Information Security Audit Plan for Trump Hotel: Foundation Course
VerifiedAdded on 2023/04/06
|18
|2377
|269
Report
AI Summary
This document presents an information security audit plan conducted for Trump Hotel following a cybersecurity incident that resulted in data loss. The audit assesses the hotel's information security control framework, policies, systems, applications, and network infrastructure. Key risks identified include data loss, identity theft, system failures, denial of service attacks, compliance risks, insider threats, and legal risks. The audit plan outlines specific objectives, such as evaluating existing security management frameworks, assessing security awareness campaigns, and determining the effectiveness of personnel screening. The plan details the schedule, methods (including meetings, documentation reviews, interviews, and physical security audits), and responsible parties for each phase of the audit. Furthermore, it lists key questions and required documentation to evaluate the hotel's security posture and compliance with relevant standards, with a final report and presentation to the board.

Information Security Audit: 1
Information Security Audit Plan of Trump Hotel
by [Student Name]
Foundation Course – [Course Name]
Tutor: [Tutor]
[Institutional Affiliation]
[Department]
[Date]
Information Security Audit Plan of Trump Hotel
by [Student Name]
Foundation Course – [Course Name]
Tutor: [Tutor]
[Institutional Affiliation]
[Department]
[Date]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Information Security Audit: 2
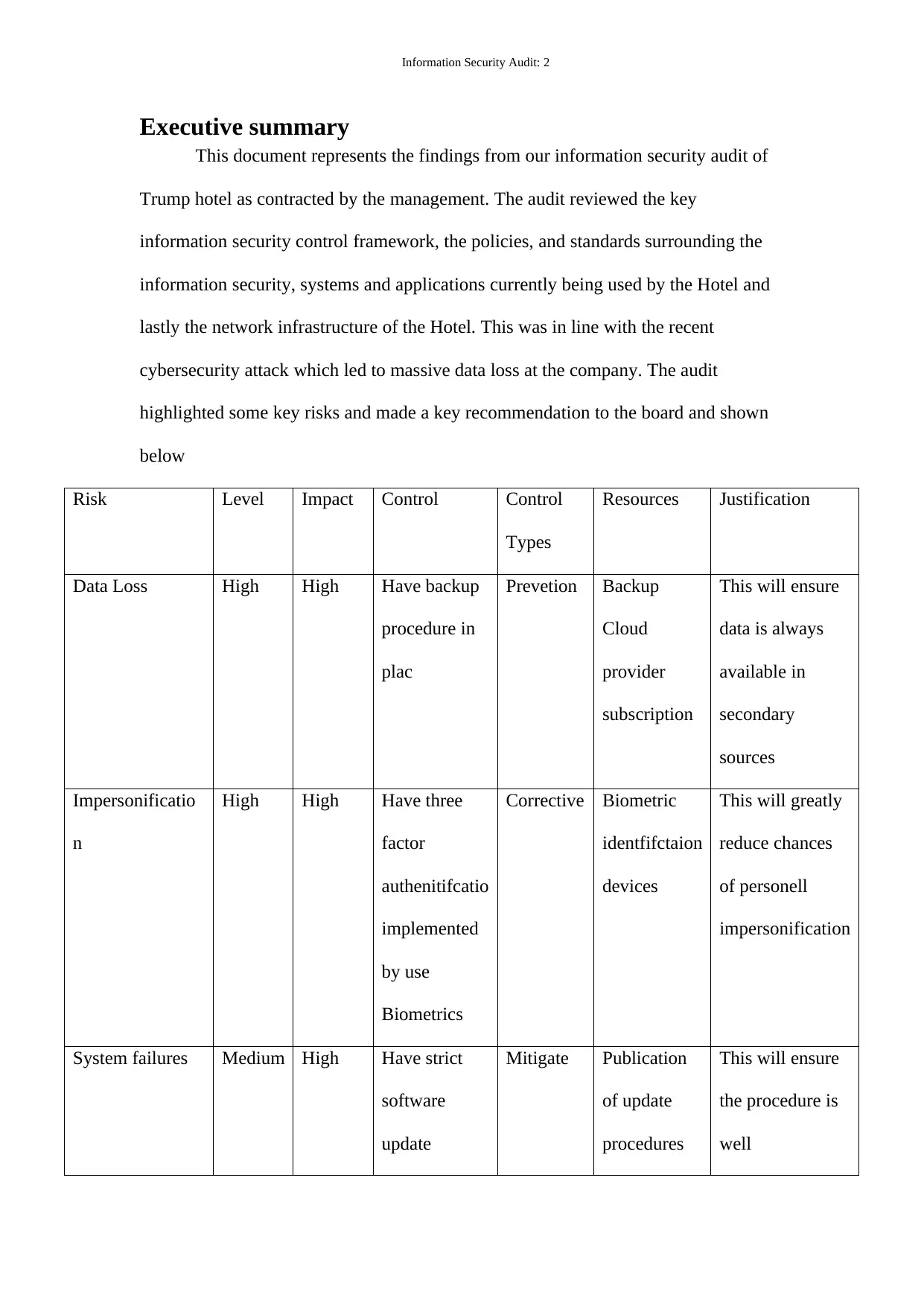
Executive summary
This document represents the findings from our information security audit of
Trump hotel as contracted by the management. The audit reviewed the key
information security control framework, the policies, and standards surrounding the
information security, systems and applications currently being used by the Hotel and
lastly the network infrastructure of the Hotel. This was in line with the recent
cybersecurity attack which led to massive data loss at the company. The audit
highlighted some key risks and made a key recommendation to the board and shown
below
Risk Level Impact Control Control
Types
Resources Justification
Data Loss High High Have backup
procedure in
plac
Prevetion Backup
Cloud
provider
subscription
This will ensure
data is always
available in
secondary
sources
Impersonificatio
n
High High Have three
factor
authenitifcatio
implemented
by use
Biometrics
Corrective Biometric
identfifctaion
devices
This will greatly
reduce chances
of personell
impersonification
System failures Medium High Have strict
software
update
Mitigate Publication
of update
procedures
This will ensure
the procedure is
well
Executive summary
This document represents the findings from our information security audit of
Trump hotel as contracted by the management. The audit reviewed the key
information security control framework, the policies, and standards surrounding the
information security, systems and applications currently being used by the Hotel and
lastly the network infrastructure of the Hotel. This was in line with the recent
cybersecurity attack which led to massive data loss at the company. The audit
highlighted some key risks and made a key recommendation to the board and shown
below
Risk Level Impact Control Control
Types
Resources Justification
Data Loss High High Have backup
