MITS4004 Research Study 1: Comprehensive ICMP and IP Wireshark Lab
VerifiedAdded on 2023/04/20
|18
|1719
|295
Practical Assignment
AI Summary
This document presents a detailed analysis of ICMP and IP protocols using Wireshark, based on the MITS4004 Research Study 1. The lab report includes experiments with ping and traceroute, examining packet structures, IP addresses, and ICMP types. It covers topics such as ICMP echo requests and replies, IP header analysis, fragmentation, and TTL values. The study provides insights into network communication, packet behavior, and protocol characteristics, supported by captured data and screenshots. The report also answers specific questions related to the observed network traffic and protocol functionalities. Desklib offers a range of similar solved assignments for students.

Running head: DATA COMMUNICATION
Data Communication
Name of the Student:
Name of the University:
Author Note
Data Communication
Name of the Student:
Name of the University:
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
DATA COMMUNICATION
ICMP and Ping
Starting wireshark
Ping on command prompt
DATA COMMUNICATION
ICMP and Ping
Starting wireshark
Ping on command prompt

2
DATA COMMUNICATION
1. What is the IP address of your host? What is the IP address of the destination
host?
The host IP address is 192.168.43.247 and the destination IP address is 143.89.44.246.
2. Why is it that an ICMP packet does not have source and destination port
numbers?
ICMP is a protocol which is designed so that the communication can take place in
between the routers and the hosts with the information gained from the network-layer.
However, this does not interfere with the processes in the application layer. Hence, the ICMP
packet does not have source and destination port numbers.
DATA COMMUNICATION
1. What is the IP address of your host? What is the IP address of the destination
host?
The host IP address is 192.168.43.247 and the destination IP address is 143.89.44.246.
2. Why is it that an ICMP packet does not have source and destination port
numbers?
ICMP is a protocol which is designed so that the communication can take place in
between the routers and the hosts with the information gained from the network-layer.
However, this does not interfere with the processes in the application layer. Hence, the ICMP
