Hybrid Cloud Deployment: Security, Risks & AWS Migration Strategies
VerifiedAdded on 2021/05/31
|10
|2217
|80
Report
AI Summary
This report provides a comprehensive analysis of hybrid cloud architecture, focusing on the reasons for deployment, associated risks, and controlling measures. It delves into information security considerations, business continuity planning, remote server administration, and resource management within a hybrid cloud environment. A significant portion of the report is dedicated to migrating an email instance to AWS, highlighting potential issues and challenges. The document emphasizes the importance of risk assessment, security policies, and service level agreements (SLAs) in ensuring a successful and secure hybrid cloud implementation. It also touches upon the advantages and limitations of hybrid cloud strategies, offering insights into cost savings, security enhancements, and operational efficiencies. Concluding with a detailed discussion on the migration process and potential issues in AWS, the report serves as a valuable resource for understanding the complexities and benefits of hybrid cloud adoption.

Contents
Contents......................................................................................................................................................1
Cloud architecture.......................................................................................................................................1
Reasons to deploy.......................................................................................................................................2
Risks associated with hybrid cloud strategy and controlling measures.......................................................3
Information security....................................................................................................................................5
Business continuity plan..............................................................................................................................5
Remote server administration and Resource Management........................................................................6
Migrating Email instance to AWS and its issues..........................................................................................8
Issues in the AWS migration........................................................................................................................8
References...................................................................................................................................................9
Cloud architecture
Hybrid cloud architecture is the combination of on premises resources (private) and
cloud resources (public). It is a good approach while the company has on premises
resources and migration of these resources will take long time (Morgenthal, 2015).
Therefore, the implementation of new resources must be selected for cloud. The
resources recommended for cloud can be data storage, management tools, network
applications and security tools. Hybrid cloud deployment needs the following:
IaaS platform like AWS, Azure or Google to implement public infrastructure
Private cloud
WAN in between these two environments
1
Contents......................................................................................................................................................1
Cloud architecture.......................................................................................................................................1
Reasons to deploy.......................................................................................................................................2
Risks associated with hybrid cloud strategy and controlling measures.......................................................3
Information security....................................................................................................................................5
Business continuity plan..............................................................................................................................5
Remote server administration and Resource Management........................................................................6
Migrating Email instance to AWS and its issues..........................................................................................8
Issues in the AWS migration........................................................................................................................8
References...................................................................................................................................................9
Cloud architecture
Hybrid cloud architecture is the combination of on premises resources (private) and
cloud resources (public). It is a good approach while the company has on premises
resources and migration of these resources will take long time (Morgenthal, 2015).
Therefore, the implementation of new resources must be selected for cloud. The
resources recommended for cloud can be data storage, management tools, network
applications and security tools. Hybrid cloud deployment needs the following:
IaaS platform like AWS, Azure or Google to implement public infrastructure
Private cloud
WAN in between these two environments
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Hybrid cloud architecture
Reasons to deploy
The reasons of recommendation for hybrid cloud architecture for Regional Gardens are
(JARIWALA, 2013):
Flexible architecture
Security of most concern applications and data can be ensured by deploying
them on cloud. Devices are configured in such a way that only authorized
machines can access the data.
To implement an efficient operation process in business hybrid cloud is the most
flexible approach (Ahmed, 2017).
Contribution of hybrid cloud strategy
2
Reasons to deploy
The reasons of recommendation for hybrid cloud architecture for Regional Gardens are
(JARIWALA, 2013):
Flexible architecture
Security of most concern applications and data can be ensured by deploying
them on cloud. Devices are configured in such a way that only authorized
machines can access the data.
To implement an efficient operation process in business hybrid cloud is the most
flexible approach (Ahmed, 2017).
