Cloud Computing & ICT Audit for Antique Boutique Operations
VerifiedAdded on 2023/04/25
|43
|8201
|156
Case Study
AI Summary
This case study presents an ICT audit conducted for a small business, Antique Boutique, focusing on critical systems such as cash registers and EFTPOS terminals. The audit identifies major transaction systems, data inputs and outputs, and potential business exposures related to system failures, including the absence of a 'wet weather plan.' It assesses business satisfaction with current systems, reliability issues like EFTPOS disputes, and technical risks such as single points of failure. The audit also evaluates hardware performance, disaster recovery planning, data backup procedures, software heritage, user support, and cost implications. Furthermore, it examines desktop software and office productivity tools, including licensing arrangements, training effectiveness, and the presence of unused software. The findings aim to inform the implementation of cloud computing services to enhance business operations and disaster recovery capabilities. Desklib provides a platform for students to access this and other solved assignments for academic assistance.

Running head: CLOUD COMPUTING
Cloud Computing
Name of the Student
Name of the University
Author’s Note
Cloud Computing
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
CLOUD COMPUTING
Answer to Question 4:
4.a. Reflection and research. Listing four sources for information about cloud computing for
small business:
1.
" Learn Now Publications - Log In ". 2019. Content.Lnonline.Com.Au. Accessed
March 28 2019. https://content.lnonline.com.au/lms/training/item.aspx?iid=115009.
2.
Rittinghouse, John W., and James F. Ransome. Cloud computing: implementation,
management, and security. CRC press, 2016.
3.
Wang, Xiu Li, Li Wang, Zhuming Bi, Yang Yang Li, and Yingcheng Xu. "Cloud
computing in human resource management (HRM) system for small and medium
enterprises (SMEs)." The International Journal of Advanced Manufacturing
Technology 84, no. 1-4 (2016): 485-496.
4.
Khan, Nabeel, and Adil Al-Yasiri. "Identifying cloud security threats to strengthen
cloud computing adoption framework." Procedia Computer Science 94 (2016): 485-
490.
Answer to Question 6:
6.a. ICT Audit for Antique Boutique
ICT Audit: The Antique Boutique
Critical Systems Audit Tick
if
done
Comment (brief)
CLOUD COMPUTING
Answer to Question 4:
4.a. Reflection and research. Listing four sources for information about cloud computing for
small business:
1.
" Learn Now Publications - Log In ". 2019. Content.Lnonline.Com.Au. Accessed
March 28 2019. https://content.lnonline.com.au/lms/training/item.aspx?iid=115009.
2.
Rittinghouse, John W., and James F. Ransome. Cloud computing: implementation,
management, and security. CRC press, 2016.
3.
Wang, Xiu Li, Li Wang, Zhuming Bi, Yang Yang Li, and Yingcheng Xu. "Cloud
computing in human resource management (HRM) system for small and medium
enterprises (SMEs)." The International Journal of Advanced Manufacturing
Technology 84, no. 1-4 (2016): 485-496.
4.
Khan, Nabeel, and Adil Al-Yasiri. "Identifying cloud security threats to strengthen
cloud computing adoption framework." Procedia Computer Science 94 (2016): 485-
490.
Answer to Question 6:
6.a. ICT Audit for Antique Boutique
ICT Audit: The Antique Boutique
Critical Systems Audit Tick
if
done
Comment (brief)

2
CLOUD COMPUTING
Identify:
• The major transaction or information
systems that the organisation relies on.
The internal and external data from
the organization is captured for the
identification of major transaction.
Currently the organization is based on
phone line and electrical power and it
was updated lastly on 2012. They
follow manual transaction processing
voucher and the authorization is
managed with the means of 1800
number acting as a backup for
terminal failing.
Interfaces:
For each identified system, find out:
• What input information it needs and
where it comes from.
The cash flow acts as an input for the
cash register and EFTPOS terminal
for facilitating sales. The information
comes from the customer and emails
coming from Hotmail account.
• What information outputs it supplies
directly to staff.
Manual Transaction Processing
Vouchers are supplied directly to the
staffs.
