Cyber Security Project: Application for HREC Approval (Standard)
VerifiedAdded on 2023/06/07
|19
|6680
|406
Homework Assignment
AI Summary
This document is an application for Human Research Ethics Committee (HREC) approval for a cyber security research project (ITECH 5500). The project aims to investigate various aspects of cyber security, including system threats, vulnerabilities, cybercrimes, countermeasures, and regulations. The application details the project's aims, significance, research questions, methodology (survey-based with primary and secondary data collection), and participant recruitment strategy. It also addresses funding, multi-center research considerations, external approvals, and ethical aspects, such as informed consent and data usage. The research seeks to understand and address the increasing cyber threats faced by organizations and individuals due to the growing reliance on the internet and information systems. The project will use survey methodology to collect data from employees of a company to identify cyber security challenges and countermeasures. The document includes a lay description explaining the project in everyday language, and a detailed outline of the research aims, significance, and ethical considerations related to the project. The application also includes details on funding, external approvals, and the recruitment of participants, ensuring compliance with ethical guidelines. The project emphasizes the importance of cyber security in protecting information and data in an increasingly interconnected world.
Application for HREC
Approval (Standard)
Human Research Ethics Committee
1. PROJECT DETAILS
Project title:
Cyber Security
What type of project is this? (Tick as many as apply)
Funded Consultancy Class Research Project Postgraduate Diploma
Clinical Trial Undergraduate Research Masters by Research
Staff Research Project Honours Research PhD
Other Masters by Coursework Higher Doctorate
Through which School/Section is the research to be conducted?
ITECH 5500 Professional Research and Communication
What is your expected completion date? (Approval will be granted up until this date)
28/09/2018
Your project must not commence until full approval is granted.
2. RESEARCHERS
Principal Researcher (must be a STAFF MEMBER)
Title & Name:
Position:
School/Section:
Phone number:
Email address:
Academic qualifications:
Describe what this researcher will do in
the context of this project:
Include a brief summary of relevant
experience for this project:
Student/Other Researcher/s
**copy and paste this table for each person involved in the project
Title & Name:
Position:
School/Section:
Phone number:
Email address:
Student ID number:
Academic qualifications:
Describe what this researcher will do in
the context of this project:
Cyber security is the process of securing data and
information systems from theft, damage, corruption, or
disruption; sometimes it is referred to as computer
security or IT security. It entails protection of data and
information systems from physical access,
unauthorized network access, data and code injections,
CRICOS Provider No. 00103D V1 2018 Page 1 of 19
Approval (Standard)
Human Research Ethics Committee
1. PROJECT DETAILS
Project title:
Cyber Security
What type of project is this? (Tick as many as apply)
Funded Consultancy Class Research Project Postgraduate Diploma
Clinical Trial Undergraduate Research Masters by Research
Staff Research Project Honours Research PhD
Other Masters by Coursework Higher Doctorate
Through which School/Section is the research to be conducted?
ITECH 5500 Professional Research and Communication
What is your expected completion date? (Approval will be granted up until this date)
28/09/2018
Your project must not commence until full approval is granted.
2. RESEARCHERS
Principal Researcher (must be a STAFF MEMBER)
Title & Name:
Position:
School/Section:
Phone number:
Email address:
Academic qualifications:
Describe what this researcher will do in
the context of this project:
Include a brief summary of relevant
experience for this project:
Student/Other Researcher/s
**copy and paste this table for each person involved in the project
Title & Name:
Position:
School/Section:
Phone number:
Email address:
Student ID number:
Academic qualifications:
Describe what this researcher will do in
the context of this project:
Cyber security is the process of securing data and
information systems from theft, damage, corruption, or
disruption; sometimes it is referred to as computer
security or IT security. It entails protection of data and
information systems from physical access,
unauthorized network access, data and code injections,
CRICOS Provider No. 00103D V1 2018 Page 1 of 19
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Application for HREC
Approval (Standard)
Human Research Ethics Committee
and other malpractices that may impact the privacy
and integrity of data and information. Currently, there
the use of computer and internet have increased
because of technology evolution over the years.
Include a brief summary of relevant
experience for this project:
Cyber security is a wide subject that should be handled
by several key experts. Cyber criminals are educated
and well-informed on cyber trends to enable them steal
secret and private information, intellectual property,
and confidential information. Cybercrimes are
becoming more frequent and complex especially
where financial gain is involved. Individuals,
governments, businesses, and corporations are
becoming a baseline of cyberattacks because of the
increasing use of internet. The way individuals share
information and communicate through the internet has
evolved because of the emergence of social
networking sites, cloud computing, and smart phones.
The increasing volume of data and information over
the internet has necessitated the need of cyber security.
There exist many computer crimes that may adversely
affect organizations in terms of loss of information and
money.
3. LAY DESCRIPTION
Provide a brief outline of the project describing in everyday, jargon-free language the key aspects
of the research (e.g., who will be participating, what information will be collected and by what
means, what participants will be required to do, etc.) and the key research aims. The lay
description must be in everyday, jargon-free language that is comprehensible by the average
educated layperson. Define any technical terms or discipline-specific phrases, and use the full form
of all acronyms the first time they are used. (300 words max.)
This report seeks to expound on the subject of cyber security and the various issues facing
this concept. It explores the increasing threats and vulnerabilities affecting information systems. The
increasing use of internet across the world has improved communications and information sharing
but have also given rise to more cyberattacks. The effects and impacts of cybercrime are real even
though online threats are not visible; globally accessed information systems are the mostly targeted
systems and thus are more vulnerable. The value of information to companies and governments gets
more amplified as its transmission on cyberspace continue to increase.
Cyber criminals are identifying more system vulnerabilities in the major networks and thus
information security remains a major concern around the world. Each day new cyber tools and
disruptive technologies are challenging organizations to implement new security intelligence
measure that can be able to detect, sieve, and notify for any possible threat. This paper gives more
details on information systems threats and vulnerabilities, types of cybercrimes, factors promoting
cybercrimes, counter measures to cybercrimes, and cyber security regulations.
CRICOS Provider No. 00103D V1 2018 Page 2 of 19
Approval (Standard)
Human Research Ethics Committee
and other malpractices that may impact the privacy
and integrity of data and information. Currently, there
the use of computer and internet have increased
because of technology evolution over the years.
Include a brief summary of relevant
experience for this project:
Cyber security is a wide subject that should be handled
by several key experts. Cyber criminals are educated
and well-informed on cyber trends to enable them steal
secret and private information, intellectual property,
and confidential information. Cybercrimes are
becoming more frequent and complex especially
where financial gain is involved. Individuals,
governments, businesses, and corporations are
becoming a baseline of cyberattacks because of the
increasing use of internet. The way individuals share
information and communicate through the internet has
evolved because of the emergence of social
networking sites, cloud computing, and smart phones.
The increasing volume of data and information over
the internet has necessitated the need of cyber security.
There exist many computer crimes that may adversely
affect organizations in terms of loss of information and
money.
3. LAY DESCRIPTION
Provide a brief outline of the project describing in everyday, jargon-free language the key aspects
of the research (e.g., who will be participating, what information will be collected and by what
means, what participants will be required to do, etc.) and the key research aims. The lay
description must be in everyday, jargon-free language that is comprehensible by the average
educated layperson. Define any technical terms or discipline-specific phrases, and use the full form
of all acronyms the first time they are used. (300 words max.)
