ICT705 - E-Voting System Analysis: Data and System Integration
VerifiedAdded on 2023/05/28
|11
|3056
|346
Report
AI Summary
This report provides an analysis of e-voting systems through the lens of Enterprise Information Architecture (EIA). It explores the benefits of EIA in enhancing the security and efficiency of e-voting processes, particularly in the context of Australian federal elections. The report discusses the components of EIA, including technical, organizational, and business architectures, and their roles in data management and integration. It also addresses challenges such as data mapping, security, and privacy, and proposes strategies to overcome these issues, including the adoption of advanced security tools, big data, and cloud computing technologies. The report concludes with recommendations for the Australian government to improve the data analytics and security aspects of their e-voting system.

E-VOTING
0
E-Voting system
0
E-Voting system
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

E-VOTING
1
Executive summary
An electronic voting is defined as a voting process which uses electronic devices to store and
record human data. In the last few years, the use of e-voting system has increased by 50%
because it has the potential to improve the performance of federal election. This report aim
is to analysis the enterprise's information architecture with their advantages and challenges
faced by this process. It is observed that in the year 2013 there was a loss of ballot papers
during the federal election and the performance of the e-voting system can be increased by
using EIA RA process. The issue of security can be in increased by adopting advanced
security tools like firewall, encryption and cryptography. The Australian government should
ensure that they use big data and cloud computing technology to improve data analytics
and data mapping steps.
1
Executive summary
An electronic voting is defined as a voting process which uses electronic devices to store and
record human data. In the last few years, the use of e-voting system has increased by 50%
because it has the potential to improve the performance of federal election. This report aim
is to analysis the enterprise's information architecture with their advantages and challenges
faced by this process. It is observed that in the year 2013 there was a loss of ballot papers
during the federal election and the performance of the e-voting system can be increased by
using EIA RA process. The issue of security can be in increased by adopting advanced
security tools like firewall, encryption and cryptography. The Australian government should
ensure that they use big data and cloud computing technology to improve data analytics
and data mapping steps.

E-VOTING
2
Table of Contents
Executive summary...............................................................................................................................1
1.0 Introduction.....................................................................................................................................3
2.0 Enterprise information architecture reference architecture...........................................................3
Benefits of enterprise information architecture................................................................................5
Operational advantages.................................................................................................................6
Managerial benefits.......................................................................................................................6
Strategic benefits...........................................................................................................................6
3.0 Information Management and Integration......................................................................................6
A quick and accurate understanding of data.................................................................................6
Handling changes in data over time..............................................................................................7
Data mapping................................................................................................................................7
Security and privacy issues............................................................................................................7
Strategies to overcome challenges....................................................................................................7
4.0 Conclusion.......................................................................................................................................8
5.0 Recommendation............................................................................................................................8
References.............................................................................................................................................9
2
Table of Contents
Executive summary...............................................................................................................................1
1.0 Introduction.....................................................................................................................................3
2.0 Enterprise information architecture reference architecture...........................................................3
Benefits of enterprise information architecture................................................................................5
Operational advantages.................................................................................................................6
Managerial benefits.......................................................................................................................6
Strategic benefits...........................................................................................................................6
3.0 Information Management and Integration......................................................................................6
A quick and accurate understanding of data.................................................................................6
Handling changes in data over time..............................................................................................7
Data mapping................................................................................................................................7
Security and privacy issues............................................................................................................7
Strategies to overcome challenges....................................................................................................7
4.0 Conclusion.......................................................................................................................................8
5.0 Recommendation............................................................................................................................8
References.............................................................................................................................................9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

E-VOTING
3
Table of figure
Figure 1: Enterprise information architecture.......................................................................................5
Figure 2: enterprise information architecture.......................................................................................6
3
Table of figure
Figure 1: Enterprise information architecture.......................................................................................5
Figure 2: enterprise information architecture.......................................................................................6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

E-VOTING
4
1.0 Introduction
E-voting is defined as an electronic voting system that uses different types of practices and
technologies to record and count the total numbers of votes. In such kind of process, the
assistance of electronic technologies involves collecting the data or information of any
person and store in an electronic manner. In this modern era, the use of e-voting system has
increased by 40% and most countries use this technique during the federal election
(Alathur, Ilavarasan, and Gupta, 2016). The purpose of this report is to describe the concept
of the e-voting system and the role of enterprise information architecture reference
architecture in e-voting with their benefits. A recent study shows that Australian federal
government increased the efficiency of the voting process by 40% because they developed a
new approach (E-voting) which record the data of every person and stored into more
advanced computer devices (Bouras, Katris and Triantafillou, 2003). To improve the
performance and effectiveness of federal election information technology developed a new
technique that is EIA RA that will be analysis in this report. Mainly, this report is divided into
the main two parts, for example, enterprise information architecture reference architecture
and information management and integration.
