Security Policy in the Healthcare Industry: My Health Record Analysis
VerifiedAdded on 2022/11/13
|12
|2344
|232
Report
AI Summary
This report examines the security policy for the healthcare industry, specifically in the context of Australia's 'My Health Record' system. The report is divided into two parts: the first part outlines the planning, development, and management of a security policy, including steps like risk assessment, establishing a security culture, reviewing IT policies, employee education, and disaster recovery planning. The second part provides a description of the organization and IT systems, identifies potential risks such as poor planning, stakeholder refusal, financial and technical risks, and security gaps, discusses these risks, conducts a risk assessment, and presents a risk register. The report emphasizes the importance of security measures to protect sensitive patient data, mitigate risks, and improve the efficiency of healthcare systems. The analysis underscores the need for robust security measures to address potential threats and ensure the integrity and confidentiality of patient information within electronic health record systems.

Running head: HEALTHCARE INDUSTRY
Security policy in healthcare
Name of the Student
Name of the University
Author’s Note
Security policy in healthcare
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
HEALTHCARE INDUSTRY
Table of Contents
1.0 Introduction.....................................................................................................................2
2.0 Part one.................................................................................................................................2
2.0.1 Plan System Access Security Policy.............................................................................2
2.0.2 Develop System Access Security Policy.......................................................................3
2.0.3 Manage System Access Security Policy.......................................................................4
2.1 Part two................................................................................................................................4
2.1.1 Description of organization and IT systems..................................................................4
2.1.2 Identification of risks in IT systems..............................................................................4
2.1.3 Discussions of risks.......................................................................................................5
2.1.4 Risk assessment.............................................................................................................6
2.1.5 Risk register..................................................................................................................6
3.0 Conclusion............................................................................................................................8
References................................................................................................................................10
HEALTHCARE INDUSTRY
Table of Contents
1.0 Introduction.....................................................................................................................2
2.0 Part one.................................................................................................................................2
2.0.1 Plan System Access Security Policy.............................................................................2
2.0.2 Develop System Access Security Policy.......................................................................3
2.0.3 Manage System Access Security Policy.......................................................................4
2.1 Part two................................................................................................................................4
2.1.1 Description of organization and IT systems..................................................................4
2.1.2 Identification of risks in IT systems..............................................................................4
2.1.3 Discussions of risks.......................................................................................................5
2.1.4 Risk assessment.............................................................................................................6
2.1.5 Risk register..................................................................................................................6
3.0 Conclusion............................................................................................................................8
References................................................................................................................................10

2
HEALTHCARE INDUSTRY
1.0 Introduction
In Australia, the commonwealth Government has decided to develop an electronic
healthcare information system named “My Healthcare Record”. This record system contains
of patients’ information, as well as their health related doctor information as well as other
information on clinical systems (Adler-Milstein et al. 2015). This information system has
developed due to arise few problems. The Government of Australia has developed this
system to improve the better treatment quality as well as to reduce the issues which are
arising due to lack of maintenance of patients’ information (Ancker et al. 2015). This system
also helps to reduce the extra costs that are not manageable for the healthcare industry. This
paper follows that points which reflects on the development of security system on healthcare
industry. Also, this following represents about the risks that are arriving in the healthcare
industry due to development of electronic security system.
2.0 Part one
2.0.1 Plan System Access Security Policy
To establish the security system in healthcare industry, there must be required to
develop a plan before implementing the system (Austin et al. 2015). There are few step that
are required to develop a planning process for the development of security system in
healthcare industry. The steps are as follows:
Conduction of risk assessment:
Before the implementation of security system, it is required to develop a risk
assessment plan that determines the systems for requiring protection.
Establishment of security culture:
The security plans are needs to develop to protect the patients’ information
and improves the organization efficiency.
