ICT Ethical Dilemmas and Cyber Crime: Design Thinking Process Report
VerifiedAdded on 2019/10/31
|15
|3033
|163
Report
AI Summary
This report presents a comprehensive analysis of ICT ethical dilemmas and cybercrime, focusing on the application of design thinking principles to mitigate security risks. The introduction identifies the core problem of ICT security vulnerabilities, including threats like viruses, worms, and Trojans, and acknowledges market competition from technologies such as business intelligence and Big Data tools. The report then details the implementation of design thinking tools like virtualization, journey mapping, value chain analysis, and mind mapping to enhance security. A launch plan, resource plan, and long-term strategies are proposed, alongside recommendations for technical training, encryption, and firewall implementation. The report concludes with a time frame for mitigating ICT managerial issues, emphasizing the importance of a proactive and strategic approach to cybersecurity. This report provides insights into how design thinking processes can be applied in the ICT management field to address ethical dilemmas and cybercrime concerns effectively.

Running head: DESIGN THINKING PROCESS
Design Thinking Process: ICT Ethical Dilemmas and Cyber Crime
Name of the student:
Name of the university:
Design Thinking Process: ICT Ethical Dilemmas and Cyber Crime
Name of the student:
Name of the university:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1DESIGN THINKING PROCESS
Table of Contents
1. Introduction..................................................................................................................................2
1.1 The identified problem..........................................................................................................2
1.2 The market competition of the technology............................................................................4
2. Further implementation of design thinking process tools and technologies used before the
implementation of the launching.....................................................................................................4
3. Launch plan.................................................................................................................................7
4. Resource plan...............................................................................................................................7
5. Long term plan.............................................................................................................................7
6. Recommendation.........................................................................................................................8
7. Time frame or schedule develop for mitigating the ICT managerial level issues.......................8
Conclusion.....................................................................................................................................11
References......................................................................................................................................12
Table of Contents
1. Introduction..................................................................................................................................2
1.1 The identified problem..........................................................................................................2
1.2 The market competition of the technology............................................................................4
2. Further implementation of design thinking process tools and technologies used before the
implementation of the launching.....................................................................................................4
3. Launch plan.................................................................................................................................7
4. Resource plan...............................................................................................................................7
5. Long term plan.............................................................................................................................7
6. Recommendation.........................................................................................................................8
7. Time frame or schedule develop for mitigating the ICT managerial level issues.......................8
Conclusion.....................................................................................................................................11
References......................................................................................................................................12

2DESIGN THINKING PROCESS
1. Introduction
This report depicts the crucial necessity of using different design thinking process tools
and technologies, so that the identified issues could be minimized completely from the digital
platform. For developing this particular project, at the very initial phase a problem has been
identified. After the identification of the problem it is necessary to consider the potential
competitors of the digital field. In order to minimize the identified issues it is very much
necessary to apply proper design thinking tool and technologies. In case of ICT management and
digital field, the biggest issue is the security.
1.1 The identified problem
After analyzing the information and communication technology trends it has been found
that many security level issues and concerns are associated to it. ICT is referred to as a
technology which is required for the processing if different information. Generally, ICT is the
combination of use of the electronic computers, different software application, communication
equipments needed to convert the retrieve, transmit and process. With the help of electronic
system the information can be processed in a well manner including information transmission,
capturing and conversion (Wang & Lu, 2013). The communication system holds broadcasting,
telecommunication and many other programs those help to distribute the system. The computer
systems also include network engineering, robotics, electronics and technical support as well. In
order to increase the security level of the ICT system the management must adopt proper design
thinking approach. With the help of industry level security the information processing will
become much secured than the previous processes (Vaugh & Ryan, 2015). There are different
ways through which the ICT system can be affected such as virus, malware, worm, DOS etc. All
1. Introduction
This report depicts the crucial necessity of using different design thinking process tools
and technologies, so that the identified issues could be minimized completely from the digital
platform. For developing this particular project, at the very initial phase a problem has been
identified. After the identification of the problem it is necessary to consider the potential
competitors of the digital field. In order to minimize the identified issues it is very much
necessary to apply proper design thinking tool and technologies. In case of ICT management and
digital field, the biggest issue is the security.
