Comprehensive Security Analysis of a Healthcare Information System
VerifiedAdded on 2022/09/28
|11
|3717
|24
Report
AI Summary
This report provides a comprehensive security analysis of healthcare information systems. It begins by identifying five common security threats facing healthcare organizations, including ransomware, theft of patient data, insider threats, phishing, and cryptojacking. The report then applies the STRIDE model to analyze these threats and outline the necessary security requirements to mitigate them. Following this, the DREAD model is employed to assess the risk posed by each threat. Finally, the report measures the overall risks to the healthcare system and suggests appropriate security measures, such as employee education, policy enforcement, and technological solutions like web filters and data encryption, to protect sensitive patient information and ensure the integrity of healthcare operations. This assignment is designed to provide a reflective analysis on security in the healthcare domain.

INFORMATION SYSTEM: HEALTHCARE SYSTEM
Student’s Name
Institutional Affiliation
City
Email
Abstract-The advancement in information system has seen
healthcare organization turn to health information
technology (HIT) to improve care service delivery.
However, with the introduction of different health
information technology systems healthcare organizations
have become prone to cyberattacks. Cybercriminals have
seen healthcare organizations as a soft landing place to
steal personal information. This paper discuss about
common security threats facing healthcare systems,
analysis of security requirements put in place to counter
these security threats in healthcare organizations and lastly
conclusion regarding security system in healthcare
industry.
Keywords-health information technology,
cybercriminals, security threats, healthcare, healthcare
system and cyberattacks.
I. INTRODUCTION
Over the past decade or so information systems in
healthcare have become increasingly advanced as well as
the ever-growing variety of capabilities have resulted into
the widespread usage of these systems in the entire
healthcare industry. Generally, the usage of certain
information management level has turn out to be nearly
universal amongst healthcare amenities, providers and
health systems. Health information system (HIS) is a
system that has been designed to accomplish healthcare
data and information. This comprises systems that collect,
manage, store and convey patient’s electronic medical
records (ERM) [4].
The health information technology is the technological
field that is majorly concern with the development of health
information systems. Some of the healthcare information
systems include Electronic Medical Record (EMR) and
Electronic Health Records (EHR) Practice Management
Software (PMS), Master Patient Index (MPI), Remote
Patient Monitoring (RPM), patient portal, and Clinical
Decision Support (CDS).
The introduction of health information systems in the
healthcare industry tend to target data management and
improve efficiency. Consequently, the major benefits
associated with healthcare information systems include data
analytics, collaborative care population health management
and cost control among others [5]. In light of this statement,
this paper provides a security analysis related to healthcare
system. The paper focus on two security models STRIDE
and DREAD by identifying the security threats related to
Student’s Name
Institutional Affiliation
City
Abstract-The advancement in information system has seen
healthcare organization turn to health information
technology (HIT) to improve care service delivery.
However, with the introduction of different health
information technology systems healthcare organizations
have become prone to cyberattacks. Cybercriminals have
seen healthcare organizations as a soft landing place to
steal personal information. This paper discuss about
common security threats facing healthcare systems,
analysis of security requirements put in place to counter
these security threats in healthcare organizations and lastly
conclusion regarding security system in healthcare
industry.
Keywords-health information technology,
cybercriminals, security threats, healthcare, healthcare
system and cyberattacks.
I. INTRODUCTION
Over the past decade or so information systems in
healthcare have become increasingly advanced as well as
the ever-growing variety of capabilities have resulted into
the widespread usage of these systems in the entire
healthcare industry. Generally, the usage of certain
information management level has turn out to be nearly
universal amongst healthcare amenities, providers and
health systems. Health information system (HIS) is a
system that has been designed to accomplish healthcare
data and information. This comprises systems that collect,
manage, store and convey patient’s electronic medical
records (ERM) [4].
The health information technology is the technological
field that is majorly concern with the development of health
information systems. Some of the healthcare information
systems include Electronic Medical Record (EMR) and
Electronic Health Records (EHR) Practice Management
Software (PMS), Master Patient Index (MPI), Remote
Patient Monitoring (RPM), patient portal, and Clinical
Decision Support (CDS).
The introduction of health information systems in the
healthcare industry tend to target data management and
improve efficiency. Consequently, the major benefits
associated with healthcare information systems include data
analytics, collaborative care population health management
and cost control among others [5]. In light of this statement,
this paper provides a security analysis related to healthcare
system. The paper focus on two security models STRIDE
and DREAD by identifying the security threats related to
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

healthcare system, provide a list security requirements to
counter healthcare system threats using STRIDE model.
The paper then analyses the risk posed by each threat to the
healthcare system using DREAD model. Lastly, the paper
measures the overall risks of the healthcare system and
commends the appropriate security measures to overcome
these threats.
II. FIVE COMMON SECURITY THREATS
Due to the crucial nature of the operations that healthcare
facilities undertake it puts them on the radar of attackers.
Health data and information is a highly valued resource in
the cybercriminal domain, hence it makes it an objective
for theft. As a result of what is at stake that is the security
of patients healthcare establishments are more probable to
pay ransomware burdens [6]. In this regard, the prevalent
healthcare security coercions include ransomware, theft of
patient data, insider threats, phishing and cryptojacking.
Ransomware
Recent reports indicate that ransomware is
rapidly becoming an exhortation in the healthcare industry
[2]. Ransomware is a malware type which archetypally
averts healthcare organizations from retrieving some parts
of their systems. For instance, the malware can block out an
entity together with its users from vital networks like EHRs
and they cannot be in a position to access if not they pay a
specified sum of money. Unfortunately, this may possibly
pose major problems for a healthcare facility’s data
security. In the recent past there has been increased cases of
ransomware attacks happening across the world. For
example, in 2016, Hollywood Presbyterian Medicare
Center (HPMC) fall a prey to an attack which express in
code its information and averted employees from gaining
access to certain parts of the infirmary system. As a result
of the attack, HPMC had to pay approximately $17,000 to
regain access [9]. The good news is that the hospital’s
information that was stored in the EHR was not misused or
accessed by unauthorized persons. The actors in the
Hollywood Presbyterian Center Hospital attack used an
open source tool known as JexBoss to search over the
Internet for valuable JBoss servers. In the process the
attackers managed to infect HPMC healthcare system.
