Bell Studio Case Study: Strategic Information Systems Analysis Report
VerifiedAdded on 2023/01/04
|13
|2206
|65
Report
AI Summary
This report presents a case study analysis of Bell Studio's strategic information systems, focusing on its centralized system for managing art supplies. It examines the company's transaction, financial, and management cycles, along with its account reporting procedures. The report utilizes Data Flow Diagrams (DFDs) and system flowcharts to illustrate the working operations within the purchasing, cash disbursements, and payroll systems. It identifies internal control weaknesses and associated risks, such as system failures, fraud, and human error, and proposes mitigation strategies. The analysis covers the centralized management system's advantages and disadvantages, emphasizing the need for improved security measures and updated information systems to address the risks associated with the current centralized approach. The report concludes by summarizing the findings and emphasizing the importance of a robust information system for Bell Studio's continued success.

Running head: STRATEGIC INFORMATION FOR BUSINESS AND ENTERPRISE
Strategic Information for Business and Enterprise
Name of Student-
Name of University-
Author’s Note
Strategic Information for Business and Enterprise
Name of Student-
Name of University-
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1STRATEGIC INFORMATION FOR BUSINESS AND ENTERPRISE
Executive Summary
The main role of a business analyst is to carry out all the working process or operations
in an enterprise. Bell Studio is an enterprise that deals with supplies of art materials.
This enterprise follows its own centralized system or maintain its information system in
the enterprise and the business analyst of the enterprise has the responsibility to
maintain its working process. The report consists of the working operations of the Bell
Studio defining the transaction cycle of the enterprise, along with the financial cycle, the
management cycle, and the account reporting procedure of the Bell Studio. Details of
the working operations are explained in this report with the help of DFD (Data Flow
Diagram) and in the form of system flowchart.
Executive Summary
The main role of a business analyst is to carry out all the working process or operations
in an enterprise. Bell Studio is an enterprise that deals with supplies of art materials.
This enterprise follows its own centralized system or maintain its information system in
the enterprise and the business analyst of the enterprise has the responsibility to
maintain its working process. The report consists of the working operations of the Bell
Studio defining the transaction cycle of the enterprise, along with the financial cycle, the
management cycle, and the account reporting procedure of the Bell Studio. Details of
the working operations are explained in this report with the help of DFD (Data Flow
Diagram) and in the form of system flowchart.

2STRATEGIC INFORMATION FOR BUSINESS AND ENTERPRISE
Table of Contents
1. Introduction....................................................................................................................3
2. Data Flow Diagram for the Purchasing system and System of Cash Disbursements. .4
3. Data Flow Diagram of Payroll System...........................................................................5
4. System Flowchart of Purchases System.......................................................................6
5. System Flowchart of Cash Disbursements System......................................................7
6. System Flowchart of Payroll System.............................................................................8
7. Internal Control Weakness and Risk Associated..........................................................8
8. Conclusion...................................................................................................................10
Reference........................................................................................................................11
Table of Contents
1. Introduction....................................................................................................................3
2. Data Flow Diagram for the Purchasing system and System of Cash Disbursements. .4
3. Data Flow Diagram of Payroll System...........................................................................5
4. System Flowchart of Purchases System.......................................................................6
5. System Flowchart of Cash Disbursements System......................................................7
6. System Flowchart of Payroll System.............................................................................8
7. Internal Control Weakness and Risk Associated..........................................................8
8. Conclusion...................................................................................................................10
Reference........................................................................................................................11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3STRATEGIC INFORMATION FOR BUSINESS AND ENTERPRISE
1. Introduction
Case study of Bell Studio states that the working process of the business is
carried out with a centralized information system that is being worked in the
organization. The centralized system used in the Bell Studio includes centralized
management that shows the leadership form of the clerks involved in the system. The
organization has many management systems and reporting system by which the
centralized system is being updated and all the information is stored in the system by
the administrators of the organization.
The centralized system in this particular organization helps in decision making of
the system and keeping the authority of the organization on top. The centralized system
that is being followed in the Bell studio includes many disadvantages that leads
business analyst of the Bell Studio to evaluate the business processes and operations
that are carried out in the organization.
This report is conducted on the behalf of the business analyst of Bell Studio so
that the business processes can be evaluated and the business risks that might occur in
the business operations can be evaluated. The evaluation of the processes is done by
analysing the business processes diagrams such as DFD diagrams and Flowchart
diagram of three main sub-systems conducted in Bell Studio. This report also states the
details of all the risks or the drawbacks that the company faces because of the
centralized information system in the working procedure of the Bell Studio. The security
measures are also mentioned in this report that can be taken on the behalf of Bell
Studio management for conducting its business processes.
1. Introduction
Case study of Bell Studio states that the working process of the business is
carried out with a centralized information system that is being worked in the
organization. The centralized system used in the Bell Studio includes centralized
management that shows the leadership form of the clerks involved in the system. The
organization has many management systems and reporting system by which the
centralized system is being updated and all the information is stored in the system by
the administrators of the organization.
