Comprehensive System Design for Human Resource Management System
VerifiedAdded on 2023/05/28
|10
|2192
|225
Report
AI Summary
This document provides a comprehensive system design for a Human Resource Management (HRM) system, focusing on key components, user interface design, security concerns, and deployment strategies. It begins by outlining the system's architecture, utilizing a Platform as a Service (PaaS) cloud model and a hybrid cloud infrastructure for enhanced flexibility and cost-effectiveness. The report emphasizes the importance of a well-designed user interface, balancing form and function for optimal user experience. A significant portion is dedicated to identifying and mitigating potential security threats, including malware, network attacks, and data breaches, through advanced technical controls and encryption. Finally, the document details a management approach for implementation, testing, and deployment, utilizing PMBoK for implementation, a detailed test plan for testing, and a phased approach for deployment, ensuring a smooth and secure transition.

[Type the company name]
Human Resource Management System
System Design
12/7/2018
Human Resource Management System
System Design
12/7/2018
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Human Resource Management System
Table of Contents
System Components..............................................................................................................................2
Platform as a Service (PaaS) Cloud...................................................................................................2
Hybrid Cloud Infrastructure..............................................................................................................2
User interface........................................................................................................................................3
Security Concerns and Approach to Mitigate the Concerns...................................................................5
Management Approach..........................................................................................................................7
References.............................................................................................................................................9
Table of Contents
System Components..............................................................................................................................2
Platform as a Service (PaaS) Cloud...................................................................................................2
Hybrid Cloud Infrastructure..............................................................................................................2
User interface........................................................................................................................................3
Security Concerns and Approach to Mitigate the Concerns...................................................................5
Management Approach..........................................................................................................................7
References.............................................................................................................................................9

Human Resource Management System
System Components
Platform as a Service (PaaS) Cloud
The architecture diagram for the system deployment is as shown in the figure below. The
cloud model that will be used for the purpose of deployment will be Platform as a Service
(PaaS) model. In this case, the cloud provider will host the hardware and software needed for
the human resource management system. The model will provide the employees of
Globoforce and other system users with the ease of usage of the system along with the
simplicity of the operations. The pay per use model will be followed and the organization will
be charged only for the services that it will use (Pahl, 2015). This will ensure that the cost-
effectiveness of the processes is always maintained. The security of the data sets and the
processes will also be maintained by the cloud model.
PaaS Cloud
System Components
Platform as a Service (PaaS) Cloud
The architecture diagram for the system deployment is as shown in the figure below. The
cloud model that will be used for the purpose of deployment will be Platform as a Service
(PaaS) model. In this case, the cloud provider will host the hardware and software needed for
the human resource management system. The model will provide the employees of
Globoforce and other system users with the ease of usage of the system along with the
simplicity of the operations. The pay per use model will be followed and the organization will
be charged only for the services that it will use (Pahl, 2015). This will ensure that the cost-
effectiveness of the processes is always maintained. The security of the data sets and the
processes will also be maintained by the cloud model.
PaaS Cloud
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Human Resource Management System
Hybrid Cloud Infrastructure
Hybrid Cloud Model
The cloud delivery model that will be used for the human resource management system for
Globoforce will be Hybrid cloud. It is the cloud model that is a mix of on-premises and third-
party cloud models. There will be enhanced system flexibility and data deployment options
provided to the organization with the aid of this model. Private clouds are not really scalable
and provide with a limited flexibility. However, public clouds are flexible and scalable. The
balance between the two will be maintained by the hybrid cloud model. It will also provide
balance to the users on the basis of their requirements and will prove to be cost-effective in
nature. Security is one of the major properties that are associated with the private cloud;
however, it is the weakness of the public cloud models (Linthicum, 2016). The overall system
security will be balanced out with the inclusion of hybrid cloud as the delivery model for the
system.