While there is no definitive proof, some people have
speculated that that the high ransom demands observed in
healthcare associated cases is a show that the cyber threat
actors could have been aware of who they had exactly
infected. The effect of ransomware when a healthcare
organization is not quickly recovered could be devastating
Theft of patient data
According to [7] healthcare data is more valuable
as compared to financial data to cybercriminals. On the
same note, a report by the Trend Micro Cybercrime and
Other Threats faced by the Healthcare Industry shows that
stolen medical insurance identification cards sell for
approximately five dollar on the dark web. Therefore,
hackers can use the data from the ID cards as well as other
medical data to gain access to healthcare organizational
documents like driver licenses that sell for up to $200
according to the report by Trend Micro. Accordingly,
healthcare information and data is exceedingly important
compared to credit card data since they aggregates much
information in a single place. These data include an
counter healthcare system threats using STRIDE model.
The paper then analyses the risk posed by each threat to the
healthcare system using DREAD model. Lastly, the paper
measures the overall risks of the healthcare system and
commends the appropriate security measures to overcome
these threats.
II. FIVE COMMON SECURITY THREATS
Due to the crucial nature of the operations that healthcare
facilities undertake it puts them on the radar of attackers.
Health data and information is a highly valued resource in
the cybercriminal domain, hence it makes it an objective
for theft. As a result of what is at stake that is the security
of patients healthcare establishments are more probable to
pay ransomware burdens [6]. In this regard, the prevalent
healthcare security coercions include ransomware, theft of
patient data, insider threats, phishing and cryptojacking.
Ransomware
Recent reports indicate that ransomware is
rapidly becoming an exhortation in the healthcare industry
[2]. Ransomware is a malware type which archetypally
averts healthcare organizations from retrieving some parts
of their systems. For instance, the malware can block out an
entity together with its users from vital networks like EHRs
and they cannot be in a position to access if not they pay a
specified sum of money. Unfortunately, this may possibly
pose major problems for a healthcare facility’s data
security. In the recent past there has been increased cases of
ransomware attacks happening across the world. For
example, in 2016, Hollywood Presbyterian Medicare
Center (HPMC) fall a prey to an attack which express in
code its information and averted employees from gaining
access to certain parts of the infirmary system. As a result
of the attack, HPMC had to pay approximately $17,000 to
regain access [9]. The good news is that the hospital’s
information that was stored in the EHR was not misused or
accessed by unauthorized persons. The actors in the
Hollywood Presbyterian Center Hospital attack used an
open source tool known as JexBoss to search over the
Internet for valuable JBoss servers. In the process the
attackers managed to infect HPMC healthcare system.
While there is no definitive proof, some people have
speculated that that the high ransom demands observed in
healthcare associated cases is a show that the cyber threat
actors could have been aware of who they had exactly
infected. The effect of ransomware when a healthcare
organization is not quickly recovered could be devastating
Theft of patient data
According to [7] healthcare data is more valuable
as compared to financial data to cybercriminals. On the
same note, a report by the Trend Micro Cybercrime and
Other Threats faced by the Healthcare Industry shows that
stolen medical insurance identification cards sell for
approximately five dollar on the dark web. Therefore,
hackers can use the data from the ID cards as well as other
medical data to gain access to healthcare organizational
documents like driver licenses that sell for up to $200
according to the report by Trend Micro. Accordingly,
healthcare information and data is exceedingly important
compared to credit card data since they aggregates much
information in a single place. These data include an

individual’s vital background data and financial
information hence cybercriminals find healthcare systems
prime because they contain vital information needed for
identity theft. In this regard, cyber criminals are advancing
their tricks regarding to how they steal health data and a
good example is the pseudo-ransomware [8]. The pseudo-
ransomware is a malware which steal healthcare data and
information by laterally moving across the systems and
installing additional spyware that are later on used to
benefit the criminals.
Insider threats
Insider threats is among the leading data security
challenges facing healthcare industry. In accordance to the
recent report released by Verizon Protected Health
Information Data Beach, approximately 60% of all the
threats actors’ responsible breaches among healthcare
organizations come from insiders. The main aggravator to
insider treats is for financial gains. On the same note,
curiosity and fun are other perpetrators of insider breaches
whereby insider access data that is external their job
responsibilities in search of PHI on celebrities. Healthcare
organization are frequently preoccupied with protecting the
integrity of their network and company from external
threats in addressing the actual and dangerous risk that lie
within their organization-insiders [3]. Insiders comprises all
individuals within the healthcare organization who have
access to healthcare systems such as healthcare networks,
ERMs, documents containing PHI and email accounts.
Insider threats can pose an organization heavy fines for the
breach of HIPAA regulations as well as the violation of
patient privacy. Additionally, they could also damage the
reputation of the healthcare organization.
Phishing
It is an attack process that is deployed in the
healthcare system through email. Generally, the
communications seem legitimate which instruct the
employee to follow a certain link to a web page where they
are asked to complete certain actions that trigger a malware
download. In this sense, the attacker poses as an authentic
entity or person in an email to get the target to offer worthy
information like credentials or click on a link which leads
in a ransomware downloaded on the victim’s machine.
Cryptojacking
With the advent of the internet of things in the
healthcare industry cyberattacks have increased. After the
healthcare industry being faced with ransomware, phishing
and data theft, cybercriminals are shifting their methods
and currently tapping into the cryptojacking. Cryptojacking
is a cybersecurity threat that thrives on the process power
of a compromised device to mine cryptocurrency on behalf
of the hacker [1]. Hence, cryptojacking has deleterious
consequences to the functionality of a compromised device
which reduces it overall lifetime. In the healthcare setting
which have a variety of medical devices used for patient
care, cryptojacking has become a major risk to patient
safety.
III. ANALYSIS OF SECURITY
REQUIREMENTS USING STRIDE
MODEL
information hence cybercriminals find healthcare systems
prime because they contain vital information needed for
identity theft. In this regard, cyber criminals are advancing
their tricks regarding to how they steal health data and a
good example is the pseudo-ransomware [8]. The pseudo-
ransomware is a malware which steal healthcare data and
information by laterally moving across the systems and
installing additional spyware that are later on used to
benefit the criminals.