The centralized system in this particular organization helps in decision making of
the system and keeping the authority of the organization on top. The centralized system
that is being followed in the Bell studio includes many disadvantages that leads
business analyst of the Bell Studio to evaluate the business processes and operations
that are carried out in the organization.
This report is conducted on the behalf of the business analyst of Bell Studio so
that the business processes can be evaluated and the business risks that might occur in
the business operations can be evaluated. The evaluation of the processes is done by
analysing the business processes diagrams such as DFD diagrams and Flowchart
diagram of three main sub-systems conducted in Bell Studio. This report also states the
details of all the risks or the drawbacks that the company faces because of the
centralized information system in the working procedure of the Bell Studio. The security
measures are also mentioned in this report that can be taken on the behalf of Bell
Studio management for conducting its business processes.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
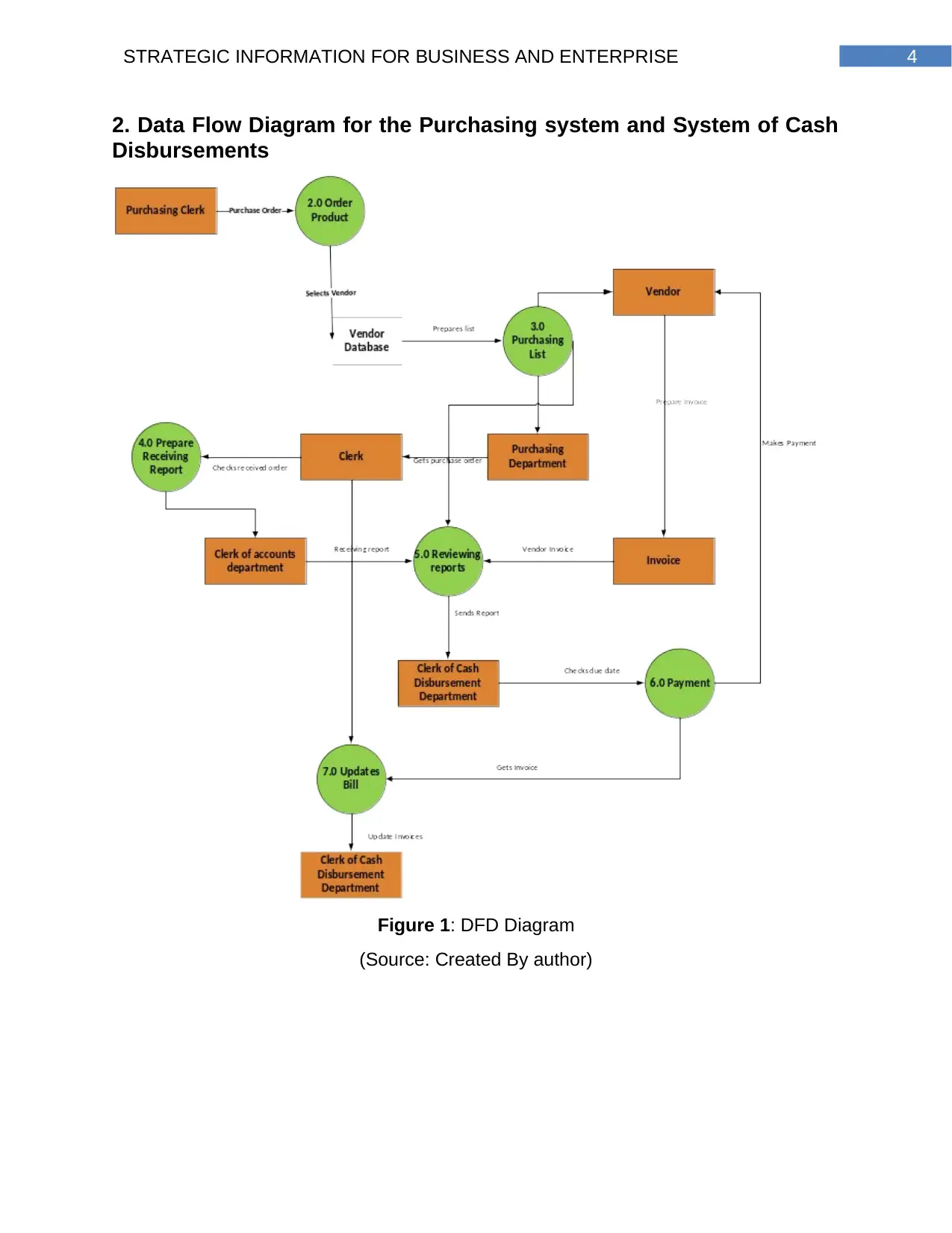
4STRATEGIC INFORMATION FOR BUSINESS AND ENTERPRISE
2. Data Flow Diagram for the Purchasing system and System of Cash
Disbursements
Figure 1: DFD Diagram
(Source: Created By author)
2. Data Flow Diagram for the Purchasing system and System of Cash
Disbursements
Figure 1: DFD Diagram
(Source: Created By author)