procedure in
plac
Prevetion Backup
Cloud
provider
subscription
This will ensure
data is always
available in
secondary
sources
Impersonificatio
n
High High Have three
factor
authenitifcatio
implemented
by use
Biometrics
Corrective Biometric
identfifctaion
devices
This will greatly
reduce chances
of personell
impersonification
System failures Medium High Have strict
software
update
Mitigate Publication
of update
procedures
This will ensure
the procedure is
well
Information Security Audit: 3
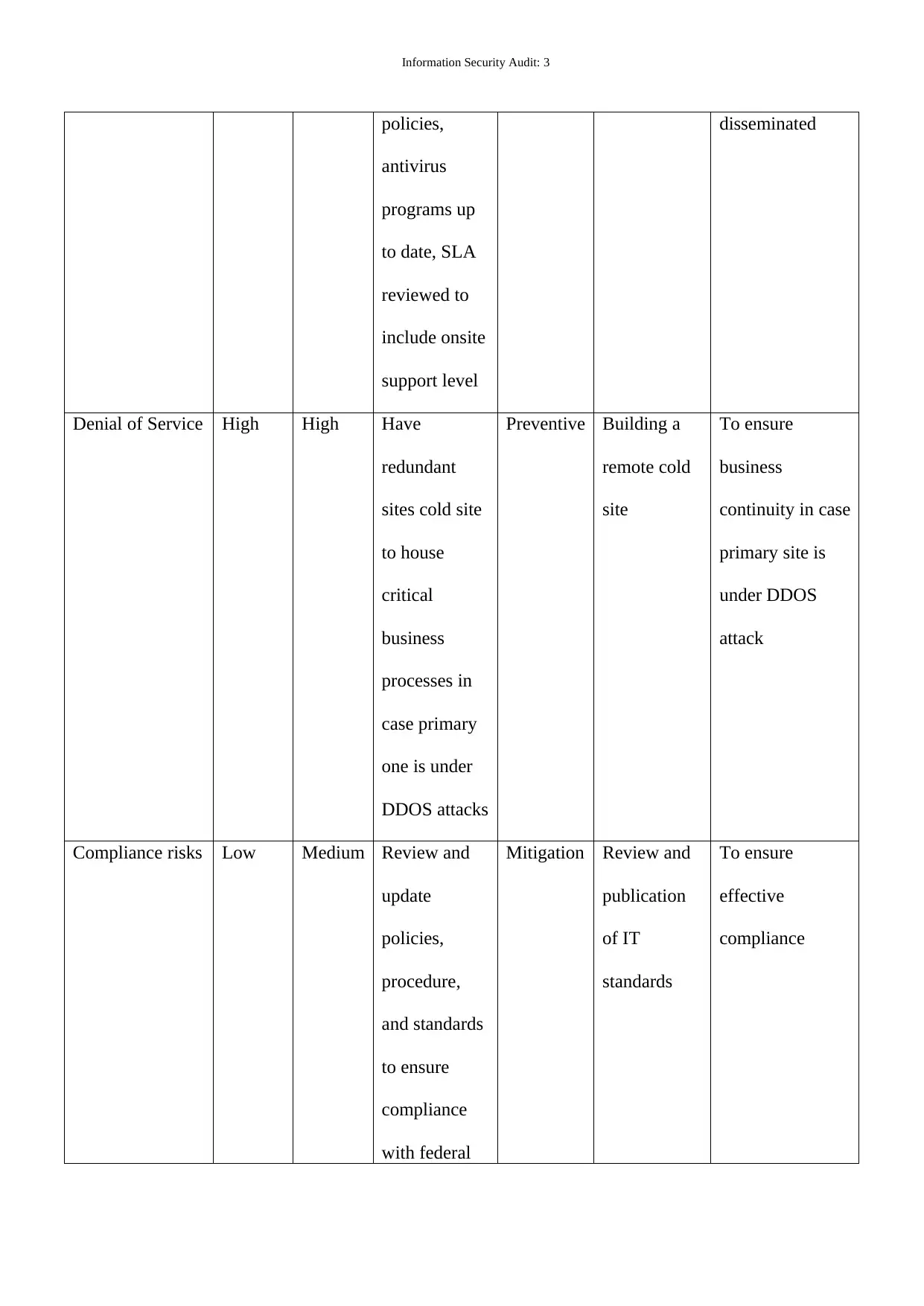
policies,
antivirus
programs up
to date, SLA
reviewed to
include onsite
support level
disseminated
Denial of Service High High Have
redundant
sites cold site
to house
critical
business
processes in
case primary
one is under
DDOS attacks
Preventive Building a
remote cold
site
To ensure
business
continuity in case
primary site is
under DDOS
attack
Compliance risks Low Medium Review and
update
policies,
procedure,
and standards
to ensure
compliance
with federal
Mitigation Review and
publication
of IT
standards
To ensure
effective
compliance
policies,
antivirus
programs up
to date, SLA
reviewed to
include onsite
support level
disseminated
Denial of Service High High Have
redundant
sites cold site
to house
critical
business
processes in
case primary
one is under
DDOS attacks
Preventive Building a
remote cold
site
To ensure
business
continuity in case
primary site is
under DDOS
attack
Compliance risks Low Medium Review and
update
policies,
procedure,
and standards
to ensure
compliance
with federal
Mitigation Review and
publication
of IT
standards
To ensure
effective
compliance
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Information Security Audit: 4
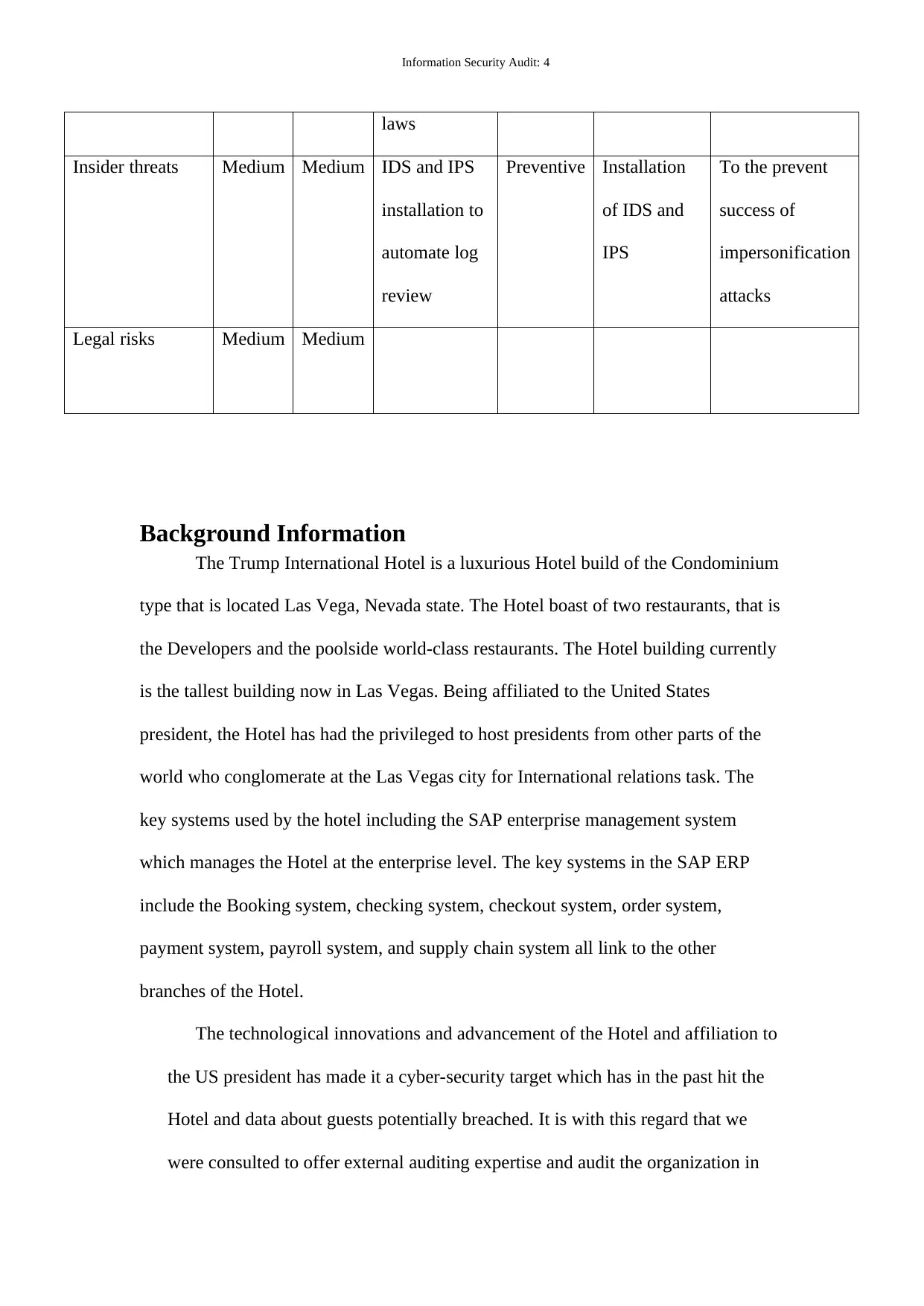
laws
Insider threats Medium Medium IDS and IPS
installation to
automate log
review
Preventive Installation
of IDS and
IPS
To the prevent
success of
impersonification
attacks
Legal risks Medium Medium
Background Information
The Trump International Hotel is a luxurious Hotel build of the Condominium
type that is located Las Vega, Nevada state. The Hotel boast of two restaurants, that is
the Developers and the poolside world-class restaurants. The Hotel building currently
is the tallest building now in Las Vegas. Being affiliated to the United States
president, the Hotel has had the privileged to host presidents from other parts of the
world who conglomerate at the Las Vegas city for International relations task. The
key systems used by the hotel including the SAP enterprise management system
which manages the Hotel at the enterprise level. The key systems in the SAP ERP
include the Booking system, checking system, checkout system, order system,
payment system, payroll system, and supply chain system all link to the other
branches of the Hotel.
The technological innovations and advancement of the Hotel and affiliation to
the US president has made it a cyber-security target which has in the past hit the
Hotel and data about guests potentially breached. It is with this regard that we
were consulted to offer external auditing expertise and audit the organization in
laws
Insider threats Medium Medium IDS and IPS
installation to
automate log
review
Preventive Installation
of IDS and
IPS
To the prevent
success of
impersonification
attacks
Legal risks Medium Medium
Background Information
The Trump International Hotel is a luxurious Hotel build of the Condominium