2.0 Enterprise information architecture reference architecture
Term EIA is defined as part of enterprise architecture which is used to provide a common
outline for the cost-effective approach to share data across the various organizations. It is
one of the best approaches that have the potential to develop a more effective e-voting
system and Australian government can adopt this technique in order to improve the
security of individual votes (Cortier, 2015). It is observed that this technology is used by
many government authorities to reduce assessment, design and implement of the common
business language and process redundancy assessment. There are main three sub-
architectures of EIA process which are the following:
Technical architecture
Organization architecture
Business architecture
Business architecture provides an integrated opinion of the data from a business-oriented
perspective. Technical architecture provides a way to outlook the current technical
environment and migration strategy to bring the desired technical environment.
Organization architecture deals with the high-level structure of an organization and
processes completed by every person. The recent study identified that enterprise
information architecture is a kind of process that evaluates the current state, future stage,
and exchange information to achieve more effective enterprise change (Geerts, and
McCarthy, 2008). It is a map of the information concept that can be used for development
of e-voting system and Australian government can adopt this technique during generation
of electronic voting for the election. Mainly, this technique is used to identify what these
information con concepts involve, how they are designed and implemented within an
information technology system and how they are connected to each other. The architecture
of an enterprise system is divided into main four parts, for example, conceptual, logical,
physical, and governance.
4
1.0 Introduction
E-voting is defined as an electronic voting system that uses different types of practices and
technologies to record and count the total numbers of votes. In such kind of process, the
assistance of electronic technologies involves collecting the data or information of any
person and store in an electronic manner. In this modern era, the use of e-voting system has
increased by 40% and most countries use this technique during the federal election
(Alathur, Ilavarasan, and Gupta, 2016). The purpose of this report is to describe the concept
of the e-voting system and the role of enterprise information architecture reference
architecture in e-voting with their benefits. A recent study shows that Australian federal
government increased the efficiency of the voting process by 40% because they developed a
new approach (E-voting) which record the data of every person and stored into more
advanced computer devices (Bouras, Katris and Triantafillou, 2003). To improve the
performance and effectiveness of federal election information technology developed a new
technique that is EIA RA that will be analysis in this report. Mainly, this report is divided into
the main two parts, for example, enterprise information architecture reference architecture
and information management and integration.
2.0 Enterprise information architecture reference architecture
Term EIA is defined as part of enterprise architecture which is used to provide a common
outline for the cost-effective approach to share data across the various organizations. It is
one of the best approaches that have the potential to develop a more effective e-voting
system and Australian government can adopt this technique in order to improve the
security of individual votes (Cortier, 2015). It is observed that this technology is used by
many government authorities to reduce assessment, design and implement of the common
business language and process redundancy assessment. There are main three sub-
architectures of EIA process which are the following:
Technical architecture
Organization architecture
Business architecture
Business architecture provides an integrated opinion of the data from a business-oriented
perspective. Technical architecture provides a way to outlook the current technical
environment and migration strategy to bring the desired technical environment.
Organization architecture deals with the high-level structure of an organization and
processes completed by every person. The recent study identified that enterprise
information architecture is a kind of process that evaluates the current state, future stage,
and exchange information to achieve more effective enterprise change (Geerts, and
McCarthy, 2008). It is a map of the information concept that can be used for development
of e-voting system and Australian government can adopt this technique during generation
of electronic voting for the election. Mainly, this technique is used to identify what these
information con concepts involve, how they are designed and implemented within an
information technology system and how they are connected to each other. The architecture
of an enterprise system is divided into main four parts, for example, conceptual, logical,
physical, and governance.