Insider threats
Insider threats is among the leading data security
challenges facing healthcare industry. In accordance to the
recent report released by Verizon Protected Health
Information Data Beach, approximately 60% of all the
threats actors’ responsible breaches among healthcare
organizations come from insiders. The main aggravator to
insider treats is for financial gains. On the same note,
curiosity and fun are other perpetrators of insider breaches
whereby insider access data that is external their job
responsibilities in search of PHI on celebrities. Healthcare
organization are frequently preoccupied with protecting the
integrity of their network and company from external
threats in addressing the actual and dangerous risk that lie
within their organization-insiders [3]. Insiders comprises all
individuals within the healthcare organization who have
access to healthcare systems such as healthcare networks,
ERMs, documents containing PHI and email accounts.
Insider threats can pose an organization heavy fines for the
breach of HIPAA regulations as well as the violation of
patient privacy. Additionally, they could also damage the
reputation of the healthcare organization.
Phishing
It is an attack process that is deployed in the
healthcare system through email. Generally, the
communications seem legitimate which instruct the
employee to follow a certain link to a web page where they
are asked to complete certain actions that trigger a malware
download. In this sense, the attacker poses as an authentic
entity or person in an email to get the target to offer worthy
information like credentials or click on a link which leads
in a ransomware downloaded on the victim’s machine.
Cryptojacking
With the advent of the internet of things in the
healthcare industry cyberattacks have increased. After the
healthcare industry being faced with ransomware, phishing
and data theft, cybercriminals are shifting their methods
and currently tapping into the cryptojacking. Cryptojacking
is a cybersecurity threat that thrives on the process power
of a compromised device to mine cryptocurrency on behalf
of the hacker [1]. Hence, cryptojacking has deleterious
consequences to the functionality of a compromised device
which reduces it overall lifetime. In the healthcare setting
which have a variety of medical devices used for patient
care, cryptojacking has become a major risk to patient
safety.
III. ANALYSIS OF SECURITY
REQUIREMENTS USING STRIDE
MODEL
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
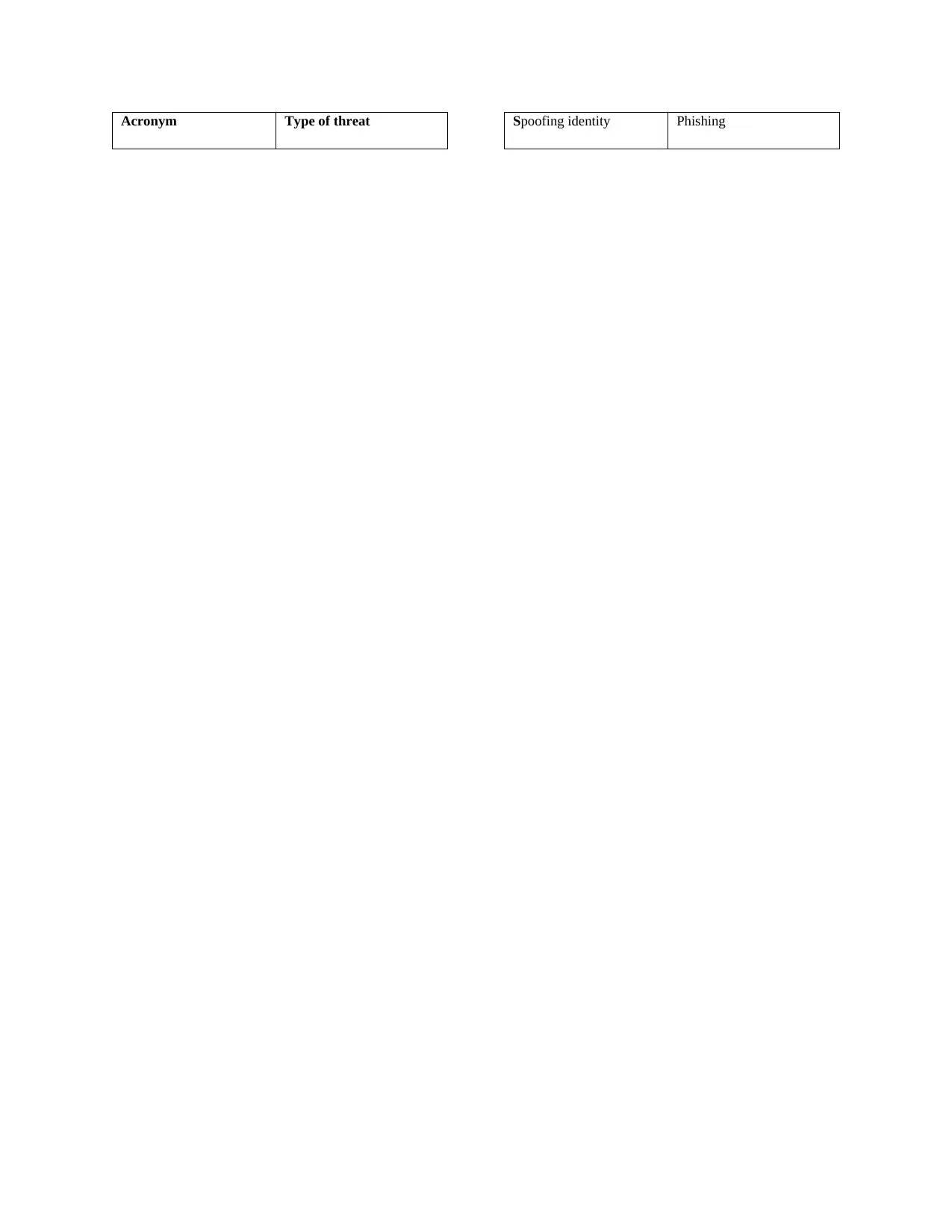
Acronym Type of threat Spoofing identity Phishing
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
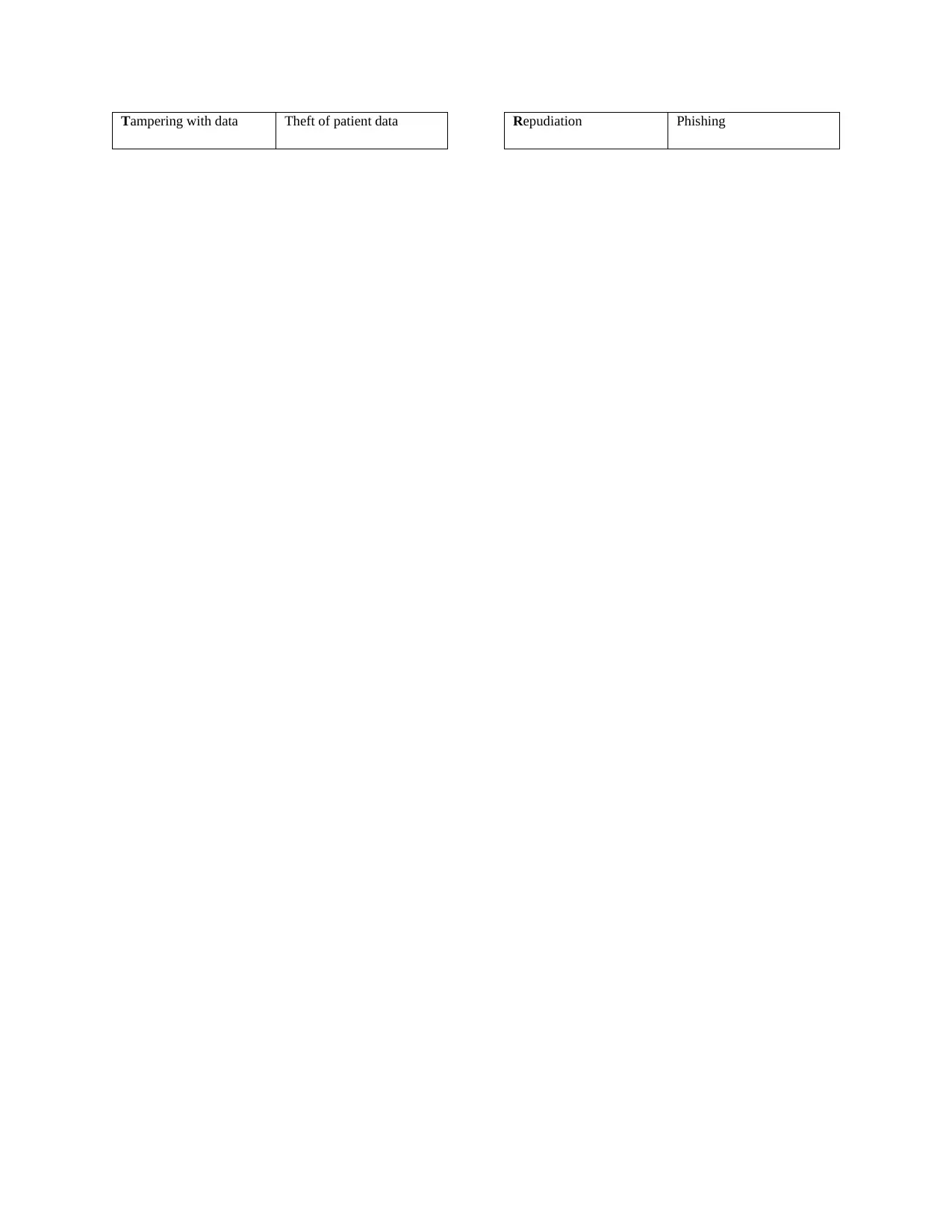
Tampering with data Theft of patient data Repudiation Phishing

Information disclosure Insider threat, theft of
patient data