User interface
User interface designing is a critical part of the overall system development project because it
caters to the actual user’s side of experience. A bad user interface would result in a bad user
experience thereby ultimately hampering the overall prowess of the system. A system may be
negatively seen if it has a bad user interface. User interface is often a complex piece of the
puzzle because sometimes the focus is given more towards beautifying the designs i.e.,
catering to the ‘form’ of the system. Whereas on the other hand, if developers cater to the
‘functions’ of the system, again the message is lost because, now the system may be too
complicated or cluttered for the end-user. Therefore, it is important to strive a balance
Hybrid Cloud Infrastructure
Hybrid Cloud Model
The cloud delivery model that will be used for the human resource management system for
Globoforce will be Hybrid cloud. It is the cloud model that is a mix of on-premises and third-
party cloud models. There will be enhanced system flexibility and data deployment options
provided to the organization with the aid of this model. Private clouds are not really scalable
and provide with a limited flexibility. However, public clouds are flexible and scalable. The
balance between the two will be maintained by the hybrid cloud model. It will also provide
balance to the users on the basis of their requirements and will prove to be cost-effective in
nature. Security is one of the major properties that are associated with the private cloud;
however, it is the weakness of the public cloud models (Linthicum, 2016). The overall system
security will be balanced out with the inclusion of hybrid cloud as the delivery model for the
system.
User interface
User interface designing is a critical part of the overall system development project because it
caters to the actual user’s side of experience. A bad user interface would result in a bad user
experience thereby ultimately hampering the overall prowess of the system. A system may be
negatively seen if it has a bad user interface. User interface is often a complex piece of the
puzzle because sometimes the focus is given more towards beautifying the designs i.e.,
catering to the ‘form’ of the system. Whereas on the other hand, if developers cater to the
‘functions’ of the system, again the message is lost because, now the system may be too
complicated or cluttered for the end-user. Therefore, it is important to strive a balance
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
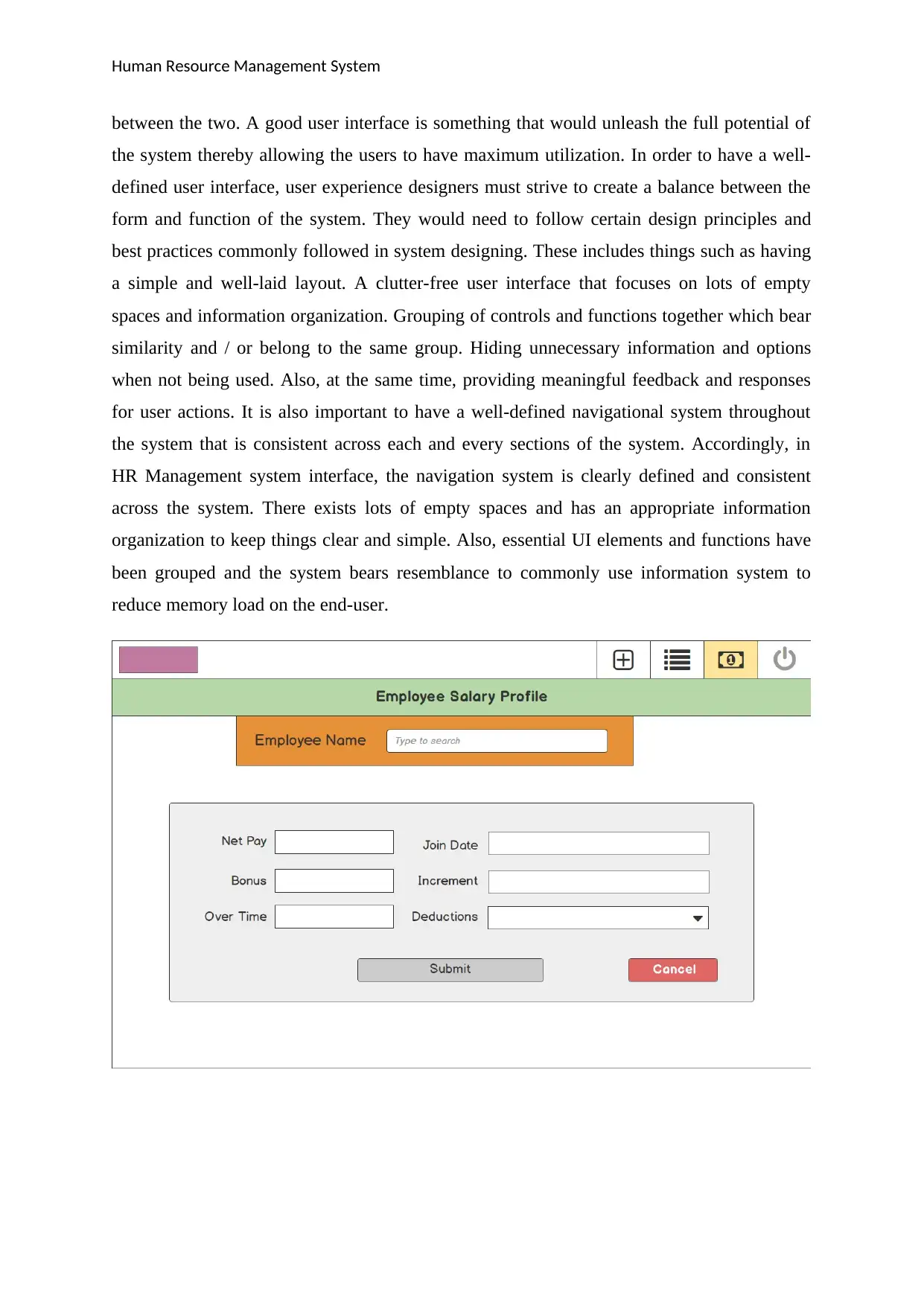
Human Resource Management System
between the two. A good user interface is something that would unleash the full potential of