1.1 The identified problem
After analyzing the information and communication technology trends it has been found
that many security level issues and concerns are associated to it. ICT is referred to as a
technology which is required for the processing if different information. Generally, ICT is the
combination of use of the electronic computers, different software application, communication
equipments needed to convert the retrieve, transmit and process. With the help of electronic
system the information can be processed in a well manner including information transmission,
capturing and conversion (Wang & Lu, 2013). The communication system holds broadcasting,
telecommunication and many other programs those help to distribute the system. The computer
systems also include network engineering, robotics, electronics and technical support as well. In
order to increase the security level of the ICT system the management must adopt proper design
thinking approach. With the help of industry level security the information processing will
become much secured than the previous processes (Vaugh & Ryan, 2015). There are different
ways through which the ICT system can be affected such as virus, malware, worm, DOS etc. All
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3DESIGN THINKING PROCESS
of these security level threats affected the general information flow approach, In order to
mitigate the issues it is very much necessary to dope proper design thinking approach (Suh et al.,
2014). The ICT security level issues are as follows:
Virus: Computer virus is a malware that propagates through making copy of it. As the
copies inserted within the system it might corrupt all the preliminarily stored files and data as
well. The computer virus is designed as an amusement or slight annoyance. However, the virus
could play active roles only if the device gets started and if the devices are switched off then that
time the virus cannot replicate itself (Ben-Asher & Gonzalez, 2015). Virus could affect an entire
system and security from the virus attack is not at all easy job. Virus has the ability to interrupt
the generally data flow by simply destroying the back up as well as stored data those are stored
in the data server. As the business is getting increased in according to that the number of data or
information are also getting increased (Cavelty, 2014). As, management of those data are
becoming much difficult thus data management techniques are inventing. In order to
management those data properly it is necessary to adopt proper data management technique or
tools.
Worm: Computer worms are referred to as the function that has be ability to replicate
itself through copying the functionalities. The affect of the parent worm and its replicates are
similar in nature. Once a file gets infected it becomes able to spread the same throughout. Social
engineering is referred to as a process, through which a target system can transmit the harms
(Kwon, Liu & Hwang, 2013). With the vulnerability in the system takes different advantages of
file transmission and information transport feature as well.
of these security level threats affected the general information flow approach, In order to
mitigate the issues it is very much necessary to dope proper design thinking approach (Suh et al.,
2014). The ICT security level issues are as follows:
Virus: Computer virus is a malware that propagates through making copy of it. As the
copies inserted within the system it might corrupt all the preliminarily stored files and data as
well. The computer virus is designed as an amusement or slight annoyance. However, the virus
could play active roles only if the device gets started and if the devices are switched off then that
time the virus cannot replicate itself (Ben-Asher & Gonzalez, 2015). Virus could affect an entire
system and security from the virus attack is not at all easy job. Virus has the ability to interrupt
the generally data flow by simply destroying the back up as well as stored data those are stored
in the data server. As the business is getting increased in according to that the number of data or
information are also getting increased (Cavelty, 2014). As, management of those data are
becoming much difficult thus data management techniques are inventing. In order to
management those data properly it is necessary to adopt proper data management technique or
tools.
Worm: Computer worms are referred to as the function that has be ability to replicate
itself through copying the functionalities. The affect of the parent worm and its replicates are
similar in nature. Once a file gets infected it becomes able to spread the same throughout. Social
engineering is referred to as a process, through which a target system can transmit the harms
(Kwon, Liu & Hwang, 2013). With the vulnerability in the system takes different advantages of
file transmission and information transport feature as well.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4DESIGN THINKING PROCESS
Trojan: Trojan is another virus which is basically a segment of software that looks
legitimate. It does not have the ability to make their replica and at the same time it cannot even
infect other files also (Pan et al., 2017). With the user interaction the Trojan virus could make
their replication. Again if the infected email or files are downloaded by the other users then that
time the other user’s device can get infected in the similar way.
1.2 The market competition of the technology
Information and Communication Technology (ICT) is referred to as one of the latest
technologies that are widely used by most of the medium to large business organizations. While
analyzing the details of this advanced technology it has been found that all other technologies
such as business intelligence, Big Data tool, and Information system are the biggest competitor
to the system (Sommestad, Ekstedt & Holm, 2013). It is easier for the data hackers to hijack data
in ICT system rather than the other technologies. In order to minimize the issues associated to
the security it is necessary to adopt proper design thinking tools and technologies.
2. Further implementation of design thinking process tools and technologies
used before the implementation of the launching
Design thinking process is referred to as a system that combines three different
overlapping spaces such as viability, feasibility and desirability. The time when three of these
perspectives are identified the innovation will increase accordingly (Vaugh & Ryan, 2015). With
the help of the Design Thinking (DT) tool and technique, the interest of the business community
will get increase. Different guidelines and Design Thinking (DT) tools are there those should be
used by the managerial head for minimizing the invention level risks and issues associated to
ICT system (Plattner et al., 2014). The design thinking tools are as follows:
Trojan: Trojan is another virus which is basically a segment of software that looks
legitimate. It does not have the ability to make their replica and at the same time it cannot even
infect other files also (Pan et al., 2017). With the user interaction the Trojan virus could make
their replication. Again if the infected email or files are downloaded by the other users then that
time the other user’s device can get infected in the similar way.