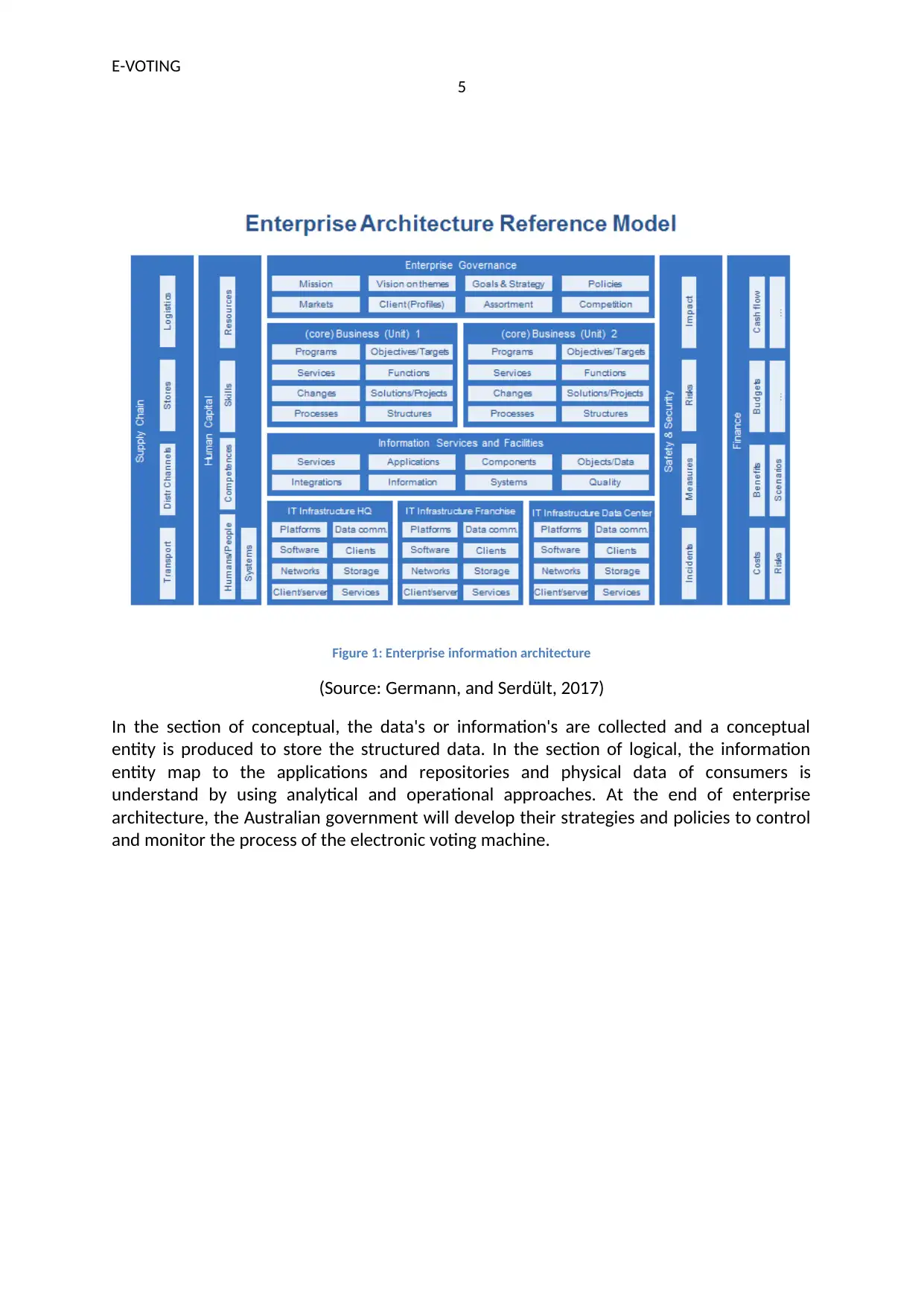
E-VOTING
5
Figure 1: Enterprise information architecture
(Source: Germann, and Serdült, 2017)
In the section of conceptual, the data's or information's are collected and a conceptual
entity is produced to store the structured data. In the section of logical, the information
entity map to the applications and repositories and physical data of consumers is
understand by using analytical and operational approaches. At the end of enterprise
architecture, the Australian government will develop their strategies and policies to control
and monitor the process of the electronic voting machine.