Contribution of hybrid cloud strategy
2
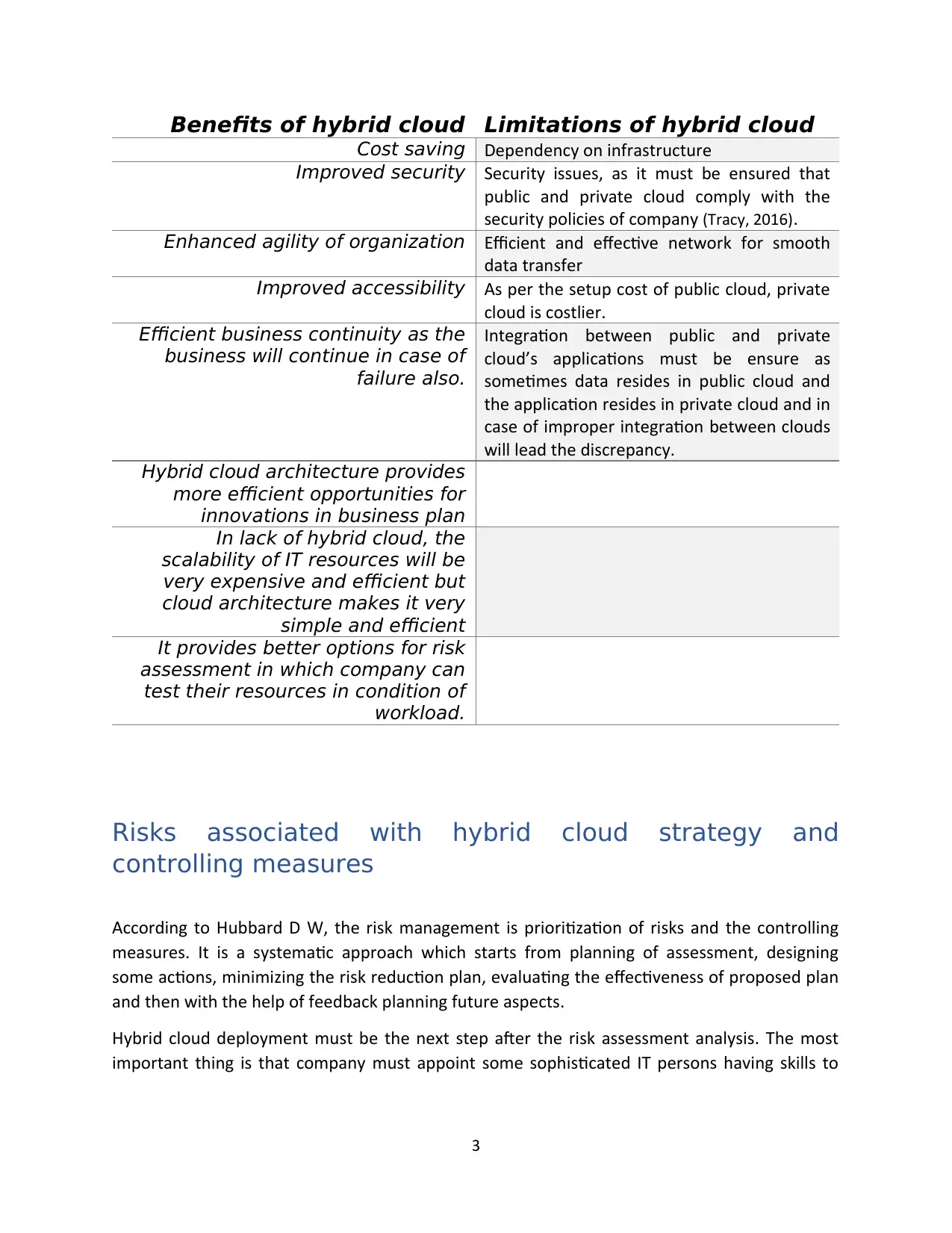
Benefits of hybrid cloud Limitations of hybrid cloud
Cost saving Dependency on infrastructure
Improved security Security issues, as it must be ensured that
public and private cloud comply with the
security policies of company (Tracy, 2016).
Enhanced agility of organization Efficient and effective network for smooth
data transfer
Improved accessibility As per the setup cost of public cloud, private
cloud is costlier.
Efficient business continuity as the
business will continue in case of
failure also.
Integration between public and private
cloud’s applications must be ensure as
sometimes data resides in public cloud and
the application resides in private cloud and in
case of improper integration between clouds
will lead the discrepancy.
