ICT40118 Cyber Security: Demonstration of Ransomware Presentation
VerifiedAdded on 2022/11/16
|19
|815
|500
Presentation
AI Summary
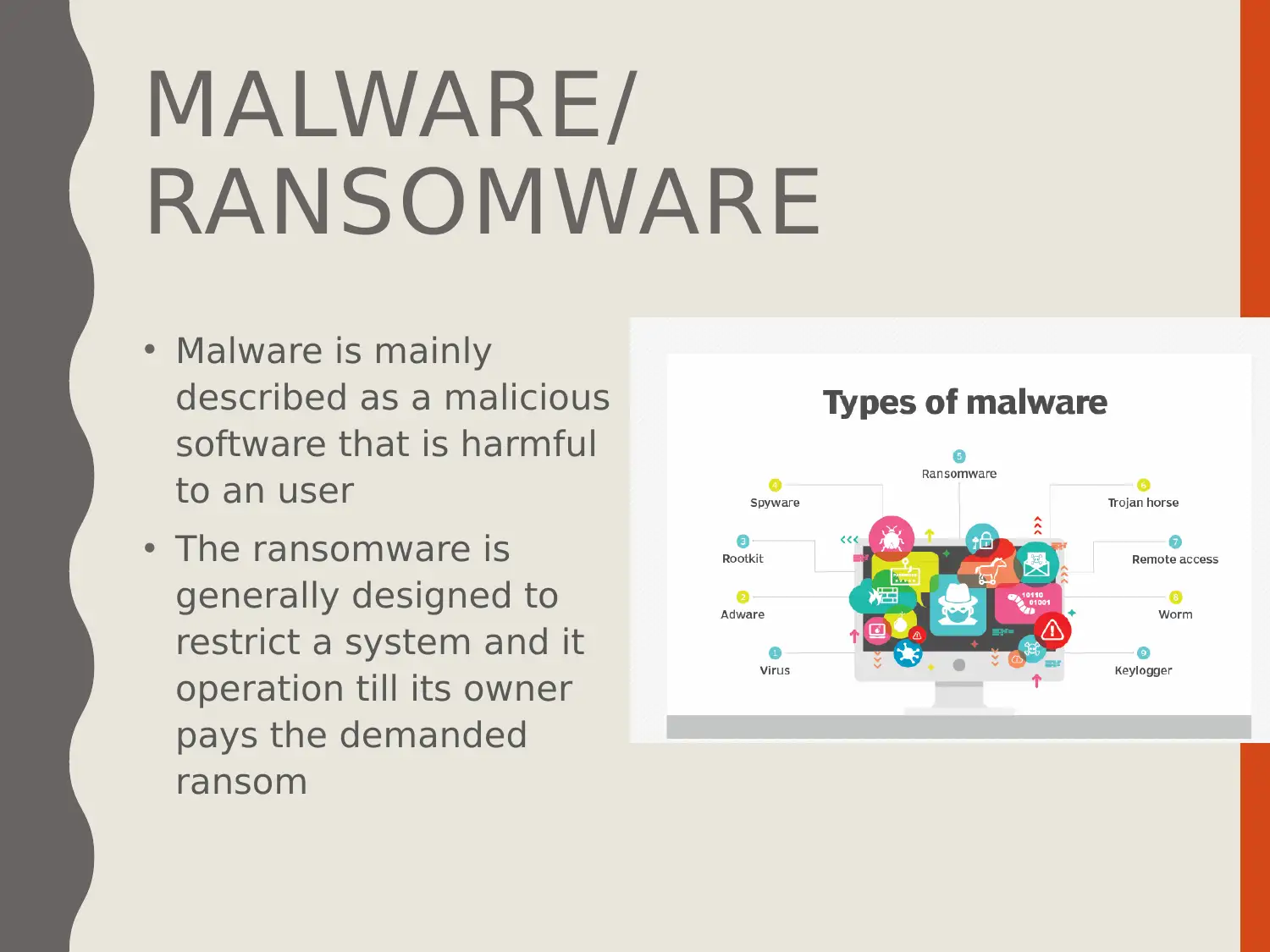
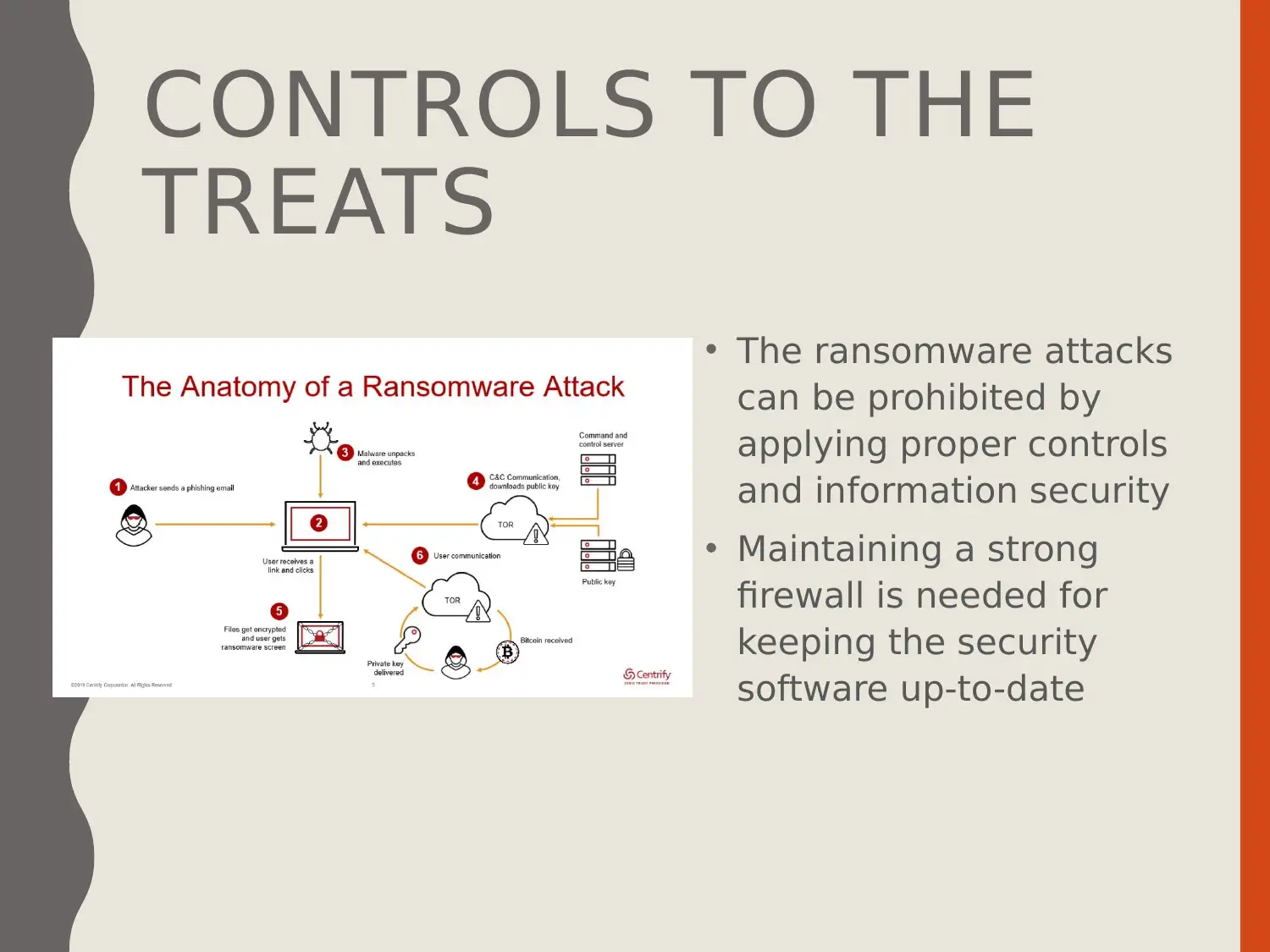
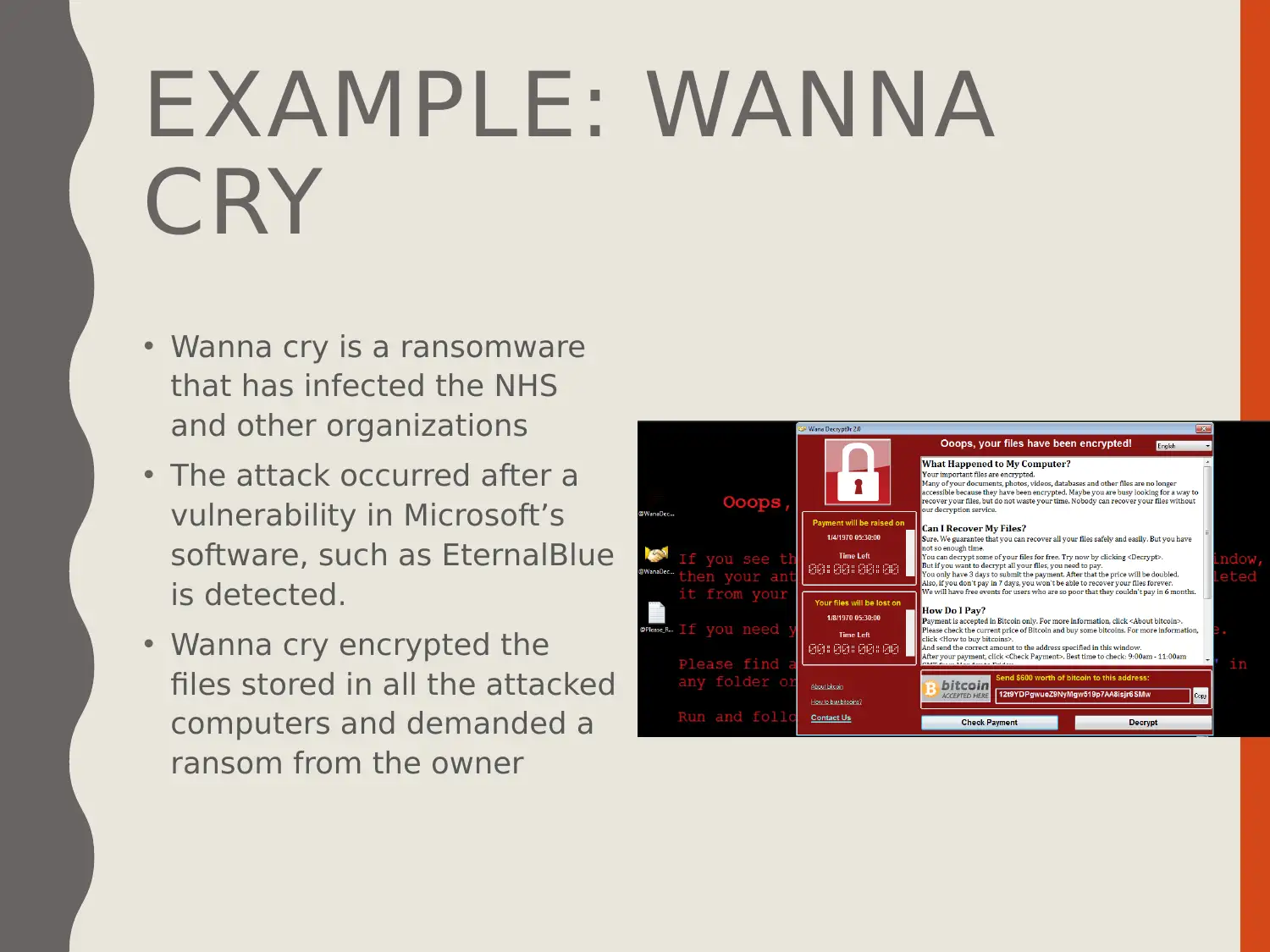
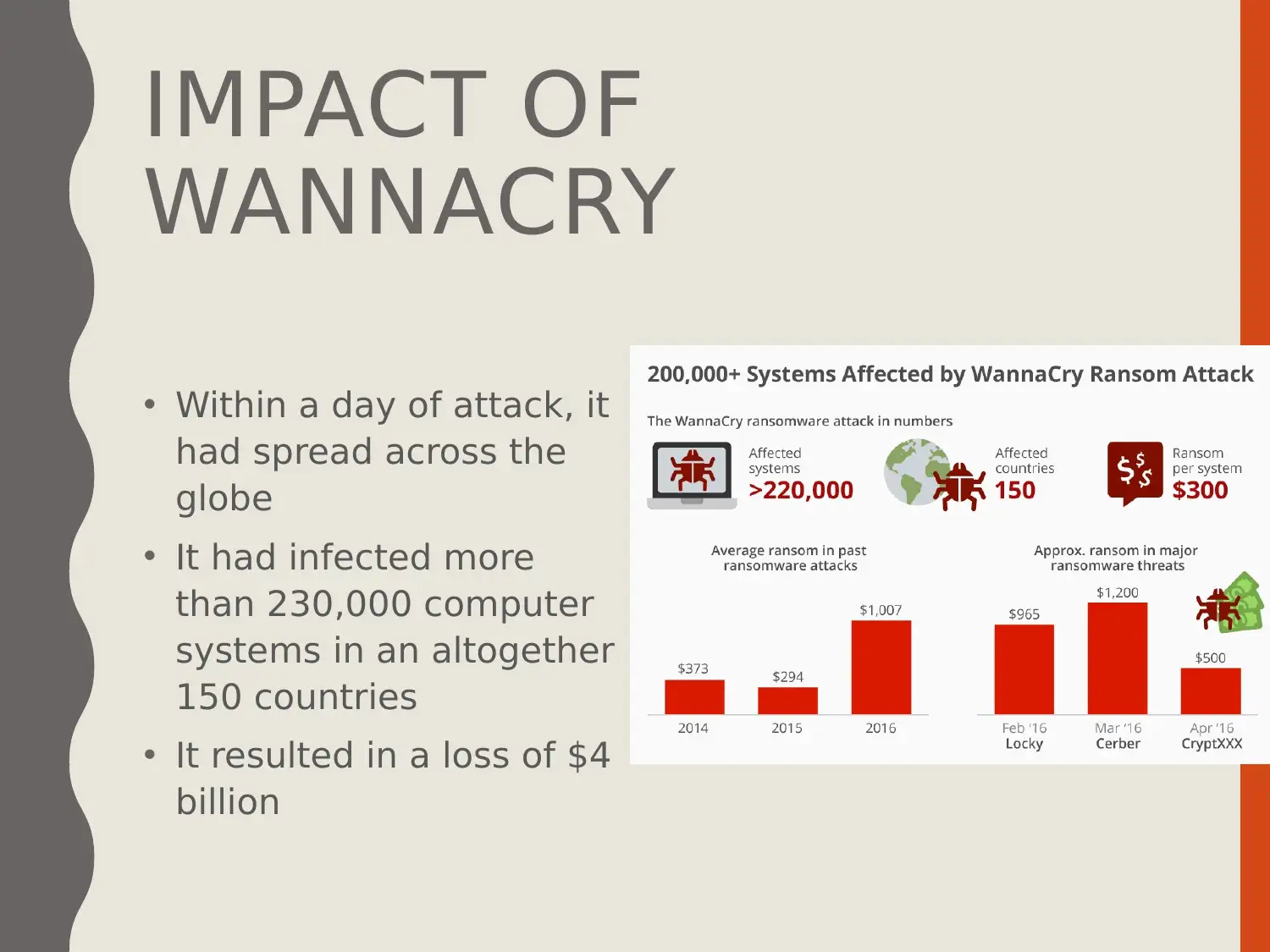
This presentation delves into the cyber security threat of ransomware, defining it as a malicious act disrupting digital resources. The presentation outlines the aims and objectives, which include comprehending the concept of cyber security, understanding ransomware, and recommending control measures. It explains ransomware as a type of malware that restricts system operation until a ransom is paid, detailing its operation and the assets targeted. The presentation covers controls for mitigating ransomware attacks, such as strong firewalls and up-to-date security software, using WannaCry as a case study to illustrate the impact and management of such threats. The presentation also provides recommendations for future work, including regular security patches and the use of antivirus software.
1 out of 19














![[object Object]](/_next/static/media/star-bottom.7253800d.svg)