packet does not have source and destination port numbers.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
DATA COMMUNICATION
3. Examine one of the ping request packets sent by your host. What are the
ICMP type and code numbers? What other fields does this ICMP packet have?
How many bytes are the checksum, sequence number and identifier fields?
The ICMP type is 8 and the code number is 0. The other fields that the ICMP packet
have are checksum, checksum status, identifier (BE), identifier (LE), sequence number (BE),
sequence number (LE) and data. The checksum is 2 bytes, sequence number is 2 bytes and an
identifier field is of 2 bytes.
DATA COMMUNICATION
3. Examine one of the ping request packets sent by your host. What are the
ICMP type and code numbers? What other fields does this ICMP packet have?
How many bytes are the checksum, sequence number and identifier fields?
The ICMP type is 8 and the code number is 0. The other fields that the ICMP packet
have are checksum, checksum status, identifier (BE), identifier (LE), sequence number (BE),
sequence number (LE) and data. The checksum is 2 bytes, sequence number is 2 bytes and an
identifier field is of 2 bytes.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
DATA COMMUNICATION
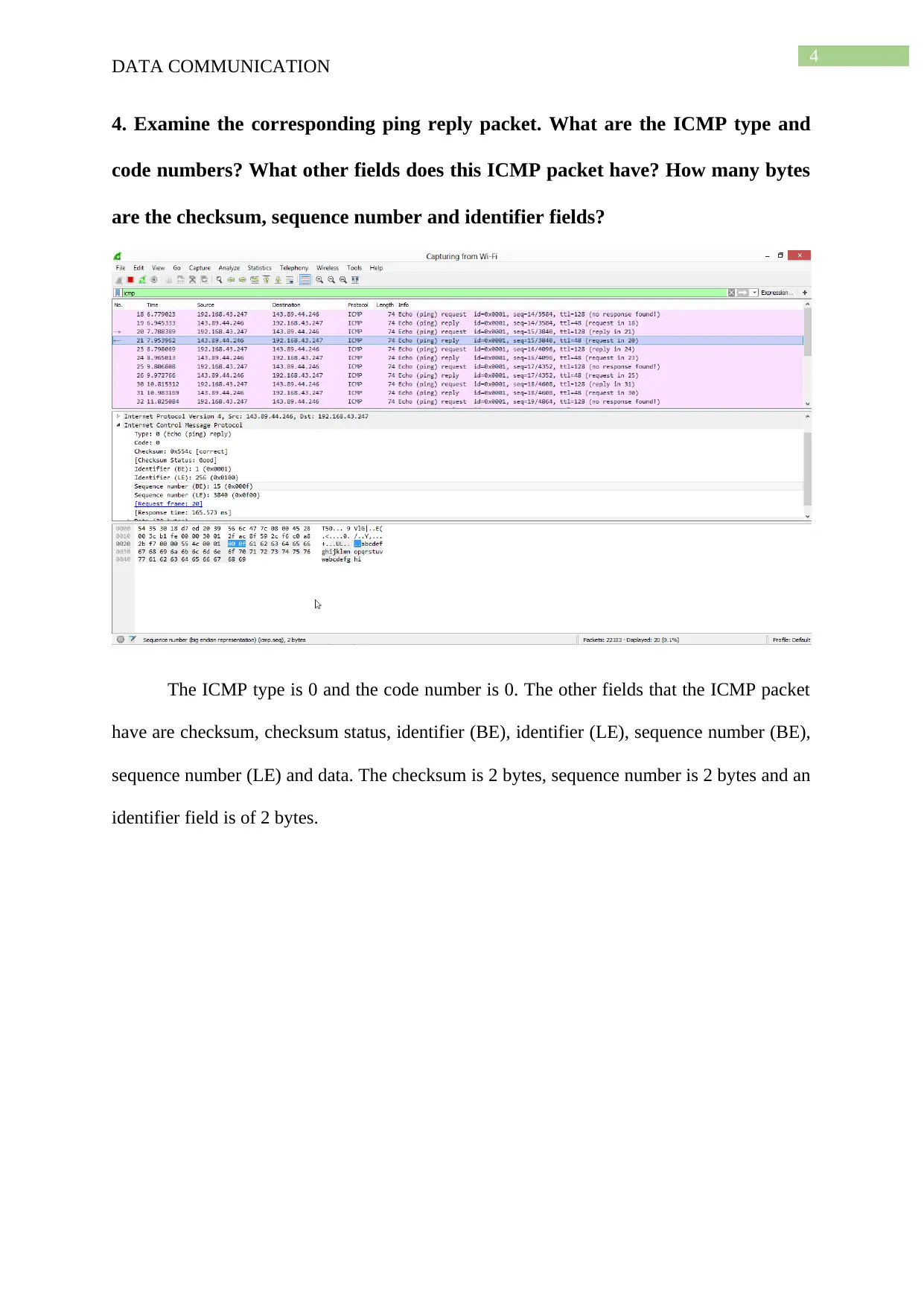
4. Examine the corresponding ping reply packet. What are the ICMP type and
code numbers? What other fields does this ICMP packet have? How many bytes
are the checksum, sequence number and identifier fields?
The ICMP type is 0 and the code number is 0. The other fields that the ICMP packet
have are checksum, checksum status, identifier (BE), identifier (LE), sequence number (BE),
sequence number (LE) and data. The checksum is 2 bytes, sequence number is 2 bytes and an
identifier field is of 2 bytes.
DATA COMMUNICATION
4. Examine the corresponding ping reply packet. What are the ICMP type and
code numbers? What other fields does this ICMP packet have? How many bytes
are the checksum, sequence number and identifier fields?
The ICMP type is 0 and the code number is 0. The other fields that the ICMP packet
have are checksum, checksum status, identifier (BE), identifier (LE), sequence number (BE),
sequence number (LE) and data. The checksum is 2 bytes, sequence number is 2 bytes and an
identifier field is of 2 bytes.

