Risk and Crisis Management: Procurement Fraud at HS2 High Speed Rail
VerifiedAdded on 2021/01/01
|9
|2491
|92
Report
AI Summary
This report provides a comprehensive analysis of procurement fraud risks associated with the High Speed 2 (HS2) railway project in the United Kingdom. It begins with an introduction to risk assessment and its application to procurement processes, highlighting the potential for fraud within the HS2 project, particularly in areas such as procurement, business valuation, and staff malfeasance. The report delves into the importance of fraud risk assessment tools, enterprise risk management (ERM), and the concept of risk appetite, discussing how organizations like HS2 can define and communicate their risk tolerance levels. It then examines the challenges and complexities of integrating ERM, including issues related to system implementation, human error, and the volatile environment in which HS2 operates. The report also addresses the lack of robust anti-fraud strategies in procurement and the absence of formal guidance to mitigate procurement fraud risks. Finally, it explores the integrated risk management process, its components, and its role in helping organizations achieve their objectives by identifying, assessing, and controlling risks. The report concludes by summarizing the key findings, emphasizing the need for effective risk management to combat procurement fraud and protect the integrity of the HS2 project.

RISK AND CRISIS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
INTRODUCTION...........................................................................................................................1
Fraud risk assessment..................................................................................................................1
CONCLUSION................................................................................................................................6
REFERENCES................................................................................................................................7
INTRODUCTION...........................................................................................................................1
Fraud risk assessment..................................................................................................................1
CONCLUSION................................................................................................................................6
REFERENCES................................................................................................................................7

INTRODUCTION
Risk assessment is referred as term used for purpose of describing overall method or
process where hazards and risk factors are identified which has potential to cause harm. In the
similar aspect, there is analysis and evaluation of associated risk with particular hazard such as
risk analysis and evaluation. The present report would discuss about procurement fraud risk at
high speed railways under construction in United Kingdom which is directly linked to
Birmingham, Leeds. London, Manchester and East Midlands. In the same series, it will articulate
about risk integrated for overall features of risk appetite and exposure along with difficulties,
complexities and challenges for expecting safety risk to show integration of assessment for
purpose of ERM. Furthermore, it will show implication about argument in which managers could
interpret this integrated representation of risk exposure and appetite. Lastly, this would be
supported with structure comparison along with prevailing methods of risk detection, assessment
and control.
Fraud risk assessment
Fraud risk assessment tool is replicated as invaluable resource for purpose of fraud
examiners to address and identify the vulnerabilities of clients or employers to internal fraud. At
HS2, fraud risk assessment directly forms with basis for method to manage fraud risk faced
through organization (Berry‐Stölzle and Xu, 2018). The result through multiple fraud risks
assessment for purpose of developing fraud strategy. Generally, fraud risks directly evolve with
growth of HS2 project as at present, it is as transition phase by designing to build stage. In the
present scenario, HS2 faces four major fraud risks such as procurement fraud, business or
property valuation fraud, mandate fraud and staff Malfeasance. It has been articulated that
procurement fraud is referred as greatest threat.
Procurement process is replicated as process of agreeing and finding to terms along with
acquiring goods, works or service through external source often via competitive or tendering
binding process. On basis of fraud detection, process of procurement directly employ
mechanisms of competitive bidding could be reduced to four basic stages which are pre
solicitation, solicitation, evaluation and award and last is post award and administration phase. In
this aspect, there is consideration of types of fraud risk linked with initial element of process of
procurement as pre solicitation phase (The seven global procurement fraud challenges, 2019).
Simultaneously, risk appetite is replicated as amount of risk on wide level where organization is
1
Risk assessment is referred as term used for purpose of describing overall method or
process where hazards and risk factors are identified which has potential to cause harm. In the
similar aspect, there is analysis and evaluation of associated risk with particular hazard such as
risk analysis and evaluation. The present report would discuss about procurement fraud risk at
high speed railways under construction in United Kingdom which is directly linked to
Birmingham, Leeds. London, Manchester and East Midlands. In the same series, it will articulate
about risk integrated for overall features of risk appetite and exposure along with difficulties,
complexities and challenges for expecting safety risk to show integration of assessment for
purpose of ERM. Furthermore, it will show implication about argument in which managers could
interpret this integrated representation of risk exposure and appetite. Lastly, this would be
supported with structure comparison along with prevailing methods of risk detection, assessment
and control.
