University Name: System Analysis of Headspace Cloud Application Report
VerifiedAdded on 2020/03/23
|10
|2671
|376
Report
AI Summary
This report presents a detailed system analysis of Headspace's cloud application, focusing on its functional and non-functional requirements. It utilizes the FURPS+ model to evaluate system aspects such as functionality, usability, reliability, performance, and supportability, including specific constraints. The report differentiates between functional and non-functional requirements, providing examples within a cloud system context. It reviews cloud-based storage, highlighting advantages like usability, accessibility, and cost savings, while also addressing disadvantages such as data security concerns. The report also discusses Software Development Life Cycle (SDLC) approaches, comparing predictive and adaptive models, and recommending the adaptive model for Headspace due to its suitability for larger projects and its potential to mitigate data breach risks. The report concludes with a comprehensive list of references used in the analysis.

Running head: SYSTEM ANALYSIS OF HEADSPACE
System Analysis of Headspace
Name of Student-
Name of University-
Author Note-
System Analysis of Headspace
Name of Student-
Name of University-
Author Note-
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SYSTEM ANALYSIS OF HEADSPACE
Non-Functional Requirement
The non-functional requirement that Headspace can use in its cloud application system is
FURPS+. The acronym of FURPS+ is functionality, usage, reliability, the system performance
and the supportability. The + is to specify the constraints of the non functional requirements of
cloud system of Headspace. The technique of FURPS+ is to make validation to all the
requirements that are prioritized and also understands the necessities and needs of the client (Al-
Rawashdeh, Al’azzeh & Al-Qatawneh, 2014). The non functional requirements helps to
understand the different types of classification that are related to stress which is solved by the
FURPS+ technique. The explanation of the FURPS+ technique is as follows:
Functionality: The acronym of F in FURPS+ is Functionality. F defines the main feature
of the product which is similar with the cloud solution that is to be developed in Headspace. The
requirements of the functionality of FURPS+ are very much technical oriented (Awan, Malik &
Javed, 2015). The functional requirements that are mainly required include the functional
requirement of licensing, mail, printing, security, workflow, system management, localization,
printing and also auditing.
Usability: U in FURPS+ is the acronym of Usability. This usability includes all the issues
of user interface such as capturing, stating and looking at that are required. Usability ensures the
technique of using the non functional requirements of cloud system properly in Headspace.
Reliability: The aspect which includes accuracy, recoverability and availability are
included in reliability. The reliability on recovery and computations are the factors of reliability
that prevents the system from being shut down.
Non-Functional Requirement
The non-functional requirement that Headspace can use in its cloud application system is
FURPS+. The acronym of FURPS+ is functionality, usage, reliability, the system performance
and the supportability. The + is to specify the constraints of the non functional requirements of
cloud system of Headspace. The technique of FURPS+ is to make validation to all the
requirements that are prioritized and also understands the necessities and needs of the client (Al-
Rawashdeh, Al’azzeh & Al-Qatawneh, 2014). The non functional requirements helps to
understand the different types of classification that are related to stress which is solved by the
FURPS+ technique. The explanation of the FURPS+ technique is as follows:
Functionality: The acronym of F in FURPS+ is Functionality. F defines the main feature
of the product which is similar with the cloud solution that is to be developed in Headspace. The
requirements of the functionality of FURPS+ are very much technical oriented (Awan, Malik &
Javed, 2015). The functional requirements that are mainly required include the functional
requirement of licensing, mail, printing, security, workflow, system management, localization,
printing and also auditing.
Usability: U in FURPS+ is the acronym of Usability. This usability includes all the issues
of user interface such as capturing, stating and looking at that are required. Usability ensures the
technique of using the non functional requirements of cloud system properly in Headspace.
Reliability: The aspect which includes accuracy, recoverability and availability are
included in reliability. The reliability on recovery and computations are the factors of reliability
that prevents the system from being shut down.

2SYSTEM ANALYSIS OF HEADSPACE
Performance: The performance is the acronym of P in FURPS+ (Punia & Kaur, 2014).
The feature that are included in performance are the information throughput in the clod system,
time take by the cloud system to response and the start up time of the system and also the
recovery time that the cloud system needs.
Supportability: The supportability is the S in the FURPS+. The supportability includes
other requirements that are needed in the cloud system which includes adaptability,
configurability, localizability, scalability, testability, installability and also maintainability.