Hybrid cloud architecture provides
more efficient opportunities for
innovations in business plan
In lack of hybrid cloud, the
scalability of IT resources will be
very expensive and efficient but
cloud architecture makes it very
simple and efficient
It provides better options for risk
assessment in which company can
test their resources in condition of
workload.
Risks associated with hybrid cloud strategy and
controlling measures
According to Hubbard D W, the risk management is prioritization of risks and the controlling
measures. It is a systematic approach which starts from planning of assessment, designing
some actions, minimizing the risk reduction plan, evaluating the effectiveness of proposed plan
and then with the help of feedback planning future aspects.
Hybrid cloud deployment must be the next step after the risk assessment analysis. The most
important thing is that company must appoint some sophisticated IT persons having skills to
3
Cost saving Dependency on infrastructure
Improved security Security issues, as it must be ensured that
public and private cloud comply with the
security policies of company (Tracy, 2016).
Enhanced agility of organization Efficient and effective network for smooth
data transfer
Improved accessibility As per the setup cost of public cloud, private
cloud is costlier.
Efficient business continuity as the
business will continue in case of
failure also.
Integration between public and private
cloud’s applications must be ensure as
sometimes data resides in public cloud and
the application resides in private cloud and in
case of improper integration between clouds
will lead the discrepancy.
Hybrid cloud architecture provides
more efficient opportunities for
innovations in business plan
In lack of hybrid cloud, the
scalability of IT resources will be
very expensive and efficient but
cloud architecture makes it very
simple and efficient
It provides better options for risk
assessment in which company can
test their resources in condition of
workload.
Risks associated with hybrid cloud strategy and
controlling measures
According to Hubbard D W, the risk management is prioritization of risks and the controlling
measures. It is a systematic approach which starts from planning of assessment, designing
some actions, minimizing the risk reduction plan, evaluating the effectiveness of proposed plan
and then with the help of feedback planning future aspects.
Hybrid cloud deployment must be the next step after the risk assessment analysis. The most
important thing is that company must appoint some sophisticated IT persons having skills to
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
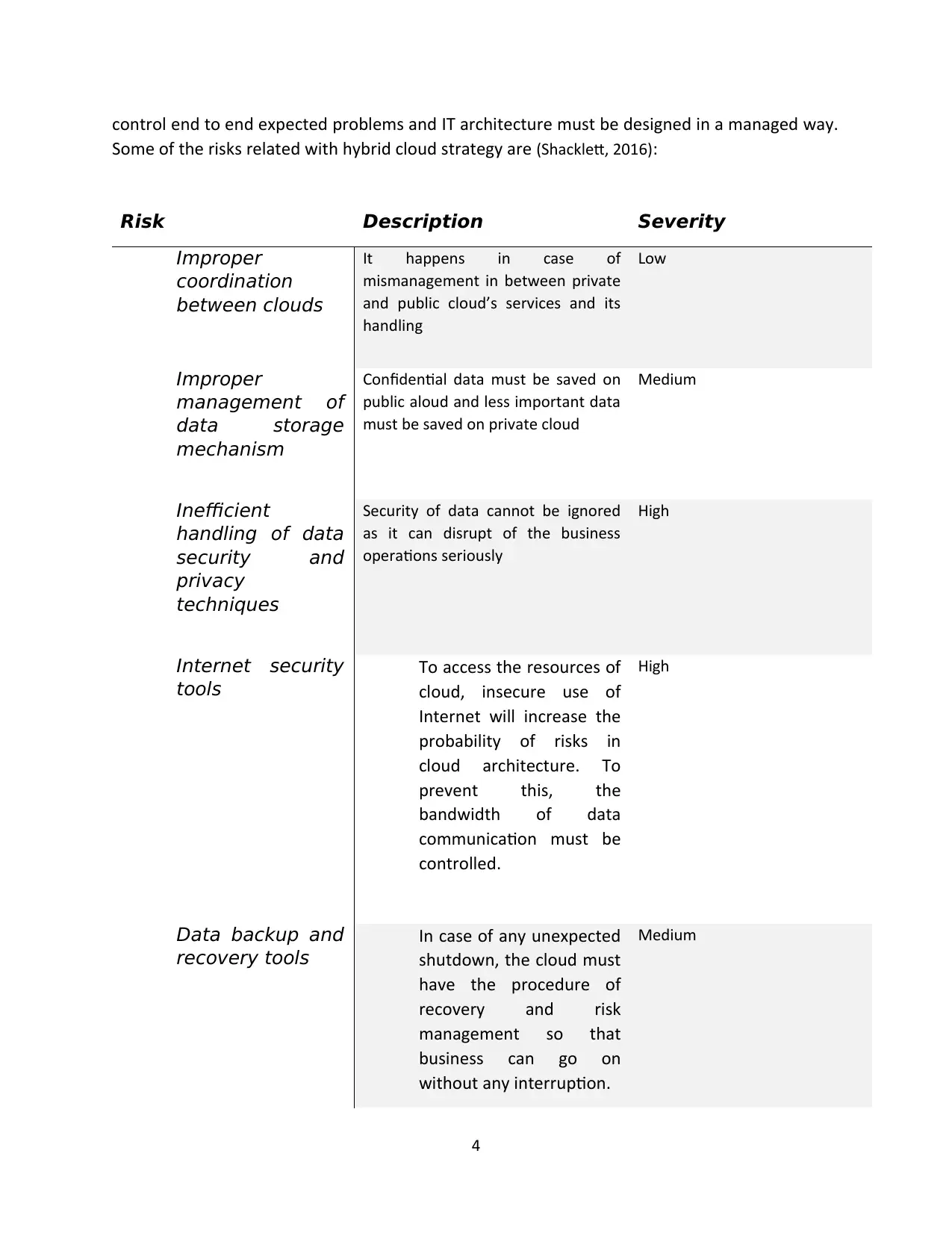
