Assessment Item 2 Report: Healthcare System Security Policies
VerifiedAdded on 2022/11/25
|13
|3040
|271
Report
AI Summary
This report addresses the development and management of a security policy for the "My Health Record" system in the Australian healthcare context, focusing on protecting sensitive patient information. It outlines policies and procedures for system administrators, doctors, and nurses, detailing their roles, privileges, and responsibilities. The report then conducts a risk assessment, identifying potential threats to Netflix's information system, including reliance on cloud services and potential vulnerabilities. It analyzes the consequences of these risks, such as data breaches and reputational damage, and proposes mitigation strategies to enhance system security. The document emphasizes the importance of robust security policies, regular risk assessments, and proactive measures to safeguard sensitive data and maintain system integrity. The report is structured in two parts, the first part focuses on planning, developing and managing security policy and the second part focuses on risk assessment.

Running head: ASSESSMENT ITEM 2 1
Assessment Item 2
Student
Tutor
Institutional Affiliations
Date
Assessment Item 2
Student
Tutor
Institutional Affiliations
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ASSESSMENT ITEM 2 2
Table of Contents
Table of Contents........................................................................................................................................2
Part 1: Plan, Develop and manage security policy.......................................................................................3
Introduction.................................................................................................................................................3
The System Access Security Policy Plan..............................................................................................3
System access security policies..............................................................................................................4
System administrator........................................................................................................................5
Doctors................................................................................................................................................6
Nurses.................................................................................................................................................7
Managing a system security policy.......................................................................................................8
Part 2: Risk assessment.............................................................................................................................8
The risks in Netflix’s system.....................................................................................................................8
Consequences of the risks.....................................................................................................................9
Mitigation strategies............................................................................................................................10
Risk register.........................................................................................................................................10
Conclusion................................................................................................................................................10
Table of Contents
Table of Contents........................................................................................................................................2
Part 1: Plan, Develop and manage security policy.......................................................................................3
Introduction.................................................................................................................................................3
The System Access Security Policy Plan..............................................................................................3
System access security policies..............................................................................................................4
System administrator........................................................................................................................5
Doctors................................................................................................................................................6
Nurses.................................................................................................................................................7
Managing a system security policy.......................................................................................................8
Part 2: Risk assessment.............................................................................................................................8
The risks in Netflix’s system.....................................................................................................................8
Consequences of the risks.....................................................................................................................9
Mitigation strategies............................................................................................................................10
Risk register.........................................................................................................................................10
Conclusion................................................................................................................................................10

ASSESSMENT ITEM 2 3
Part 1: Plan, Develop and manage security policy
Introduction
For healthcare organizations, information is a critical asset that demands a maximum
protection from unauthorized access. As a result, it is imperative that pertinent policies and
procedures are developed to guide how healthcare organization personnel access, use and
manage information. While there is an assumption that healthcare facilities may not necessarily
need a set of information governance policies like other organizations, the plan by the
Commonwealth Government of Australia to launch the “My Health Records” a secure online
summary of an individual’s health records requires them to do so. The “My Health Records” will
carry sensitive information that requires to be safeguarded from unauthorized access. In this
rationale, this document seek to develop a system access security policies that would govern the
access to the “My Health Records.”
The System Access Security Policy Plan
In this system security plan, we present an overview of the system access security
requirements for the “My Health Records” and it describes the policies planned to offer the level
of security that is required for the information to be secured from unauthorized access.
In the information security policy, we will focus on three personnel including the system
administrator, doctors and nurses. All of the personnel will have their status which will be
categorized with the level of sensitivity. The users’ privileges after authentication is shown in the
following table.
Part 1: Plan, Develop and manage security policy
Introduction
For healthcare organizations, information is a critical asset that demands a maximum
protection from unauthorized access. As a result, it is imperative that pertinent policies and
procedures are developed to guide how healthcare organization personnel access, use and
manage information. While there is an assumption that healthcare facilities may not necessarily
need a set of information governance policies like other organizations, the plan by the
Commonwealth Government of Australia to launch the “My Health Records” a secure online
summary of an individual’s health records requires them to do so. The “My Health Records” will
carry sensitive information that requires to be safeguarded from unauthorized access. In this
rationale, this document seek to develop a system access security policies that would govern the
access to the “My Health Records.”