The FURPS+ has a + sign which indicates some of the specific constraints which
includes interface, physical constraints, design and implementation constraints.
Interface Constraints- The constraint of interference is the requirement that is required to
interact with the entire external item (Ameller et al., 2013). When the interface of Headspace is
developed, it is difficult to interact with all the external systems.
Physical Constraints- The physical constraints of non functional requirements affects all
the hardware that is required in the system of cloud. The shape, weight and size of the hardware
are determined in physical constraints.
Design Constraints- The design constraint of non functional requirement implements the
design of the system (Penzenstadler et al., 2013). The required database that is required in the
cloud system of Headspace is designed in the Design Constraints.
Implementation Constraint- The limit that is given to the constriction and the coding
which includes implementation language, standards and platforms are all determined in the
Implementation Constraints.
Performance: The performance is the acronym of P in FURPS+ (Punia & Kaur, 2014).
The feature that are included in performance are the information throughput in the clod system,
time take by the cloud system to response and the start up time of the system and also the
recovery time that the cloud system needs.
Supportability: The supportability is the S in the FURPS+. The supportability includes
other requirements that are needed in the cloud system which includes adaptability,
configurability, localizability, scalability, testability, installability and also maintainability.
The FURPS+ has a + sign which indicates some of the specific constraints which
includes interface, physical constraints, design and implementation constraints.
Interface Constraints- The constraint of interference is the requirement that is required to
interact with the entire external item (Ameller et al., 2013). When the interface of Headspace is
developed, it is difficult to interact with all the external systems.
Physical Constraints- The physical constraints of non functional requirements affects all
the hardware that is required in the system of cloud. The shape, weight and size of the hardware
are determined in physical constraints.
Design Constraints- The design constraint of non functional requirement implements the
design of the system (Penzenstadler et al., 2013). The required database that is required in the
cloud system of Headspace is designed in the Design Constraints.
Implementation Constraint- The limit that is given to the constriction and the coding
which includes implementation language, standards and platforms are all determined in the
Implementation Constraints.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3SYSTEM ANALYSIS OF HEADSPACE
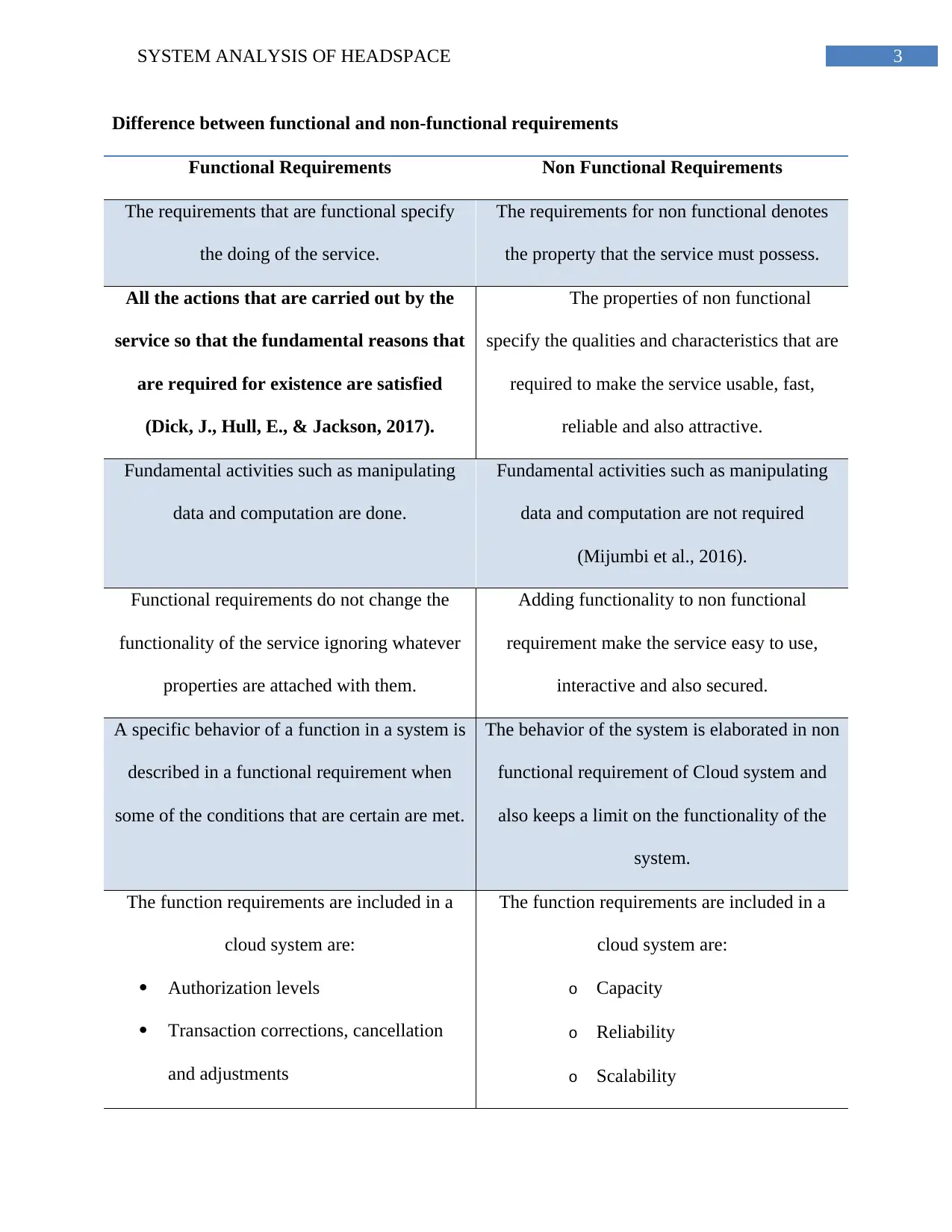
Difference between functional and non-functional requirements
Functional Requirements Non Functional Requirements
The requirements that are functional specify
the doing of the service.
The requirements for non functional denotes
the property that the service must possess.
All the actions that are carried out by the
service so that the fundamental reasons that
are required for existence are satisfied
