Comprehensive Security Analysis of HSBC Mobile Banking Application
VerifiedAdded on 2023/03/23
|14
|2888
|71
Report
AI Summary
This report provides a detailed security analysis of mobile banking applications, using the HSBC mobile banking app as a case study. It begins with an introduction to mobile applications, emphasizing their vulnerabilities and threats, particularly within the banking sector. The report then outlines the detailed working procedures of mobile banking, highlighting the interconnected concepts of mobile accounting, brokerage, and financial information services. It identifies critical assets at risk, including data and financial constraints, and discusses various threats such as weak server-side controls, data transport layer vulnerabilities, and client-side interventions. The report further details the controls implemented by HSBC, including authenticity, confidentiality, and logging controls. Security objectives are outlined, such as maintaining application security, PIN auto-generation, and user training. The report also explores risk evolution across devices, networks, and data centers, detailing specific threats like phishing, man-in-the-middle attacks, and DNS poisoning. Testing with the HSBC mobile banking application is demonstrated through screenshots of security authentication procedures and transaction verification. Finally, the report concludes by summarizing the key findings and emphasizing the importance of robust security measures in mobile banking.

Running head: SECURE USAGE OF MOBILE APPLICATION
Secure Usage of Mobile Application
Name of the student:
Name of the university:
Author Note:
Secure Usage of Mobile Application
Name of the student:
Name of the university:
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SECURE USAGE OF MOBILE APPLICATION
Table of Contents
1. Introduction............................................................................................................................2
2. Detailed working procedure...................................................................................................2
3. Assets at Risk.........................................................................................................................3
4. Threats....................................................................................................................................4
5. Controls..................................................................................................................................5
6. Security Objectives................................................................................................................6
7. Risk Evolution........................................................................................................................6
7.1 Risks with the device.......................................................................................................7
7.2 Risk with the network......................................................................................................8
7.3 Risk with the data centre..................................................................................................8
8. Testing with HSBC mobile banking application...................................................................8
9. Conclusion............................................................................................................................11
10. References..........................................................................................................................12
Table of Contents
1. Introduction............................................................................................................................2
2. Detailed working procedure...................................................................................................2
3. Assets at Risk.........................................................................................................................3
4. Threats....................................................................................................................................4
5. Controls..................................................................................................................................5
6. Security Objectives................................................................................................................6
7. Risk Evolution........................................................................................................................6
7.1 Risks with the device.......................................................................................................7
7.2 Risk with the network......................................................................................................8
7.3 Risk with the data centre..................................................................................................8
8. Testing with HSBC mobile banking application...................................................................8
9. Conclusion............................................................................................................................11
10. References..........................................................................................................................12

2SECURE USAGE OF MOBILE APPLICATION
1. Introduction
The report encompasses the technology of mobile application that is presently used by
the mobile developers for providing the enhanced interface for the usage of mobile devices.
This application is said to be a computer programs that are structured to run on the platforms
of mobile phone or tablet. The mobile application firstly intended to assist the user by
providing services like email, contact databases, calendars and many more. However, with
the growing trends in the need of the mobile applications led this industry to highly develop
user-defined software as well as this also incorporates certain vulnerabilities as well as threats
towards its users (Bhatnagar, Malik and Butakov, 2018). This report deals with the various
constraints regarding the security of the mobile application usage in a particular domain that
is banking applications and the potential mobile application of the HSBC mobile banking is
taken as an example for the testing purpose..
2. Detailed working procedure
This report deals with the security assessment analysis of the mobile baking
applications that are used by many users all around the world. The financial institutions
provide this banking service, which helps the customers to carry out the financial transaction
in an easy way as well as with the help of the remotely effective devices such as mobile
phones or tablets (Marforio et al., 2016). The detailed concept of the mobile banking
software may be depicted by the three concepts, which are meant to be interconnected with
each other. These are stated as accounting of mobile, brokerage of mobile and financial
information services with the implication of mobile. Most of the services regarding the
mobile banking are transaction based which requires a potential level of security for carrying
out the transactions. This mobile application accesses the server of the bank where each of
the data regarding the customers are critically saved. The account information regarding the
1. Introduction
The report encompasses the technology of mobile application that is presently used by
the mobile developers for providing the enhanced interface for the usage of mobile devices.