5
Figure 1: Enterprise information architecture
(Source: Germann, and Serdült, 2017)
In the section of conceptual, the data's or information's are collected and a conceptual
entity is produced to store the structured data. In the section of logical, the information
entity map to the applications and repositories and physical data of consumers is
understand by using analytical and operational approaches. At the end of enterprise
architecture, the Australian government will develop their strategies and policies to control
and monitor the process of the electronic voting machine.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
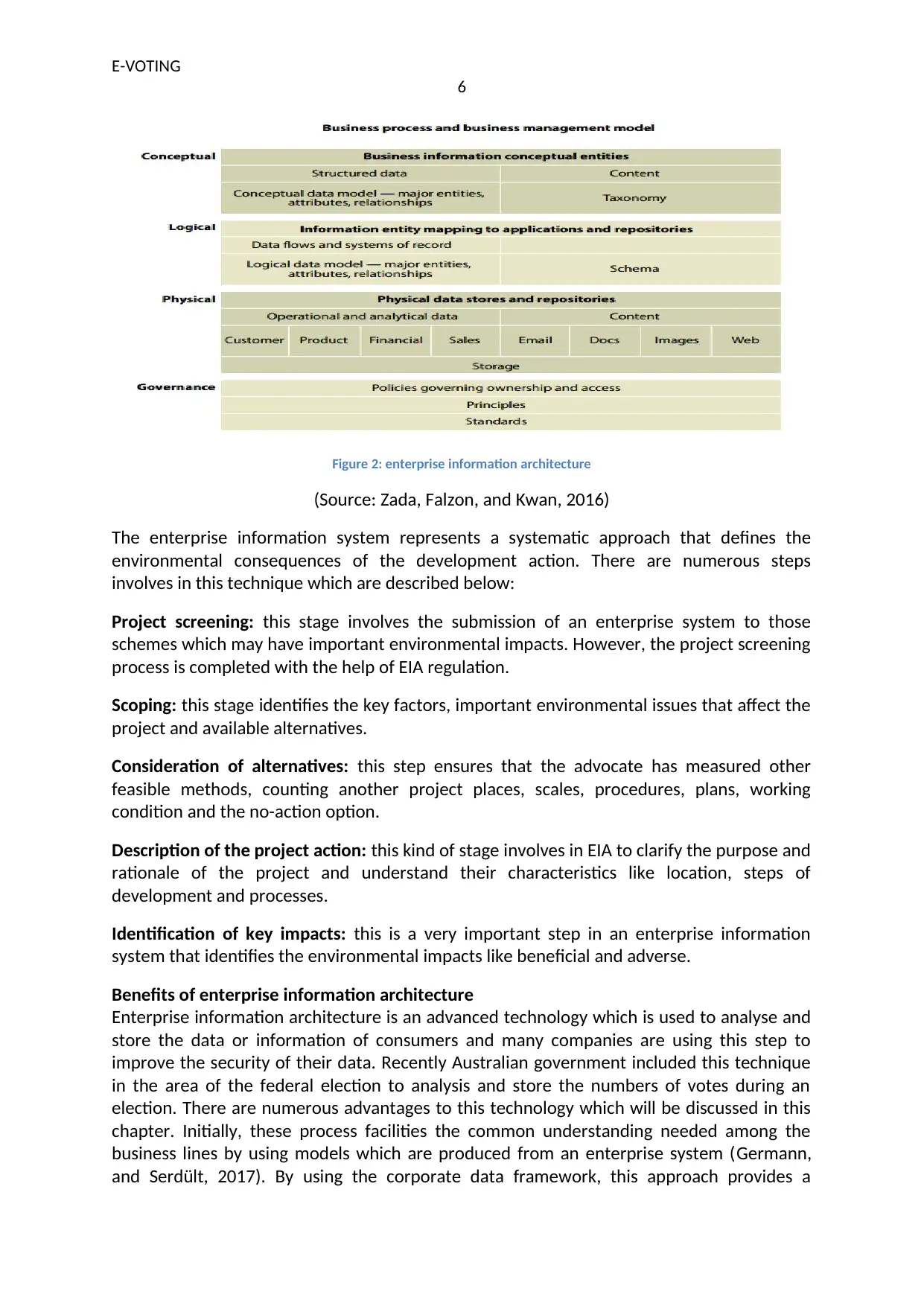
E-VOTING
6
Figure 2: enterprise information architecture
(Source: Zada, Falzon, and Kwan, 2016)
The enterprise information system represents a systematic approach that defines the
environmental consequences of the development action. There are numerous steps
involves in this technique which are described below:
Project screening: this stage involves the submission of an enterprise system to those
schemes which may have important environmental impacts. However, the project screening
process is completed with the help of EIA regulation.
Scoping: this stage identifies the key factors, important environmental issues that affect the
project and available alternatives.
Consideration of alternatives: this step ensures that the advocate has measured other
feasible methods, counting another project places, scales, procedures, plans, working
condition and the no-action option.
Description of the project action: this kind of stage involves in EIA to clarify the purpose and
rationale of the project and understand their characteristics like location, steps of
development and processes.
Identification of key impacts: this is a very important step in an enterprise information
system that identifies the environmental impacts like beneficial and adverse.