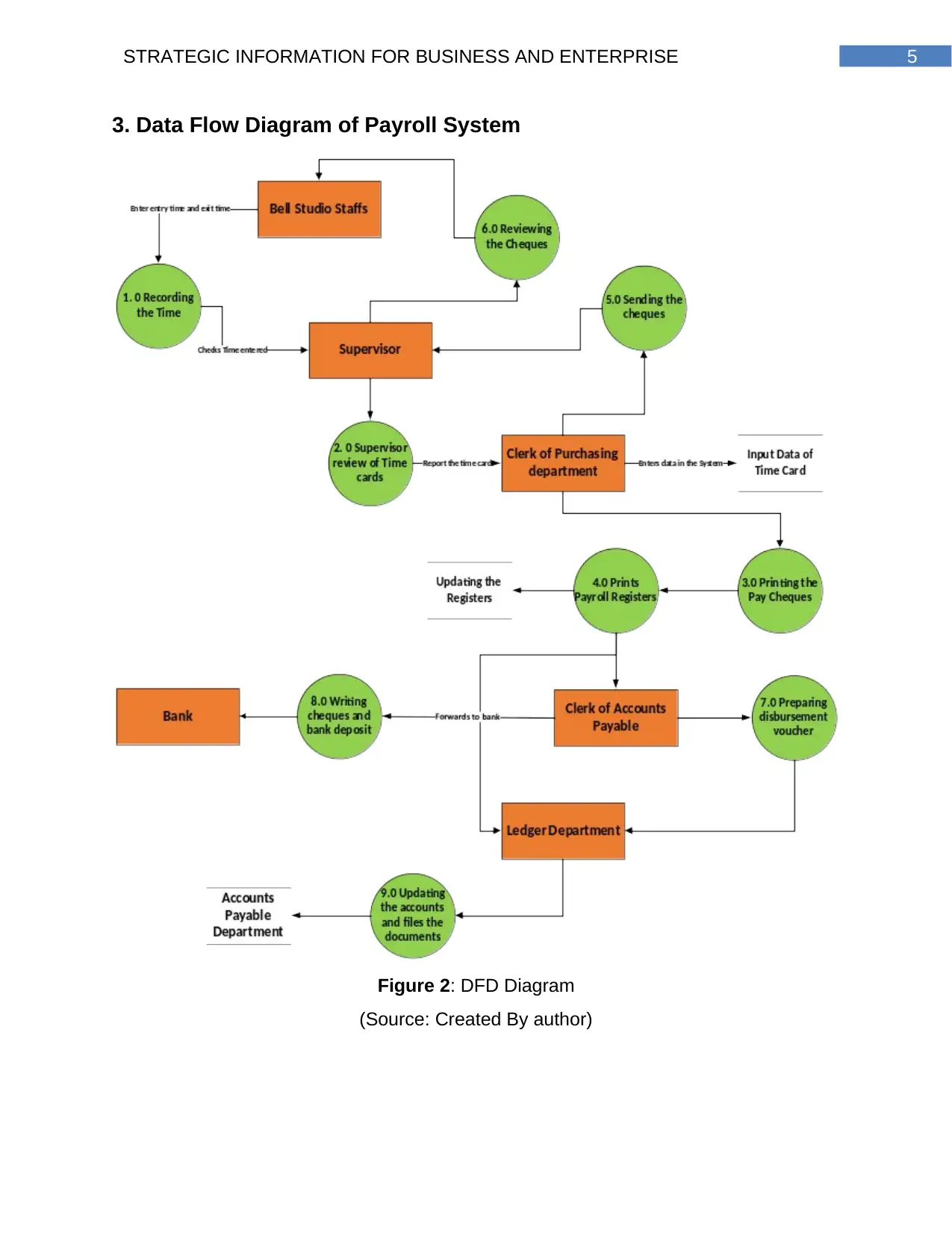
5STRATEGIC INFORMATION FOR BUSINESS AND ENTERPRISE
3. Data Flow Diagram of Payroll System
Figure 2: DFD Diagram
(Source: Created By author)
3. Data Flow Diagram of Payroll System
Figure 2: DFD Diagram
(Source: Created By author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
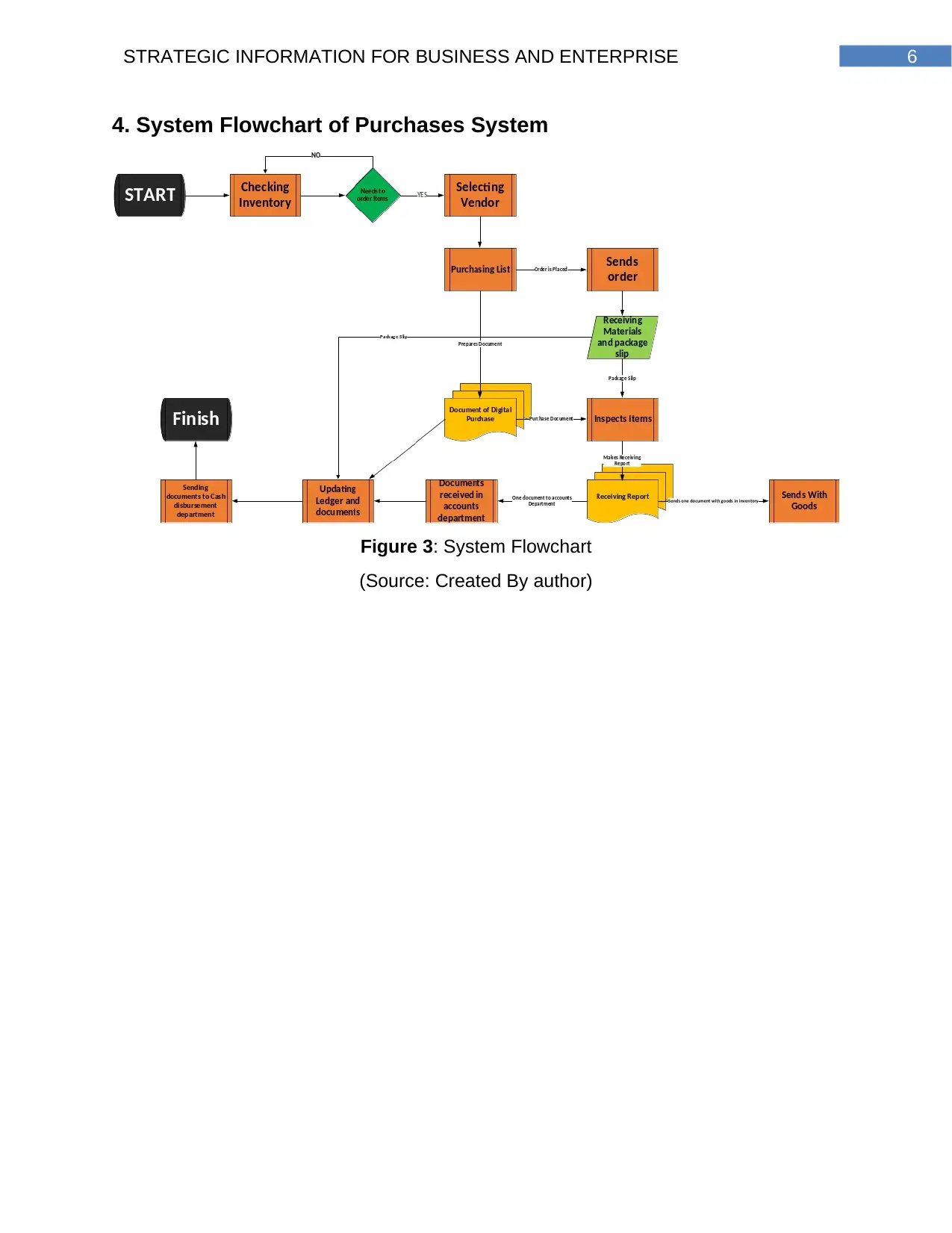
6STRATEGIC INFORMATION FOR BUSINESS AND ENTERPRISE
4. System Flowchart of Purchases System
Figure 3: System Flowchart
(Source: Created By author)
4. System Flowchart of Purchases System
Figure 3: System Flowchart
(Source: Created By author)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
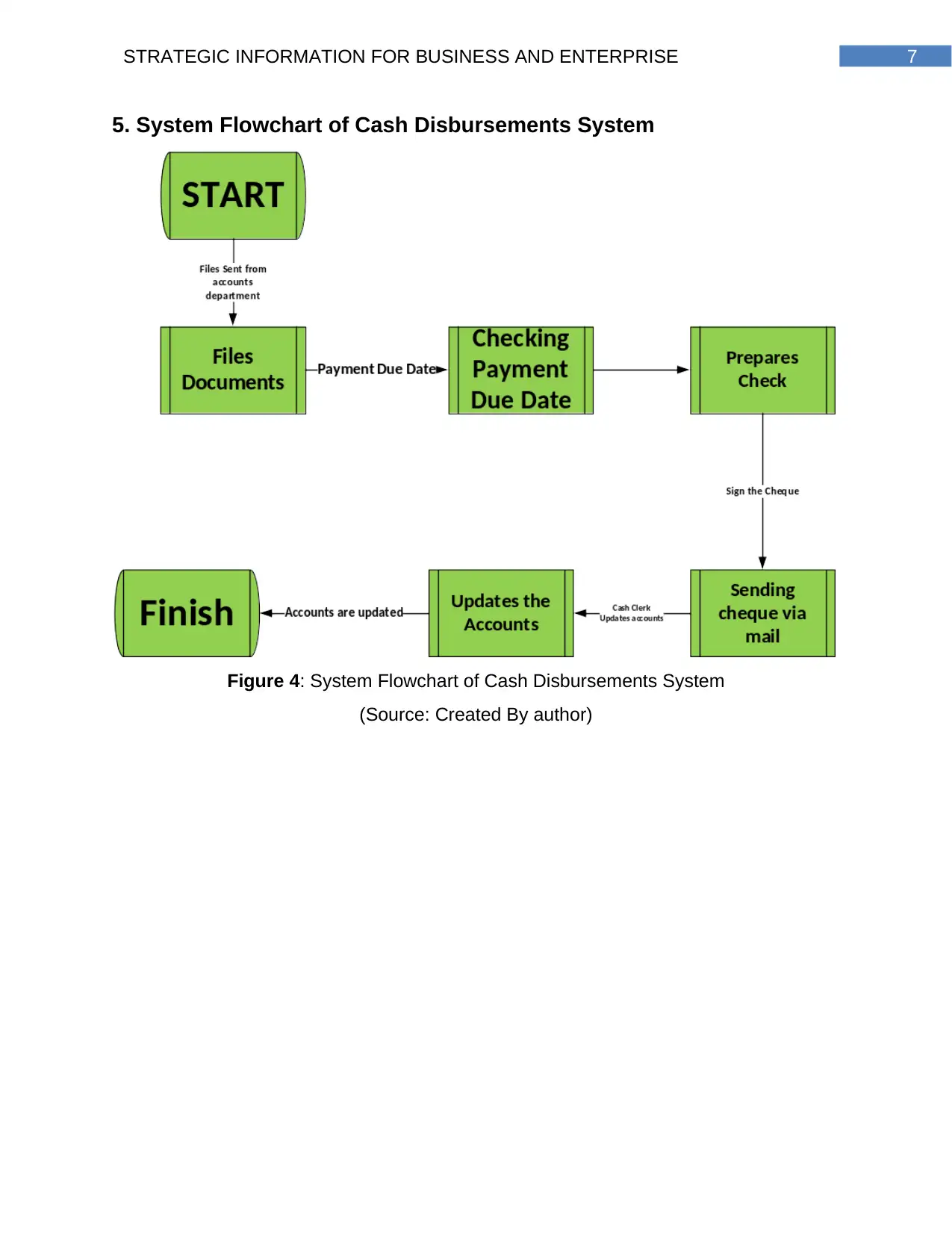
7STRATEGIC INFORMATION FOR BUSINESS AND ENTERPRISE
5. System Flowchart of Cash Disbursements System
Figure 4: System Flowchart of Cash Disbursements System
(Source: Created By author)
5. System Flowchart of Cash Disbursements System
Figure 4: System Flowchart of Cash Disbursements System
(Source: Created By author)
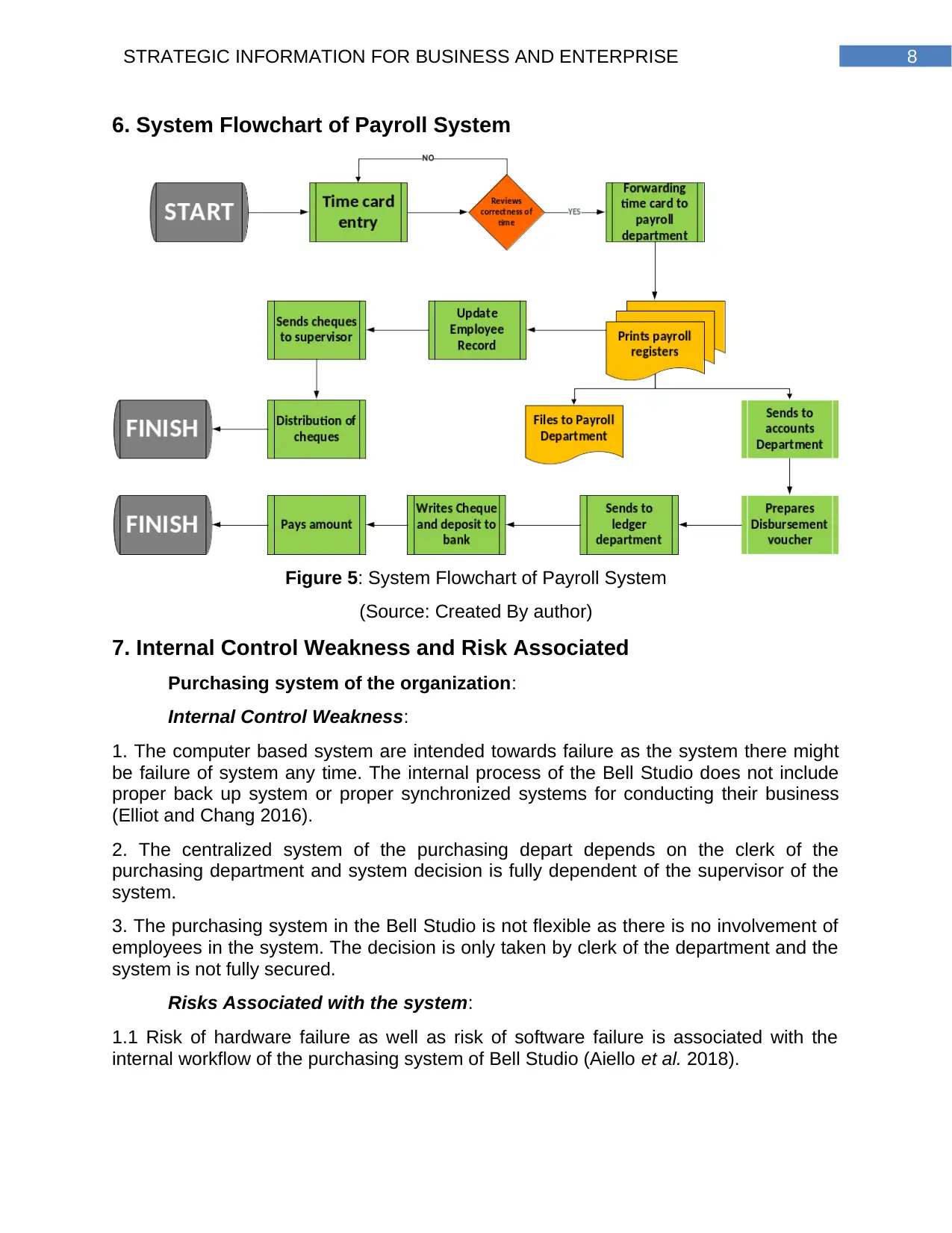
8STRATEGIC INFORMATION FOR BUSINESS AND ENTERPRISE
6. System Flowchart of Payroll System
Figure 5: System Flowchart of Payroll System
(Source: Created By author)
7. Internal Control Weakness and Risk Associated
Purchasing system of the organization:
Internal Control Weakness:
1. The computer based system are intended towards failure as the system there might
be failure of system any time. The internal process of the Bell Studio does not include