CLOUD COMPUTING
Identify:
• The major transaction or information
systems that the organisation relies on.
The internal and external data from
the organization is captured for the
identification of major transaction.
Currently the organization is based on
phone line and electrical power and it
was updated lastly on 2012. They
follow manual transaction processing
voucher and the authorization is
managed with the means of 1800
number acting as a backup for
terminal failing.
Interfaces:
For each identified system, find out:
• What input information it needs and
where it comes from.
The cash flow acts as an input for the
cash register and EFTPOS terminal
for facilitating sales. The information
comes from the customer and emails
coming from Hotmail account.
• What information outputs it supplies
directly to staff.
Manual Transaction Processing
Vouchers are supplied directly to the
staffs.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
CLOUD COMPUTING
• What information, if any, it provides as
inputs to other information systems.
The Manual Transaction processing
are authorised using 1800 number and
can be used as a backup for failing of
terminal.
Business exposures:
• For each, identify the business processes
which stop if the system stops.
The exchange of the currency would
be stopped if the system stops.
• Find out if the business has a ‘wet
weather plan’ enabling it to operate at a
basic level in the event of failure of any
critical system.
The business have no Wet Weather
Plan and it is not prepared for
handling any case of event failure.
There are no power backup or
secondary ISP involved in the
business.
Business satisfaction:
• Ask around to gauge the mood of the
people in the organisation about how
well each critical system is ‘bedded in’
and how well it fulfils business needs.
A stakeholder meeting is needed to be
arranged for analysing the mood of
the people working in the
organization and their satisfaction
level is needed to be analysed.
Reliability:
• Find out about the history of failures, if
any, of each critical system and thereby
obtain a picture of overall reliability.
The EFTPOS are consider as reliable
but sometimes it faced bank disputes
regarding accepting cards. Reliable
CLOUD COMPUTING
• What information, if any, it provides as
inputs to other information systems.
The Manual Transaction processing
are authorised using 1800 number and
can be used as a backup for failing of
terminal.
Business exposures:
• For each, identify the business processes
which stop if the system stops.
The exchange of the currency would
be stopped if the system stops.
• Find out if the business has a ‘wet
weather plan’ enabling it to operate at a
basic level in the event of failure of any
critical system.
The business have no Wet Weather
Plan and it is not prepared for
handling any case of event failure.
There are no power backup or
secondary ISP involved in the
business.
Business satisfaction:
• Ask around to gauge the mood of the
people in the organisation about how
well each critical system is ‘bedded in’
and how well it fulfils business needs.
A stakeholder meeting is needed to be
arranged for analysing the mood of
the people working in the
organization and their satisfaction
level is needed to be analysed.
Reliability:
• Find out about the history of failures, if
any, of each critical system and thereby
obtain a picture of overall reliability.
The EFTPOS are consider as reliable
but sometimes it faced bank disputes
regarding accepting cards. Reliable
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
CLOUD COMPUTING
alternate payment methods are needed
to be available for increasing the
overall reliability.
Technical risks:
• Identify any critical dependencies and
single points of failure for each system.
That includes big things like what happens
if a main computer or server fails, and little
things like whether kicking a plug out
could stop the system entirely.
If the main server fails the whole cash
register system collapses and thus it is
needed to create a backup server for
eliminating the risk of downtime. The
risk of potential fraud by the cashiers
are needed to be monitored and
mistakes are need to be avoided.
Hardware and performance:
• Identify the hardware the system runs on,
and whether there is anything special about
its brand or configuration that makes it
precisely right for its job.
There are 5 computers with each of
the managers that are used in the
business. The hardware is 9 years old
and have needs to be replaced for
improving the performance of the
employees and supporting the latest
version of software. There are also 5
network printers for the management
of printing jobs, one for each store.
The printer is HP LaserJet Pro MFP
M402n network printer and precisely
CLOUD COMPUTING
alternate payment methods are needed
to be available for increasing the
overall reliability.
Technical risks:
• Identify any critical dependencies and
single points of failure for each system.
That includes big things like what happens
if a main computer or server fails, and little
things like whether kicking a plug out
could stop the system entirely.