HEALTHCARE INDUSTRY
1.0 Introduction
In Australia, the commonwealth Government has decided to develop an electronic
healthcare information system named “My Healthcare Record”. This record system contains
of patients’ information, as well as their health related doctor information as well as other
information on clinical systems (Adler-Milstein et al. 2015). This information system has
developed due to arise few problems. The Government of Australia has developed this
system to improve the better treatment quality as well as to reduce the issues which are
arising due to lack of maintenance of patients’ information (Ancker et al. 2015). This system
also helps to reduce the extra costs that are not manageable for the healthcare industry. This
paper follows that points which reflects on the development of security system on healthcare
industry. Also, this following represents about the risks that are arriving in the healthcare
industry due to development of electronic security system.
2.0 Part one
2.0.1 Plan System Access Security Policy
To establish the security system in healthcare industry, there must be required to
develop a plan before implementing the system (Austin et al. 2015). There are few step that
are required to develop a planning process for the development of security system in
healthcare industry. The steps are as follows:
Conduction of risk assessment:
Before the implementation of security system, it is required to develop a risk
assessment plan that determines the systems for requiring protection.
Establishment of security culture:
The security plans are needs to develop to protect the patients’ information
and improves the organization efficiency.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
HEALTHCARE INDUSTRY
Reviewing IT policies:
To develop the security system, it is required to know properly about the IT
rules and regulations (Campanella et al. 2015). Because the IT policies helps
to protect the information as well as to control the individual’s information for
minimizing the risks to the electronic records.
Provide education to the employees about the security systems:
It is the important step for the employees to know properly the information of
the security systems (Chen et al. 2015). Because the security system is a
unique system that it needs to know how the system ids operated. Without
knowing the procedures of the system, the employee’s cannot handle the
system.
Inclusion of disaster recovery plan:
It is required to develop a disaster recovery plan for the implementation of the
security plan so that it can minimize the unscheduled downtime and recovers
the data.
2.0.2 Develop System Access Security Policy
The security system helps the healthcare industry to improve the efficiency of the
healthcare industry. It constitutes a system that must be accessed by the system administrator,
doctors as well as patients (De Moor et al. 2015). The overall procedures has occurred over
the internet. The system administrator accesses the information related to the patients. The
patients input their details in the system and access about the treatment procedure, the
availability of doctors and also the availability of medicines (Freire et al. 2016). The doctors
also can access the system so that they can understand what the affected diseases of the
patient and how these disease can overcome.
HEALTHCARE INDUSTRY
Reviewing IT policies:
To develop the security system, it is required to know properly about the IT
rules and regulations (Campanella et al. 2015). Because the IT policies helps
to protect the information as well as to control the individual’s information for
minimizing the risks to the electronic records.
Provide education to the employees about the security systems:
It is the important step for the employees to know properly the information of
the security systems (Chen et al. 2015). Because the security system is a
unique system that it needs to know how the system ids operated. Without
knowing the procedures of the system, the employee’s cannot handle the
system.
Inclusion of disaster recovery plan:
It is required to develop a disaster recovery plan for the implementation of the
security plan so that it can minimize the unscheduled downtime and recovers
the data.
2.0.2 Develop System Access Security Policy
The security system helps the healthcare industry to improve the efficiency of the
healthcare industry. It constitutes a system that must be accessed by the system administrator,
doctors as well as patients (De Moor et al. 2015). The overall procedures has occurred over
the internet. The system administrator accesses the information related to the patients. The
patients input their details in the system and access about the treatment procedure, the
availability of doctors and also the availability of medicines (Freire et al. 2016). The doctors
also can access the system so that they can understand what the affected diseases of the
patient and how these disease can overcome.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
HEALTHCARE INDUSTRY
2.0.3 Manage System Access Security Policy
The system security policy provides the security in healthcare industry. With the help
of this system, the security issues can be minimized very well. The information related to the
patient behave as a sensitive data in the healthcare industry (Gai et al. 2015). It has to secure
so that the created problems do not affect the patients’ health. By using this system, the data
are more secure and from the outside, nobody can accumulate this information. The overall
system is accessed by the system administrator. He can access all the information and
generate a database of patients’ information. It is easy for the doctors also, because they can
handle the information and provide the exact medication for the patients.
