HND Computing: IT Security Risks, Audit & Policies in Organizations
VerifiedAdded on 2023/06/03
|21
|5652
|106
Report
AI Summary
This report examines organizational information security risks and policies, focusing on a retail shop in East London and its "Shopaholics" application. It identifies potential risks like data theft, DoS attacks, and employee vandalism, and proposes security measures such as strong passwords, antivirus programs, firewalls, and data backup systems. The report discusses the impacts of incorrect firewall and VPN configurations, DMZ setup, static IP configuration, and network address translation. Data protection procedures and organizational regulations are outlined, along with the benefits of network monitoring systems and the ISO 31000 risk management methodology. A proposed security policy, including a security council and a real-time notification system, is presented, followed by a disaster recovery plan and the role of stakeholders in security audits. The document is a student contribution available on Desklib, a platform offering study tools and resources for students.

Running head: ORGANIZATIONAL INFORMATION SECURITY RISKS AND POLICIES
ORGANIZATIONAL INFORMATION SECURITY RISKS AND POLICIES
Name of the student:
Name of the university:
Author note:
ORGANIZATIONAL INFORMATION SECURITY RISKS AND POLICIES
Name of the student:
Name of the university:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
ORGANIZATIONAL INFORMATION SECURITY RISKS AND POLICIES
Executive summary:
Information security is one of the most important concerns of the companies in today’s world.
There are different kinds of issues that are being faced by the organizations regarding data theft
and security breach. Therefore, it is of utmost importance that the organizations come up with
innovative security policies, ensure that there is a proper data backup system, and risk
management strategy within the working operations. The following report will study the working
of a retail shop in East London, which uses an application called shopaholics, and study the
different threats related to the application. The paragraphs will highlight how the disaster
recovery can be carried out in the organization and the security systems can be designed keeping
in mind the recent DoS attack and virus infection issue faced by the retail shop. By the end of the
report, the reader will have a clear idea on the organizational security measures that can be
implemented within the organization.
ORGANIZATIONAL INFORMATION SECURITY RISKS AND POLICIES
Executive summary:
Information security is one of the most important concerns of the companies in today’s world.
There are different kinds of issues that are being faced by the organizations regarding data theft
and security breach. Therefore, it is of utmost importance that the organizations come up with
innovative security policies, ensure that there is a proper data backup system, and risk
management strategy within the working operations. The following report will study the working
of a retail shop in East London, which uses an application called shopaholics, and study the
different threats related to the application. The paragraphs will highlight how the disaster
recovery can be carried out in the organization and the security systems can be designed keeping
in mind the recent DoS attack and virus infection issue faced by the retail shop. By the end of the
report, the reader will have a clear idea on the organizational security measures that can be
implemented within the organization.

2
ORGANIZATIONAL INFORMATION SECURITY RISKS AND POLICIES
Table of Contents
Introduction:....................................................................................................................................4
Potential risks for the shopaholic’s application:..............................................................................4
P1. IT industry risks:....................................................................................................................5
Data theft:....................................................................................................................................5
DOS attacks:................................................................................................................................5
Employee Vandalism:..................................................................................................................6
P2. Security measures needed for the retail shop:.......................................................................6
Setting strong passwords in the servers and workstations:......................................................6
Usage of strong enterprise antivirus programs and network firewalls:...................................6
Use of proper data back up and disaster management system:...............................................7
Risk assessment procedure for the retail shop:................................................................................7
P3. Potential impacts of incorrect firewall and VPN configuration:...............................................8
DMZ configuration:.....................................................................................................................9
Static IP configuration:..............................................................................................................10
Network address translation (NAT) configuration and its advantages:.....................................11
P5. Data protection procedures:.................................................................................................11
P6. Processes of data protection:...............................................................................................11
Organizational regulations:........................................................................................................12
ORGANIZATIONAL INFORMATION SECURITY RISKS AND POLICIES
Table of Contents
Introduction:....................................................................................................................................4
Potential risks for the shopaholic’s application:..............................................................................4
P1. IT industry risks:....................................................................................................................5
Data theft:....................................................................................................................................5
DOS attacks:................................................................................................................................5
Employee Vandalism:..................................................................................................................6
P2. Security measures needed for the retail shop:.......................................................................6
Setting strong passwords in the servers and workstations:......................................................6
Usage of strong enterprise antivirus programs and network firewalls:...................................6
Use of proper data back up and disaster management system:...............................................7
Risk assessment procedure for the retail shop:................................................................................7
