Creating and Managing Digital Systems: Privacy Challenges Report
VerifiedAdded on 2023/06/08
|13
|4467
|174
Report
AI Summary
This report examines the vulnerabilities and challenges that healthcare organizations face due to the increasing reliance on information systems and the internet. It highlights how these technologies, while offering numerous benefits, also create significant risks to patient data privacy, intellectual property, and overall system security. The report discusses the reasons for healthcare organizations' vulnerability, including the open nature of information systems, the complexities introduced by rapid technological advancements, and the potential for both internal and external threats. It also explores the specific challenges in protecting the interests of healthcare staff, patients, and customers, emphasizing the risks of cyberattacks and data breaches. Furthermore, the report explains how internet users can leverage self-regulation, legislation, and informed consent to protect their individual privacy and discusses the importance of copyrights, trademarks, and patents in safeguarding intellectual property rights. The report likely concludes with recommendations for strengthening data protection measures and mitigating the risks associated with digital systems in the healthcare sector.

Creating and Managing
Digital Systems
Digital Systems
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
INTRODUCTION ..........................................................................................................................3
MAIN BODY...................................................................................................................................3
Reasons why some healthcare organisations have become independent and vulnerable because
of Information Systems:...............................................................................................................3
Explanation of the internet challenges faced in view of protecting healthcare staffs', patients'
and customers' data privacy and intellectual property:................................................................4
Explanation of how the internet users can protect their individual privacy with the help of self
regulation, legislation, and informed consent:.............................................................................6
Discussion of two ways that protect the intellectual property rights:..........................................7
Recommendations:.......................................................................................................................8
CONCLUSION................................................................................................................................8
REFERENCES..............................................................................................................................10
INTRODUCTION ..........................................................................................................................3
MAIN BODY...................................................................................................................................3
Reasons why some healthcare organisations have become independent and vulnerable because
of Information Systems:...............................................................................................................3
Explanation of the internet challenges faced in view of protecting healthcare staffs', patients'
and customers' data privacy and intellectual property:................................................................4
Explanation of how the internet users can protect their individual privacy with the help of self
regulation, legislation, and informed consent:.............................................................................6
Discussion of two ways that protect the intellectual property rights:..........................................7
Recommendations:.......................................................................................................................8
CONCLUSION................................................................................................................................8
REFERENCES..............................................................................................................................10

INTRODUCTION
The idea of privacy and fair information practices has raised questions in both the
categories of being in favour as well as being against it. To put it in its simplest form, it can be
defined as the set or standards of information collected about the personal data and highlighting
the issues related to it. It means that are certain ways to obtain data regarding any matter and
keep in mind its privacy policies to eliminate any kind of illegal and unfair practices. The term
privacy deals with the capacity an entity might have in obtaining any data to determine what all
information can be shared with whom and how. The FIP's are different in the opinions of people
as to how they see then term as in the privacy policies. Some of these can be general and provide
guidance while for some it can be conflicting in nature. However, it is advisable to collect
information according to the appropriate means and should be kept in mind as to how can these
not hurt anyone in anyway.
TASK-1
Reasons why some healthcare organisations have become independent and vulnerable because of
Information Systems:
As healthcare is related with the society and its constituents, it has become more
dependent on factors that can prove out to be a great source of protection towards their activities
and to save themselves from outsiders (Handtke. Schilgen. and Mösko. 2019). They are at a risk
because of the attackers' immoral goals to attain information about various sectors and elements
of the healthcare organisation that may hinder the confidentiality of their operations and pose
threat to their safety measures. In cybercrimes, the main goal of the attacker is to gather as much
information about health records as much it is possible to harm the healthcare sector and their
services. These informations can be misused by them in order to acquire a large portion of
resources available with the healthcare organisations. The organisations have become vulnerable
due to the above mentioned reasons due to the nature of information systems being an open
system that imposes the risk of vulnerability that creates possible access to the irrelevant
authorities through system's memory. There is no reliability of these information systems as they
are robotic elements and can be accessed by anyone, anytime and anyhow it wants to be done
(Feldman. Buchalter. and Hayes. 2018). The rapid development of information systems in order
to accelerate its development, has unknowingly created complexity in its authentication and
relevancy. The healthcare organisations and their overall operational activities are disrupted by
The idea of privacy and fair information practices has raised questions in both the
categories of being in favour as well as being against it. To put it in its simplest form, it can be
defined as the set or standards of information collected about the personal data and highlighting
the issues related to it. It means that are certain ways to obtain data regarding any matter and
keep in mind its privacy policies to eliminate any kind of illegal and unfair practices. The term
privacy deals with the capacity an entity might have in obtaining any data to determine what all
information can be shared with whom and how. The FIP's are different in the opinions of people
as to how they see then term as in the privacy policies. Some of these can be general and provide
guidance while for some it can be conflicting in nature. However, it is advisable to collect
information according to the appropriate means and should be kept in mind as to how can these
not hurt anyone in anyway.