2.1 Part two
2.1.1 Description of organization and IT systems
With the development of the internet system, the healthcare industry improves their
efficiency than the previous stages (Kim et al. 2015). Due to use the internet system, it
provides the electronic healthcare record so that the data are kept in that system with a
security. The record contains various information related to the patients and also the
information related to the clinical systems. In the case study, the Government of Australia
wants to develop the online system named my health record which follows all the activities of
the electronic healthcare record. And also, he wants to develop a security system for
minimizing the issues. The security system provides security to all the data of my health
record database.
2.1.2 Identification of risks in IT systems
A security system is implemented in my health record which may causes several risk
factors. The following risks related to this health record are:
HEALTHCARE INDUSTRY
2.0.3 Manage System Access Security Policy
The system security policy provides the security in healthcare industry. With the help
of this system, the security issues can be minimized very well. The information related to the
patient behave as a sensitive data in the healthcare industry (Gai et al. 2015). It has to secure
so that the created problems do not affect the patients’ health. By using this system, the data
are more secure and from the outside, nobody can accumulate this information. The overall
system is accessed by the system administrator. He can access all the information and
generate a database of patients’ information. It is easy for the doctors also, because they can
handle the information and provide the exact medication for the patients.
2.1 Part two
2.1.1 Description of organization and IT systems
With the development of the internet system, the healthcare industry improves their
efficiency than the previous stages (Kim et al. 2015). Due to use the internet system, it
provides the electronic healthcare record so that the data are kept in that system with a
security. The record contains various information related to the patients and also the
information related to the clinical systems. In the case study, the Government of Australia
wants to develop the online system named my health record which follows all the activities of
the electronic healthcare record. And also, he wants to develop a security system for
minimizing the issues. The security system provides security to all the data of my health
record database.
2.1.2 Identification of risks in IT systems
A security system is implemented in my health record which may causes several risk
factors. The following risks related to this health record are:

5
HEALTHCARE INDUSTRY
(1) Poor planning for the implementation of EMR because in the health record there are a
lots of doctors and staffs are available in this system (Petrakaki, Klecun and Cornford
2016). All these may create a negative impact on this system.
(2) Refusal of the stakeholders about this system. Because, most of the time, they do not
understand properly about the healthcare record system.
(3) If all the activities of the healthcare record are not understood by the healthcare
authority, that results financial as well as technical risks may happen.
(4) This healthcare record system is too expensive and therefore it may enlist the risk
factors of the healthcare record system.
(5) Security as well as privacy gaps may occur the risk related to the personal information
of patients.
2.1.3 Discussions of risks
The risks are discussed as follows:
(1) Poor implementation planning of the healthcare record. The healthcare record consists
of clinical system information that means the information related to the number of
doctors as well as hospitals staffs. Therefore, all these factors may generate a negative
impact on the healthcare record system.
(2) It is required to understand properly about the activities of the healthcare record
systems. Most of the stakeholders have no idea about the electronic healthcare record
system so that it may cause another risk in the security systems.
(3) If all the activities and procedures are not understand properly, therefore it may cause
financial risks as well as technical risks.
(4) The implementation of this electronic healthcare system is too much expensive. For
that, it may cause the budget related problems.
HEALTHCARE INDUSTRY
(1) Poor planning for the implementation of EMR because in the health record there are a
lots of doctors and staffs are available in this system (Petrakaki, Klecun and Cornford
2016). All these may create a negative impact on this system.
(2) Refusal of the stakeholders about this system. Because, most of the time, they do not
understand properly about the healthcare record system.
(3) If all the activities of the healthcare record are not understood by the healthcare
authority, that results financial as well as technical risks may happen.
(4) This healthcare record system is too expensive and therefore it may enlist the risk
factors of the healthcare record system.
(5) Security as well as privacy gaps may occur the risk related to the personal information
of patients.