1.2 The market competition of the technology
Information and Communication Technology (ICT) is referred to as one of the latest
technologies that are widely used by most of the medium to large business organizations. While
analyzing the details of this advanced technology it has been found that all other technologies
such as business intelligence, Big Data tool, and Information system are the biggest competitor
to the system (Sommestad, Ekstedt & Holm, 2013). It is easier for the data hackers to hijack data
in ICT system rather than the other technologies. In order to minimize the issues associated to
the security it is necessary to adopt proper design thinking tools and technologies.
2. Further implementation of design thinking process tools and technologies
used before the implementation of the launching
Design thinking process is referred to as a system that combines three different
overlapping spaces such as viability, feasibility and desirability. The time when three of these
perspectives are identified the innovation will increase accordingly (Vaugh & Ryan, 2015). With
the help of the Design Thinking (DT) tool and technique, the interest of the business community
will get increase. Different guidelines and Design Thinking (DT) tools are there those should be
used by the managerial head for minimizing the invention level risks and issues associated to
ICT system (Plattner et al., 2014). The design thinking tools are as follows:

5DESIGN THINKING PROCESS
Virtualization: Virtualization is referred to as a process of visual as well virtual
representation of new innovative thinking approaches to identify and execute the innovative
thoughts. It is not just about the visualization but also the outline developed for the out of box
thinking. With the help of this tool, the system developer will be able to design a completely out
of box approach (Sou, Sandberg & Johansson, 2013). This kind of advanced level thinking
cannot be generated with any kind of training and development program. Proper matchup
between the idea and design is little difficult but still it helps to develop an advanced model.
Journey mapping: Journey mapping is similar to the experience mapping. In order to
minimize the identified design or ICT level issues, it is necessary to develop a journey mapping
considering the project initiation up to the project completion phase (Wang & Lu, 2013). Most of
the times, the consumers feel unable to articulate the objectives of the requirements those have
been identified. Thus, in order to reduce the rate of error it is very much necessary to map the
journey of the system developers.
Value chain analysis: This is another important tool that might be used by the system
developers to examine the way through which the business might interact with the value chain
partners for production, marketing and new offers distributions (Vaugh & Ryan, 2015). In order
to create better vale for the consumers, value chain analysis model can be used by the
management authority. On the other hand, the ability of the competitors (in this case hackers)
intention can also be identified with the help of the value chain analysis.
Mind mapping: With the help of mind mapping, different ideas like security
identification, security analysis ad security development methodologies can be integrated
together; The ICT system developer will be able to integrate all of these ideas properly, through
Virtualization: Virtualization is referred to as a process of visual as well virtual
representation of new innovative thinking approaches to identify and execute the innovative
thoughts. It is not just about the visualization but also the outline developed for the out of box
thinking. With the help of this tool, the system developer will be able to design a completely out
of box approach (Sou, Sandberg & Johansson, 2013). This kind of advanced level thinking
cannot be generated with any kind of training and development program. Proper matchup
between the idea and design is little difficult but still it helps to develop an advanced model.
Journey mapping: Journey mapping is similar to the experience mapping. In order to
minimize the identified design or ICT level issues, it is necessary to develop a journey mapping
considering the project initiation up to the project completion phase (Wang & Lu, 2013). Most of
the times, the consumers feel unable to articulate the objectives of the requirements those have
been identified. Thus, in order to reduce the rate of error it is very much necessary to map the
journey of the system developers.
Value chain analysis: This is another important tool that might be used by the system
developers to examine the way through which the business might interact with the value chain
partners for production, marketing and new offers distributions (Vaugh & Ryan, 2015). In order
to create better vale for the consumers, value chain analysis model can be used by the
management authority. On the other hand, the ability of the competitors (in this case hackers)
intention can also be identified with the help of the value chain analysis.
Mind mapping: With the help of mind mapping, different ideas like security
identification, security analysis ad security development methodologies can be integrated
together; The ICT system developer will be able to integrate all of these ideas properly, through
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6DESIGN THINKING PROCESS
the help of mind mapping (Howlett, 2014). In order to provide a key design criterion to the
system developers, the mind maps are used for visualizing, structuring and classifying different
creative brain formulations.
Development of rapid concept: As technology is improving day by day thus according
to the changing technologies the developers should consider every advanced ideas. In order to
mitigate the security level issues associated to ICT management system it is necessary to
consider all advanced security design approaches like encryption, firewall (Hahn et al., 2013). If
proper application firewall is used then, none of the unauthorized user will be able to access data
from ICT server.
Assumption of testing: In order to attract new customers advanced business ideas and
experimental resultants should be considered. After the identification of the information the
accurate attractive idea should be figure out.
Rapid prototyping: In order to abstract new ideas with tangible and potential ideas it is
necessary to make rapid prototyping (Cavelty, 2014). Prototype is nothing but a blueprint of the
system. Considering the changing requirements and feedback from the security developers the
prototype should be developed iteratively.