(Dick, J., Hull, E., & Jackson, 2017).
The properties of non functional
specify the qualities and characteristics that are
required to make the service usable, fast,
reliable and also attractive.
Fundamental activities such as manipulating
data and computation are done.
Fundamental activities such as manipulating
data and computation are not required
(Mijumbi et al., 2016).
Functional requirements do not change the
functionality of the service ignoring whatever
properties are attached with them.
Adding functionality to non functional
requirement make the service easy to use,
interactive and also secured.
A specific behavior of a function in a system is
described in a functional requirement when
some of the conditions that are certain are met.
The behavior of the system is elaborated in non
functional requirement of Cloud system and
also keeps a limit on the functionality of the
system.
The function requirements are included in a
cloud system are:
Authorization levels
Transaction corrections, cancellation
and adjustments
The function requirements are included in a
cloud system are:
o Capacity
o Reliability
o Scalability
Difference between functional and non-functional requirements
Functional Requirements Non Functional Requirements
The requirements that are functional specify
the doing of the service.
The requirements for non functional denotes
the property that the service must possess.
All the actions that are carried out by the
service so that the fundamental reasons that
are required for existence are satisfied
(Dick, J., Hull, E., & Jackson, 2017).
The properties of non functional
specify the qualities and characteristics that are
required to make the service usable, fast,
reliable and also attractive.
Fundamental activities such as manipulating
data and computation are done.
Fundamental activities such as manipulating
data and computation are not required
(Mijumbi et al., 2016).
Functional requirements do not change the
functionality of the service ignoring whatever
properties are attached with them.
Adding functionality to non functional
requirement make the service easy to use,
interactive and also secured.
A specific behavior of a function in a system is
described in a functional requirement when
some of the conditions that are certain are met.
The behavior of the system is elaborated in non
functional requirement of Cloud system and
also keeps a limit on the functionality of the
system.
The function requirements are included in a
cloud system are:
Authorization levels
Transaction corrections, cancellation
and adjustments
The function requirements are included in a
cloud system are:
o Capacity
o Reliability
o Scalability
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4SYSTEM ANALYSIS OF HEADSPACE
Historical data
Administrative functions
Certification requirements
Business Rules
Regulatory and legal requirements
External Interfaces
Reporting requirements
Authentication and
Audit Tracking
o Maintainability
o Regulatory
o Environmental
o Interoperability
o Usability
o Manageability
o Security
o Performance that includes
throughput, response time, static
volumetric and utilization
o Availability
o Serviceability
o Data Integrity
o Recoverability
The example of Functional requirement is
sending an email when a new customer signs
up an account or opens a new account.