The System Access Security Policy Plan
In this system security plan, we present an overview of the system access security
requirements for the “My Health Records” and it describes the policies planned to offer the level
of security that is required for the information to be secured from unauthorized access.
In the information security policy, we will focus on three personnel including the system
administrator, doctors and nurses. All of the personnel will have their status which will be
categorized with the level of sensitivity. The users’ privileges after authentication is shown in the
following table.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
ASSESSMENT ITEM 2 4
Roles Privileges Level of sensitivity Duties
System administrator Full administrative
access
Moderate Will install, configure
and monitor software
Will get reports and
add patient data.
Will perform system
updates and file
backups.
Doctor Perform
administration
Limited Enter prescription
data through system
admin.
Monitor patient data.
Nurse Limited access Limited Acquire and monitor
patient records.
Monitor patient data
Table 1: Users privileges after authentication
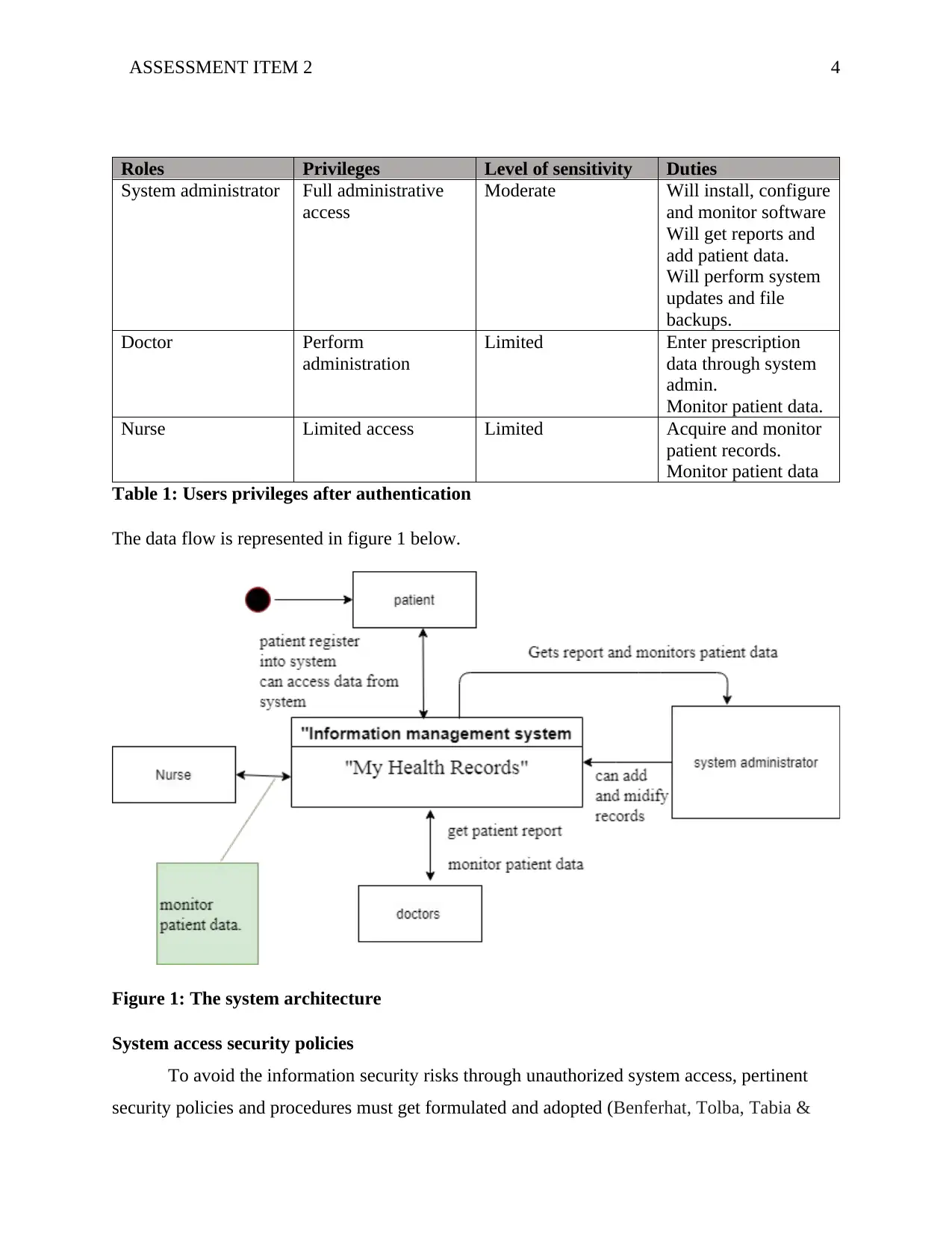
The data flow is represented in figure 1 below.