This report seeks to expound on the subject of cyber security and the various issues facing
this concept. It explores the increasing threats and vulnerabilities affecting information systems. The
increasing use of internet across the world has improved communications and information sharing
but have also given rise to more cyberattacks. The effects and impacts of cybercrime are real even
though online threats are not visible; globally accessed information systems are the mostly targeted
systems and thus are more vulnerable. The value of information to companies and governments gets
more amplified as its transmission on cyberspace continue to increase.
Cyber criminals are identifying more system vulnerabilities in the major networks and thus
information security remains a major concern around the world. Each day new cyber tools and
disruptive technologies are challenging organizations to implement new security intelligence
measure that can be able to detect, sieve, and notify for any possible threat. This paper gives more
details on information systems threats and vulnerabilities, types of cybercrimes, factors promoting
cybercrimes, counter measures to cybercrimes, and cyber security regulations.
CRICOS Provider No. 00103D V1 2018 Page 2 of 19

Application for HREC
Approval (Standard)
Human Research Ethics Committee
4. RESEARCH AIMS & SIGNIFICANCE
State the aims, key research questions, and significance of the project. Where relevant, state the
specific hypothesis to be tested. Also provide a brief description of the relevance of your proposed
project to current research; (supported by a literature review and references) – refer to National
Statement 1.1c, a justification as to why your research should proceed, including an explanation of
any expected benefits to the community and its potential to contribute to existing knowledge.
(600 words max.)
Statement of Problem
The increasing overdependence of computers and internet by almost all organizations and
industries as well as individuals to share and transmit data and information have posed great
challenges to cyber security. As such there is need to protect and secure cyber segments of the
information systems against the increasing cybercrimes such as hacking and phishing. Cyber-attacks
have led to disruption of many information systems as it has been evidenced in various critical
infrastructures such as inventory and financial systems which has resulted to loses. As such there is
need to develop measure and systems to address this challenge.
Research Questions
This research seeks to answer the following questions:
i. What are some of the existing system threats and vulnerabilities?
ii. What are the common types of cybercrimes?
iii. What factors are promoting cybercrimes?
iv. What cybercrime counter measures can be put in place?
v. What are some of the cyber security regulations?
Aims and Objectives
The following are the objectives that this research seeks to accomplish:
i. Identify information system threats and vulnerabilities
ii. Identify the common types of cybercrimes
iii. Identify the factors promoting cybercrimes
iv. Identify counter measures to cybercrimes
v. Identify cyber security regulations.
This report will seek to discuss the various aspects of cyber security including threats and
vulnerabilities, cybercrimes, cybercrime counter measures, factors promoting cybercrimes, and
cyber security regulations.
5. FUNDING & FINANCIAL BENEFITS
Researchers should include any source of funding (e.g., departmental, commercial, non-
commercial, governmental) The HREC will consider whether there is a conflict of interest.
CRICOS Provider No. 00103D V1 2018 Page 3 of 19
Approval (Standard)
Human Research Ethics Committee
4. RESEARCH AIMS & SIGNIFICANCE
State the aims, key research questions, and significance of the project. Where relevant, state the
specific hypothesis to be tested. Also provide a brief description of the relevance of your proposed
project to current research; (supported by a literature review and references) – refer to National
Statement 1.1c, a justification as to why your research should proceed, including an explanation of
any expected benefits to the community and its potential to contribute to existing knowledge.
(600 words max.)
Statement of Problem
The increasing overdependence of computers and internet by almost all organizations and
industries as well as individuals to share and transmit data and information have posed great
challenges to cyber security. As such there is need to protect and secure cyber segments of the
information systems against the increasing cybercrimes such as hacking and phishing. Cyber-attacks
have led to disruption of many information systems as it has been evidenced in various critical
infrastructures such as inventory and financial systems which has resulted to loses. As such there is
need to develop measure and systems to address this challenge.
Research Questions
This research seeks to answer the following questions:
i. What are some of the existing system threats and vulnerabilities?
ii. What are the common types of cybercrimes?
iii. What factors are promoting cybercrimes?
iv. What cybercrime counter measures can be put in place?
v. What are some of the cyber security regulations?
Aims and Objectives
The following are the objectives that this research seeks to accomplish:
i. Identify information system threats and vulnerabilities
ii. Identify the common types of cybercrimes
iii. Identify the factors promoting cybercrimes
iv. Identify counter measures to cybercrimes
v. Identify cyber security regulations.
This report will seek to discuss the various aspects of cyber security including threats and
vulnerabilities, cybercrimes, cybercrime counter measures, factors promoting cybercrimes, and
cyber security regulations.
5. FUNDING & FINANCIAL BENEFITS
Researchers should include any source of funding (e.g., departmental, commercial, non-
commercial, governmental) The HREC will consider whether there is a conflict of interest.
CRICOS Provider No. 00103D V1 2018 Page 3 of 19
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Application for HREC
Approval (Standard)
Human Research Ethics Committee
Are any of the researchers affiliated with or in receipt of any financial benefit
from any of the external organisations involved in your research?
Yes No
If yes, explain how, how much and for what purpose:
Has this protocol received research funding or is this submission being
made as part of an application for research funding?
Yes No
What is the status of the funding application? Approved Refused Pending
If yes, what is the source of the funding?
Not Applicable for this project
What is the project grant title and proposed grant duration?
Not Applicable for this project
What is the registration number of the grant/funding application?
Not Applicable for this project
What is the deadline for the granting body?
Not Applicable for this project
Does this project require HREC approval before consideration for
funding?
Yes No
How will participants be informed of the source of the funding?
The research coordinator will keep the participants informed
6. MULTI CENTRE RESEARCH
Other HREC Approvals
The principal researcher is responsible for informing each HREC of all other sites at which the
research is being proposed or conducted; disclosing to each HREC any previous decisions
regarding the research made by another HREC; and informing each HREC of whether the protocol
is presently before another HREC.
Is this protocol being submitted or has it been previously submitted to
another Human Research Ethics Committee?
Yes No
If yes, give details of other centres involved; the approval status of the study at each centre; and
details of any required amendments.
7. EXTERNAL APPROVALS
If your research involves participants from other organisations (e.g. educational institutions,
companies, agencies, collectives), you may need to obtain authorised approval before approaching
participants, eg: Department of Education and Training, School Principals, School Councils (for
research involving Government schools); Catholic Education Office (Catholic schools); School
Boards (Independent schools); Senior Officers (Commercial or Government entities); Elders
CRICOS Provider No. 00103D V1 2018 Page 4 of 19
Approval (Standard)
Human Research Ethics Committee
Are any of the researchers affiliated with or in receipt of any financial benefit
from any of the external organisations involved in your research?
Yes No
If yes, explain how, how much and for what purpose:
Has this protocol received research funding or is this submission being
made as part of an application for research funding?
Yes No
What is the status of the funding application? Approved Refused Pending
If yes, what is the source of the funding?
Not Applicable for this project
What is the project grant title and proposed grant duration?
Not Applicable for this project
What is the registration number of the grant/funding application?
Not Applicable for this project
What is the deadline for the granting body?
Not Applicable for this project
Does this project require HREC approval before consideration for
funding?
Yes No
How will participants be informed of the source of the funding?