2.1.3 Discussions of risks
The risks are discussed as follows:
(1) Poor implementation planning of the healthcare record. The healthcare record consists
of clinical system information that means the information related to the number of
doctors as well as hospitals staffs. Therefore, all these factors may generate a negative
impact on the healthcare record system.
(2) It is required to understand properly about the activities of the healthcare record
systems. Most of the stakeholders have no idea about the electronic healthcare record
system so that it may cause another risk in the security systems.
(3) If all the activities and procedures are not understand properly, therefore it may cause
financial risks as well as technical risks.
(4) The implementation of this electronic healthcare system is too much expensive. For
that, it may cause the budget related problems.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
HEALTHCARE INDUSTRY
(5) Security as well as privacy gaps are most important to generate the risks about the
stolen of information related to the patients.
2.1.4 Risk assessment
The following risks can be removed if the electronic healthcare record follows such
policies.
(1) The planning process is implemented properly. Because for the small range of
patients, it is not required to provide the large range of doctors. But in the serious
cases, it must provide the large amount of doctors. So, in this case, proper
implementation of planning is necessary.
(2) It is required for all the stakeholders related to the healthcare industry to know all the
activities of the electronic healthcare record systems.
(3) It is required to know all the procedures as well as steps related to the electronic
healthcare record so that it can minimize the financial and technical issues.
2.1.5 Risk register
The following risk register is necessary to understand the risks properly.
Risk Id Risk Name Risk
Description
Occurrence
chances
Impact Mitigation
plan
1 Poor
implementatio
n of planning
The large
range of
doctors,
staffs as well
as patients
can create a
negative
High Medium Proper
development of
the planning
process
HEALTHCARE INDUSTRY
(5) Security as well as privacy gaps are most important to generate the risks about the
stolen of information related to the patients.
2.1.4 Risk assessment
The following risks can be removed if the electronic healthcare record follows such
policies.
(1) The planning process is implemented properly. Because for the small range of
patients, it is not required to provide the large range of doctors. But in the serious
cases, it must provide the large amount of doctors. So, in this case, proper
implementation of planning is necessary.
(2) It is required for all the stakeholders related to the healthcare industry to know all the
activities of the electronic healthcare record systems.
(3) It is required to know all the procedures as well as steps related to the electronic
healthcare record so that it can minimize the financial and technical issues.
2.1.5 Risk register
The following risk register is necessary to understand the risks properly.
Risk Id Risk Name Risk
Description
Occurrence
chances
Impact Mitigation
plan
1 Poor
implementatio
n of planning
The large
range of
doctors,
staffs as well
as patients
can create a
negative
High Medium Proper
development of
the planning
process
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
HEALTHCARE INDUSTRY
impact in
this system
2 Refusal of
stakeholders
The
stakeholders
have no
sufficient
knowledge
of the
electronic
healthcare
record
system
Medium Low Provide proper
knowledge of
this system to
the
stakeholders
3 Financial and
Technical risk
Due to non-
sufficient
knowledge
of this
system may
cause these
risks
Medium High Keep exact
information
related to the
performance
activities of the
electronic
healthcare
systems
4 Budget related
risk
Because of
the expenses
of the
electronic
healthcare
High High Estimate the
proper budget
at the initial
time of
implementation
HEALTHCARE INDUSTRY
impact in
this system
2 Refusal of
stakeholders
The
stakeholders
have no
sufficient
knowledge
of the
electronic
healthcare
record
system
Medium Low Provide proper
knowledge of
this system to
the
stakeholders
3 Financial and
Technical risk
Due to non-
sufficient
knowledge
of this
system may
cause these
risks
Medium High Keep exact
information
related to the
performance
activities of the
electronic
healthcare
systems
4 Budget related
risk
Because of
the expenses
of the
electronic
healthcare
High High Estimate the
proper budget
at the initial
time of
implementation
8
HEALTHCARE INDUSTRY
system of this system
5 Security issues Security
gaps may
occur the
stolen case
of the
patients
related
sensitive
information
Very High Very High Proper
implementation
of security
firewall.