Figure 1: The system architecture
System access security policies
To avoid the information security risks through unauthorized system access, pertinent
security policies and procedures must get formulated and adopted (Benferhat, Tolba, Tabia &
Roles Privileges Level of sensitivity Duties
System administrator Full administrative
access
Moderate Will install, configure
and monitor software
Will get reports and
add patient data.
Will perform system
updates and file
backups.
Doctor Perform
administration
Limited Enter prescription
data through system
admin.
Monitor patient data.
Nurse Limited access Limited Acquire and monitor
patient records.
Monitor patient data
Table 1: Users privileges after authentication
The data flow is represented in figure 1 below.
Figure 1: The system architecture
System access security policies
To avoid the information security risks through unauthorized system access, pertinent
security policies and procedures must get formulated and adopted (Benferhat, Tolba, Tabia &
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ASSESSMENT ITEM 2 5
Belkhir, 2016). Healthcare organizations are required to safeguard and guarantee availability,
integrity as well as the confidentiality to patients’ data. As such, we will formulate security
controls to ensure the maximum security to the organizations system. The security controls will
only govern the three users including the system administrator, the doctor and nurse.
System administrator
The system administrators refer to the health organization personnel who are granted with
full administrative access to the system. Below show the policies, procedures and managerial for
the system administrators.
Purpose
This policy have a purpose to establish the Commonwealth Government of Australia
along with the healthcare organizations’ expectation for the healthcare organization’s employees
who have a full administrative access rights to “My Health Records” information system of
patients.
Policy
Objective: to ensure that the healthcare organization systems has satisfactory controls for
restricting the administrative access to “My Health Records.”
1.1. System administrators’ accounts shall only be requested by supervisors and managers of
the organization and must be approved on basis of the underlying regulations.
1.2. The system administrator shall have a nominative and individual privileged account
rather than generic administrative accounts.
1.3. All data in the “My Health Records” shall be the properties of the healthcare
organization.
1.4. The system administrators granted with privileges to access, monitor, and update data in
“My Health Records” are responsible for their actions while using these privileges.
Procedures
i. The managers order for an administrator account to be created.
ii. Administrator is then privileged to get reports and monitor the system data.
iii. Administrator directly insert and modify data into “My Health Records” under the
instructions from relevant personnel.
Belkhir, 2016). Healthcare organizations are required to safeguard and guarantee availability,
integrity as well as the confidentiality to patients’ data. As such, we will formulate security
controls to ensure the maximum security to the organizations system. The security controls will
only govern the three users including the system administrator, the doctor and nurse.
System administrator
The system administrators refer to the health organization personnel who are granted with
full administrative access to the system. Below show the policies, procedures and managerial for
the system administrators.
Purpose
This policy have a purpose to establish the Commonwealth Government of Australia
along with the healthcare organizations’ expectation for the healthcare organization’s employees
who have a full administrative access rights to “My Health Records” information system of
patients.
Policy
Objective: to ensure that the healthcare organization systems has satisfactory controls for
restricting the administrative access to “My Health Records.”
1.1. System administrators’ accounts shall only be requested by supervisors and managers of
the organization and must be approved on basis of the underlying regulations.
1.2. The system administrator shall have a nominative and individual privileged account
rather than generic administrative accounts.
1.3. All data in the “My Health Records” shall be the properties of the healthcare
organization.
