University Name: Hybrid Cloud Computing Architecture Report
VerifiedAdded on 2021/06/17
|30
|7288
|345
Report
AI Summary
This report provides a comprehensive analysis of hybrid cloud computing for a regional gardening company. It begins with an executive summary outlining the company's operations and the report's objectives. The core of the report explores proposed architectures for a hybrid cloud, including workload distribution and resource pooling. It then delves into the benefits and issues associated with Platform as a Service (PaaS) and Infrastructure as a Service (IaaS) models. A significant portion of the report is dedicated to a risk assessment for hybrid cloud and microservices, detailing potential risks such as lack of ownership, poor SLA definitions, data compliance issues, and security vulnerabilities, along with proposed preventive actions and contingency plans. The report further outlines proposed information security controls, BCP changes, hybrid cloud administration, SLA management strategies, and SharePoint migration planning. The analysis concludes with a discussion of critical points and key issues, supported by relevant references, providing a complete guide to hybrid cloud implementation.

Running head: Hybrid Cloud
Hybrid Cloud
Unit Code
Unit Name
University Name
1
Hybrid Cloud
Unit Code
Unit Name
University Name
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Hybrid Cloud
Executive Summary
The regional garden company runs a number of gardening related activities. It has a very large
display of garden products and services that open once a year for public viewing. These
initiatives include the company’s Nursery, which supplies plants and gardens for the public, as
well as Regional Gardening planners providing gardening advice and consultancy. This report
includes the capability of various cloud computing architectures, as required by a set of
professional requirements to determine eligibility for cloud computing delivery models. There is
also a highlight in this report about the government and security requirements framework for
planning the ICT risk management for cloud computing and for the cloud computing distribution
plan. Finally, business requirements are also considered in this report to plan for the migration of
cloud model.
Executive Summary
The regional garden company runs a number of gardening related activities. It has a very large
display of garden products and services that open once a year for public viewing. These
initiatives include the company’s Nursery, which supplies plants and gardens for the public, as
well as Regional Gardening planners providing gardening advice and consultancy. This report
includes the capability of various cloud computing architectures, as required by a set of
professional requirements to determine eligibility for cloud computing delivery models. There is
also a highlight in this report about the government and security requirements framework for
planning the ICT risk management for cloud computing and for the cloud computing distribution
plan. Finally, business requirements are also considered in this report to plan for the migration of
cloud model.

Hybrid Cloud
Contents
Proposed Architectures for a Hybrid Cloud....................................................................................2
PaaS.................................................................................................................................................3
IaaS..................................................................................................................................................3
Benefits and issues of PaaS.............................................................................................................4
