ICTNWK403 Project: Network Security and Data Integrity for Aged Care
VerifiedAdded on 2023/03/31
|62
|2549
|302
Project
AI Summary
This project focuses on implementing and configuring network security for a small aged-care not-for-profit organization. The goal is to create policies, implement technologies to mitigate risks, and analyze existing systems to enhance security. The project covers key areas such as creating an effective antivirus security policy, installing antivirus software, developing information security awareness training, configuring security on routers and switches, and implementing Group Policy Objects (GPO). It also includes establishing security policies, configuring user permissions, managing file and folder access, developing an inventory system, configuring firewalls and VPNs, and setting up DHCP and DNS. Furthermore, the project addresses data backup and integrity checks, monitoring logon events, creating DMZs and VLANs, setting up VPNs between sites, enforcing password policies, and implementing physical and environmental security measures. The project concludes with network performance monitoring, generating security reports, auditing security access, identifying threats and risks, making recommendations, creating a baseline, documenting the system, reviewing logs for intrusions, and conducting spot checks for potential breaches. This comprehensive approach aims to secure the organization's network and data against viruses, malicious code, and potential disasters.

University
Semester
ICTNWK403 Manage Network and
Data Integrity
Student ID
Student Name
Submission Date
1
Semester
ICTNWK403 Manage Network and
Data Integrity
Student ID
Student Name
Submission Date
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Project Description........................................................................................................................4
2. Create an effective antivirus security policy..................................................................................4
3. Install antivirus software on all appropriate systems.....................................................................6
4. Develop information security awareness training........................................................................19
5. Configure Security on the Router / modem..................................................................................21
6. Configure security on the switch.................................................................................................23
7. Configure GPO............................................................................................................................26
8. Install suitable security software no.............................................................................................27
9. Establish security policy..............................................................................................................33
10. Configure user permissions / authenticate users......................................................................35
11. Configure file and folder access permissions...........................................................................37
12. Develop and configure inventory system.................................................................................42
13. Configure firewall....................................................................................................................43
14. Configure VPN........................................................................................................................44
15. Configure DHCP.....................................................................................................................45
16. Configure DNS........................................................................................................................46
17. Configure Certificates..............................................................................................................47
18. Create backup solution.............................................................................................................47
19. Check integrity of your data....................................................................................................48
20. Monitor logon events to the domain........................................................................................49
21. Create DMZ.............................................................................................................................49
22. Create VLANS........................................................................................................................50
23. Set VPN between sites.............................................................................................................51
24. Display warning message before user loges in.........................................................................52
25. Enforce password policy..........................................................................................................52
26. Enforce physical and environmental security...........................................................................53
27. Install network performance tools............................................................................................54
28. Generate network reports.........................................................................................................54
29. Audit and record security access..............................................................................................54
30. Determine threats / identify risks.............................................................................................55
31. Make recommendations...........................................................................................................55
32. Create baseline.........................................................................................................................56
2
1. Project Description........................................................................................................................4
2. Create an effective antivirus security policy..................................................................................4
3. Install antivirus software on all appropriate systems.....................................................................6
4. Develop information security awareness training........................................................................19
5. Configure Security on the Router / modem..................................................................................21
6. Configure security on the switch.................................................................................................23
7. Configure GPO............................................................................................................................26
8. Install suitable security software no.............................................................................................27
9. Establish security policy..............................................................................................................33
10. Configure user permissions / authenticate users......................................................................35
11. Configure file and folder access permissions...........................................................................37
12. Develop and configure inventory system.................................................................................42
13. Configure firewall....................................................................................................................43
14. Configure VPN........................................................................................................................44
15. Configure DHCP.....................................................................................................................45
16. Configure DNS........................................................................................................................46
17. Configure Certificates..............................................................................................................47
18. Create backup solution.............................................................................................................47
19. Check integrity of your data....................................................................................................48
20. Monitor logon events to the domain........................................................................................49
21. Create DMZ.............................................................................................................................49
22. Create VLANS........................................................................................................................50
23. Set VPN between sites.............................................................................................................51
24. Display warning message before user loges in.........................................................................52
25. Enforce password policy..........................................................................................................52
26. Enforce physical and environmental security...........................................................................53
27. Install network performance tools............................................................................................54
28. Generate network reports.........................................................................................................54
29. Audit and record security access..............................................................................................54
30. Determine threats / identify risks.............................................................................................55
31. Make recommendations...........................................................................................................55
32. Create baseline.........................................................................................................................56
2

33. Modify system if required........................................................................................................56
34. Document your system............................................................................................................56
35. Review logs for possible intrusions.........................................................................................57
36. Carry out spot checks / document possible breaches...............................................................58
References...........................................................................................................................................60
3
34. Document your system............................................................................................................56
35. Review logs for possible intrusions.........................................................................................57
36. Carry out spot checks / document possible breaches...............................................................58
References...........................................................................................................................................60
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1. Project Description
The main aim of this project is to implement, install and configure the network security and
to use it for data production. The process of analysis and systems is to create policies, enforce
technologies to minimize risk and make them more secure for the structure on the network
configuration. The main objective of the project is to use it for the development and manage
the antivirus system for the workstation, email filtering and server of the networking system.
