HS1011 Data Communication and Networks: Network Design for EBiz.com
VerifiedAdded on 2023/06/07
|9
|1421
|132
Report
AI Summary
This report provides a detailed analysis of network design and configuration for EBiz.com, addressing the need for an efficient and secure network infrastructure across three floors with 250 computers and five servers. It explores the use of extended star topology for connecting the three floors, server-based network architecture for centralized data sharing, and appropriate IP addressing using Class C or Class B addresses. The report recommends routers or Level-3 switches for network management, Cat-6 cables or optical fiber for data transfer, and network monitoring software for user management. Furthermore, the report delves into subnetting, explaining the creation of four subnets using a /26 CIDR notation to enhance network security and performance. It also discusses the subnet mask and IP address configurations for a corporate customer network, creating 16 sub-networks with specific host ranges. References to relevant sources are included to support the analysis and recommendations. Desklib provides a platform to explore similar solved assignments.

Running Head: DATA COMMUNICATION AND NETWORKS 0
Data Communication and Networks
Individual task
Student Name
8/28/2018
Data Communication and Networks
Individual task
Student Name
8/28/2018
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Data Communication and networks 1
Data Communication and Networks
Scenario 1:
Answer: 1
Here extended star topology is used for this type of network, because in this network three floors
are connected. For better performance all computer are connected in extended start topology.
Topology is a structure of a network for mange physically and logically to all network devices
and systems. Physical means placement of devices and logical means flow of data. Five types of
topologies used for network designing, as Star, tree, bus, ring and Mesh topologies. There are
some hybrid topologies also used. Those are just merging of these topologies. Like star and bus
topology merge and it is known as extended star topologies.
Answer 2:
Network will be server based, because all computers are connected from all systems for sharing
customer’s information and billing databases. In case of peer-to-peer network, all systems are
connected like ring topology and if any connections fail it means whole network is down.
Answer 3:
In this Network, I can connect 254 computers with class- C subnet mask, which is start from
192.168.1.1 to 192.168.1.254. However, if I want to connect with servers also it means total 255
computers are there, so I used class B address, which are better for future.
Answer 4:
Router is best option for easiest reconfigure or Level-3 switch also work in this type of network.
Cat-6 cables will be provide good data transfer but if data transfer is high then also used optical
fiber for pairs of all devices. I can use some network monitor soft wares for managing user
information according to their used id and password.
Answer 5:
For managing three floors of building, Extended Star Topology will be used for EBiz.com. So
according to requirement it should be divided in three parts.
Data Communication and Networks
Scenario 1:
Answer: 1
Here extended star topology is used for this type of network, because in this network three floors
are connected. For better performance all computer are connected in extended start topology.
Topology is a structure of a network for mange physically and logically to all network devices
and systems. Physical means placement of devices and logical means flow of data. Five types of
topologies used for network designing, as Star, tree, bus, ring and Mesh topologies. There are
some hybrid topologies also used. Those are just merging of these topologies. Like star and bus
topology merge and it is known as extended star topologies.
Answer 2:
Network will be server based, because all computers are connected from all systems for sharing
customer’s information and billing databases. In case of peer-to-peer network, all systems are
connected like ring topology and if any connections fail it means whole network is down.
Answer 3:
In this Network, I can connect 254 computers with class- C subnet mask, which is start from
192.168.1.1 to 192.168.1.254. However, if I want to connect with servers also it means total 255
computers are there, so I used class B address, which are better for future.
Answer 4:
Router is best option for easiest reconfigure or Level-3 switch also work in this type of network.
Cat-6 cables will be provide good data transfer but if data transfer is high then also used optical
fiber for pairs of all devices. I can use some network monitor soft wares for managing user
information according to their used id and password.
Answer 5:
For managing three floors of building, Extended Star Topology will be used for EBiz.com. So
according to requirement it should be divided in three parts.