type that is located Las Vega, Nevada state. The Hotel boast of two restaurants, that is
the Developers and the poolside world-class restaurants. The Hotel building currently
is the tallest building now in Las Vegas. Being affiliated to the United States
president, the Hotel has had the privileged to host presidents from other parts of the
world who conglomerate at the Las Vegas city for International relations task. The
key systems used by the hotel including the SAP enterprise management system
which manages the Hotel at the enterprise level. The key systems in the SAP ERP
include the Booking system, checking system, checkout system, order system,
payment system, payroll system, and supply chain system all link to the other
branches of the Hotel.
The technological innovations and advancement of the Hotel and affiliation to
the US president has made it a cyber-security target which has in the past hit the
Hotel and data about guests potentially breached. It is with this regard that we
were consulted to offer external auditing expertise and audit the organization in
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Information Security Audit: 5
terms of information security and provide technical and managerial
recommendations to the board for action
Information Security Risks
The following are key risks identified by the audit team from the case study,
Data Loss
From the case study, it is evident that the Hotel is at risk of Losing critical and
private data about the guests and the Hotel in general. This is because it alleged the
breaches potentially stole credit card information of the guest of the hotel. The Hotel
mainly rely on the information provided by the guests to arrange for the check-ins and
do the financial transactions to finally check into the hotel, this risk is very high and
has a great negative impact on the Business ability to continue regular operations
since data is critical to their mission statement (Stafford, Deitz and Li, 2018).
Identity Theft
The guest who lost their data during the breach risks their information being
used to impersonification them on other online transactions. This is because one of the
key data stolen was the credit card information of the Millions of guests who have
previously checked into the Hotel. This is a very high risk as Millions of Americans
and the general International leader risk being impersonification by the attackers to
authorize other transaction which may be of financial nature. This has a lot of
negative impacts not only to the guests but also the Hotel and it can lead to possible
lawsuits by impersonification persons
terms of information security and provide technical and managerial
recommendations to the board for action
Information Security Risks
The following are key risks identified by the audit team from the case study,
Data Loss
From the case study, it is evident that the Hotel is at risk of Losing critical and
private data about the guests and the Hotel in general. This is because it alleged the
breaches potentially stole credit card information of the guest of the hotel. The Hotel
mainly rely on the information provided by the guests to arrange for the check-ins and
do the financial transactions to finally check into the hotel, this risk is very high and
has a great negative impact on the Business ability to continue regular operations
since data is critical to their mission statement (Stafford, Deitz and Li, 2018).