Co-creation with consumers: With the help of this particular tool the managers will be
able to attract more number of consumers and also will be able to keep them engaged to the ICT
system.
Learning launches: With this design tool the key underlying value generating
assumptions of possible growth initiatives can be implemented in the market (Sommestad,
the help of mind mapping (Howlett, 2014). In order to provide a key design criterion to the
system developers, the mind maps are used for visualizing, structuring and classifying different
creative brain formulations.
Development of rapid concept: As technology is improving day by day thus according
to the changing technologies the developers should consider every advanced ideas. In order to
mitigate the security level issues associated to ICT management system it is necessary to
consider all advanced security design approaches like encryption, firewall (Hahn et al., 2013). If
proper application firewall is used then, none of the unauthorized user will be able to access data
from ICT server.
Assumption of testing: In order to attract new customers advanced business ideas and
experimental resultants should be considered. After the identification of the information the
accurate attractive idea should be figure out.
Rapid prototyping: In order to abstract new ideas with tangible and potential ideas it is
necessary to make rapid prototyping (Cavelty, 2014). Prototype is nothing but a blueprint of the
system. Considering the changing requirements and feedback from the security developers the
prototype should be developed iteratively.
Co-creation with consumers: With the help of this particular tool the managers will be
able to attract more number of consumers and also will be able to keep them engaged to the ICT
system.
Learning launches: With this design tool the key underlying value generating
assumptions of possible growth initiatives can be implemented in the market (Sommestad,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7DESIGN THINKING PROCESS
Ekstedt & Holm, 2013). From previous learning and experiences the developers will be able to
invent advanced learning approach.
Storytelling: Rather than just identifying or focusing on the main issues a complete story
is needed to be formulized accurately. With proper security level technologies the ICT issues can
be minimized or even resoled completely.
3. Launch plan
The security services should be available to all the influencers
Brief analysis of the ICT management system
Big bang release should not be expected
Release rolling
Involvement with the business partners
Elimination of the elements of launch those are not helpful for the security
development
4. Resource plan
Understanding the current situation of ICT related issues
Development of strategic objectives for ICT security development
Developing line of action
5. Long term plan
In order to develop long term success plan it is necessary to adopt advanced cyber
security programs that is integrated into the business process, production as well (Plattner et al.,
Ekstedt & Holm, 2013). From previous learning and experiences the developers will be able to
invent advanced learning approach.
Storytelling: Rather than just identifying or focusing on the main issues a complete story
is needed to be formulized accurately. With proper security level technologies the ICT issues can
be minimized or even resoled completely.
3. Launch plan
The security services should be available to all the influencers
Brief analysis of the ICT management system
Big bang release should not be expected
Release rolling
Involvement with the business partners
Elimination of the elements of launch those are not helpful for the security
development
4. Resource plan
Understanding the current situation of ICT related issues
Development of strategic objectives for ICT security development
Developing line of action
5. Long term plan
In order to develop long term success plan it is necessary to adopt advanced cyber
security programs that is integrated into the business process, production as well (Plattner et al.,
8DESIGN THINKING PROCESS
2014. The particular aspects on which, the ICT security developers should concentrate on
different success measures and elements as well.
6. Recommendation
Technical training and development: In order to identify and reduce the ICT issues
proper training and development programs are needed to be arranged by the higher management
authority.
Encryption: In order to keep the data confidentiality encryption and decryption keys are
needed to be adopted so that the unauthorized users could not access data from the server.
Firewall: Application firewall is another security tool that should be used to maintain the
information security.