The research coordinator will keep the participants informed
6. MULTI CENTRE RESEARCH
Other HREC Approvals
The principal researcher is responsible for informing each HREC of all other sites at which the
research is being proposed or conducted; disclosing to each HREC any previous decisions
regarding the research made by another HREC; and informing each HREC of whether the protocol
is presently before another HREC.
Is this protocol being submitted or has it been previously submitted to
another Human Research Ethics Committee?
Yes No
If yes, give details of other centres involved; the approval status of the study at each centre; and
details of any required amendments.
7. EXTERNAL APPROVALS
If your research involves participants from other organisations (e.g. educational institutions,
companies, agencies, collectives), you may need to obtain authorised approval before approaching
participants, eg: Department of Education and Training, School Principals, School Councils (for
research involving Government schools); Catholic Education Office (Catholic schools); School
Boards (Independent schools); Senior Officers (Commercial or Government entities); Elders
CRICOS Provider No. 00103D V1 2018 Page 4 of 19
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Application for HREC
Approval (Standard)
Human Research Ethics Committee
(Aboriginal communities); or Representative bodies (Collectives). Copies of approval letters must
be attached to this application or, if pending at the time of submission, forwarded to HREC when
available. Some authorities may decline to provide permission letters until ethics approval has
been granted. In such cases, you should submit your application to the HREC for provisional
approval pending receipt of the documentation.
Does research involve or impact on participants from external agencies or
organisations?
Yes No
If yes, has required permission been obtained from relevant agencies? Yes No
If yes, please specify from whom and attach a copy
Not applicable for this project
If no, specify from whom, and advise when this will be obtained
It does not impact on external agencies
8. RESEARCH METHODOLOGY
Provide an outline of the proposed method, including details of data collection techniques, tasks
participants will be asked to complete, the estimated time commitment involved, and how data will
be analysed. If the project includes any procedure that is already established and uses accepted
techniques please include a description of the procedure. (500 words max).
Research Methodology
This research aims to study cyber security issues using a survey methodology. A survey
carried out on XYZ ICT company is intended to identify cyber security challenges in information
systems. The survey was conducted by administering questionnaires to the employees of XYZ.
This research investigates the various cybercrimes that employees and the company at large face
daily and some of the counter measures that have been put in place to address these threats. In
these research primary and secondary data will be collected investigate the cybercrimes and the
importance of cyber security to various organizations. Survey method will be used to collect
primary data whilst secondary data will be gathered through unpublished and published materials.
Data Collection Methods
Primary data
This data is original and is collected by use of survey methodology. Respondents were
given questionnaires for them to fill. Manual questionnaires as well as online questionnaires were
used.
Secondary data
Reputable journals, product documentation, articles, and websites were used to collect
secondary data. This was used to identify what other researchers found out about the different
cyber security aspects.
CRICOS Provider No. 00103D V1 2018 Page 5 of 19
Approval (Standard)
Human Research Ethics Committee
(Aboriginal communities); or Representative bodies (Collectives). Copies of approval letters must
be attached to this application or, if pending at the time of submission, forwarded to HREC when
available. Some authorities may decline to provide permission letters until ethics approval has
been granted. In such cases, you should submit your application to the HREC for provisional
approval pending receipt of the documentation.
Does research involve or impact on participants from external agencies or
organisations?
Yes No
If yes, has required permission been obtained from relevant agencies? Yes No
If yes, please specify from whom and attach a copy
Not applicable for this project
If no, specify from whom, and advise when this will be obtained
It does not impact on external agencies
8. RESEARCH METHODOLOGY
Provide an outline of the proposed method, including details of data collection techniques, tasks
participants will be asked to complete, the estimated time commitment involved, and how data will
be analysed. If the project includes any procedure that is already established and uses accepted
techniques please include a description of the procedure. (500 words max).
Research Methodology
This research aims to study cyber security issues using a survey methodology. A survey
carried out on XYZ ICT company is intended to identify cyber security challenges in information
systems. The survey was conducted by administering questionnaires to the employees of XYZ.
This research investigates the various cybercrimes that employees and the company at large face
daily and some of the counter measures that have been put in place to address these threats. In
these research primary and secondary data will be collected investigate the cybercrimes and the
importance of cyber security to various organizations. Survey method will be used to collect
primary data whilst secondary data will be gathered through unpublished and published materials.
Data Collection Methods
Primary data
This data is original and is collected by use of survey methodology. Respondents were
given questionnaires for them to fill. Manual questionnaires as well as online questionnaires were
used.
Secondary data
Reputable journals, product documentation, articles, and websites were used to collect
secondary data. This was used to identify what other researchers found out about the different
cyber security aspects.
CRICOS Provider No. 00103D V1 2018 Page 5 of 19

Application for HREC
Approval (Standard)
Human Research Ethics Committee
Is it likely / possible that any of the data collected may be used by you, or others, for any research
other than that outlined in this application? See NS Chapter 2.2 and Chapter 3.2 when preparing
your response.
Yes No
If YES, describe below and ensure this is outlined in all Plain Language Information Sheets
and Consent forms.
Participants should be fully informed of the possibility of any future use of data collected
and their ‘extended’ or ‘unspecified’ consent gained. Failure to do this may restrict the
future use of the data.
Any restrictions on the use of participants’ data should be recorded and the record kept with
the collected data. Restrictions must be accessible to researchers who want to access
those data for research.
9. RECRUITMENT OF PARTICIPANTS
Participant Details
Describe your proposed recruitment strategy to source target participants. Provide the number and
age range, giving a justification of your proposed sample size. Include details of statistical power of
the sample where appropriate. To ensure the requirements for consent are met, refer to the
National Statement Chapter 2.2 General requirements for consent:
Sampling Technique
The research seeks to gather information on cyber security. To sample out the
participants Yamane formulae below was used:
In this formula, N is the population size, n is the sample size and e is the level of
precision. The assumption made was that there was 0.5 variability and 95% level of
confidence. Level of significance will be 5% considering the normal distribution table
0.05 being the value of e given.
At least 30% of the sample population makes a representation of the target population.
The sample is high enough to give a general conclusion about the target population
because higher samples gives higher ecological information.
Target participants
Who are the target participants? (Tick as many as applicable)
CRICOS Provider No. 00103D V1 2018 Page 6 of 19
Approval (Standard)
Human Research Ethics Committee
Is it likely / possible that any of the data collected may be used by you, or others, for any research
other than that outlined in this application? See NS Chapter 2.2 and Chapter 3.2 when preparing
your response.
Yes No
If YES, describe below and ensure this is outlined in all Plain Language Information Sheets
and Consent forms.
Participants should be fully informed of the possibility of any future use of data collected
and their ‘extended’ or ‘unspecified’ consent gained. Failure to do this may restrict the
future use of the data.
Any restrictions on the use of participants’ data should be recorded and the record kept with
the collected data. Restrictions must be accessible to researchers who want to access
those data for research.
9. RECRUITMENT OF PARTICIPANTS
Participant Details
Describe your proposed recruitment strategy to source target participants. Provide the number and
age range, giving a justification of your proposed sample size. Include details of statistical power of
the sample where appropriate. To ensure the requirements for consent are met, refer to the
National Statement Chapter 2.2 General requirements for consent:
Sampling Technique
The research seeks to gather information on cyber security. To sample out the
participants Yamane formulae below was used:
In this formula, N is the population size, n is the sample size and e is the level of
precision. The assumption made was that there was 0.5 variability and 95% level of
confidence. Level of significance will be 5% considering the normal distribution table
0.05 being the value of e given.