P3. Potential impacts of incorrect firewall and VPN configuration:...............................................8
DMZ configuration:.....................................................................................................................9
Static IP configuration:..............................................................................................................10
Network address translation (NAT) configuration and its advantages:.....................................11
P5. Data protection procedures:.................................................................................................11
P6. Processes of data protection:...............................................................................................11
Organizational regulations:........................................................................................................12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
ORGANIZATIONAL INFORMATION SECURITY RISKS AND POLICIES
Benefits of network monitoring systems:..................................................................................12
Improvement as well as identification of security threats:....................................................12
Easy upgrade of equipment’s:...............................................................................................12
Immediate returns of investments:.........................................................................................13
Trusted networks:......................................................................................................................13
ISO 31000 risk management methodology, purpose and scope:...................................................13
Security audits and its alignment with organizational policy for the retail shop:.....................14
P7. Proposed security policy:........................................................................................................15
A security council:.....................................................................................................................15
A real-time notification system for changes:.............................................................................15
P8. Disaster recovery (DR) plan:...................................................................................................15
Role of stakeholders in security audits:.........................................................................................16
Conclusion:....................................................................................................................................16
References:....................................................................................................................................17
ORGANIZATIONAL INFORMATION SECURITY RISKS AND POLICIES
Benefits of network monitoring systems:..................................................................................12
Improvement as well as identification of security threats:....................................................12
Easy upgrade of equipment’s:...............................................................................................12
Immediate returns of investments:.........................................................................................13
Trusted networks:......................................................................................................................13
ISO 31000 risk management methodology, purpose and scope:...................................................13
Security audits and its alignment with organizational policy for the retail shop:.....................14
P7. Proposed security policy:........................................................................................................15
A security council:.....................................................................................................................15
A real-time notification system for changes:.............................................................................15
P8. Disaster recovery (DR) plan:...................................................................................................15
Role of stakeholders in security audits:.........................................................................................16
Conclusion:....................................................................................................................................16
References:....................................................................................................................................17
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
ORGANIZATIONAL INFORMATION SECURITY RISKS AND POLICIES
Introduction:
Information security within the organizations is one of the most important concerns that
are being considered by the managers and the organizational leaders in today’s world. This
report will identify the security threats the different organizations. There is a retail shop in based
East London, which has come up with its shopping application known as shopaholics that can
ease the business-oriented tasks for the customers as well as the workers of the shop including
the partners and the stakeholders associated to the retail shop. Customers can now do online
shopping from the application. By the end of this report, the reader will understand the security
related issues faced by the application, which was connected to the internet1.
Potential risks for the shopaholic’s application:
The shopaholics application stores information online in using the software solution and
there are chances that the information is hacked since the hackers use advanced hacking tools to
breach the privacy of the network and access the databases. Recently the company had faced a
DoS attack, which causes disruption of normal business operation for long hours. The
application had also faced a major virus infection. Virus infection is again a very prominent risk
for the application as well as the company since it can cause potential tax frauds and other illegal
activities2.
1 Huth, Carly L., David W. Chadwick, William R. Claycomb, and Ilsun You. "Guest editorial: A brief
overview of data leakage and insider threats." Information Systems Frontiers 15, no. 1 (2013): 1-4.
2 Jouini, Mouna, Latifa Ben Arfa Rabai, and Anis Ben Aissa. "Classification of security threats in
information systems." Procedia Computer Science 32 (2014): 489-496.
ORGANIZATIONAL INFORMATION SECURITY RISKS AND POLICIES
Introduction:
Information security within the organizations is one of the most important concerns that
are being considered by the managers and the organizational leaders in today’s world. This
report will identify the security threats the different organizations. There is a retail shop in based
East London, which has come up with its shopping application known as shopaholics that can
ease the business-oriented tasks for the customers as well as the workers of the shop including
the partners and the stakeholders associated to the retail shop. Customers can now do online
shopping from the application. By the end of this report, the reader will understand the security
related issues faced by the application, which was connected to the internet1.