the system thereby allowing the users to have maximum utilization. In order to have a well-
defined user interface, user experience designers must strive to create a balance between the
form and function of the system. They would need to follow certain design principles and
best practices commonly followed in system designing. These includes things such as having
a simple and well-laid layout. A clutter-free user interface that focuses on lots of empty
spaces and information organization. Grouping of controls and functions together which bear
similarity and / or belong to the same group. Hiding unnecessary information and options
when not being used. Also, at the same time, providing meaningful feedback and responses
for user actions. It is also important to have a well-defined navigational system throughout
the system that is consistent across each and every sections of the system. Accordingly, in
HR Management system interface, the navigation system is clearly defined and consistent
across the system. There exists lots of empty spaces and has an appropriate information
organization to keep things clear and simple. Also, essential UI elements and functions have
been grouped and the system bears resemblance to commonly use information system to
reduce memory load on the end-user.
between the two. A good user interface is something that would unleash the full potential of
the system thereby allowing the users to have maximum utilization. In order to have a well-
defined user interface, user experience designers must strive to create a balance between the
form and function of the system. They would need to follow certain design principles and
best practices commonly followed in system designing. These includes things such as having
a simple and well-laid layout. A clutter-free user interface that focuses on lots of empty
spaces and information organization. Grouping of controls and functions together which bear
similarity and / or belong to the same group. Hiding unnecessary information and options
when not being used. Also, at the same time, providing meaningful feedback and responses
for user actions. It is also important to have a well-defined navigational system throughout
the system that is consistent across each and every sections of the system. Accordingly, in
HR Management system interface, the navigation system is clearly defined and consistent
across the system. There exists lots of empty spaces and has an appropriate information
organization to keep things clear and simple. Also, essential UI elements and functions have
been grouped and the system bears resemblance to commonly use information system to
reduce memory load on the end-user.