At least 30% of the sample population makes a representation of the target population.
The sample is high enough to give a general conclusion about the target population
because higher samples gives higher ecological information.
Target participants
Who are the target participants? (Tick as many as applicable)
CRICOS Provider No. 00103D V1 2018 Page 6 of 19
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Application for HREC
Approval (Standard)
Human Research Ethics Committee
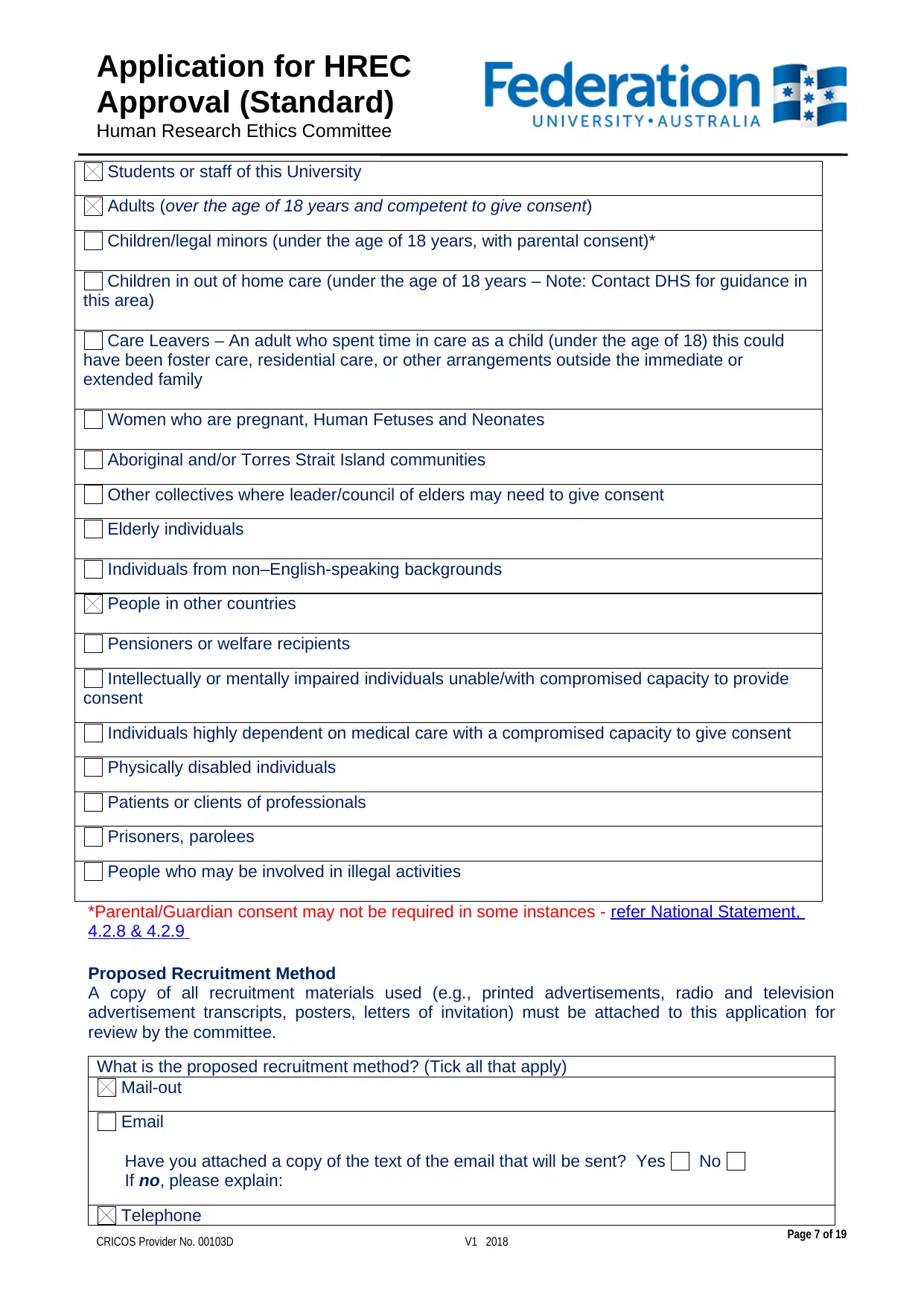
Students or staff of this University
Adults (over the age of 18 years and competent to give consent)
Children/legal minors (under the age of 18 years, with parental consent)*
Children in out of home care (under the age of 18 years – Note: Contact DHS for guidance in
this area)
Care Leavers – An adult who spent time in care as a child (under the age of 18) this could
have been foster care, residential care, or other arrangements outside the immediate or
extended family
Women who are pregnant, Human Fetuses and Neonates
Aboriginal and/or Torres Strait Island communities
Other collectives where leader/council of elders may need to give consent
Elderly individuals
Individuals from non–English-speaking backgrounds
People in other countries
Pensioners or welfare recipients
Intellectually or mentally impaired individuals unable/with compromised capacity to provide
consent
Individuals highly dependent on medical care with a compromised capacity to give consent
Physically disabled individuals
Patients or clients of professionals
Prisoners, parolees
People who may be involved in illegal activities
*Parental/Guardian consent may not be required in some instances - refer National Statement,
4.2.8 & 4.2.9
Proposed Recruitment Method
A copy of all recruitment materials used (e.g., printed advertisements, radio and television
advertisement transcripts, posters, letters of invitation) must be attached to this application for
review by the committee.
What is the proposed recruitment method? (Tick all that apply)
Mail-out
Email
Have you attached a copy of the text of the email that will be sent? Yes No
If no, please explain:
Telephone
CRICOS Provider No. 00103D V1 2018 Page 7 of 19
Approval (Standard)
Human Research Ethics Committee
Students or staff of this University
Adults (over the age of 18 years and competent to give consent)
Children/legal minors (under the age of 18 years, with parental consent)*
Children in out of home care (under the age of 18 years – Note: Contact DHS for guidance in
this area)
Care Leavers – An adult who spent time in care as a child (under the age of 18) this could
have been foster care, residential care, or other arrangements outside the immediate or
extended family
Women who are pregnant, Human Fetuses and Neonates
Aboriginal and/or Torres Strait Island communities
Other collectives where leader/council of elders may need to give consent
Elderly individuals
Individuals from non–English-speaking backgrounds
People in other countries
Pensioners or welfare recipients
Intellectually or mentally impaired individuals unable/with compromised capacity to provide
consent
Individuals highly dependent on medical care with a compromised capacity to give consent
Physically disabled individuals
Patients or clients of professionals
Prisoners, parolees
People who may be involved in illegal activities
*Parental/Guardian consent may not be required in some instances - refer National Statement,
4.2.8 & 4.2.9
Proposed Recruitment Method
A copy of all recruitment materials used (e.g., printed advertisements, radio and television
advertisement transcripts, posters, letters of invitation) must be attached to this application for
review by the committee.
