HI5019 Strategic Info Systems: Bell Studio Expenditure Cycle Risks
VerifiedAdded on 2023/03/23
|18
|3622
|41
Case Study
AI Summary
This report analyzes Bell Studio's current strategic information systems, focusing on potential risks, internal controls within the expenditure cycle, and various operational processes. It includes data flow diagrams (DFDs) for the purchase, payroll, and cash disbursement systems, along with corresponding system flowcharts. The report elucidates weaknesses in the internal control system, highlighting major risks associated with these vulnerabilities, such as unauthorized access, viruses, malware, sniffing, and spoofing. It concludes by emphasizing the importance of addressing these weaknesses to ensure the secure and effective functioning of Bell Studio's information systems, and the need for implementing robust security protocols to mitigate cyber threats and data breaches.

Running head: STRATEGIC INFORMATION SYSTEMS
Strategic Information System
Name of the Student
Name of the University
Author Note
Strategic Information System
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1STRATEGIC INFORMATION SYSTEMS
Table of Contents
Introduction................................................................................................................................2
DFD of Purchase System...........................................................................................................2
DFD of Payroll System..............................................................................................................3
DFD of Cash Disbursement System..........................................................................................4
System Flowchart of Cash Disbursement System.....................................................................5
System Flowchart of Purchase System......................................................................................6
Elucidation of the weaknesses in the internal control of the system and the major risks
coupled with the recognized weaknesses...................................................................................7
Weaknesses in the organization.............................................................................................7
Risks...........................................................................................................................................9
Unauthorized access...............................................................................................................9
Viruses and malware..............................................................................................................9
Sniffing and Spoofing..........................................................................................................11
Conclusion................................................................................................................................14
References................................................................................................................................15
Table of Contents