Fraud risk assessment
Fraud risk assessment tool is replicated as invaluable resource for purpose of fraud
examiners to address and identify the vulnerabilities of clients or employers to internal fraud. At
HS2, fraud risk assessment directly forms with basis for method to manage fraud risk faced
through organization (Berry‐Stölzle and Xu, 2018). The result through multiple fraud risks
assessment for purpose of developing fraud strategy. Generally, fraud risks directly evolve with
growth of HS2 project as at present, it is as transition phase by designing to build stage. In the
present scenario, HS2 faces four major fraud risks such as procurement fraud, business or
property valuation fraud, mandate fraud and staff Malfeasance. It has been articulated that
procurement fraud is referred as greatest threat.
Procurement process is replicated as process of agreeing and finding to terms along with
acquiring goods, works or service through external source often via competitive or tendering
binding process. On basis of fraud detection, process of procurement directly employ
mechanisms of competitive bidding could be reduced to four basic stages which are pre
solicitation, solicitation, evaluation and award and last is post award and administration phase. In
this aspect, there is consideration of types of fraud risk linked with initial element of process of
procurement as pre solicitation phase (The seven global procurement fraud challenges, 2019).
Simultaneously, risk appetite is replicated as amount of risk on wide level where organization is
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
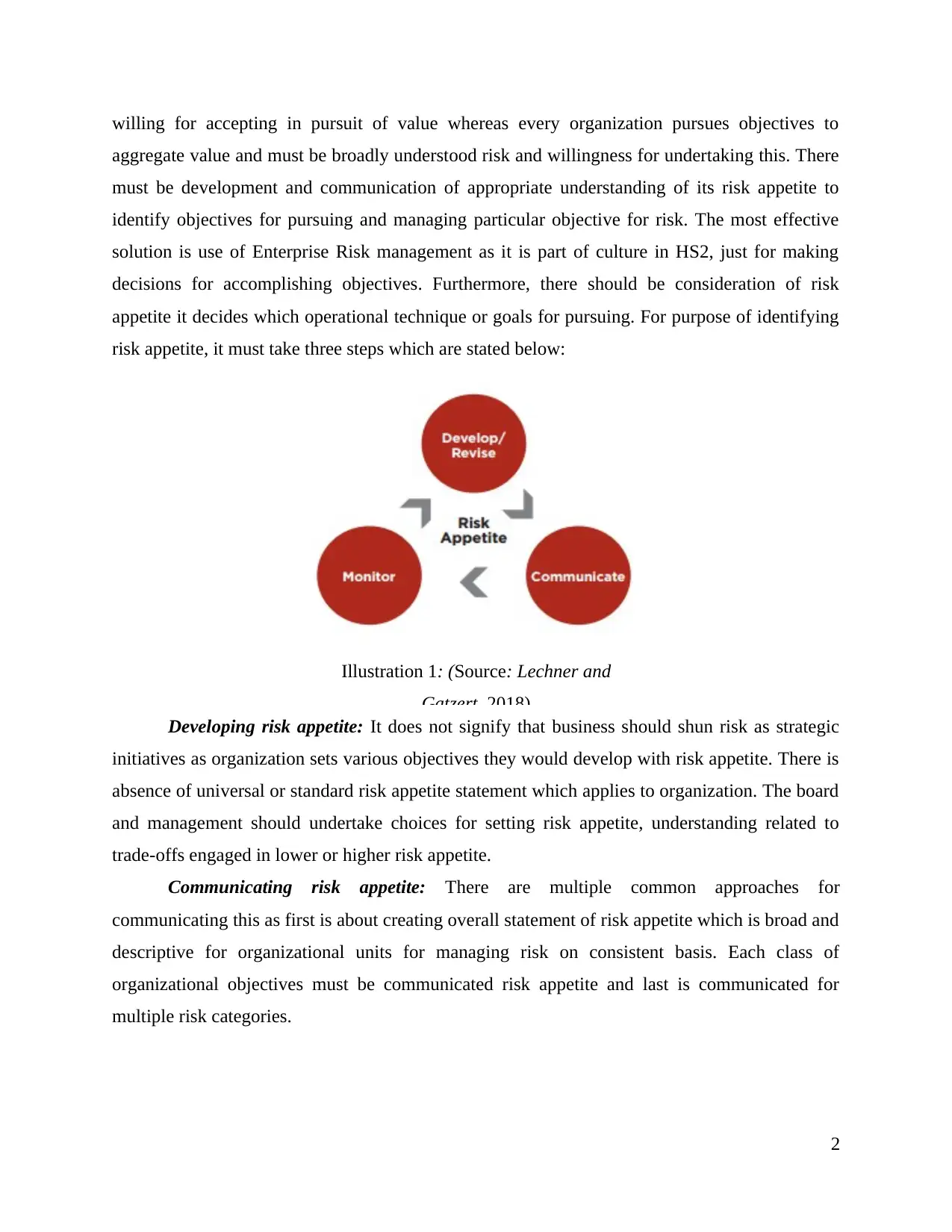
willing for accepting in pursuit of value whereas every organization pursues objectives to
aggregate value and must be broadly understood risk and willingness for undertaking this. There
must be development and communication of appropriate understanding of its risk appetite to
identify objectives for pursuing and managing particular objective for risk. The most effective
solution is use of Enterprise Risk management as it is part of culture in HS2, just for making
decisions for accomplishing objectives. Furthermore, there should be consideration of risk
appetite it decides which operational technique or goals for pursuing. For purpose of identifying
risk appetite, it must take three steps which are stated below:
Illustration 1: (Source: Lechner and
Gatzert, 2018)
Developing risk appetite: It does not signify that business should shun risk as strategic