What is the proposed recruitment method? (Tick all that apply)
Mail-out
Have you attached a copy of the text of the email that will be sent? Yes No
If no, please explain:
Telephone
CRICOS Provider No. 00103D V1 2018 Page 7 of 19
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Application for HREC
Approval (Standard)
Human Research Ethics Committee
Contact details obtained from public documents (e.g., phone book)
Recruitment by researcher(s)
Participants from a previous study
Snowball (participants suggest other potential participants)
Personal contacts – Provide details:
Other – please explain:
Advertisement (e.g. for a noticeboard or FedNews)
Have you attached a copy of the advertisement? Yes No
If no, please explain:
Facebook
Have you attached a copy of the advertisement that will be posted on Facebook?
Yes No
If no, please explain:
Other Social Media forum
Name forum:
Have you attached a copy of the advertisement that will be posted?
Yes No
If no, please explain:
I have read and will comply with the Federation Universities Social Media Policy and Social
Media Procedure
Yes No
If no, please explain why:
Recruitment by a third party (e.g., employer, doctor)
Have you attached a copy of the letter requesting their assistance, and/or the letter
confirming their willingness to assist? Yes No
If no, please explain:
Private sources
Have you attached a copy of the relevant approval letter? Yes No
If no, please explain:
10. BURDENS OF RESEARCH (RISK & RISK MANAGEMENT)
This section raises the issue of your duty of care toward research participants. To what risks are
participants subjected? What will you do should an emergency occur, or should a participant
become upset or distressed? What is your risk management strategy?
Refer National Statement: Section 2.1 Risk and Benefit
CRICOS Provider No. 00103D V1 2018 Page 8 of 19
Approval (Standard)
Human Research Ethics Committee
Contact details obtained from public documents (e.g., phone book)
Recruitment by researcher(s)
Participants from a previous study
Snowball (participants suggest other potential participants)
Personal contacts – Provide details:
Other – please explain:
Advertisement (e.g. for a noticeboard or FedNews)
Have you attached a copy of the advertisement? Yes No
If no, please explain:
Have you attached a copy of the advertisement that will be posted on Facebook?
Yes No
If no, please explain:
Other Social Media forum
Name forum:
Have you attached a copy of the advertisement that will be posted?
Yes No
If no, please explain:
I have read and will comply with the Federation Universities Social Media Policy and Social
Media Procedure
Yes No
If no, please explain why:
Recruitment by a third party (e.g., employer, doctor)
Have you attached a copy of the letter requesting their assistance, and/or the letter
confirming their willingness to assist? Yes No
If no, please explain:
Private sources
Have you attached a copy of the relevant approval letter? Yes No
If no, please explain:
10. BURDENS OF RESEARCH (RISK & RISK MANAGEMENT)
This section raises the issue of your duty of care toward research participants. To what risks are
participants subjected? What will you do should an emergency occur, or should a participant
become upset or distressed? What is your risk management strategy?
Refer National Statement: Section 2.1 Risk and Benefit
CRICOS Provider No. 00103D V1 2018 Page 8 of 19
Application for HREC
Approval (Standard)
Human Research Ethics Committee
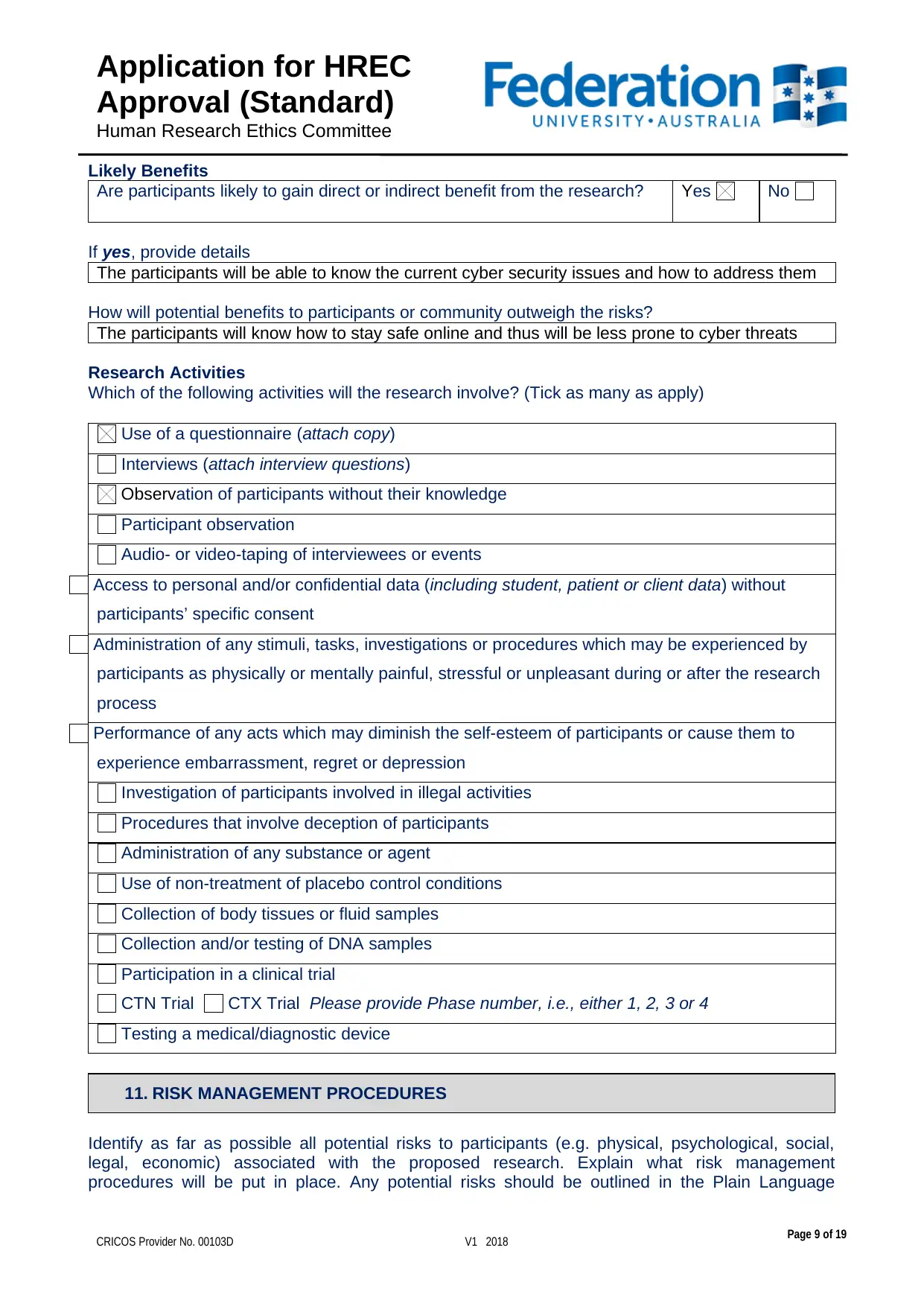
Likely Benefits
Are participants likely to gain direct or indirect benefit from the research? Yes No
If yes, provide details
The participants will be able to know the current cyber security issues and how to address them
How will potential benefits to participants or community outweigh the risks?