Benefits and issues of IaaS..............................................................................................................5
Risk report for Hybrid Cloud and Microservices............................................................................5
Proposed Information Security controls..........................................................................................8
BCP Changes.................................................................................................................................10
Hybrid Cloud Administration and SLA Management...................................................................14
SharePoint Migration Planning......................................................................................................18
Critical Points and Key issues.......................................................................................................20
References......................................................................................................................................22
Contents
Proposed Architectures for a Hybrid Cloud....................................................................................2
PaaS.................................................................................................................................................3
IaaS..................................................................................................................................................3
Benefits and issues of PaaS.............................................................................................................4
Benefits and issues of IaaS..............................................................................................................5
Risk report for Hybrid Cloud and Microservices............................................................................5
Proposed Information Security controls..........................................................................................8
BCP Changes.................................................................................................................................10
Hybrid Cloud Administration and SLA Management...................................................................14
SharePoint Migration Planning......................................................................................................18
Critical Points and Key issues.......................................................................................................20
References......................................................................................................................................22
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Hybrid Cloud
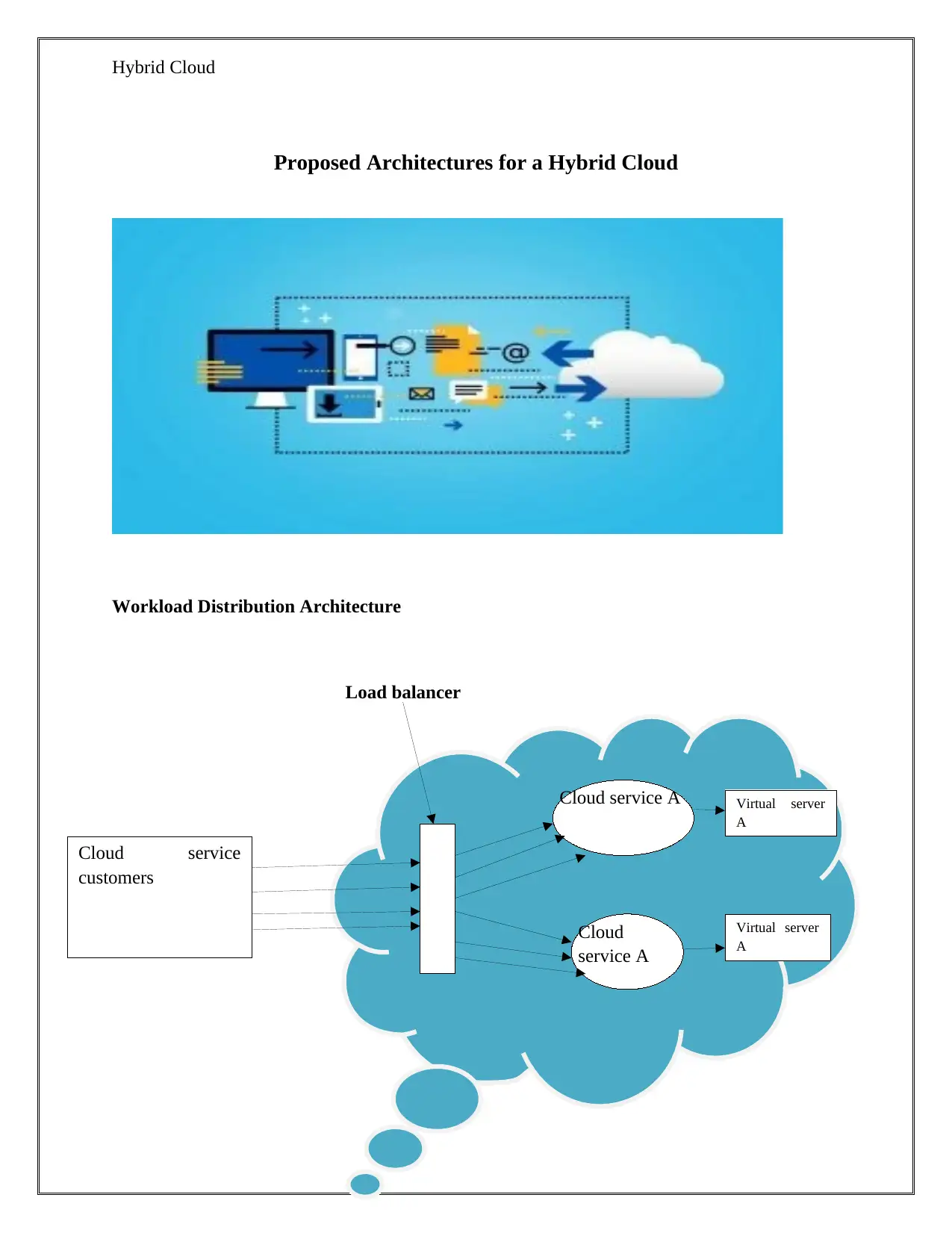
Proposed Architectures for a Hybrid Cloud
Workload Distribution Architecture
Load balancer
Cloud service
customers
Cloud service A
Cloud
service A
Virtual server
A
Virtual server
A
Proposed Architectures for a Hybrid Cloud
Workload Distribution Architecture
Load balancer
Cloud service
customers
Cloud service A
Cloud
service A
Virtual server
A
Virtual server
A
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Hybrid Cloud
Workload Distribution & Resource Pooling Architectures
The Cloud architects should implement some concepts or best practice to create extremely
scalable applications. This concept is very critical because of continuous expansions of data sets,
unpredictable traffic pattern, as well as the need for earlier response time. The 2 common basic
cloud planning models are workload distribution architecture moreover resource pool
architecture.