proper back up system or proper synchronized systems for conducting their business
(Elliot and Chang 2016).
2. The centralized system of the purchasing depart depends on the clerk of the
purchasing department and system decision is fully dependent of the supervisor of the
system.
3. The purchasing system in the Bell Studio is not flexible as there is no involvement of
employees in the system. The decision is only taken by clerk of the department and the
system is not fully secured.
Risks Associated with the system:
1.1 Risk of hardware failure as well as risk of software failure is associated with the
internal workflow of the purchasing system of Bell Studio (Aiello et al. 2018).
6. System Flowchart of Payroll System
Figure 5: System Flowchart of Payroll System
(Source: Created By author)
7. Internal Control Weakness and Risk Associated
Purchasing system of the organization:
Internal Control Weakness:
1. The computer based system are intended towards failure as the system there might
be failure of system any time. The internal process of the Bell Studio does not include
proper back up system or proper synchronized systems for conducting their business
(Elliot and Chang 2016).
2. The centralized system of the purchasing depart depends on the clerk of the
purchasing department and system decision is fully dependent of the supervisor of the
system.
3. The purchasing system in the Bell Studio is not flexible as there is no involvement of
employees in the system. The decision is only taken by clerk of the department and the
system is not fully secured.
Risks Associated with the system:
1.1 Risk of hardware failure as well as risk of software failure is associated with the
internal workflow of the purchasing system of Bell Studio (Aiello et al. 2018).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9STRATEGIC INFORMATION FOR BUSINESS AND ENTERPRISE
This risk can be mitigated by keeping extra back up system for conducting the
business process in the organization. There must be proper backup system and
hardware system that for dealing with the operations in the business (Conte et al. 2017).
2.1 As a system is Bell Studio is a centralized system, risk of fraud and risk of getting
virus and malware in the computer system is very common.
This risk can be mitigated by installing proper anti-virus in the working system so
that the virus and malwares can be removed. There should be proper password and
user id system for each department and clerk must be given training about how to use
the system and not to share their personal user name or passwords with others.
Cash Disbursement system of the organization:
Internal Control Weakness:
1. The cheques in the cash disbursement system are printed and written manually by
the clerks and that creates an internal weakness in the system. Cheque payment is not
very appropriate for handling a system.
2. The cheques are sent to the supplier through mail which also serves as internal
weakness of the system. Mail can be hacked and read by any unauthorized users in the
network.
3. The files stored in each department are stored manually and that is an internal
weakness. The files might get misplaced or they can be deliberately removed
(Rittinghouse and Ransome 2017).
Risks Associated with the system:
1.1 Risks of having human error or carelessness is involved in the system. The clerks
might not be effective enough to do their work properly (Larimi, Haghifam and
Moradkhani 2016).
The company can use an advanced information technology such as block chain
technology or accounting information system for conducting its business processes
(Cohn et al. 2017).
2.1 Risk of fraud detecting and risk of security issues (Yau and Ives 2016).
This risk can be mitigated through implementing automatic system in the
company. The employees can be involved for taking decisions for the company and
they can be involved in taking major decisions of the company (Chmielewski and
Kitchen 2017).
Payroll system of the organization:
Internal Control Weakness:
1. Internal weakness includes employees writing their own office duty hours in the time
card of the company. The employees might not be fair at all the time to entry their time
and date of working (Peng et al. 2016).
This risk can be mitigated by keeping extra back up system for conducting the
business process in the organization. There must be proper backup system and
hardware system that for dealing with the operations in the business (Conte et al. 2017).