This application is said to be a computer programs that are structured to run on the platforms
of mobile phone or tablet. The mobile application firstly intended to assist the user by
providing services like email, contact databases, calendars and many more. However, with
the growing trends in the need of the mobile applications led this industry to highly develop
user-defined software as well as this also incorporates certain vulnerabilities as well as threats
towards its users (Bhatnagar, Malik and Butakov, 2018). This report deals with the various
constraints regarding the security of the mobile application usage in a particular domain that
is banking applications and the potential mobile application of the HSBC mobile banking is
taken as an example for the testing purpose..
2. Detailed working procedure
This report deals with the security assessment analysis of the mobile baking
applications that are used by many users all around the world. The financial institutions
provide this banking service, which helps the customers to carry out the financial transaction
in an easy way as well as with the help of the remotely effective devices such as mobile
phones or tablets (Marforio et al., 2016). The detailed concept of the mobile banking
software may be depicted by the three concepts, which are meant to be interconnected with
each other. These are stated as accounting of mobile, brokerage of mobile and financial
information services with the implication of mobile. Most of the services regarding the
mobile banking are transaction based which requires a potential level of security for carrying
out the transactions. This mobile application accesses the server of the bank where each of
the data regarding the customers are critically saved. The account information regarding the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3SECURE USAGE OF MOBILE APPLICATION
customers as well as the account transactions are stated to be the active procedures within the
environment of banking facilities. These services also keeps a track of the investments that
are carried out by the customers within the environment of banks applications (He, Tian and
Shen, 2015). These transactions are carried out by secure payment gateways that are
embedded within the mobile application systems. The secure payment gateway provides an
access to the server networks of the bank thus adhering the various constraints of the
customers present in the bank.
3. Assets at Risk
The different assets that are subjected to risks within the environment of the banking
facilities that are offered by the mobile banking applications are stated as follows:
Data: This is stated as the most important asset regarding a mobile banking software, which
is used by each of the banking sectors to communicate or maintain a relationship of the
organization with the banks (Shahriar, Klintic and Clincy, 2015). The importance of this
asset is that it possess all the important requirements regarding the customers, which are very
important and should be restricted from the unknown users that are trying to access the data
of the customers.
Financial constraints: As customer always seeks to keep financial transactions with the
banking service providers the usage of the financial constraints are mainly focused by both
the servers as well as the customers (Yıldırım and Varol, 2015). The card as well as the loan
facilities availed by the customers within the mobile banking application is set to an asset that
might be at risk with the vulnerabilities, which might occur within the mobile banking
environment.
Other constraints: The mobile banking application that are used by the customers to
remotely access their bank services as well as to carry out the financial transactions.
customers as well as the account transactions are stated to be the active procedures within the
environment of banking facilities. These services also keeps a track of the investments that
are carried out by the customers within the environment of banks applications (He, Tian and
Shen, 2015). These transactions are carried out by secure payment gateways that are
embedded within the mobile application systems. The secure payment gateway provides an
access to the server networks of the bank thus adhering the various constraints of the
customers present in the bank.
3. Assets at Risk
The different assets that are subjected to risks within the environment of the banking
facilities that are offered by the mobile banking applications are stated as follows:
Data: This is stated as the most important asset regarding a mobile banking software, which
is used by each of the banking sectors to communicate or maintain a relationship of the
organization with the banks (Shahriar, Klintic and Clincy, 2015). The importance of this
asset is that it possess all the important requirements regarding the customers, which are very
important and should be restricted from the unknown users that are trying to access the data
of the customers.
Financial constraints: As customer always seeks to keep financial transactions with the
banking service providers the usage of the financial constraints are mainly focused by both
the servers as well as the customers (Yıldırım and Varol, 2015). The card as well as the loan
facilities availed by the customers within the mobile banking application is set to an asset that
might be at risk with the vulnerabilities, which might occur within the mobile banking
environment.