Denial of service Ransomware
Elevation of privilege Cryptojacking
IV. ANALYSIS OF SECURITY
REQUIREMENTS IN HEALTHCARE
SYSTEM
Approaches to defend against insider threats in healthcare
The standard approach to mitigate insider threats is
subdivided into four categories educate, deter, detect and
investigate.
Educate
Healthcare employees should be educated on the
permitted uses and disclosures of PHI and the risks related
to behaviors such as patient data security, and privacy.
Deter
Healthcare organization should develop policies
to reduce risks and strongly enforce these policies. Also,
employees need to be clearly explained to the consequences
associated with violation as well as breaching of HIPAA
regulations.
Detect
Healthcare facilities are supposed to implement
technological solutions which allow them to detect
breaches rapidly and ensure constant checks of access logs.
Investigate
Once probable security and privacy breaches are
detected they should be investigated quickly to restrict the
harm caused. When the root cause of the breach is
determined, steps ought to be undertaken to avert a
recurrence [10].
V. WAYS TO PROTECT HEALTHCARE
DATA FROM PHISHING
Since there are numerous ways through which
employees can receive communications instructing them
regarding visiting websites that are not safe, the best
strategy to protect healthcare information and data from
phishing is to prevent workers from being able to visit
unsafe websites. This could be attained through use of safe
web filters that are configured to deny access to fake
websites as well as website harboring malware. In the way,
healthcare organization will block the download of file
types often related to malware [11]. The web filters protect
healthcare data from phishing attacks using approaches
such as category filters, blacklists and keyword filters.
Category filters are used to deny access to certain
website categories which typically harbor malware.
Therefore, system administrators should configure
healthcare web filters to deny access to dissimilar website
categories such as those containing pharmaceuticals
products, freeware and pornography.
Blacklists is used to deny access to website that
are known to be unsafe or those that mask their true
identify behind a proxy server [12]. The blacklists should
be updated on a regular basis to reflect the most recent-
patient data
Denial of service Ransomware
Elevation of privilege Cryptojacking
IV. ANALYSIS OF SECURITY
REQUIREMENTS IN HEALTHCARE
SYSTEM
Approaches to defend against insider threats in healthcare
The standard approach to mitigate insider threats is
subdivided into four categories educate, deter, detect and
investigate.
Educate
Healthcare employees should be educated on the
permitted uses and disclosures of PHI and the risks related
to behaviors such as patient data security, and privacy.