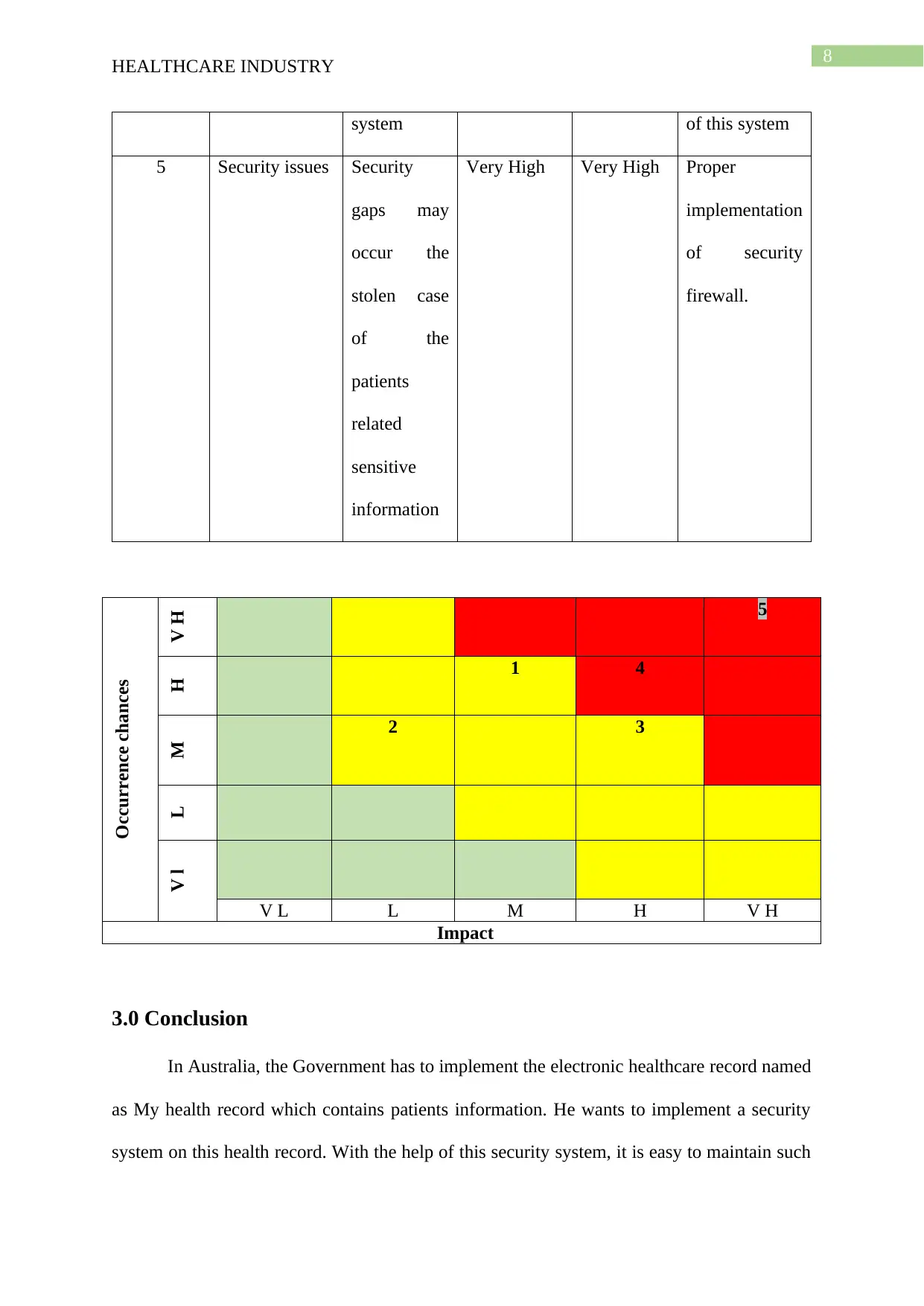
Occurrence chances
V H 5
H 1 4
M 2 3
LV l
V L L M H V H
Impact
3.0 Conclusion
In Australia, the Government has to implement the electronic healthcare record named
as My health record which contains patients information. He wants to implement a security
system on this health record. With the help of this security system, it is easy to maintain such
HEALTHCARE INDUSTRY
system of this system
5 Security issues Security
gaps may
occur the
stolen case
of the
patients
related
sensitive
information
Very High Very High Proper
implementation
of security
firewall.