Data Communication and networks 2
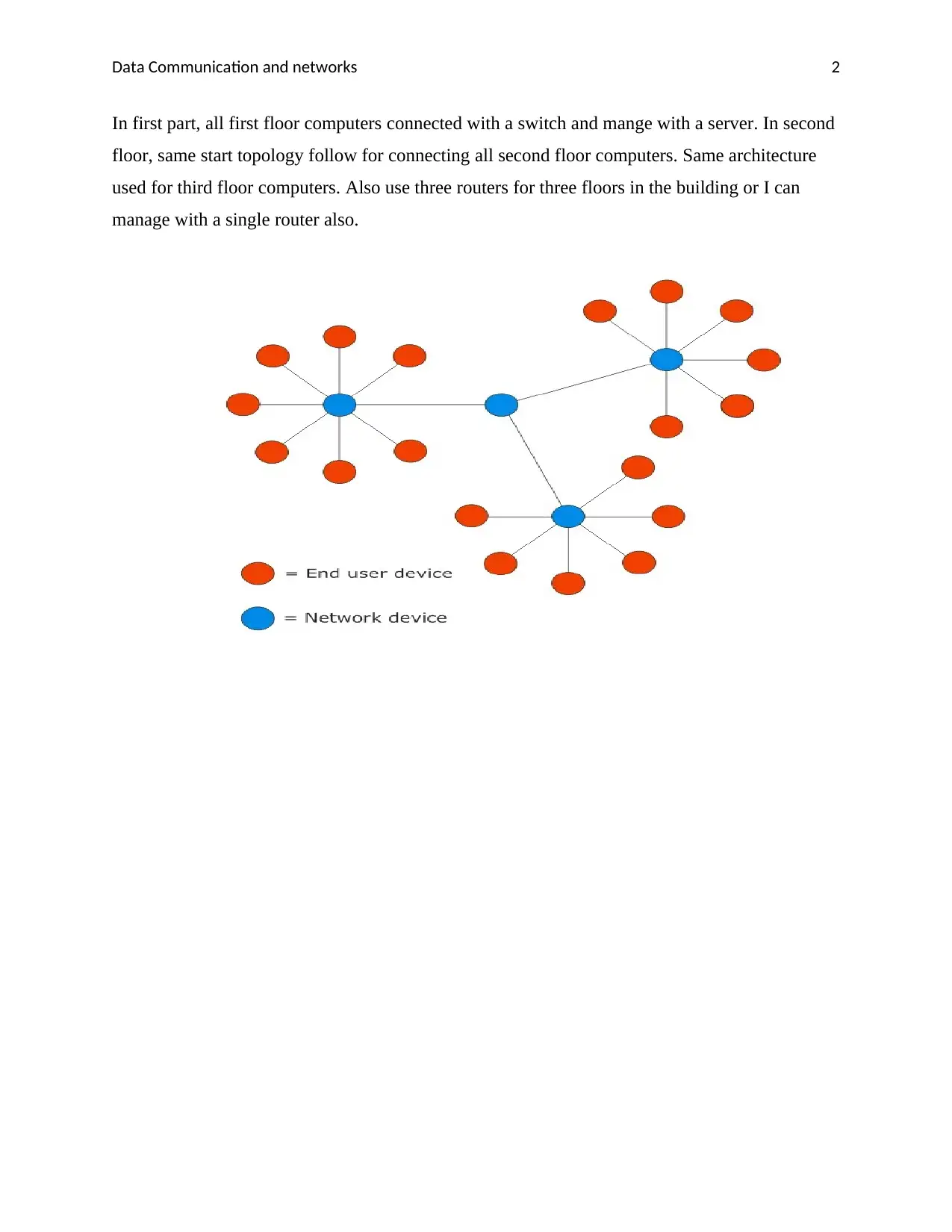
In first part, all first floor computers connected with a switch and mange with a server. In second
floor, same start topology follow for connecting all second floor computers. Same architecture
used for third floor computers. Also use three routers for three floors in the building or I can
manage with a single router also.