1.4. The system administrators granted with privileges to access, monitor, and update data in
“My Health Records” are responsible for their actions while using these privileges.
Procedures
i. The managers order for an administrator account to be created.
ii. Administrator is then privileged to get reports and monitor the system data.
iii. Administrator directly insert and modify data into “My Health Records” under the
instructions from relevant personnel.

ASSESSMENT ITEM 2 6
iv. Administrator updates the system and ensure that all applications required for the system
to function are installed.
Managerial
i. Manages all user accounts.
ii. Add or remove a user account.
iii. Monitors the system performance.
iv. Resolves issues with passwords and usernames.
Doctors
The doctors are the employees of the healthcare organization. These personnel are
granted with user accounts where they can monitor patient data from the “My Health Records”
database. The following policies will control their access to the system.
Purpose
The policy have a purpose to establish the expectations of the Commonwealth
Government of Australia along with the healthcare organizations’ expectation for the healthcare
users including doctors of the organization. The policy is also purposed to serve as a resource
especially for new doctors.
Policy
Objective: to ensure that the system is accessed in a proper manner and users’ managed with
professionalism and ethics.
1.5. The user account for doctors shall be opened by the administrator upon order from
managers.
1.6. Any remote access to the system by doctors shall be two-factor authentication.
1.7. Any doctor provided with access to the “My Health Records” data shall be responsible
for the ethical use of the information.
1.8. The doctors granted with privileges to access and monitor data in “My Health Records”
are responsible for their actions while using these privileges.
Procedures
i. The administrator create an account for the doctors.
ii. The doctors monitor the patient data.
iv. Administrator updates the system and ensure that all applications required for the system
to function are installed.
Managerial
i. Manages all user accounts.
ii. Add or remove a user account.
iii. Monitors the system performance.
iv. Resolves issues with passwords and usernames.
Doctors
The doctors are the employees of the healthcare organization. These personnel are
granted with user accounts where they can monitor patient data from the “My Health Records”
database. The following policies will control their access to the system.
Purpose
The policy have a purpose to establish the expectations of the Commonwealth
Government of Australia along with the healthcare organizations’ expectation for the healthcare
users including doctors of the organization. The policy is also purposed to serve as a resource
especially for new doctors.
Policy
Objective: to ensure that the system is accessed in a proper manner and users’ managed with
professionalism and ethics.
1.5. The user account for doctors shall be opened by the administrator upon order from
managers.
1.6. Any remote access to the system by doctors shall be two-factor authentication.
1.7. Any doctor provided with access to the “My Health Records” data shall be responsible
for the ethical use of the information.
1.8. The doctors granted with privileges to access and monitor data in “My Health Records”
are responsible for their actions while using these privileges.
Procedures
i. The administrator create an account for the doctors.
ii. The doctors monitor the patient data.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

ASSESSMENT ITEM 2 7
iii. They acquire patient reports.
iv. Add patient data to my “Health Records.”
Managerial
i. Monitor patient data
ii. Examine patient reports
iii. Provide prescriptions
Nurses
Nurses are also employees in healthcare organizations who provide care to patients in the
health facility. They work with doctors to ensure that patients are well and healthy. The nurses
are also granted access to system by the system administrators to ensure they conduct their duties
perfectly. The following show the policies for the nurses that guide their operation with the
system.
Purpose
The purpose of the policy is for the information system to be used as required and to
safeguard the information system from any access that is not authorized.
Policy
Objective: To ensure that the system is free from unauthorized access.
1.7. The nurses’ account shall be opened by the administrator under the manager’s
instructions.
1.8. Any remote access to the system by nurses shall be two-factor authentication.
1.9. The nurses granted with privileges to access and monitor data in “My Health
Records” are responsible for their actions while using these privileges.
Procedure
i. Administrator create a user account for nurses
ii. Record patient records into the system.
iii. Monitor the patient records.
Managerial
i. Receive patients
iii. They acquire patient reports.
iv. Add patient data to my “Health Records.”