Workload distributional architecture
The workload distribution architectures use information technology assets that may scale out by
using one or more of the same IT resource. This is accomplished using load balancers that
provide run-time logic that evenly distributes workload between available information
technology resources. These models may be apply to several IT assets as well as is usually
utilized with it; the distributed effective server, the cloud storage gadgets furthermore cloud
service. Additionally to the load balancer or the aforementioned assets, all these mechanisms
may be an element of these models:
1) Cloud Usage Monitor may perform data processing and runtime tracking
2) Audit monitors use to monitor system can need to meet statutory necessities
3) The Hypervisor for managing workloads and virtual hosts those need to be distributed
4) Separating the logical network boundaries of the cloud customer network boundary
5) Asset clusters that are usually utilized to support the workload balancing between cluster
nodes
6) The assets replication to generate fresh virtual resource instance under the improved
workloads
Workload Distribution & Resource Pooling Architectures
The Cloud architects should implement some concepts or best practice to create extremely
scalable applications. This concept is very critical because of continuous expansions of data sets,
unpredictable traffic pattern, as well as the need for earlier response time. The 2 common basic
cloud planning models are workload distribution architecture moreover resource pool
architecture.
Workload distributional architecture
The workload distribution architectures use information technology assets that may scale out by
using one or more of the same IT resource. This is accomplished using load balancers that
provide run-time logic that evenly distributes workload between available information
technology resources. These models may be apply to several IT assets as well as is usually
utilized with it; the distributed effective server, the cloud storage gadgets furthermore cloud
service. Additionally to the load balancer or the aforementioned assets, all these mechanisms
may be an element of these models:
1) Cloud Usage Monitor may perform data processing and runtime tracking
2) Audit monitors use to monitor system can need to meet statutory necessities
3) The Hypervisor for managing workloads and virtual hosts those need to be distributed
4) Separating the logical network boundaries of the cloud customer network boundary
5) Asset clusters that are usually utilized to support the workload balancing between cluster
nodes
6) The assets replication to generate fresh virtual resource instance under the improved
workloads

Hybrid Cloud
Resource Pool Architecture
The resource pool architectures are also based on grouping the same IT assets into teams. Pools
may be virtual and physical resources. This same resource is automatically teamed as well as
maintained by system to ensure they stay in sync. A sample resource pool is as follows: A
physical server pool that contains network server that has an operating system or the other
needed applications available for immediate use.
• The virtual server pool is usually configured based on the customer's pre-selected template.
• A storage pool consisting of files and block-based storage container.
• The networks pool of unusual pre-configured networks devices. Examples; the Virtual
firewall as well as switches for superfluous connection, the load balancing, or link aggregation.
• CPU assets are allocated to the virtual server's CPU pool.
• It can be used to vertically adjust the physical RAM pool of a newly provisioned physical
server.
Sharing the same IT assets for extensibility may error-prone or there is an issue that makes them
totally synchronize on a continuous basis. Solution to these issues is to utilize automatic
synchronization systems to team the same IT assets into the pool or keep them synchronized. The
following is an example of how a company can use a resource pool in the business using the
Memory PoolCPU Pool Storage pool Network pool
Resource Pool Architecture
The resource pool architectures are also based on grouping the same IT assets into teams. Pools
may be virtual and physical resources. This same resource is automatically teamed as well as
maintained by system to ensure they stay in sync. A sample resource pool is as follows: A
physical server pool that contains network server that has an operating system or the other
needed applications available for immediate use.
• The virtual server pool is usually configured based on the customer's pre-selected template.
• A storage pool consisting of files and block-based storage container.
• The networks pool of unusual pre-configured networks devices. Examples; the Virtual
firewall as well as switches for superfluous connection, the load balancing, or link aggregation.
• CPU assets are allocated to the virtual server's CPU pool.
• It can be used to vertically adjust the physical RAM pool of a newly provisioned physical
server.
Sharing the same IT assets for extensibility may error-prone or there is an issue that makes them
totally synchronize on a continuous basis. Solution to these issues is to utilize automatic
synchronization systems to team the same IT assets into the pool or keep them synchronized. The
following is an example of how a company can use a resource pool in the business using the
Memory PoolCPU Pool Storage pool Network pool
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Hybrid Cloud
examples in Cloud web Pattern. The asset pool architecture may be used to scale the system
vertically and horizontally, depends on how pool is organized. For Example; If the workload
increase or more CPU, as well as RAM assets, are also required, CPU moreover RAM resource
pools may be used to scale information technology resources (for example virtual servers)
vertically. The virtual servers may extract these assets from RAM and CPU asset pools.