Benefits of enterprise information architecture
Enterprise information architecture is an advanced technology which is used to analyse and
store the data or information of consumers and many companies are using this step to
improve the security of their data. Recently Australian government included this technique
in the area of the federal election to analysis and store the numbers of votes during an
election. There are numerous advantages to this technology which will be discussed in this
chapter. Initially, these process facilities the common understanding needed among the
business lines by using models which are produced from an enterprise system (Germann,
and Serdült, 2017). By using the corporate data framework, this approach provides a
6
Figure 2: enterprise information architecture
(Source: Zada, Falzon, and Kwan, 2016)
The enterprise information system represents a systematic approach that defines the
environmental consequences of the development action. There are numerous steps
involves in this technique which are described below:
Project screening: this stage involves the submission of an enterprise system to those
schemes which may have important environmental impacts. However, the project screening
process is completed with the help of EIA regulation.
Scoping: this stage identifies the key factors, important environmental issues that affect the
project and available alternatives.
Consideration of alternatives: this step ensures that the advocate has measured other
feasible methods, counting another project places, scales, procedures, plans, working
condition and the no-action option.
Description of the project action: this kind of stage involves in EIA to clarify the purpose and
rationale of the project and understand their characteristics like location, steps of
development and processes.
Identification of key impacts: this is a very important step in an enterprise information
system that identifies the environmental impacts like beneficial and adverse.
Benefits of enterprise information architecture
Enterprise information architecture is an advanced technology which is used to analyse and
store the data or information of consumers and many companies are using this step to
improve the security of their data. Recently Australian government included this technique
in the area of the federal election to analysis and store the numbers of votes during an
election. There are numerous advantages to this technology which will be discussed in this
chapter. Initially, these process facilities the common understanding needed among the
business lines by using models which are produced from an enterprise system (Germann,
and Serdült, 2017). By using the corporate data framework, this approach provides a
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

E-VOTING
7
platform for the evaluation of the existing data structure and maintains the integrated set of
the data structure. Another most important advantage of this technique is the simple
integration of new business data to existing procedure setting with statistics plotted to the
Australian government model as compare to databases. It also provides a quick orientation
process for the new resources to improve the security of the electronic voting system.
Operational advantages
A recent study investigated that enterprise information architecture is a high-level
architecture system which is a more effective approach to manage the information of
consumers. It has the potential to reduce redundant efforts, operation and processes that
increase a company’s performance. With the help of this process the efficiency of the
federal system in Australia can be increased (Zada, Falzon, and Kwan, 2016).
Managerial benefits
It is observed that the enterprise system has the capability to manage and control the
complexity of information technology and provide a suitable process to handle the business
operations. It also improves the risk and change management process and risk assessment is
one of the complex tasks for every enterprise system. With the help of this method
government authority can map portfolio, mapping and optimization capabilities (Germann,
and Serdült, 2017).
Strategic benefits
According to an expert of enterprise system the EIA RA approach also increased the quality
of data and in the field of electronic voting, this technique improves the overall efficiency of
the voting process. There are many other advantages of this technology which are described
below:
Increased project success and company goal achievement
Also, provide guidance
Increased information technology alignment and options
Also increased the long-term investments
Provide consumer satisfaction process (Giachetti, 2016).
3.0 Information Management and Integration
Data management and integration both are the main key factors for the development of
electronic voting because e-voting contains a large amount of consumer’s data which is
managed by data management process. The aim of the data integration process is to cartel
dissimilar sets of data into expressive information (Niu, Da Xu, and Bi, 2013). There are
various challenged faced by these approaches in the area of electronic voting which are
described below:
A quick and accurate understanding of data
The Australian government developed the electronic voting process to improve the
efficiency of the federal election but they are facing the issue of quick response. Due to
which the experts of the EIA system are not able to understand the data sources (Pang, et
al., 2015). Such kind of problem occurs when a large amount of individual’s data collects
from different resources and e-voting process collects both structured and unstructured
7
platform for the evaluation of the existing data structure and maintains the integrated set of
the data structure. Another most important advantage of this technique is the simple
integration of new business data to existing procedure setting with statistics plotted to the
Australian government model as compare to databases. It also provides a quick orientation
process for the new resources to improve the security of the electronic voting system.
Operational advantages
A recent study investigated that enterprise information architecture is a high-level
architecture system which is a more effective approach to manage the information of
consumers. It has the potential to reduce redundant efforts, operation and processes that
increase a company’s performance. With the help of this process the efficiency of the
federal system in Australia can be increased (Zada, Falzon, and Kwan, 2016).