Managerial
i. Monitor patient data
ii. Examine patient reports
iii. Provide prescriptions
Nurses
Nurses are also employees in healthcare organizations who provide care to patients in the
health facility. They work with doctors to ensure that patients are well and healthy. The nurses
are also granted access to system by the system administrators to ensure they conduct their duties
perfectly. The following show the policies for the nurses that guide their operation with the
system.
Purpose
The purpose of the policy is for the information system to be used as required and to
safeguard the information system from any access that is not authorized.
Policy
Objective: To ensure that the system is free from unauthorized access.
1.7. The nurses’ account shall be opened by the administrator under the manager’s
instructions.
1.8. Any remote access to the system by nurses shall be two-factor authentication.
1.9. The nurses granted with privileges to access and monitor data in “My Health
Records” are responsible for their actions while using these privileges.
Procedure
i. Administrator create a user account for nurses
ii. Record patient records into the system.
iii. Monitor the patient records.
Managerial
i. Receive patients
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ASSESSMENT ITEM 2 8
ii. Record patient’s medical duties into the system
iii. Monitor the health records of patients
Managing a system security policy
As mentioned in the previous sections, the main purpose of the policies is to ensure the
system is used in a proper manner and safeguarded from unauthorized access. However, this
cannot be achieved until a proper system security management is implemented (Peltier, 2016;
Vittor, Sukumara, Sudarsan & Starck, 2017). In this effect, this section outlines how the policies
formulated in the preceding sections will be applied to ensure a robust system.
In order to ensure compliance, the management shall ensure that not any single policy is
violated by any organization personnel. Any individual found in violation of the policies shall be
a subjected to the disciplinary action which might lead to penalties or firing or even prosecution
as defined by the organization’s underlying policies.
The policy exceptions, if any, shall be corrected; the policies shall be reviewed regularly
to ensure that the policy is monitored and enforce compliance (Chen, Oshiba & Chiong, 2016).
Additionally, the policy shall be amended to ensure that it is always relevant.
Part 2: Risk assessment
A risk assessment is also an important aspect when it comes to ensuring a robust security
of an information system of an organization. It is essential to make sure that a system is free
from any risk that may result in any form of security breach (Senft, Gallegos & Davis, 2016). As
such, an organization’s IT personnel must perform a regular risk assessment and fix identified
threats if any to boost the system security. For the purpose of this paper, we seek to conduct a
risk assessment on Netflix organization’s information system.
The risks in Netflix’s system
Netflix is one of the most successful organizations providing online movie services based
in the United States. They also offer cloud based services. The organization have been gaining a
rapid expansion on the amount of the titles it produce making it the most famous online show
provider around the globe. As such, the organization has gained a considerable number of
subscribers from all over the world. With this population, it goes without saying that Netflix is a
potential hot spot of security threats.
ii. Record patient’s medical duties into the system
iii. Monitor the health records of patients
Managing a system security policy
As mentioned in the previous sections, the main purpose of the policies is to ensure the
system is used in a proper manner and safeguarded from unauthorized access. However, this
cannot be achieved until a proper system security management is implemented (Peltier, 2016;
Vittor, Sukumara, Sudarsan & Starck, 2017). In this effect, this section outlines how the policies
formulated in the preceding sections will be applied to ensure a robust system.
In order to ensure compliance, the management shall ensure that not any single policy is
violated by any organization personnel. Any individual found in violation of the policies shall be
a subjected to the disciplinary action which might lead to penalties or firing or even prosecution
as defined by the organization’s underlying policies.
The policy exceptions, if any, shall be corrected; the policies shall be reviewed regularly
to ensure that the policy is monitored and enforce compliance (Chen, Oshiba & Chiong, 2016).
Additionally, the policy shall be amended to ensure that it is always relevant.
Part 2: Risk assessment
A risk assessment is also an important aspect when it comes to ensuring a robust security
of an information system of an organization. It is essential to make sure that a system is free
from any risk that may result in any form of security breach (Senft, Gallegos & Davis, 2016). As
such, an organization’s IT personnel must perform a regular risk assessment and fix identified
threats if any to boost the system security. For the purpose of this paper, we seek to conduct a
risk assessment on Netflix organization’s information system.