In first part, all first floor computers connected with a switch and mange with a server. In second
floor, same start topology follow for connecting all second floor computers. Same architecture
used for third floor computers. Also use three routers for three floors in the building or I can
manage with a single router also.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Data Communication and networks 3
Scenario 2:
Answer 1:
Before I start subnetting. I have to ask ourselves these two questions for managing network.
First is “how many subnet do I need?”
2n is number of subnets.
Where, n is the number of 1’s in the subnetmask.
So in this scenario, I need three subnets are needed for this network.
Second question is “how many hosts per subnet do I need?” in an octet, 8 bits are there so when I
take 2 bits for subnetting then 6 bits for hosts.
2m - 2 = number of hosts per subnet.
Where, y is the number of 0’s in the subnet mask.
So according to that I can manage this network by three subnets.
Answer 2:
A subnet mask allows networks to divide in small networks for security and performance
purposes. Subnet mask is not an IP address; it is a part of network bits, which are used to create
sub-networks. In this scenario, three routers are connected with three switches. Therefore, I can
divide this network in three parts.
(Source: Mubashir, 2013)
Scenario 2:
Answer 1:
Before I start subnetting. I have to ask ourselves these two questions for managing network.
First is “how many subnet do I need?”
2n is number of subnets.
Where, n is the number of 1’s in the subnetmask.
So in this scenario, I need three subnets are needed for this network.
Second question is “how many hosts per subnet do I need?” in an octet, 8 bits are there so when I
take 2 bits for subnetting then 6 bits for hosts.
2m - 2 = number of hosts per subnet.
Where, y is the number of 0’s in the subnet mask.
So according to that I can manage this network by three subnets.
Answer 2:
A subnet mask allows networks to divide in small networks for security and performance
purposes. Subnet mask is not an IP address; it is a part of network bits, which are used to create