Identity Theft
The guest who lost their data during the breach risks their information being
used to impersonification them on other online transactions. This is because one of the
key data stolen was the credit card information of the Millions of guests who have
previously checked into the Hotel. This is a very high risk as Millions of Americans
and the general International leader risk being impersonification by the attackers to
authorize other transaction which may be of financial nature. This has a lot of
negative impacts not only to the guests but also the Hotel and it can lead to possible
lawsuits by impersonification persons
Information Security Audit: 6
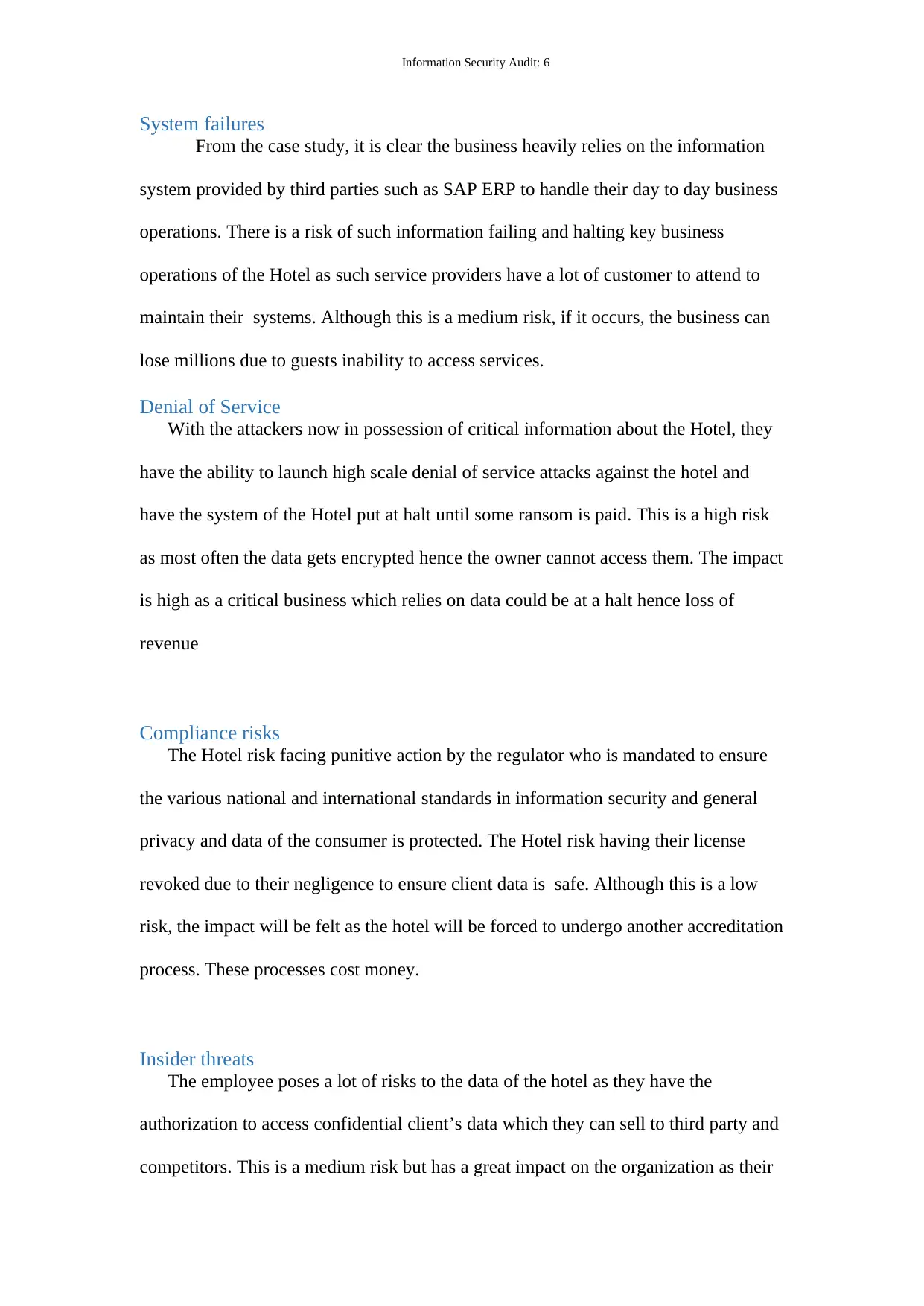
System failures
From the case study, it is clear the business heavily relies on the information
system provided by third parties such as SAP ERP to handle their day to day business
operations. There is a risk of such information failing and halting key business
operations of the Hotel as such service providers have a lot of customer to attend to
maintain their systems. Although this is a medium risk, if it occurs, the business can
lose millions due to guests inability to access services.
Denial of Service
With the attackers now in possession of critical information about the Hotel, they
have the ability to launch high scale denial of service attacks against the hotel and
have the system of the Hotel put at halt until some ransom is paid. This is a high risk
as most often the data gets encrypted hence the owner cannot access them. The impact
is high as a critical business which relies on data could be at a halt hence loss of
revenue
Compliance risks
The Hotel risk facing punitive action by the regulator who is mandated to ensure
the various national and international standards in information security and general
privacy and data of the consumer is protected. The Hotel risk having their license
revoked due to their negligence to ensure client data is safe. Although this is a low
risk, the impact will be felt as the hotel will be forced to undergo another accreditation
process. These processes cost money.
Insider threats
The employee poses a lot of risks to the data of the hotel as they have the
authorization to access confidential client’s data which they can sell to third party and
competitors. This is a medium risk but has a great impact on the organization as their
System failures
From the case study, it is clear the business heavily relies on the information
system provided by third parties such as SAP ERP to handle their day to day business
operations. There is a risk of such information failing and halting key business
operations of the Hotel as such service providers have a lot of customer to attend to
maintain their systems. Although this is a medium risk, if it occurs, the business can
lose millions due to guests inability to access services.