control end to end expected problems and IT architecture must be designed in a managed way.
Some of the risks related with hybrid cloud strategy are (Shacklett, 2016):
Risk Description Severity
Improper
coordination
between clouds
It happens in case of
mismanagement in between private
and public cloud’s services and its
handling
Low
Improper
management of
data storage
mechanism
Confidential data must be saved on
public aloud and less important data
must be saved on private cloud
Medium
Inefficient
handling of data
security and
privacy
techniques
Security of data cannot be ignored
as it can disrupt of the business
operations seriously
High
Internet security
tools
To access the resources of
cloud, insecure use of
Internet will increase the
probability of risks in
cloud architecture. To
prevent this, the
bandwidth of data
communication must be
controlled.
High
Data backup and
recovery tools
In case of any unexpected
shutdown, the cloud must
have the procedure of
recovery and risk
management so that
business can go on
without any interruption.
Medium
4
Some of the risks related with hybrid cloud strategy are (Shacklett, 2016):
Risk Description Severity
Improper
coordination
between clouds
It happens in case of
mismanagement in between private
and public cloud’s services and its
handling
Low
Improper
management of
data storage
mechanism
Confidential data must be saved on
public aloud and less important data
must be saved on private cloud
Medium
Inefficient
handling of data
security and
privacy
techniques
Security of data cannot be ignored
as it can disrupt of the business
operations seriously
High
Internet security
tools
To access the resources of
cloud, insecure use of
Internet will increase the
probability of risks in
cloud architecture. To
prevent this, the
bandwidth of data
communication must be
controlled.
High
Data backup and
recovery tools
In case of any unexpected
shutdown, the cloud must
have the procedure of
recovery and risk
management so that
business can go on
without any interruption.
Medium
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SLA Before migrating business
on cloud, the agreement
between organization and
cloud service provider
must be signed and all the
software and applications
must be licensed. The
contract must have a clear
picture of pricing and all
other conditions.
High
Information security
To implement information security while migrating on hybrid cloud, business
organizations must follow some guidelines, such as:
Selection of right public cloud service provider: It ensures the method of
protection to be followed, the data recovery and backup mechanism, server
administration and authentication of virtual machines (Kaushal, 2017).