The characteristics and attributes of system
quality are specified such as all users who are
accessing the database are to have a modified
updated data.
Table 1: Showing Difference of Functional and Non-Functional Requirements
Review of Cloud Based
The advantages of Cloud Based Storage are as follows:
Historical data
Administrative functions
Certification requirements
Business Rules
Regulatory and legal requirements
External Interfaces
Reporting requirements
Authentication and
Audit Tracking
o Maintainability
o Regulatory
o Environmental
o Interoperability
o Usability
o Manageability
o Security
o Performance that includes
throughput, response time, static
volumetric and utilization
o Availability
o Serviceability
o Data Integrity
o Recoverability
The example of Functional requirement is
sending an email when a new customer signs
up an account or opens a new account.
The characteristics and attributes of system
quality are specified such as all users who are
accessing the database are to have a modified
updated data.
Table 1: Showing Difference of Functional and Non-Functional Requirements
Review of Cloud Based
The advantages of Cloud Based Storage are as follows:

5SYSTEM ANALYSIS OF HEADSPACE
1. Usability: The services of cloud storage are reviewed in usability in the desktop folders
that uses PCs and MACs (Abolfazli et al., 2014). This helps the users to drop and drag
the files in between local storage and cloud storage.
2. Bandwidth: The emails files that are sent to individuals are avoided and web link are sent
to all recipients via email.
3. Accessibility: The files that are stored can be accessed via Internet from anywhere the
user wants. The files are accessed easily by the users.
4. Disaster Recovery: The service of cloud has a high backup plan in case if some
emergency occurs. Backup plan for any business can use the cloud storage to keep a
second copy of a data or information that is important. The files that are backup in the
cloud can be accessed by the user from anywhere via internet connection.
5. Cost Saving: Organizations and businesses use operational costs that are needed annually
by using the cloud storage. The cost of storing data internally in cloud is almost 3 cents
per GB. The additional cost saving can be found in using cloud because internal power is
not needed to remotely store the information.
Disadvantages of Cloud Storage are:
1. Usability: Users have to be careful in using the drop and drag feature of cloud for moving
the document in folder of cloud storage (Rahimi et al., 2014). Copy and paste is not
allowed in this process. The users have to be careful to use drag and drop feature.
2. Bandwidth: Specific bandwidths are allowed by specific cloud services. The users of the
cloud services have to be careful in using the amount of bandwidth. If the users exceed
the amount of bandwidth that is allowed to tem, then extra charge is taken from them for
the extra amount that is used.
1. Usability: The services of cloud storage are reviewed in usability in the desktop folders
that uses PCs and MACs (Abolfazli et al., 2014). This helps the users to drop and drag
the files in between local storage and cloud storage.
2. Bandwidth: The emails files that are sent to individuals are avoided and web link are sent
to all recipients via email.
3. Accessibility: The files that are stored can be accessed via Internet from anywhere the
user wants. The files are accessed easily by the users.
4. Disaster Recovery: The service of cloud has a high backup plan in case if some
emergency occurs. Backup plan for any business can use the cloud storage to keep a
second copy of a data or information that is important. The files that are backup in the
cloud can be accessed by the user from anywhere via internet connection.
5. Cost Saving: Organizations and businesses use operational costs that are needed annually
by using the cloud storage. The cost of storing data internally in cloud is almost 3 cents
per GB. The additional cost saving can be found in using cloud because internal power is
not needed to remotely store the information.
Disadvantages of Cloud Storage are:
1. Usability: Users have to be careful in using the drop and drag feature of cloud for moving
the document in folder of cloud storage (Rahimi et al., 2014). Copy and paste is not
allowed in this process. The users have to be careful to use drag and drop feature.
2. Bandwidth: Specific bandwidths are allowed by specific cloud services. The users of the
cloud services have to be careful in using the amount of bandwidth. If the users exceed
the amount of bandwidth that is allowed to tem, then extra charge is taken from them for
the extra amount that is used.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6SYSTEM ANALYSIS OF HEADSPACE
3. Accessibility: The cloud storage cannot be accessed without the internet connection. If
there is no internet, the user will not be able to get access to the files.