Denial of Service
With the attackers now in possession of critical information about the Hotel, they
have the ability to launch high scale denial of service attacks against the hotel and
have the system of the Hotel put at halt until some ransom is paid. This is a high risk
as most often the data gets encrypted hence the owner cannot access them. The impact
is high as a critical business which relies on data could be at a halt hence loss of
revenue
Compliance risks
The Hotel risk facing punitive action by the regulator who is mandated to ensure
the various national and international standards in information security and general
privacy and data of the consumer is protected. The Hotel risk having their license
revoked due to their negligence to ensure client data is safe. Although this is a low
risk, the impact will be felt as the hotel will be forced to undergo another accreditation
process. These processes cost money.
Insider threats
The employee poses a lot of risks to the data of the hotel as they have the
authorization to access confidential client’s data which they can sell to third party and
competitors. This is a medium risk but has a great impact on the organization as their
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Information Security Audit: 7
intellectual properties risk being stolen and completive advantages removed (Bozkus
Kahyaoglu and Caliyurt, 2018).
Legal risk
Due to the advertised data breach, the hotel risk having serious lawsuits
initiated by an affected guest who may want to settle the privacy loss in courts. This is
a medium risk which has a high impact as the reputation of the hotel will be greatly
jeopardized.
Audit Plan, Objectives and Goals
The main goal for conducting the audit is to assess the how effective and
efficient the various security control measure is and then level of compliance the
Hotel has made with regard to federal standards and policies. To achieve this goal, the
following specific objectives are listed
1. To find out if Hotel security management control frameworks have been
existing and deployed.
2. To find out if the Hotel information security education and awareness
campaigns are adequate.
3. To find out if an effective screening of personnel is enforced
4. To find out if the hotel has been conducting risk assessment regularly.
5. To find out the efficiency of the physical guards in safeguarding critical
assets
Audit plan
To achieve the above goals, the following plan will be executed to ensure all
the key areas of the audit is achieved
intellectual properties risk being stolen and completive advantages removed (Bozkus
Kahyaoglu and Caliyurt, 2018).
Legal risk
Due to the advertised data breach, the hotel risk having serious lawsuits
initiated by an affected guest who may want to settle the privacy loss in courts. This is
a medium risk which has a high impact as the reputation of the hotel will be greatly
jeopardized.
Audit Plan, Objectives and Goals
The main goal for conducting the audit is to assess the how effective and
efficient the various security control measure is and then level of compliance the
Hotel has made with regard to federal standards and policies. To achieve this goal, the
following specific objectives are listed
1. To find out if Hotel security management control frameworks have been
existing and deployed.
2. To find out if the Hotel information security education and awareness
campaigns are adequate.
3. To find out if an effective screening of personnel is enforced
4. To find out if the hotel has been conducting risk assessment regularly.
5. To find out the efficiency of the physical guards in safeguarding critical
assets
Audit plan
To achieve the above goals, the following plan will be executed to ensure all
the key areas of the audit is achieved
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
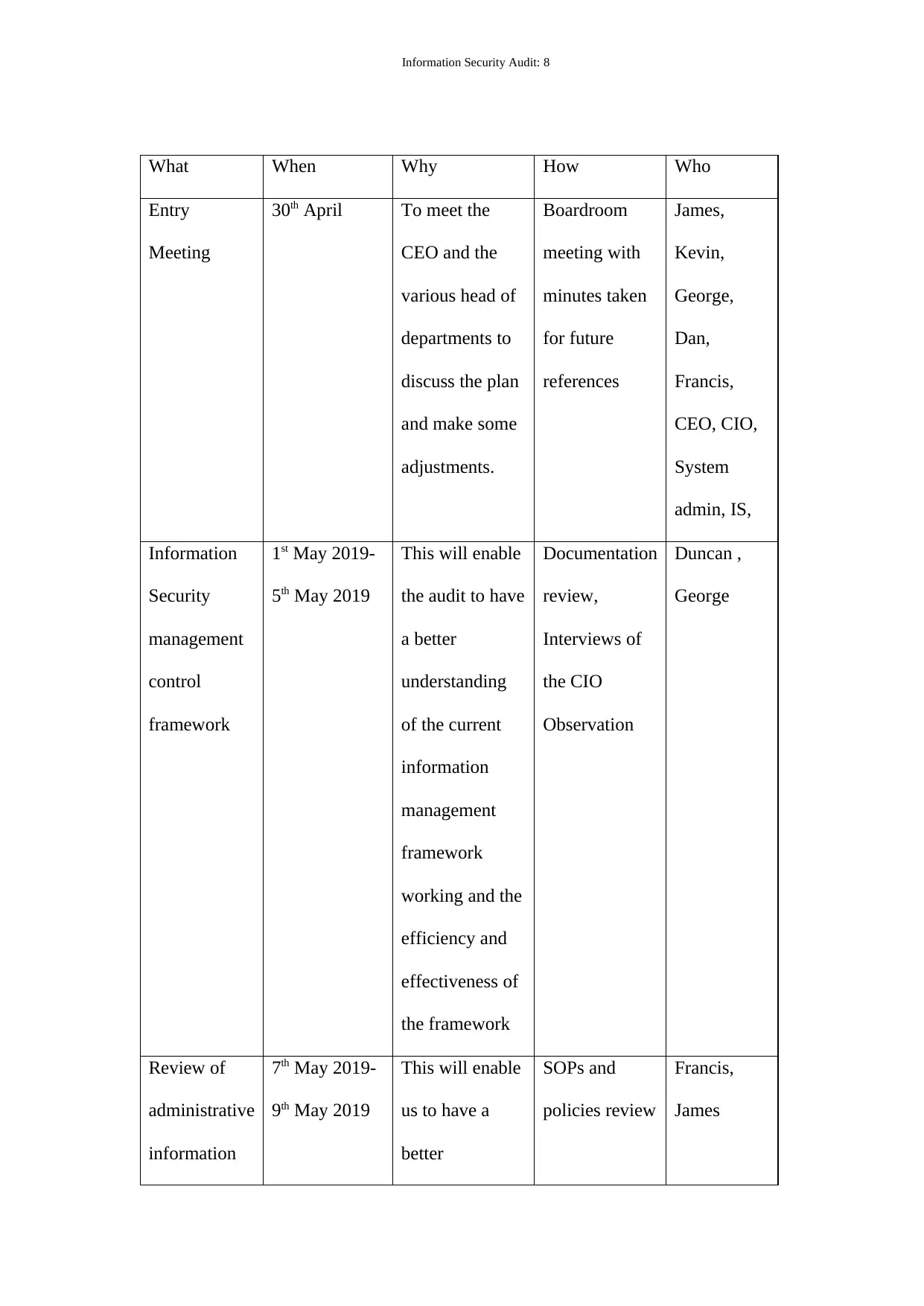
Information Security Audit: 8
What When Why How Who
Entry
Meeting
30th April To meet the
CEO and the
various head of
departments to
discuss the plan
and make some
adjustments.