The participants will know how to stay safe online and thus will be less prone to cyber threats
Research Activities
Which of the following activities will the research involve? (Tick as many as apply)
Use of a questionnaire (attach copy)
Interviews (attach interview questions)
Observation of participants without their knowledge
Participant observation
Audio- or video-taping of interviewees or events
Access to personal and/or confidential data (including student, patient or client data) without
participants’ specific consent
Administration of any stimuli, tasks, investigations or procedures which may be experienced by
participants as physically or mentally painful, stressful or unpleasant during or after the research
process
Performance of any acts which may diminish the self-esteem of participants or cause them to
experience embarrassment, regret or depression
Investigation of participants involved in illegal activities
Procedures that involve deception of participants
Administration of any substance or agent
Use of non-treatment of placebo control conditions
Collection of body tissues or fluid samples
Collection and/or testing of DNA samples
Participation in a clinical trial
CTN Trial CTX Trial Please provide Phase number, i.e., either 1, 2, 3 or 4
Testing a medical/diagnostic device
11. RISK MANAGEMENT PROCEDURES
Identify as far as possible all potential risks to participants (e.g. physical, psychological, social,
legal, economic) associated with the proposed research. Explain what risk management
procedures will be put in place. Any potential risks should be outlined in the Plain Language
CRICOS Provider No. 00103D V1 2018 Page 9 of 19
Approval (Standard)
Human Research Ethics Committee
Likely Benefits
Are participants likely to gain direct or indirect benefit from the research? Yes No
If yes, provide details
The participants will be able to know the current cyber security issues and how to address them
How will potential benefits to participants or community outweigh the risks?
The participants will know how to stay safe online and thus will be less prone to cyber threats
Research Activities
Which of the following activities will the research involve? (Tick as many as apply)
Use of a questionnaire (attach copy)
Interviews (attach interview questions)
Observation of participants without their knowledge
Participant observation
Audio- or video-taping of interviewees or events
Access to personal and/or confidential data (including student, patient or client data) without
participants’ specific consent
Administration of any stimuli, tasks, investigations or procedures which may be experienced by
participants as physically or mentally painful, stressful or unpleasant during or after the research
process
Performance of any acts which may diminish the self-esteem of participants or cause them to
experience embarrassment, regret or depression
Investigation of participants involved in illegal activities
Procedures that involve deception of participants
Administration of any substance or agent
Use of non-treatment of placebo control conditions
Collection of body tissues or fluid samples
Collection and/or testing of DNA samples
Participation in a clinical trial
CTN Trial CTX Trial Please provide Phase number, i.e., either 1, 2, 3 or 4
Testing a medical/diagnostic device
11. RISK MANAGEMENT PROCEDURES
Identify as far as possible all potential risks to participants (e.g. physical, psychological, social,
legal, economic) associated with the proposed research. Explain what risk management
procedures will be put in place. Any potential risks should be outlined in the Plain Language
CRICOS Provider No. 00103D V1 2018 Page 9 of 19
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Application for HREC
Approval (Standard)
Human Research Ethics Committee
Information Statement (PLIS) along with contact details of an appropriately qualified organisation
for participant reference in case of distress, eg: Lifeline
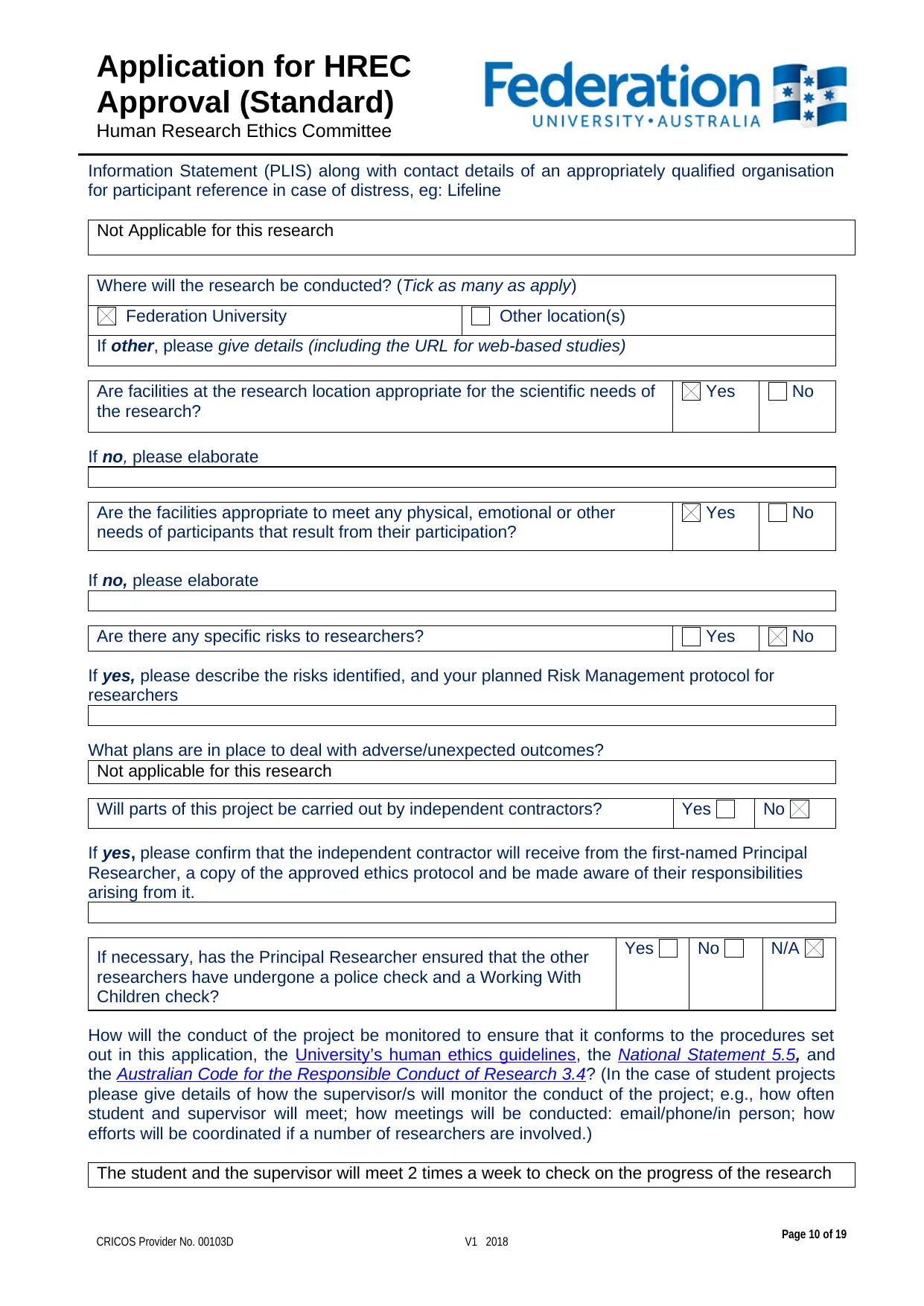
Not Applicable for this research
Where will the research be conducted? (Tick as many as apply)
Federation University Other location(s)
If other, please give details (including the URL for web-based studies)
Are facilities at the research location appropriate for the scientific needs of
the research?
Yes No
If no, please elaborate
Are the facilities appropriate to meet any physical, emotional or other
needs of participants that result from their participation?
Yes No
If no, please elaborate
Are there any specific risks to researchers? Yes No
If yes, please describe the risks identified, and your planned Risk Management protocol for
researchers
What plans are in place to deal with adverse/unexpected outcomes?
Not applicable for this research
Will parts of this project be carried out by independent contractors? Yes No
If yes, please confirm that the independent contractor will receive from the first-named Principal
Researcher, a copy of the approved ethics protocol and be made aware of their responsibilities
arising from it.