7. Time frame or schedule develop for mitigating the ICT managerial level
issues
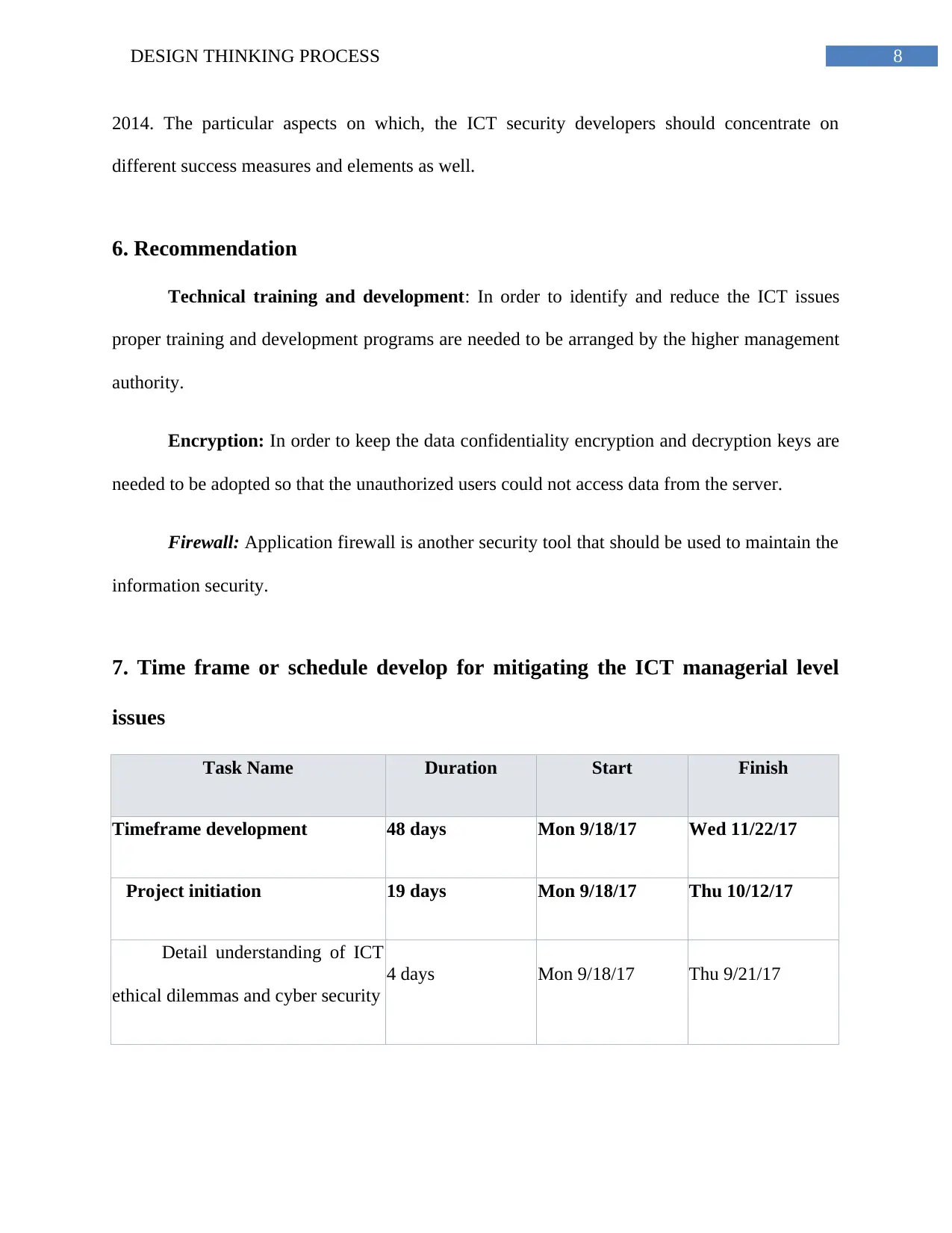
Task Name Duration Start Finish
Timeframe development 48 days Mon 9/18/17 Wed 11/22/17
Project initiation 19 days Mon 9/18/17 Thu 10/12/17
Detail understanding of ICT
ethical dilemmas and cyber security
4 days Mon 9/18/17 Thu 9/21/17
2014. The particular aspects on which, the ICT security developers should concentrate on
different success measures and elements as well.
6. Recommendation
Technical training and development: In order to identify and reduce the ICT issues
proper training and development programs are needed to be arranged by the higher management
authority.
Encryption: In order to keep the data confidentiality encryption and decryption keys are
needed to be adopted so that the unauthorized users could not access data from the server.
Firewall: Application firewall is another security tool that should be used to maintain the
information security.