Potential risks for the shopaholic’s application:
The shopaholics application stores information online in using the software solution and
there are chances that the information is hacked since the hackers use advanced hacking tools to
breach the privacy of the network and access the databases. Recently the company had faced a
DoS attack, which causes disruption of normal business operation for long hours. The
application had also faced a major virus infection. Virus infection is again a very prominent risk
for the application as well as the company since it can cause potential tax frauds and other illegal
activities2.
1 Huth, Carly L., David W. Chadwick, William R. Claycomb, and Ilsun You. "Guest editorial: A brief
overview of data leakage and insider threats." Information Systems Frontiers 15, no. 1 (2013): 1-4.
2 Jouini, Mouna, Latifa Ben Arfa Rabai, and Anis Ben Aissa. "Classification of security threats in
information systems." Procedia Computer Science 32 (2014): 489-496.

5
ORGANIZATIONAL INFORMATION SECURITY RISKS AND POLICIES
P1. IT industry risks:
Data theft:
The hackers can use advanced techniques to break into the organizational networks, and
use the important financial data and the organizational tax sheets to do tax frauds and other
illegal activities or they can also in turn blackmail the company to pay them huge amounts of
money in order to prevent the misuse of the data3.
DOS attacks:
DoS attack which is distributed in nature is a denial of service that occurs when the
available bandwidth of the target system is flooded by requests from many systems at the same
time. It usually occurs in case of many web servers4. It is a form of cybercrime in which, the
penetrator makes a machine or another network resource unavailable to its intended users
temporarily or even permanently disrupting the services of the host connected to the network of
the internet. Recently there was a DoS attack in the retail shop of east London, wherein the
servers were down for 4 hours5. All the important tasks were halted and it caused many problems
for the customers as well as the shop authorities.
Employee Vandalism:
This occurs when the employees purposely cause corruption of the important data if they
have a revengeful mentality towards the fellow employees or even the organization as a whole
for their own personal interests6.
3
43Dover, Jeremy M. "A denial of service attack against the Open Floodlight SDN controller." Dover
Networks, Tech. Rep.(2013).
54 Hardy, Seth, Masashi Crete-Nishihata, Katharine Kleemola, Adam Senft, Byron Sonne, Greg Wiseman,
Phillipa Gill, and Ronald J. Deibert. "Targeted Threat Index: Characterizing and Quantifying Politically-
Motivated Targeted Malware." In USENIX Security Symposium, pp. 527-541. 2014.
65 Greenbaum, Rebecca L., Mary Bardes Mawritz, David M. Mayer, and Manuela Priesemuth. "To act out,
to withdraw, or to constructively resist? Employee reactions to supervisor abuse of customers and the
moderating role of employee moral identity." Human Relations 66, no. 7 (2013): 925-950.
ORGANIZATIONAL INFORMATION SECURITY RISKS AND POLICIES
P1. IT industry risks:
Data theft:
The hackers can use advanced techniques to break into the organizational networks, and
use the important financial data and the organizational tax sheets to do tax frauds and other
illegal activities or they can also in turn blackmail the company to pay them huge amounts of
money in order to prevent the misuse of the data3.
DOS attacks:
DoS attack which is distributed in nature is a denial of service that occurs when the
available bandwidth of the target system is flooded by requests from many systems at the same
time. It usually occurs in case of many web servers4. It is a form of cybercrime in which, the
penetrator makes a machine or another network resource unavailable to its intended users
temporarily or even permanently disrupting the services of the host connected to the network of
the internet. Recently there was a DoS attack in the retail shop of east London, wherein the
servers were down for 4 hours5. All the important tasks were halted and it caused many problems
for the customers as well as the shop authorities.
Employee Vandalism:
This occurs when the employees purposely cause corruption of the important data if they
have a revengeful mentality towards the fellow employees or even the organization as a whole
for their own personal interests6.
3
43Dover, Jeremy M. "A denial of service attack against the Open Floodlight SDN controller." Dover
Networks, Tech. Rep.(2013).