The IT resources may scale out by adding one and more of the same IT assets. The load
balancers also provide run-time logic to consistently distribute workload across the existing IT
assets. Resulting workload’s distribution architecture also reduces the overuse and
underutilization of IT resources to the extent that they rely on the complexity of load balancing
algorithm along with runtime logic. This infrastructure model may be applied to several IT asset,
usually distributed virtual servers, the cloud storage device or the cloud services to support
workload distribution.
Resource pool
The resource pool architecture is based on utilization of single or the more asset pools where the
same IT assets are grouped furthermore also maintained by the system and the system
automatically make sure that they are synchronized.
Here is a general example of an asset pool:
After the resource pool is defined, several instances of information technology assets
from every pool may be formed to provide a pool of "real-time" IT assets.
Maybe advantages and problems of deployment results
Cloud systems need methods that can dynamically scale or shrink IT resources based on demand,
or have a mechanism that can provide redundancy moreover ease of managing IT assets. The
WDA provides the method to distribute workloads among various copies of information
examples in Cloud web Pattern. The asset pool architecture may be used to scale the system
vertically and horizontally, depends on how pool is organized. For Example; If the workload
increase or more CPU, as well as RAM assets, are also required, CPU moreover RAM resource
pools may be used to scale information technology resources (for example virtual servers)
vertically. The virtual servers may extract these assets from RAM and CPU asset pools.
The IT resources may scale out by adding one and more of the same IT assets. The load
balancers also provide run-time logic to consistently distribute workload across the existing IT
assets. Resulting workload’s distribution architecture also reduces the overuse and
underutilization of IT resources to the extent that they rely on the complexity of load balancing
algorithm along with runtime logic. This infrastructure model may be applied to several IT asset,
usually distributed virtual servers, the cloud storage device or the cloud services to support
workload distribution.
Resource pool
The resource pool architecture is based on utilization of single or the more asset pools where the
same IT assets are grouped furthermore also maintained by the system and the system
automatically make sure that they are synchronized.
Here is a general example of an asset pool:
After the resource pool is defined, several instances of information technology assets
from every pool may be formed to provide a pool of "real-time" IT assets.
Maybe advantages and problems of deployment results
Cloud systems need methods that can dynamically scale or shrink IT resources based on demand,
or have a mechanism that can provide redundancy moreover ease of managing IT assets. The
WDA provides the method to distribute workloads among various copies of information
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Hybrid Cloud
technology resources, moreover resource pools provide the way to automatically synchronize IT
asset by using resource pools and provide an on-demand dynamic allocation method of
resources. In short, they may be used to design as well as execute complex architecture to
automatically scale IT resources as workloads increase and decrease, and provide simultaneous
IT resources, provide system redundancy, balance the load among resources, and manage and
audit IT resources.
Benefits
Cost: Here, no calculations or hardware resources are waiting for the balance sheet. Depreciation
and monthly inspection system usage do not exist.
Scale: "Flexibility and resiliency": It can be transferred from the private network to the public
network in order to test the latest applications.
Issues:
1. There is no control over virtual machine processor data is not processed, it is a large security
risk because Regional Gardens Ltd does not know what is actually happening to organization’s
data (Jamshidi, Ahmad & Pahl, 2013).
2. There is no control on the platform according to the cloud offerings
3. The platform is usually a shared platform, such as other customers also running diverse
websites on a similar IIS platform.