Other constraints: The mobile banking application that are used by the customers to
remotely access their bank services as well as to carry out the financial transactions.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4SECURE USAGE OF MOBILE APPLICATION
Moreover, the banking application also accesses the present data within the device making it
accessible to the untrusted data hackers.
4. Threats
There are many potential threats that are associated while carrying out the transactions
through a mobile banking software. These are stated as follows:
Controls of weak server sides: The communication of the data assets within the server of the
banks as well as the customer data present in the remote mobile phones are totally controlled
by the server side security checks (Aljawarneh, 2016). If the server side protection is not
adhered in a real time basis then the data protection is hampered regarding the data or
information present in the server environment as well as the device or application that are
associated with the transaction. The security feature is too much dependant on the remote
device OS security for the security updates and the data responsibilities associated with the
remote devices.
Protection of data transport layer: The transport layer is through which the information is
being transferred within the client server environment (Mullan, Bradley and Loane, 2017).
For the security of the data within the transport layer, SSL as well as TLS are used for the
encryption of data. Moreover, the SSL chain verification is necessary for the data
transportation.
Authorization and authentication: The poor authentication as well as authorization
techniques of the data within the mobile data environment needs to be anonymously operated
through the backend server within the application of the remote mobile devices (Sundaram,
Thomas and Agilandeeswari, 2019)
. The internet connections are not reliable for the usage of the transaction facility by the
mobile devices. The security logins are based on the offline mode that makes the
Moreover, the banking application also accesses the present data within the device making it
accessible to the untrusted data hackers.
4. Threats
There are many potential threats that are associated while carrying out the transactions
through a mobile banking software. These are stated as follows:
Controls of weak server sides: The communication of the data assets within the server of the
banks as well as the customer data present in the remote mobile phones are totally controlled
by the server side security checks (Aljawarneh, 2016). If the server side protection is not
adhered in a real time basis then the data protection is hampered regarding the data or
information present in the server environment as well as the device or application that are
associated with the transaction. The security feature is too much dependant on the remote
device OS security for the security updates and the data responsibilities associated with the
remote devices.
Protection of data transport layer: The transport layer is through which the information is
being transferred within the client server environment (Mullan, Bradley and Loane, 2017).
For the security of the data within the transport layer, SSL as well as TLS are used for the
encryption of data. Moreover, the SSL chain verification is necessary for the data
transportation.
Authorization and authentication: The poor authentication as well as authorization
techniques of the data within the mobile data environment needs to be anonymously operated
through the backend server within the application of the remote mobile devices (Sundaram,
Thomas and Agilandeeswari, 2019)
. The internet connections are not reliable for the usage of the transaction facility by the
mobile devices. The security logins are based on the offline mode that makes the

5SECURE USAGE OF MOBILE APPLICATION
authentication more vulnerable regarding the banking system environment within the mobile
application.
Client Side Interventions: This is expected to be the injections of the malicious softwares
that intervenes the mobile application present within the mobile device of the users. This
approach may put an adverse effect regarding the potential damage of the data present within
the network environment of the server as well as the mobile devices (Zheng, Pan and Yilmaz,
2017). The poor framework of the data present within the remote device can make the data to
be exposed for the attackers thus leading potential threats.
5. Controls
The controls that are identified in the overall application of the mobile banking
facility of HSBC are provided as follows:
Controls of Authenticity: The devices in which the customer is using the mobile banking
application must be provided with the authenticity verification controls regarding the user of
the mobile banking application (Bojjagani and Sastry, 2016).
Controls of confidentiality: As the application will be comprising of many user data and
important information the application must be designed with such facilities that the
confidentiality of the users cannot be intervened by the non-trusted sources (Nosrati and
Bidgoli, 2015).
Controls of logging in: The logging credentials provided by the mobile banking application
provides many type of verification methods of the user data, the most significant being the
face ID, which is depicted as the most unique login credential of the user by the mobile
banking application (Seo and Park, 2018)
.
authentication more vulnerable regarding the banking system environment within the mobile
application.