2.1 As a system is Bell Studio is a centralized system, risk of fraud and risk of getting
virus and malware in the computer system is very common.
This risk can be mitigated by installing proper anti-virus in the working system so
that the virus and malwares can be removed. There should be proper password and
user id system for each department and clerk must be given training about how to use
the system and not to share their personal user name or passwords with others.
Cash Disbursement system of the organization:
Internal Control Weakness:
1. The cheques in the cash disbursement system are printed and written manually by
the clerks and that creates an internal weakness in the system. Cheque payment is not
very appropriate for handling a system.
2. The cheques are sent to the supplier through mail which also serves as internal
weakness of the system. Mail can be hacked and read by any unauthorized users in the
network.
3. The files stored in each department are stored manually and that is an internal
weakness. The files might get misplaced or they can be deliberately removed
(Rittinghouse and Ransome 2017).
Risks Associated with the system:
1.1 Risks of having human error or carelessness is involved in the system. The clerks
might not be effective enough to do their work properly (Larimi, Haghifam and
Moradkhani 2016).
The company can use an advanced information technology such as block chain
technology or accounting information system for conducting its business processes
(Cohn et al. 2017).
2.1 Risk of fraud detecting and risk of security issues (Yau and Ives 2016).
This risk can be mitigated through implementing automatic system in the
company. The employees can be involved for taking decisions for the company and
they can be involved in taking major decisions of the company (Chmielewski and
Kitchen 2017).
Payroll system of the organization:
Internal Control Weakness:
1. Internal weakness includes employees writing their own office duty hours in the time
card of the company. The employees might not be fair at all the time to entry their time
and date of working (Peng et al. 2016).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10STRATEGIC INFORMATION FOR BUSINESS AND ENTERPRISE
2. Cheque distribution is another internal weakness of the system as there might be
chance of misplacing the cheques before handling them to the staffs (Xiao et al. 2018).
Risks Associated with the system:
1.1 Risk includes slowing down the processes of the Bell Studio. As there are many
management processes and the processes are only initiated with the decisions of the
clerk, it might lead to slow down the processes of the Bell Studio (Gandy 2016).
This can be mitigated by using some other information system for the enterprise which
is more secured and reliable (Tian 2017).
2.1 Risk of staff being dishonest to the system. The system uses time card to record
their timing in the office and that might not always be honest (Pappas et al. 2017).
8. Conclusion
The working process of the Bell Studio includes a centralized working process of
the system that consists of different working procedure of the organization. There are
many locations where outlet of Bell Studio is located and for conducting the processes
of Bell Studio, there is a need to have proper information system in the organization.
The Studio works with art supplies materials and includes many processes that
deals with the financial cycles, the transaction cycles and with the management cycle of
the process in the system.
This report above states the details of all the transaction process, the purchasing
process, the reporting of the processes and the payroll system that are included in the
system. The weakness or the drawbacks that are associated with the internal processes
of the system are also discussed in this report stating how the risks can be mitigated in
the enterprise.
2. Cheque distribution is another internal weakness of the system as there might be
chance of misplacing the cheques before handling them to the staffs (Xiao et al. 2018).
Risks Associated with the system:
1.1 Risk includes slowing down the processes of the Bell Studio. As there are many
management processes and the processes are only initiated with the decisions of the
clerk, it might lead to slow down the processes of the Bell Studio (Gandy 2016).
This can be mitigated by using some other information system for the enterprise which
is more secured and reliable (Tian 2017).
2.1 Risk of staff being dishonest to the system. The system uses time card to record
their timing in the office and that might not always be honest (Pappas et al. 2017).
8. Conclusion
The working process of the Bell Studio includes a centralized working process of
the system that consists of different working procedure of the organization. There are
many locations where outlet of Bell Studio is located and for conducting the processes
of Bell Studio, there is a need to have proper information system in the organization.
The Studio works with art supplies materials and includes many processes that
deals with the financial cycles, the transaction cycles and with the management cycle of
the process in the system.
This report above states the details of all the transaction process, the purchasing
process, the reporting of the processes and the payroll system that are included in the
system. The weakness or the drawbacks that are associated with the internal processes
of the system are also discussed in this report stating how the risks can be mitigated in
the enterprise.

11STRATEGIC INFORMATION FOR BUSINESS AND ENTERPRISE
Reference
Aiello, G., Giovino, I., Vallone, M., Catania, P. and Argento, A., 2018. A decision support
system based on multisensor data fusion for sustainable greenhouse
management. Journal of Cleaner Production, 172, pp.4057-4065.
Chmielewski, T. and Kitchen, J., iControl Networks Inc, 2017. Generating risk profile
using data of home monitoring and security system. U.S.
Cohn, A.W., Battles, R.E., Proft, D. and Shumate, S.W., iControl Networks Inc,
2017. Method and system for automatically providing alternate network access for
telecommunications. U.S. Patent Application 15/452,149.
Conte de Leon, D., Stalick, A.Q., Jillepalli, A.A., Haney, M.A. and Sheldon, F.T., 2017.