TASK-1
Reasons why some healthcare organisations have become independent and vulnerable because of
Information Systems:
As healthcare is related with the society and its constituents, it has become more
dependent on factors that can prove out to be a great source of protection towards their activities
and to save themselves from outsiders (Handtke. Schilgen. and Mösko. 2019). They are at a risk
because of the attackers' immoral goals to attain information about various sectors and elements
of the healthcare organisation that may hinder the confidentiality of their operations and pose
threat to their safety measures. In cybercrimes, the main goal of the attacker is to gather as much
information about health records as much it is possible to harm the healthcare sector and their
services. These informations can be misused by them in order to acquire a large portion of
resources available with the healthcare organisations. The organisations have become vulnerable
due to the above mentioned reasons due to the nature of information systems being an open
system that imposes the risk of vulnerability that creates possible access to the irrelevant
authorities through system's memory. There is no reliability of these information systems as they
are robotic elements and can be accessed by anyone, anytime and anyhow it wants to be done
(Feldman. Buchalter. and Hayes. 2018). The rapid development of information systems in order
to accelerate its development, has unknowingly created complexity in its authentication and
relevancy. The healthcare organisations and their overall operational activities are disrupted by
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

these complexities in the form of various man made and natural factors such as humans and
technology with the same motive of conducting malicious activities such as fraud.
To reduce the involvement of such malpractices, there are several measures taken to
create technical and innovative processors that can detect these unwanted factors which hinder
the quality of these creative information systems. There are many relevant possibilities of
internal stealing and possession over the data, the healthcare organisations are vulnerable to both
internal and external environment around them. There are multiple ways in which the internal
illegal attempts can be taken in the form of staffs, outsiders entering the premises, etc. in order to
steal credentials that are extremely confidential for the organisation on which the overall
operational activities are dependent on. The main risk of these information systems initiates
when the details are exposed to the public or the rivalries in terms to commit a variety of crimes.
Usage of such information systems have both pros and cons for an organization as it has many
levels to pass through in order to meet its final collaboration with the authorities. The
intermediaries involved in the process might be the cause of presenting the outdated data
pertaining to the high operational costs. With these high operational and production costs, there
is a threat of duplication of the equipment used in the treatment of the patients without anyone's
knowledge about the exchange of equipment (Rothstein. and Tovino. 2019). Apart form having
these negative point of view of the technical information systems, there are some benefits such as
the reduction in human errors, facilitating coordination, etc. Even though there are numerous
benefits, the human nature is to hinder the privacy concerns and acquire data and information
about health issues of the people and influence terrorism.
Explanation of the internet challenges faced in view of protecting healthcare staffs', patients' and
customers' data privacy and intellectual property:
The procedure and method of operating healthcare organisation has changed
tremendously in the past years in view of its staff, patients and customers. Not only in the form
of rendering services for their benefit and care, but also for protecting their interests and
intellectual rights from the dangerous practices (Greeter. and Reiboldt. 2022). The new
technology and legislative rules and regulations in the territory have provided assistance in the
form of security from the breach of data and other actionable crimes. In the current scenario,
there are many problems faced by the health systems across the globe in order to protect the
rights and interests of their people along with the customers and patients. There is no doubt that
technology with the same motive of conducting malicious activities such as fraud.
To reduce the involvement of such malpractices, there are several measures taken to
create technical and innovative processors that can detect these unwanted factors which hinder
the quality of these creative information systems. There are many relevant possibilities of
internal stealing and possession over the data, the healthcare organisations are vulnerable to both
internal and external environment around them. There are multiple ways in which the internal
illegal attempts can be taken in the form of staffs, outsiders entering the premises, etc. in order to
steal credentials that are extremely confidential for the organisation on which the overall
operational activities are dependent on. The main risk of these information systems initiates
when the details are exposed to the public or the rivalries in terms to commit a variety of crimes.
Usage of such information systems have both pros and cons for an organization as it has many
levels to pass through in order to meet its final collaboration with the authorities. The
intermediaries involved in the process might be the cause of presenting the outdated data
pertaining to the high operational costs. With these high operational and production costs, there
is a threat of duplication of the equipment used in the treatment of the patients without anyone's
knowledge about the exchange of equipment (Rothstein. and Tovino. 2019). Apart form having
these negative point of view of the technical information systems, there are some benefits such as
the reduction in human errors, facilitating coordination, etc. Even though there are numerous
benefits, the human nature is to hinder the privacy concerns and acquire data and information
about health issues of the people and influence terrorism.