Client Side Interventions: This is expected to be the injections of the malicious softwares
that intervenes the mobile application present within the mobile device of the users. This
approach may put an adverse effect regarding the potential damage of the data present within
the network environment of the server as well as the mobile devices (Zheng, Pan and Yilmaz,
2017). The poor framework of the data present within the remote device can make the data to
be exposed for the attackers thus leading potential threats.
5. Controls
The controls that are identified in the overall application of the mobile banking
facility of HSBC are provided as follows:
Controls of Authenticity: The devices in which the customer is using the mobile banking
application must be provided with the authenticity verification controls regarding the user of
the mobile banking application (Bojjagani and Sastry, 2016).
Controls of confidentiality: As the application will be comprising of many user data and
important information the application must be designed with such facilities that the
confidentiality of the users cannot be intervened by the non-trusted sources (Nosrati and
Bidgoli, 2015).
Controls of logging in: The logging credentials provided by the mobile banking application
provides many type of verification methods of the user data, the most significant being the
face ID, which is depicted as the most unique login credential of the user by the mobile
banking application (Seo and Park, 2018)
.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6SECURE USAGE OF MOBILE APPLICATION
6. Security Objectives
The security objectives regarding the usage of the HSBC mobile banking application
can be depicted as follows:
Maintenance of the application: The timely updates regarding the security features of the
mobile banking softwares must be provided to the users device for maintaining the
application and thus restricting it from the attackers.
The PIN auto generation: The unique PIN that is provided each time to a user for carrying
out the monetary transactions should be thoroughly verified by the server end so that any
vulnerability does not affects the transaction procedure (Kouraogo, Zkik and Orhanou, 2016).
Moreover, if this PIN generation methodology is also substituted by the fingerprint and face
ID verification methods then it can be well explained that the security feature may be
enhanced.
Training regarding the usage of the application: The proper using methods of the
application may be clearly stated by the mobile application of HSBC via notifications
(Malaquias and Hwang, 2016). The demo modules should also be clearly stated to the users
using the application do not face any difficulty as well as the proper security measures must
also be stated that will lower down the vulnerability of the user data (Seo and Park, 2018)
.
7. Risk Evolution
The risks that are identified while using the mobile banking application of the HSBC
bank are stated in the following section. The Surface of Attack may be broadly divided into 3
sections that are identified as the device, the network and the data centre.
6. Security Objectives
The security objectives regarding the usage of the HSBC mobile banking application
can be depicted as follows:
Maintenance of the application: The timely updates regarding the security features of the
mobile banking softwares must be provided to the users device for maintaining the
application and thus restricting it from the attackers.
The PIN auto generation: The unique PIN that is provided each time to a user for carrying
out the monetary transactions should be thoroughly verified by the server end so that any
vulnerability does not affects the transaction procedure (Kouraogo, Zkik and Orhanou, 2016).
Moreover, if this PIN generation methodology is also substituted by the fingerprint and face
ID verification methods then it can be well explained that the security feature may be
enhanced.
Training regarding the usage of the application: The proper using methods of the
application may be clearly stated by the mobile application of HSBC via notifications
(Malaquias and Hwang, 2016). The demo modules should also be clearly stated to the users
using the application do not face any difficulty as well as the proper security measures must
also be stated that will lower down the vulnerability of the user data (Seo and Park, 2018)
.