54 Hardy, Seth, Masashi Crete-Nishihata, Katharine Kleemola, Adam Senft, Byron Sonne, Greg Wiseman,
Phillipa Gill, and Ronald J. Deibert. "Targeted Threat Index: Characterizing and Quantifying Politically-
Motivated Targeted Malware." In USENIX Security Symposium, pp. 527-541. 2014.
65 Greenbaum, Rebecca L., Mary Bardes Mawritz, David M. Mayer, and Manuela Priesemuth. "To act out,
to withdraw, or to constructively resist? Employee reactions to supervisor abuse of customers and the
moderating role of employee moral identity." Human Relations 66, no. 7 (2013): 925-950.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
ORGANIZATIONAL INFORMATION SECURITY RISKS AND POLICIES
P2. Security measures needed for the retail shop:
Setting strong passwords in the servers and workstations:
A strong password is a combination of uppercase as well as lower case alphabets,
numbers and symbols. No two computers within the shop should have the same password.
Setting up a strong password will ensure that employees cannot access each other’s computers as
well as the emails, which in turn can reduces data theft and issues like employee vandalism
within the retail shop.
Usage of strong enterprise antivirus programs and network firewalls:
There are different enterprise level antivirus software’s like the Kaspersky internet
security as well as the Norton antivirus program that are available for the corporates for securing
their organizational systems7.
Network firewalls should also be implemented in the local area networks (LAN) within
the shop to prevent the computer from opening up any kind of malicious website on the
computers. These attacks occurs when the packets are being routed from a particular routing
device located in the given network8. Unnecessary inbound traffic apart from the data related to
the shopaholic site, is blocked when the systems/servers remain connected to the VyprVPN
(Vypr virtual private network), thereby acting as firewall.
Use of proper data back up and disaster management system:
An efficient data backup cycle will ensure that even if there are any kinds of unforeseen
situations of data insecurity, there are no troubles and the data is retained safe. There should be
centralized servers that should store all the information of the customers as well as the
76 Zhang-Kennedy, Leah, Sonia Chiasson, and Robert Biddle. "Stop clicking on “update later”: Persuading
users they need up-to-date antivirus protection." In International Conference on Persuasive Technology,
pp. 302-322. Springer, Cham, 2014.
87 Sood, Aditya K., and Richard J. Enbody. "Targeted cyberattacks: a superset of advanced persistent
threats." IEEE security & privacy 11, no. 1 (2013): 54-61.
ORGANIZATIONAL INFORMATION SECURITY RISKS AND POLICIES
P2. Security measures needed for the retail shop:
Setting strong passwords in the servers and workstations:
A strong password is a combination of uppercase as well as lower case alphabets,
numbers and symbols. No two computers within the shop should have the same password.
Setting up a strong password will ensure that employees cannot access each other’s computers as
well as the emails, which in turn can reduces data theft and issues like employee vandalism
within the retail shop.
Usage of strong enterprise antivirus programs and network firewalls:
There are different enterprise level antivirus software’s like the Kaspersky internet
security as well as the Norton antivirus program that are available for the corporates for securing
their organizational systems7.
Network firewalls should also be implemented in the local area networks (LAN) within
the shop to prevent the computer from opening up any kind of malicious website on the
computers. These attacks occurs when the packets are being routed from a particular routing
device located in the given network8. Unnecessary inbound traffic apart from the data related to
the shopaholic site, is blocked when the systems/servers remain connected to the VyprVPN
(Vypr virtual private network), thereby acting as firewall.
Use of proper data back up and disaster management system:
An efficient data backup cycle will ensure that even if there are any kinds of unforeseen
situations of data insecurity, there are no troubles and the data is retained safe. There should be
centralized servers that should store all the information of the customers as well as the
76 Zhang-Kennedy, Leah, Sonia Chiasson, and Robert Biddle. "Stop clicking on “update later”: Persuading
users they need up-to-date antivirus protection." In International Conference on Persuasive Technology,
pp. 302-322. Springer, Cham, 2014.