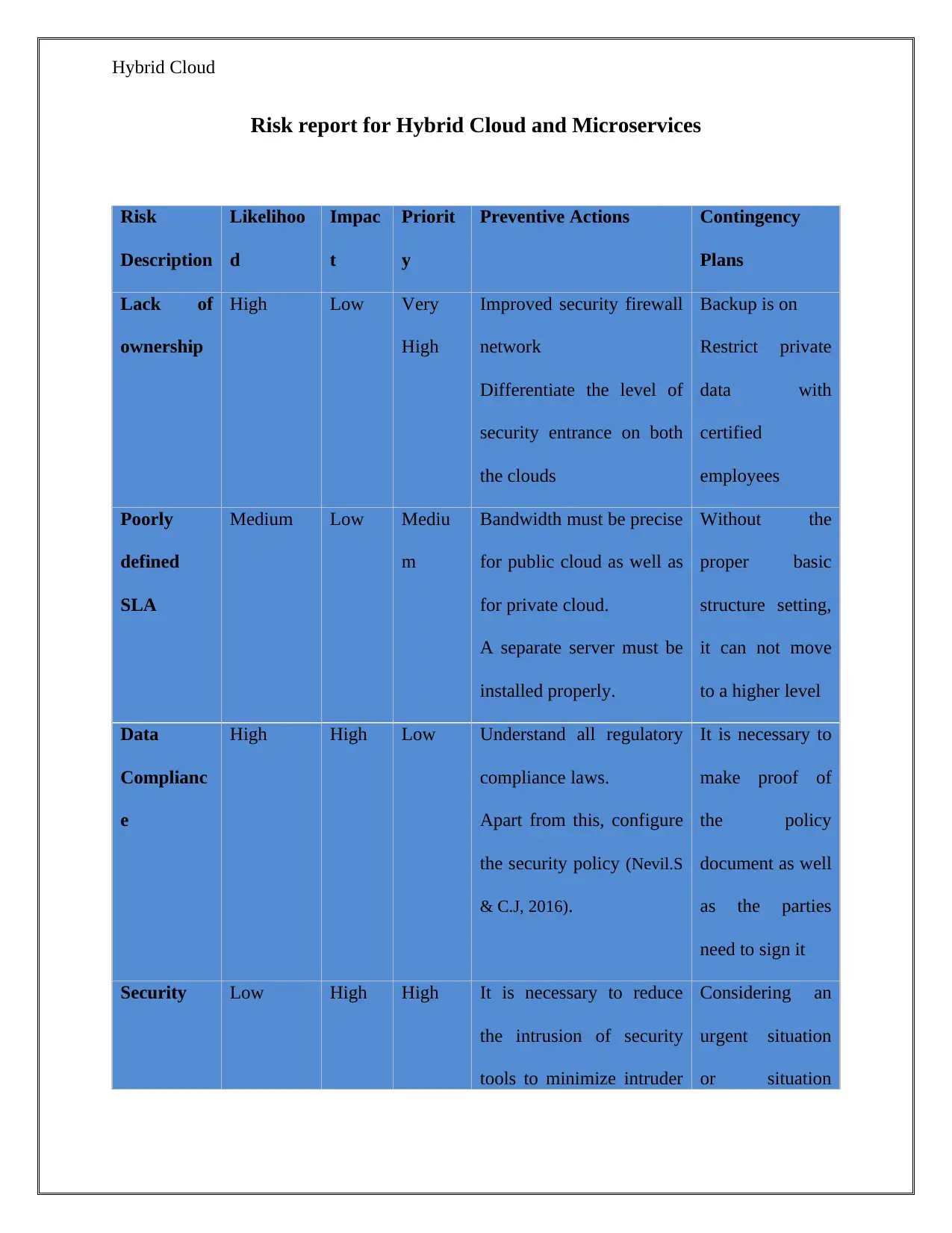
Risk report for Hybrid Cloud and Microservices
Risk Description Likelihood Impact Priority Preventive Actions Contingency Plans
technology resources, moreover resource pools provide the way to automatically synchronize IT
asset by using resource pools and provide an on-demand dynamic allocation method of
resources. In short, they may be used to design as well as execute complex architecture to
automatically scale IT resources as workloads increase and decrease, and provide simultaneous
IT resources, provide system redundancy, balance the load among resources, and manage and
audit IT resources.
Benefits
Cost: Here, no calculations or hardware resources are waiting for the balance sheet. Depreciation
and monthly inspection system usage do not exist.
Scale: "Flexibility and resiliency": It can be transferred from the private network to the public
network in order to test the latest applications.
Issues:
1. There is no control over virtual machine processor data is not processed, it is a large security
risk because Regional Gardens Ltd does not know what is actually happening to organization’s
data (Jamshidi, Ahmad & Pahl, 2013).
2. There is no control on the platform according to the cloud offerings
3. The platform is usually a shared platform, such as other customers also running diverse
websites on a similar IIS platform.