7. Risk Evolution
The risks that are identified while using the mobile banking application of the HSBC
bank are stated in the following section. The Surface of Attack may be broadly divided into 3
sections that are identified as the device, the network and the data centre.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7SECURE USAGE OF MOBILE APPLICATION
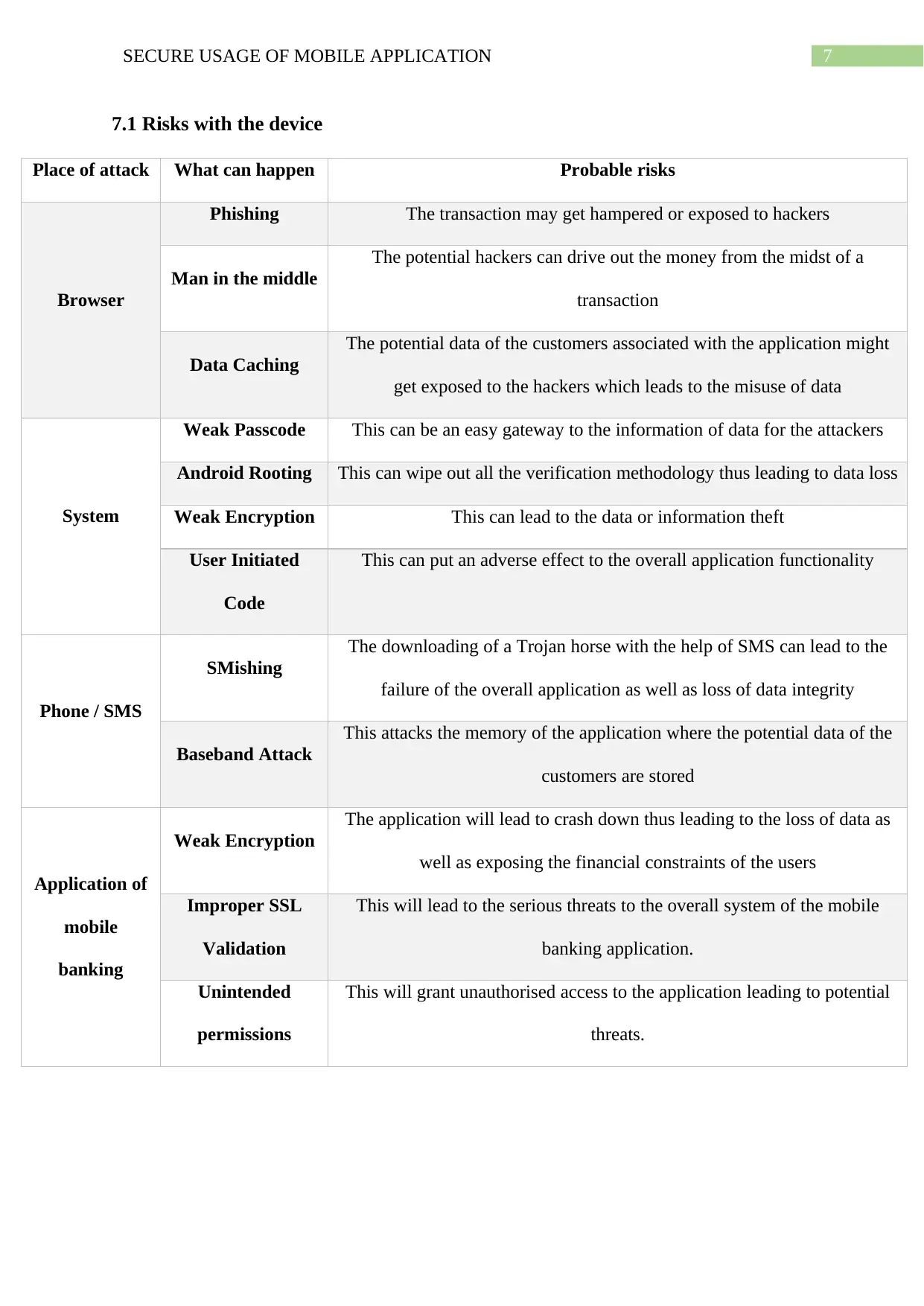
7.1 Risks with the device
Place of attack What can happen Probable risks
Browser
Phishing The transaction may get hampered or exposed to hackers
Man in the middle
The potential hackers can drive out the money from the midst of a
transaction
Data Caching
The potential data of the customers associated with the application might
get exposed to the hackers which leads to the misuse of data
System
Weak Passcode This can be an easy gateway to the information of data for the attackers
Android Rooting This can wipe out all the verification methodology thus leading to data loss
Weak Encryption This can lead to the data or information theft
User Initiated
Code
This can put an adverse effect to the overall application functionality
Phone / SMS
SMishing
The downloading of a Trojan horse with the help of SMS can lead to the
failure of the overall application as well as loss of data integrity
Baseband Attack
This attacks the memory of the application where the potential data of the
customers are stored
Application of
mobile
banking
Weak Encryption
The application will lead to crash down thus leading to the loss of data as
well as exposing the financial constraints of the users
Improper SSL
Validation
This will lead to the serious threats to the overall system of the mobile
banking application.
