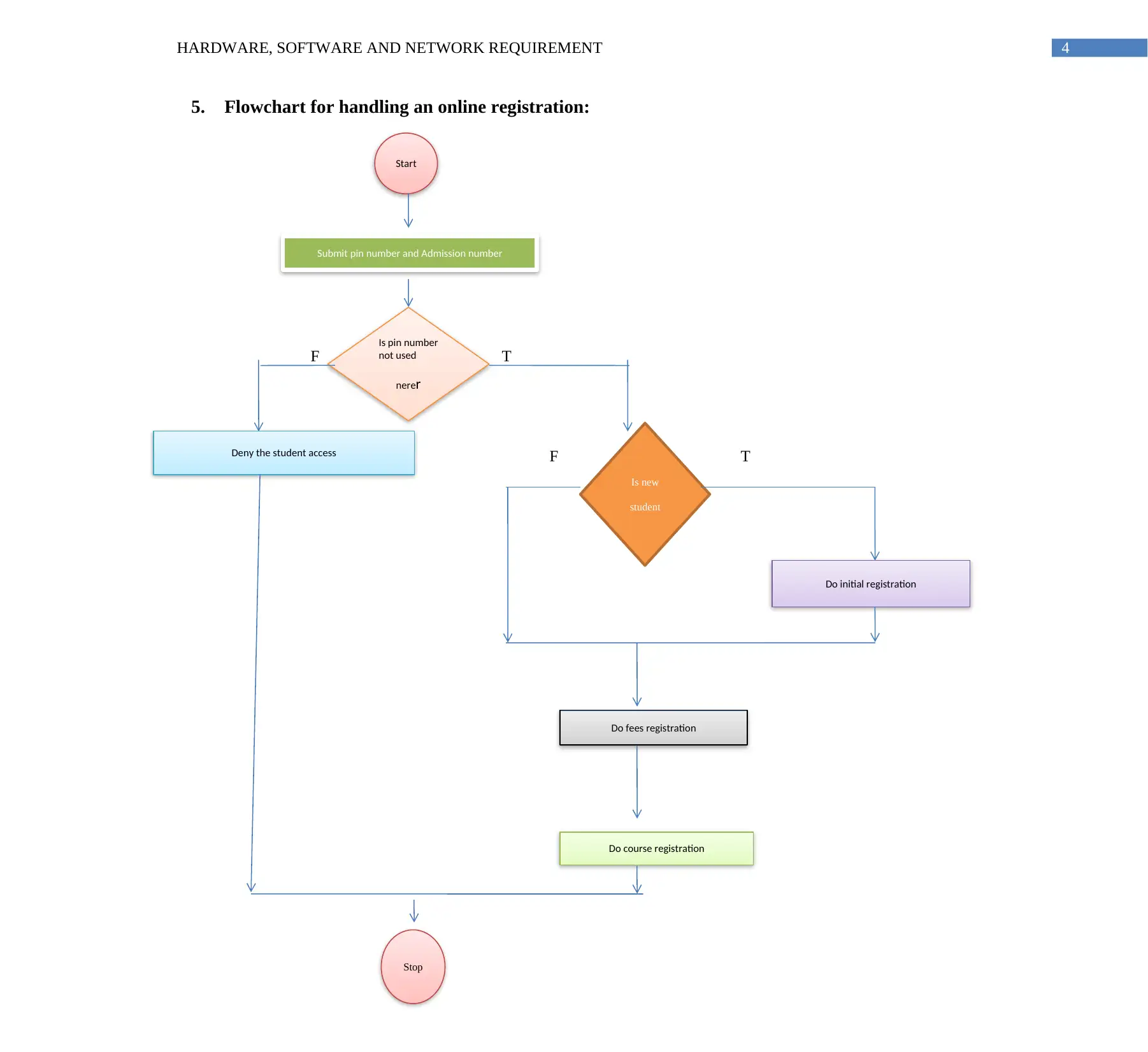
5. Flowchart for handling an online registration:
F T
F T
Is new
student
Start
Submit pin number and Admission number
Is pin number
not used
nerer
Deny the student access
Do initial registration
Do fees registration
Do course registration
Stop
5. Flowchart for handling an online registration:
F T
F T
Is new
student
Start
Submit pin number and Admission number
Is pin number
not used
nerer
Deny the student access
Do initial registration
Do fees registration
Do course registration
Stop

5HARDWARE, SOFTWARE AND NETWORK REQUIREMENT
6. Information systems usage and security concerns:
Information system uses in computer systems design, finance, government sector, larger
corporations and other businesses. It controls unauthorized personnel prevention from the
accessing system and also detects and remediate security gap (Von Solms & Van Niekerk, 2013).