Introduction................................................................................................................................2
DFD of Purchase System...........................................................................................................2
DFD of Payroll System..............................................................................................................3
DFD of Cash Disbursement System..........................................................................................4
System Flowchart of Cash Disbursement System.....................................................................5
System Flowchart of Purchase System......................................................................................6
Elucidation of the weaknesses in the internal control of the system and the major risks
coupled with the recognized weaknesses...................................................................................7
Weaknesses in the organization.............................................................................................7
Risks...........................................................................................................................................9
Unauthorized access...............................................................................................................9
Viruses and malware..............................................................................................................9
Sniffing and Spoofing..........................................................................................................11
Conclusion................................................................................................................................14
References................................................................................................................................15
2STRATEGIC INFORMATION SYSTEMS
Introduction
This particular report focuses on the current scenario of Bell Studio. Evaluation of the
potential risks of the company, internal controls of the expenditure cycle and the various
processes is done. The report contains the data flow diagram (DFD) of cash disbursement
system. In this report the DFD of payroll system is given along with purchase system
flowchart, payroll and the cash disbursement system. In addition to the above discussion, the
internal control system and the weaknesses of the system is concisely explored. The report
further highlights the risks coupled with the system weaknesses. At the end the report
provides a pertinent conclusion for the discussion.
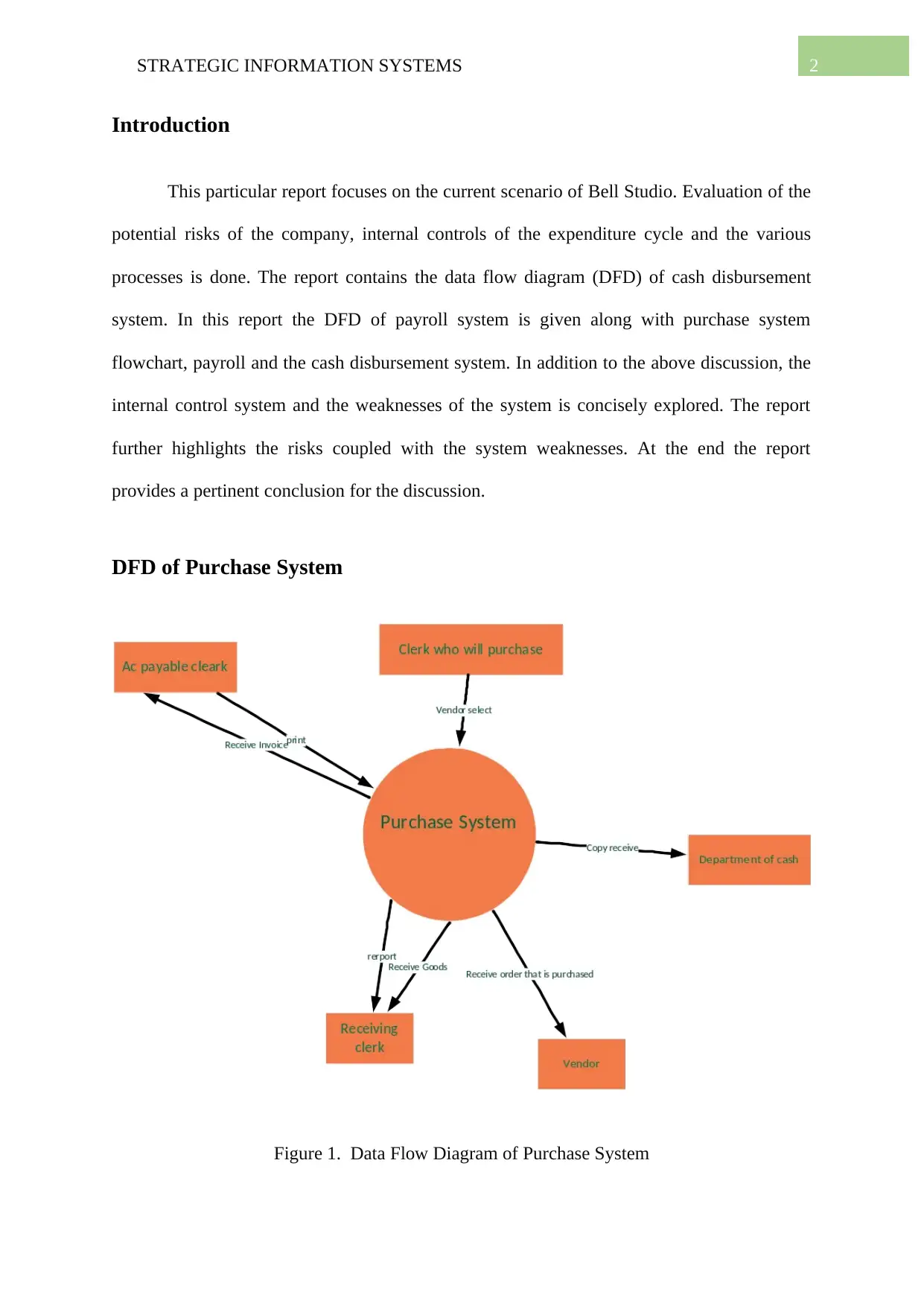
DFD of Purchase System
Figure 1. Data Flow Diagram of Purchase System
Introduction
This particular report focuses on the current scenario of Bell Studio. Evaluation of the
potential risks of the company, internal controls of the expenditure cycle and the various
processes is done. The report contains the data flow diagram (DFD) of cash disbursement
system. In this report the DFD of payroll system is given along with purchase system
flowchart, payroll and the cash disbursement system. In addition to the above discussion, the