87 Sood, Aditya K., and Richard J. Enbody. "Targeted cyberattacks: a superset of advanced persistent
threats." IEEE security & privacy 11, no. 1 (2013): 54-61.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
ORGANIZATIONAL INFORMATION SECURITY RISKS AND POLICIES
management and operations information of the shopaholic’s application thereby reducing the risk
of data loss and misuse in case of accidents and server breakdowns9.
The employees should also be adequately trained so that in case of any such unforeseen
conditions the employees are efficient enough to handle the recovery tools10.
P3. Potential impacts of incorrect firewall and VPN configuration:
If the private and secure connection is not completed successfully, secure data
transmission between the source and the destination is not possible. There are different kinds of
security implications for VPNs configures in transport and the tunnel mode. Considering the case
of the classic client-based Internet Protocol sec VPN, there are two parties of each VPN
connections: the VPN client and the VPN gateway. Manipulation proposals of Phase 1 and/or
Phase 2 in the IPsec connection can cause security compromises, if VPN is not configures
properly11.
Another threat of incorrect VPN configuration is that when the users change the client
parameters like the pre-shared key values. The key value is generally unknown to the user and
the client will therefore not be able to establish a valid VPN connection. Therefore, in order to
make it work again the user will try to obtain the exact VPN configuration. In the process of
transmission of the important security value (key value) security breaches can occur.
DMZ configuration:
The steps to set up a DMZ on a network are explained below:
98 Van De Walle, Bartel, Murray Turoff, and Starr Roxanne Hiltz. Information systems for emergency
management, 2014.
109 Jehanzeb, Khawaja, and Nadeem Ahmed Bashir. "Training and development program and its benefits
to employee and organization: A conceptual study." European Journal of business and management 5,
no. 2 (2013).
1110 Kumar, KM Sumesh, and Kinn Abass Bakon. "The Analysis of Firewall and VPN in Enterprise Network
Performances."
ORGANIZATIONAL INFORMATION SECURITY RISKS AND POLICIES
management and operations information of the shopaholic’s application thereby reducing the risk
of data loss and misuse in case of accidents and server breakdowns9.
The employees should also be adequately trained so that in case of any such unforeseen
conditions the employees are efficient enough to handle the recovery tools10.
P3. Potential impacts of incorrect firewall and VPN configuration:
If the private and secure connection is not completed successfully, secure data
transmission between the source and the destination is not possible. There are different kinds of
security implications for VPNs configures in transport and the tunnel mode. Considering the case
of the classic client-based Internet Protocol sec VPN, there are two parties of each VPN
connections: the VPN client and the VPN gateway. Manipulation proposals of Phase 1 and/or
Phase 2 in the IPsec connection can cause security compromises, if VPN is not configures
properly11.
Another threat of incorrect VPN configuration is that when the users change the client
parameters like the pre-shared key values. The key value is generally unknown to the user and
the client will therefore not be able to establish a valid VPN connection. Therefore, in order to
make it work again the user will try to obtain the exact VPN configuration. In the process of
transmission of the important security value (key value) security breaches can occur.
DMZ configuration:
The steps to set up a DMZ on a network are explained below:
98 Van De Walle, Bartel, Murray Turoff, and Starr Roxanne Hiltz. Information systems for emergency
management, 2014.
109 Jehanzeb, Khawaja, and Nadeem Ahmed Bashir. "Training and development program and its benefits
to employee and organization: A conceptual study." European Journal of business and management 5,
no. 2 (2013).
1110 Kumar, KM Sumesh, and Kinn Abass Bakon. "The Analysis of Firewall and VPN in Enterprise Network
Performances."

8
ORGANIZATIONAL INFORMATION SECURITY RISKS AND POLICIES
1. A web browser has to be launched from the smartphone or the computer, which is already
connected to the network of the router.
2. The default username and password is admin and password respectively.
3. Under the ADVANCED option >select “Setup” > then select “LAN Setup”.
4. The Default DMZ check box of the Server has to be selected.
5. The IP address has to be manually typed12.
6. Click on apply.
P4. Advantages of DMZ in network security:
Adding a DMZ provides a “quarantined” network area in case of a virus attack or an
intrusion that attacks only part of the network and the rest of the network remains unaffected,
thereby allowing the affected network area to be partitioned from the rest of the working
network.