sub-networks. In this scenario, three routers are connected with three switches. Therefore, I can
divide this network in three parts.
(Source: Mubashir, 2013)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Data Communication and networks 4
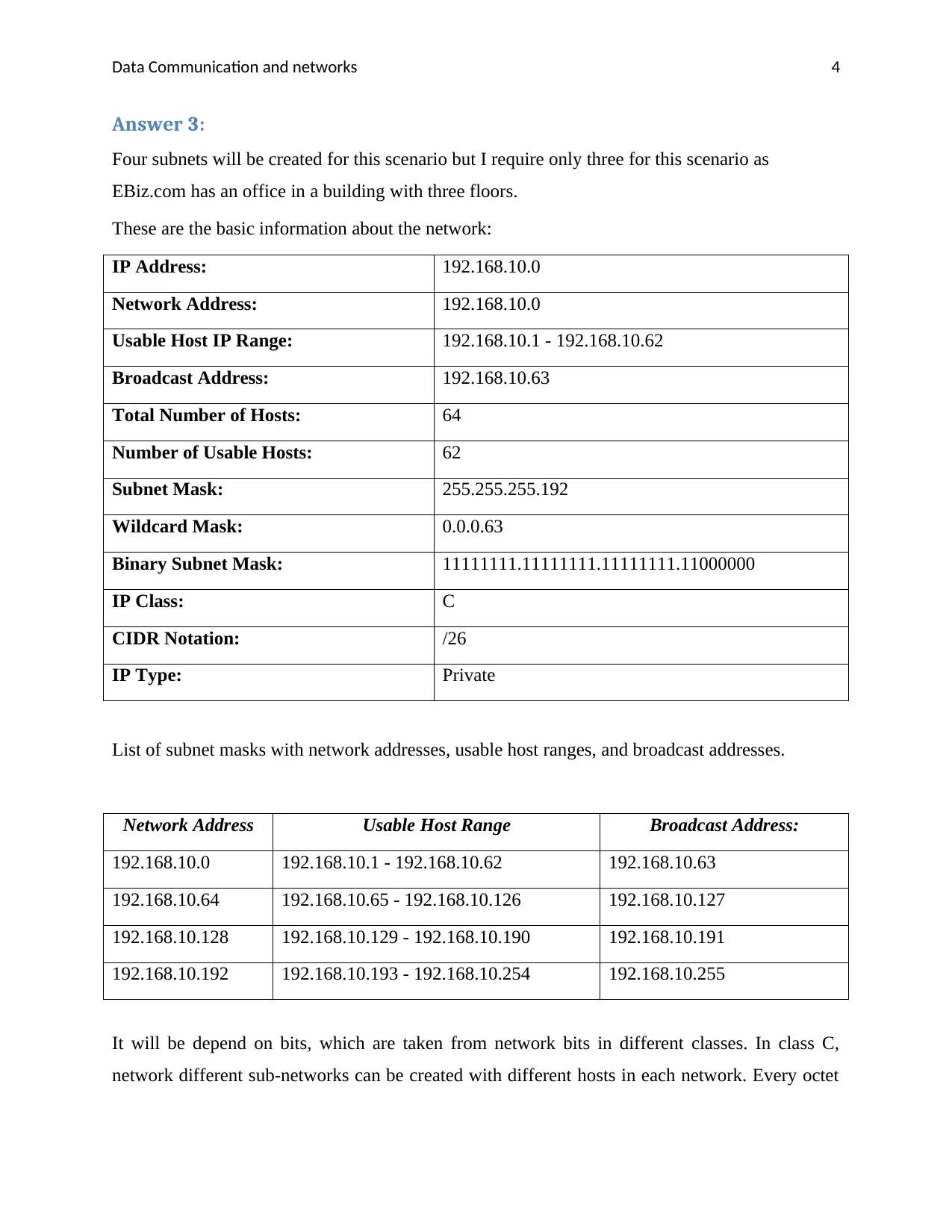
Answer 3:
Four subnets will be created for this scenario but I require only three for this scenario as
EBiz.com has an office in a building with three floors.
These are the basic information about the network:
IP Address: 192.168.10.0
Network Address: 192.168.10.0
Usable Host IP Range: 192.168.10.1 - 192.168.10.62
Broadcast Address: 192.168.10.63
Total Number of Hosts: 64
Number of Usable Hosts: 62
Subnet Mask: 255.255.255.192
Wildcard Mask: 0.0.0.63
Binary Subnet Mask: 11111111.11111111.11111111.11000000
IP Class: C
CIDR Notation: /26
IP Type: Private
List of subnet masks with network addresses, usable host ranges, and broadcast addresses.
Network Address Usable Host Range Broadcast Address:
192.168.10.0 192.168.10.1 - 192.168.10.62 192.168.10.63
192.168.10.64 192.168.10.65 - 192.168.10.126 192.168.10.127
192.168.10.128 192.168.10.129 - 192.168.10.190 192.168.10.191
192.168.10.192 192.168.10.193 - 192.168.10.254 192.168.10.255
It will be depend on bits, which are taken from network bits in different classes. In class C,
network different sub-networks can be created with different hosts in each network. Every octet
Answer 3:
Four subnets will be created for this scenario but I require only three for this scenario as
EBiz.com has an office in a building with three floors.
These are the basic information about the network:
IP Address: 192.168.10.0
Network Address: 192.168.10.0
Usable Host IP Range: 192.168.10.1 - 192.168.10.62
Broadcast Address: 192.168.10.63
Total Number of Hosts: 64
Number of Usable Hosts: 62
Subnet Mask: 255.255.255.192
Wildcard Mask: 0.0.0.63
Binary Subnet Mask: 11111111.11111111.11111111.11000000
IP Class: C
CIDR Notation: /26
IP Type: Private
List of subnet masks with network addresses, usable host ranges, and broadcast addresses.