4. Data Security: The safety and privacy of the data are to be maintained by cloud storage.
This proves the main disadvantage for the cloud system storage. The data privacy can be
hampered in the cloud storage service. This makes the business more uneasy and unsafe.
5. Software: The software that is used to access the data have to be installed on all the
devices that uses the cloud service, otherwise the files are not accessible.
The data are to be kept secured by using a cloud service in the Headspace. The following
aspects are to be kept in mind to give a security to all the data that is stored in the cloud
storage. First of all the security agreement that s given by the cloud are to be read properly by
the user. The users have to be sure what agreement the provider of cloud is giving to the user.
The user agreement are to be made clear so that their does not come any data related threat to
the data that are stored in the cloud (Wei et al., 2014). The documents that are stored usually
faces data security which hampers the privacy if the user. Secondly the passwords that are
created in for the security of the applications are to be very securely done. The passwords are
to be strong enough so that any data breach does not take place the technologies that are used
by the cyber attacker takes very less time to break the passwords that are used in application
in cloud storage. The cloud storages are very much prone to data breach. Hackers find it
easy to hack the applications that are connected to cloud. The passwords for the emails and
other needed applications are to be made double secured. Lastly, a cloud service that is
securely encrypted is to be used. To protect the data breach and secure the data, encryption
process is the most important method that is used. Different cloud services have different
3. Accessibility: The cloud storage cannot be accessed without the internet connection. If
there is no internet, the user will not be able to get access to the files.
4. Data Security: The safety and privacy of the data are to be maintained by cloud storage.
This proves the main disadvantage for the cloud system storage. The data privacy can be
hampered in the cloud storage service. This makes the business more uneasy and unsafe.
5. Software: The software that is used to access the data have to be installed on all the
devices that uses the cloud service, otherwise the files are not accessible.
The data are to be kept secured by using a cloud service in the Headspace. The following
aspects are to be kept in mind to give a security to all the data that is stored in the cloud
storage. First of all the security agreement that s given by the cloud are to be read properly by
the user. The users have to be sure what agreement the provider of cloud is giving to the user.
The user agreement are to be made clear so that their does not come any data related threat to
the data that are stored in the cloud (Wei et al., 2014). The documents that are stored usually
faces data security which hampers the privacy if the user. Secondly the passwords that are
created in for the security of the applications are to be very securely done. The passwords are
to be strong enough so that any data breach does not take place the technologies that are used