The selected firm has 20 desktop and 20 laptop computers. The identification of the virus is
done by analysing it by two methods that are denoted as, Viruses and Malicious code on the
network. Disaster Recovery and Business management planning on the network security will
be investigated.
2. Create an effective antivirus security policy
Creating of the antivirus security software should mainly be specified for
the detection of the viruses on the computer and laptop. Analysis of each laptop and computer
for malicious threats shall be carried out for the pc so as to keep them in good condition. The
advanced security of the Comoro antivirus can be used for the detection of the virus and to
identify the same on each computer for any malicious attacks, to protect all the computers,
remove any malicious file and only access given for the important data of the computer
security. The Comoro antivirus features are given below (Gollmann, 2011),
Detects suspicious files immediately
Offers intelligent definition technique
Real time protection
Instant and quick update on the latest virus definition.
Access scanning.
4
The main aim of this project is to implement, install and configure the network security and
to use it for data production. The process of analysis and systems is to create policies, enforce
technologies to minimize risk and make them more secure for the structure on the network
configuration. The main objective of the project is to use it for the development and manage
the antivirus system for the workstation, email filtering and server of the networking system.
The selected firm has 20 desktop and 20 laptop computers. The identification of the virus is
done by analysing it by two methods that are denoted as, Viruses and Malicious code on the
network. Disaster Recovery and Business management planning on the network security will