Deter
Healthcare organization should develop policies
to reduce risks and strongly enforce these policies. Also,
employees need to be clearly explained to the consequences
associated with violation as well as breaching of HIPAA
regulations.
Detect
Healthcare facilities are supposed to implement
technological solutions which allow them to detect
breaches rapidly and ensure constant checks of access logs.
Investigate
Once probable security and privacy breaches are
detected they should be investigated quickly to restrict the
harm caused. When the root cause of the breach is
determined, steps ought to be undertaken to avert a
recurrence [10].
V. WAYS TO PROTECT HEALTHCARE
DATA FROM PHISHING
Since there are numerous ways through which
employees can receive communications instructing them
regarding visiting websites that are not safe, the best
strategy to protect healthcare information and data from
phishing is to prevent workers from being able to visit
unsafe websites. This could be attained through use of safe
web filters that are configured to deny access to fake
websites as well as website harboring malware. In the way,
healthcare organization will block the download of file
types often related to malware [11]. The web filters protect
healthcare data from phishing attacks using approaches
such as category filters, blacklists and keyword filters.
Category filters are used to deny access to certain
website categories which typically harbor malware.
Therefore, system administrators should configure
healthcare web filters to deny access to dissimilar website
categories such as those containing pharmaceuticals
products, freeware and pornography.
Blacklists is used to deny access to website that
are known to be unsafe or those that mask their true
identify behind a proxy server [12]. The blacklists should
be updated on a regular basis to reflect the most recent-
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

reported phishing attacks experienced in the healthcare
sector as well as additional threats to online security.
Keyword filters
This enables the system administrator to fine-tune
web filtering parameters to regulate access to websites that
contain particular file type of words.
Accordingly, these mechanisms work in unison to
safeguard healthcare data from phishing and to prevent
other website borne threats.
VI. STEPS TO PREVENT THEFT OF
PATIENT DATA
Reduce risk connected with personal patient
information: When it comes to identity theft the storage and
use of patient’s social security numbers is the primary
source of vulnerability. Data entry errors and breaches
means that a patient’s data is likely to fall into the wrong
hands hence compromising both the patient as well as the
healthcare facility. In this regard, hospital staff are
supposed to take care not to discuss patient information on
public, with family or friends. For physical form such as
patient records and charts should be safely used and stored
[13].
Secure methods should be used to storing patient
health information: Each health organization should take
the necessary precautions measures to ensure the safety and
security of patient information. Healthcare organization
should invest in the right health information technology
such as the use of unique health safety identifier (UHSI) to
reinforce data and information security.
Assemble and use an advisory committee: It is of
great advantage for any healthcare environment to establish
a diverse team of leaders to come together to constantly
review and assess security issues as well as vulnerabilities.
This helps to raise awareness and discussing perceived
risks that allow hospital management to be well-informed
on matter to do with decision-making and implementing
efforts to minimize risks and safeguard sensitive
information. The advisory committee aid to prevent against
identity theft in addition to the selected team of
professionals helping to addressing issues in prompt and
adequate manner. The use of inventory system that track all
processes and systems which contribute to security
breaches could enable the health facility identify their
weaknesses to make improvements on their security
systems [14]. When an issue is discovered the advisory
committee will be bettered prepared to prioritize areas of
concern and make necessary improvements required.
Educate patient regarding medical identity theft:
Research has shown that most cases of fraud ca be
prevented or stopped early if patients pay closer attention to
their records and statements to pinpoint suspicious
practices. Healthcare facilities can help to reduce such
cases by teaching patients on what they should take caution
not to share sensitive medical details such as insurance
cards. Additionally, hospitals should make it simple for
patients to gain access to their medical documents. Educate
staff on security threats and warning signs: Not all data
breaches are malicious and human error is a major
component ranging from accidentally publishing patient
data on public websites to mailing personal data to the
sector as well as additional threats to online security.
Keyword filters
This enables the system administrator to fine-tune
web filtering parameters to regulate access to websites that
contain particular file type of words.
Accordingly, these mechanisms work in unison to
safeguard healthcare data from phishing and to prevent
other website borne threats.
VI. STEPS TO PREVENT THEFT OF
PATIENT DATA
Reduce risk connected with personal patient
information: When it comes to identity theft the storage and
use of patient’s social security numbers is the primary
source of vulnerability. Data entry errors and breaches
means that a patient’s data is likely to fall into the wrong
hands hence compromising both the patient as well as the
healthcare facility. In this regard, hospital staff are
supposed to take care not to discuss patient information on
public, with family or friends. For physical form such as
patient records and charts should be safely used and stored
[13].
Secure methods should be used to storing patient
health information: Each health organization should take
the necessary precautions measures to ensure the safety and
security of patient information. Healthcare organization
should invest in the right health information technology
such as the use of unique health safety identifier (UHSI) to
reinforce data and information security.
Assemble and use an advisory committee: It is of
great advantage for any healthcare environment to establish
a diverse team of leaders to come together to constantly
review and assess security issues as well as vulnerabilities.
This helps to raise awareness and discussing perceived
risks that allow hospital management to be well-informed
on matter to do with decision-making and implementing
efforts to minimize risks and safeguard sensitive
information. The advisory committee aid to prevent against
identity theft in addition to the selected team of
professionals helping to addressing issues in prompt and
adequate manner. The use of inventory system that track all
processes and systems which contribute to security
breaches could enable the health facility identify their
weaknesses to make improvements on their security
systems [14]. When an issue is discovered the advisory
committee will be bettered prepared to prioritize areas of
concern and make necessary improvements required.
Educate patient regarding medical identity theft:
Research has shown that most cases of fraud ca be
prevented or stopped early if patients pay closer attention to
their records and statements to pinpoint suspicious
practices. Healthcare facilities can help to reduce such
cases by teaching patients on what they should take caution
not to share sensitive medical details such as insurance
cards. Additionally, hospitals should make it simple for
patients to gain access to their medical documents. Educate
staff on security threats and warning signs: Not all data
breaches are malicious and human error is a major
component ranging from accidentally publishing patient
data on public websites to mailing personal data to the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
wrong patients. Training employees about the possible
pitfalls could help in protecting private patient information.