initiatives as organization sets various objectives they would develop with risk appetite. There is
absence of universal or standard risk appetite statement which applies to organization. The board
and management should undertake choices for setting risk appetite, understanding related to
trade-offs engaged in lower or higher risk appetite.
Communicating risk appetite: There are multiple common approaches for
communicating this as first is about creating overall statement of risk appetite which is broad and
descriptive for organizational units for managing risk on consistent basis. Each class of
organizational objectives must be communicated risk appetite and last is communicated for
multiple risk categories.
2
aggregate value and must be broadly understood risk and willingness for undertaking this. There
must be development and communication of appropriate understanding of its risk appetite to
identify objectives for pursuing and managing particular objective for risk. The most effective
solution is use of Enterprise Risk management as it is part of culture in HS2, just for making
decisions for accomplishing objectives. Furthermore, there should be consideration of risk
appetite it decides which operational technique or goals for pursuing. For purpose of identifying
risk appetite, it must take three steps which are stated below:
Illustration 1: (Source: Lechner and
Gatzert, 2018)
Developing risk appetite: It does not signify that business should shun risk as strategic
initiatives as organization sets various objectives they would develop with risk appetite. There is
absence of universal or standard risk appetite statement which applies to organization. The board
and management should undertake choices for setting risk appetite, understanding related to
trade-offs engaged in lower or higher risk appetite.
Communicating risk appetite: There are multiple common approaches for
communicating this as first is about creating overall statement of risk appetite which is broad and
descriptive for organizational units for managing risk on consistent basis. Each class of
organizational objectives must be communicated risk appetite and last is communicated for
multiple risk categories.
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Monitor and updating risk appetite: after communication, it must be reinforce or revisit
and it could not set and then left alone. This should be reviewed in context that how HS2
operates especially with presence of alteration in business model.