be investigated.
2. Create an effective antivirus security policy
Creating of the antivirus security software should mainly be specified for
the detection of the viruses on the computer and laptop. Analysis of each laptop and computer
for malicious threats shall be carried out for the pc so as to keep them in good condition. The
advanced security of the Comoro antivirus can be used for the detection of the virus and to
identify the same on each computer for any malicious attacks, to protect all the computers,
remove any malicious file and only access given for the important data of the computer
security. The Comoro antivirus features are given below (Gollmann, 2011),
Detects suspicious files immediately
Offers intelligent definition technique
Real time protection
Instant and quick update on the latest virus definition.
Access scanning.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
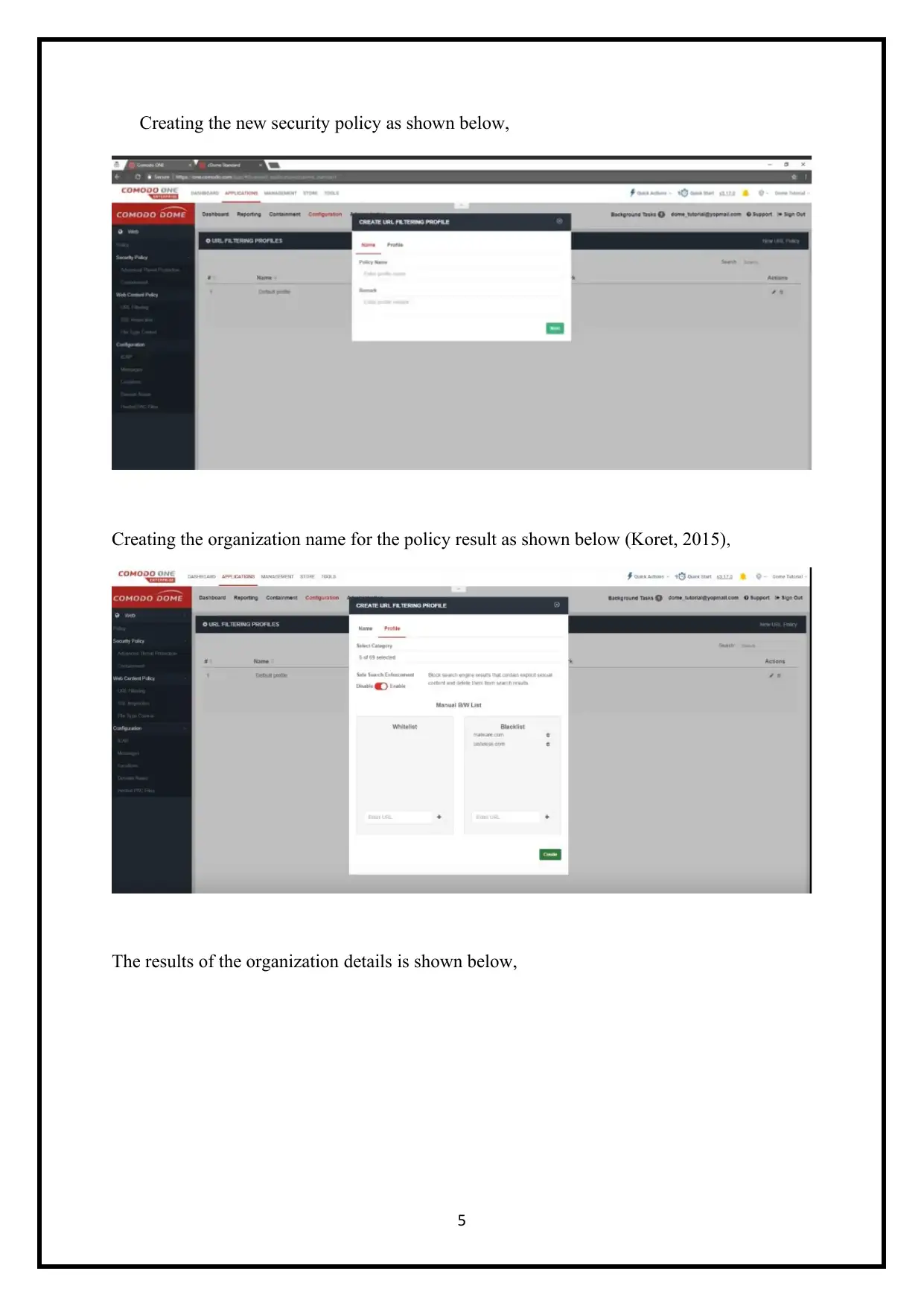
Creating the new security policy as shown below,
Creating the organization name for the policy result as shown below (Koret, 2015),
The results of the organization details is shown below,
5
Creating the organization name for the policy result as shown below (Koret, 2015),