Network Address Usable Host Range Broadcast Address:
192.168.10.0 192.168.10.1 - 192.168.10.62 192.168.10.63
192.168.10.64 192.168.10.65 - 192.168.10.126 192.168.10.127
192.168.10.128 192.168.10.129 - 192.168.10.190 192.168.10.191
192.168.10.192 192.168.10.193 - 192.168.10.254 192.168.10.255
It will be depend on bits, which are taken from network bits in different classes. In class C,
network different sub-networks can be created with different hosts in each network. Every octet
Data Communication and networks 5
has 8 bits so it is 28 means 256 nodes, but first and last used for set and reset. In this given
scenario, 4 subnets are created because I take 2 bits for sub networks.
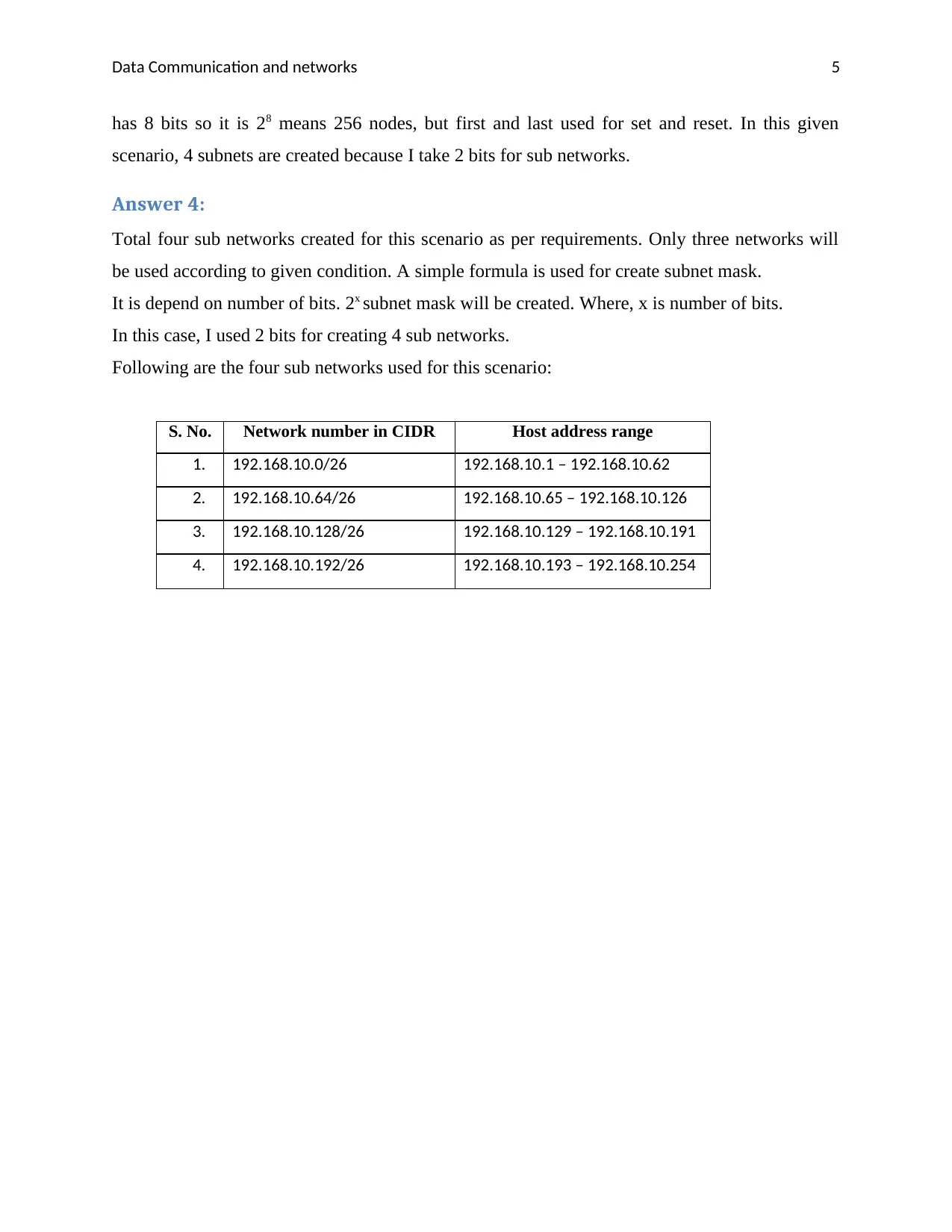
Answer 4:
Total four sub networks created for this scenario as per requirements. Only three networks will
be used according to given condition. A simple formula is used for create subnet mask.