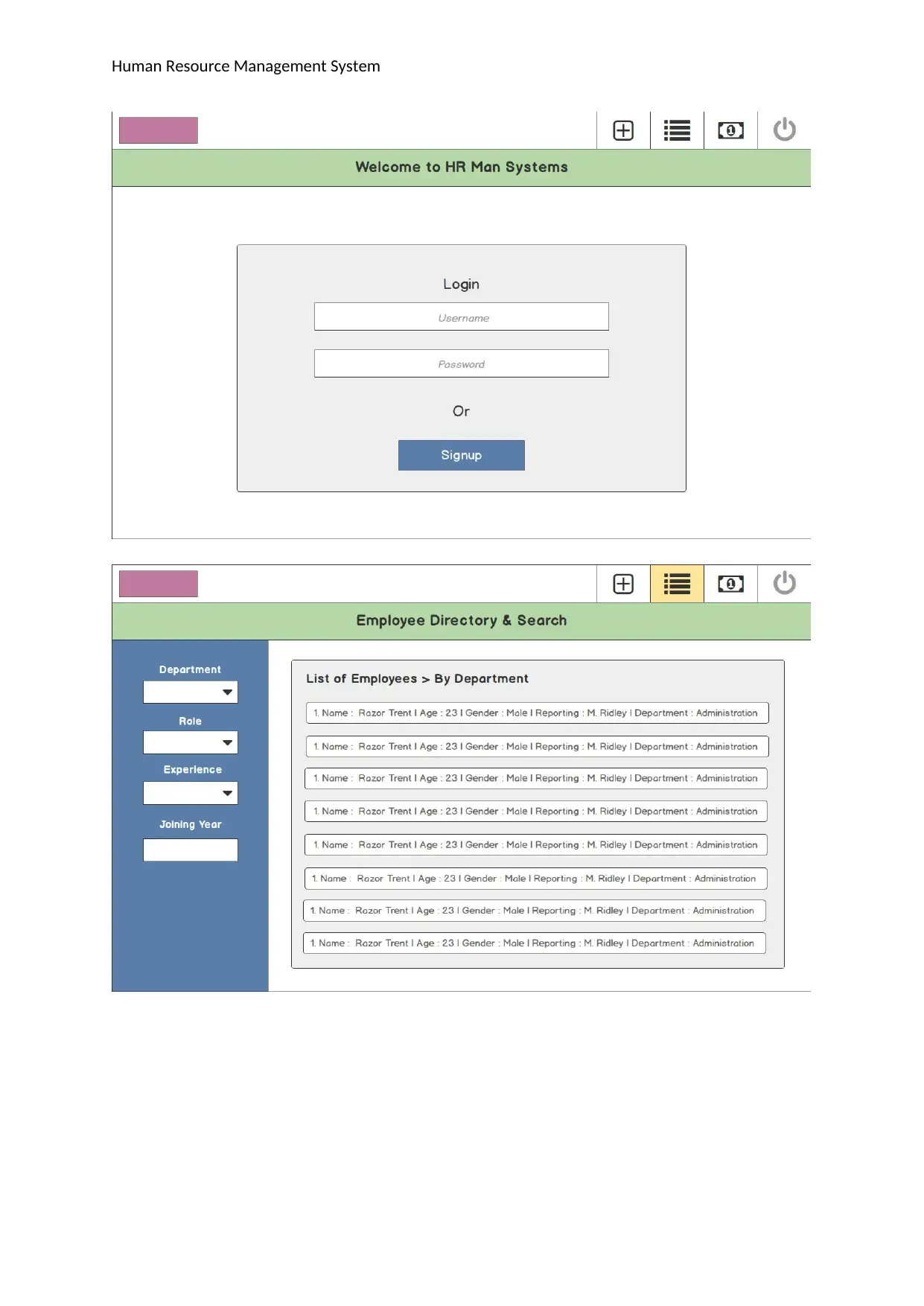
Human Resource Management System
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
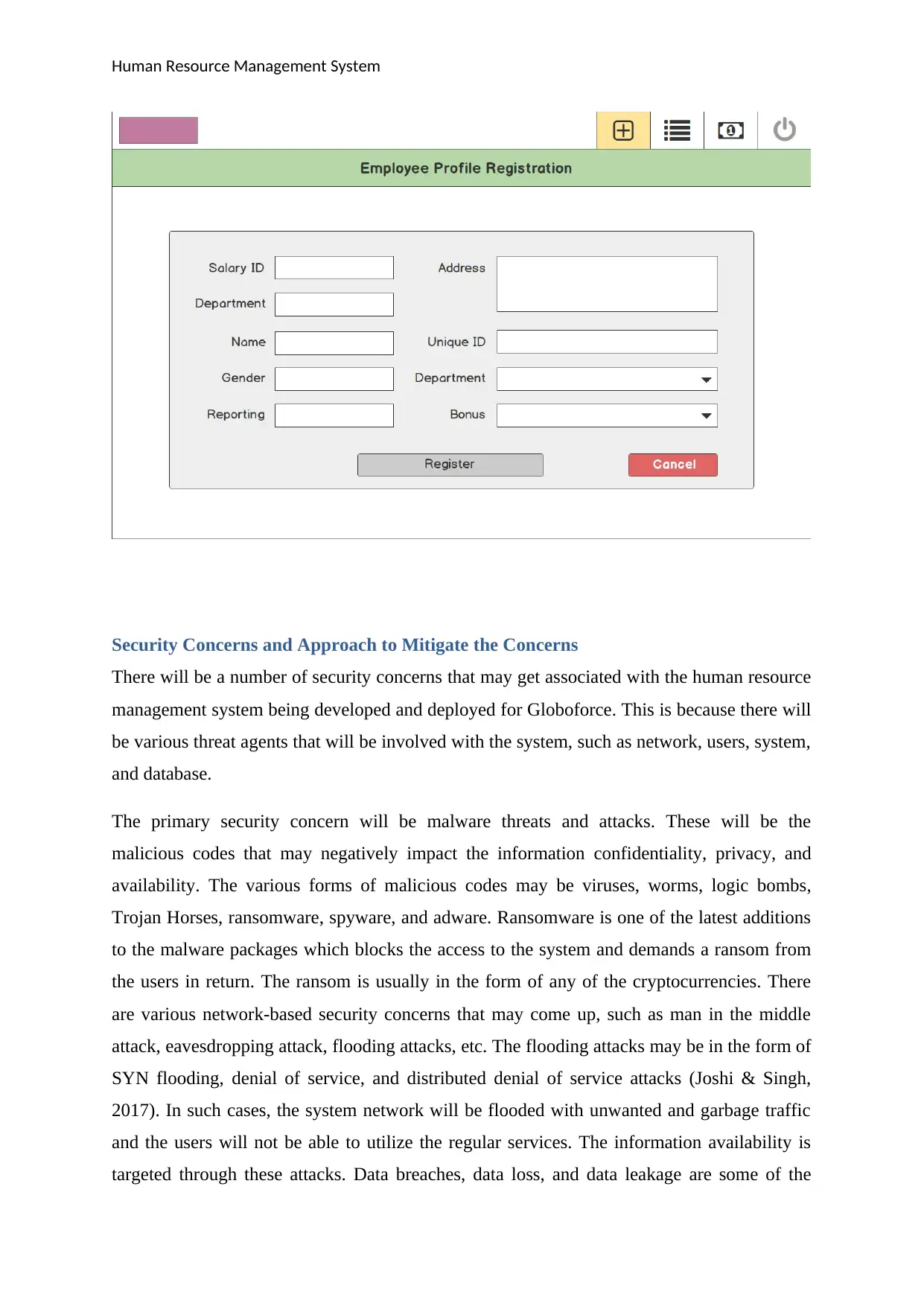
Human Resource Management System
Security Concerns and Approach to Mitigate the Concerns
There will be a number of security concerns that may get associated with the human resource
management system being developed and deployed for Globoforce. This is because there will
be various threat agents that will be involved with the system, such as network, users, system,
and database.