5
DATA COMMUNICATION
ICMP and Traceroute
DATA COMMUNICATION
ICMP and Traceroute
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
DATA COMMUNICATION
DATA COMMUNICATION
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
DATA COMMUNICATION
5. What is the IP address of your host? What is the IP address of the target
destination host?
The IP address of the host is 192.168.43.247. The IP address of the destination host is
128.93.162.84.
6. If ICMP sent UDP packets instead (as in Unix/Linux), would the IP protocol
number still be 01 for the probe packets? If not, what would it be?
The IP protocol number would be 0x11 instead of 01 if ICMP sent UDP packets
instead.
7. Examine the ICMP echo packet in your screenshot. Is this different from the
ICMP ping query packets in the first half of this lab? If yes, how so?
It has been found that the ICMP echo packets are similar to the ICMP ping query
packets which were obtained in the first half of the lab. All the fields identified at the first
half of the lab are same to that of the ICMP echo packets.
DATA COMMUNICATION
5. What is the IP address of your host? What is the IP address of the target
destination host?
The IP address of the host is 192.168.43.247. The IP address of the destination host is
128.93.162.84.
6. If ICMP sent UDP packets instead (as in Unix/Linux), would the IP protocol
number still be 01 for the probe packets? If not, what would it be?
The IP protocol number would be 0x11 instead of 01 if ICMP sent UDP packets
instead.
7. Examine the ICMP echo packet in your screenshot. Is this different from the
ICMP ping query packets in the first half of this lab? If yes, how so?
It has been found that the ICMP echo packets are similar to the ICMP ping query
packets which were obtained in the first half of the lab. All the fields identified at the first
half of the lab are same to that of the ICMP echo packets.

8
DATA COMMUNICATION
8. Examine the ICMP error packet in your screenshot. It has more fields than the
ICMP echo packet. What is included in those fields?
The additional fields in the error packets are the differentiated services field, the time
to live field, flag fields and the header filed. It contains 4 bytes of the error packets.
9. Examine the last three ICMP packets received by the source host. How are
these packets different from the ICMP error packets? Why are they different?
The last three ICMP packets received by the source host are type 0 while the error
packets are of type 8. In addition to this, the ICMP packets received by the host has time to
live 49, however the error packets have a time to live 1.
DATA COMMUNICATION
8. Examine the ICMP error packet in your screenshot. It has more fields than the
ICMP echo packet. What is included in those fields?
The additional fields in the error packets are the differentiated services field, the time
to live field, flag fields and the header filed. It contains 4 bytes of the error packets.
9. Examine the last three ICMP packets received by the source host. How are
these packets different from the ICMP error packets? Why are they different?
The last three ICMP packets received by the source host are type 0 while the error
packets are of type 8. In addition to this, the ICMP packets received by the host has time to
live 49, however the error packets have a time to live 1.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
DATA COMMUNICATION
10. Within the tracert measurements, is there a link whose delay is significantly
longer than others? Refer to the screenshot in Figure 4, is there a link whose
delay is significantly longer than others? On the basis of the router names, can
you guess the location of the two routers on the end of this link?
Yes, there is link in between hop 12 and 13, whose delay is significantly longer than
others. No router names can-not help in determining their locations.
DATA COMMUNICATION
10. Within the tracert measurements, is there a link whose delay is significantly
longer than others? Refer to the screenshot in Figure 4, is there a link whose
delay is significantly longer than others? On the basis of the router names, can
you guess the location of the two routers on the end of this link?
Yes, there is link in between hop 12 and 13, whose delay is significantly longer than
others. No router names can-not help in determining their locations.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
DATA COMMUNICATION
A look at the captured trace
DATA COMMUNICATION
A look at the captured trace

11
DATA COMMUNICATION
DATA COMMUNICATION
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