7. Time frame or schedule develop for mitigating the ICT managerial level
issues
Task Name Duration Start Finish
Timeframe development 48 days Mon 9/18/17 Wed 11/22/17
Project initiation 19 days Mon 9/18/17 Thu 10/12/17
Detail understanding of ICT
ethical dilemmas and cyber security
4 days Mon 9/18/17 Thu 9/21/17
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
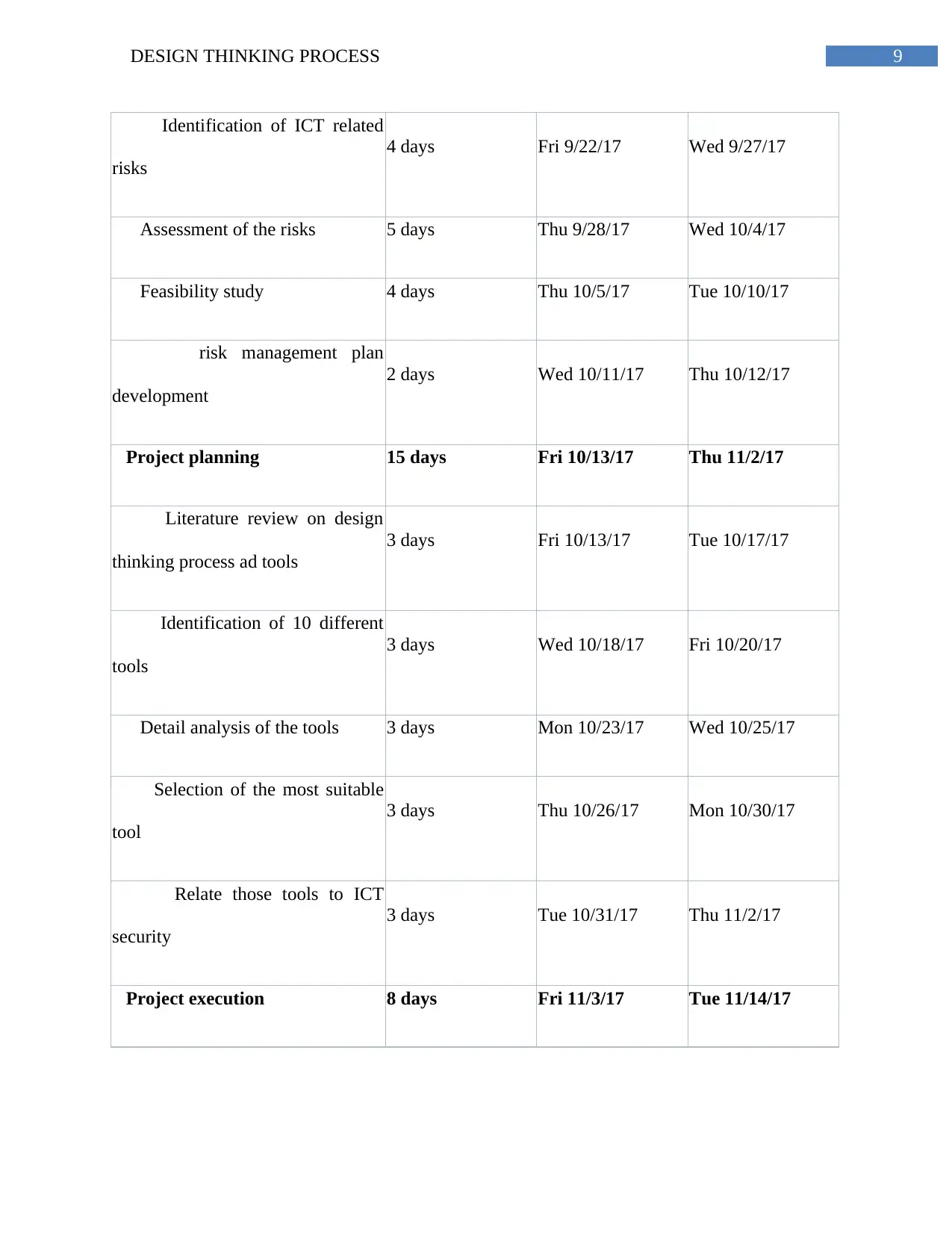
9DESIGN THINKING PROCESS
Identification of ICT related
risks
4 days Fri 9/22/17 Wed 9/27/17
Assessment of the risks 5 days Thu 9/28/17 Wed 10/4/17
Feasibility study 4 days Thu 10/5/17 Tue 10/10/17
risk management plan
development
2 days Wed 10/11/17 Thu 10/12/17
Project planning 15 days Fri 10/13/17 Thu 11/2/17
Literature review on design
thinking process ad tools
3 days Fri 10/13/17 Tue 10/17/17
Identification of 10 different
tools
3 days Wed 10/18/17 Fri 10/20/17
Detail analysis of the tools 3 days Mon 10/23/17 Wed 10/25/17
Selection of the most suitable
tool
3 days Thu 10/26/17 Mon 10/30/17
Relate those tools to ICT
security
3 days Tue 10/31/17 Thu 11/2/17
Project execution 8 days Fri 11/3/17 Tue 11/14/17
Identification of ICT related
risks
4 days Fri 9/22/17 Wed 9/27/17
Assessment of the risks 5 days Thu 9/28/17 Wed 10/4/17