Boardroom
meeting with
minutes taken
for future
references
James,
Kevin,
George,
Dan,
Francis,
CEO, CIO,
System
admin, IS,
Information
Security
management
control
framework
1st May 2019-
5th May 2019
This will enable
the audit to have
a better
understanding
of the current
information
management
framework
working and the
efficiency and
effectiveness of
the framework
Documentation
review,
Interviews of
the CIO
Observation
Duncan ,
George
Review of
administrative
information
7th May 2019-
9th May 2019
This will enable
us to have a
better
SOPs and
policies review
Francis,
James
What When Why How Who
Entry
Meeting
30th April To meet the
CEO and the
various head of
departments to
discuss the plan
and make some
adjustments.
Boardroom
meeting with
minutes taken
for future
references
James,
Kevin,
George,
Dan,
Francis,
CEO, CIO,
System
admin, IS,
Information
Security
management
control
framework
1st May 2019-
5th May 2019
This will enable
the audit to have
a better
understanding
of the current
information
management
framework
working and the
efficiency and
effectiveness of
the framework
Documentation
review,
Interviews of
the CIO
Observation
Duncan ,
George
Review of
administrative
information
7th May 2019-
9th May 2019
This will enable
us to have a
better
SOPs and
policies review
Francis,
James
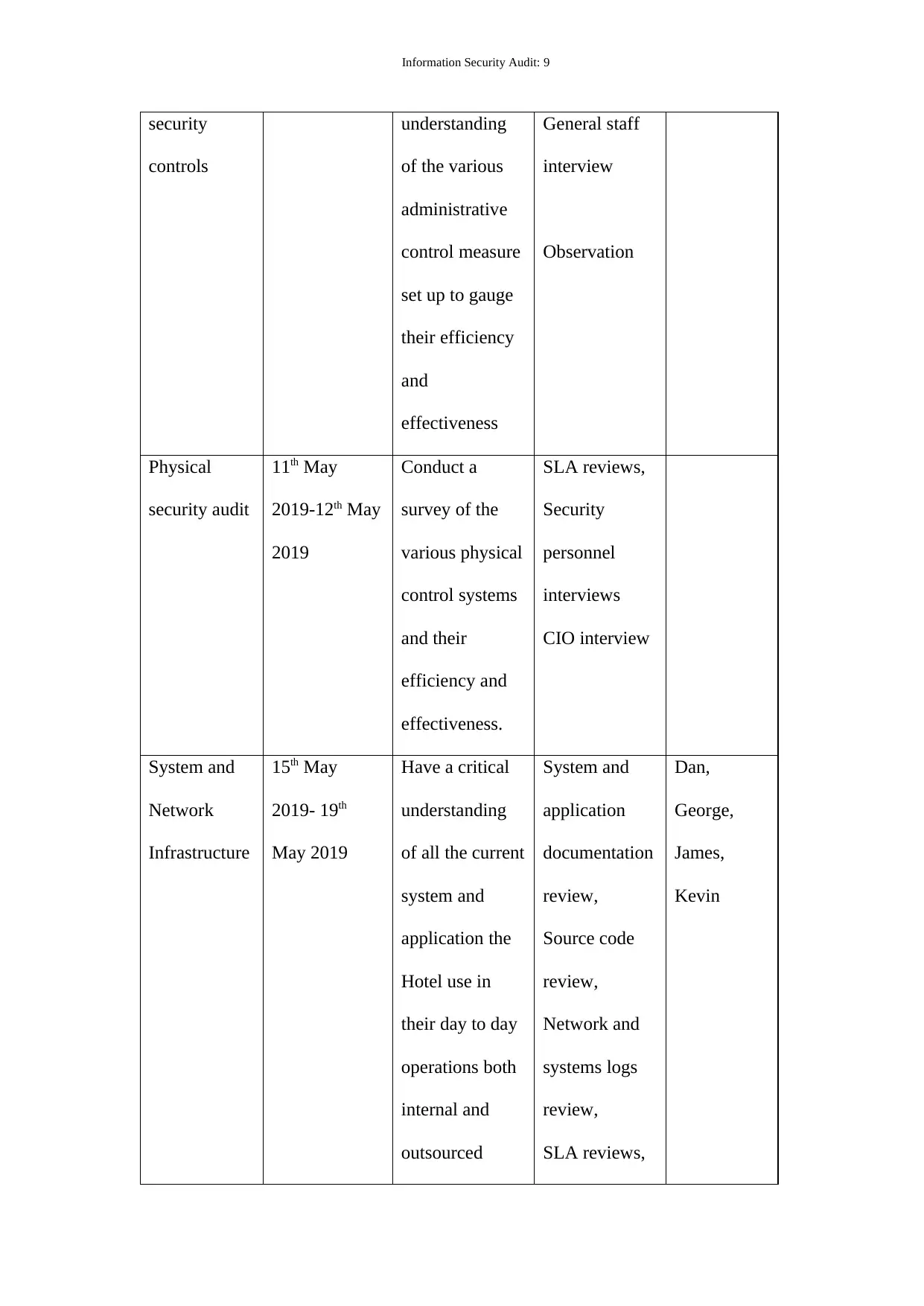
Information Security Audit: 9
security
controls
understanding
of the various
administrative
control measure
set up to gauge
their efficiency
and
effectiveness
General staff
interview
Observation
Physical
security audit
11th May
2019-12th May
2019
Conduct a
survey of the
various physical
control systems
and their
efficiency and
effectiveness.
SLA reviews,
Security
personnel
interviews
CIO interview
System and
Network
Infrastructure
15th May
2019- 19th
May 2019
Have a critical
understanding
of all the current
system and
application the
Hotel use in
their day to day
operations both
internal and
outsourced
System and
application
documentation
review,
Source code
review,
Network and
systems logs
review,
SLA reviews,
Dan,
George,
James,
Kevin
security
controls
understanding
of the various
administrative
control measure
set up to gauge
their efficiency
and
effectiveness
General staff
interview
Observation
Physical
security audit
11th May
2019-12th May
2019
Conduct a
survey of the
various physical
control systems
and their
efficiency and
effectiveness.