internal control system and the weaknesses of the system is concisely explored. The report
further highlights the risks coupled with the system weaknesses. At the end the report
provides a pertinent conclusion for the discussion.
DFD of Purchase System
Figure 1. Data Flow Diagram of Purchase System
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3STRATEGIC INFORMATION SYSTEMS
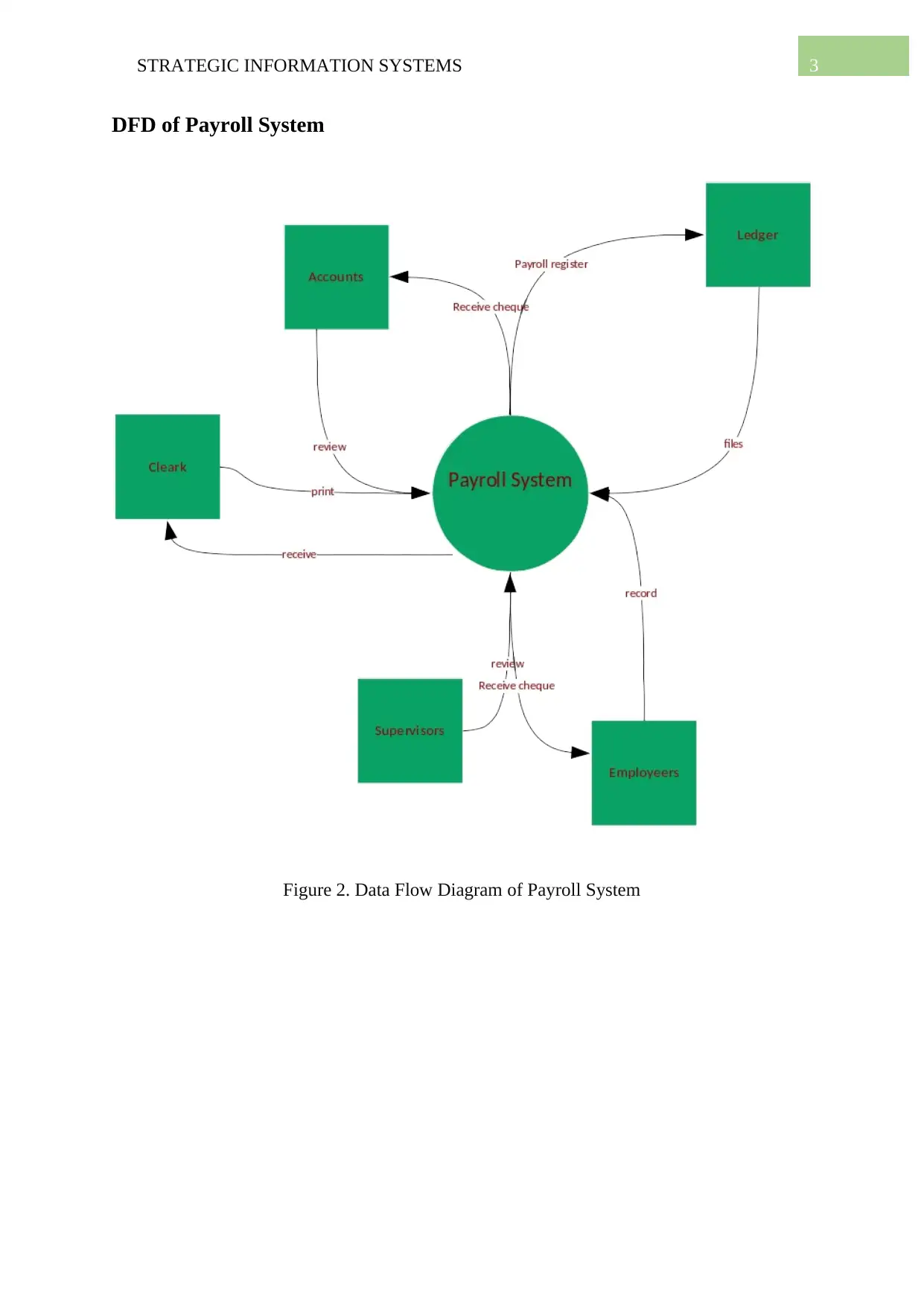
DFD of Payroll System
Figure 2. Data Flow Diagram of Payroll System
DFD of Payroll System
Figure 2. Data Flow Diagram of Payroll System
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4STRATEGIC INFORMATION SYSTEMS
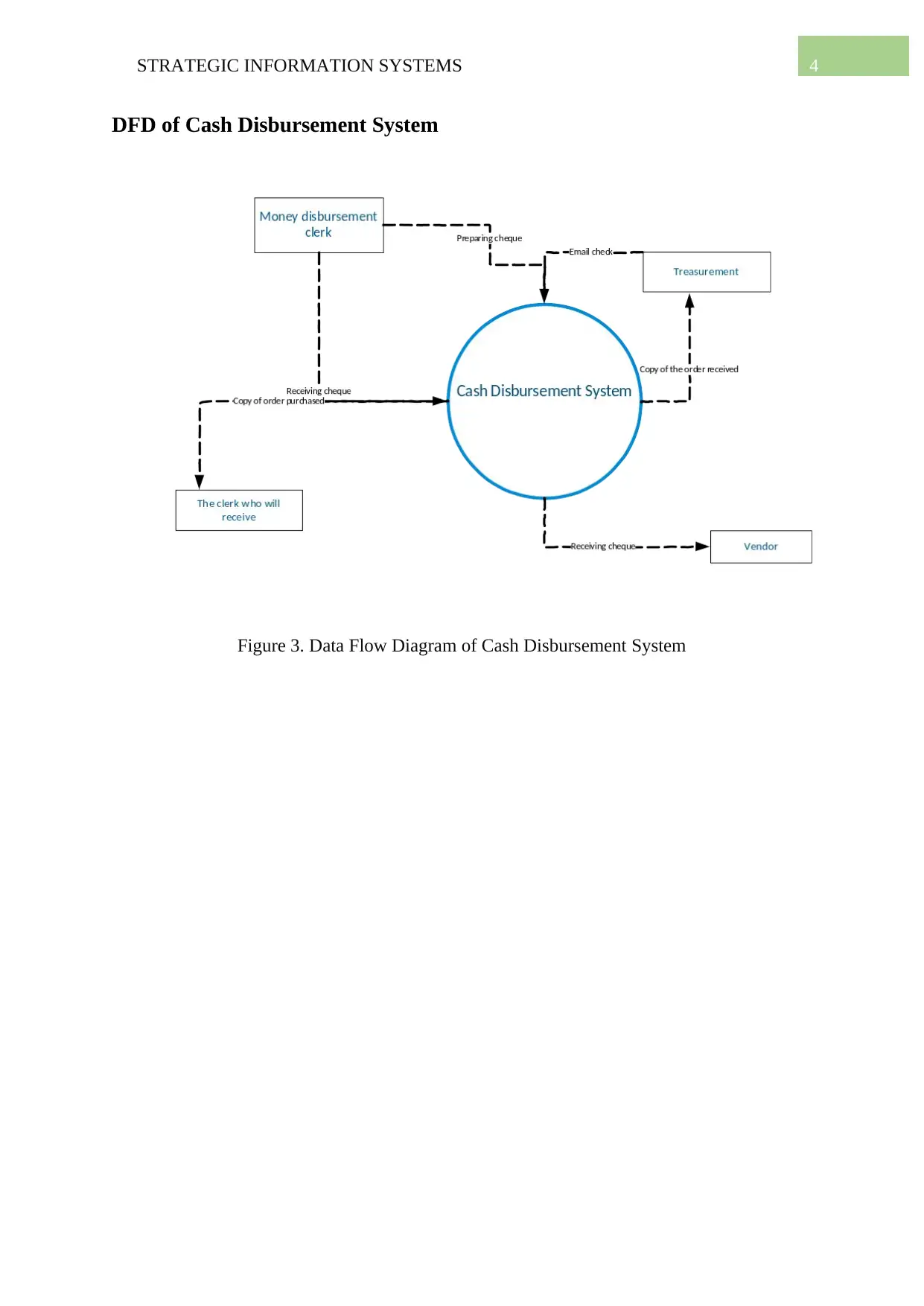
DFD of Cash Disbursement System
Figure 3. Data Flow Diagram of Cash Disbursement System
DFD of Cash Disbursement System
Figure 3. Data Flow Diagram of Cash Disbursement System
5STRATEGIC INFORMATION SYSTEMS
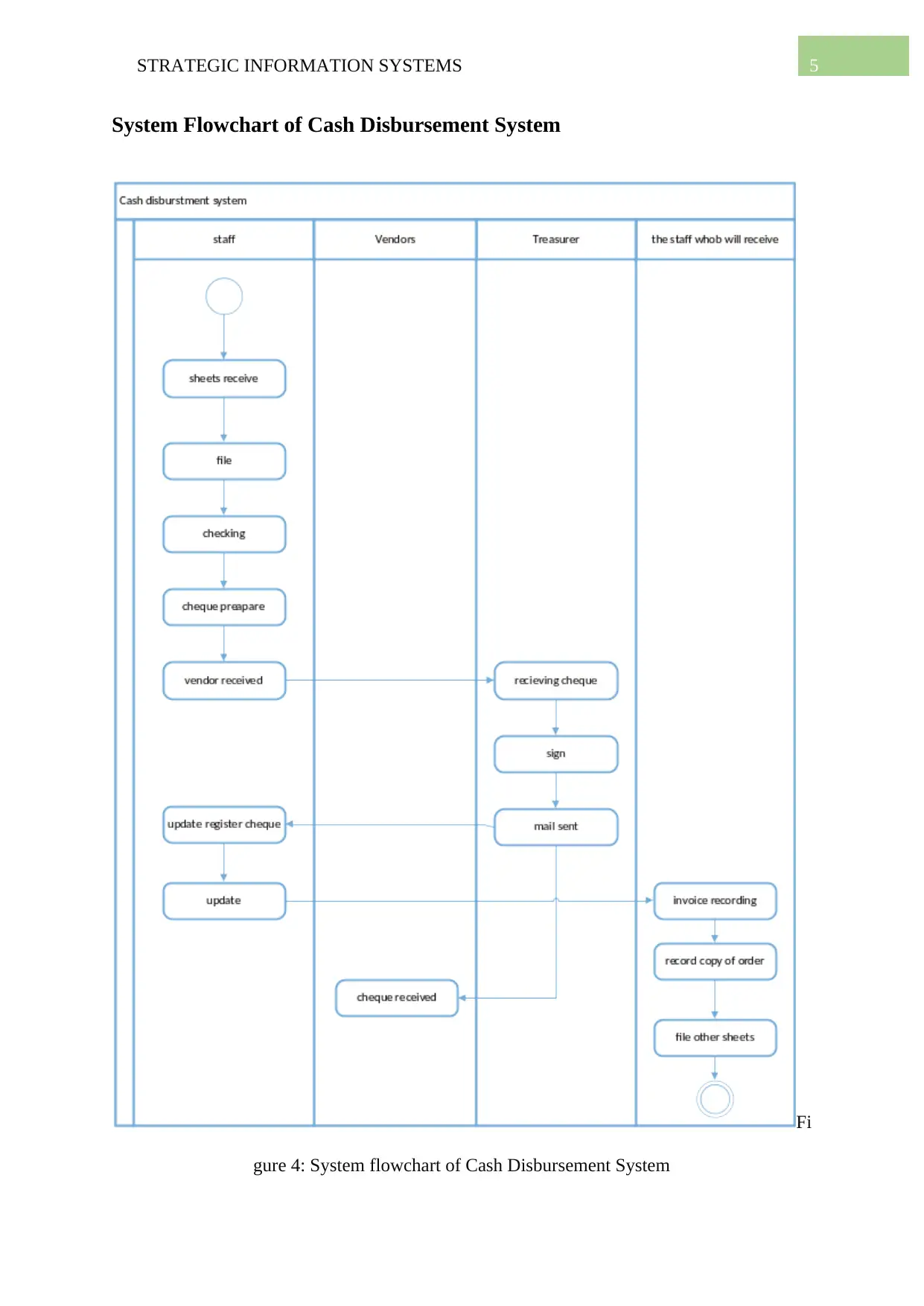
System Flowchart of Cash Disbursement System
Fi
gure 4: System flowchart of Cash Disbursement System
System Flowchart of Cash Disbursement System
Fi
gure 4: System flowchart of Cash Disbursement System
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6STRATEGIC INFORMATION SYSTEMS
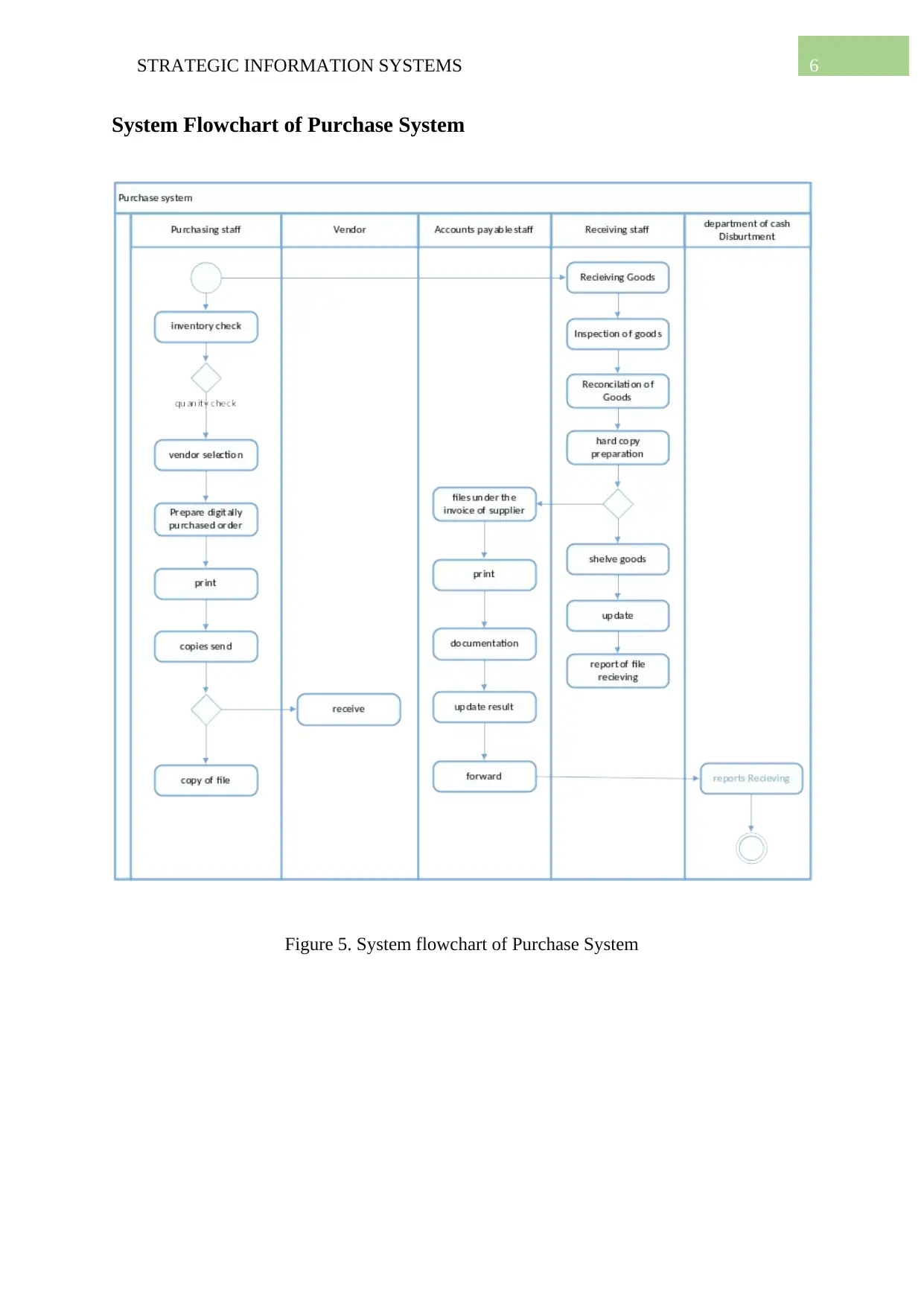
System Flowchart of Purchase System
Figure 5. System flowchart of Purchase System
System Flowchart of Purchase System
Figure 5. System flowchart of Purchase System
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7STRATEGIC INFORMATION SYSTEMS
Elucidation of the weaknesses in the internal control of the system and the
major risks coupled with the recognized weaknesses.