Feasibility study 4 days Thu 10/5/17 Tue 10/10/17
risk management plan
development
2 days Wed 10/11/17 Thu 10/12/17
Project planning 15 days Fri 10/13/17 Thu 11/2/17
Literature review on design
thinking process ad tools
3 days Fri 10/13/17 Tue 10/17/17
Identification of 10 different
tools
3 days Wed 10/18/17 Fri 10/20/17
Detail analysis of the tools 3 days Mon 10/23/17 Wed 10/25/17
Selection of the most suitable
tool
3 days Thu 10/26/17 Mon 10/30/17
Relate those tools to ICT
security
3 days Tue 10/31/17 Thu 11/2/17
Project execution 8 days Fri 11/3/17 Tue 11/14/17
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
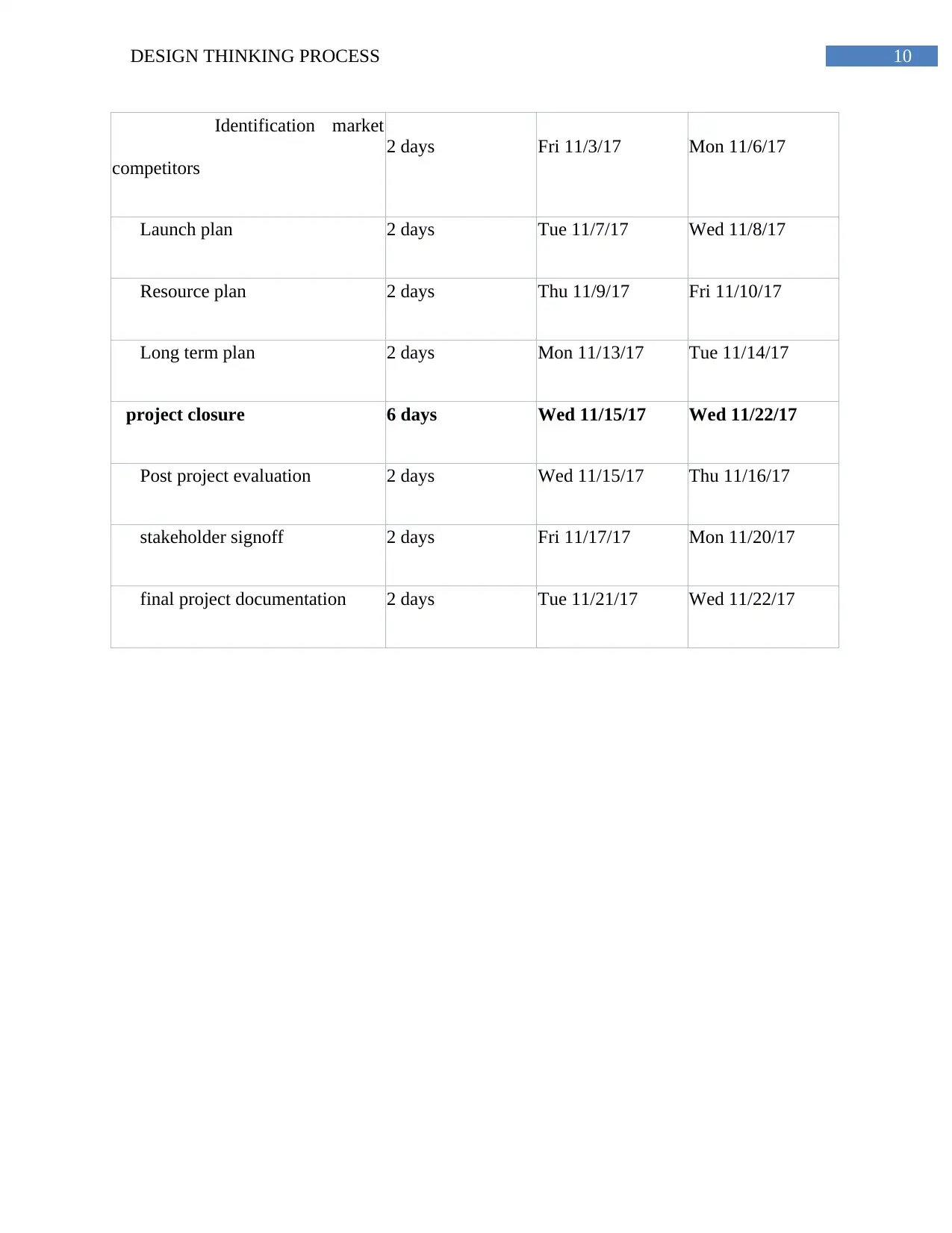
10DESIGN THINKING PROCESS
Identification market
competitors
2 days Fri 11/3/17 Mon 11/6/17
Launch plan 2 days Tue 11/7/17 Wed 11/8/17
Resource plan 2 days Thu 11/9/17 Fri 11/10/17
Long term plan 2 days Mon 11/13/17 Tue 11/14/17
project closure 6 days Wed 11/15/17 Wed 11/22/17
Post project evaluation 2 days Wed 11/15/17 Thu 11/16/17
stakeholder signoff 2 days Fri 11/17/17 Mon 11/20/17
final project documentation 2 days Tue 11/21/17 Wed 11/22/17
Identification market
competitors
2 days Fri 11/3/17 Mon 11/6/17