Best practices to prevent cryptojacking healthcare
cybersecurity
Identify and monitor all linked medical devices:
The healthcare administrator should make sure that each
connected medical device is monitored in real-time to allow
for constant probe for vulnerabilities which could signal the
device has been compromised [17].
Segment connected medical devices: Well-
segmented linked medical devices according to risk profile
and vulnerabilities could help reduce hackers’ entrée into
the healthcare system in the event of a cyberattack.
Healthcare organization can alleviate such risks by
establishing isolated network for linked devices, which is
simple and can be achieved using firewall and VLANs
technology [15].
Ensuring regular software update: Periodical
software updates are essential to warding off something
that could easily be thwarted cyberattacks. Each linked
medical device should be updated regularly for software
patching and firmware updates to minimize medical
devices from exploitation.
Establish cybersecurity framework and incident
response plan: Healthcare systems require comprehensive
cybersecurity plan that include incident response procedure
which can be deployed at a moment’s notice that involves
all key stakeholders in all departments within the healthcare
facility.
VII. WAYS TO PREVENT RANSOMWARE
ATTACKS
The best approach to prevent ransomware from
succeeding is by healthcare organization training their staff
about cyber hygiene. Cyber hygiene is thinking prior to
making a click on a computer and avoiding surfing the
internet for personal reasons such as Facebook, and Google
using a workstation computer [18]. Also, healthcare
facilities should establish strong backup which should be
tested to ensure that they are capable of restoring processes
and not depend on external support.
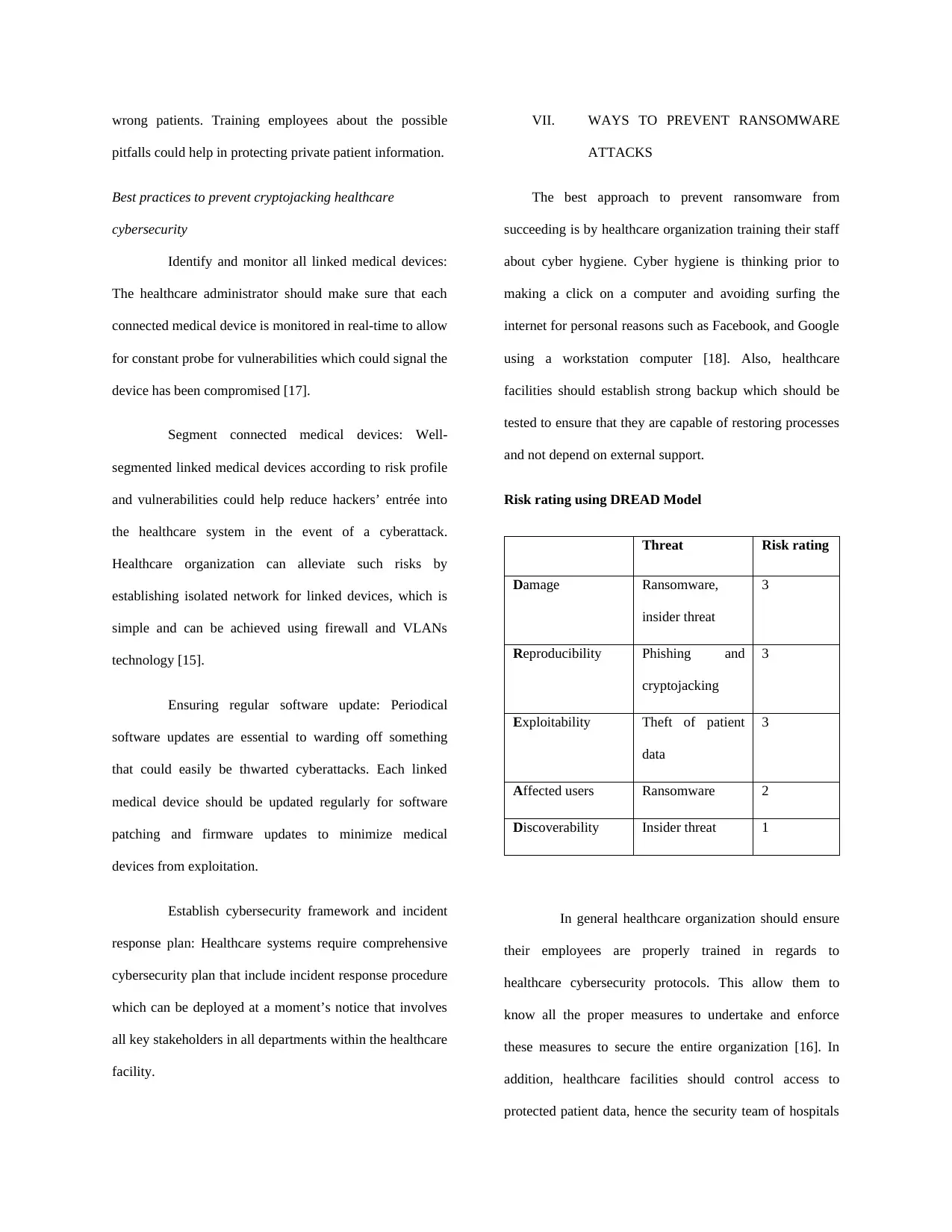
Risk rating using DREAD Model
Threat Risk rating
Damage Ransomware,
insider threat
3
Reproducibility Phishing and
cryptojacking
3
Exploitability Theft of patient
data
3
Affected users Ransomware 2
Discoverability Insider threat 1
In general healthcare organization should ensure
their employees are properly trained in regards to
healthcare cybersecurity protocols. This allow them to
know all the proper measures to undertake and enforce
these measures to secure the entire organization [16]. In
addition, healthcare facilities should control access to
protected patient data, hence the security team of hospitals
pitfalls could help in protecting private patient information.
Best practices to prevent cryptojacking healthcare
cybersecurity
Identify and monitor all linked medical devices:
The healthcare administrator should make sure that each
connected medical device is monitored in real-time to allow
for constant probe for vulnerabilities which could signal the
device has been compromised [17].