If necessary, has the Principal Researcher ensured that the other
researchers have undergone a police check and a Working With
Children check?
Yes No N/A
How will the conduct of the project be monitored to ensure that it conforms to the procedures set
out in this application, the University’s human ethics guidelines, the National Statement 5.5, and
the Australian Code for the Responsible Conduct of Research 3.4? (In the case of student projects
please give details of how the supervisor/s will monitor the conduct of the project; e.g., how often
student and supervisor will meet; how meetings will be conducted: email/phone/in person; how
efforts will be coordinated if a number of researchers are involved.)
The student and the supervisor will meet 2 times a week to check on the progress of the research
CRICOS Provider No. 00103D V1 2018 Page 10 of 19
Approval (Standard)
Human Research Ethics Committee
Information Statement (PLIS) along with contact details of an appropriately qualified organisation
for participant reference in case of distress, eg: Lifeline
Not Applicable for this research
Where will the research be conducted? (Tick as many as apply)
Federation University Other location(s)
If other, please give details (including the URL for web-based studies)
Are facilities at the research location appropriate for the scientific needs of
the research?
Yes No
If no, please elaborate
Are the facilities appropriate to meet any physical, emotional or other
needs of participants that result from their participation?
Yes No
If no, please elaborate
Are there any specific risks to researchers? Yes No
If yes, please describe the risks identified, and your planned Risk Management protocol for
researchers
What plans are in place to deal with adverse/unexpected outcomes?
Not applicable for this research
Will parts of this project be carried out by independent contractors? Yes No
If yes, please confirm that the independent contractor will receive from the first-named Principal
Researcher, a copy of the approved ethics protocol and be made aware of their responsibilities
arising from it.
If necessary, has the Principal Researcher ensured that the other
researchers have undergone a police check and a Working With
Children check?
Yes No N/A
How will the conduct of the project be monitored to ensure that it conforms to the procedures set
out in this application, the University’s human ethics guidelines, the National Statement 5.5, and
the Australian Code for the Responsible Conduct of Research 3.4? (In the case of student projects
please give details of how the supervisor/s will monitor the conduct of the project; e.g., how often
student and supervisor will meet; how meetings will be conducted: email/phone/in person; how
efforts will be coordinated if a number of researchers are involved.)
The student and the supervisor will meet 2 times a week to check on the progress of the research
CRICOS Provider No. 00103D V1 2018 Page 10 of 19
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Application for HREC
Approval (Standard)
Human Research Ethics Committee
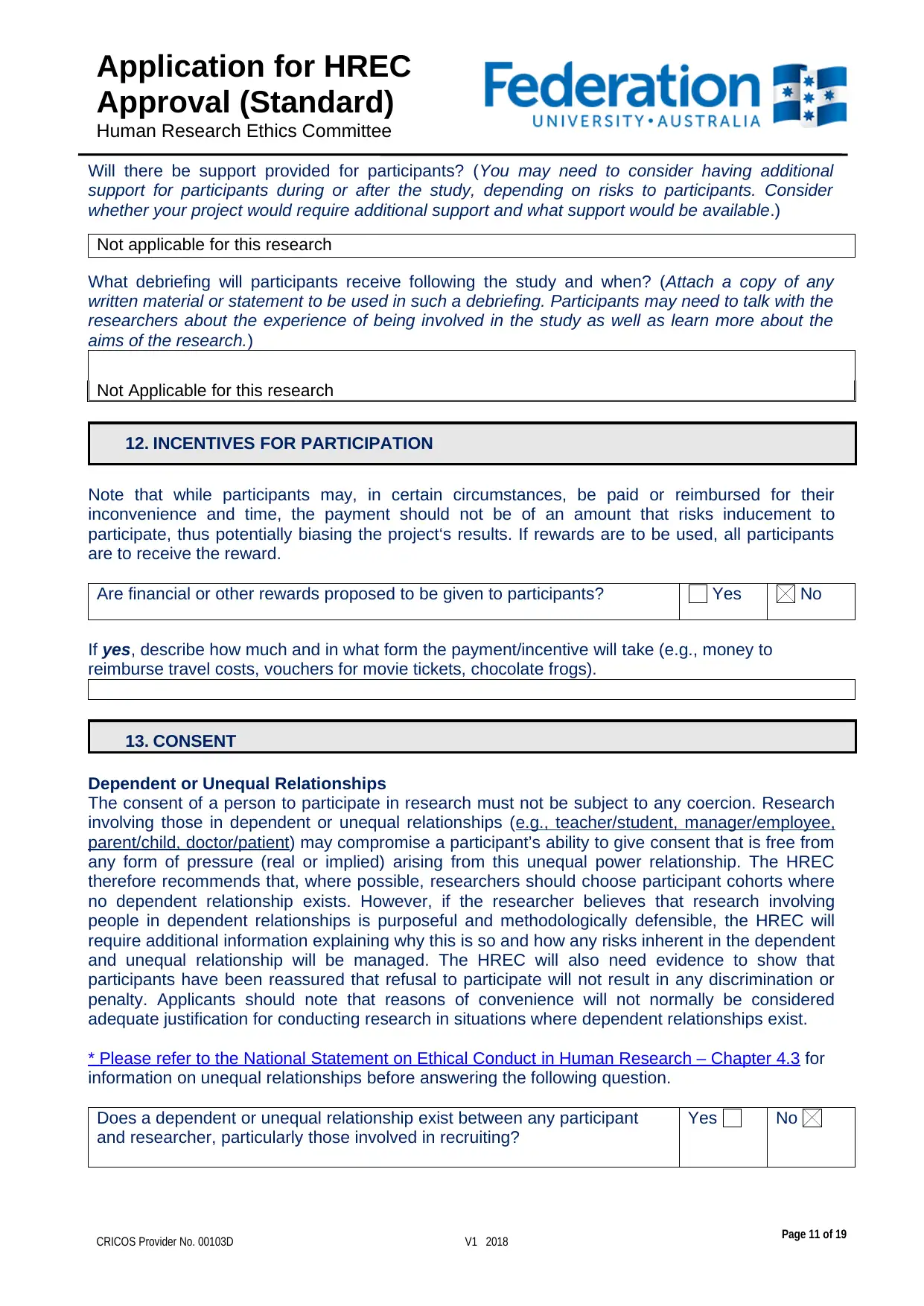
Will there be support provided for participants? (You may need to consider having additional
support for participants during or after the study, depending on risks to participants. Consider
whether your project would require additional support and what support would be available.)
Not applicable for this research
What debriefing will participants receive following the study and when? (Attach a copy of any
written material or statement to be used in such a debriefing. Participants may need to talk with the
researchers about the experience of being involved in the study as well as learn more about the
aims of the research.)
Not Applicable for this research
12. INCENTIVES FOR PARTICIPATION
Note that while participants may, in certain circumstances, be paid or reimbursed for their
inconvenience and time, the payment should not be of an amount that risks inducement to
participate, thus potentially biasing the project‘s results. If rewards are to be used, all participants
are to receive the reward.
Are financial or other rewards proposed to be given to participants? Yes No
If yes, describe how much and in what form the payment/incentive will take (e.g., money to
reimburse travel costs, vouchers for movie tickets, chocolate frogs).