It is depend on number of bits. 2x subnet mask will be created. Where, x is number of bits.
In this case, I used 2 bits for creating 4 sub networks.
Following are the four sub networks used for this scenario:
S. No. Network number in CIDR Host address range
1. 192.168.10.0/26 192.168.10.1 – 192.168.10.62
2. 192.168.10.64/26 192.168.10.65 – 192.168.10.126
3. 192.168.10.128/26 192.168.10.129 – 192.168.10.191
4. 192.168.10.192/26 192.168.10.193 – 192.168.10.254
has 8 bits so it is 28 means 256 nodes, but first and last used for set and reset. In this given
scenario, 4 subnets are created because I take 2 bits for sub networks.
Answer 4:
Total four sub networks created for this scenario as per requirements. Only three networks will
be used according to given condition. A simple formula is used for create subnet mask.
It is depend on number of bits. 2x subnet mask will be created. Where, x is number of bits.
In this case, I used 2 bits for creating 4 sub networks.
Following are the four sub networks used for this scenario:
S. No. Network number in CIDR Host address range
1. 192.168.10.0/26 192.168.10.1 – 192.168.10.62
2. 192.168.10.64/26 192.168.10.65 – 192.168.10.126
3. 192.168.10.128/26 192.168.10.129 – 192.168.10.191
4. 192.168.10.192/26 192.168.10.193 – 192.168.10.254
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Data Communication and networks 6
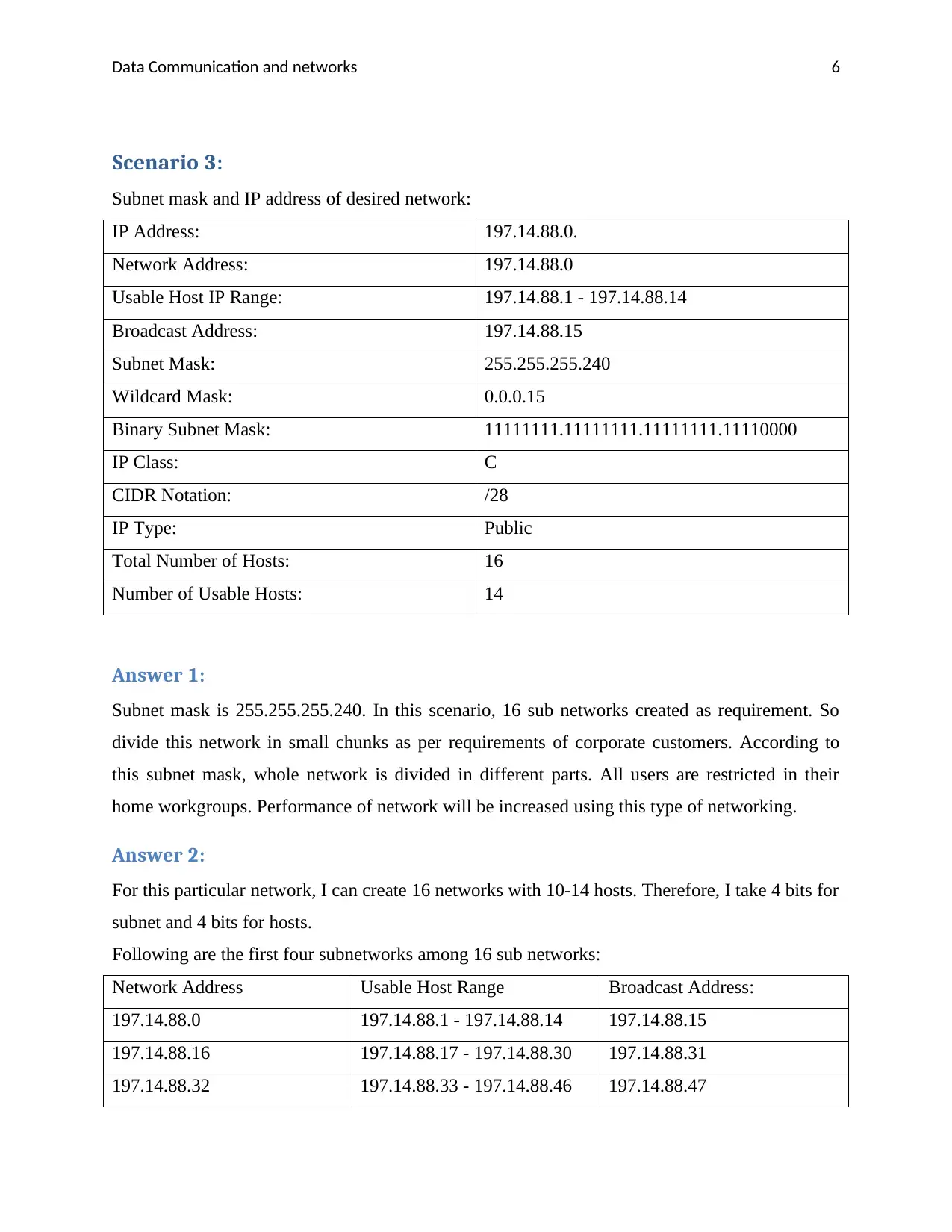
Scenario 3:
Subnet mask and IP address of desired network:
IP Address: 197.14.88.0.
Network Address: 197.14.88.0
Usable Host IP Range: 197.14.88.1 - 197.14.88.14
Broadcast Address: 197.14.88.15
Subnet Mask: 255.255.255.240
Wildcard Mask: 0.0.0.15
Binary Subnet Mask: 11111111.11111111.11111111.11110000