The primary security concern will be malware threats and attacks. These will be the
malicious codes that may negatively impact the information confidentiality, privacy, and
availability. The various forms of malicious codes may be viruses, worms, logic bombs,
Trojan Horses, ransomware, spyware, and adware. Ransomware is one of the latest additions
to the malware packages which blocks the access to the system and demands a ransom from
the users in return. The ransom is usually in the form of any of the cryptocurrencies. There
are various network-based security concerns that may come up, such as man in the middle
attack, eavesdropping attack, flooding attacks, etc. The flooding attacks may be in the form of
SYN flooding, denial of service, and distributed denial of service attacks (Joshi & Singh,
2017). In such cases, the system network will be flooded with unwanted and garbage traffic
and the users will not be able to utilize the regular services. The information availability is
targeted through these attacks. Data breaches, data loss, and data leakage are some of the
Security Concerns and Approach to Mitigate the Concerns
There will be a number of security concerns that may get associated with the human resource
management system being developed and deployed for Globoforce. This is because there will
be various threat agents that will be involved with the system, such as network, users, system,
and database.
The primary security concern will be malware threats and attacks. These will be the
malicious codes that may negatively impact the information confidentiality, privacy, and
availability. The various forms of malicious codes may be viruses, worms, logic bombs,
Trojan Horses, ransomware, spyware, and adware. Ransomware is one of the latest additions
to the malware packages which blocks the access to the system and demands a ransom from
the users in return. The ransom is usually in the form of any of the cryptocurrencies. There
are various network-based security concerns that may come up, such as man in the middle
attack, eavesdropping attack, flooding attacks, etc. The flooding attacks may be in the form of
SYN flooding, denial of service, and distributed denial of service attacks (Joshi & Singh,
2017). In such cases, the system network will be flooded with unwanted and garbage traffic
and the users will not be able to utilize the regular services. The information availability is
targeted through these attacks. Data breaches, data loss, and data leakage are some of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Human Resource Management System
other form of security attacks that may come up. There will be databases integrated with the
human resource management system. Database attacks, such as SQL injection attacks or
cross-site scripting attacks may occur. In these attacks, the malicious queries will be used by
the attacker to gain access to the system or the information sets. Data integrity is one of the
essential information properties which may be targeted through the attacks as message
alteration and media alteration attacks. The employees of the organization may also pass on
the system information to the unauthorized entities which may be an accidental or deliberate
act. These insider threats may possess a great risk to the information security and privacy.
There are various measures that may be taken to mitigate and avoid these security concerns.
There shall be integration of advanced technical security controls that shall be done on the
system. The installation and integration of anti-malware and anti-denial tools shall be done
with the human resource management system. Also, advanced access control, such as role-
based or attribute-based access control along with multi-fold authentication shall be used so
that the unauthorized users do not gain access to the system (Qian, Fang & Gonzalez, 2012).
These measures will enforce stronger identity management and user control. Encryption is
one of the necessary measures that shall be taken to avoid the impacts of the security attacks.
The data and information sets in the database and transmitted over the network shall always
be encrypted using the advanced encryption algorithms, such as multi-path encryption,
hashing algorithms, and likewise. In this manner, the attackers will not be able to make use of
these data sets even when they succeed in capturing the data sets. The use of basic methods,
such as firewalls, proxy servers along with the reviews & audits by management shall also be
adopted.
Management Approach
There are various phases that will be involved in the development and delivery of human
resource management system for Globoforce. Three such critical processes will be
implementation, testing, and deployment. Planning and management of these processes will
be done using different approaches as discussed below.
The planning and management of the implementation processes and its associated activities
shall be done using Project Management Body of Knowledge (PMBoK) as the approach. The
implementation shall be carried out in a step by step process and there shall be five broad
phases involved. The initiation of the implementation process shall begin with its feasibility
other form of security attacks that may come up. There will be databases integrated with the
human resource management system. Database attacks, such as SQL injection attacks or
cross-site scripting attacks may occur. In these attacks, the malicious queries will be used by
the attacker to gain access to the system or the information sets. Data integrity is one of the
essential information properties which may be targeted through the attacks as message
alteration and media alteration attacks. The employees of the organization may also pass on
the system information to the unauthorized entities which may be an accidental or deliberate
act. These insider threats may possess a great risk to the information security and privacy.