Explanation of the internet challenges faced in view of protecting healthcare staffs', patients' and
customers' data privacy and intellectual property:
The procedure and method of operating healthcare organisation has changed
tremendously in the past years in view of its staff, patients and customers. Not only in the form
of rendering services for their benefit and care, but also for protecting their interests and
intellectual rights from the dangerous practices (Greeter. and Reiboldt. 2022). The new
technology and legislative rules and regulations in the territory have provided assistance in the
form of security from the breach of data and other actionable crimes. In the current scenario,
there are many problems faced by the health systems across the globe in order to protect the
rights and interests of their people along with the customers and patients. There is no doubt that
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

technology has amended many operational activities, both in positive and negative ways. On one
hand, the internet of things enables healthcare specialists to identify and collect ideas about how
the privacy and intellectual rights can be preserved, but on the other hand there are specific
challenges faced in the view of data security and privacy. These can include the capturing of real
and accurate data about the privacy rights and lack of adherence to data protocols and standards
because of ambiguity regarding the ownership and regulation of data and details.
Challenges faced in protecting healthcare staffs' interests:
In the wave of protecting internal staffs' interests, healthcare sector faces challenges in
the form of current digital platforms used in the process (Ghiasvand. and et.al., 2021). These
digital platforms might protect the data from internal and external actions of the outsiders, but it
imposes security risks about one's private information getting stolen by the means of breach of
information. With the usage of technology in order to grab personal information about the staffs,
they can be threatened to get involved in the malpractices against the patients' and customers.
The information can be copied through several means with the help of hackers and internal threat
composition.
Challenges faced in protecting patients' interests:
The patients rights and interests are to be protected in order to save them from getting
exposed to the outer world. The internet has opened doors to copy and replicate the data and
materials about the locals in the industry that are now prone to many health hazards if the
information is not protected properly. It is a common issue of online interactions that people are
not been guided towards how to save their rights and interests against the illegal activities
committed. All these contents about people has to be protected by the healthcare systems in order
to protect them from getting attacked.
Challenges faced in protecting customers' interests:
The healthcare organisations are prone to cyberattacks on electronic health records of
their customers which pose a risk to the privacy and protective rights because of the interference
of hackers to get access to the information system. This can cause prejudices in protecting the
rights of the customers of healthcare systems. These challenges faced by the systems can deter
the ability of performing effectively in the healthcare industry and can also result in their
reputation and recognition. The information leaked can also be sold at high prices, and can
regulate some political issues with the organisation.
hand, the internet of things enables healthcare specialists to identify and collect ideas about how
the privacy and intellectual rights can be preserved, but on the other hand there are specific
challenges faced in the view of data security and privacy. These can include the capturing of real
and accurate data about the privacy rights and lack of adherence to data protocols and standards
because of ambiguity regarding the ownership and regulation of data and details.
Challenges faced in protecting healthcare staffs' interests:
In the wave of protecting internal staffs' interests, healthcare sector faces challenges in
the form of current digital platforms used in the process (Ghiasvand. and et.al., 2021). These
digital platforms might protect the data from internal and external actions of the outsiders, but it
imposes security risks about one's private information getting stolen by the means of breach of
information. With the usage of technology in order to grab personal information about the staffs,
they can be threatened to get involved in the malpractices against the patients' and customers.
The information can be copied through several means with the help of hackers and internal threat
composition.
Challenges faced in protecting patients' interests:
The patients rights and interests are to be protected in order to save them from getting
exposed to the outer world. The internet has opened doors to copy and replicate the data and
materials about the locals in the industry that are now prone to many health hazards if the
information is not protected properly. It is a common issue of online interactions that people are
not been guided towards how to save their rights and interests against the illegal activities
committed. All these contents about people has to be protected by the healthcare systems in order
to protect them from getting attacked.
Challenges faced in protecting customers' interests:
The healthcare organisations are prone to cyberattacks on electronic health records of
their customers which pose a risk to the privacy and protective rights because of the interference
of hackers to get access to the information system. This can cause prejudices in protecting the
rights of the customers of healthcare systems. These challenges faced by the systems can deter
the ability of performing effectively in the healthcare industry and can also result in their
reputation and recognition. The information leaked can also be sold at high prices, and can
regulate some political issues with the organisation.

Explanation of how the internet users can protect their individual privacy with the help of self
regulation, legislation, and informed consent:
Every service provider nowadays of both online and offline collects, and interprets
personal data for providing people with relevant and accurate information through the sources.