While articulating challenges and complexities to integrate Enterprise risk management
in HS2, it has articulated multiple aspects as first is system itself could be improper and other
second factor direct deals with human error and then environment complexities. Moreover, other
factors directly deal with issues in determining risk which are linked to last part of specific
metrics (Lundqvist and Vilhelmsson, 2018). On basis of human errors, it ensures about
framework which suits organization whereas human factors are required to be minimised. The
first problem is that not everyone could be on same page so project team must develop as
glossary of risk at initial phase of implementation process of ERM so HS2 could save money and
time as well. In this aspect, team of risk management has to fully agree on definition of risks, its
assessment and management , significance, ERM , residual risk, inherent risk and likelihood. The
more advanced techniques of risk identification like control self assessment, might be adopted
eventually. However, every team member authority along with responsibility for risk should be
spelled out.
Furthermore, with context to complex environment is that world faces VUCA as with
volatility, uncertainty, complexity and ambiguity. Volatility is replicated as dynamics, speed and
nature of change forces. Uncertainty points out lack of predictability of events and issues and
complexity is confounding of problems and chaos which surrounds of organisation. Lastly,
ambiguity is haziness of reality and mixed meaning of conditions, cause and effect confusion. As
per evaluating and measuring risk it is very important to know about happening in environment
as Tsunamis, hurricanes, terrorism and earthquakes impacts organizations throughout the world.
The most important challenge is related to process as identify risks, assessing risk, evaluating,
treating and monitoring risk. With reference to this process, it must include reviews of initial
reports of audit, brainstorming, business studies, scenario analysis and many more. The
challenge here is for determining proper technique along with its combination so various risks
could be cared in effective format.
On the contrary, procurement fraud risk is with absence of doubt of more visibility in UK
and at international phase as well. The procurement fraud is not reflected on agenda of
boardroom and often no strategy of anti-fraud in procurement started across the business. In the
3
and it could not set and then left alone. This should be reviewed in context that how HS2
operates especially with presence of alteration in business model.
While articulating challenges and complexities to integrate Enterprise risk management
in HS2, it has articulated multiple aspects as first is system itself could be improper and other
second factor direct deals with human error and then environment complexities. Moreover, other
factors directly deal with issues in determining risk which are linked to last part of specific
metrics (Lundqvist and Vilhelmsson, 2018). On basis of human errors, it ensures about
framework which suits organization whereas human factors are required to be minimised. The
first problem is that not everyone could be on same page so project team must develop as
glossary of risk at initial phase of implementation process of ERM so HS2 could save money and
time as well. In this aspect, team of risk management has to fully agree on definition of risks, its
assessment and management , significance, ERM , residual risk, inherent risk and likelihood. The
more advanced techniques of risk identification like control self assessment, might be adopted
eventually. However, every team member authority along with responsibility for risk should be
spelled out.
Furthermore, with context to complex environment is that world faces VUCA as with
volatility, uncertainty, complexity and ambiguity. Volatility is replicated as dynamics, speed and
nature of change forces. Uncertainty points out lack of predictability of events and issues and
complexity is confounding of problems and chaos which surrounds of organisation. Lastly,
ambiguity is haziness of reality and mixed meaning of conditions, cause and effect confusion. As
per evaluating and measuring risk it is very important to know about happening in environment
as Tsunamis, hurricanes, terrorism and earthquakes impacts organizations throughout the world.
The most important challenge is related to process as identify risks, assessing risk, evaluating,
treating and monitoring risk. With reference to this process, it must include reviews of initial
reports of audit, brainstorming, business studies, scenario analysis and many more. The
challenge here is for determining proper technique along with its combination so various risks
could be cared in effective format.
On the contrary, procurement fraud risk is with absence of doubt of more visibility in UK
and at international phase as well. The procurement fraud is not reflected on agenda of
boardroom and often no strategy of anti-fraud in procurement started across the business. In the
3

same series, successful anti-fraud strategy comprises identification of risk, detection, prevention
and investigation. Various organization has some form of anti-bribery along with strategy of
corruption and guidance as well. It is potentially high risk area as numerous organizations carries
numerous transactions of procurement per year. Simultaneously, lack of risk identification incur
virtually in each area encountered globally. Multiple organizations such as HS2 does not have
fraud in procurement on register of risk with designated risk owner. In addition to this,
procurement fraud is not replicated as threat within project. There is often absence of formal
guidance within HS2 to mitigate and decrease risk of procurement fraud. It is associated with
lack of strategy and impossible to say that fraud could not be substituted on complete aspect but
focusing on decreasing opportunities to happen at initial place and raised likelihood of fraudsters
being caught.