The results of the organization details is shown below,
5
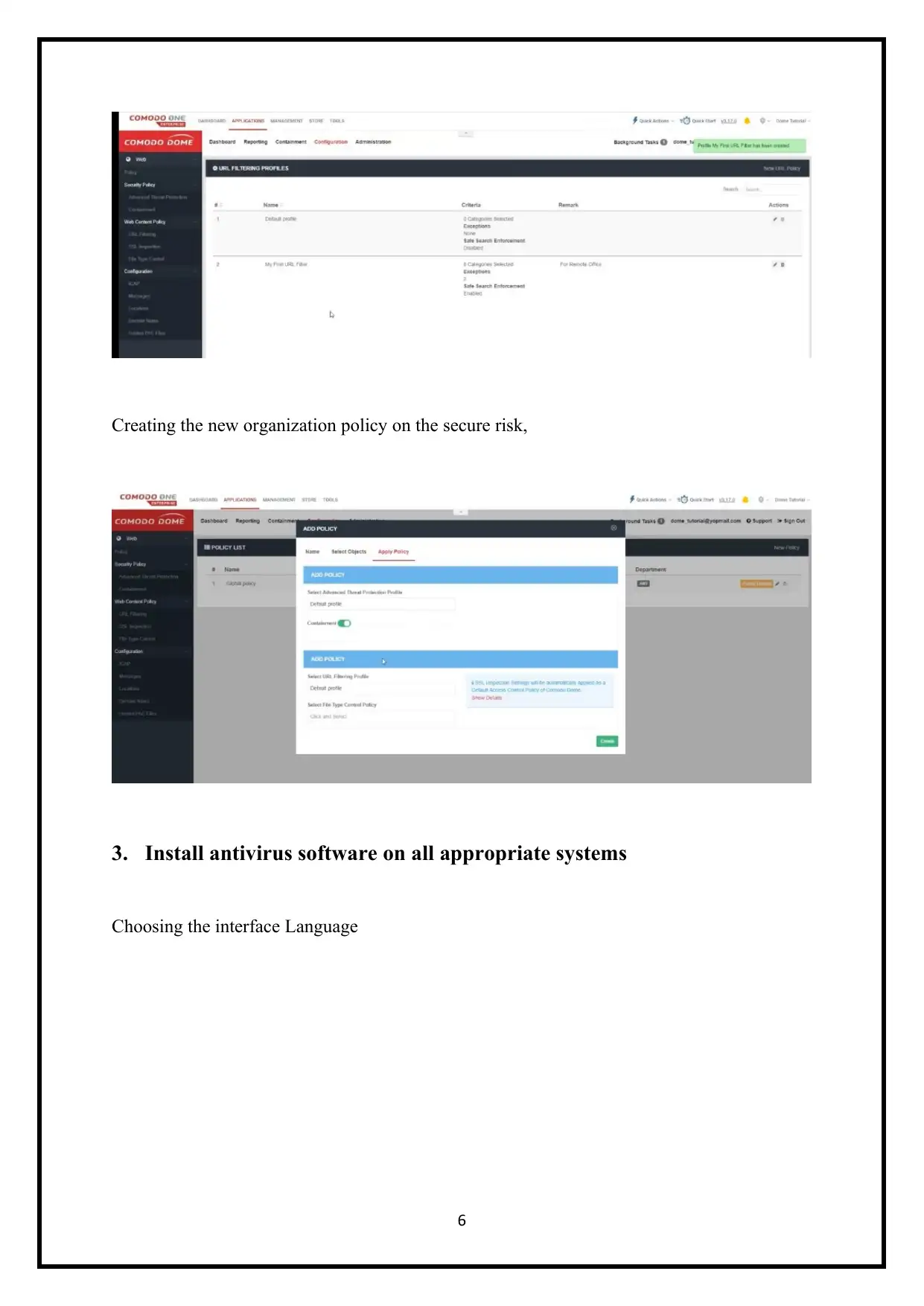
Creating the new organization policy on the secure risk,
3. Install antivirus software on all appropriate systems
Choosing the interface Language
6
3. Install antivirus software on all appropriate systems
Choosing the interface Language
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
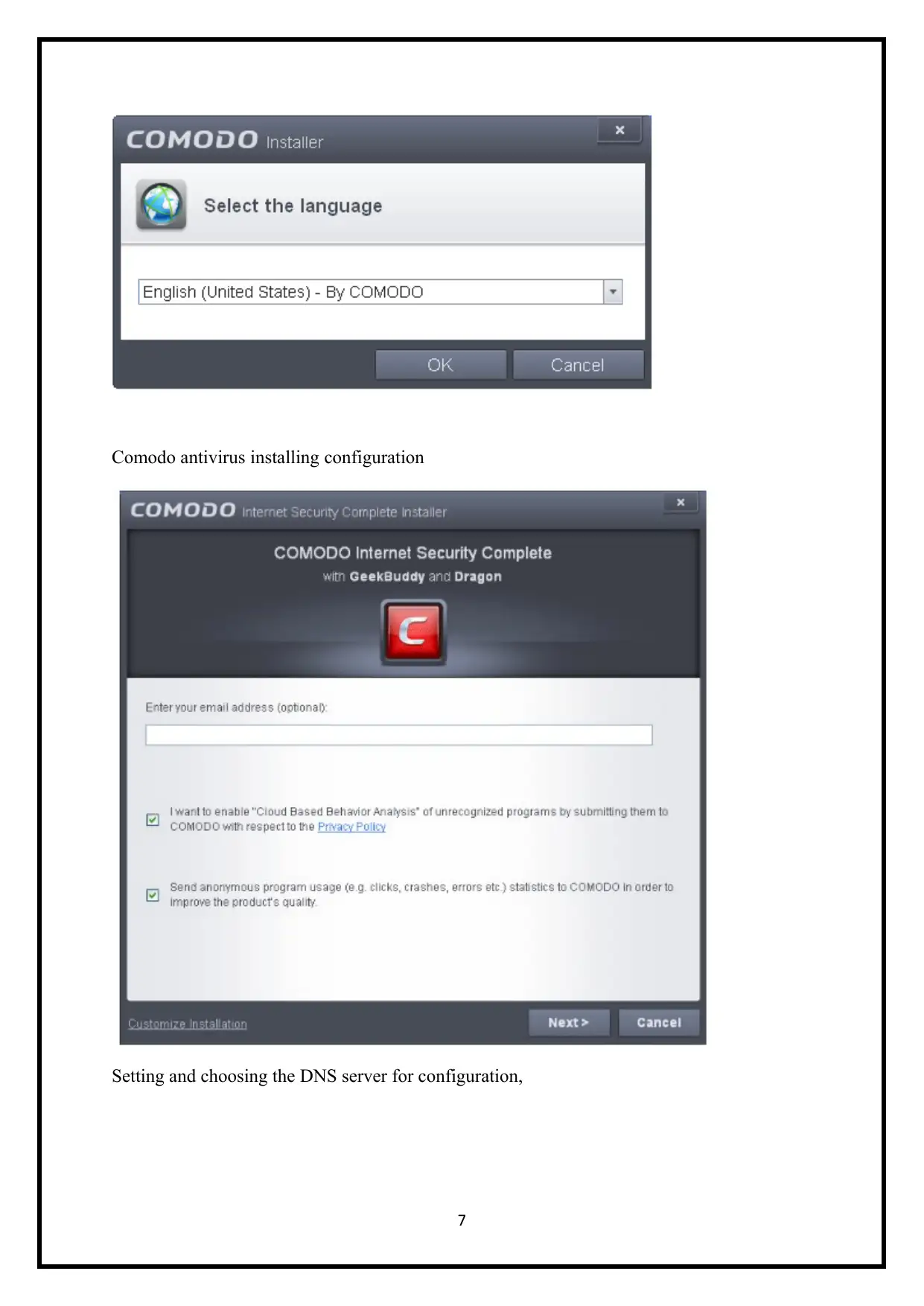
Comodo antivirus installing configuration
Setting and choosing the DNS server for configuration,
7
Setting and choosing the DNS server for configuration,
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