There are various measures that may be taken to mitigate and avoid these security concerns.
There shall be integration of advanced technical security controls that shall be done on the
system. The installation and integration of anti-malware and anti-denial tools shall be done
with the human resource management system. Also, advanced access control, such as role-
based or attribute-based access control along with multi-fold authentication shall be used so
that the unauthorized users do not gain access to the system (Qian, Fang & Gonzalez, 2012).
These measures will enforce stronger identity management and user control. Encryption is
one of the necessary measures that shall be taken to avoid the impacts of the security attacks.
The data and information sets in the database and transmitted over the network shall always
be encrypted using the advanced encryption algorithms, such as multi-path encryption,
hashing algorithms, and likewise. In this manner, the attackers will not be able to make use of
these data sets even when they succeed in capturing the data sets. The use of basic methods,
such as firewalls, proxy servers along with the reviews & audits by management shall also be
adopted.
Management Approach
There are various phases that will be involved in the development and delivery of human
resource management system for Globoforce. Three such critical processes will be
implementation, testing, and deployment. Planning and management of these processes will
be done using different approaches as discussed below.
The planning and management of the implementation processes and its associated activities
shall be done using Project Management Body of Knowledge (PMBoK) as the approach. The
implementation shall be carried out in a step by step process and there shall be five broad
phases involved. The initiation of the implementation process shall begin with its feasibility

Human Resource Management System
analysis followed by the development of the implementation plan in the planning phase.
System implementation shall be carried out in the execution phase along with the
management of the changes. Quality assessment and management shall be done in the control
and monitoring phases followed by the closure. An implementation closure report shall be
submitted as the final activity for this process. The implementation process will be in sync
with the other project areas and activities with the aid of PMBoK methodology (Zwikael,
2009).
Testing processes and activities shall be managed by the development of a test plan as the
first process. The test plan shall describe the test approach, test processes to be carried out,
defect reporting methods, testing tools, and roles and responsibilities. There shall be different
types of testing processes that shall be carried out for the human resource management
system. System, unit, and integration testing shall be conducted along with regression and
sanity testing. Security and performance are the two essential system qualities and shall be
validated using security and performance testing respectively. Once the test plan is in place,
test creation shall begin on HP Quality Centre as the tool and the execution of the test cases
and scenarios shall be done thereafter. The defects that will be identified shall be logged in
Bugzilla as the testing tool and the development team shall be notified about the same. The
test reports shall be prepared and shared with the management every week highlighting the
defect summary and status for every defect logged in the tool. The defect status of all the
defects shall be closed before marking the testing activity as completed.
The system deployment shall be planned and managed using a phased approach. The testing
of the system using the production data shall be done followed by a series of reviews and
audits by the management. The acceptance on all the deliverables along with the sign-off
from the sponsor shall be provided to carry out with the deployment process. The deployment
plan shall be prepared in the planning and analysis phase that shall list out the step by step
approach to be followed. The management shall measure the performance of the resources
and perform the closure activities before the system is deployed and released for the client.
The deployment report and customer feedback shall be collected and analysed to understand
the customer response on the release that is provided to them (Rose & Indelicato, 2009).
analysis followed by the development of the implementation plan in the planning phase.
System implementation shall be carried out in the execution phase along with the
management of the changes. Quality assessment and management shall be done in the control
and monitoring phases followed by the closure. An implementation closure report shall be
submitted as the final activity for this process. The implementation process will be in sync
with the other project areas and activities with the aid of PMBoK methodology (Zwikael,
2009).
