Network Analysis Lab: ICMP and IP Protocol Examination (MITS4004)
VerifiedAdded on 2022/12/15
|23
|1613
|478
Practical Assignment
AI Summary
This assignment, a practical lab report for the MITS4004 course, focuses on the analysis of ICMP and IP protocols using Wireshark. The lab is divided into three parts: pinging a website, tracerouting a website, and using PingPlotter. Part A involves pinging a website hosted in Europe and analyzing the ICMP echo request and reply packets, examining fields such as IP addresses, ICMP types and codes, and byte sizes. Part B involves tracerouting a website, exploring ICMP error packets and the differences between them and echo packets, and analyzing delays in the network path. Part C utilizes PingPlotter to trace a website with varying packet sizes, analyzing IP header fields, fragmentation, and the values of fields that change or remain constant across different ICMP messages. The report includes screenshots, explanations, and answers to specific questions about the network traffic, providing a detailed examination of network protocols and packet structures. The assignment concludes with a bibliography of relevant resources.
1 out of 23


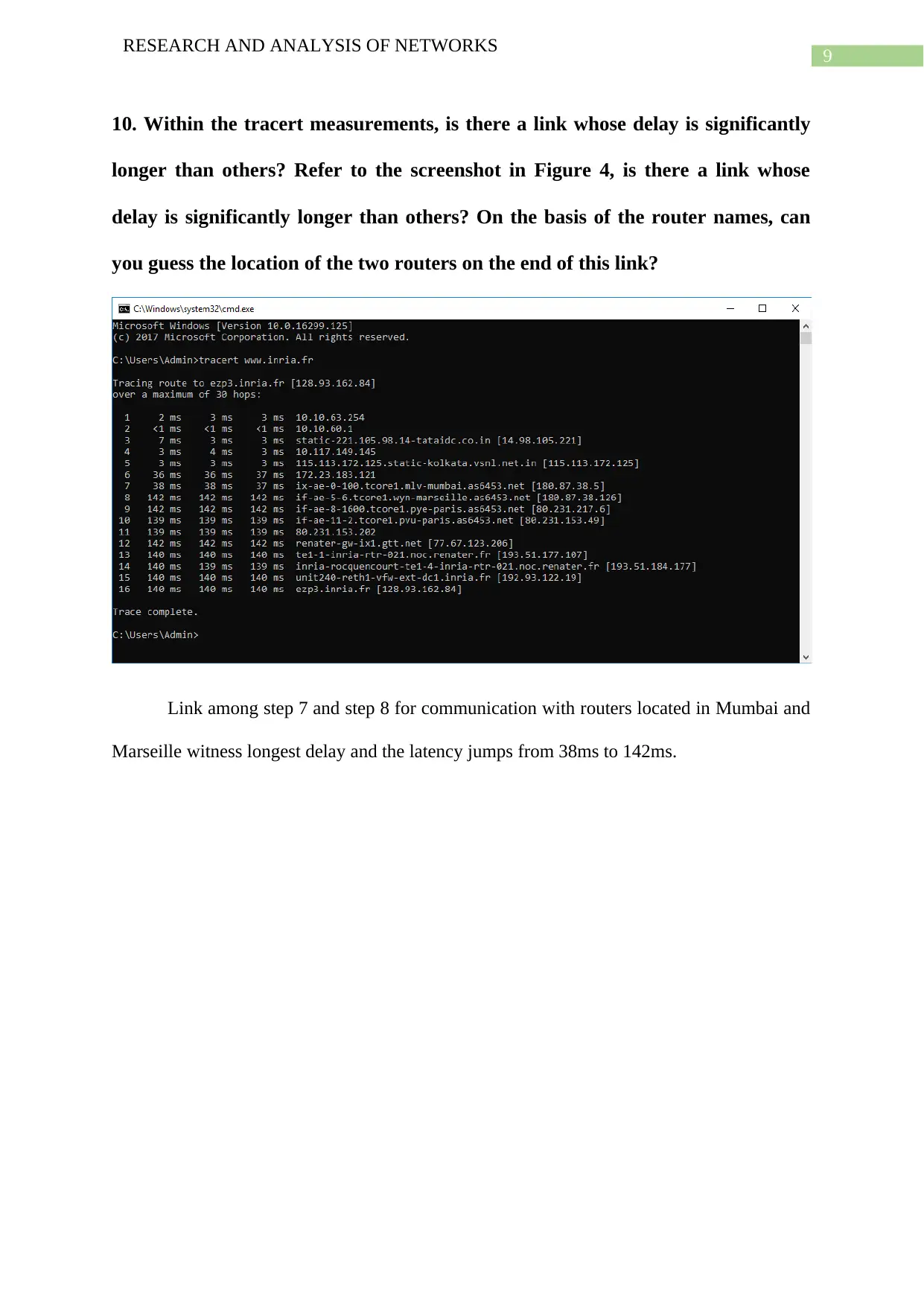
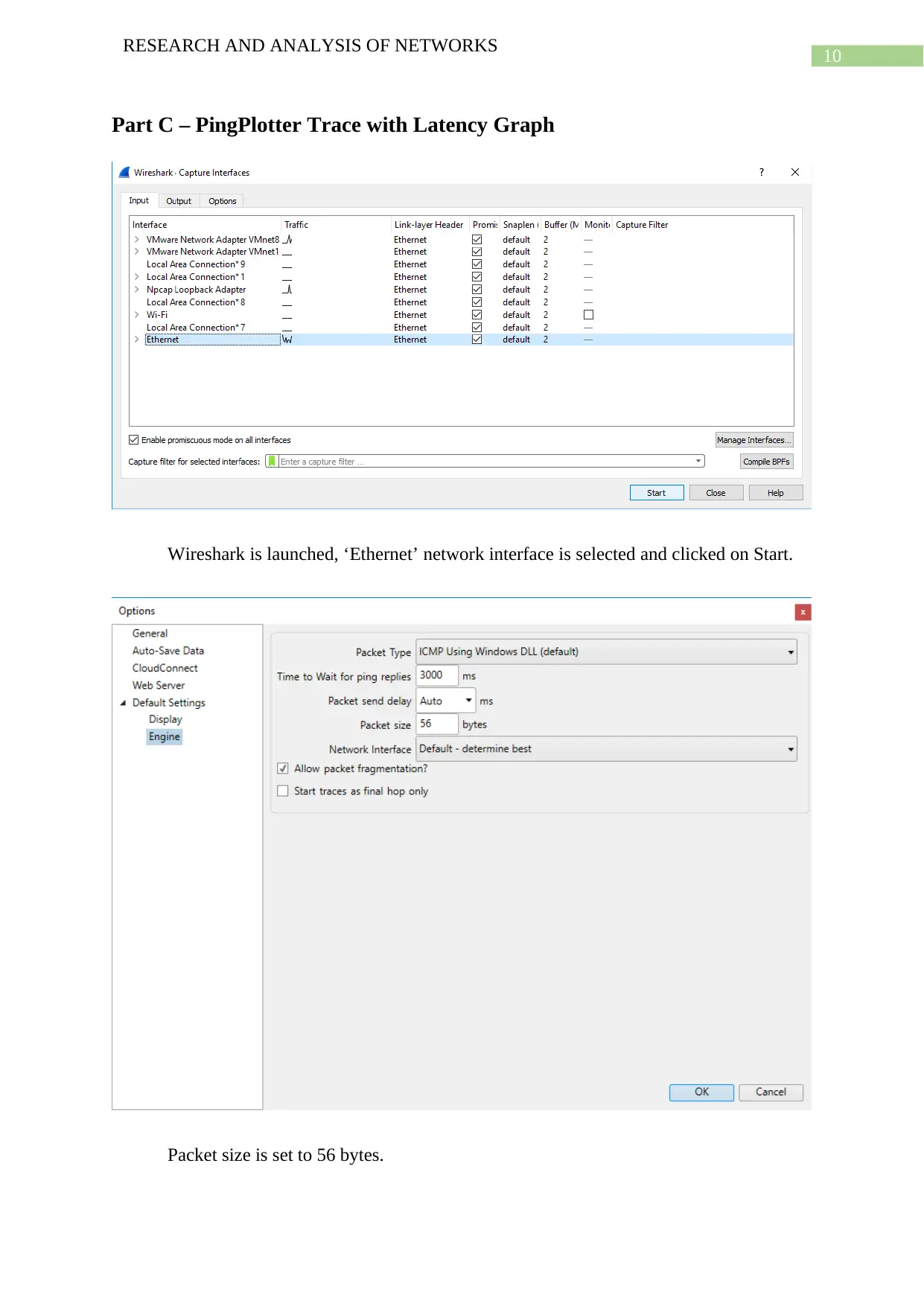
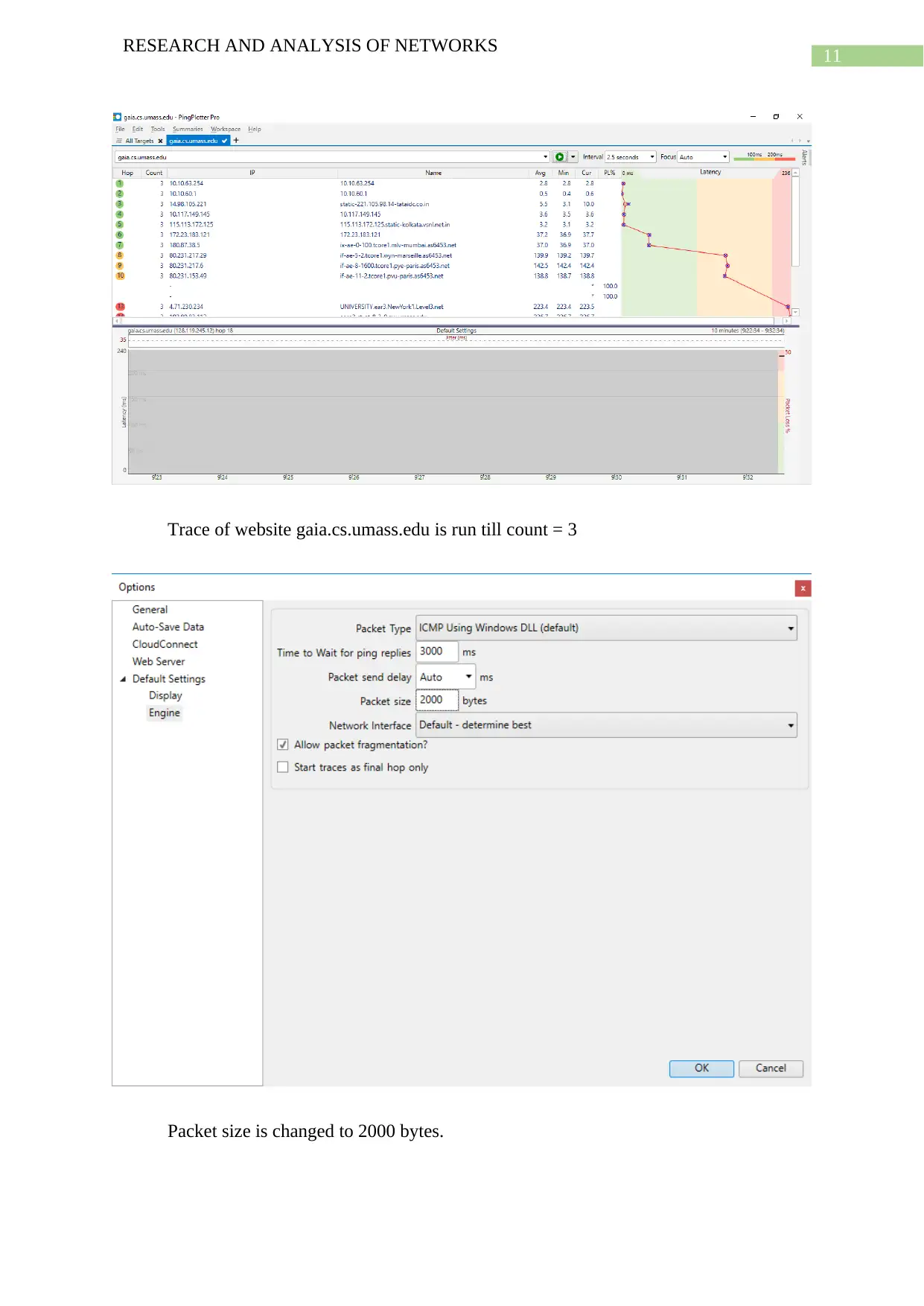





![[object Object]](/_next/static/media/star-bottom.7253800d.svg)