SLA reviews,
Security
personnel
interviews
CIO interview
System and
Network
Infrastructure
15th May
2019- 19th
May 2019
Have a critical
understanding
of all the current
system and
application the
Hotel use in
their day to day
operations both
internal and
outsourced
System and
application
documentation
review,
Source code
review,
Network and
systems logs
review,
SLA reviews,
Dan,
George,
James,
Kevin
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
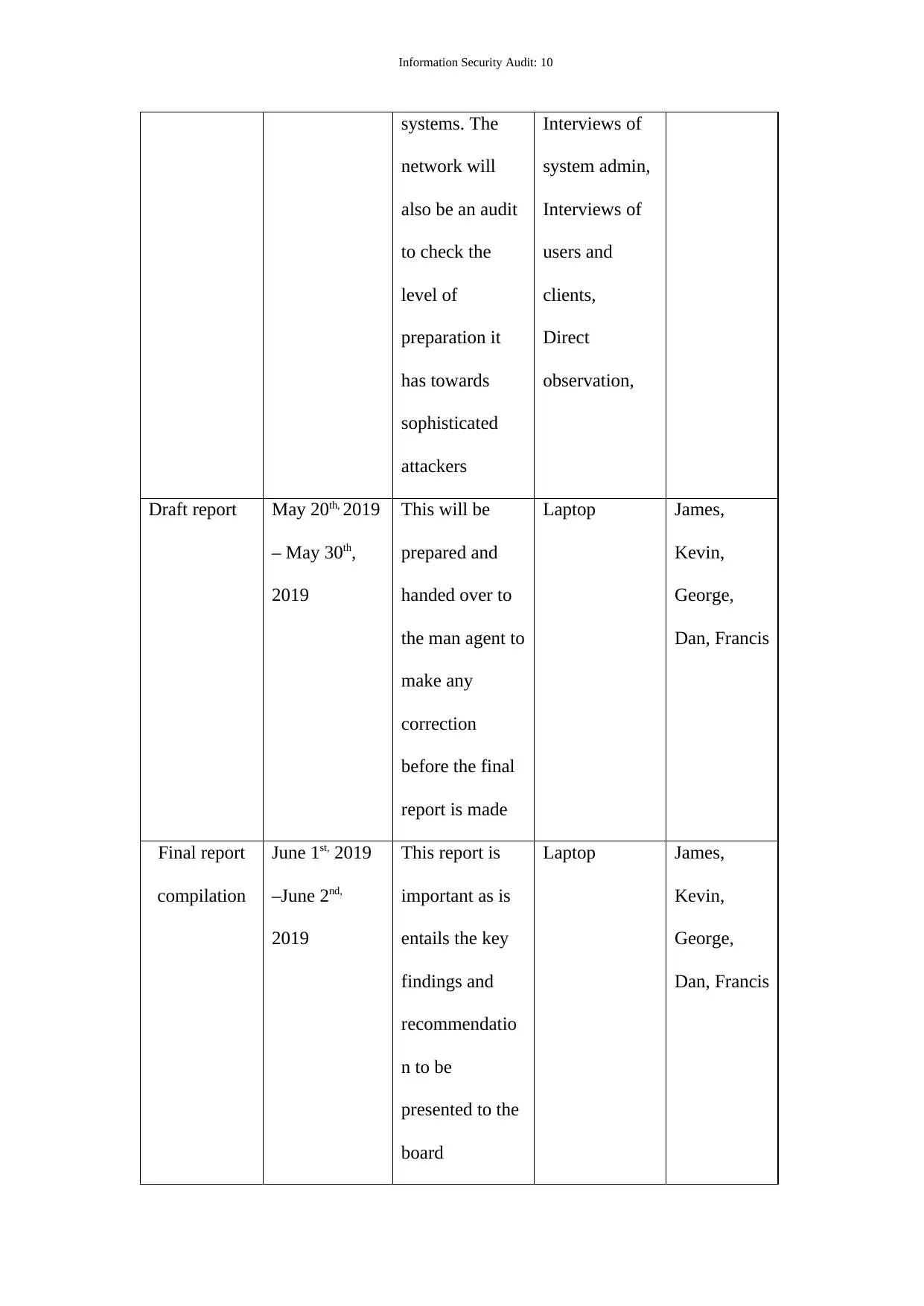
Information Security Audit: 10
systems. The
network will
also be an audit
to check the
level of
preparation it
has towards
sophisticated
attackers
Interviews of
system admin,
Interviews of
users and
clients,
Direct
observation,
Draft report May 20th, 2019
– May 30th,
2019
This will be
prepared and
handed over to
the man agent to
make any
correction
before the final
report is made
Laptop James,
Kevin,
George,
Dan, Francis
Final report
compilation
June 1st, 2019
–June 2nd,
2019
This report is
important as is
entails the key
findings and
recommendatio
n to be
presented to the
board
Laptop James,
Kevin,
George,
Dan, Francis
systems. The
network will
also be an audit
to check the
level of
preparation it
has towards
sophisticated
attackers
Interviews of
system admin,
Interviews of
users and
clients,
Direct
observation,
Draft report May 20th, 2019
– May 30th,
2019
This will be
prepared and
handed over to
the man agent to
make any
correction
before the final
report is made
Laptop James,
Kevin,
George,
Dan, Francis
Final report
compilation
June 1st, 2019
–June 2nd,
2019
This report is
important as is
entails the key
findings and
recommendatio
n to be
presented to the
board
Laptop James,
Kevin,
George,
Dan, Francis
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
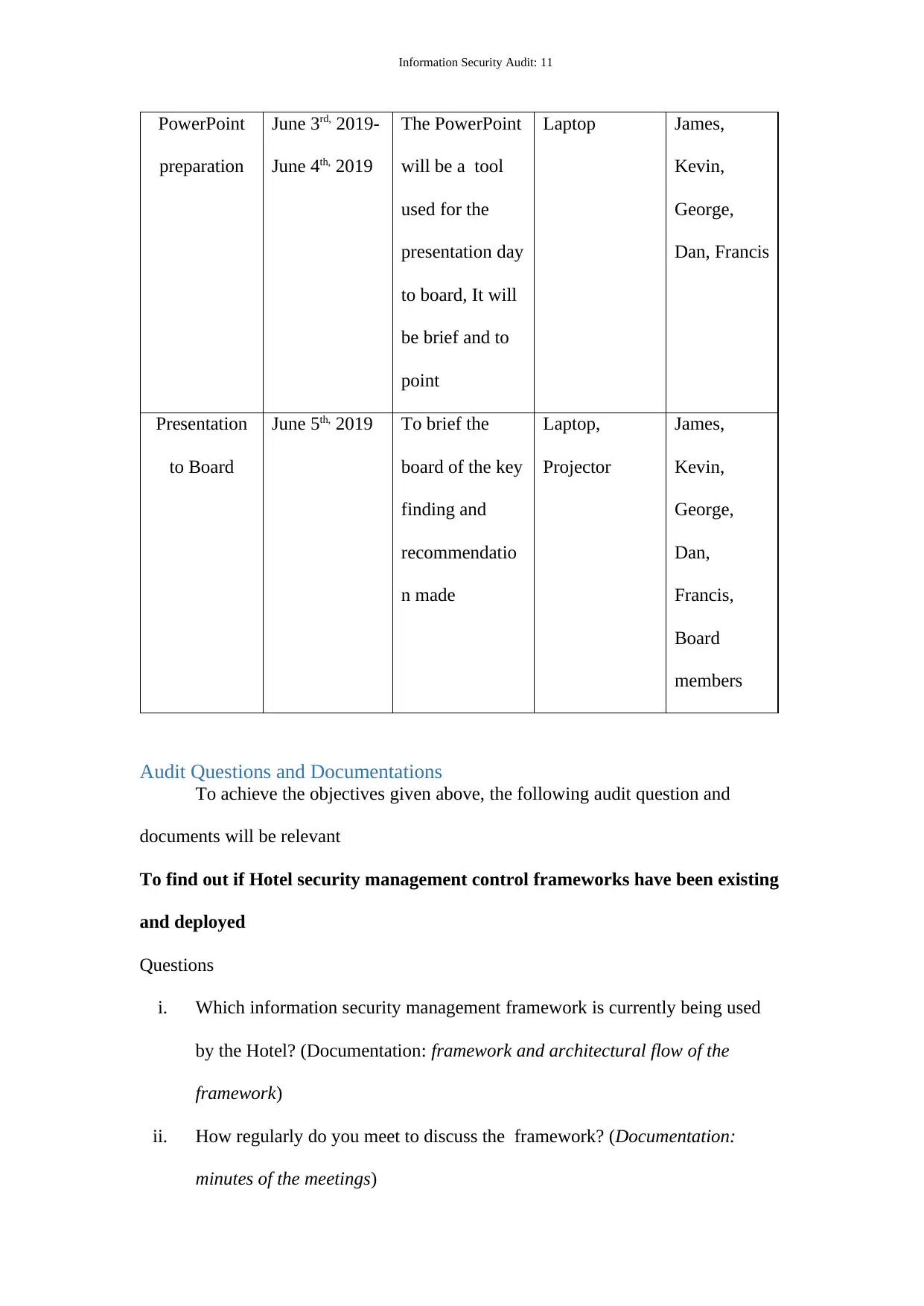
Information Security Audit: 11
PowerPoint
preparation
June 3rd, 2019-
June 4th, 2019
The PowerPoint
will be a tool
used for the
presentation day
to board, It will
be brief and to
point
Laptop James,
Kevin,
George,
Dan, Francis
Presentation
to Board
June 5th, 2019 To brief the
board of the key
finding and
recommendatio
n made
Laptop,
Projector
James,
Kevin,
George,
Dan,
Francis,
Board
members
Audit Questions and Documentations
To achieve the objectives given above, the following audit question and
documents will be relevant
To find out if Hotel security management control frameworks have been existing
and deployed
Questions
i. Which information security management framework is currently being used
by the Hotel? (Documentation: framework and architectural flow of the
framework)
ii. How regularly do you meet to discuss the framework? (Documentation:
minutes of the meetings)
PowerPoint
preparation
June 3rd, 2019-
June 4th, 2019
The PowerPoint
will be a tool
used for the
presentation day
to board, It will
be brief and to
point
Laptop James,
Kevin,
George,
Dan, Francis
Presentation