If the main server fails the whole cash
register system collapses and thus it is
needed to create a backup server for
eliminating the risk of downtime. The
risk of potential fraud by the cashiers
are needed to be monitored and
mistakes are need to be avoided.
Hardware and performance:
• Identify the hardware the system runs on,
and whether there is anything special about
its brand or configuration that makes it
precisely right for its job.
There are 5 computers with each of
the managers that are used in the
business. The hardware is 9 years old
and have needs to be replaced for
improving the performance of the
employees and supporting the latest
version of software. There are also 5
network printers for the management
of printing jobs, one for each store.
The printer is HP LaserJet Pro MFP
M402n network printer and precisely

5
CLOUD COMPUTING
right for the job.
• At the same time, ask around to gauge the
system’s response time, and whether it is
performing well enough.
The response of the peripheral
devices are needed to be analysed for
the measurement of the performance
of the system and improvement of the
local area wiring and configuration.
Disaster planning:
• Identify the disaster recovery plan and
process that will swing into action to repair
the situation if/when the system does fail.
The current data are backed up in
portable hard drives before closing
any of the application and another
backup is taken at the end of the day.
The recovery plan can be used for
repairing the situation if any failure
occurs in the current system.
• At the same time, identify who the
critical people are who would coordinate
that type of recovery.
Their input will be useful later, when
considering how cloud computing might
assist in disaster recovery.
The network support team and the
account manager is responsible of
handling the recovery situation and
input the data back to the system after
recovery.
The backup of the data can be stored
as archive in the cloud platform such
that it can help in assisting the
disaster recovery situation.
CLOUD COMPUTING
right for the job.
• At the same time, ask around to gauge the
system’s response time, and whether it is
performing well enough.
The response of the peripheral
devices are needed to be analysed for
the measurement of the performance
of the system and improvement of the
local area wiring and configuration.
Disaster planning:
• Identify the disaster recovery plan and
process that will swing into action to repair
the situation if/when the system does fail.
The current data are backed up in
portable hard drives before closing
any of the application and another
backup is taken at the end of the day.
The recovery plan can be used for
repairing the situation if any failure
occurs in the current system.
• At the same time, identify who the
critical people are who would coordinate
that type of recovery.
Their input will be useful later, when
considering how cloud computing might
assist in disaster recovery.
The network support team and the
account manager is responsible of
handling the recovery situation and
input the data back to the system after
recovery.
The backup of the data can be stored
as archive in the cloud platform such
that it can help in assisting the
disaster recovery situation.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
CLOUD COMPUTING
Backups:
• Find out how and how often data on the
system gets backed-up and where data
copies are kept.
The data gets backed up in the
portable hard drive by the bookkeeper
each time before closing a program
and the original file is left on the
system.
Software heritage:
• Find out who is the application software
supplier of this system; whether it is a
commercially-sourced system from a well-
respected supplier and subject to
maintenance contract support, or whether it
is written and maintained in-house.
Microsoft Office and MYOB is the
supplier of application software and it
is a commercially sourced system that
is designed for the small scale
business. It can be used for updating
conveniently and easily offering
different feature and options in the
business for the improvement of
customer satisfaction.
User support:
• Find out how new users get trained on the
system and what the help-desk support
arrangements are.
The new users are trained on the
system by providing the a
presentation and engaging them with
the existing employees. The can also
check the manual book for
understanding the working of the
CLOUD COMPUTING
Backups:
• Find out how and how often data on the
system gets backed-up and where data
copies are kept.
The data gets backed up in the
portable hard drive by the bookkeeper
each time before closing a program
and the original file is left on the
system.
Software heritage:
• Find out who is the application software
supplier of this system; whether it is a
commercially-sourced system from a well-
respected supplier and subject to
maintenance contract support, or whether it
is written and maintained in-house.
Microsoft Office and MYOB is the
supplier of application software and it
is a commercially sourced system that
is designed for the small scale
business. It can be used for updating
conveniently and easily offering
different feature and options in the
business for the improvement of
customer satisfaction.
User support:
• Find out how new users get trained on the
system and what the help-desk support
arrangements are.