Occurrence chances
V H 5
H 1 4
M 2 3
LV l
V L L M H V H
Impact
3.0 Conclusion
In Australia, the Government has to implement the electronic healthcare record named
as My health record which contains patients information. He wants to implement a security
system on this health record. With the help of this security system, it is easy to maintain such
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
HEALTHCARE INDUSTRY
security issues related to the healthcare industry. However, with the addition of the security
system, there may occur various kinds of risks associated with the healthcare industry. The
risks are defined as technical risk, financial risk, stakeholders related risks etc. But these risk
are maintained if the industry follow such rules and regulations. In this way, the security
policy is implemented in the healthcare industry.
HEALTHCARE INDUSTRY
security issues related to the healthcare industry. However, with the addition of the security
system, there may occur various kinds of risks associated with the healthcare industry. The
risks are defined as technical risk, financial risk, stakeholders related risks etc. But these risk
are maintained if the industry follow such rules and regulations. In this way, the security
policy is implemented in the healthcare industry.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
HEALTHCARE INDUSTRY
References
Adler-Milstein, J., DesRoches, C.M., Kralovec, P., Foster, G., Worzala, C., Charles, D.,
Searcy, T. and Jha, A.K., 2015. Electronic health record adoption in US hospitals: progress
continues, but challenges persist. Health affairs, 34(12), pp.2174-2180.
Ancker, J.S., Kern, L.M., Edwards, A., Nosal, S., Stein, D.M., Hauser, D., Kaushal, R. and
with the HITEC Investigators, 2015. Associations between healthcare quality and use of
electronic health record functions in ambulatory care. Journal of the American Medical
Informatics Association, 22(4), pp.864-871.
Austin, T., Sun, S., Lim, Y.S., Nguyen, D., Lea, N., Tapuria, A. and Kalra, D., 2015. An
electronic healthcare record server implemented in PostgreSQL. Journal of healthcare
engineering, 6(3), pp.325-344.
Campanella, P., Lovato, E., Marone, C., Fallacara, L., Mancuso, A., Ricciardi, W. and
Specchia, M.L., 2015. The impact of electronic health records on healthcare quality: a
systematic review and meta-analysis. The European Journal of Public Health, 26(1), pp.60-
64.
Chen, Y., Ghosh, J., Bejan, C.A., Gunter, C.A., Gupta, S., Kho, A., Liebovitz, D., Sun, J.,
Denny, J. and Malin, B., 2015. Building bridges across electronic health record systems
through inferred phenotypic topics. Journal of biomedical informatics, 55, pp.82-93.
De Moor, G., Sundgren, M., Kalra, D., Schmidt, A., Dugas, M., Claerhout, B., Karakoyun,
T., Ohmann, C., Lastic, P.Y., Ammour, N. and Kush, R., 2015. Using electronic health
records for clinical research: the case of the EHR4CR project. Journal of biomedical
informatics, 53, pp.162-173.
HEALTHCARE INDUSTRY
References
Adler-Milstein, J., DesRoches, C.M., Kralovec, P., Foster, G., Worzala, C., Charles, D.,
Searcy, T. and Jha, A.K., 2015. Electronic health record adoption in US hospitals: progress
continues, but challenges persist. Health affairs, 34(12), pp.2174-2180.