There are many nations who adapt to the comprehensive and strict laws in order to protect the
interests and individual privacy policy of its internet users. The internet should possess consent
of the owner of information in prior to collecting these in order to protect the individuals from
any privacy related issues. The technological advances can also be utilised by one to protect the
intellectual rights from the hazards of innovative and dynamic world. Social media threats can
now be easily avoided with the help of various legislations and laws imposed by the political
interferences. These law state that data collected must be parallel to the purpose and mission of
the information provided by the owner to reduce the risks of rights. The collection and
interpretation of data should be all in accordance with obligations of the legal bodies as
prescribed. Any individual can make use of such privileges granted by the nation in order to
protect their rights and interests against the breaches of many kind. These privileges enjoyed
provide relevant data to the relevant sources who genuinely deserve information of someone in
order to enhance the technological advancements prevailing in the world. To maintain the
security and privacy of information of the internet users, it is their own responsibility and duty
because no one can protect these better than the real owner.
Therefore, the real owner is entitled to many rights and privileges to protect themselves
from the risk of getting exposed whether financially or non financially. For instance,
International data protection and privacy policies are regularly in track of maintaining
records of informed consent given to the actual receiver of the information to limit and process
the ideology of providing others with the consent of optimising their information for privacy
reasons. The main reason is to focus on enhancing technologies, strategies and controls over
cyberattacks committed in the course of action. The internet users are even entitled to the
strategy of minimising the collection and processing of personal data in order to limit the impact
of privacy hindrances. They can also hide personal data and their interrelationships to minimise
abuse to the given information. They are provided with the controlling tools in order to
implement data protection rights and improve the quality and accuracy of information received.
With these advantages provided to the individual internet users, it has now become very easy to
regulation, legislation, and informed consent:
Every service provider nowadays of both online and offline collects, and interprets
personal data for providing people with relevant and accurate information through the sources.
There are many nations who adapt to the comprehensive and strict laws in order to protect the
interests and individual privacy policy of its internet users. The internet should possess consent
of the owner of information in prior to collecting these in order to protect the individuals from
any privacy related issues. The technological advances can also be utilised by one to protect the
intellectual rights from the hazards of innovative and dynamic world. Social media threats can
now be easily avoided with the help of various legislations and laws imposed by the political
interferences. These law state that data collected must be parallel to the purpose and mission of
the information provided by the owner to reduce the risks of rights. The collection and
interpretation of data should be all in accordance with obligations of the legal bodies as
prescribed. Any individual can make use of such privileges granted by the nation in order to
protect their rights and interests against the breaches of many kind. These privileges enjoyed
provide relevant data to the relevant sources who genuinely deserve information of someone in
order to enhance the technological advancements prevailing in the world. To maintain the
security and privacy of information of the internet users, it is their own responsibility and duty
because no one can protect these better than the real owner.
Therefore, the real owner is entitled to many rights and privileges to protect themselves
from the risk of getting exposed whether financially or non financially. For instance,
International data protection and privacy policies are regularly in track of maintaining
records of informed consent given to the actual receiver of the information to limit and process
the ideology of providing others with the consent of optimising their information for privacy
reasons. The main reason is to focus on enhancing technologies, strategies and controls over
cyberattacks committed in the course of action. The internet users are even entitled to the
strategy of minimising the collection and processing of personal data in order to limit the impact
of privacy hindrances. They can also hide personal data and their interrelationships to minimise
abuse to the given information. They are provided with the controlling tools in order to
implement data protection rights and improve the quality and accuracy of information received.
With these advantages provided to the individual internet users, it has now become very easy to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

protect their individual privacy policies with the help of technical advancements such as the
authentication systems that give the overview of how these can be optimised by people to
connect with assurance and reliable parties.
Discussion of two ways that protect the intellectual property rights:
Intellectual property rights are the ownership rights that are granted to people when they
create their own ideas about something (Nomani. Alhalboosi. and Rauf. 2020). In order to
protect these interests and rights against any party, it is essential to follow some ways that can
prove out to be beneficial in maintaining privacy policies. There are two impactful and
influential ways, in which these intellectual rights can be preserved and protected.
1. Copyrights, Trademarks, and Patents:
The basic way of protecting the intellectual property rights is to get access to the
copyrights, patents, etc. for eliminating threats of cyberattacks. These are legal evidences with
the real owner in order to present these at the time of need. Copyrights are the tangible
representation of the original ideas, which unfortunately can not be protected individually. These
help in the enforcement of their rights against any kind of infringement by the lawsuits in order
to support any kind of malpractices. In a similar way, Trademarks are the symbols, and logos
that differentiates one's possession of their goods and services. These are optimised to make sure
that the rights are reliably recognised by the industry and is varied from one product with other.
It helps in avoiding confusion among the operators of similar products and services and to
maintain privacy policies. Patents are one kind of trade secrets in the form of protecting
intellectual rights that keep the innovation and technical advancements within the possession of
the real owner. There is also no fear of duplication as they are unique in their own way for the
general public to maintain integrity in protecting their intellectual property rights. There are not
many formalities to be done in order to obtain one which makes it highly reliable.