Risk report for Hybrid Cloud and Microservices
Risk Description Likelihood Impact Priority Preventive Actions Contingency Plans

Hybrid Cloud
Lack of ownership High Low Very High Improved security firewall network
Differentiate the level of security entrance on both the clouds Backup is on
Restrict private data with certified employees
Poorly defined SLA Medium Low Medium Bandwidth must be precise for public cloud
as well as for private cloud.
A separate server must be installed properly. Without the proper basic structure setting, it can
not move to a higher level
Data Compliance High High Low Understand all regulatory compliance laws.
Apart from this, configure the security policy (Nevil.S & C.J, 2016). It is necessary to make
proof of the policy document as well as the parties need to sign it
Security Low High High It is necessary to reduce the intrusion of security tools to
minimize intruder attacks and reducing data redundancy. Considering an urgent situation or
situation which can definitely be measured for high growth
Risks associated AWS hybrid cloud and microservices strategy
Distributed computing gives an essential strategy to get to servers, storing, databases and a wide
course of action of use benefits over the Internet. A Cloud organization arranges, for instance,
Amazon Web Services claims and keeps up the framework related hardware required for these
application organizations, while your course of action and use what you require through a web
application. In a dispersed registering condition, new IT resources are simply ever a tick away,
which suggests association diminish the time it takes to make those benefits available to
Regional Graden's designers from weeks to minutes.
Lack of ownership High Low Very High Improved security firewall network
Differentiate the level of security entrance on both the clouds Backup is on
Restrict private data with certified employees
Poorly defined SLA Medium Low Medium Bandwidth must be precise for public cloud
as well as for private cloud.
A separate server must be installed properly. Without the proper basic structure setting, it can
not move to a higher level
Data Compliance High High Low Understand all regulatory compliance laws.
Apart from this, configure the security policy (Nevil.S & C.J, 2016). It is necessary to make
proof of the policy document as well as the parties need to sign it
Security Low High High It is necessary to reduce the intrusion of security tools to
minimize intruder attacks and reducing data redundancy. Considering an urgent situation or
situation which can definitely be measured for high growth
Risks associated AWS hybrid cloud and microservices strategy
Distributed computing gives an essential strategy to get to servers, storing, databases and a wide
course of action of use benefits over the Internet. A Cloud organization arranges, for instance,
Amazon Web Services claims and keeps up the framework related hardware required for these
application organizations, while your course of action and use what you require through a web
application. In a dispersed registering condition, new IT resources are simply ever a tick away,
which suggests association diminish the time it takes to make those benefits available to
Regional Graden's designers from weeks to minutes.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Hybrid Cloud
Lack of ownership: Cloud retailers should fully verify the security of processed data. Once the
cloud is deployed, these activities lose the ability to tell their data sets. Enterprise managers
should know what security standards the client can use to avoid accidents.
Solution: Data ownership and security need verification. Avoid suppliers who cannot provide
reasonable proprietary expectations. Identify vendors in well-organized service-level agreements
that cover hybrid IT companies. Know what data is accessible; Provider provides access to logs
and statistics and all jurisdiction or geographical locations to store data (Manias & Baude, 2012).
Security: Many business administrators are disabled if failing to use authentication, identity
management, and permission processes for private and public clouds. Cloud security protocols
should be integrated (Narasimhan G., 2018).
Solution: Change the control of the two clouds. Synchronize ongoing security data or identity
management services with Regional Gardens Ltd and Cloud Systems. Maintain the latest state of
internal data collection for sensitive data that is not suitable for the public cloud.
Explicit definition of SLA
When regional gardens moved to the cloud, they lost the ability to control the data set, which
forced them to rely on service providers to securely secure the data in the public domain. Work
to synchronize security data or run in two clouds with the System Regional Garden Limited,
which use Identity Management Services (Ahmad, Shanmugam, Idris, Samy & Hasan AlBakri,
2013).
Solution: Access permissions and protection must be explained and there is a clear definition of
security measures in the SLA. This applies only to the expectations and needs of the cloud
service providers. The reasonable expectation of the service is to be clearly explained in detail in
Lack of ownership: Cloud retailers should fully verify the security of processed data. Once the
cloud is deployed, these activities lose the ability to tell their data sets. Enterprise managers
should know what security standards the client can use to avoid accidents.