by the cyber attacker takes very less time to break the passwords that are used in application
in cloud storage. The cloud storages are very much prone to data breach. Hackers find it
easy to hack the applications that are connected to cloud. The passwords for the emails and
other needed applications are to be made double secured. Lastly, a cloud service that is
securely encrypted is to be used. To protect the data breach and secure the data, encryption
process is the most important method that is used. Different cloud services have different
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7SYSTEM ANALYSIS OF HEADSPACE
encryption process. It is recommended to use cloud services like Wuala or Spideroak so that
the data is kept secured in Headspace.
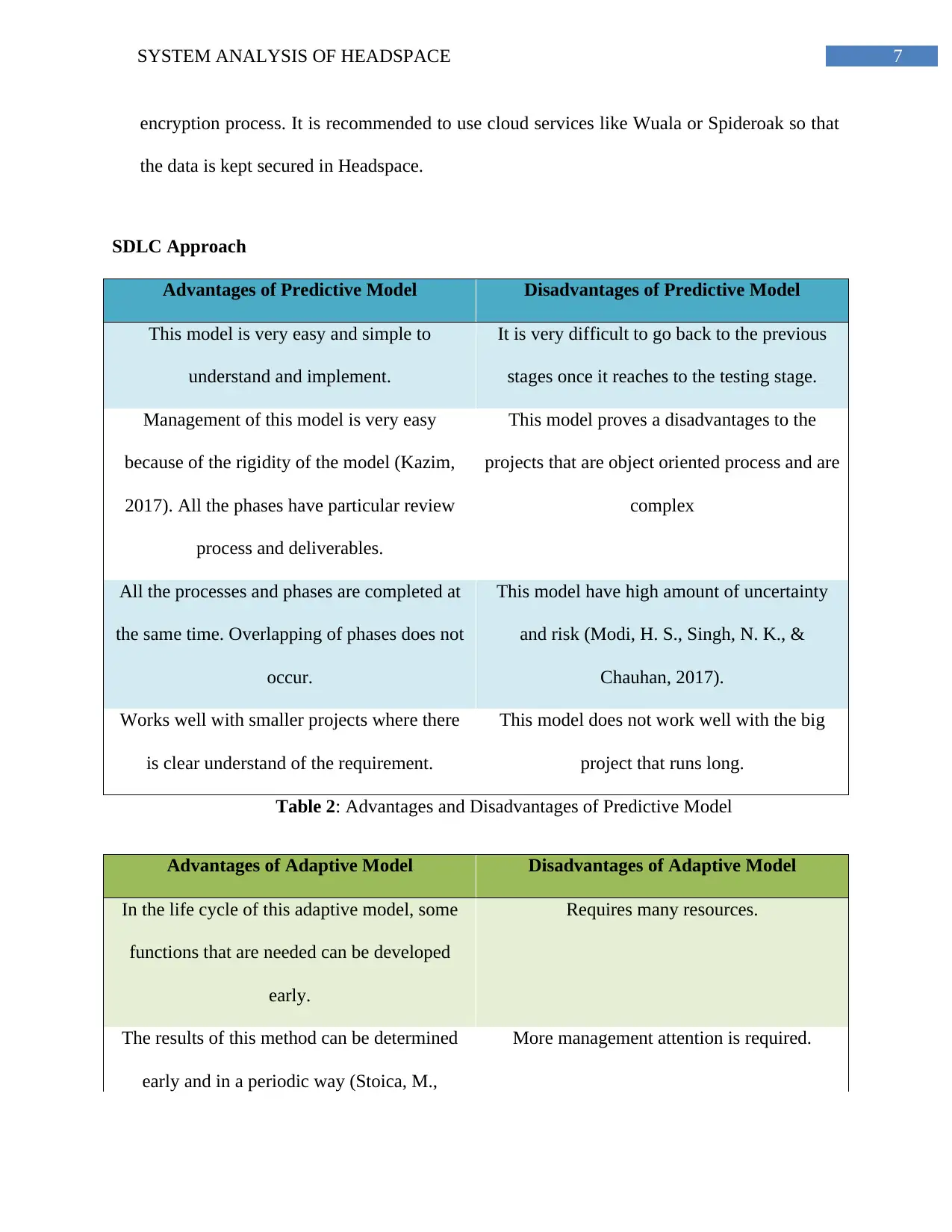
SDLC Approach
Advantages of Predictive Model Disadvantages of Predictive Model
This model is very easy and simple to
understand and implement.
It is very difficult to go back to the previous
stages once it reaches to the testing stage.
Management of this model is very easy
because of the rigidity of the model (Kazim,
2017). All the phases have particular review
process and deliverables.
This model proves a disadvantages to the
projects that are object oriented process and are
complex
All the processes and phases are completed at
the same time. Overlapping of phases does not
occur.
This model have high amount of uncertainty
and risk (Modi, H. S., Singh, N. K., &
Chauhan, 2017).
Works well with smaller projects where there
is clear understand of the requirement.
This model does not work well with the big
project that runs long.
Table 2: Advantages and Disadvantages of Predictive Model
Advantages of Adaptive Model Disadvantages of Adaptive Model
In the life cycle of this adaptive model, some
functions that are needed can be developed
early.
Requires many resources.
The results of this method can be determined
early and in a periodic way (Stoica, M.,
More management attention is required.
encryption process. It is recommended to use cloud services like Wuala or Spideroak so that
the data is kept secured in Headspace.
SDLC Approach
Advantages of Predictive Model Disadvantages of Predictive Model
This model is very easy and simple to
understand and implement.
It is very difficult to go back to the previous
stages once it reaches to the testing stage.
Management of this model is very easy
because of the rigidity of the model (Kazim,
2017). All the phases have particular review
process and deliverables.
This model proves a disadvantages to the
projects that are object oriented process and are
complex
All the processes and phases are completed at
the same time. Overlapping of phases does not
occur.
This model have high amount of uncertainty
and risk (Modi, H. S., Singh, N. K., &
Chauhan, 2017).
Works well with smaller projects where there
is clear understand of the requirement.
This model does not work well with the big
project that runs long.
Table 2: Advantages and Disadvantages of Predictive Model
Advantages of Adaptive Model Disadvantages of Adaptive Model
In the life cycle of this adaptive model, some
functions that are needed can be developed
early.
