Security Risk Assessment: Analysis of Hospital Project
VerifiedAdded on 2019/09/24
|3
|292
|136
Project
AI Summary
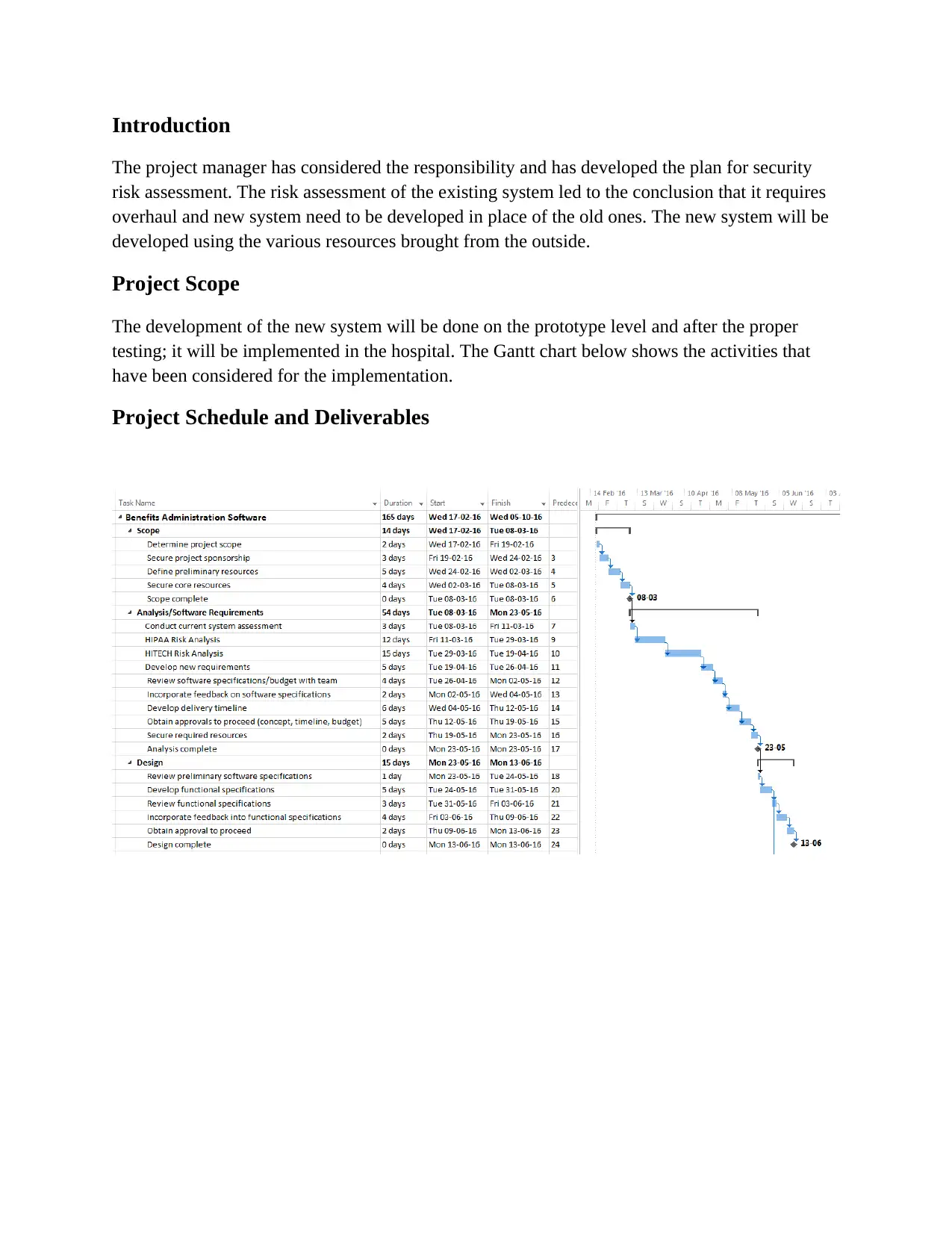
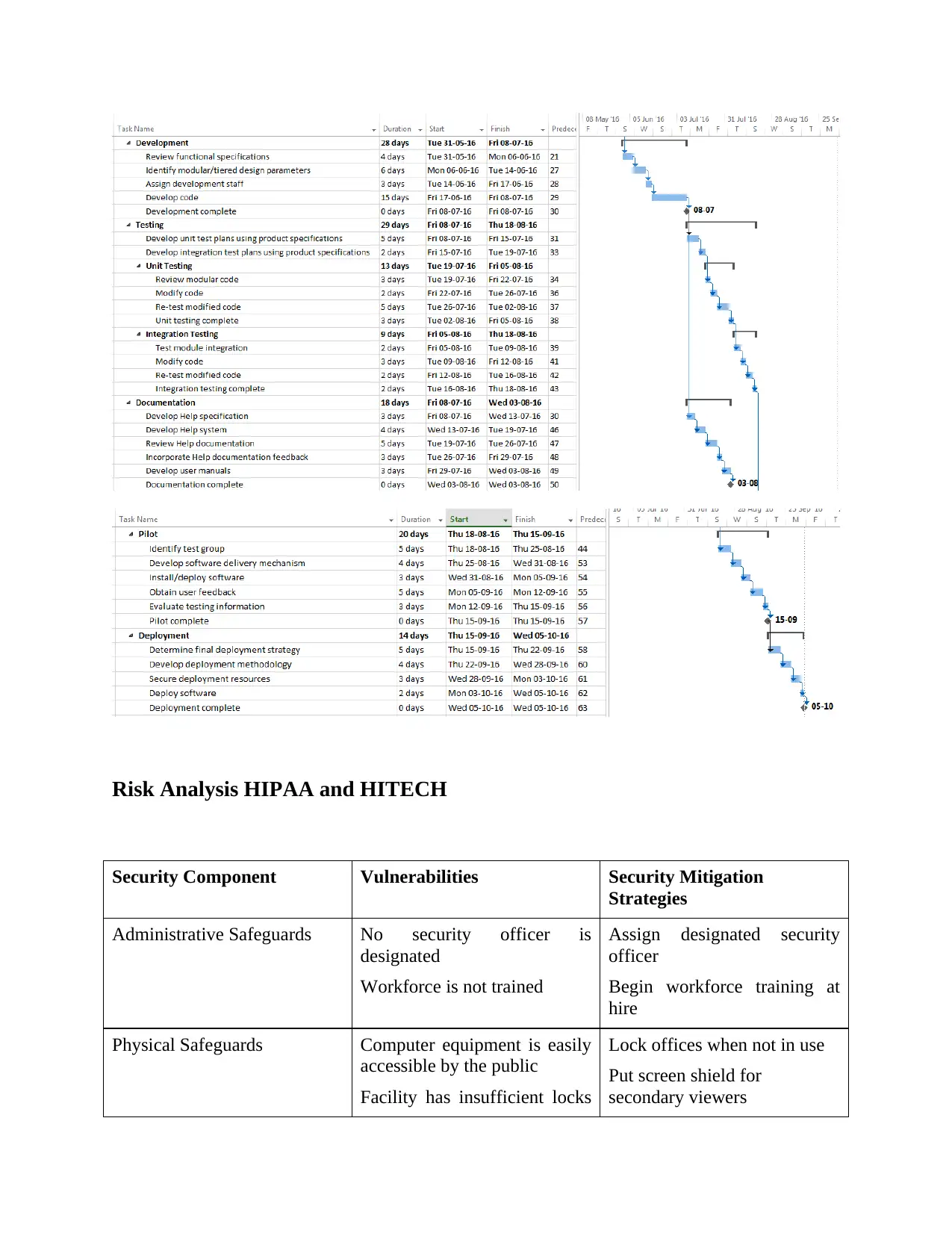
This assignment presents a comprehensive security risk assessment for a hospital project, focusing on the development of a new system to replace an existing one. The project scope includes prototype development and subsequent testing before implementation. A Gantt chart outlines the project schedule, detailing activities and deliverables. The risk analysis identifies vulnerabilities and proposes security mitigation strategies, covering administrative, physical, and technical safeguards. It addresses issues like lack of a designated security officer, insufficient physical security, and inadequate access controls. The assignment also covers organizational standards, project budget, and required policies and procedures. The project aims to ensure the security of patient data and compliance with HIPAA and HITECH regulations.
1 out of 3







![[object Object]](/_next/static/media/star-bottom.7253800d.svg)