Although it has been implicated that amount of risk at wide level, a business is directly
willing for accepting pursuit of value along with reflection of risk management philosophy
which influences culture of entity along with its operating style. Risk appetite guides allocation
of resource and aligns business, people and processes in infrastructure to respond and monitor
risks. It has been implicated that risk appetite is strategic and related to pursuit objectives of
organizations. This directly forms integral part of corporate governance and guides resource
allocation. Simultaneously, this guides infrastructure of business which supports activities on
basis of assessing, responding, recognising and monitoring risk with pursuit of organizational
objectives. It has been extracted that risk appetite influences HS2's attitude towards risk and in
multi-dimensional includes applied to value pursuit in long and short term strategic planning
cycle (Fraud Risk Assessment Tool, 2019). Although, there is requirement of effective
monitoring of risk and continues for risk appetite as integral part of Enterprise risk management.
Moreover, ERM is defined as overarching framework and is structure as analytical
process which concentrates on determining and substituting financial impact along with volatility
of a risk portfolio. The significance is that each risk could be offered as opportunity for gaining
competitive advantage. It has been resulted that organization with strong ERM system could
directly outperform as business with weak system. Furthermore, risk appetite is known as
exposure level that business is prepared for accept, mainly risk tolerated through company. This
has been suggested that business is required for managing risks in cases of risk occurrence could
have presence of serious consequences related to activities. The risk complexity and increment
4
and investigation. Various organization has some form of anti-bribery along with strategy of
corruption and guidance as well. It is potentially high risk area as numerous organizations carries
numerous transactions of procurement per year. Simultaneously, lack of risk identification incur
virtually in each area encountered globally. Multiple organizations such as HS2 does not have
fraud in procurement on register of risk with designated risk owner. In addition to this,
procurement fraud is not replicated as threat within project. There is often absence of formal
guidance within HS2 to mitigate and decrease risk of procurement fraud. It is associated with
lack of strategy and impossible to say that fraud could not be substituted on complete aspect but
focusing on decreasing opportunities to happen at initial place and raised likelihood of fraudsters
being caught.
Although it has been implicated that amount of risk at wide level, a business is directly
willing for accepting pursuit of value along with reflection of risk management philosophy
which influences culture of entity along with its operating style. Risk appetite guides allocation
of resource and aligns business, people and processes in infrastructure to respond and monitor
risks. It has been implicated that risk appetite is strategic and related to pursuit objectives of
organizations. This directly forms integral part of corporate governance and guides resource
allocation. Simultaneously, this guides infrastructure of business which supports activities on
basis of assessing, responding, recognising and monitoring risk with pursuit of organizational
objectives. It has been extracted that risk appetite influences HS2's attitude towards risk and in
multi-dimensional includes applied to value pursuit in long and short term strategic planning
cycle (Fraud Risk Assessment Tool, 2019). Although, there is requirement of effective
monitoring of risk and continues for risk appetite as integral part of Enterprise risk management.
Moreover, ERM is defined as overarching framework and is structure as analytical
process which concentrates on determining and substituting financial impact along with volatility
of a risk portfolio. The significance is that each risk could be offered as opportunity for gaining
competitive advantage. It has been resulted that organization with strong ERM system could
directly outperform as business with weak system. Furthermore, risk appetite is known as
exposure level that business is prepared for accept, mainly risk tolerated through company. This
has been suggested that business is required for managing risks in cases of risk occurrence could
have presence of serious consequences related to activities. The risk complexity and increment
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

has led management of organization for understanding that it is better for purpose of managing
risk to recoup loss. On basis of this requirement, different organizations proceed for
implementing risk management, developing particular strategies which have defined behaviour
of organization for risk and arrangements of management.