Solution: Data ownership and security need verification. Avoid suppliers who cannot provide
reasonable proprietary expectations. Identify vendors in well-organized service-level agreements
that cover hybrid IT companies. Know what data is accessible; Provider provides access to logs
and statistics and all jurisdiction or geographical locations to store data (Manias & Baude, 2012).
Security: Many business administrators are disabled if failing to use authentication, identity
management, and permission processes for private and public clouds. Cloud security protocols
should be integrated (Narasimhan G., 2018).
Solution: Change the control of the two clouds. Synchronize ongoing security data or identity
management services with Regional Gardens Ltd and Cloud Systems. Maintain the latest state of
internal data collection for sensitive data that is not suitable for the public cloud.
Explicit definition of SLA
When regional gardens moved to the cloud, they lost the ability to control the data set, which
forced them to rely on service providers to securely secure the data in the public domain. Work
to synchronize security data or run in two clouds with the System Regional Garden Limited,
which use Identity Management Services (Ahmad, Shanmugam, Idris, Samy & Hasan AlBakri,
2013).
Solution: Access permissions and protection must be explained and there is a clear definition of
security measures in the SLA. This applies only to the expectations and needs of the cloud
service providers. The reasonable expectation of the service is to be clearly explained in detail in
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Hybrid Cloud
the SLA so that if the service is not interrupted or the data is compromised then the customer's
shelter. Before signing a contract, it has been reviewed by an attorney (Linthicum, 2017).
Data compliance: More precedential care of hybrid clouds is needed when compliance is needed.
It is difficult to follow and display with hybrid models because the data is moved back.
Solution: It is necessary to coordinate two clouds. Regional Gardens Ltd do not have to make
sure organization only follow its public cloud provider and private cloud. To handle sensitive
data, two clouds must meet the industry standards for data protection.
the SLA so that if the service is not interrupted or the data is compromised then the customer's
shelter. Before signing a contract, it has been reviewed by an attorney (Linthicum, 2017).
Data compliance: More precedential care of hybrid clouds is needed when compliance is needed.
It is difficult to follow and display with hybrid models because the data is moved back.
Solution: It is necessary to coordinate two clouds. Regional Gardens Ltd do not have to make
sure organization only follow its public cloud provider and private cloud. To handle sensitive
data, two clouds must meet the industry standards for data protection.
Hybrid Cloud
Risk report for Hybrid Cloud and Microservices
Risk
Description
Likelihoo
d
Impac
t
Priorit
y
Preventive Actions Contingency
Plans
Lack of
ownership
High Low Very
High
Improved security firewall
network
Differentiate the level of
security entrance on both
the clouds
Backup is on
Restrict private
data with
certified
employees
Poorly
defined
SLA
Medium Low Mediu
m
Bandwidth must be precise
for public cloud as well as
for private cloud.
A separate server must be
installed properly.
Without the
proper basic
structure setting,
it can not move
to a higher level
Data
Complianc
e
High High Low Understand all regulatory
compliance laws.
Apart from this, configure
the security policy (Nevil.S
& C.J, 2016).
It is necessary to
make proof of
the policy
document as well
as the parties
need to sign it
Security Low High High It is necessary to reduce
the intrusion of security
tools to minimize intruder
Considering an
urgent situation
or situation
Risk report for Hybrid Cloud and Microservices
Risk
Description
Likelihoo
d
Impac
t
Priorit
y
Preventive Actions Contingency
Plans
Lack of
ownership
High Low Very
High
Improved security firewall
network
Differentiate the level of
security entrance on both
the clouds
Backup is on
Restrict private
data with
certified
employees
Poorly
defined
SLA
Medium Low Mediu
m
Bandwidth must be precise
for public cloud as well as
for private cloud.
A separate server must be
installed properly.
Without the
proper basic
structure setting,
it can not move
to a higher level
Data
Complianc
e
High High Low Understand all regulatory
compliance laws.
Apart from this, configure
the security policy (Nevil.S
& C.J, 2016).
It is necessary to
make proof of
the policy
document as well
as the parties
need to sign it
Security Low High High It is necessary to reduce
the intrusion of security
tools to minimize intruder
Considering an
urgent situation
or situation
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 30
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