1211 Dart, Eli, Lauren Rotman, Brian Tierney, Mary Hester, and Jason Zurawski. "The science dmz: A
network design pattern for data-intensive science." Scientific Programming 22, no. 2 (2014): 173-185.
ORGANIZATIONAL INFORMATION SECURITY RISKS AND POLICIES
1. A web browser has to be launched from the smartphone or the computer, which is already
connected to the network of the router.
2. The default username and password is admin and password respectively.
3. Under the ADVANCED option >select “Setup” > then select “LAN Setup”.
4. The Default DMZ check box of the Server has to be selected.
5. The IP address has to be manually typed12.
6. Click on apply.
P4. Advantages of DMZ in network security:
Adding a DMZ provides a “quarantined” network area in case of a virus attack or an
intrusion that attacks only part of the network and the rest of the network remains unaffected,
thereby allowing the affected network area to be partitioned from the rest of the working
network.
1211 Dart, Eli, Lauren Rotman, Brian Tierney, Mary Hester, and Jason Zurawski. "The science dmz: A
network design pattern for data-intensive science." Scientific Programming 22, no. 2 (2014): 173-185.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
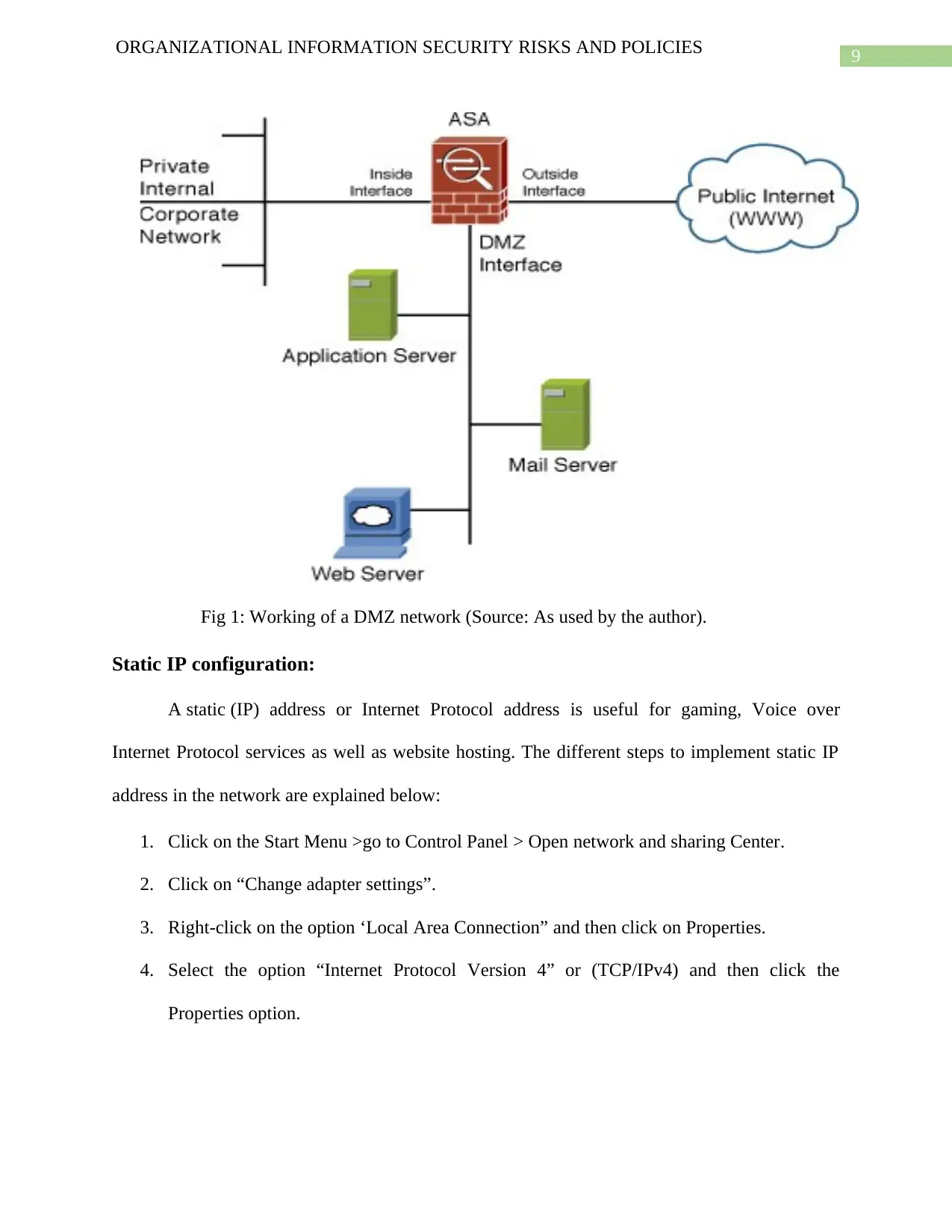
9
ORGANIZATIONAL INFORMATION SECURITY RISKS AND POLICIES
Fig 1: Working of a DMZ network (Source: As used by the author).