The new users are trained on the
system by providing the a
presentation and engaging them with
the existing employees. The can also
check the manual book for
understanding the working of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
CLOUD COMPUTING
system.
Cost implications:
• Find out how much money was spent
putting this system in, and also its annual
ongoing cost.
For putting in Microsoft Office Suite
$296 is spent for a license of 5
terminal and for MYOB and initial
cost of $1195.00 is spent. There are
no annual going cost.
• Estimate costs to the organisation for
each hour, or day, if this system is out-of-
action.
The cost to the organization for an
hour or day if the system is down is
minimum $100 since more employees
are needed for handling the customer
request and manually recording the
transactions.
Management mood:
• If you can, get a sense of senior
management’s overall mood about this
system.
The senior management would be
happy with the implementation of the
system since it is simplified
technology and helps in smooth
running the business.
CLOUD COMPUTING
system.
Cost implications:
• Find out how much money was spent
putting this system in, and also its annual
ongoing cost.
For putting in Microsoft Office Suite
$296 is spent for a license of 5
terminal and for MYOB and initial
cost of $1195.00 is spent. There are
no annual going cost.
• Estimate costs to the organisation for
each hour, or day, if this system is out-of-
action.
The cost to the organization for an
hour or day if the system is down is
minimum $100 since more employees
are needed for handling the customer
request and manually recording the
transactions.
Management mood:
• If you can, get a sense of senior
management’s overall mood about this
system.
The senior management would be
happy with the implementation of the
system since it is simplified
technology and helps in smooth
running the business.
8
CLOUD COMPUTING
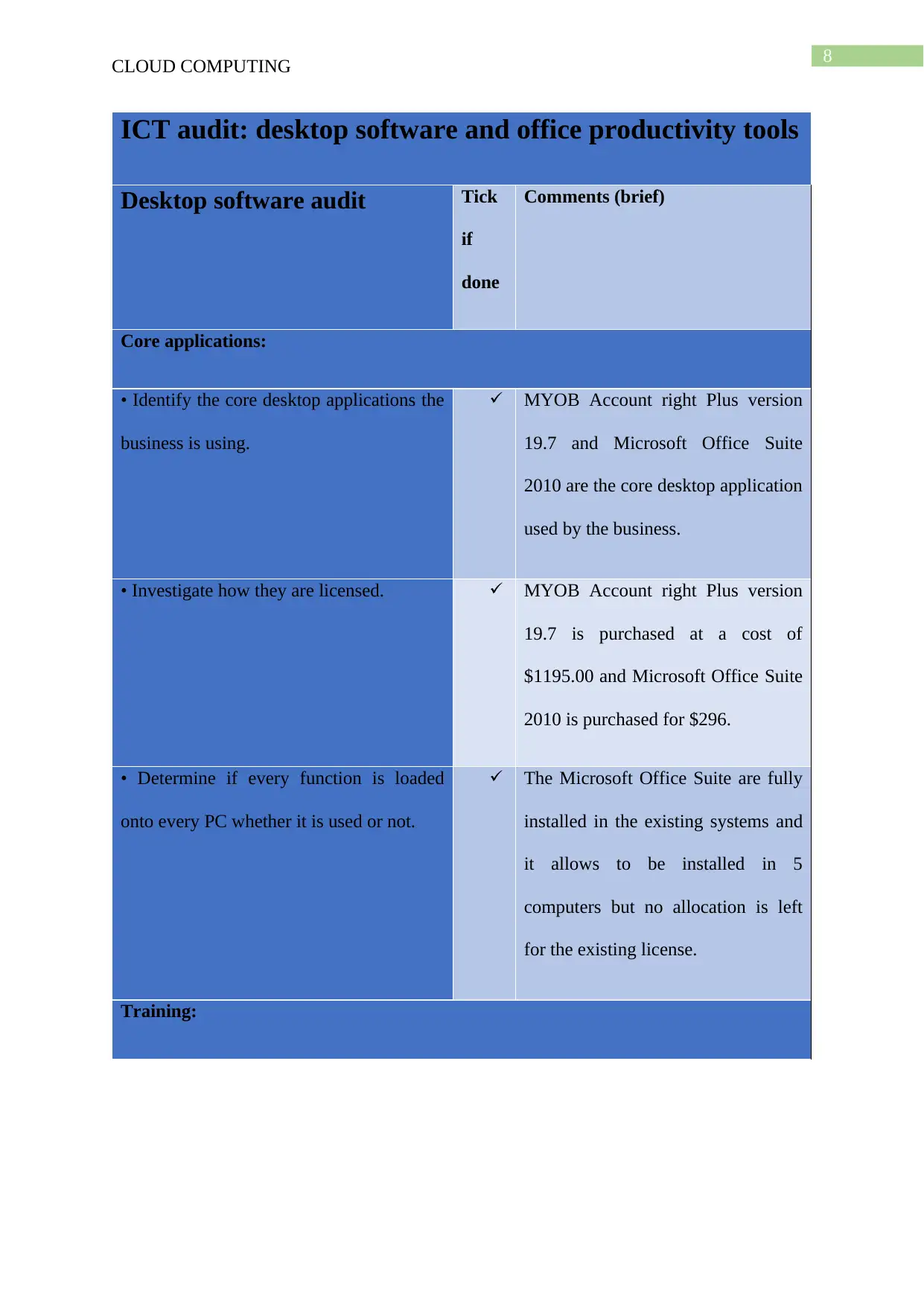
ICT audit: desktop software and office productivity tools
Desktop software audit Tick
if
done
Comments (brief)
Core applications:
• Identify the core desktop applications the
business is using.
MYOB Account right Plus version
19.7 and Microsoft Office Suite
2010 are the core desktop application
used by the business.
• Investigate how they are licensed. MYOB Account right Plus version
19.7 is purchased at a cost of
$1195.00 and Microsoft Office Suite
2010 is purchased for $296.
• Determine if every function is loaded
onto every PC whether it is used or not.
The Microsoft Office Suite are fully
installed in the existing systems and
it allows to be installed in 5
computers but no allocation is left
for the existing license.
Training:
CLOUD COMPUTING