It must be understandable by the IT experts where the area of vulnerability in
business is and how to control it. Technical understanding of environment is
expected in continuous way. It can be done by following a regular process of
auditing.
The security policies of organization must ensure the compliance and the
alternative ways to keep backup and recovery of information.
The information security can be on risk, if the selection of public cloud service
provider is not done cautiously. This is the responsibility of IT department of
organization that the security parameters must be managed efficiently and
consistently (Shacklett, 10-hybrid-cloud-risk-areas-that-the-enterprise-must-manage,
2016).
The information exchange must be done in encrypted manner, for this antivirus
programs or Firewall can be implemented in business. The selection of antivirus
must cover DoS attack, IP protection, Defined SLAs and preventive measures
about malicious employees.
Business continuity plan
5
on cloud, the agreement
between organization and
cloud service provider
must be signed and all the
software and applications
must be licensed. The
contract must have a clear
picture of pricing and all
other conditions.
High
Information security
To implement information security while migrating on hybrid cloud, business
organizations must follow some guidelines, such as:
Selection of right public cloud service provider: It ensures the method of
protection to be followed, the data recovery and backup mechanism, server
administration and authentication of virtual machines (Kaushal, 2017).
It must be understandable by the IT experts where the area of vulnerability in
business is and how to control it. Technical understanding of environment is
expected in continuous way. It can be done by following a regular process of
auditing.
The security policies of organization must ensure the compliance and the
alternative ways to keep backup and recovery of information.
The information security can be on risk, if the selection of public cloud service
provider is not done cautiously. This is the responsibility of IT department of
organization that the security parameters must be managed efficiently and
consistently (Shacklett, 10-hybrid-cloud-risk-areas-that-the-enterprise-must-manage,
2016).
The information exchange must be done in encrypted manner, for this antivirus
programs or Firewall can be implemented in business. The selection of antivirus
must cover DoS attack, IP protection, Defined SLAs and preventive measures
about malicious employees.
Business continuity plan
5

Business continuity plan is a procedure which ensures the existence of business in
extreme conditions. The conditions may vary from the loss of a specific key to the
destruction of resources but the manager of business must prepare for any condition
and follow guidelines to run business (Campbell, 2016).
As the hybrid cloud adopt the advantages of both public and private cloud, the business
organization can deploy the critical applications on the private cloud and less complex
applications on public cloud. Private cloud provides enhanced security whereas the
public cloud provides the cheap business continuity plan. Private cloud encrypts the
data through passwords and firewall can prevent the unauthorized data packets to
communicate in the network of business. It increases the cost of business. Data security
and recovery ensures the business continuity and hence placed in the private cloud.
To prepare the business continuity plan below information must be ensured:
Data must be kept in form of backup which impacts on business analytics and risk
assessment.
Data recovery point must be maintained
The contact list of all the employees, stakeholders, contractors and suppliers must be
maintained.
The steps to be followed in case of problems must be kept.
Remote server administration and Resource Management
Remote server administration is a component of windows server which is used to manage remote
resources of network. It was firstly introduced in Windows Server 2008 R2. With the help of RSAT the
administrators can run special programs called snap-ins which can control the applications of other
computers. This software also includes Hyper-V management and updates related with clusters. This
software is compatible with every version of Windows OS. In hybrid cloud, the network security is the
most essential part of strategy and Firewall is by default the most important tool of RSAT. By default in
RSAT, this feature is on. We recommend the Windows 2008 Server core edition for the hybrid cloud of
regional gardens as it can be manageable in many ways through MMC (Khanin, 2008):
Server roles: if this option is installed, the ports are opened by default and there is no need of extra
configuration. If MMC snap-in is installed for a specific role then the user can directly control the role at
server core.
Domain joined: Till the domain is created, the settings are changed and the remote management is
possible.
Workgroup server: The latest scenario, which tests windows 2008 server. To allow the remote access,
we must provide the permission for firewall configuration.
6
extreme conditions. The conditions may vary from the loss of a specific key to the
destruction of resources but the manager of business must prepare for any condition
and follow guidelines to run business (Campbell, 2016).