Unintended
permissions
This will grant unauthorised access to the application leading to potential
threats.
7.1 Risks with the device
Place of attack What can happen Probable risks
Browser
Phishing The transaction may get hampered or exposed to hackers
Man in the middle
The potential hackers can drive out the money from the midst of a
transaction
Data Caching
The potential data of the customers associated with the application might
get exposed to the hackers which leads to the misuse of data
System
Weak Passcode This can be an easy gateway to the information of data for the attackers
Android Rooting This can wipe out all the verification methodology thus leading to data loss
Weak Encryption This can lead to the data or information theft
User Initiated
Code
This can put an adverse effect to the overall application functionality
Phone / SMS
SMishing
The downloading of a Trojan horse with the help of SMS can lead to the
failure of the overall application as well as loss of data integrity
Baseband Attack
This attacks the memory of the application where the potential data of the
customers are stored
Application of
mobile
banking
Weak Encryption
The application will lead to crash down thus leading to the loss of data as
well as exposing the financial constraints of the users
Improper SSL
Validation
This will lead to the serious threats to the overall system of the mobile
banking application.
Unintended
permissions
This will grant unauthorised access to the application leading to potential
threats.

8SECURE USAGE OF MOBILE APPLICATION
7.2 Risk with the network
The probable risks associated with the network may be depicted as follows:
Wi-Fi
The encryption of the Wi-Fi module may lead the attackers to
easily hack the data and financial constraints associated with the
application
Session Hacking
This occurs at the time of transaction when the same is carried
out via the application.
DNS Poisoning
This can attack the server side of the application via the mobile