Segment connected medical devices: Well-
segmented linked medical devices according to risk profile
and vulnerabilities could help reduce hackers’ entrée into
the healthcare system in the event of a cyberattack.
Healthcare organization can alleviate such risks by
establishing isolated network for linked devices, which is
simple and can be achieved using firewall and VLANs
technology [15].
Ensuring regular software update: Periodical
software updates are essential to warding off something
that could easily be thwarted cyberattacks. Each linked
medical device should be updated regularly for software
patching and firmware updates to minimize medical
devices from exploitation.
Establish cybersecurity framework and incident
response plan: Healthcare systems require comprehensive
cybersecurity plan that include incident response procedure
which can be deployed at a moment’s notice that involves
all key stakeholders in all departments within the healthcare
facility.
VII. WAYS TO PREVENT RANSOMWARE
ATTACKS
The best approach to prevent ransomware from
succeeding is by healthcare organization training their staff
about cyber hygiene. Cyber hygiene is thinking prior to
making a click on a computer and avoiding surfing the
internet for personal reasons such as Facebook, and Google
using a workstation computer [18]. Also, healthcare
facilities should establish strong backup which should be
tested to ensure that they are capable of restoring processes
and not depend on external support.
Risk rating using DREAD Model
Threat Risk rating
Damage Ransomware,
insider threat
3
Reproducibility Phishing and
cryptojacking
3
Exploitability Theft of patient
data
3
Affected users Ransomware 2
Discoverability Insider threat 1
In general healthcare organization should ensure
their employees are properly trained in regards to
healthcare cybersecurity protocols. This allow them to
know all the proper measures to undertake and enforce
these measures to secure the entire organization [16]. In
addition, healthcare facilities should control access to
protected patient data, hence the security team of hospitals

should carefully regulate access to patient records by only
permitting authorized people to access these details through
auditing the system to verify identify of who access what
and at what time. Furthermore, employees whose
contracted has been terminated their access to the system
should be removed to avoid problems in their bid to
revenge.
VIII. CONCLUSION
In summery healthcare system is faced by numerous
security risks both from inside and external the
organization. Cybercriminals are targeting healthcare
organizations more than any other sector because
healthcare facilities contain highly confidential personal
information which is highly lucrative to them. Therefore,
healthcare should establish highly secure health
information technology systems and secure them through
firewalls and regular update to avoid falling victims of
cyberattacks. They should implement layered security
protocols so that even when an attacker break through one
layer they can still not manage to access the protect data.
Layered security protocols allow identification of the
attacker before it is too late.
REFERENCES
[1] Abomhara M. Cyber security and the internet of things:
vulnerabilities, threats, intruders and attacks. Journal of
Cyber Security and Mobility. 2015 Jan 31; 4(1):65-88.
[2] Al-Janabi S, Al-Shourbaji I, Shojafar M, Shamshirband
S. Survey of main challenges (security and privacy) in
wireless body area networks for healthcare applications.
Egyptian Informatics Journal. 2017 Jul 1; 18(2):113-22.
[3] Luna R, Rhine E, Myhra M, Sullivan R, Kruse CS.
Cyber threats to health information systems: A systematic
review. Technology and Health Care. 2016 Jan 1; 24(1):1-
9.
[4] Luo E, Bhuiyan MZ, Wang G, Rahman MA, Wu J,
Atiquzzaman M. Privacyprotector: Privacy-protected
patient data collection in IoT-based healthcare systems.
IEEE Communications Magazine. 2018 Feb 13; 56 (2):163-
8.
[5] Easttom C, Butler W. A Modified McCumber Cube as a
Basis for a Taxonomy of Cyber Attacks. In2019 IEEE 9th
Annual Computing and Communication Workshop and
Conference (CCWC) 2019 Jan 7 (pp. 0943-0949). IEEE.
[6] Razzaq MA, Gill SH, Qureshi MA, Ullah S. Security
issues in the Internet of Things (IoT): A comprehensive
study. International Journal of Advanced Computer Science
and Applications. 2017 Jun 1; 8 (6):383.
[7] Walker-Roberts S, Hammoudeh M, Dehghantanha A. A
systematic review of the availability and efficacy of
countermeasures to internal threats in healthcare critical
infrastructure. IEEE Access. 2018 Mar 20; 6:25167-77.
[8] Zhou W, Jia Y, Peng A, Zhang Y, Liu P. The effect of
iot new features on security and privacy: New threats,
existing solutions, and challenges yet to be solved. IEEE
Internet of Things Journal. 2018 Jun 15; 6(2):1606-16.
permitting authorized people to access these details through
auditing the system to verify identify of who access what
and at what time. Furthermore, employees whose
contracted has been terminated their access to the system
should be removed to avoid problems in their bid to
revenge.
VIII. CONCLUSION
In summery healthcare system is faced by numerous
security risks both from inside and external the
organization. Cybercriminals are targeting healthcare
organizations more than any other sector because
healthcare facilities contain highly confidential personal
information which is highly lucrative to them. Therefore,
healthcare should establish highly secure health
information technology systems and secure them through
firewalls and regular update to avoid falling victims of
cyberattacks. They should implement layered security
protocols so that even when an attacker break through one
layer they can still not manage to access the protect data.
Layered security protocols allow identification of the
attacker before it is too late.
REFERENCES
[1] Abomhara M. Cyber security and the internet of things:
vulnerabilities, threats, intruders and attacks. Journal of
Cyber Security and Mobility. 2015 Jan 31; 4(1):65-88.
[2] Al-Janabi S, Al-Shourbaji I, Shojafar M, Shamshirband
S. Survey of main challenges (security and privacy) in
wireless body area networks for healthcare applications.
Egyptian Informatics Journal. 2017 Jul 1; 18(2):113-22.
[3] Luna R, Rhine E, Myhra M, Sullivan R, Kruse CS.
Cyber threats to health information systems: A systematic
review. Technology and Health Care. 2016 Jan 1; 24(1):1-
9.
[4] Luo E, Bhuiyan MZ, Wang G, Rahman MA, Wu J,
Atiquzzaman M. Privacyprotector: Privacy-protected
patient data collection in IoT-based healthcare systems.