Launch plan 2 days Tue 11/7/17 Wed 11/8/17
Resource plan 2 days Thu 11/9/17 Fri 11/10/17
Long term plan 2 days Mon 11/13/17 Tue 11/14/17
project closure 6 days Wed 11/15/17 Wed 11/22/17
Post project evaluation 2 days Wed 11/15/17 Thu 11/16/17
stakeholder signoff 2 days Fri 11/17/17 Mon 11/20/17
final project documentation 2 days Tue 11/21/17 Wed 11/22/17
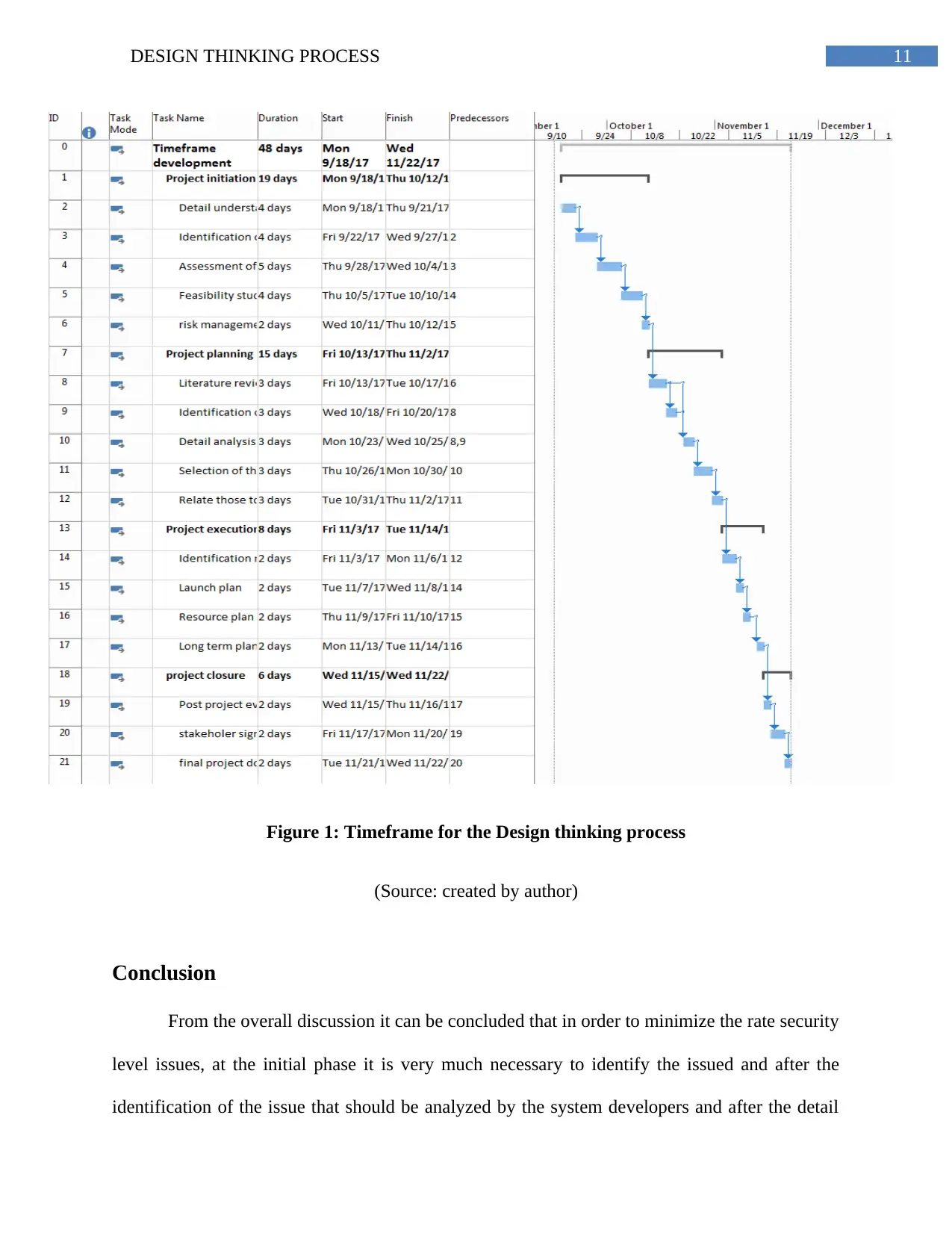
11DESIGN THINKING PROCESS
Figure 1: Timeframe for the Design thinking process
(Source: created by author)
Conclusion
From the overall discussion it can be concluded that in order to minimize the rate security
level issues, at the initial phase it is very much necessary to identify the issued and after the
identification of the issue that should be analyzed by the system developers and after the detail
Figure 1: Timeframe for the Design thinking process
(Source: created by author)
Conclusion
From the overall discussion it can be concluded that in order to minimize the rate security
level issues, at the initial phase it is very much necessary to identify the issued and after the
identification of the issue that should be analyzed by the system developers and after the detail
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