Managerial benefits
It is observed that the enterprise system has the capability to manage and control the
complexity of information technology and provide a suitable process to handle the business
operations. It also improves the risk and change management process and risk assessment is
one of the complex tasks for every enterprise system. With the help of this method
government authority can map portfolio, mapping and optimization capabilities (Germann,
and Serdült, 2017).
Strategic benefits
According to an expert of enterprise system the EIA RA approach also increased the quality
of data and in the field of electronic voting, this technique improves the overall efficiency of
the voting process. There are many other advantages of this technology which are described
below:
Increased project success and company goal achievement
Also, provide guidance
Increased information technology alignment and options
Also increased the long-term investments
Provide consumer satisfaction process (Giachetti, 2016).
3.0 Information Management and Integration
Data management and integration both are the main key factors for the development of
electronic voting because e-voting contains a large amount of consumer’s data which is
managed by data management process. The aim of the data integration process is to cartel
dissimilar sets of data into expressive information (Niu, Da Xu, and Bi, 2013). There are
various challenged faced by these approaches in the area of electronic voting which are
described below:
A quick and accurate understanding of data
The Australian government developed the electronic voting process to improve the
efficiency of the federal election but they are facing the issue of quick response. Due to
which the experts of the EIA system are not able to understand the data sources (Pang, et
al., 2015). Such kind of problem occurs when a large amount of individual’s data collects
from different resources and e-voting process collects both structured and unstructured

E-VOTING
8
data. The Australian government can adopt the advanced information technology to analyse
the human data and improve the performance of data integration approach.
Handling changes in data over time
This is one of the common problems faced by data integration approach in electronic voting
because various resources are updated at various intervals. It is observed that sources can
have very unusual processes for controlling updates which can cause supposition in
databases (Weerakkody, and Choudrie, 2009). It is very difficult to combine the data
collected from various resources due to which the e-voting machine faced the issue of data
handling (Reiners, 2017). Most the countries are using big data technology during the
election because it has potential to analysis the huge amount of data and information. The
data from multiple resources are completely based on the contexts and consistency due to
which the issue of handling changes occur.
Data mapping
Data mapping is a very common challenge faced by data management and data integration
process because the electronic voting method contains both unstructured and structured
data due to which the issue of data mapping occurred. To map data with stored data the
electronic voting uses business analysis, technical knowledge and domain expertise steps
(Rouhani, et al., 2015).
Security and privacy issues
Security of data is a very crucial situation of every organization because the use of
information technology is growing rapidly due to which various kinds of security threats and
risks are also increased. The electronic voting system uses internet connectivity and
computer networks and hackers develop a huge amount of traffic that transfer on the
network of e-voting due to which government can lose human data (Soomro, Shah, and
Ahmed, 2016). Data breaching, hacking, cyber-attacks, DDOS attack and malware all these
are security issues occurred in the data integration of electronic voting.
Strategies to overcome challenges
Information technology developed many security policies or strategies to improve the
performance of the information management and integration which are described below:
The Australian federal government can adopt security programmes to control data
integration issues
At the time of the election, they can perform their electronic systems and check their
availability
The excerpts of EIA RA should ensure that all security tools are working and any
problem occurs in the computer system then take action immediately.
Update software on regular basis (Xu, 2011).
Use big data and cloud computing to analysis and control both unstructured and
structured data
The government should design and implement the security plans to handle the issue
of cyber-crimes
If any unwanted signal or unauthentic networks observed in their servers than use
firewall or antivirus to block them
8
data. The Australian government can adopt the advanced information technology to analyse
the human data and improve the performance of data integration approach.
Handling changes in data over time
This is one of the common problems faced by data integration approach in electronic voting
because various resources are updated at various intervals. It is observed that sources can
have very unusual processes for controlling updates which can cause supposition in
databases (Weerakkody, and Choudrie, 2009). It is very difficult to combine the data
collected from various resources due to which the e-voting machine faced the issue of data
handling (Reiners, 2017). Most the countries are using big data technology during the
election because it has potential to analysis the huge amount of data and information. The
data from multiple resources are completely based on the contexts and consistency due to
which the issue of handling changes occur.
Data mapping
Data mapping is a very common challenge faced by data management and data integration
process because the electronic voting method contains both unstructured and structured
data due to which the issue of data mapping occurred. To map data with stored data the
electronic voting uses business analysis, technical knowledge and domain expertise steps
(Rouhani, et al., 2015).