IEEE Communications Magazine. 2018 Feb 13; 56 (2):163-
8.
[5] Easttom C, Butler W. A Modified McCumber Cube as a
Basis for a Taxonomy of Cyber Attacks. In2019 IEEE 9th
Annual Computing and Communication Workshop and
Conference (CCWC) 2019 Jan 7 (pp. 0943-0949). IEEE.
[6] Razzaq MA, Gill SH, Qureshi MA, Ullah S. Security
issues in the Internet of Things (IoT): A comprehensive
study. International Journal of Advanced Computer Science
and Applications. 2017 Jun 1; 8 (6):383.
[7] Walker-Roberts S, Hammoudeh M, Dehghantanha A. A
systematic review of the availability and efficacy of
countermeasures to internal threats in healthcare critical
infrastructure. IEEE Access. 2018 Mar 20; 6:25167-77.
[8] Zhou W, Jia Y, Peng A, Zhang Y, Liu P. The effect of
iot new features on security and privacy: New threats,
existing solutions, and challenges yet to be solved. IEEE
Internet of Things Journal. 2018 Jun 15; 6(2):1606-16.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

[9] Guillén-Gámez FD, García-Magariño I, Bravo-Agapito
J, Lacuesta R, Lloret J. A proposal to improve the
authentication process in m-health environments. IEEE
Access. 2017 Sep 18; 5:22530-44.
[10] Meng W, Li W, Xiang Y, Choo KK. A bayesian
inference-based detection mechanism to defend medical
smartphone networks against insider attacks. Journal of
Network and Computer Applications. 2017 Jan 15;78:162-
9.
[11] Walker-Roberts S, Hammoudeh M, Dehghantanha A.
A systematic review of the availability and efficacy of
countermeasures to internal threats in healthcare critical
infrastructure. IEEE Access. 2018 Mar 20;6:25167-77.
[12] Hatwood C, Alexander S, Imsand E. Nurse
Researchers Move to the Cloud: Protecting Sensitive Data
in Cloud-Based Storage Environments. Clinical Nurse
Specialist. 2019 Jul 1;33(4):164-6.
[13] Krishnan R, Rainwater R, FitzGerald D, inventors;
Aetna Inc, assignee. Risk based medical identity theft
prevention. United States patent application US
15/651,577. 2018 Jan 18.
[14] Kennelty KA, Jensen LL, Gehring M, Gilmore-
Bykovskyi A, Roiland RA, Kordahl R, Kind AJ. Preventing
Opioid Prescription Theft and Ensuring SeCure Transfer of
Personal Health Information (PROTECT PHI) when
Patients Transition from the Hospital to a Nursing Home.
Journal of the American Geriatrics Society. 2016
Sep;64(9):e23.
[15] Le DN, Kumar R, Mishra BK, Chatterjee JM, Khari
M, editors. Cyber Security in Parallel and Distributed
Computing: Concepts, Techniques, Applications and Case
Studies. John Wiley & Sons; 2019 Mar 21.
[16]Butt UJ, Abbod M, Lors A, Jahankhani H, Jamal A,
Kumar A. Ransomware Threat and its Impact on SCADA.
In2019 IEEE 12th International Conference on Global
Security, Safety and Sustainability (ICGS3) 2019 Jan 16
(pp. 205-212). IEEE.
[17] Kethineni S, Cao Y. The Rise in Popularity of
Cryptocurrency and Associated Criminal Activity.
International Criminal Justice Review.
2019:1057567719827051.
[18] Valentino-DeVries J, Singer N, Keller MH, Krolik A.
Your apps know where you were last night, and they’re not
keeping it secret. New York Times. 2018 Dec 10;10.
J, Lacuesta R, Lloret J. A proposal to improve the
authentication process in m-health environments. IEEE
Access. 2017 Sep 18; 5:22530-44.
[10] Meng W, Li W, Xiang Y, Choo KK. A bayesian
inference-based detection mechanism to defend medical
smartphone networks against insider attacks. Journal of
Network and Computer Applications. 2017 Jan 15;78:162-
9.
[11] Walker-Roberts S, Hammoudeh M, Dehghantanha A.
A systematic review of the availability and efficacy of
countermeasures to internal threats in healthcare critical
infrastructure. IEEE Access. 2018 Mar 20;6:25167-77.
[12] Hatwood C, Alexander S, Imsand E. Nurse
Researchers Move to the Cloud: Protecting Sensitive Data
in Cloud-Based Storage Environments. Clinical Nurse
Specialist. 2019 Jul 1;33(4):164-6.
[13] Krishnan R, Rainwater R, FitzGerald D, inventors;
Aetna Inc, assignee. Risk based medical identity theft
prevention. United States patent application US
15/651,577. 2018 Jan 18.
[14] Kennelty KA, Jensen LL, Gehring M, Gilmore-
Bykovskyi A, Roiland RA, Kordahl R, Kind AJ. Preventing
Opioid Prescription Theft and Ensuring SeCure Transfer of
Personal Health Information (PROTECT PHI) when
Patients Transition from the Hospital to a Nursing Home.
Journal of the American Geriatrics Society. 2016
Sep;64(9):e23.
[15] Le DN, Kumar R, Mishra BK, Chatterjee JM, Khari
M, editors. Cyber Security in Parallel and Distributed
Computing: Concepts, Techniques, Applications and Case
Studies. John Wiley & Sons; 2019 Mar 21.
[16]Butt UJ, Abbod M, Lors A, Jahankhani H, Jamal A,
Kumar A. Ransomware Threat and its Impact on SCADA.
In2019 IEEE 12th International Conference on Global
Security, Safety and Sustainability (ICGS3) 2019 Jan 16
(pp. 205-212). IEEE.
[17] Kethineni S, Cao Y. The Rise in Popularity of
Cryptocurrency and Associated Criminal Activity.
International Criminal Justice Review.
2019:1057567719827051.
[18] Valentino-DeVries J, Singer N, Keller MH, Krolik A.
Your apps know where you were last night, and they’re not
keeping it secret. New York Times. 2018 Dec 10;10.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