IP Class: C
CIDR Notation: /28
IP Type: Public
Total Number of Hosts: 16
Number of Usable Hosts: 14
Answer 1:
Subnet mask is 255.255.255.240. In this scenario, 16 sub networks created as requirement. So
divide this network in small chunks as per requirements of corporate customers. According to
this subnet mask, whole network is divided in different parts. All users are restricted in their
home workgroups. Performance of network will be increased using this type of networking.
Answer 2:
For this particular network, I can create 16 networks with 10-14 hosts. Therefore, I take 4 bits for
subnet and 4 bits for hosts.
Following are the first four subnetworks among 16 sub networks:
Network Address Usable Host Range Broadcast Address:
197.14.88.0 197.14.88.1 - 197.14.88.14 197.14.88.15
197.14.88.16 197.14.88.17 - 197.14.88.30 197.14.88.31
197.14.88.32 197.14.88.33 - 197.14.88.46 197.14.88.47
Scenario 3:
Subnet mask and IP address of desired network:
IP Address: 197.14.88.0.
Network Address: 197.14.88.0
Usable Host IP Range: 197.14.88.1 - 197.14.88.14
Broadcast Address: 197.14.88.15
Subnet Mask: 255.255.255.240
Wildcard Mask: 0.0.0.15
Binary Subnet Mask: 11111111.11111111.11111111.11110000
IP Class: C
CIDR Notation: /28
IP Type: Public
Total Number of Hosts: 16
Number of Usable Hosts: 14
Answer 1:
Subnet mask is 255.255.255.240. In this scenario, 16 sub networks created as requirement. So
divide this network in small chunks as per requirements of corporate customers. According to
this subnet mask, whole network is divided in different parts. All users are restricted in their
home workgroups. Performance of network will be increased using this type of networking.