Security and privacy issues
Security of data is a very crucial situation of every organization because the use of
information technology is growing rapidly due to which various kinds of security threats and
risks are also increased. The electronic voting system uses internet connectivity and
computer networks and hackers develop a huge amount of traffic that transfer on the
network of e-voting due to which government can lose human data (Soomro, Shah, and
Ahmed, 2016). Data breaching, hacking, cyber-attacks, DDOS attack and malware all these
are security issues occurred in the data integration of electronic voting.
Strategies to overcome challenges
Information technology developed many security policies or strategies to improve the
performance of the information management and integration which are described below:
The Australian federal government can adopt security programmes to control data
integration issues
At the time of the election, they can perform their electronic systems and check their
availability
The excerpts of EIA RA should ensure that all security tools are working and any
problem occurs in the computer system then take action immediately.
Update software on regular basis (Xu, 2011).
Use big data and cloud computing to analysis and control both unstructured and
structured data
The government should design and implement the security plans to handle the issue
of cyber-crimes
If any unwanted signal or unauthentic networks observed in their servers than use
firewall or antivirus to block them
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

E-VOTING
9
Australian federal government can adopt the cryptography and encryption
technology to improve the security of their data and information management
system.
The issue of data mapping can be resolved by using a big data approach because it
has the potential to analysis and maps both unstructured and structured data
Use the printer machine along with the e-voting system
Conduct more extensive pre-election voting machine test which avoids the future
issues faced by the Australian government
4.0 Conclusion
This report is completely based on the electronic voting system and with the help of this
research readers can expand their knowledge in the area of a federal election. Electronic
voting is one of the advanced technologies for an election that uses electronic systems,
computer devices and IT technologies to record, store and maintain consumer data. It has
the potential to improve the security of data and performance of election federal system
and Australian federal government can adopt this process to improve the effectiveness of
election. This report described the importance of enterprise information architecture with
their advantages and challenged faced by data integration and information management.
The Australian federal government should ensure that they follow the concept of enterprise
information architecture and handle consumer’s data in a more effective manner.
5.0 Recommendation
It is recommended that the issue of security is increasing due to use of unauthentic servers
and networks which can be handled by using advanced security plans like firewall, antivirus,
cryptography and encryption technology. The Australian government should adopt develop
security strategies or policies to improve the performance of the electronic voting system
and use advanced information technology to improve data mapping steps. The sensitivity of
the data can be increased by using big data and cloud computing technologies and analysis
of both unstructured and structured data can be done by using a big data approach.
9
Australian federal government can adopt the cryptography and encryption
technology to improve the security of their data and information management
system.
The issue of data mapping can be resolved by using a big data approach because it
has the potential to analysis and maps both unstructured and structured data
Use the printer machine along with the e-voting system
Conduct more extensive pre-election voting machine test which avoids the future
issues faced by the Australian government
4.0 Conclusion
This report is completely based on the electronic voting system and with the help of this
research readers can expand their knowledge in the area of a federal election. Electronic
voting is one of the advanced technologies for an election that uses electronic systems,
computer devices and IT technologies to record, store and maintain consumer data. It has
the potential to improve the security of data and performance of election federal system
and Australian federal government can adopt this process to improve the effectiveness of
election. This report described the importance of enterprise information architecture with
their advantages and challenged faced by data integration and information management.
The Australian federal government should ensure that they follow the concept of enterprise
information architecture and handle consumer’s data in a more effective manner.
5.0 Recommendation
It is recommended that the issue of security is increasing due to use of unauthentic servers
and networks which can be handled by using advanced security plans like firewall, antivirus,
cryptography and encryption technology. The Australian government should adopt develop
security strategies or policies to improve the performance of the electronic voting system
and use advanced information technology to improve data mapping steps. The sensitivity of
the data can be increased by using big data and cloud computing technologies and analysis
of both unstructured and structured data can be done by using a big data approach.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

E-VOTING
10
References
Alathur, S., Ilavarasan, P.V. and Gupta, M.P., (2016) Determinants of e-participation in the
citizens and the government initiatives: Insights from India. Socio-Economic Planning
Sciences, 55(1), pp.25-35.
Bouras, C., Katris, N. and Triantafillou, V., (2003) An electronic voting service to support
decision-making in local government. Telematics and Informatics, 20(3), pp.255-274.
Cortier, V., (2015) Formal verification of e-voting: solutions and challenges. ACM SIGLOG
News, 2(1), pp.25-34.
Geerts, G.L. and McCarthy, W.E., (2008) An ontological analysis of the economic primitives
of the extended-REA enterprise information architecture. International Journal of
Accounting Information Systems, 3(1), pp.1-16.