Requires many resources.
The results of this method can be determined
early and in a periodic way (Stoica, M.,
More management attention is required.
8SYSTEM ANALYSIS OF HEADSPACE
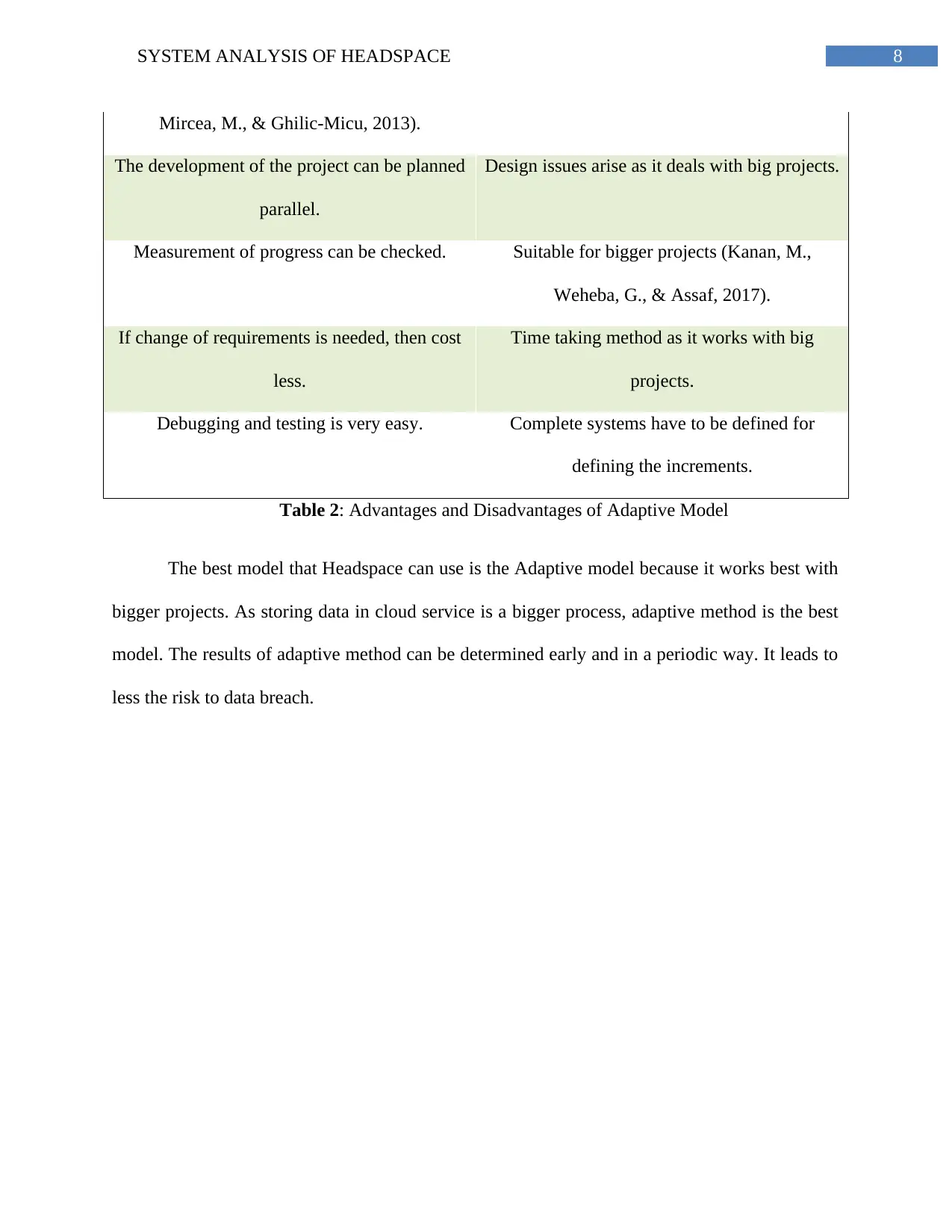
Mircea, M., & Ghilic-Micu, 2013).
The development of the project can be planned
parallel.
Design issues arise as it deals with big projects.
Measurement of progress can be checked. Suitable for bigger projects (Kanan, M.,
Weheba, G., & Assaf, 2017).
If change of requirements is needed, then cost
less.
Time taking method as it works with big
projects.