application making all possible data exposed to threats
7.3 Risk with the data centre
This adheres two possible risks areas that are likely to be the Web Server and
Database. The possible risks associated with the webserver are server misconfiguration, brute
forces attack as well as weak input validation (He, Chan and Guizani, 2015). While the
database side risks are identified as SQL injection and OS Command Execution.
8. Testing with HSBC mobile banking application
The below figure depicts the three type of security authentication procedures as
provided by the HSBC mobile banking application.
7.2 Risk with the network
The probable risks associated with the network may be depicted as follows:
Wi-Fi
The encryption of the Wi-Fi module may lead the attackers to
easily hack the data and financial constraints associated with the
application
Session Hacking
This occurs at the time of transaction when the same is carried
out via the application.
DNS Poisoning
This can attack the server side of the application via the mobile
application making all possible data exposed to threats
7.3 Risk with the data centre
This adheres two possible risks areas that are likely to be the Web Server and
Database. The possible risks associated with the webserver are server misconfiguration, brute
forces attack as well as weak input validation (He, Chan and Guizani, 2015). While the
database side risks are identified as SQL injection and OS Command Execution.
8. Testing with HSBC mobile banking application
The below figure depicts the three type of security authentication procedures as
provided by the HSBC mobile banking application.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
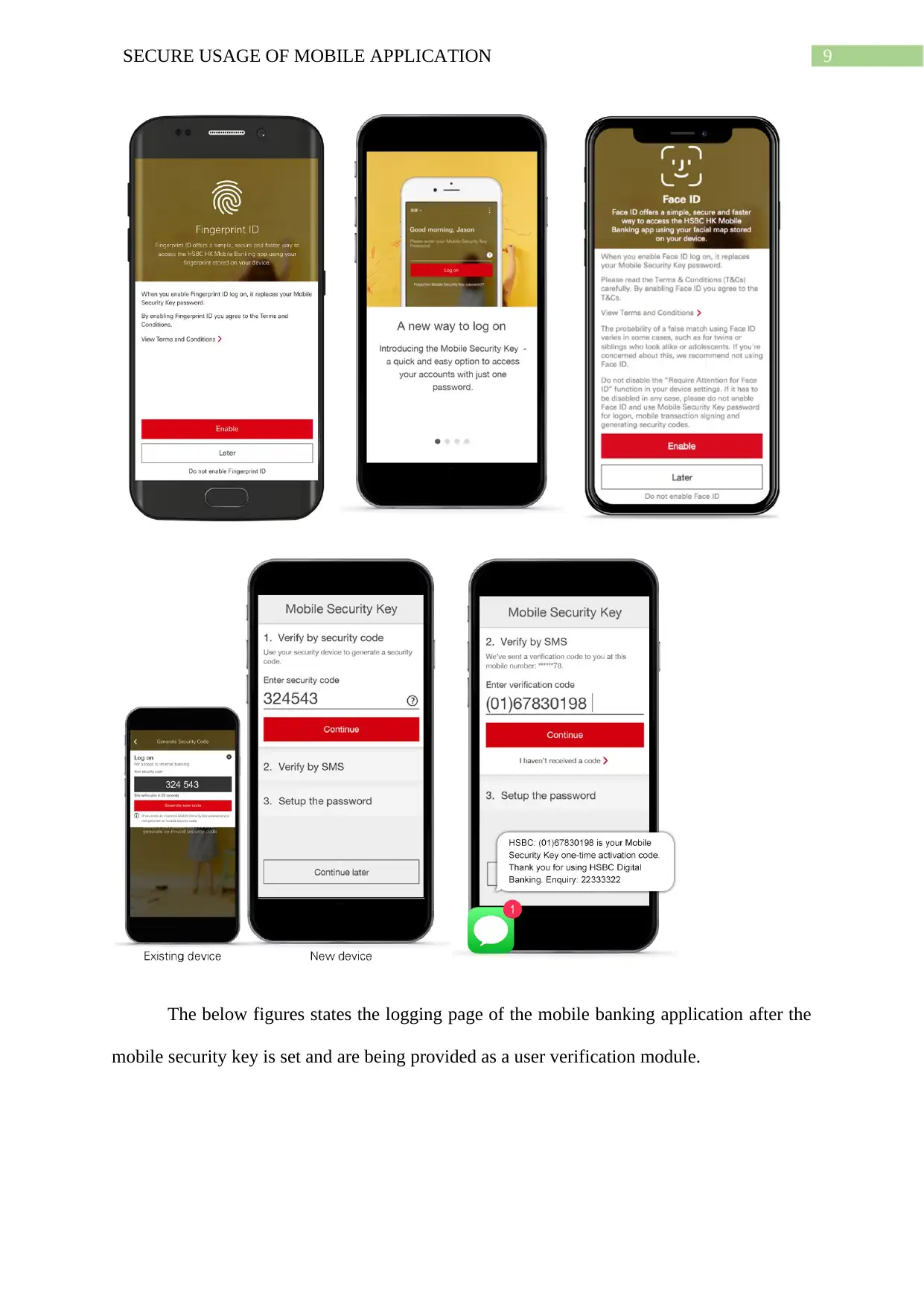
9SECURE USAGE OF MOBILE APPLICATION
The below figures states the logging page of the mobile banking application after the
mobile security key is set and are being provided as a user verification module.