Weaknesses in the organization
The organization has numerous weaknesses in the system in relation to the cash
disbursement system, purchase system and the payroll system (Rusly et al. 2018). The
weaknesses pose to be major risks for the organization hence there is a need to assess the
issues on an immediate basis to allow genuine functioning of systems in the organization
(Pearlson, Saunder and Galletta 2016). The weaknesses of the organization connected to the
system are as below:
The cash disbursement system or the purchasing system of the organization is highly
complex and holds critical significance (Musgrove and Walsh 2015). Improvisation in the
system can cause disruptions in the operations of the organization. The implementation of the
changes and the way it is deployed cause problem in the operations of the organization
(DeVan et al. 2015). Few of the administrators of the company would choose to delay the
updates or some may choose segmentation of the process to prevent process shutdown or
process downtime. The many outdated systems of the company are already falling behind at
work. The lagging behind without any significant update patches will really push the
organization to face major risk. The risks will cost the organization heavily (Rezvani, Dong
and Khosravi 2017). The identified gaps in the system could be prevailing in the system
unidentified for a very long and that can cause potential damage to the organization (Ogiela
2015). The software lies deprived and unrecognized in the system and no minor software
patches are applied on it, thus extending the intensity of the danger (Cassidy 2016).
Elucidation of the weaknesses in the internal control of the system and the
major risks coupled with the recognized weaknesses.
Weaknesses in the organization
The organization has numerous weaknesses in the system in relation to the cash
disbursement system, purchase system and the payroll system (Rusly et al. 2018). The
weaknesses pose to be major risks for the organization hence there is a need to assess the
issues on an immediate basis to allow genuine functioning of systems in the organization
(Pearlson, Saunder and Galletta 2016). The weaknesses of the organization connected to the
system are as below:
The cash disbursement system or the purchasing system of the organization is highly
complex and holds critical significance (Musgrove and Walsh 2015). Improvisation in the
system can cause disruptions in the operations of the organization. The implementation of the
changes and the way it is deployed cause problem in the operations of the organization
(DeVan et al. 2015). Few of the administrators of the company would choose to delay the
updates or some may choose segmentation of the process to prevent process shutdown or
process downtime. The many outdated systems of the company are already falling behind at
work. The lagging behind without any significant update patches will really push the
organization to face major risk. The risks will cost the organization heavily (Rezvani, Dong
and Khosravi 2017). The identified gaps in the system could be prevailing in the system
unidentified for a very long and that can cause potential damage to the organization (Ogiela
2015). The software lies deprived and unrecognized in the system and no minor software
patches are applied on it, thus extending the intensity of the danger (Cassidy 2016).

8STRATEGIC INFORMATION SYSTEMS
The organization has severe weaknesses in its system that makes the system and the
software of the organization highly vulnerable to several external threats (Laudon and
Laudon 2016). The hard files which are managed might lead to potential risks for the
organization as any threat or loss can led to heavy data loss for the company. The database of
the company where majority of the data, especially where company invoices are stored is
prone to security risk finally resulting in data loss (Gillett 2016). It becomes easy for the
cyber attacker or the hacker for that matter to get access of the information inside the
computer system of the organization. Since there are vulnerabilities in the system of the
organization the hackers can easily device a path to enter in to computer system of the
company and compromise the data available in the database of the company. There are
advanced dangers that the organization faces which evolves out of modern technology
methods. The organization stores its financial records and other professional reports or
records in database which several loopholes as there are security failures in the system
(Morden 2016). The organization can only avoid data breaches by implementing security
protocols and responding efficiently and immediately to the redundant breaches noticed in the
network system.
The network vulnerabilities which can become the expected entry point for the
attackers to get into the system must be focused on to protect the system from breaches. The
organization runs major risks of cyber attacks and data theft as the organization is still using
outdated version of software which are not strong enough to prevent the external attacks. It is
easy of the attackers to gain access into the system and destroy the data of the organization.
The information in the system lies unsecured which provides the leverage to external
operators to siphon data out of the organization and misuse it. The process becomes easy for
siphoning of data which should have been difficult.