Answer 2:
For this particular network, I can create 16 networks with 10-14 hosts. Therefore, I take 4 bits for
subnet and 4 bits for hosts.
Following are the first four subnetworks among 16 sub networks:
Network Address Usable Host Range Broadcast Address:
197.14.88.0 197.14.88.1 - 197.14.88.14 197.14.88.15
197.14.88.16 197.14.88.17 - 197.14.88.30 197.14.88.31
197.14.88.32 197.14.88.33 - 197.14.88.46 197.14.88.47
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Data Communication and networks 7
197.14.88.48 197.14.88.49 - 197.14.88.62 197.14.88.63
References
Fall, K. R. & Stevens, W. R., 2011. TCP/IP Illustrated, Volume 1: The Protocols. 2 ed. New
Jersey: Addison-Wesley.
Certiology, 2018. Network Devices:. [Online]
Available at: http://www.certiology.com/computing/computer-networking/network-devices.html
[Accessed 29 08 2018].
Cisco, 20018. IP Addressing and Subnetting for New Users. [Online]
Available at: https://www.cisco.com/c/en/us/support/docs/ip/routing-information-protocol-rip/
13788-3.html
[Accessed 29 08 2018].
Cowley, J., 2012. Communications and Networking. 2 ed. kingswinford: Springer Science &
Business Media.
Kenneth C. Mansfield, J. & Antonakos, J. L., 2009. Computer Networking for LANS to WANS:
Hardware, Software and Security. 1 ed. Bostan(MA): Cengage Learning.
lifewire, 2018. Subnet Masks and Subnetting. [Online]
Available at: https://www.lifewire.com/internet-protocol-tutorial-subnets-818378
[Accessed 28 08 2018].
Subnetting, 2018. Subnetting Tutorial. [Online]
Available at: https://www.subnetting.net/Tutorial.aspx
[Accessed 29 08 2018].
Techdonut, 2018. Network management tasks. [Online]
Available at: https://www.techdonut.co.uk/buy-and-manage-it/regular-it-maintenance/network-
management-tasks
[Accessed 29 08 2018].
197.14.88.48 197.14.88.49 - 197.14.88.62 197.14.88.63
References
Fall, K. R. & Stevens, W. R., 2011. TCP/IP Illustrated, Volume 1: The Protocols. 2 ed. New
Jersey: Addison-Wesley.
Certiology, 2018. Network Devices:. [Online]
Available at: http://www.certiology.com/computing/computer-networking/network-devices.html
[Accessed 29 08 2018].
Cisco, 20018. IP Addressing and Subnetting for New Users. [Online]
Available at: https://www.cisco.com/c/en/us/support/docs/ip/routing-information-protocol-rip/
13788-3.html
[Accessed 29 08 2018].
Cowley, J., 2012. Communications and Networking. 2 ed. kingswinford: Springer Science &
Business Media.
Kenneth C. Mansfield, J. & Antonakos, J. L., 2009. Computer Networking for LANS to WANS:
Hardware, Software and Security. 1 ed. Bostan(MA): Cengage Learning.
lifewire, 2018. Subnet Masks and Subnetting. [Online]
Available at: https://www.lifewire.com/internet-protocol-tutorial-subnets-818378
[Accessed 28 08 2018].
Subnetting, 2018. Subnetting Tutorial. [Online]
Available at: https://www.subnetting.net/Tutorial.aspx
[Accessed 29 08 2018].
Techdonut, 2018. Network management tasks. [Online]
Available at: https://www.techdonut.co.uk/buy-and-manage-it/regular-it-maintenance/network-
management-tasks
[Accessed 29 08 2018].

Data Communication and networks 8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