Integrated risk management process is set and designed through management and
implemented through entire staff within business. Simultaneously, this process is not linear risk
management might have impact on other risks along with control devices determined as being
very effective to limit risk and keeping within acceptable limits might prove as beneficial to
control other risks (Challenges in implementing enterprise risk management, 2014). The role of
enterprise risk management system is for ensuring that implementation of function of risk
management as these are activated with management system signals of organization with
existence of threat in attaining to its objectives and delivering expected outcome due to activities.
It could be observed that developing and implementing integrated risk management directly
enables management of entity to lay emphasis efforts on risks impact attainment of objectives.
On basis of implication, this risk management system shows integration of each activity and
actions on basis of risk and risk management in individual system so it could act at individual
level. This implementation of ERM within business would lead to strategic risk analysis,
reporting, operational and of compliance which might impact attainment (Enterprise Risk
management, 2018).
In this aspect, prioritization and definition as per level of risk and cost required of control
devices to substitute consequences with risk manifestation or for limiting risk, this would
constitute as threat to organization. The evaluation and identification of internal control on basis
of activities and actions attached to aims, both with context of existence and expected for exist
and establishment of zones or areas which has need to implement measures of control, so that
target set to aims to be attained within planned conditions. The design and implementation with
certain measures of internal control for purpose of improving activities. This offers conditions
for business to directly comply through different situations and established data and critical
information concerned to HS2's environment which might be used for analysis and strategy of
decision making.
Lastly, as per structure of this enterprise risk management the attainment of objectives
within presupposes of organization meeting in logical sequence of particular and required
5
risk to recoup loss. On basis of this requirement, different organizations proceed for
implementing risk management, developing particular strategies which have defined behaviour
of organization for risk and arrangements of management.
Integrated risk management process is set and designed through management and
implemented through entire staff within business. Simultaneously, this process is not linear risk
management might have impact on other risks along with control devices determined as being
very effective to limit risk and keeping within acceptable limits might prove as beneficial to
control other risks (Challenges in implementing enterprise risk management, 2014). The role of
enterprise risk management system is for ensuring that implementation of function of risk
management as these are activated with management system signals of organization with
existence of threat in attaining to its objectives and delivering expected outcome due to activities.
It could be observed that developing and implementing integrated risk management directly
enables management of entity to lay emphasis efforts on risks impact attainment of objectives.
On basis of implication, this risk management system shows integration of each activity and
actions on basis of risk and risk management in individual system so it could act at individual
level. This implementation of ERM within business would lead to strategic risk analysis,
reporting, operational and of compliance which might impact attainment (Enterprise Risk
management, 2018).
In this aspect, prioritization and definition as per level of risk and cost required of control
devices to substitute consequences with risk manifestation or for limiting risk, this would
constitute as threat to organization. The evaluation and identification of internal control on basis
of activities and actions attached to aims, both with context of existence and expected for exist
and establishment of zones or areas which has need to implement measures of control, so that
target set to aims to be attained within planned conditions. The design and implementation with
certain measures of internal control for purpose of improving activities. This offers conditions
for business to directly comply through different situations and established data and critical
information concerned to HS2's environment which might be used for analysis and strategy of
decision making.
Lastly, as per structure of this enterprise risk management the attainment of objectives
within presupposes of organization meeting in logical sequence of particular and required
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

activities by setting context, objectives, risk assessment and identification, setting risk response,
implementation of measures of control, communication and information and monitoring. While
implementation, this system involves determining and assessing risks which is threat for
accomplishing objectives (Mayer and et.al., 2018). The process of risk involves consideration of
probability of materialization of risks at some point of activities progress which might be
condition in favour of risk emergence and then impact of risk on objectives shows consequence
of risk materialization.
CONCLUSION
On basis of above report, it had been concluded that fraud risk has four faces in which
procurement fraud is huge threat. Moreover, fraud is likely outcome through combination of
multiple factors as risk management cycle in which first risk is determined, assessing scale of
risk, risk response, implementing strategy, track control and review and refine it. It has shown
that with finite resources, HS2 should be capable for deciding to assess and mitigating fraud risk.