Germann, M. and Serdült, U., (2017) Internet voting and turnout: Evidence from
Switzerland. Electoral Studies, 47(2), pp.1-12.
Giachetti, R.E., (2016) Design of enterprise systems: Theory, architecture, and methods. CRC
Press.
Niu, N., Da Xu, L. and Bi, Z., (2013) Enterprise information systems architecture—Analysis
and evaluation. IEEE Transactions on Industrial Informatics, 9(4), pp.2147-2154.
Pang, Z., Chen, Q., Han, W. and Zheng, L., (2015) Value-centric design of the internet-of-
things solution for food supply chain: Value creation, sensor portfolio and information
fusion. Information Systems Frontiers, 17(2), pp.289-319.
Reiners, M., (2017) Electronic Voting in Comparative Perspective: Status Quo in Estonia and
Trends in Central Europe. Journal of Comparative Politics, 10(1), p.40.
Rouhani, B.D., Mahrin, M.N.R., Nikpay, F., Ahmad, R.B. and Nikfard, P., (2015) A systematic
literature review on Enterprise Architecture Implementation Methodologies. Information
and Software Technology, 62(1), pp.1-20.
Soomro, Z.A., Shah, M.H. and Ahmed, J., (2016) Information security management needs a
more holistic approach: A literature review. International Journal of Information
Management, 36(2), pp.215-225.
Weerakkody, V. and Choudrie, J., (2009) Exploring e-government in the UK: Challenges,
issues and complexities. Journal of Information Science & Technology, 2(2), pp. 12-16.
Xu, L.D., (2011) Information architecture for supply chain quality management. International
Journal of Production Research, 49(1), pp.183-198.
Zada, P., Falzon, G. and Kwan, P., (2016) Perceptions of the Australian public towards mobile
internet e-voting: risks, choice and trust. Electronic Journal of e-Government, 14(1), pp.117-
34.
10
References
Alathur, S., Ilavarasan, P.V. and Gupta, M.P., (2016) Determinants of e-participation in the
citizens and the government initiatives: Insights from India. Socio-Economic Planning
Sciences, 55(1), pp.25-35.
Bouras, C., Katris, N. and Triantafillou, V., (2003) An electronic voting service to support
decision-making in local government. Telematics and Informatics, 20(3), pp.255-274.
Cortier, V., (2015) Formal verification of e-voting: solutions and challenges. ACM SIGLOG
News, 2(1), pp.25-34.
Geerts, G.L. and McCarthy, W.E., (2008) An ontological analysis of the economic primitives
of the extended-REA enterprise information architecture. International Journal of
Accounting Information Systems, 3(1), pp.1-16.
Germann, M. and Serdült, U., (2017) Internet voting and turnout: Evidence from
Switzerland. Electoral Studies, 47(2), pp.1-12.
Giachetti, R.E., (2016) Design of enterprise systems: Theory, architecture, and methods. CRC
Press.
Niu, N., Da Xu, L. and Bi, Z., (2013) Enterprise information systems architecture—Analysis
and evaluation. IEEE Transactions on Industrial Informatics, 9(4), pp.2147-2154.
Pang, Z., Chen, Q., Han, W. and Zheng, L., (2015) Value-centric design of the internet-of-
things solution for food supply chain: Value creation, sensor portfolio and information
fusion. Information Systems Frontiers, 17(2), pp.289-319.
Reiners, M., (2017) Electronic Voting in Comparative Perspective: Status Quo in Estonia and
Trends in Central Europe. Journal of Comparative Politics, 10(1), p.40.
Rouhani, B.D., Mahrin, M.N.R., Nikpay, F., Ahmad, R.B. and Nikfard, P., (2015) A systematic
literature review on Enterprise Architecture Implementation Methodologies. Information
and Software Technology, 62(1), pp.1-20.
Soomro, Z.A., Shah, M.H. and Ahmed, J., (2016) Information security management needs a
more holistic approach: A literature review. International Journal of Information
Management, 36(2), pp.215-225.
Weerakkody, V. and Choudrie, J., (2009) Exploring e-government in the UK: Challenges,
issues and complexities. Journal of Information Science & Technology, 2(2), pp. 12-16.
Xu, L.D., (2011) Information architecture for supply chain quality management. International
Journal of Production Research, 49(1), pp.183-198.
Zada, P., Falzon, G. and Kwan, P., (2016) Perceptions of the Australian public towards mobile
internet e-voting: risks, choice and trust. Electronic Journal of e-Government, 14(1), pp.117-
34.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