2. Innovative techniques:
Innovative techniques are very effective when it comes to protecting the rights and
privacy of data, information and intellectual properties from the threats of uncertainties of the
dynamic world. It is a highly adopted tool to avoid plagiarism in one's creation and the term
creativity also gets promoted in the wave of protecting intellectual rights. There are endless
innovative ideas and techniques to improvise the protection of such crucial rights that can pose
threats to the information and data, if leaked and reached to an irrelevant source. Apart from
authentication systems that give the overview of how these can be optimised by people to
connect with assurance and reliable parties.
Discussion of two ways that protect the intellectual property rights:
Intellectual property rights are the ownership rights that are granted to people when they
create their own ideas about something (Nomani. Alhalboosi. and Rauf. 2020). In order to
protect these interests and rights against any party, it is essential to follow some ways that can
prove out to be beneficial in maintaining privacy policies. There are two impactful and
influential ways, in which these intellectual rights can be preserved and protected.
1. Copyrights, Trademarks, and Patents:
The basic way of protecting the intellectual property rights is to get access to the
copyrights, patents, etc. for eliminating threats of cyberattacks. These are legal evidences with
the real owner in order to present these at the time of need. Copyrights are the tangible
representation of the original ideas, which unfortunately can not be protected individually. These
help in the enforcement of their rights against any kind of infringement by the lawsuits in order
to support any kind of malpractices. In a similar way, Trademarks are the symbols, and logos
that differentiates one's possession of their goods and services. These are optimised to make sure
that the rights are reliably recognised by the industry and is varied from one product with other.
It helps in avoiding confusion among the operators of similar products and services and to
maintain privacy policies. Patents are one kind of trade secrets in the form of protecting
intellectual rights that keep the innovation and technical advancements within the possession of
the real owner. There is also no fear of duplication as they are unique in their own way for the
general public to maintain integrity in protecting their intellectual property rights. There are not
many formalities to be done in order to obtain one which makes it highly reliable.
2. Innovative techniques:
Innovative techniques are very effective when it comes to protecting the rights and
privacy of data, information and intellectual properties from the threats of uncertainties of the
dynamic world. It is a highly adopted tool to avoid plagiarism in one's creation and the term
creativity also gets promoted in the wave of protecting intellectual rights. There are endless
innovative ideas and techniques to improvise the protection of such crucial rights that can pose
threats to the information and data, if leaked and reached to an irrelevant source. Apart from
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

having beneficial rights, these might be prone to some risks as cyberattacks can be carried out in
any way to hinder the privacy policies. Therefore, it is advisable to collect evidence while being
innovative in order to be on a safer side. The rivals can obtain information about anything from
anywhere and anytime without the knowledge of the rightful owner that creates misconception
among the parties (Gürkaynak. and et.al., 2018). This is where the evidences can be fruitfully
utilised for the evolution of maintaining intellectual property rights against those who want to
accomplish their illegal tasks with the help of someone else's property and rights. A proper
strategy must be formed in order to bring out the creativity and uniqueness to avoid duplication
of property rights.
Recommendations:
The healthcare organisation and sectors can improve only with the help of technologies
an innovation tactics and techniques. The contemporary information systems technology and the
internet pose challenges to the protection of an individual's intellectual rights and properties
because these are not properly taken care of (RECOMMENDATIONS ABOUT INFORMATION
SYSTEMS. 2022). In the healthcare sector, it is important to protect innovations and techniques
to avoid plagiarism in the activities so that no one else can use the blueprint of data to develop a
similar production of services in order to become more successful in the sector. This can hinder
the privacy of many people related to the healthcare sector in different ways and can pose threat
to their personal and professional rights. The technologies should be wisely optimised by the
healthcare providers so that the harnessing power of these technologies can be achieved in the
sustainability of development goals.
CONCLUSION
The above report about Creating and Managing Digital Systems concluded on the basis
of the facilities that Information systems provide to the healthcare sectors. The contemporary
information systems technology reduces many human efforts in carrying out a level of
anonymity and offers various advantages to the people in need. In order to decrease the use of
complex activities by some people, it is always advisable to connect with the legal bodies and
higher technical advancements to avoid any risk of breach of information and private data about
constituents of the healthcare sector. It was also discussed in the brief about how can an
individual protect its own intellectual rights and privacy policies from the attacks and what are
various privileges granted to them in order to protect their interests. All these benefits and
any way to hinder the privacy policies. Therefore, it is advisable to collect evidence while being
innovative in order to be on a safer side. The rivals can obtain information about anything from
anywhere and anytime without the knowledge of the rightful owner that creates misconception
among the parties (Gürkaynak. and et.al., 2018). This is where the evidences can be fruitfully
utilised for the evolution of maintaining intellectual property rights against those who want to
accomplish their illegal tasks with the help of someone else's property and rights. A proper
strategy must be formed in order to bring out the creativity and uniqueness to avoid duplication
of property rights.