Blockchain: properties and misconceptions. Asia Pacific Journal of Innovation and
Entrepreneurship, 11(3), pp.286-300.
Duncan, R.A.K. and Whittington, M., 2016. Enhancing cloud security and privacy: the
power and the weakness of the audit trail. CLOUD COMPUTING 2016.
Elliot, M. and Chang, A., Palantir Technologies Inc, 2016. Computer-implemented
systems and methods for comparing and associating objects. U.S. Patent 9,286,373.
Gandy, O.H., 2016. Coming to terms with chance: Engaging rational discrimination and
cumulative disadvantage. Routledge.
Kim, J.B., Lee, J.J. and Park, J.C., 2016. Internal control weakness and the
asymmetrical behavior of selling, general, and administrative costs. General, and
Administrative Costs (December 3, 2016).
Larimi, S.M.M., Haghifam, M.R. and Moradkhani, A., 2016. Risk-based reconfiguration
of active electric distribution networks. IET Generation, Transmission &
Distribution, 10(4), pp.1006-1015.
Pappas, Y., Anandan, C., Liu, J., Car, J., Sheikh, A. and Majeed, A., 2017. Computer-
assisted history-taking systems (CAHTS) in health care: benefits, risks and potential for
further development. Journal of Innovation in Health Informatics.
Peng, Z., Lu, Y., Miller, A., Johnson, C. and Zhao, T., 2016. Risk assessment of railway
transportation systems using timed fault trees. Quality and Reliability Engineering
International, 32(1), pp.181-194.
Rittinghouse, J.W. and Ransome, J.F., 2017. Cloud computing: implementation,
management, and security. CRC press.
Tian, F., 2017, June. A supply chain traceability system for food safety based on
HACCP, blockchain & Internet of things. In 2017 International Conference on Service
Systems and Service Management (pp. 1-6). IEEE.
Xiao, X., Chen, C., Sangaiah, A.K., Hu, G., Ye, R. and Jiang, Y., 2018. CenLocShare: a
centralized privacy-preserving location-sharing system for mobile online social
networks. Future Generation Computer Systems, 86, pp.863-872.
Reference
Aiello, G., Giovino, I., Vallone, M., Catania, P. and Argento, A., 2018. A decision support
system based on multisensor data fusion for sustainable greenhouse
management. Journal of Cleaner Production, 172, pp.4057-4065.
Chmielewski, T. and Kitchen, J., iControl Networks Inc, 2017. Generating risk profile
using data of home monitoring and security system. U.S.
Cohn, A.W., Battles, R.E., Proft, D. and Shumate, S.W., iControl Networks Inc,
2017. Method and system for automatically providing alternate network access for
telecommunications. U.S. Patent Application 15/452,149.
Conte de Leon, D., Stalick, A.Q., Jillepalli, A.A., Haney, M.A. and Sheldon, F.T., 2017.
Blockchain: properties and misconceptions. Asia Pacific Journal of Innovation and
Entrepreneurship, 11(3), pp.286-300.
Duncan, R.A.K. and Whittington, M., 2016. Enhancing cloud security and privacy: the
power and the weakness of the audit trail. CLOUD COMPUTING 2016.
Elliot, M. and Chang, A., Palantir Technologies Inc, 2016. Computer-implemented
systems and methods for comparing and associating objects. U.S. Patent 9,286,373.
Gandy, O.H., 2016. Coming to terms with chance: Engaging rational discrimination and
cumulative disadvantage. Routledge.
Kim, J.B., Lee, J.J. and Park, J.C., 2016. Internal control weakness and the
asymmetrical behavior of selling, general, and administrative costs. General, and
Administrative Costs (December 3, 2016).
Larimi, S.M.M., Haghifam, M.R. and Moradkhani, A., 2016. Risk-based reconfiguration
of active electric distribution networks. IET Generation, Transmission &
Distribution, 10(4), pp.1006-1015.
Pappas, Y., Anandan, C., Liu, J., Car, J., Sheikh, A. and Majeed, A., 2017. Computer-
assisted history-taking systems (CAHTS) in health care: benefits, risks and potential for
further development. Journal of Innovation in Health Informatics.
Peng, Z., Lu, Y., Miller, A., Johnson, C. and Zhao, T., 2016. Risk assessment of railway
transportation systems using timed fault trees. Quality and Reliability Engineering
International, 32(1), pp.181-194.
Rittinghouse, J.W. and Ransome, J.F., 2017. Cloud computing: implementation,
management, and security. CRC press.
Tian, F., 2017, June. A supply chain traceability system for food safety based on
HACCP, blockchain & Internet of things. In 2017 International Conference on Service
Systems and Service Management (pp. 1-6). IEEE.
Xiao, X., Chen, C., Sangaiah, A.K., Hu, G., Ye, R. and Jiang, Y., 2018. CenLocShare: a
centralized privacy-preserving location-sharing system for mobile online social
networks. Future Generation Computer Systems, 86, pp.863-872.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