Debugging and testing is very easy. Complete systems have to be defined for
defining the increments.
Table 2: Advantages and Disadvantages of Adaptive Model
The best model that Headspace can use is the Adaptive model because it works best with
bigger projects. As storing data in cloud service is a bigger process, adaptive method is the best
model. The results of adaptive method can be determined early and in a periodic way. It leads to
less the risk to data breach.
Mircea, M., & Ghilic-Micu, 2013).
The development of the project can be planned
parallel.
Design issues arise as it deals with big projects.
Measurement of progress can be checked. Suitable for bigger projects (Kanan, M.,
Weheba, G., & Assaf, 2017).
If change of requirements is needed, then cost
less.
Time taking method as it works with big
projects.
Debugging and testing is very easy. Complete systems have to be defined for
defining the increments.
Table 2: Advantages and Disadvantages of Adaptive Model
The best model that Headspace can use is the Adaptive model because it works best with
bigger projects. As storing data in cloud service is a bigger process, adaptive method is the best
model. The results of adaptive method can be determined early and in a periodic way. It leads to
less the risk to data breach.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9SYSTEM ANALYSIS OF HEADSPACE
References
Abolfazli, S., Sanaei, Z., Ahmed, E., Gani, A., & Buyya, R. (2014). Cloud-based augmentation
for mobile devices: motivation, taxonomies, and open challenges. IEEE Communications
Surveys & Tutorials, 16(1), 337-368.
Al-Rawashdeh, T. A., Al’azzeh, F. M., & Al-Qatawneh, S. M. (2014). Evaluation of ERP
systems quality model using analytic hierarchy process (AHP) technique. Journal of
Software Engineering and Applications, 7(04), 225.
Ameller, D., Ayala, C., Cabot, J., & Franch, X. (2013). Non-functional requirements in
architectural decision making. IEEE software, 30(2), 61-67.
Awan, S., Malik, F., & Javed, A. (2015). An Efficient and Objective Generalized Comparison
technique for Software Quality Models. International Journal of Modern Education and
Computer Science, 7(12), 57.
Dick, J., Hull, E., & Jackson, K. (2017). Requirements engineering. Springer.
Kanan, M., Weheba, G., & Assaf, R. (2017). Economic Advantages of Utilizing the Integrated
Quality Software Development Model. Ind Eng Manage, 6(210), 2169-0316.
Kazim, A. (2017). A Study of Software Development Life Cycle Process Models. International
Journal of Advanced Research in Computer Science, 8(1).
Mijumbi, R., Serrat, J., Gorricho, J. L., Bouten, N., De Turck, F., & Boutaba, R. (2016). Network
function virtualization: State-of-the-art and research challenges. IEEE Communications
Surveys & Tutorials, 18(1), 236-262.
References
Abolfazli, S., Sanaei, Z., Ahmed, E., Gani, A., & Buyya, R. (2014). Cloud-based augmentation
for mobile devices: motivation, taxonomies, and open challenges. IEEE Communications
Surveys & Tutorials, 16(1), 337-368.
Al-Rawashdeh, T. A., Al’azzeh, F. M., & Al-Qatawneh, S. M. (2014). Evaluation of ERP
systems quality model using analytic hierarchy process (AHP) technique. Journal of
Software Engineering and Applications, 7(04), 225.
Ameller, D., Ayala, C., Cabot, J., & Franch, X. (2013). Non-functional requirements in
architectural decision making. IEEE software, 30(2), 61-67.
Awan, S., Malik, F., & Javed, A. (2015). An Efficient and Objective Generalized Comparison
technique for Software Quality Models. International Journal of Modern Education and
Computer Science, 7(12), 57.
Dick, J., Hull, E., & Jackson, K. (2017). Requirements engineering. Springer.
Kanan, M., Weheba, G., & Assaf, R. (2017). Economic Advantages of Utilizing the Integrated
Quality Software Development Model. Ind Eng Manage, 6(210), 2169-0316.
Kazim, A. (2017). A Study of Software Development Life Cycle Process Models. International
Journal of Advanced Research in Computer Science, 8(1).
Mijumbi, R., Serrat, J., Gorricho, J. L., Bouten, N., De Turck, F., & Boutaba, R. (2016). Network
function virtualization: State-of-the-art and research challenges. IEEE Communications
Surveys & Tutorials, 18(1), 236-262.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