As the hybrid cloud adopt the advantages of both public and private cloud, the business
organization can deploy the critical applications on the private cloud and less complex
applications on public cloud. Private cloud provides enhanced security whereas the
public cloud provides the cheap business continuity plan. Private cloud encrypts the
data through passwords and firewall can prevent the unauthorized data packets to
communicate in the network of business. It increases the cost of business. Data security
and recovery ensures the business continuity and hence placed in the private cloud.
To prepare the business continuity plan below information must be ensured:
Data must be kept in form of backup which impacts on business analytics and risk
assessment.
Data recovery point must be maintained
The contact list of all the employees, stakeholders, contractors and suppliers must be
maintained.
The steps to be followed in case of problems must be kept.
Remote server administration and Resource Management
Remote server administration is a component of windows server which is used to manage remote
resources of network. It was firstly introduced in Windows Server 2008 R2. With the help of RSAT the
administrators can run special programs called snap-ins which can control the applications of other
computers. This software also includes Hyper-V management and updates related with clusters. This
software is compatible with every version of Windows OS. In hybrid cloud, the network security is the
most essential part of strategy and Firewall is by default the most important tool of RSAT. By default in
RSAT, this feature is on. We recommend the Windows 2008 Server core edition for the hybrid cloud of
regional gardens as it can be manageable in many ways through MMC (Khanin, 2008):
Server roles: if this option is installed, the ports are opened by default and there is no need of extra
configuration. If MMC snap-in is installed for a specific role then the user can directly control the role at
server core.
Domain joined: Till the domain is created, the settings are changed and the remote management is
possible.
Workgroup server: The latest scenario, which tests windows 2008 server. To allow the remote access,
we must provide the permission for firewall configuration.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

In order to access cloud resources, SLA is must in between cloud service provider and cloud consumer. It
ensures the quality of services. It is a detailed explanation of various points in form of checklist, which
contains almost all the parameters to define a satisfactory service level. In case of IaaS and PaaS the
client can use the hardware and software resources, the client can change the settings regarding the OS
control, storage location and applications but it does not provide the authorization to client to
administer the cloud. The dynamic nature of cloud is the main cause of interruption in quality of services
which can be manages through SLA.
Main Components of SLA
Some of the advantages of SLA are:
Increases Customer’s satisfaction level
Improved relationship between service provider and consumers
Ensures the level of quality
Enhanced performance
Fault tolerance can be improved
SLA management is an integral process which is done on various levels like:
Level of operation Description
Business level management At business level management the authentication
and authorization parameters are decided and
signed by both the parties service provider and
client
Service level management Following are the main points should be done at
service level management:
SLA creation
Monitoring
Maintenance
Reporting
7
ensures the quality of services. It is a detailed explanation of various points in form of checklist, which
contains almost all the parameters to define a satisfactory service level. In case of IaaS and PaaS the
client can use the hardware and software resources, the client can change the settings regarding the OS
control, storage location and applications but it does not provide the authorization to client to
administer the cloud. The dynamic nature of cloud is the main cause of interruption in quality of services
which can be manages through SLA.