The organization has severe weaknesses in its system that makes the system and the
software of the organization highly vulnerable to several external threats (Laudon and
Laudon 2016). The hard files which are managed might lead to potential risks for the
organization as any threat or loss can led to heavy data loss for the company. The database of
the company where majority of the data, especially where company invoices are stored is
prone to security risk finally resulting in data loss (Gillett 2016). It becomes easy for the
cyber attacker or the hacker for that matter to get access of the information inside the
computer system of the organization. Since there are vulnerabilities in the system of the
organization the hackers can easily device a path to enter in to computer system of the
company and compromise the data available in the database of the company. There are
advanced dangers that the organization faces which evolves out of modern technology
methods. The organization stores its financial records and other professional reports or
records in database which several loopholes as there are security failures in the system
(Morden 2016). The organization can only avoid data breaches by implementing security
protocols and responding efficiently and immediately to the redundant breaches noticed in the
network system.
The network vulnerabilities which can become the expected entry point for the
attackers to get into the system must be focused on to protect the system from breaches. The
organization runs major risks of cyber attacks and data theft as the organization is still using
outdated version of software which are not strong enough to prevent the external attacks. It is
easy of the attackers to gain access into the system and destroy the data of the organization.
The information in the system lies unsecured which provides the leverage to external
operators to siphon data out of the organization and misuse it. The process becomes easy for
siphoning of data which should have been difficult.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9STRATEGIC INFORMATION SYSTEMS
An additional weakness of the organization that can be highlighted is the culture of
the organization. The cultural weakness of the organization leads to opening of
supplementary weakness in organizational system. Further the employees of the organization
pose to be a weakness for the company if the organizational protocols are not followed by the
employees and misleading the procedures set by the organization. When such
mismanagement occurs in the employee culture of the organization, the organization starts
facing additional unconventional risks from its own employees.
Risks
Unauthorized access
Unauthorized access is the commonest security risk that jeopardizes the network
system of the organization. The confidential and sensitive data of the organization runs a high
risk of getting stolen or compromised. The hackers or the cyber criminals use modern
advanced technology to get into the system of the organization. The acquired skills of the
hackers enable them to stay unidentified in the system for a very long time and provide an
easy method to access the information in the system.
Viruses and malware
There are many risks an organization face regarding to security threats and attacks.
The risk of virus attack or malware attack is another risk for the system of the organization.
Virus is software deliberately designed and devised in a fashion to gain easy access of the
organization’s network system. Virus enters the system without any permission from the user
and lies undetected in the system for a long time. Slowly the virus starts spreading all over
the network channel as it continuously duplicates itself within the system of the organization.
The virus slows down the system finally resulting in server crash and massive loss of data. It
An additional weakness of the organization that can be highlighted is the culture of
the organization. The cultural weakness of the organization leads to opening of
supplementary weakness in organizational system. Further the employees of the organization
pose to be a weakness for the company if the organizational protocols are not followed by the
employees and misleading the procedures set by the organization. When such
mismanagement occurs in the employee culture of the organization, the organization starts
facing additional unconventional risks from its own employees.
Risks
Unauthorized access
Unauthorized access is the commonest security risk that jeopardizes the network
system of the organization. The confidential and sensitive data of the organization runs a high
risk of getting stolen or compromised. The hackers or the cyber criminals use modern
advanced technology to get into the system of the organization. The acquired skills of the
hackers enable them to stay unidentified in the system for a very long time and provide an
easy method to access the information in the system.
Viruses and malware
There are many risks an organization face regarding to security threats and attacks.
The risk of virus attack or malware attack is another risk for the system of the organization.
Virus is software deliberately designed and devised in a fashion to gain easy access of the
organization’s network system. Virus enters the system without any permission from the user
and lies undetected in the system for a long time. Slowly the virus starts spreading all over
the network channel as it continuously duplicates itself within the system of the organization.
The virus slows down the system finally resulting in server crash and massive loss of data. It
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10STRATEGIC INFORMATION SYSTEMS
is seen in numerous cases that damage caused can be accidental resulting from poor
programming issues.
The damage faced by the organization regard to its information system, can be either
because of accidental cause or the intension can be purposeful. The actions are sometime
fueled by individual motives as an act of industrial sabotage. The employees of the
organization have all the important knowledge and information to bring about huge damage
in the company. This provides the attackers multiple opportunities to interrupt the working of
the company and damage the system severely. The impacts of the attacks can be on the
infrastructure as well as on the hardware of the organization. The attackers can easily alter
and modify the available data from the system. There are also chances of the deleting the data
for feeding in incorrect data in the system of the organization which will badly affect the
working of the system of the organization. The cyber attackers can implement logic bombs in
to the system and remove important software from the system of the organization. The
deliberate motive to harm the organization can pose to be a significant threat for the
organization. Any data loss from the database effects the organizational function and
performance and not only that, the organization runs a extra risk of facing threats from the
data if they are used against them. The threat from the vandalism lies in fact that this
organization has been temporarily denied the access to the system and the resources for some
of the individuals. The major damages as known cause severe issues for the organization, the
minor damages cannot always be ignored or denied. A cumulative effect of the minor
damages builds up to a major damage that affects the organization intensely (Chakraborty
2017). The major damages results due to human errors in handling the system and the data of
the system. The employees of the company sometimes misuse the data available to them or
cause accidental damage which in turn affects the business or the enterprise massively. Any
kind of minor or major human errors on the information and network system of the company
is seen in numerous cases that damage caused can be accidental resulting from poor
programming issues.