7. Ethical handling of customer’s private information:
Ethical processing of customers’ private information is used in identity theft, information-
intensive environment, information warfare, contemporary corporations, phishing scams,
extortion and cyber terrorism (Slade & Prinsloo, 2013).
8. Conclusion:
It concluded that information systems are a theoretical study of information and the
complementary networks of hardware and software that every individual and organizations use
to assemble, filter, process, develop and distributional data. An insistence is taken place in the
information system for definite boundary, processors, users, storage, preceding communication
networks and inputs-output.
6. Information systems usage and security concerns:
Information system uses in computer systems design, finance, government sector, larger
corporations and other businesses. It controls unauthorized personnel prevention from the
accessing system and also detects and remediate security gap (Von Solms & Van Niekerk, 2013).
7. Ethical handling of customer’s private information:
Ethical processing of customers’ private information is used in identity theft, information-
intensive environment, information warfare, contemporary corporations, phishing scams,
extortion and cyber terrorism (Slade & Prinsloo, 2013).
8. Conclusion:
It concluded that information systems are a theoretical study of information and the
complementary networks of hardware and software that every individual and organizations use
to assemble, filter, process, develop and distributional data. An insistence is taken place in the
information system for definite boundary, processors, users, storage, preceding communication
networks and inputs-output.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6HARDWARE, SOFTWARE AND NETWORK REQUIREMENT
9. References:
Cassidy, A. (2016). A practical guide to information systems strategic planning. Auerbach
Publications.
Demirkan, H., & Delen, D. (2013). Leveraging the capabilities of service-oriented decision
support systems: Putting analytics and big data in cloud. Decision Support
Systems, 55(1), 412-421.
Dwivedi, Y. K., Wastell, D., Laumer, S., Henriksen, H. Z., Myers, M. D., Bunker, D., ... &
Srivastava, S. C. (2015). Research on information systems failures and successes: Status
update and future directions. Information Systems Frontiers, 17(1), 143-157.
Ifinedo, P. (2014). Information systems security policy compliance: An empirical study of the
effects of socialisation, influence, and cognition. Information & Management, 51(1), 69-
79.
Slade, S., & Prinsloo, P. (2013). Learning analytics: Ethical issues and dilemmas. American
Behavioral Scientist, 57(10), 1510-1529.
Von Solms, R., & Van Niekerk, J. (2013). From information security to cyber
security. computers & security, 38, 97-102.
9. References:
Cassidy, A. (2016). A practical guide to information systems strategic planning. Auerbach
Publications.
Demirkan, H., & Delen, D. (2013). Leveraging the capabilities of service-oriented decision
support systems: Putting analytics and big data in cloud. Decision Support
Systems, 55(1), 412-421.
Dwivedi, Y. K., Wastell, D., Laumer, S., Henriksen, H. Z., Myers, M. D., Bunker, D., ... &
Srivastava, S. C. (2015). Research on information systems failures and successes: Status
update and future directions. Information Systems Frontiers, 17(1), 143-157.
Ifinedo, P. (2014). Information systems security policy compliance: An empirical study of the
effects of socialisation, influence, and cognition. Information & Management, 51(1), 69-
79.
Slade, S., & Prinsloo, P. (2013). Learning analytics: Ethical issues and dilemmas. American
Behavioral Scientist, 57(10), 1510-1529.
Von Solms, R., & Van Niekerk, J. (2013). From information security to cyber
security. computers & security, 38, 97-102.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