Static IP configuration:
A static (IP) address or Internet Protocol address is useful for gaming, Voice over
Internet Protocol services as well as website hosting. The different steps to implement static IP
address in the network are explained below:
1. Click on the Start Menu >go to Control Panel > Open network and sharing Center.
2. Click on “Change adapter settings”.
3. Right-click on the option ‘Local Area Connection” and then click on Properties.
4. Select the option “Internet Protocol Version 4” or (TCP/IPv4) and then click the
Properties option.
ORGANIZATIONAL INFORMATION SECURITY RISKS AND POLICIES
Fig 1: Working of a DMZ network (Source: As used by the author).
Static IP configuration:
A static (IP) address or Internet Protocol address is useful for gaming, Voice over
Internet Protocol services as well as website hosting. The different steps to implement static IP
address in the network are explained below:
1. Click on the Start Menu >go to Control Panel > Open network and sharing Center.
2. Click on “Change adapter settings”.
3. Right-click on the option ‘Local Area Connection” and then click on Properties.
4. Select the option “Internet Protocol Version 4” or (TCP/IPv4) and then click the
Properties option.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
ORGANIZATIONAL INFORMATION SECURITY RISKS AND POLICIES
5. Select "Use the following IP address" option and then the IP address, Default Gateway as
well as the DNS server subnet mask should be entered13. Then click on Ok and close the
dialog box.
Network address translation (NAT) configuration and its advantages:
Network Address Translation or NAT helps in protecting the identity of the internal
network and no internal IP addresses re being exposed in the internet. Therefore, it can protect
the data of the retail shop in East London from being attacked by the hackers 14. Firstly, it hides
the IP addresses of any devices on the organizational network from the outside world, giving
them all a single address. Secondly, the incoming traffic (packets) are only allowed by the
network of the retail shop if it has been requested by any of the computers, else not.
P5. Data protection procedures:
A procedure wherein an administrator should be appointed who will handle all the
incoming requests from the employees regarding accessing data from the systems. The
administrator will also be responsible for assigning priority levels to the employees. Stringent
internet policies should also be implemented within the organizations to ensure it is not misused
for any kind of data misuse.
Risk assessment procedure for the retail shop:
Three most important question s have to be answered in order to develop a proper
procedure to reduce the IT data risks within the retails hosp. Those questions are: which is the
risk that has to be addressed on a priority basis? Is the most cost effecting way been used to
reduce it?. Since the company has recently faced issues like DoS attacks and virus infections, it
1312 Piyare, Rajeev. "Internet of things: ubiquitous home control and monitoring system using android
based smart phone." International Journal of Internet of Things 2, no. 1 (2013): 5-11.
1413 Troan, Ole, David Miles, Satoru Matsushima, Tadahisa Okimoto, and Dan Wing. Ipv6 multihoming
without network address translation. No. RFC 7157. 2014.
ORGANIZATIONAL INFORMATION SECURITY RISKS AND POLICIES
5. Select "Use the following IP address" option and then the IP address, Default Gateway as
well as the DNS server subnet mask should be entered13. Then click on Ok and close the
dialog box.