ICT audit: desktop software and office productivity tools
Desktop software audit Tick
if
done
Comments (brief)
Core applications:
• Identify the core desktop applications the
business is using.
MYOB Account right Plus version
19.7 and Microsoft Office Suite
2010 are the core desktop application
used by the business.
• Investigate how they are licensed. MYOB Account right Plus version
19.7 is purchased at a cost of
$1195.00 and Microsoft Office Suite
2010 is purchased for $296.
• Determine if every function is loaded
onto every PC whether it is used or not.
The Microsoft Office Suite are fully
installed in the existing systems and
it allows to be installed in 5
computers but no allocation is left
for the existing license.
Training:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
CLOUD COMPUTING
• Find out who trains users in, and supports
their ongoing use of, the desktop
application software.
The existing employees trains and
support each other for using the
programs.
• Make an assessment of how effective and
efficient the software support in the
business seems to be.
The assistance of the employees is an
efficient and effective approach
seemed in the business.
Version issues:
• Find out if there are there any instances
where different versions of desktop
software are used and for what reason.
There is no instance where different
version of desktop software is used.
Document storage protocols:
• Investigate the organisation’s policies for
documents to be saved to shared servers.
The normal documents can be saved
in the shared servers but it should not
contain the sensitive files because it
can be misused by any third party
user to cause harm for the company.
• Find out if there are examples where
users store their own documents on their
own PC drives and if so, investigate the
reasons for that.
A separate drive is should be
allocated to the user for storing the
files because it can be backed up
easily without backing the system
files.
Planning for new desktop tools:
CLOUD COMPUTING
• Find out who trains users in, and supports
their ongoing use of, the desktop
application software.
The existing employees trains and
support each other for using the
programs.
• Make an assessment of how effective and
efficient the software support in the
business seems to be.
The assistance of the employees is an
efficient and effective approach
seemed in the business.
Version issues:
• Find out if there are there any instances
where different versions of desktop
software are used and for what reason.
There is no instance where different
version of desktop software is used.
Document storage protocols:
• Investigate the organisation’s policies for
documents to be saved to shared servers.