Recommendations:
The healthcare organisation and sectors can improve only with the help of technologies
an innovation tactics and techniques. The contemporary information systems technology and the
internet pose challenges to the protection of an individual's intellectual rights and properties
because these are not properly taken care of (RECOMMENDATIONS ABOUT INFORMATION
SYSTEMS. 2022). In the healthcare sector, it is important to protect innovations and techniques
to avoid plagiarism in the activities so that no one else can use the blueprint of data to develop a
similar production of services in order to become more successful in the sector. This can hinder
the privacy of many people related to the healthcare sector in different ways and can pose threat
to their personal and professional rights. The technologies should be wisely optimised by the
healthcare providers so that the harnessing power of these technologies can be achieved in the
sustainability of development goals.
CONCLUSION
The above report about Creating and Managing Digital Systems concluded on the basis
of the facilities that Information systems provide to the healthcare sectors. The contemporary
information systems technology reduces many human efforts in carrying out a level of
anonymity and offers various advantages to the people in need. In order to decrease the use of
complex activities by some people, it is always advisable to connect with the legal bodies and
higher technical advancements to avoid any risk of breach of information and private data about
constituents of the healthcare sector. It was also discussed in the brief about how can an
individual protect its own intellectual rights and privacy policies from the attacks and what are
various privileges granted to them in order to protect their interests. All these benefits and

advantages can be effectively utilised by the healthcare sector and organisations in order to
protect their people from the challenges of cybercrimes.
TASK-3
1.
A)
The projects are having multiple characteristics but some most prominent are as-
A project has a pre decided time frame in which it is supposed to be completed.
There are some assumptions kept in projects in order to carry out it successfully.
All the projects are having need of multiple resources either human resource, financial
resources or other forms but it is inevitable part of projects (Guo and Zhang, 2022)
The projects are having their cost. This cost may get measured in term of finance or it
may not be but the cost factor cannot be eliminated to the fullest extent.
The all projects are based on certain risk, risk is the most common factor, the degree and
direction may be ingratiating but the risk cannot be eliminated to the fullest extent.
B)
Project initiation document is the well-structured document which consists range of
things such as project activities, the way they are to be performed, how and what type of
methodologies and actions will be taken into focus etc.
This is very much essential since for executing a project successfully, the only way is
PID. This document helps to eradicate the vagueness and it drives the decision making process
and also suggest some better ways to overcome the issues.
The project scope, risks factors, communication factors all these aspects can be covered
with the help of PID. Project parameters, breakdown structure, resource planning,
communication planning all these get covered in PID (Hair and Sarstedt, 2021)
It is said that if the PID is diversified and articulating all the relevant dimensions then for
a project manager it becomes handy to guide its team to achieve the aims and objectives the
project. With this regard, the role of PID is highly needed.
2.
A)
protect their people from the challenges of cybercrimes.
TASK-3
1.
A)
The projects are having multiple characteristics but some most prominent are as-
A project has a pre decided time frame in which it is supposed to be completed.
There are some assumptions kept in projects in order to carry out it successfully.
All the projects are having need of multiple resources either human resource, financial
resources or other forms but it is inevitable part of projects (Guo and Zhang, 2022)
The projects are having their cost. This cost may get measured in term of finance or it
may not be but the cost factor cannot be eliminated to the fullest extent.
The all projects are based on certain risk, risk is the most common factor, the degree and
direction may be ingratiating but the risk cannot be eliminated to the fullest extent.
B)
Project initiation document is the well-structured document which consists range of
things such as project activities, the way they are to be performed, how and what type of
methodologies and actions will be taken into focus etc.
This is very much essential since for executing a project successfully, the only way is
PID. This document helps to eradicate the vagueness and it drives the decision making process
and also suggest some better ways to overcome the issues.
The project scope, risks factors, communication factors all these aspects can be covered
with the help of PID. Project parameters, breakdown structure, resource planning,
communication planning all these get covered in PID (Hair and Sarstedt, 2021)
It is said that if the PID is diversified and articulating all the relevant dimensions then for
a project manager it becomes handy to guide its team to achieve the aims and objectives the
project. With this regard, the role of PID is highly needed.
2.
A)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

In any project there is need to have rationality when it comes to make decision. The
Scope statement becomes quite helpful. It has seen that the project which do not have scope
statement face creepy issues.
Scope statement is a driving force which aids a project to make the efforts in right
direction, and can also drive the communication in appropriate manner. The project team also
gets driven by scope statement and they can work without getting confused if the statement is
well articulated and guiding them at all phases.