Network address translation (NAT) configuration and its advantages:
Network Address Translation or NAT helps in protecting the identity of the internal
network and no internal IP addresses re being exposed in the internet. Therefore, it can protect
the data of the retail shop in East London from being attacked by the hackers 14. Firstly, it hides
the IP addresses of any devices on the organizational network from the outside world, giving
them all a single address. Secondly, the incoming traffic (packets) are only allowed by the
network of the retail shop if it has been requested by any of the computers, else not.
P5. Data protection procedures:
A procedure wherein an administrator should be appointed who will handle all the
incoming requests from the employees regarding accessing data from the systems. The
administrator will also be responsible for assigning priority levels to the employees. Stringent
internet policies should also be implemented within the organizations to ensure it is not misused
for any kind of data misuse.
Risk assessment procedure for the retail shop:
Three most important question s have to be answered in order to develop a proper
procedure to reduce the IT data risks within the retails hosp. Those questions are: which is the
risk that has to be addressed on a priority basis? Is the most cost effecting way been used to
reduce it?. Since the company has recently faced issues like DoS attacks and virus infections, it
1312 Piyare, Rajeev. "Internet of things: ubiquitous home control and monitoring system using android
based smart phone." International Journal of Internet of Things 2, no. 1 (2013): 5-11.
1413 Troan, Ole, David Miles, Satoru Matsushima, Tadahisa Okimoto, and Dan Wing. Ipv6 multihoming
without network address translation. No. RFC 7157. 2014.

11
ORGANIZATIONAL INFORMATION SECURITY RISKS AND POLICIES
is of utmost priority that it secures the servers from DoS attacks and starts using proper antivirus
software’s as well as firewall in order to efficiently secure all the organizational workstations
from any kind of data theft or misuse by the intruders. Enterprise antivirus software’s such as
Norton as well as Kaspersky software’s can be used to run regular and routines scans
mandatorily on the all the computers.
In case of qualitative risk analysis, the risks faced by the organizations are first identified
such as data theft, virus infections. Alter the risks have been identified the mitigation techniques
such as installing antivirus programs as well as network firewalls are implemented in order to
overcome such risks. A detailed qualitative study about the nature of the threats is carried out.
Quantitative risk analysis is done only on a set of potential threats that have been
identified to be the most dangerous risks and have to be mitigated on the highest priority base
done the results from the qualitative study of the risks. This analysis is only performed on risks,
which are marked for further analysis by Perform Qualitative Risk Analysis process.
ISO 31000 risk management methodology, purpose and scope:
The different risks in terms of data security and other risks faced by the retail shop in
East London can have multiple effects in terms of its professional performance as well as
economic reputation. Other risks in terms of its social, environmental as well as safety measures
can have long-term negative outcomes on the working of the organization. Therefore, a proper
risk management methodology is needed for the retail shop to ensure its smooth functioning in
the future.
ORGANIZATIONAL INFORMATION SECURITY RISKS AND POLICIES
is of utmost priority that it secures the servers from DoS attacks and starts using proper antivirus
software’s as well as firewall in order to efficiently secure all the organizational workstations
from any kind of data theft or misuse by the intruders. Enterprise antivirus software’s such as
Norton as well as Kaspersky software’s can be used to run regular and routines scans
mandatorily on the all the computers.
In case of qualitative risk analysis, the risks faced by the organizations are first identified
such as data theft, virus infections. Alter the risks have been identified the mitigation techniques
such as installing antivirus programs as well as network firewalls are implemented in order to
overcome such risks. A detailed qualitative study about the nature of the threats is carried out.
Quantitative risk analysis is done only on a set of potential threats that have been
identified to be the most dangerous risks and have to be mitigated on the highest priority base
done the results from the qualitative study of the risks. This analysis is only performed on risks,
which are marked for further analysis by Perform Qualitative Risk Analysis process.
ISO 31000 risk management methodology, purpose and scope:
The different risks in terms of data security and other risks faced by the retail shop in
East London can have multiple effects in terms of its professional performance as well as
economic reputation. Other risks in terms of its social, environmental as well as safety measures
can have long-term negative outcomes on the working of the organization. Therefore, a proper
risk management methodology is needed for the retail shop to ensure its smooth functioning in
the future.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 21
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