The damage faced by the organization regard to its information system, can be either
because of accidental cause or the intension can be purposeful. The actions are sometime
fueled by individual motives as an act of industrial sabotage. The employees of the
organization have all the important knowledge and information to bring about huge damage
in the company. This provides the attackers multiple opportunities to interrupt the working of
the company and damage the system severely. The impacts of the attacks can be on the
infrastructure as well as on the hardware of the organization. The attackers can easily alter
and modify the available data from the system. There are also chances of the deleting the data
for feeding in incorrect data in the system of the organization which will badly affect the
working of the system of the organization. The cyber attackers can implement logic bombs in
to the system and remove important software from the system of the organization. The
deliberate motive to harm the organization can pose to be a significant threat for the
organization. Any data loss from the database effects the organizational function and
performance and not only that, the organization runs a extra risk of facing threats from the
data if they are used against them. The threat from the vandalism lies in fact that this
organization has been temporarily denied the access to the system and the resources for some
of the individuals. The major damages as known cause severe issues for the organization, the
minor damages cannot always be ignored or denied. A cumulative effect of the minor
damages builds up to a major damage that affects the organization intensely (Chakraborty
2017). The major damages results due to human errors in handling the system and the data of
the system. The employees of the company sometimes misuse the data available to them or
cause accidental damage which in turn affects the business or the enterprise massively. Any
kind of minor or major human errors on the information and network system of the company

11STRATEGIC INFORMATION SYSTEMS
massively impacts the security of the organization. Purposeful manmade threats damage the
security structures of the enterprise by making the enterprise’s network vulnerable (Shi and
Li 2016). Then, the security threats faced by the organizations can be effectively mitigated.
Sniffing and Spoofing
Sniffing tools are used to sniff on all the data packets that flow through the network
channel. The attackers try to tap the line of flow of the data packets in the network channel to
get valuable information from the data packets. Sniffing can be done by the attackers or by an
employee form the organization can also find a vulnerable spot to sniff on the data packets
(Niemelä et al. 2016). When the organization performs diagnosis of network issues by
capturing data which are transmitted over the network of the company, employees can
unethically use it to gather passwords and data to harm the company for selfish motives.
When information is caught in transit, the malicious user easily gains access into the network
system of the business enterprise. If the organization’s switch port is open, it becomes easy
for the sniffers to sniff the data out of the system (Hadid 2015). Anyone within the network
system can get access to the data packets. Snoop servers are used to capture network traffic
for analysis. Snooping protocol monitors information on a computer bus to ensure efficient
processing. The attackers can study the flow of traffic in the system, protected and
unprotected version of it (Anilkumar et al. 2019). If there are excess vulnerable spots within
the system, the right condition along with right protocols provides the attackers the advantage
to easily collect information. The collected data or the information can be further used to
project additional attacks on the company or cause destruction in the server system of the
business or enterprise. To detect sniffers in the network system of the enterprise becomes
hard for the enterprise to identify. Sniffing can be done on web traffics, FTP passwords, the
massively impacts the security of the organization. Purposeful manmade threats damage the
security structures of the enterprise by making the enterprise’s network vulnerable (Shi and
Li 2016). Then, the security threats faced by the organizations can be effectively mitigated.
Sniffing and Spoofing
Sniffing tools are used to sniff on all the data packets that flow through the network
channel. The attackers try to tap the line of flow of the data packets in the network channel to
get valuable information from the data packets. Sniffing can be done by the attackers or by an
employee form the organization can also find a vulnerable spot to sniff on the data packets
(Niemelä et al. 2016). When the organization performs diagnosis of network issues by
capturing data which are transmitted over the network of the company, employees can
unethically use it to gather passwords and data to harm the company for selfish motives.
When information is caught in transit, the malicious user easily gains access into the network
system of the business enterprise. If the organization’s switch port is open, it becomes easy
for the sniffers to sniff the data out of the system (Hadid 2015). Anyone within the network
system can get access to the data packets. Snoop servers are used to capture network traffic
for analysis. Snooping protocol monitors information on a computer bus to ensure efficient
processing. The attackers can study the flow of traffic in the system, protected and
unprotected version of it (Anilkumar et al. 2019). If there are excess vulnerable spots within
the system, the right condition along with right protocols provides the attackers the advantage
to easily collect information. The collected data or the information can be further used to
project additional attacks on the company or cause destruction in the server system of the
business or enterprise. To detect sniffers in the network system of the enterprise becomes
hard for the enterprise to identify. Sniffing can be done on web traffics, FTP passwords, the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