B)
Work Breakdown Structure is used to depict all the activities which are to be enforced in
certain project. This statement is highly necessary since if there is good work and activities
allocation then the project performance goes high.
It articulates all activities in a rational and orderly manner. The activities, under which
head they are, what are the following activities etc. are depicted in the structure. The biggest role
of WBS is to help in understanding various acts and the way they are to be performed (Picciotto,
2020)
WBS gives direction to the project manager and the all team members to carry out their actives
in a well-structured manner. It directs them to carry out activities keeping them aware of the set
of activities so it would be fair to articulate that the WBS is highly prominent for project
managers.
3.
Network diagram for the suggested project is as-
Scope statement becomes quite helpful. It has seen that the project which do not have scope
statement face creepy issues.
Scope statement is a driving force which aids a project to make the efforts in right
direction, and can also drive the communication in appropriate manner. The project team also
gets driven by scope statement and they can work without getting confused if the statement is
well articulated and guiding them at all phases.
B)
Work Breakdown Structure is used to depict all the activities which are to be enforced in
certain project. This statement is highly necessary since if there is good work and activities
allocation then the project performance goes high.
It articulates all activities in a rational and orderly manner. The activities, under which
head they are, what are the following activities etc. are depicted in the structure. The biggest role
of WBS is to help in understanding various acts and the way they are to be performed (Picciotto,
2020)
WBS gives direction to the project manager and the all team members to carry out their actives
in a well-structured manner. It directs them to carry out activities keeping them aware of the set
of activities so it would be fair to articulate that the WBS is highly prominent for project
managers.
3.
Network diagram for the suggested project is as-
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
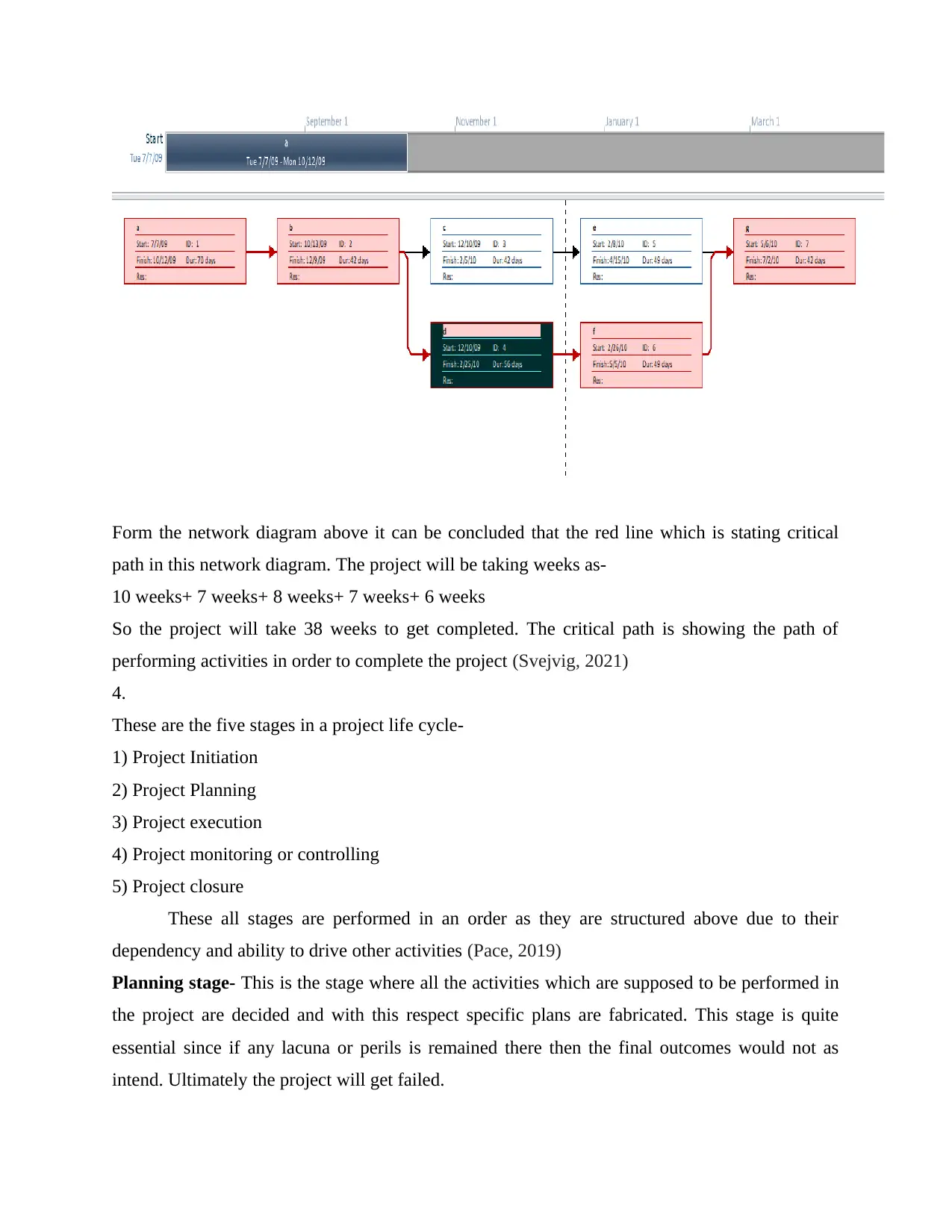
Form the network diagram above it can be concluded that the red line which is stating critical
path in this network diagram. The project will be taking weeks as-
10 weeks+ 7 weeks+ 8 weeks+ 7 weeks+ 6 weeks
So the project will take 38 weeks to get completed. The critical path is showing the path of
performing activities in order to complete the project (Svejvig, 2021)
4.