The normal documents can be saved
in the shared servers but it should not
contain the sensitive files because it
can be misused by any third party
user to cause harm for the company.
• Find out if there are examples where
users store their own documents on their
own PC drives and if so, investigate the
reasons for that.
A separate drive is should be
allocated to the user for storing the
files because it can be backed up
easily without backing the system
files.
Planning for new desktop tools:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
CLOUD COMPUTING
• Find out if there is any formal business
process by which new desktop application
software gets identified, trialled and
purchased, and who manages that.
The utilization of excel and MYOB
AccountRight Plus Version 19.7 by
the book keeper is recognized
because the bookkeeper produces
quarterly reports in MYOB and
stores the data in excel for creating
charts and displaying it to Alvin.
• At the same time, find out if there is
anything new in the planning pipeline right
now in this regard, and why.
ALVIN is looking for upgrading the
current internet plan with an addition
of $25extra per month.
Rogue applications:
• Keep a look-out for examples where
application software has been introduced
onto a PC that doesn’t appear to be part of
the overall ICT plan. If individual users
have done this, ask them why, and see if
you can identify net efficiency gains, or
losses, from them having done so.
The purchase of MYOB does not
appears a part of the overall ICT plan
because the software is not used
inefficiently where as manual ledgers
are used for entering the payroll
amount in MYOB.
Licensing regime:
CLOUD COMPUTING
• Find out if there is any formal business
process by which new desktop application
software gets identified, trialled and
purchased, and who manages that.
The utilization of excel and MYOB
AccountRight Plus Version 19.7 by
the book keeper is recognized
because the bookkeeper produces
quarterly reports in MYOB and
stores the data in excel for creating
charts and displaying it to Alvin.
• At the same time, find out if there is
anything new in the planning pipeline right
now in this regard, and why.
ALVIN is looking for upgrading the
current internet plan with an addition
of $25extra per month.
Rogue applications:
• Keep a look-out for examples where
application software has been introduced
onto a PC that doesn’t appear to be part of
the overall ICT plan. If individual users
have done this, ask them why, and see if
you can identify net efficiency gains, or
losses, from them having done so.
The purchase of MYOB does not
appears a part of the overall ICT plan