to Board
June 5th, 2019 To brief the
board of the key
finding and
recommendatio
n made
Laptop,
Projector
James,
Kevin,
George,
Dan,
Francis,
Board
members
Audit Questions and Documentations
To achieve the objectives given above, the following audit question and
documents will be relevant
To find out if Hotel security management control frameworks have been existing
and deployed
Questions
i. Which information security management framework is currently being used
by the Hotel? (Documentation: framework and architectural flow of the
framework)
ii. How regularly do you meet to discuss the framework? (Documentation:
minutes of the meetings)

Information Security Audit: 12
iii. Do you have an existing incidence response plan in place? (Documentation:
incidence response plan)
iv. Are business continuity plans included in the framework? (Documentation:
BCP)
To find out if the Hotel information security education and awareness campaigns
are adequate.
Questions
i. Do you conduct regular training to employees on information security?
(Documentation: Training Report)
ii. Is their information security awareness educational material currently
deployed (Documentation: the awareness messages tool)?
iii. How regularly do you update the awareness messages?
To find out if an effective screening of personnel is enforced
Questions
i. What procedure are in place for onboarding a new hire?
(Documentation: onboarding procedure).
ii. How to handle the firing of employees? (Insist on having a copy of
the firing procedure)
iii. What is the job description of the various experts in the IT department
(Insist on having their job roles and responsibilities document availed
and their current certifications)?
To find out how information security breaches are dealt with
iii. Do you have an existing incidence response plan in place? (Documentation:
incidence response plan)
iv. Are business continuity plans included in the framework? (Documentation:
BCP)
To find out if the Hotel information security education and awareness campaigns
are adequate.
Questions
i. Do you conduct regular training to employees on information security?
(Documentation: Training Report)
ii. Is their information security awareness educational material currently
deployed (Documentation: the awareness messages tool)?
iii. How regularly do you update the awareness messages?
To find out if an effective screening of personnel is enforced
Questions
i. What procedure are in place for onboarding a new hire?
(Documentation: onboarding procedure).
ii. How to handle the firing of employees? (Insist on having a copy of
the firing procedure)
iii. What is the job description of the various experts in the IT department
(Insist on having their job roles and responsibilities document availed
and their current certifications)?
To find out how information security breaches are dealt with
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