The risks in Netflix’s system
Netflix is one of the most successful organizations providing online movie services based
in the United States. They also offer cloud based services. The organization have been gaining a
rapid expansion on the amount of the titles it produce making it the most famous online show
provider around the globe. As such, the organization has gained a considerable number of
subscribers from all over the world. With this population, it goes without saying that Netflix is a
potential hot spot of security threats.

ASSESSMENT ITEM 2 9
Additionally, the organization has committed itself to supplying movies to its clients. For
this to be achieved by Netflix, the organization almost exclusively rely on cloud based services
from cloud vendors which is a potential threat. This is in the sense that statistics show that
companies who have always relied on cloud have at least experienced an attack and the same
could happen to Netflix too being that it hold a population of subscribers that hackers would lust
for.
Moreover, the organization has implemented some of the world’s best security
management software. This is also attributed to the fact that Netflix rely on big releases and
hence it has to protect the originality which is the key driver of its revenue model. But the
organization provide less effort to information security management policies, this could be
another risk that would be exploited by cyber criminals. This is even exemplified by the theft
that occurred in its Larson Studio in the year 2017. An American media company, New York
Times (2017) reportedly learned about the theft experienced in the Larson Studio. It comes after
the organization have received several warning about vulnerabilities involving third party
vendors. Additionally, the email phishing attack that compromised over 110 million subscribers
in 2017 could also signify that the Netflix system is not robust enough (Sebayan, 2017). This
could be another major risk to the organization’s system.
Consequences of the risks
The risks identified in the organization’s system may have various consequences to the
organization. First off, over-relying on cloud based vendors for a business organization like
Netflix could lead to an attack which may consequently result in loss of sensitive data (Ye,
Wandong & Nan, 2016). Nobody will not trust the organization with his sensitive information
thus ruining the Netflix business. Additionally, the lack of robust security management policies
could greatly compromise Netflix. This is attributed to the fact that human beings are the
weakest link in cyber security, as such without well-articulated policies to govern them the
information system is likely to be compromised with would consequently lead to privacy breach
which consequently compromise the organization’s reputation (Faerber et al. 2015). In addition
to this, the evident weak information system may lead to attacks like ransomeware which would
eventually lock the organization out of its system which would considerably cost the
organization financially.
Additionally, the organization has committed itself to supplying movies to its clients. For
this to be achieved by Netflix, the organization almost exclusively rely on cloud based services
from cloud vendors which is a potential threat. This is in the sense that statistics show that
companies who have always relied on cloud have at least experienced an attack and the same
could happen to Netflix too being that it hold a population of subscribers that hackers would lust
for.
Moreover, the organization has implemented some of the world’s best security
management software. This is also attributed to the fact that Netflix rely on big releases and
hence it has to protect the originality which is the key driver of its revenue model. But the
organization provide less effort to information security management policies, this could be
another risk that would be exploited by cyber criminals. This is even exemplified by the theft
that occurred in its Larson Studio in the year 2017. An American media company, New York
Times (2017) reportedly learned about the theft experienced in the Larson Studio. It comes after
the organization have received several warning about vulnerabilities involving third party
vendors. Additionally, the email phishing attack that compromised over 110 million subscribers
in 2017 could also signify that the Netflix system is not robust enough (Sebayan, 2017). This
could be another major risk to the organization’s system.
Consequences of the risks
The risks identified in the organization’s system may have various consequences to the
organization. First off, over-relying on cloud based vendors for a business organization like
Netflix could lead to an attack which may consequently result in loss of sensitive data (Ye,
Wandong & Nan, 2016). Nobody will not trust the organization with his sensitive information
thus ruining the Netflix business. Additionally, the lack of robust security management policies
could greatly compromise Netflix. This is attributed to the fact that human beings are the
weakest link in cyber security, as such without well-articulated policies to govern them the
information system is likely to be compromised with would consequently lead to privacy breach
which consequently compromise the organization’s reputation (Faerber et al. 2015). In addition
to this, the evident weak information system may lead to attacks like ransomeware which would
eventually lock the organization out of its system which would considerably cost the
organization financially.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
ASSESSMENT ITEM 2 10
Inherent risk assessment
In the inherent risk assessment, Netflix organization is an online based corporate. This
means that the company rely on internet for its business. Being that it operates online, it is
automatic that the organization’s system would be a subject to security and privacy breach. This
is also supported by the fact that almost every organizations operating online have at least
experienced cybercrime, google one of the online giants being an example; Bank info security
reported that 5 million google passwords leaked (Mathew, 2014).