because the software is not used
inefficiently where as manual ledgers
are used for entering the payroll
amount in MYOB.
Licensing regime:
11
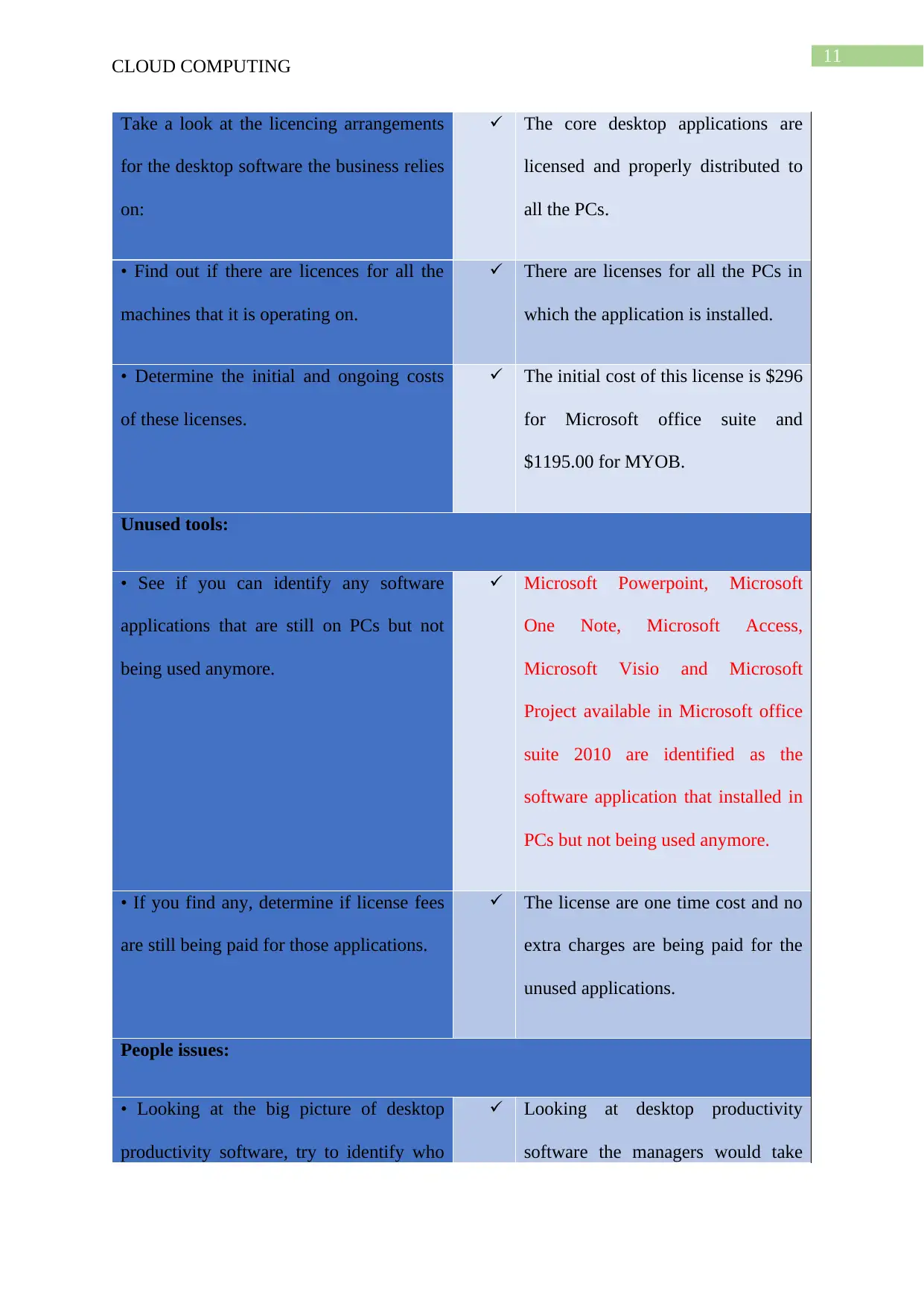
CLOUD COMPUTING
Take a look at the licencing arrangements
for the desktop software the business relies
on:
The core desktop applications are
licensed and properly distributed to
all the PCs.
• Find out if there are licences for all the
machines that it is operating on.
There are licenses for all the PCs in
which the application is installed.
• Determine the initial and ongoing costs
of these licenses.
The initial cost of this license is $296
for Microsoft office suite and
$1195.00 for MYOB.
Unused tools:
• See if you can identify any software
applications that are still on PCs but not
being used anymore.
Microsoft Powerpoint, Microsoft
One Note, Microsoft Access,
Microsoft Visio and Microsoft
Project available in Microsoft office
suite 2010 are identified as the
software application that installed in
PCs but not being used anymore.
• If you find any, determine if license fees
are still being paid for those applications.
The license are one time cost and no
extra charges are being paid for the
unused applications.
People issues:
• Looking at the big picture of desktop
productivity software, try to identify who
Looking at desktop productivity
software the managers would take
CLOUD COMPUTING
Take a look at the licencing arrangements
for the desktop software the business relies
on:
The core desktop applications are
licensed and properly distributed to
all the PCs.
• Find out if there are licences for all the
machines that it is operating on.
There are licenses for all the PCs in
which the application is installed.
• Determine the initial and ongoing costs
of these licenses.
The initial cost of this license is $296
for Microsoft office suite and
$1195.00 for MYOB.
Unused tools:
• See if you can identify any software
applications that are still on PCs but not
being used anymore.
Microsoft Powerpoint, Microsoft
One Note, Microsoft Access,
Microsoft Visio and Microsoft
Project available in Microsoft office
suite 2010 are identified as the
software application that installed in
PCs but not being used anymore.
• If you find any, determine if license fees
are still being paid for those applications.
The license are one time cost and no
extra charges are being paid for the
unused applications.
People issues:
• Looking at the big picture of desktop
productivity software, try to identify who
Looking at desktop productivity
software the managers would take
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 43
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.