These are the five stages in a project life cycle-
1) Project Initiation
2) Project Planning
3) Project execution
4) Project monitoring or controlling
5) Project closure
These all stages are performed in an order as they are structured above due to their
dependency and ability to drive other activities (Pace, 2019)
Planning stage- This is the stage where all the activities which are supposed to be performed in
the project are decided and with this respect specific plans are fabricated. This stage is quite
essential since if any lacuna or perils is remained there then the final outcomes would not as
intend. Ultimately the project will get failed.
path in this network diagram. The project will be taking weeks as-
10 weeks+ 7 weeks+ 8 weeks+ 7 weeks+ 6 weeks
So the project will take 38 weeks to get completed. The critical path is showing the path of
performing activities in order to complete the project (Svejvig, 2021)
4.
These are the five stages in a project life cycle-
1) Project Initiation
2) Project Planning
3) Project execution
4) Project monitoring or controlling
5) Project closure
These all stages are performed in an order as they are structured above due to their
dependency and ability to drive other activities (Pace, 2019)
Planning stage- This is the stage where all the activities which are supposed to be performed in
the project are decided and with this respect specific plans are fabricated. This stage is quite
essential since if any lacuna or perils is remained there then the final outcomes would not as
intend. Ultimately the project will get failed.

Control stage- This is the stage where the project is controlled or monitored since at once
project got started and the activities are being performed then there is need to keep eyes on them
so can eradicate any type of irregularity or discrepancy which may bring sort of catastrophe to
the final outcomes. It paves the way forward and also drives to make proper decision to wipe out
such perilous points.
5.
The success of project depends on different resources. The main resources are
materialistic resources, financial resources and human resources. All other resources are having
good characteristic that they do not have any emotional or skilfulness. Their performance hugely
depends on the performance of human resources. It would be highly fair to conclude that if the
human resources are high skilled then the remaining resources can be driven to perform better.
This is prime duty of a project manager to ensure that there must be proper and absolute
recruitment when it comes to team. If a good team is there, then it would no longer a challenge to
carry out the project with great success. The main aim or objective of any project is to make the
expedition which can only be grabbed if there is a well skilled team (Flyvbjerg, 2021)
The team is supposed to have multiple abilities at the same time, since in a project
multiple activities are performed and there is strong need to have such team members who can
play vital and diversified role to manage the project. If there is such team, then it becomes quite
simpler to execute the project with greater ease. It is only possible with such versatile team. So it
would be fair, to articulate that a project manager is supposed to make such strong team.
project got started and the activities are being performed then there is need to keep eyes on them
so can eradicate any type of irregularity or discrepancy which may bring sort of catastrophe to
the final outcomes. It paves the way forward and also drives to make proper decision to wipe out
such perilous points.
5.
The success of project depends on different resources. The main resources are
materialistic resources, financial resources and human resources. All other resources are having
good characteristic that they do not have any emotional or skilfulness. Their performance hugely
depends on the performance of human resources. It would be highly fair to conclude that if the
human resources are high skilled then the remaining resources can be driven to perform better.
This is prime duty of a project manager to ensure that there must be proper and absolute
recruitment when it comes to team. If a good team is there, then it would no longer a challenge to
carry out the project with great success. The main aim or objective of any project is to make the
expedition which can only be grabbed if there is a well skilled team (Flyvbjerg, 2021)
The team is supposed to have multiple abilities at the same time, since in a project
multiple activities are performed and there is strong need to have such team members who can
play vital and diversified role to manage the project. If there is such team, then it becomes quite
simpler to execute the project with greater ease. It is only possible with such versatile team. So it
would be fair, to articulate that a project manager is supposed to make such strong team.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