Testing processes and activities shall be managed by the development of a test plan as the
first process. The test plan shall describe the test approach, test processes to be carried out,
defect reporting methods, testing tools, and roles and responsibilities. There shall be different
types of testing processes that shall be carried out for the human resource management
system. System, unit, and integration testing shall be conducted along with regression and
sanity testing. Security and performance are the two essential system qualities and shall be
validated using security and performance testing respectively. Once the test plan is in place,
test creation shall begin on HP Quality Centre as the tool and the execution of the test cases
and scenarios shall be done thereafter. The defects that will be identified shall be logged in
Bugzilla as the testing tool and the development team shall be notified about the same. The
test reports shall be prepared and shared with the management every week highlighting the
defect summary and status for every defect logged in the tool. The defect status of all the
defects shall be closed before marking the testing activity as completed.
The system deployment shall be planned and managed using a phased approach. The testing
of the system using the production data shall be done followed by a series of reviews and
audits by the management. The acceptance on all the deliverables along with the sign-off
from the sponsor shall be provided to carry out with the deployment process. The deployment
plan shall be prepared in the planning and analysis phase that shall list out the step by step
approach to be followed. The management shall measure the performance of the resources
and perform the closure activities before the system is deployed and released for the client.
The deployment report and customer feedback shall be collected and analysed to understand
the customer response on the release that is provided to them (Rose & Indelicato, 2009).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Human Resource Management System
References
Joshi, C., & Singh, U. (2017). Information security risks management framework – A step
towards mitigating security risks in university network. Journal Of Information
Security And Applications, 35, 128-137. doi: 10.1016/j.jisa.2017.06.006
Linthicum, D. (2016). Emerging Hybrid Cloud Patterns. IEEE Cloud Computing, 3(1), 88-91.
doi: 10.1109/mcc.2016.22
Pahl, C. (2015). Containerization and the PaaS Cloud. IEEE Cloud Computing, 2(3), 24-31.
doi: 10.1109/mcc.2015.51
Qian, Y., Fang, Y., & Gonzalez, J. (2012). Managing information security risks during new
technology adoption. Computers & Security, 31(8), 859-869. doi:
10.1016/j.cose.2012.09.001
Rose, K., & Indelicato, G. (2009). Book Review: A Guide to the Project Management Body
of Knowledge (PMBOK® Guide), Fourth EditionA Guide to the Project
Management Body of Knowledge (PMBOK® Guide), Fourth Edition Project
Management Institute. Project Management Journal, 40(2), 104-104. doi:
10.1002/pmj.20125
Zwikael, O. (2009). The Relative Importance of the PMBOK® Guide's Nine Knowledge
Areas during Project Planning. Project Management Journal, 40(4), 94-103. doi:
10.1002/pmj.20116
References
Joshi, C., & Singh, U. (2017). Information security risks management framework – A step
towards mitigating security risks in university network. Journal Of Information
Security And Applications, 35, 128-137. doi: 10.1016/j.jisa.2017.06.006
Linthicum, D. (2016). Emerging Hybrid Cloud Patterns. IEEE Cloud Computing, 3(1), 88-91.
doi: 10.1109/mcc.2016.22
Pahl, C. (2015). Containerization and the PaaS Cloud. IEEE Cloud Computing, 2(3), 24-31.
doi: 10.1109/mcc.2015.51
Qian, Y., Fang, Y., & Gonzalez, J. (2012). Managing information security risks during new
technology adoption. Computers & Security, 31(8), 859-869. doi:
10.1016/j.cose.2012.09.001
Rose, K., & Indelicato, G. (2009). Book Review: A Guide to the Project Management Body
of Knowledge (PMBOK® Guide), Fourth EditionA Guide to the Project
Management Body of Knowledge (PMBOK® Guide), Fourth Edition Project
Management Institute. Project Management Journal, 40(2), 104-104. doi:
10.1002/pmj.20125
Zwikael, O. (2009). The Relative Importance of the PMBOK® Guide's Nine Knowledge
Areas during Project Planning. Project Management Journal, 40(4), 94-103. doi:
10.1002/pmj.20116
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