The below figures states the logging page of the mobile banking application after the
mobile security key is set and are being provided as a user verification module.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10SECURE USAGE OF MOBILE APPLICATION
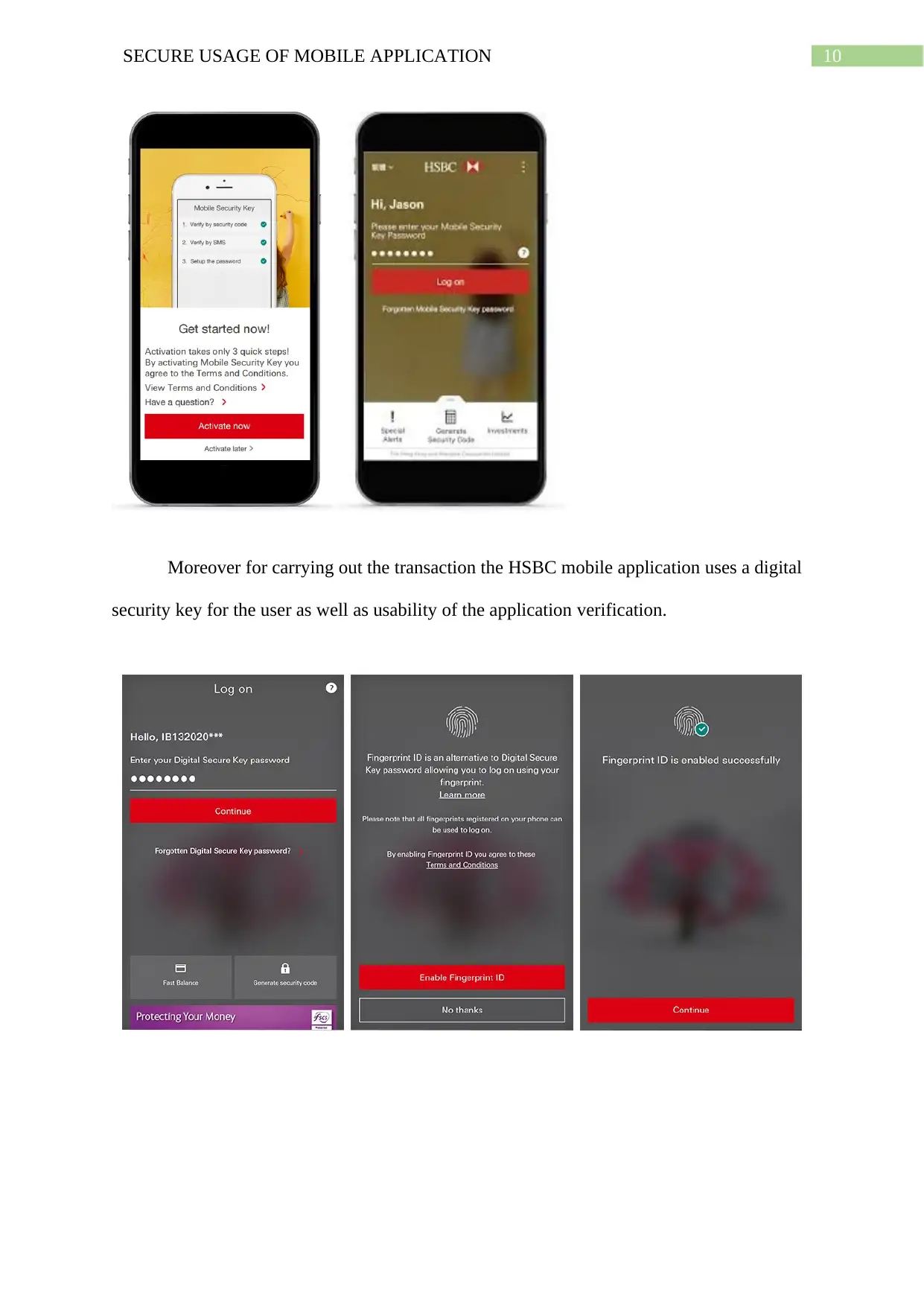
Moreover for carrying out the transaction the HSBC mobile application uses a digital
security key for the user as well as usability of the application verification.
Moreover for carrying out the transaction the HSBC mobile application uses a digital
security key for the user as well as usability of the application verification.

11SECURE USAGE OF MOBILE APPLICATION
9. Conclusion
Thus from the above report it can be depicted that the mobile application software is
an effective software provided by banks for carrying out transactions. However it possesses
some threats, as well as risks associated with it, which must be analysed by the software
development team, and necessary steps should be adhered for the mitigation of these risks.
Thus, it can be concluded that the mobile banking software of HSBC has enhanced features
such as finger print verification as well as face ID verification that distinguishes the features
of authenticity from other mobile banking application present in the market globally.
9. Conclusion
Thus from the above report it can be depicted that the mobile application software is
an effective software provided by banks for carrying out transactions. However it possesses
some threats, as well as risks associated with it, which must be analysed by the software
development team, and necessary steps should be adhered for the mitigation of these risks.
Thus, it can be concluded that the mobile banking software of HSBC has enhanced features
such as finger print verification as well as face ID verification that distinguishes the features
of authenticity from other mobile banking application present in the market globally.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