Mitigation strategies
In the risk concerning cloud based services, the organization can reduce the risk by
opting for other more secure options rather than cloud. Additionally, Netflix can scrutinize the
cloud service provider and ensure that its security management system is of high standard.
Regarding the information system management policies, the organization can formulate a well-
articulated pertinent policies that govern its staff to tighten the system security. For the
organization’s system, Netflix should consider a regular risk assessment to identify loopholes
within the system and fix accordingly Blanke & McGrady 2016). With the implementation of the
above strategies, there is likelihood that the organization will have a robust system that is free
from any form of cyber-attack.
Residual risk
Besides implementing the risk mitigation strategies mentioned in the above sections, still
there would be chances for residual risks. Opting for other options in a bid to resolve the issue
regarding overdependence on cloud would not completely eradicate the threat of data theft. This
is attributed to the fact that cybercrime is everywhere. As such, the organizations system still get
accessed by criminals which would likewise lead to data theft.
Risk register
Threat
description
Vulnerabilit
y
Asset
s
Likelihoo
d
Impacts Risk Mitigatio
n actions
Data theft Over
depending on
cloud
data Medium Loss of data Loss of
reputation
Opt for
other
options.
Inherent risk assessment
In the inherent risk assessment, Netflix organization is an online based corporate. This
means that the company rely on internet for its business. Being that it operates online, it is
automatic that the organization’s system would be a subject to security and privacy breach. This
is also supported by the fact that almost every organizations operating online have at least
experienced cybercrime, google one of the online giants being an example; Bank info security
reported that 5 million google passwords leaked (Mathew, 2014).
Mitigation strategies
In the risk concerning cloud based services, the organization can reduce the risk by
opting for other more secure options rather than cloud. Additionally, Netflix can scrutinize the
cloud service provider and ensure that its security management system is of high standard.
Regarding the information system management policies, the organization can formulate a well-
articulated pertinent policies that govern its staff to tighten the system security. For the
organization’s system, Netflix should consider a regular risk assessment to identify loopholes
within the system and fix accordingly Blanke & McGrady 2016). With the implementation of the
above strategies, there is likelihood that the organization will have a robust system that is free
from any form of cyber-attack.
Residual risk
Besides implementing the risk mitigation strategies mentioned in the above sections, still
there would be chances for residual risks. Opting for other options in a bid to resolve the issue
regarding overdependence on cloud would not completely eradicate the threat of data theft. This
is attributed to the fact that cybercrime is everywhere. As such, the organizations system still get
accessed by criminals which would likewise lead to data theft.
Risk register
Threat
description
Vulnerabilit
y
Asset
s
Likelihoo
d
Impacts Risk Mitigatio
n actions
Data theft Over
depending on
cloud
data Medium Loss of data Loss of
reputation
Opt for
other
options.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
ASSESSMENT ITEM 2 11
Unauthorize
d system
access
Ineffective
security
management
controls
data High Loss of data,
Ruin
organization’
s reputation
Loss of trust Formulate
IT
security
policies
Phishing
attack
Flabby
system
Serve
r
Medium Services will
be
unavailable
Ransomewar
e
Regular
risk
assessmen
t
Conclusion
In summary, we have planned, developed information security policies. The document
has also demonstrated how the formulated policies can be managed to ensure compliance. We
also conducted a risk assessment test on Netflix organization and come up with risks as well as
their mitigation strategies. Based on the analysis, it is worth noting that system security
management is essential for any data driven organization.
Unauthorize
d system
access
Ineffective
security
management
controls
data High Loss of data,
Ruin
organization’
s reputation
Loss of trust Formulate
IT
security
policies
Phishing
attack
Flabby
system
Serve
r
Medium Services will
be
unavailable
Ransomewar
e
Regular
risk
assessmen
t
Conclusion
In summary, we have planned, developed information security policies. The document
has also demonstrated how the formulated policies can be managed to ensure compliance. We
also conducted a risk assessment test on Netflix organization and come up with risks as well as
their mitigation strategies. Based on the analysis, it is worth noting that system security
management is essential for any data driven organization.