Main Components of SLA
Some of the advantages of SLA are:
Increases Customer’s satisfaction level
Improved relationship between service provider and consumers
Ensures the level of quality
Enhanced performance
Fault tolerance can be improved
SLA management is an integral process which is done on various levels like:
Level of operation Description
Business level management At business level management the authentication
and authorization parameters are decided and
signed by both the parties service provider and
client
Service level management Following are the main points should be done at
service level management:
SLA creation
Monitoring
Maintenance
Reporting
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

assessment
Network level management Network monitoring which can be in form of
active monitoring and passive monitoring
Migrating Email instance to AWS and its issues
With the latest innovation of Microsoft’s Amazon web services, we can easily migrate most of the
applications of public cloud of business organization, covering IT infrastructure, expenses of daily
routine, administrative tools etc. It will increase the performance of applications and provide much
awaited security to applications (Omran, 2017). One of the application which is to be migrated on AWS
is Email instance. If it is done, then accessibility of this application will increase in many folds. The main
advantages of migrating Emails to AWS are:
Automate the process
Minimum bandwidth required
No replicate data present
Speed up the process
Available 24x7
The migration process may include following steps:
Overview of migrating Email on AWs
8
Network level management Network monitoring which can be in form of
active monitoring and passive monitoring
Migrating Email instance to AWS and its issues
With the latest innovation of Microsoft’s Amazon web services, we can easily migrate most of the
applications of public cloud of business organization, covering IT infrastructure, expenses of daily
routine, administrative tools etc. It will increase the performance of applications and provide much
awaited security to applications (Omran, 2017). One of the application which is to be migrated on AWS
is Email instance. If it is done, then accessibility of this application will increase in many folds. The main
advantages of migrating Emails to AWS are:
Automate the process
Minimum bandwidth required
No replicate data present
Speed up the process
Available 24x7
The migration process may include following steps:
Overview of migrating Email on AWs
8

Issues in the AWS migration
Before migrating any application to the cloud, it must be analyzed properly. It is the better approach
that migration should start with the small piece of application. Some other issues which might occur
mean while the process are:
Cloud finance: Basically it depends on the choice of organization, in some cases, the company don’t
want to migrate on premise application to cloud, as it will decrease the overall control of company on to
application. On the other hand some companies prefer cost cutting and they migrate the application to
the cloud (YIGAL, 2016).
Security and Availability issues: It is the main concern in migration process, as in the case of private
cloud, the security will depend on cloud service providers, but it can be achieve through specifying the
rules and guidelines at the time of agreement.
Need Re-hosting or Rebuilding application: Before migrating any application to the cloud, the IT
managers must prepare the data which is to be deployed on AWS. Sometimes the same application can
be redeployed on a totally different hardware configuration it is called as redeploying the application.
References
Ahmed, J. (2017, october 12).
top-5-reasons-go-hybrid-cloud. Retrieved from www.mdsc1.com:
https://www.mdsc1.com/blog/top-5-reasons-go-hybrid-cloud/
Campbell, M. (2016, January 15).
7-hybrid-cloud-backup-and-business-continuity-mistakes. Retrieved
from www.networkcomputing.com: https://www.networkcomputing.com/data-centers/7-
hybrid-cloud-backup-and-business-continuity-mistakes/341570530
JARIWALA, D. (2013, December 16).
3-disadvantages-hybrid-cloud. Retrieved from
www.techstagram.com: https://www.techstagram.com/2013/12/16/3-disadvantages-hybrid-
cloud/
Kaushal, R. (2017, February 20).
deployment-and-implementation-of-hybrid-cloud-for-an-
enterprises.html. Retrieved from blog.calsoftinc.com:
https://blog.calsoftinc.com/2017/02/deployment-and-implementation-of-hybrid-cloud-for-an-
enterprises.html
Khanin, M. (2008, April 27).
configuring-the-firewall-on-server-core-for-remote-management. Retrieved
from itknowledgeexchange.techtarget.com:
https://itknowledgeexchange.techtarget.com/network-administrator/configuring-the-firewall-
on-server-core-for-remote-management/
Morgenthal, J. (2015, April 30).
7-rules-hybrid-cloud. Retrieved from dzone.com:
https://dzone.com/articles/7-rules-hybrid-cloud
Omran, A. (2017, March 14).
aws-server-migration-service-server-migration-to-the-cloud-made-easy.
Retrieved from aws.amazon.com: https://aws.amazon.com/blogs/apn/aws-server-migration-
9
Before migrating any application to the cloud, it must be analyzed properly. It is the better approach
that migration should start with the small piece of application. Some other issues which might occur
mean while the process are:
Cloud finance: Basically it depends on the choice of organization, in some cases, the company don’t
want to migrate on premise application to cloud, as it will decrease the overall control of company on to
application. On the other hand some companies prefer cost cutting and they migrate the application to
the cloud (YIGAL, 2016).
Security and Availability issues: It is the main concern in migration process, as in the case of private
cloud, the security will depend on cloud service providers, but it can be achieve through specifying the
rules and guidelines at the time of agreement.