13. CONSENT
Dependent or Unequal Relationships
The consent of a person to participate in research must not be subject to any coercion. Research
involving those in dependent or unequal relationships (e.g., teacher/student, manager/employee,
parent/child, doctor/patient) may compromise a participant’s ability to give consent that is free from
any form of pressure (real or implied) arising from this unequal power relationship. The HREC
therefore recommends that, where possible, researchers should choose participant cohorts where
no dependent relationship exists. However, if the researcher believes that research involving
people in dependent relationships is purposeful and methodologically defensible, the HREC will
require additional information explaining why this is so and how any risks inherent in the dependent
and unequal relationship will be managed. The HREC will also need evidence to show that
participants have been reassured that refusal to participate will not result in any discrimination or
penalty. Applicants should note that reasons of convenience will not normally be considered
adequate justification for conducting research in situations where dependent relationships exist.
* Please refer to the National Statement on Ethical Conduct in Human Research – Chapter 4.3 for
information on unequal relationships before answering the following question.
Does a dependent or unequal relationship exist between any participant
and researcher, particularly those involved in recruiting?
Yes No
CRICOS Provider No. 00103D V1 2018 Page 11 of 19
Approval (Standard)
Human Research Ethics Committee
Will there be support provided for participants? (You may need to consider having additional
support for participants during or after the study, depending on risks to participants. Consider
whether your project would require additional support and what support would be available.)
Not applicable for this research
What debriefing will participants receive following the study and when? (Attach a copy of any
written material or statement to be used in such a debriefing. Participants may need to talk with the
researchers about the experience of being involved in the study as well as learn more about the
aims of the research.)
Not Applicable for this research
12. INCENTIVES FOR PARTICIPATION
Note that while participants may, in certain circumstances, be paid or reimbursed for their
inconvenience and time, the payment should not be of an amount that risks inducement to
participate, thus potentially biasing the project‘s results. If rewards are to be used, all participants
are to receive the reward.
Are financial or other rewards proposed to be given to participants? Yes No
If yes, describe how much and in what form the payment/incentive will take (e.g., money to
reimburse travel costs, vouchers for movie tickets, chocolate frogs).
13. CONSENT
Dependent or Unequal Relationships
The consent of a person to participate in research must not be subject to any coercion. Research
involving those in dependent or unequal relationships (e.g., teacher/student, manager/employee,
parent/child, doctor/patient) may compromise a participant’s ability to give consent that is free from
any form of pressure (real or implied) arising from this unequal power relationship. The HREC
therefore recommends that, where possible, researchers should choose participant cohorts where
no dependent relationship exists. However, if the researcher believes that research involving
people in dependent relationships is purposeful and methodologically defensible, the HREC will
require additional information explaining why this is so and how any risks inherent in the dependent
and unequal relationship will be managed. The HREC will also need evidence to show that
participants have been reassured that refusal to participate will not result in any discrimination or
penalty. Applicants should note that reasons of convenience will not normally be considered
adequate justification for conducting research in situations where dependent relationships exist.
* Please refer to the National Statement on Ethical Conduct in Human Research – Chapter 4.3 for
information on unequal relationships before answering the following question.
Does a dependent or unequal relationship exist between any participant
and researcher, particularly those involved in recruiting?
Yes No
CRICOS Provider No. 00103D V1 2018 Page 11 of 19
Application for HREC
Approval (Standard)
Human Research Ethics Committee
If yes, please explain the relationship and the steps to be taken by the researchers to ensure that
the participant’s participation is purely voluntary and not influenced by the relationship in any way.
Informing Participants – Plain Language Information Statement (PLIS)
The potential participant must be provided with information at their level of comprehension about
the purpose, methods, demands, risks, inconveniences, discomforts, and possible outcomes of the
research (including the likelihood and form of publication of research results, and whether their
data may be made available for future research projects) so their consent is fully informed.
Download the current template for the PLIS from the HREC website.
Have you attached a copy of the PLIS for participants? Yes No
If no, please explain
The research will be conducted within the university with major participants being students and staff
members. Therefore, there is no need for PLIS
Does the PLIS comply with the following guidelines? YES N/A
It is presented on the Fed Uni HREC approved template, downloaded from the
website
*
It has clear identification of the University, the School(s) involved, the project
title, the Principal and Other Researchers (including FedUni contact details).
*
It details what involvement in the project will require (e.g., involvement in
interviews, completion of questionnaire, audio/video-taping of events), estimated
time commitment, any risks involved.
*
It advises how participants’ contact details were obtained and/or how potential
participants were selected
If staff or students of the Federation University are to be involved as
participants, it advises that the project has received clearance by the HREC
It advises that if the sample size is small this may have implications for
privacy/anonymity.
It states clearly that if participants are in a dependent relationship with any of the
researchers involvement in the project will not affect ongoing assessment,
grades, employment, management or treatment of health (as relevant).
It states clearly that involvement in the project is voluntary and that participants
are free to withdraw their consent to participate at any time, and to withdraw any
unprocessed data previously supplied.
*
It states that arrangements will be made to protect confidentiality of data,
including that confidentiality of information provided is subject to legal limitations
(e.g., subpoena, freedom of information claim, or mandatory reporting in some
professions).
It advises whether or not data will be destroyed after a minimum period.
It advises the de-identified data collected may be used in future research
projects
It provides any other relevant information. *
* Required
CRICOS Provider No. 00103D V1 2018 Page 12 of 19
Approval (Standard)
Human Research Ethics Committee
If yes, please explain the relationship and the steps to be taken by the researchers to ensure that
the participant’s participation is purely voluntary and not influenced by the relationship in any way.
Informing Participants – Plain Language Information Statement (PLIS)
The potential participant must be provided with information at their level of comprehension about
the purpose, methods, demands, risks, inconveniences, discomforts, and possible outcomes of the
research (including the likelihood and form of publication of research results, and whether their
data may be made available for future research projects) so their consent is fully informed.
Download the current template for the PLIS from the HREC website.
Have you attached a copy of the PLIS for participants? Yes No
If no, please explain
The research will be conducted within the university with major participants being students and staff
members. Therefore, there is no need for PLIS
Does the PLIS comply with the following guidelines? YES N/A
It is presented on the Fed Uni HREC approved template, downloaded from the
website
*
It has clear identification of the University, the School(s) involved, the project
title, the Principal and Other Researchers (including FedUni contact details).
*
It details what involvement in the project will require (e.g., involvement in
interviews, completion of questionnaire, audio/video-taping of events), estimated
time commitment, any risks involved.
*
It advises how participants’ contact details were obtained and/or how potential
participants were selected
If staff or students of the Federation University are to be involved as
participants, it advises that the project has received clearance by the HREC
It advises that if the sample size is small this may have implications for
privacy/anonymity.
It states clearly that if participants are in a dependent relationship with any of the
researchers involvement in the project will not affect ongoing assessment,
grades, employment, management or treatment of health (as relevant).
It states clearly that involvement in the project is voluntary and that participants
are free to withdraw their consent to participate at any time, and to withdraw any
unprocessed data previously supplied.
*
It states that arrangements will be made to protect confidentiality of data,
including that confidentiality of information provided is subject to legal limitations
(e.g., subpoena, freedom of information claim, or mandatory reporting in some
professions).
It advises whether or not data will be destroyed after a minimum period.
It advises the de-identified data collected may be used in future research
projects
It provides any other relevant information. *
* Required
CRICOS Provider No. 00103D V1 2018 Page 12 of 19
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