ASSESSMENT ITEM 2 12
References
Benferhat, S., Tolba, M., Tabia, K., & Belkhir, A. (2016, August). Representing sequences of
actions in access control security policies. In Proceedings of the 1st International
Workshop on AI for Privacy and Security (p. 5). ACM.
Blanke, S. J., & McGrady, E. (2016). When it comes to securing patient health information from
breaches, your best medicine is a dose of prevention: A cybersecurity risk assessment
checklist. Journal of Healthcare Risk Management, 36(1), 14-24.
Chen, L., Oshiba, D., & Chiong, J. (2016). U.S. Patent No. 9,270,705. Washington, DC: U.S.
Patent and Trademark Office.
Faerber, A. E., Horvath, R., Stillman, C., O’Connell, M. L., Hamilton, A. L., Newhall, K. A., &
Goodney, P. P. (2015). Development and pilot feasibility study of a health information
technology tool to calculate mortality risk for patients with asymptomatic carotid
stenosis: the Carotid Risk Assessment Tool (CARAT). BMC medical informatics and
decision making, 15(1), 20.
Mathew J. (2014). “Five million google passwords leaked.” Retrieved on 11th September 2019
from: <https://www.bankinfosecurity.com/5-million-google-passwords-leaked-a-
7299#targetText=Data%20Leak%3A%20Huge,owned%20by%20CSIS%20Security%20Group.>
New York Times. (2017). “Hacker Leaks Episodes from Netflix Show and Threatens Other
Networks.” Retrieved on 9th September, 2019 from: <
https://www.nytimes.com/2017/04/29/business/media/netflix-hack-orange-is-the-new-
black.html?_r=0>
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. Auerbach Publications.
Sebayan, D. (2017, November). “Email phishing scam targeted millions of Netflix subscribers.”
Retrieved on 9th September, 2019 from: < https://www.itgovernanceusa.com/blog/email-
phishing-scam-targeted-millions-of-netflix-subscribers>
References
Benferhat, S., Tolba, M., Tabia, K., & Belkhir, A. (2016, August). Representing sequences of
actions in access control security policies. In Proceedings of the 1st International
Workshop on AI for Privacy and Security (p. 5). ACM.
Blanke, S. J., & McGrady, E. (2016). When it comes to securing patient health information from
breaches, your best medicine is a dose of prevention: A cybersecurity risk assessment
checklist. Journal of Healthcare Risk Management, 36(1), 14-24.
Chen, L., Oshiba, D., & Chiong, J. (2016). U.S. Patent No. 9,270,705. Washington, DC: U.S.
Patent and Trademark Office.
Faerber, A. E., Horvath, R., Stillman, C., O’Connell, M. L., Hamilton, A. L., Newhall, K. A., &
Goodney, P. P. (2015). Development and pilot feasibility study of a health information
technology tool to calculate mortality risk for patients with asymptomatic carotid
stenosis: the Carotid Risk Assessment Tool (CARAT). BMC medical informatics and
decision making, 15(1), 20.
Mathew J. (2014). “Five million google passwords leaked.” Retrieved on 11th September 2019
from: <https://www.bankinfosecurity.com/5-million-google-passwords-leaked-a-
7299#targetText=Data%20Leak%3A%20Huge,owned%20by%20CSIS%20Security%20Group.>
New York Times. (2017). “Hacker Leaks Episodes from Netflix Show and Threatens Other
Networks.” Retrieved on 9th September, 2019 from: <
https://www.nytimes.com/2017/04/29/business/media/netflix-hack-orange-is-the-new-
black.html?_r=0>
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. Auerbach Publications.
Sebayan, D. (2017, November). “Email phishing scam targeted millions of Netflix subscribers.”
Retrieved on 9th September, 2019 from: < https://www.itgovernanceusa.com/blog/email-
phishing-scam-targeted-millions-of-netflix-subscribers>
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