Need Re-hosting or Rebuilding application: Before migrating any application to the cloud, the IT
managers must prepare the data which is to be deployed on AWS. Sometimes the same application can
be redeployed on a totally different hardware configuration it is called as redeploying the application.
References
Ahmed, J. (2017, october 12).
top-5-reasons-go-hybrid-cloud. Retrieved from www.mdsc1.com:
https://www.mdsc1.com/blog/top-5-reasons-go-hybrid-cloud/
Campbell, M. (2016, January 15).
7-hybrid-cloud-backup-and-business-continuity-mistakes. Retrieved
from www.networkcomputing.com: https://www.networkcomputing.com/data-centers/7-
hybrid-cloud-backup-and-business-continuity-mistakes/341570530
JARIWALA, D. (2013, December 16).
3-disadvantages-hybrid-cloud. Retrieved from
www.techstagram.com: https://www.techstagram.com/2013/12/16/3-disadvantages-hybrid-
cloud/
Kaushal, R. (2017, February 20).
deployment-and-implementation-of-hybrid-cloud-for-an-
enterprises.html. Retrieved from blog.calsoftinc.com:
https://blog.calsoftinc.com/2017/02/deployment-and-implementation-of-hybrid-cloud-for-an-
enterprises.html
Khanin, M. (2008, April 27).
configuring-the-firewall-on-server-core-for-remote-management. Retrieved
from itknowledgeexchange.techtarget.com:
https://itknowledgeexchange.techtarget.com/network-administrator/configuring-the-firewall-
on-server-core-for-remote-management/
Morgenthal, J. (2015, April 30).
7-rules-hybrid-cloud. Retrieved from dzone.com:
https://dzone.com/articles/7-rules-hybrid-cloud
Omran, A. (2017, March 14).
aws-server-migration-service-server-migration-to-the-cloud-made-easy.
Retrieved from aws.amazon.com: https://aws.amazon.com/blogs/apn/aws-server-migration-
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

service-server-migration-to-the-cloud-made-easy/
Shacklett, M. (2016, April 7).
10-hybrid-cloud-risk-areas-that-the-enterprise-must-manage. Retrieved
from www.techrepublic.com: https://www.techrepublic.com/blog/10-things/10-hybrid-cloud-
risk-areas-that-the-enterprise-must-manage/
Shacklett, M. (2016, April 7).
10-hybrid-cloud-risk-areas-that-the-enterprise-must-manage. Retrieved
from www.techrepublic.com: https://www.techrepublic.com/blog/10-things/10-hybrid-cloud-
risk-areas-that-the-enterprise-must-manage/
Tracy, P. (2016, September 22).
hybrid-cloud-iot-tag31-tag99. Retrieved from www.rcrwireless.com:
https://www.rcrwireless.com/20160922/big-data-analytics/hybrid-cloud-iot-tag31-tag99
YIGAL, A. (2016, March 15).
6-key-considerations-migrating-aws. Retrieved from devops.com:
https://devops.com/6-key-considerations-migrating-aws/
10
Shacklett, M. (2016, April 7).
10-hybrid-cloud-risk-areas-that-the-enterprise-must-manage. Retrieved
from www.techrepublic.com: https://www.techrepublic.com/blog/10-things/10-hybrid-cloud-
risk-areas-that-the-enterprise-must-manage/
Shacklett, M. (2016, April 7).
10-hybrid-cloud-risk-areas-that-the-enterprise-must-manage. Retrieved
from www.techrepublic.com: https://www.techrepublic.com/blog/10-things/10-hybrid-cloud-
risk-areas-that-the-enterprise-must-manage/
Tracy, P. (2016, September 22).
hybrid-cloud-iot-tag31-tag99. Retrieved from www.rcrwireless.com:
https://www.rcrwireless.com/20160922/big-data-analytics/hybrid-cloud-iot-tag31-tag99
YIGAL, A. (2016, March 15).
6-key-considerations-migrating-aws. Retrieved from devops.com:
https://devops.com/6-key-considerations-migrating-aws/
10
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