It has articulated about targeting fraud risk management efforts with specific fraud risks which
enables significant adverse impact on attainment of objectives of organization.
6
implementation of measures of control, communication and information and monitoring. While
implementation, this system involves determining and assessing risks which is threat for
accomplishing objectives (Mayer and et.al., 2018). The process of risk involves consideration of
probability of materialization of risks at some point of activities progress which might be
condition in favour of risk emergence and then impact of risk on objectives shows consequence
of risk materialization.
CONCLUSION
On basis of above report, it had been concluded that fraud risk has four faces in which
procurement fraud is huge threat. Moreover, fraud is likely outcome through combination of
multiple factors as risk management cycle in which first risk is determined, assessing scale of
risk, risk response, implementing strategy, track control and review and refine it. It has shown
that with finite resources, HS2 should be capable for deciding to assess and mitigating fraud risk.
It has articulated about targeting fraud risk management efforts with specific fraud risks which
enables significant adverse impact on attainment of objectives of organization.
6

REFERENCES
Books and Journals
Berry‐Stölzle, T. R. and Xu, J., 2018. Enterprise risk management and the cost of
capital. Journal of Risk and Insurance. 85(1). pp.159-201.
Lechner, P. and Gatzert, N., 2018. Determinants and value of enterprise risk management:
empirical evidence from Germany. The European Journal of Finance. 24(10). pp.867-887.
Lundqvist, S. A. and Vilhelmsson, A., 2018. Enterprise Risk Management and Default Risk:
Evidence from the Banking Industry. Journal of Risk and Insurance. 85(1). pp.127-157.
Mayer, N. and et.al., 2018. An integrated conceptual model for information system security risk
management supported by enterprise architecture management. Software & Systems
Modeling. pp.1-28.
Online
Challenges in implementing enterprise risk management. 2014. [Online]. Available through
<http://www.acrn-journals.eu/resources/jfrp201403a.pdf>.
Enterprise Risk management. 2018. [Online]. Available through
<https://www.coso.org/Documents/ERM-Understanding-and-Communicating-Risk-
Appetite.pdf>.
Fraud Risk Assessment Tool. 2019. [Online]. Available through
<https://www.acfe.com/frat.aspx?id=6797>.
The seven global procurement fraud challenges. 2019. [Online]. Available through
<https://www.cips.org/en-SG/supply-management/opinion/2013/november/the-seven-
global-procurement-fraud-challenges/>.
7
Books and Journals
Berry‐Stölzle, T. R. and Xu, J., 2018. Enterprise risk management and the cost of
capital. Journal of Risk and Insurance. 85(1). pp.159-201.
Lechner, P. and Gatzert, N., 2018. Determinants and value of enterprise risk management:
empirical evidence from Germany. The European Journal of Finance. 24(10). pp.867-887.
Lundqvist, S. A. and Vilhelmsson, A., 2018. Enterprise Risk Management and Default Risk:
Evidence from the Banking Industry. Journal of Risk and Insurance. 85(1). pp.127-157.
Mayer, N. and et.al., 2018. An integrated conceptual model for information system security risk
management supported by enterprise architecture management. Software & Systems
Modeling. pp.1-28.
Online
Challenges in implementing enterprise risk management. 2014. [Online]. Available through
<http://www.acrn-journals.eu/resources/jfrp201403a.pdf>.
Enterprise Risk management. 2018. [Online]. Available through
<https://www.coso.org/Documents/ERM-Understanding-and-Communicating-Risk-
Appetite.pdf>.
Fraud Risk Assessment Tool. 2019. [Online]. Available through
<https://www.acfe.com/frat.aspx?id=6797>.
The seven global procurement fraud challenges. 2019. [Online]. Available through
<https://www.cips.org/en-SG/supply-management/opinion/2013/november/the-seven-
global-procurement-fraud-challenges/>.
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.