Ancker, J.S., Kern, L.M., Edwards, A., Nosal, S., Stein, D.M., Hauser, D., Kaushal, R. and
with the HITEC Investigators, 2015. Associations between healthcare quality and use of
electronic health record functions in ambulatory care. Journal of the American Medical
Informatics Association, 22(4), pp.864-871.
Austin, T., Sun, S., Lim, Y.S., Nguyen, D., Lea, N., Tapuria, A. and Kalra, D., 2015. An
electronic healthcare record server implemented in PostgreSQL. Journal of healthcare
engineering, 6(3), pp.325-344.
Campanella, P., Lovato, E., Marone, C., Fallacara, L., Mancuso, A., Ricciardi, W. and
Specchia, M.L., 2015. The impact of electronic health records on healthcare quality: a
systematic review and meta-analysis. The European Journal of Public Health, 26(1), pp.60-
64.
Chen, Y., Ghosh, J., Bejan, C.A., Gunter, C.A., Gupta, S., Kho, A., Liebovitz, D., Sun, J.,
Denny, J. and Malin, B., 2015. Building bridges across electronic health record systems
through inferred phenotypic topics. Journal of biomedical informatics, 55, pp.82-93.
De Moor, G., Sundgren, M., Kalra, D., Schmidt, A., Dugas, M., Claerhout, B., Karakoyun,
T., Ohmann, C., Lastic, P.Y., Ammour, N. and Kush, R., 2015. Using electronic health
records for clinical research: the case of the EHR4CR project. Journal of biomedical
informatics, 53, pp.162-173.

11
HEALTHCARE INDUSTRY
Freire, S.M., Teodoro, D., Wei-Kleiner, F., Sundvall, E., Karlsson, D. and Lambrix, P., 2016.
Comparing the performance of NoSQL approaches for managing archetype-based electronic
health record data. PloS one, 11(3), p.e0150069.
Gai, K., Qiu, M., Chen, L.C. and Liu, M., 2015, August. Electronic health record error
prevention approach using ontology in big data. In 2015 IEEE 17th International Conference
on High Performance Computing and Communications, 2015 IEEE 7th International
Symposium on Cyberspace Safety and Security, and 2015 IEEE 12th International
Conference on Embedded Software and Systems (pp. 752-757). IEEE.
Kim, S., Lee, K.H., Hwang, H. and Yoo, S., 2015. Analysis of the factors influencing
healthcare professionals’ adoption of mobile electronic medical record (EMR) using the
unified theory of acceptance and use of technology (UTAUT) in a tertiary hospital. BMC
medical informatics and decision making, 16(1), p.12.
Petrakaki, D., Klecun, E. and Cornford, T., 2016. Changes in healthcare professional work
afforded by technology: The introduction of a national electronic patient record in an English
hospital. Organization, 23(2), pp.206-226.
HEALTHCARE INDUSTRY
Freire, S.M., Teodoro, D., Wei-Kleiner, F., Sundvall, E., Karlsson, D. and Lambrix, P., 2016.
Comparing the performance of NoSQL approaches for managing archetype-based electronic
health record data. PloS one, 11(3), p.e0150069.
Gai, K., Qiu, M., Chen, L.C. and Liu, M., 2015, August. Electronic health record error
prevention approach using ontology in big data. In 2015 IEEE 17th International Conference
on High Performance Computing and Communications, 2015 IEEE 7th International
Symposium on Cyberspace Safety and Security, and 2015 IEEE 12th International
Conference on Embedded Software and Systems (pp. 752-757). IEEE.
Kim, S., Lee, K.H., Hwang, H. and Yoo, S., 2015. Analysis of the factors influencing
healthcare professionals’ adoption of mobile electronic medical record (EMR) using the
unified theory of acceptance and use of technology (UTAUT) in a tertiary hospital. BMC
medical informatics and decision making, 16(1), p.12.
Petrakaki, D., Klecun, E. and Cornford, T., 2016. Changes in healthcare professional work
afforded by technology: The introduction of a national electronic patient record in an English
hospital. Organization, 23(2), pp.206-226.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