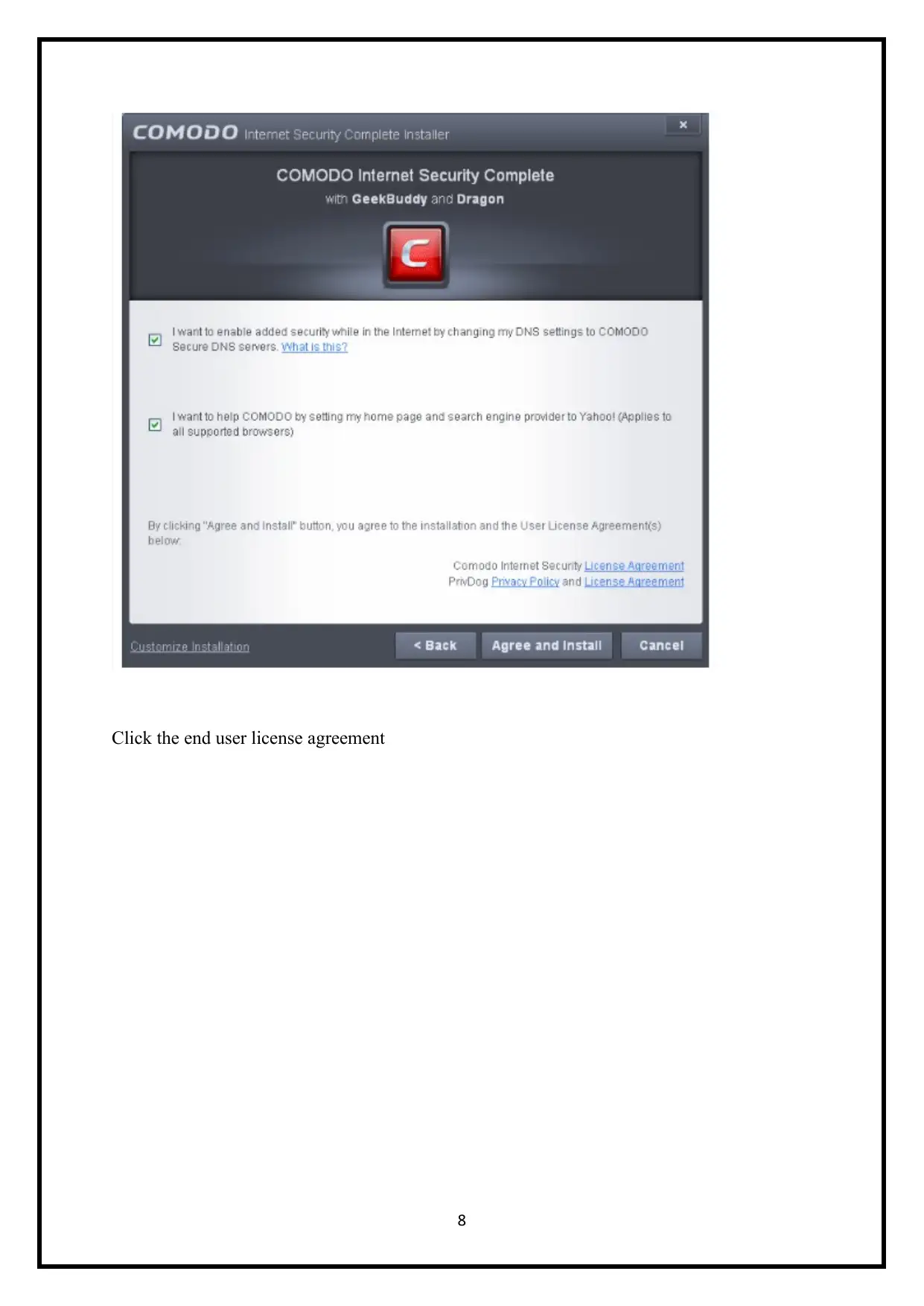
Click the end user license agreement
8
8
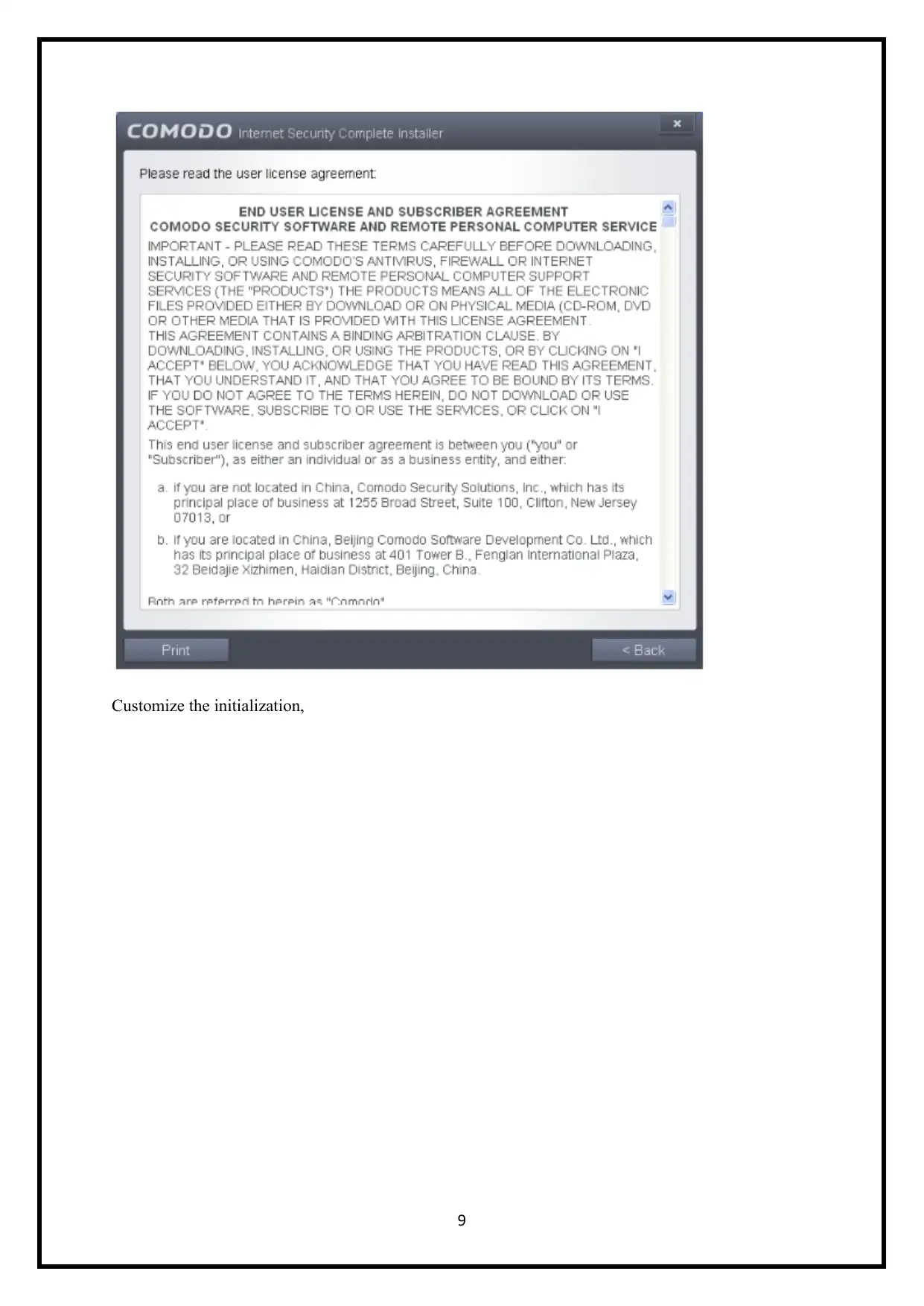
Customize the initialization,
9
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
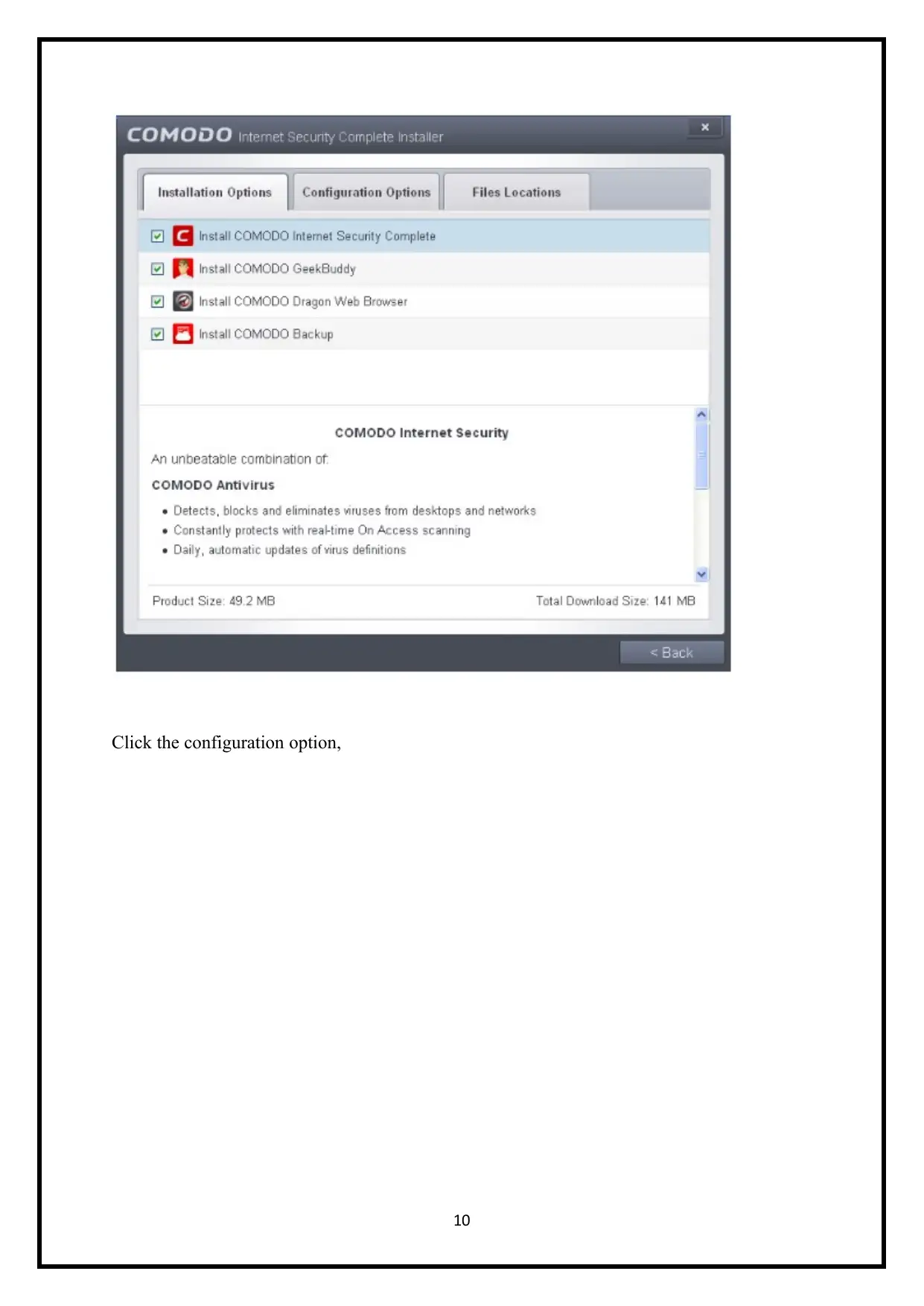
Click the configuration option,
10
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
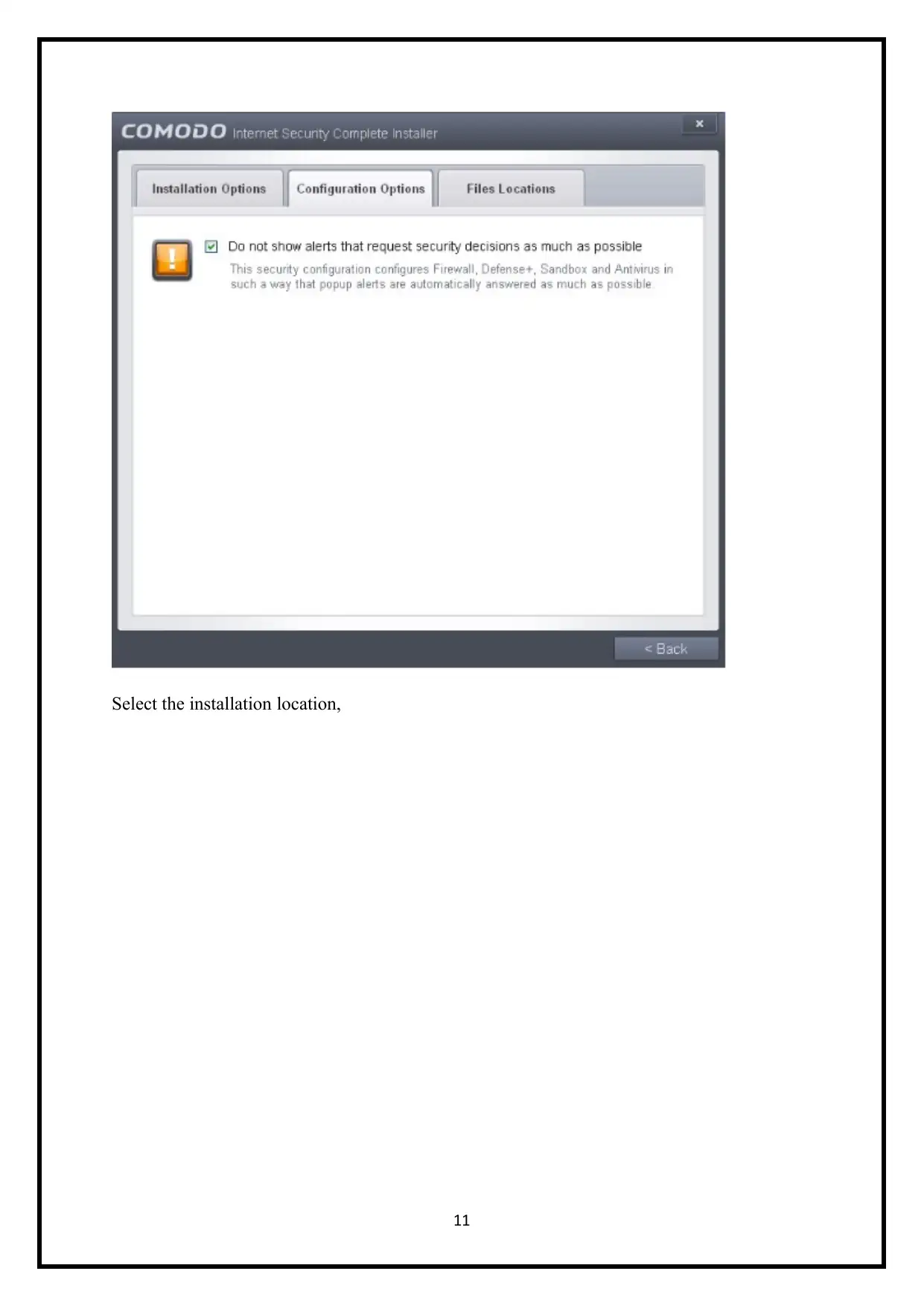
Select the installation location,
11
11
Comodo antiviruses’ installation is in progress as displayed in the below image,
12
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 62
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





